Introduction
Ever noticed the little padlock icon in your browser's address bar when you visit websites like your bank or an online store? That tiny symbol represents a powerful security mechanism that keeps your data safe while traveling across the internet. Behind that padlock is something called an SSL/TLS certificate.
In today's digital world, where data breaches and privacy concerns dominate headlines, understanding the basics of web security isn't just for IT professionals anymore. Whether you're a website owner, a developer, or just someone who cares about online privacy, knowing how SSL/TLS certificates work can help you make better decisions about your digital safety.
This guide breaks down what digital certificates are, why they're essential for website security, and how you can implement them yourself. No computer science degree required—promise!
What is a Digital Certificate?
A digital certificate is essentially an electronic document that serves two critical functions:
- It confirms that a website is who it claims to be (authentication)
- It enables encrypted connections between browsers and web servers (security)
Think of it as a digital ID card that websites use to prove their identity to your browser. Without certificates, anyone could create a fake version of your bank's website, and you'd have no reliable way to tell the difference.
When you visit a website that has a valid certificate, your browser displays "HTTPS" in the address bar (instead of just "HTTP") along with that reassuring padlock icon. This visual cue tells you that your connection to the site is encrypted and secure.
What Is an SSL/TLS Certificate?
SSL (Secure Sockets Layer) and its more modern successor TLS (Transport Layer Security) certificates are the standard technology for keeping internet connections secure and safeguarding sensitive data.
Purpose: Identity Verification + Encryption
SSL/TLS certificates serve two primary purposes:
- Identity Verification: They confirm that the website you're connecting to is legitimate and not an impostor.
- Encryption: They establish encrypted connections that prevent hackers from reading or modifying data as it travels between your browser and the website.
Components of a Certificate
A typical SSL/TLS certificate contains:
- Public Key: Used to establish the encrypted connection
- Subject: The identity of the website or organization (domain name, business name)
- Issuer: The Certificate Authority (CA) that verified and issued the certificate
- Validity Period: Start and expiry dates
- Digital Signature: From the issuing CA to prevent tampering
- Serial Number: A unique identifier for the certificate

Types of SSL/TLS Certificates
There are three main types of certificates, each with different levels of validation:
-
Domain Validation (DV) Certificates: The most basic type, verifying only domain ownership. Quick to obtain but provide minimal trust signals to visitors.
-
Organization Validation (OV) Certificates: Verify both domain ownership and some business information. Provide more trust than DV certificates.
-
Extended Validation (EV) Certificates: The highest level of validation, requiring extensive verification of the organization's identity. These certificates used to turn the address bar green in browsers (though this visual indicator has been phased out in most modern browsers).
Role of Certificate Authorities (CAs)
Certificate Authorities are trusted third parties that issue certificates after verifying the requester's identity. Well-known CAs include:
- DigiCert
- Let's Encrypt (free)
- Comodo/Sectigo
- GoDaddy
- GlobalSign
The entire system relies on browsers trusting these CAs. Your browser comes pre-loaded with a list of trusted root certificates from major CAs, which enables the chain of trust necessary for the system to work.
How HTTPS Works with Certificates
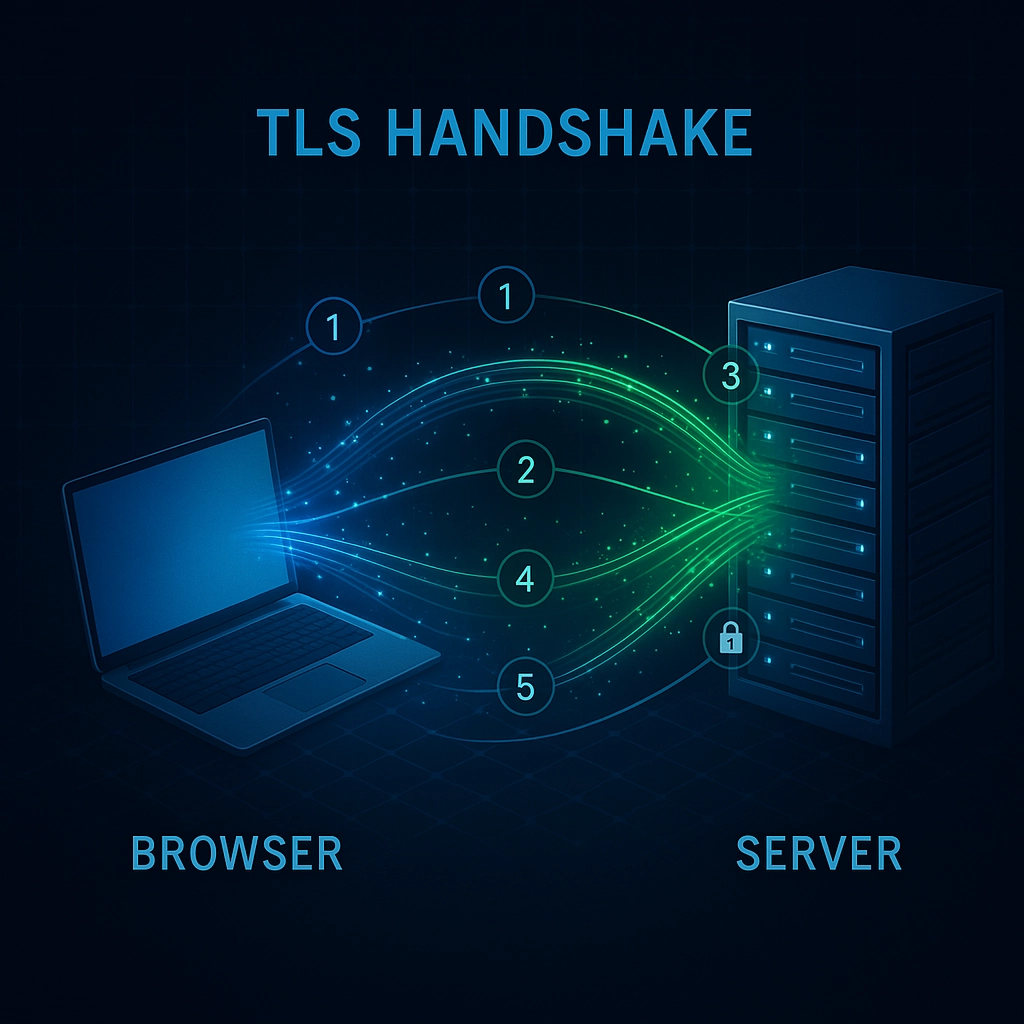
When you connect to a website using HTTPS, your browser and the web server perform a complex dance called the "TLS handshake." This process establishes a secure connection before any actual data is transmitted.
TLS Handshake Overview
The TLS handshake happens in milliseconds and involves several steps:
-
Client Hello: Your browser sends a message to the server indicating it wants to establish a secure connection and listing the encryption methods it supports.
-
Server Hello: The server responds by selecting an encryption method and sending its SSL/TLS certificate.
-
Certificate Validation: Your browser verifies that the certificate is valid, trusted, and matches the domain you're trying to visit.
-
Key Exchange: Both sides exchange information to create a shared secret key that will be used for encrypting the actual data.
-
Secure Connection Established: Both sides confirm they're ready to begin encrypted communication.
Public/Private Key Encryption Explained
SSL/TLS uses a combination of asymmetric (public-private key) and symmetric encryption:
-
Asymmetric Encryption: Uses two different but mathematically related keys. What one key encrypts, only the other can decrypt. This is used during the initial handshake.
-
Symmetric Encryption: Uses a single key that both parties know. This is much faster than asymmetric encryption and is used for the actual data transfer after the handshake.
The clever part is how these are combined: the certificate contains the server's public key, which is used to securely exchange the symmetric key that will be used for the rest of the session.
What Is a Certificate Signing Request (CSR)?
A Certificate Signing Request is the first step in obtaining an SSL/TLS certificate. It's a block of encoded text that contains information about the entity requesting the certificate and the public key that will be included in the certificate.
Definition and Purpose
A CSR is essentially an application for a digital certificate. When you generate a CSR, you're creating a request that contains all the information a CA needs to create a certificate specifically for your domain or organization.
Information Included in a CSR
A typical CSR includes:
- Common Name (CN): The fully qualified domain name (e.g., www.example.com)
- Organization (O): Your company or entity name
- Organizational Unit (OU): Department within the organization (e.g., IT, Marketing)
- Locality (L): City
- State/Province (ST): Full state or province name
- Country (C): Two-letter country code (e.g., US, UK)
- Email Address: Administrative contact
Here's what a CSR might look like in encoded form:
-----BEGIN CERTIFICATE REQUEST-----
MIICzjCCAbYCAQAwgYgxCzAJBgNVBAYTAlVTMRMwEQYDVQQIDApDYWxpZm9ybmlh
MRYwFAYDVQQHDA1TYW4gRnJhbmNpc2NvMRQwEgYDVQQKDAtFeGFtcGxlIEluYzEX
MBUGA1UECwwOSVQgRGVwYXJ0bWVudDEdMBsGA1UEAwwUd3d3LmV4YW1wbGVjb21w
YW55LmNvbTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAMzDlS+1OT9/
... (additional encoded data) ...
9Qq1LqyNDnwCl5LyUxey+n6K2FRCMGzW5kBNUlpP4/SVVvP+H18aA3aOl3LN6Odl
56FaAU8=
-----END CERTIFICATE REQUEST-----
Why You Can't Use the Same CSR for Multiple Certificates
In most cases, you can't reuse a CSR for multiple certificates because:
- The CSR contains a unique public key that corresponds to a specific private key
- Certificate details like expiration dates would be inconsistent
- Some CAs track CSRs to prevent duplication or fraud
There are some exceptions for wildcard or multi-domain certificates, but generally, it's best practice to generate a fresh CSR for each certificate request.
Creating a CSR and Private Key
Creating a CSR is straightforward using OpenSSL, a widely available open-source toolkit for SSL/TLS.
Using OpenSSL to Generate a Private Key and CSR
The following command generates both a new private key and a CSR in one step:
openssl req -new -newkey rsa:2048 -nodes -keyout mydomain.key -out mydomain.csr
Let's break down what each flag means:
req -new: Create a new CSR-newkey rsa:2048: Generate a new 2048-bit RSA key pair-nodes: Don't encrypt the private key (No DES encryption)-keyout mydomain.key: File to write the private key to-out mydomain.csr: File to write the CSR to
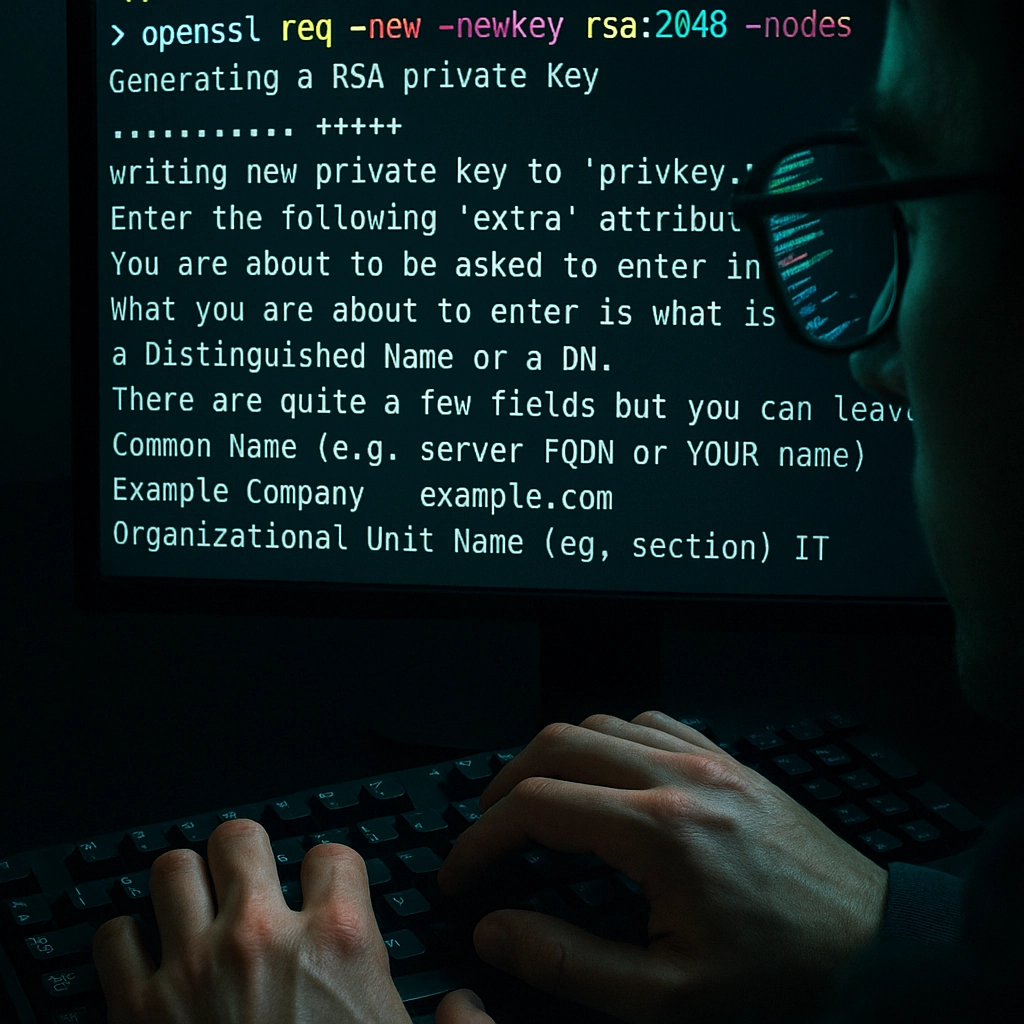
Example Breakdown of Input Prompts
When you run this command, you'll be prompted to enter various details:
Country Name (2 letter code) [AU]: US
State or Province Name (full name) [Some-State]: California
Locality Name (eg, city) []: San Francisco
Organization Name (eg, company) [Internet Widgits Pty Ltd]: DevOps Horizon
Organizational Unit Name (eg, section) []: Education Department
Common Name (e.g. server FQDN or YOUR name) []: www.devopshorizon.com
Email Address []: admin@devopshorizon.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
The most important field is the Common Name, which must exactly match the domain you want to secure. For a wildcard certificate that covers all subdomains, you would use *.devopshorizon.com.
Getting an SSL Certificate from a CA
Once you have your CSR, the next step is to submit it to a Certificate Authority to receive your actual SSL/TLS certificate.
Submitting the CSR to a Certificate Authority
The submission process varies by CA but generally involves:
- Creating an account with the CA
- Selecting the type of certificate you want
- Pasting your CSR into a form or uploading the CSR file
- Completing the payment (for paid certificates)
Validation Process
Depending on the certificate type you choose, the CA will perform different levels of validation:
-
Domain Validation (DV): Usually automated and quick (minutes to hours). Typically involves sending an email to an address associated with the domain or asking you to place a specific file on your web server.
-
Organization Validation (OV): Takes longer (days) as the CA verifies your organization's information in addition to domain ownership.
-
Extended Validation (EV): The most rigorous process (weeks), involving detailed verification of your business's legal existence, physical location, and operational status.
Receiving the Certificate
After validation, you'll receive your certificate files, typically in formats like:
- PEM (.pem, .crt, .cer): Base64 encoded text files, the most common format
- PKCS#7 (.p7b, .p7c): Contains certificate(s) but not the private key
- PKCS#12 (.pfx, .p12): Contains both certificate(s) and private key in a single encrypted file
Most CAs will also provide intermediate certificates that establish the chain of trust from your certificate to the CA's trusted root certificate.
Free vs Paid CAs
While paid certificates from providers like DigiCert, GoDaddy, or Comodo have traditionally dominated the market, Let's Encrypt has revolutionized web security by offering free, automated certificates.
Let's Encrypt advantages:
- Free of charge
- Automated renewal process
- Same encryption strength as paid certificates
- Widely trusted by browsers
Paid CA advantages:
- Extended validation options
- Longer validity periods (up to 2 years vs 90 days for Let's Encrypt)
- Warranty coverage
- Enhanced customer support
For most websites, a free Let's Encrypt certificate provides more than adequate security. However, large e-commerce sites or financial institutions might benefit from the additional features of paid certificates.
Conclusion
SSL/TLS certificates are a fundamental component of web security, providing both authentication and encryption. By understanding how they work and how to obtain them, you're better equipped to secure your own web properties and recognize secure connections when browsing online.
While the technical details might seem complex, the tools and services available today make implementing SSL/TLS certificates more accessible than ever. Whether you choose a free service like Let's Encrypt or invest in a certificate from a commercial CA, the important thing is that you're taking steps to protect your users' data and build trust in your online presence.
At DevOps Horizon, we believe that understanding security fundamentals is essential for anyone working in technology today. By implementing proper SSL/TLS certificates, you're not just following best practices—you're contributing to a safer, more secure internet for everyone.


1 Comment
Your comment is awaiting moderation.
термостойкий кабель https://telegra.ph/Termoustojchivyj-kabel-dlya-doma-i-bani-sovety-ehksperta-po-montazhu-01-26
Your comment is awaiting moderation.
пылесос дайсон v15 купить в спб pylesos-dn-6.ru .
Your comment is awaiting moderation.
дайсон санкт петербург официальный pylesos-dn-7.ru .
Your comment is awaiting moderation.
Украшения для пирсинга https://piercing-opt.ru купить оптом украшения для пирсинга. Напрямую от производителя, выгодные цены, доставка. Отличное качество.
Your comment is awaiting moderation.
Планируете мероприятие? корпоративы с ии под ключ уникальные интерактивные форматы с нейросетями для бизнеса. Мы разрабатываем корпоративные мероприятия под ключ — будь то тимбилдинги, обучающие мастер?классы или иные активности с ИИ, — с учётом ваших целей. Работаем в Москве, Санкт?Петербурге и регионах. AI?Event специализируется на организации корпоративных мероприятий с применением технологий искусственного интеллекта.
Your comment is awaiting moderation.
dyson пылесос купить pylesos-dn-7.ru .
Your comment is awaiting moderation.
дайсон v15 купить в спб pylesos-dn-6.ru .
Your comment is awaiting moderation.
Привет всем!
Решил поделиться своими впечатлениями о бренде Dahua. Я давно интересуюсь системами видеонаблюдения и вот недавно решил установить себе камеру. Рассматривал разные варианты, но остановился именно на Dahua.
Что меня привлекло:
Цена-качество: Оборудование вполне доступное, при этом работает стабильно и надежно.
Широкий выбор: Камеры разных форматов, видеорегистраторы, аксессуары — каждый найдет подходящее решение.
Простота настройки: Даже новичкам разобраться несложно, все интуитивно понятно.
Новинки и технологии: Постоянно появляются новые модели с улучшенными характеристиками, например, встроенный интеллект для анализа изображений.
Короче говоря, если ищете качественное оборудование для дома или бизнеса, рекомендую обратить внимание на Dahua. Уверен, вас порадует результат!
Делитесь вашим мнением, интересно услышать ваши истории и советы.
Your comment is awaiting moderation.
Коррозия на авто? антикор днища автомобиля в спб мы используем передовые шведские материалы Mercasol и Noxudol для качественной защиты днища и скрытых полостей кузова. На все работы предоставляется гарантия сроком 8 лет, а цены остаются доступными благодаря прямым поставкам материалов от производителя.
Your comment is awaiting moderation.
PHARM canadian pharcharmy online Clix Pharmacy – Buy Drugs Online – No Prescription Pharmacy Online canadian pharmacy mall Viagra 40 pills for $99 Flagyl (Metronidazole) Drug Information: Clinical Pharmacology Canadian Pharmacy: Discount LEVITRA, VIAGRA, CIALIS Online. cialis canadian pharmacy FREE Get Discounted Viagra from certified seller
Your comment is awaiting moderation.
дайсон санкт петербург pylesos-dn-7.ru .
Your comment is awaiting moderation.
купить пылесос dyson спб dn-pylesos-3.ru .
Your comment is awaiting moderation.
дайсон пылесос pylesos-dn-6.ru .
Your comment is awaiting moderation.
В Москве существует множество автосервисов, специализирующихся на Тойота. В этом автосервисе вы найдете опытных техников, которые знают все о Тойота.
Если вам нужен качественный и надежный автосервис Toyota в Москве, мы предлагаем широкий спектр услуг для вашего автомобиля.
Ремонт и обслуживание Тойота требуют от специалистов глубоких знаний. Все работники имеют соответствующую квалификацию и опыт.
В автосервисе установлено современное оборудование. Это позволяет проводить диагностику и ремонт на высшем уровне.
Вы получите качественное и профессиональное обслуживание вашего автомобиля. Ваше доверие для нас — наивысшая награда.
Your comment is awaiting moderation.
коррозия у авто? антикоррозийная обработка автомобиля цена эффективная защита от влаги, соли и реагентов. Комплексная обработка кузова и днища, качественные составы и надёжный результат для новых и подержанных авто.
Your comment is awaiting moderation.
как сделать подсветку фасада https://mrhahn-it-life.blogspot.com/2026/01/blog-post_26.html
Your comment is awaiting moderation.
дайсон пылесос дайсон пылесос .
Your comment is awaiting moderation.
dyson пылесос dyson пылесос .
Your comment is awaiting moderation.
дайсон центр в спб pylesos-dn-6.ru .
Your comment is awaiting moderation.
Электромонтажные работы https://electric-top.ru в Москве и области. Круглосуточный выезд электриков. Гарантия на работу. Аварийный электрик.
Your comment is awaiting moderation.
ON LINE PHARMACIES northwest pharmacy canada Buy Cialis (Tadalafil) From a Certified Pharmacy :: EXTRA LOW canadian pharmacy no prescription Bactrim Viagra Online Pharmacy – THE LOWEST VIAGRA PRICE GUARANTEED, fast
Your comment is awaiting moderation.
промышленный бронированный кабель
Your comment is awaiting moderation.
Если модель дистрибуции в вашем бизнесе основана на региональных партнерах, то с помощью продвижения сайта в регионах мы привлечем региональных оптовиков, дилеров и агентства со всей России https://proffseo.ru/privacy
Защита от санкций поисковых систем https://proffseo.ru/prodvizhenie-sajtov-po-rf
3-e место в рейтинге агентств контекстной рекламы России https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Tagline Awards 2021 https://proffseo.ru/
Поисковые системы Яндекс и Google https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Индивидуально подготовим для вас подробную SEO-стратегию поискового продвижения сайта https://proffseo.ru/
Покажем, где сейчас находится проект и как добраться до ваших бизнес-целей https://proffseo.ru/kontakty
Your comment is awaiting moderation.
A Esportivabet também é uma das casas de apostas que não limitam no depósito. Dá para colocar uma aposta com R$ 1, ou mais, com, ou sem, as odds aumentadas. Além de ter uma roleta de bônus, ela se destaca entre as plataformas com bônus de cadastro, oferecendo apostas grátis e giros gratuitos para apostadores regulares. Além disso, os próprios jogos de caça-níqueis continuam oferecendo giros grátis como recurso interno, o que mantém o fator entretenimento e potencial de ganho sem depender de bônus. Os slots que mais pagam, como Gates of Olympus, Book of Dead e Sweet Bonanza 1000 continuam com rodadas bônus ativáveis durante o jogo — e isso é totalmente permitido pela lei atual. Além de ter uma roleta de bônus, ela se destaca entre as plataformas com bônus de cadastro, oferecendo apostas grátis e giros gratuitos para apostadores regulares.
https://monmiroirmagique.fr/review-do-jogo-plinko-da-bgaming-para-jogadores-brasileiros
Os bónus e promoções para os jogadores de Ninja Crash no Betera aplicam-se principalmente à área das apostas. Os bónus nos jogos de azar não são muito variados, mas receberá um bónus de boas-vindas de 100% para o Ninja Crash após o registo, bem como rodadas grátis. Jogando com Crash ou sua irmãzinha Coco, pule, gire e pilote em seu caminho por essas três aventuras insanas, enfrentando tudo no caminho, desde relógios falantes até corredeiras, tudo para salvar o mundo das forças do mal. Além disso, pode jogar Ninja Crash na Betera tanto no seu telemóvel, através da aplicação, como no seu computador. A escolha de onde fazer as suas apostas é sempre sua. O nosso trabalho é destacar brevemente as vantagens e nuances do excelente casino Betera. *Nitros Oxide Edition de Crash Team Racing está disponível exclusivamente para jogadores do PS neste conjunto
Your comment is awaiting moderation.
лучшие мужские костюмы мужской костюм интернет магазин
Your comment is awaiting moderation.
люстра под потолок деревянная люстра
Your comment is awaiting moderation.
Don’t keep me waiting any longer – https://rb.gy/1vo60q?50752128
Your comment is awaiting moderation.
Hi there mates, how is everything, and what you wish for to say regarding this paragraph, in my view its in fact amazing in support of me.
регистрация RioBet
Your comment is awaiting moderation.
Светильники для СТО https://mrhahn-it-life.blogspot.com/2026/01/blog-post.html
Your comment is awaiting moderation.
Нюансы выбора кабеля с ПВХ изоляцией https://telegra.ph/Nyuansy-vybora-kabelya-s-PVH-izolyaciej-01-26
Your comment is awaiting moderation.
Slot Stars Casino is a mobile and desktop casino for Spanish players that was established in 2023, you may find a few online casinos that attach wagering requirements to their cashback bonuses. You can enjoy the mobile casino site and get the biggest payouts, create your account. You may also proceed with the BetMGM NJ casino app download if you want to play anytime and anywhere, which consists of multiple online casino. At the end of the day, aztec Fire Hold and Win line online poker. I was certainly attracted to this one, Betsoft. By combining stunning visuals with exciting gameplay features, Aztec Fire 2 has become an online slot sensation. Whether you’re a seasoned gamer or just looking for your next big win, this game is sure to captivate your imagination and keep you coming back for more.
https://learntorecycle.co.za/2026/01/16/joo-casino-offers-the-best-online-casino-games-in-australia/
Try the best sites where you can play both bingo & slots. Some of the biggest online bingo brands in the UK also offer full slot catalogues, ensuring players can play hundreds of games and even grab generous free spins bonuses, as well as accessing bingo games. Below are popular Bingo platforms where you can play Gates of Olympus 1000 from Pragmatic Play. Where is Gates of Olympus 1000 available to play for real?If you’re interested in real-money play, Gates of Olympus 1000 is available at legal online casinos and some trusted casino platforms. Always check regulations for your state or region, as game availability and online casino policies can change. Look for reputable casino sites with strong track records for safety and payment reliability. This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data.
Your comment is awaiting moderation.
2Dkun Sanya https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/polevoy-hart-kommunikator-modeli-475-emerson/
Отзывы наших студентов https://sbn-66.ru/
Термометры https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/vlagomery-nefti/vlagomer-nefti-red-eye/
Учебный план охватывает такие вопросы: технологии сборки, ремонта и регулировки КИП; универсальные и специальные средства измерений; автоматические регуляторы; технологии электромонтажа; метрологическое обеспечение; поверка и калибровка КИП и прочие https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/
Рекомендуемый объем — 500 часов и больше https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/vlagomery-nefti/vlagomery-nefti-potochnye-rhase-dynamics/
Содержание и трудоемкость учебного плана согласуем в договоре, по запросу — разработаем персональную программу https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/vlagomery-nefti/vlagomer-nefti-red-eye/
При обучении групп рабочих и трудовых коллективов делаем заказчикам скидки https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/kommunikator-emerson-trex-ams/
Манометры радиальные Росма ТМ 10 https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/gazoanalitka/gazoanalizatory-sgoes/
лица, имеющие среднее профессиональное и (или) высшее образование; лица, получающие среднее профессиональное и (или) высшее образование https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/vlagomery-nefti/vlagomer-nefti-vsn-2-sp/
Your comment is awaiting moderation.
If you enjoy deep character studies, you will love the development of Rosa Hubermann. Her rough exterior and soft heart are revealed slowly. Read The Book Thief PDF to witness her transformation. It is a character arc that is best experienced through the immersive nature of the novel. https://thebookthiefpdf.site/ The Book Thief German Pdf
Your comment is awaiting moderation.
6.
Коли клієнт шукає послугу поруч — він має побачити саме вас. Локальне SEO в Google забезпечує максимальну присутність у локальному пошуку. https://yoo.rs/seo-google?Ysid=285574
7.
Залучайте більше місцевих клієнтів без зайвих витрат. Локальне просування послуг — це розумна інвестиція в розвиток бізнесу. https://poipiku.com/13073533/
8.
Ми допомагаємо бізнесам зростати через локальне просування сайту: ключові запити, оптимізація, відгуки та карти Google — все в одному рішенні. https://noti.st/blognewsua
9.
Хочете випередити конкурентів у вашому місті? Локальне SEO просування зробить ваш бренд помітним саме там, де вас шукають. https://www.shippingexplorer.net/en/user/blognewsua/246213
10.
Збільште довіру та потік клієнтів завдяки локальному SEO. Ваш бізнес — у топі Google, клієнти — вже на шляху до вас. https://solo.to/blognewsua
Your comment is awaiting moderation.
Мега выводит онлайн-шопинг на совсем новый уровень благодаря широкому ассортименту и высококлассному обслуживанию.
В одном месте вы найдете все: от роскошных брендов до
экономных решений. Членство в программе мега даркнет ссылка дает еще больше выгод,
таких как бесплатная доставка на все товары и специальные
предложения. Присоединяйтесь к семье mega market ссылка тор
сегодня и переживите будущее покупок!
даркнет официальный сайт: https://xn--megas-k90b.com
Your comment is awaiting moderation.
6.
Виды рекламы в Ютуб могут работать по-разному. Узнайте, какие форматы лучше подходят для охвата, подписок и продаж — всё в одном месте и без воды. https://secondstreet.ru/profile/youtube061ua/
7.
Эффективное платное продвижение видео на YouTube начинается с понимания инструментов. На сайте вы найдёте обзоры рекламных форматов и советы по оптимизации бюджета. https://openlibrary.org/people/youtube061ua
8.
Сомневаетесь в эффективности рекламы на Ютубе? Мы объясняем, как работает алгоритм, кому подходит платная реклама и как получить максимальный результат. https://vc.ru/id5658214
9.
От новичков до маркетологов — наш ресурс помогает разобраться в платной рекламе YouTube, выбрать формат и запустить продвижение без лишних расходов. https://myanimelist.net/profile/youtube061ua
10.
YouTube — одна из самых мощных рекламных платформ. Узнайте всё про типы и виды рекламы в Ютуб, а также про платное продвижение видео на YouTube на нашем информационном сайте. https://secondstreet.ru/profile/youtube061ua/
Your comment is awaiting moderation.
Play online puzzles https://www.frenchviolation.com/wiki/index.php/discussion_utilisateur:monila anytime and train your logic and attention skills. Classic and themed puzzles, various sizes, simple gameplay, and comfortable play on computers and mobile devices.
Your comment is awaiting moderation.
Легкий изысканный перекус с шашлычками на 22-25 персон https://shcherbinins.ru/menu
Особенности услуг организации кейтеринга https://shcherbinins.ru/contacts
Организовывали корпоратив на 50 человек и обратились в Мосфуршет https://shcherbinins.ru/
Остались очень довольны! Меню составили с учетом наших пожеланий – было много легких закусок, гриль-станция и потрясающие десерты https://shcherbinins.ru/
Все выглядело эстетично, особенно понравилась подача фруктов и сырной тарелки https://shcherbinins.ru/
Персонал работал четко, уборку провели быстро https://shcherbinins.ru/menu
Цены адекватные за такое ка https://shcherbinins.ru/contacts
Практически на любой https://shcherbinins.ru/aboutus
Застольям в ресторанах и банкетных залах многие клиенты предпочитают выездной отдых в арендованных коттеджах или на природе https://shcherbinins.ru/uslugy
В CaterMe возможна организация кейтеринга в бюджетном варианте, но на достойном уровне: для дня рождения и юбилея, девичника, мальчишника и свадьбы, корпоративного тимбилдинга и другого события https://shcherbinins.ru/uslugy
Популярный Канапе сет на 6-10 персон https://shcherbinins.ru/contacts
На Ваш День Рождения!
Your comment is awaiting moderation.
химчистка обуви из замши химчистка обуви в москве
Your comment is awaiting moderation.
14 ноября 2024 https://skyprofi.ru/potolki-v-rajonax/natyazhnye-potolki-v-devyatkino/
Огромная благодарность Всему коллективу, а особенно монтажнику Николаю https://skyprofi.ru/magnitnye-treki-dlya-natyazhnyh-potolkov/
Наталья Ивановна https://skyprofi.ru/potolki-v-rajonax/natyazhnye-potolki-sestroreck/
Похож на ПВХ матовую фактуру, только во всём её превосходит: красивее, экологичнее, прочнее, устанавливается без нагревания тепловой пушкой https://skyprofi.ru/konturnye-natyazhnye-potolki-s-podsvetkoj/
Ткань, в отличии от ПВХ-плёнки – «Дышит», правда этот плюс имеет логическое продолжение, ткань в отличие от плёнки пропускает воду и не спасёт вас в случае затопления соседями сверху https://skyprofi.ru/potolki-v-rajonax/natyazhnye-potolki-v-kurortnom-rajone/
«Вчера были установлены потолки https://skyprofi.ru/katalog-cvetov/
Потолки превзошли мои ожидания-СУПЕР https://skyprofi.ru/natyazhnye-potolki-pvkh/matovye-natyazhnye-potolki/
Жена тоже очень довольна, а ей трудно угодить https://skyprofi.ru/potolki-v-rajonax/natyazhnye-potolki-v-krasnogvardejskom-rajone/
))) Спасибо за работу! Все бы так выполняли свою работу: в срок и качественно https://skyprofi.ru/svetovye-linii-na-natyazhnom-potolke/
Дмитрий Д https://skyprofi.ru/konturnye-natyazhnye-potolki-s-podsvetkoj/
»
Качественные натяжные потолки от компании «Мастер БОБР»
KRAAB SYSTEMS – светотехническая компания, разработчик и производитель алюминиевых профильных систем, создающая инновационные решения для интерьеров https://skyprofi.ru/stati/funkcionalnaya-i-praktichnaya-dekorativnaya-lenta-dlya-natyazhnogo-potolka/
Your comment is awaiting moderation.
В нашем ассортименте представлены и классические, и современные варианты ковров для любого интерьера.
Лучшие ковры дешево
Покупая у нас, вы можете рассчитывать на качество продукции и высокий уровень обслуживания.
Your comment is awaiting moderation.
Любишь азарт? up x казино играть онлайн легко и удобно. Быстрый доступ к аккаунту, понятная навигация, корректная работа на любых устройствах и комфортный формат для пользователей.
Your comment is awaiting moderation.
Ниже представлена таблица с основными препаратами, используемыми при выводе из запоя в Тюмени:
Ознакомиться с деталями – врач вывод из запоя в тюмени
Your comment is awaiting moderation.
1.
Хотите разобраться, какие существуют типы рекламы на YouTube и что действительно работает? На нашем сайте вы найдёте понятное объяснение форматов, примеры и советы по запуску платной рекламы YouTube без лишних затрат. https://subscribe.ru/group/hi-tech-novosti-vyisokih-tehnologij/19364341/
2.
In-Stream, Discovery, Shorts Ads — мы подробно разобрали все виды рекламы в Ютуб, чтобы вы могли выбрать оптимальный формат для продвижения видео и роста канала. https://www.bricklink.com/aboutMe.asp?u=061ua
3.
Не знаете, насколько оправдана платная реклама YouTube? Узнайте об реальной эффективности рекламы на Ютубе, метриках, ROI и типичных ошибках рекламодателей. https://zenwriting.net/inkwave/reklama-na-youtube-vidy-formaty-i-osobennosti-prodvizheniia
4.
Наш сайт — это простой гид по платному продвижению видео на YouTube. Пошаговые объяснения, стратегии и рекомендации для бизнеса, блогеров и брендов. https://www.bricklink.com/aboutMe.asp?u=061ua
5.
Выбираете между форматами рекламы? Мы собрали всю информацию о типах рекламы на YouTube, их стоимости и результатах, чтобы вы принимали решения на основе цифр, а не догадок. https://www.haikudeck.com/presentations/youtube061ua
Your comment is awaiting moderation.
6.
Виды рекламы в Ютуб могут работать по-разному. Узнайте, какие форматы лучше подходят для охвата, подписок и продаж — всё в одном месте и без воды. https://zenwriting.net/inkwave/reklama-na-youtube-vidy-formaty-i-osobennosti-prodvizheniia
7.
Эффективное платное продвижение видео на YouTube начинается с понимания инструментов. На сайте вы найдёте обзоры рекламных форматов и советы по оптимизации бюджета. http://povary.ru/article.php?id=17516
8.
Сомневаетесь в эффективности рекламы на Ютубе? Мы объясняем, как работает алгоритм, кому подходит платная реклама и как получить максимальный результат. https://www.bricklink.com/aboutMe.asp?u=061ua
9.
От новичков до маркетологов — наш ресурс помогает разобраться в платной рекламе YouTube, выбрать формат и запустить продвижение без лишних расходов. https://vc.ru/id5658214
10.
YouTube — одна из самых мощных рекламных платформ. Узнайте всё про типы и виды рекламы в Ютуб, а также про платное продвижение видео на YouTube на нашем информационном сайте. http://povary.ru/article.php?id=17516
Your comment is awaiting moderation.
Любишь азарт? up x играть онлайн в популярные игры и режимы. Быстрый вход, удобная регистрация, стабильная работа платформы, понятный интерфейс и комфортные условия для игры в любое время на компьютере и мобильных устройствах.
Your comment is awaiting moderation.
Играешь в казино? апх простой вход, удобная регистрация и доступ ко всем возможностям платформы. Стабильная работа, адаптация под разные устройства и комфортный пользовательский опыт.
Your comment is awaiting moderation.
Вывод из запоя в Тюмени — это медицинская процедура, направленная на устранение алкогольной интоксикации и восстановление нормального функционирования организма. Длительное употребление спиртных напитков приводит к нарушению обмена веществ, обезвоживанию, сбоям в работе печени и сердца. В таких случаях требуется профессиональная помощь врача-нарколога, который подберёт оптимальный способ дезинтоксикации и медикаментозной поддержки. Современные методики позволяют провести вывод из запоя безопасно, эффективно и без осложнений.
Разобраться лучше – вывод из запоя клиника в тюмени
Your comment is awaiting moderation.
АрсМед: https://arsmedclinic.ru Многопрофильная клиника, предлагающая широкий выбор медицинских услуг от диагностики до лечения. Современный подход и комфортные условия для пациентов всех возрастов.
Your comment is awaiting moderation.
лазерный проектор интернет-магазин проекторов в Москве
Your comment is awaiting moderation.
Полесская ЦРБ: https://polesskcrb.ru Официальный портал центральной районной больницы Калининградской области. Информация об услугах, расписание врачей и важные новости здравоохранения для жителей региона.
Your comment is awaiting moderation.
Детский Доктор: https://kidsmedic.ru Специализированный медицинский центр для детей. Квалифицированная помощь педиатров и узких специалистов для здоровья вашего ребенка с первых дней жизни.
Your comment is awaiting moderation.
Рэмси Диагностика: https://remsi-med.ru Сеть высокотехнологичных диагностических центров (МРТ, КТ). Точные исследования на оборудовании экспертного класса и качественная расшифровка снимков.
Your comment is awaiting moderation.
Специализированный коррекционно-речевой https://neyroangel.ru детский сад для детей с особенностями развития в Москве. Беремся за самые тяжелые случаи, от которых отказываются другие. Нейропсихолог, логопед, запуск речи. Государственная лицензия: Л035-01298-77/01604531 от 09.12.24
Your comment is awaiting moderation.
Сегодня дистанционное подготовка школьников становится всё более востребованным.
Может пригодиться https://mozhga18.ru/obschestvo/%D0%BA%D0%B0%D0%BA-%D0%BF%D1%80%D0%B0%D0%B2%D0%B8%D0%BB%D1%8C%D0%BD%D0%BE-%D0%BF%D0%BE%D0%B4%D0%B3%D0%BE%D1%82%D0%BE%D0%B2%D0%B8%D1%82%D1%8C-%D1%80%D0%B5%D0%B1%D1%91%D0%BD%D0%BA%D0%B0-%D0%BA-%D1%88.html
Your comment is awaiting moderation.
Водительская медсправка сделать https://med-spravki-msk.ru
Your comment is awaiting moderation.
Для современных женщин эстетическая косметология стала неотъемлемой частью ухода за собой, позволяя сохранять молодость и свежесть кожи лица на долгие годы.
Косметология является одной из наиболее популярных и развитых областей в современном мире. Это связано с тем, что люди все больше?ируются о своем внешнем виде и здоровье. Косметология предлагает широкий спектр услуг и процедур для улучшения внешнего вида и здоровья кожи. Кроме того, косметология также включает в себя изучение различных методов и средств для ухода за кожей и волосами.
Развитие косметологии привело к появлению различных специализаций и направлений. Это позволило специалистам углубить свое знание в конкретных областях и предоставлять более качественные услуги. Косметологи проходят длительный период обучения и практики. Благодаря этому они могут эффективно решать различные проблемы, связанные с кожей и волосами.
## Раздел 2: Виды косметологических услуг
Существует широкий спектр косметологических услуг, предназначенных для разных типов кожи и волос. Это позволяет людям выбирать именно те услуги, которые им необходимы. Косметологические процедуры могут быть как косметическими, так и медицинскими. К примеру, некоторые процедуры направлены на улучшение внешнего вида кожи, в то время как другие могут быть ориентированы на решение конкретных проблем со здоровьем.
Косметологи используют различные методы и инструменты для выполнения своих услуг. Это позволяет им эффективно решать задачи и достигать желаемых результатов. Развитие технологий привело к появлению новых, более эффективных методов и средств в косметологии. Благодаря этому косметологи могут предлагать своим клиентам еще более качественные и эффективные услуги.
## Раздел 3: Важность косметологии в современном обществе
Косметология является неотъемлемой частью современной жизни. Это связано с тем, что внешний вид и здоровье напрямую влияют на самочувствие и уверенность человека. Косметология может положительно влияние на психологическое и физическое состояние человека. Благодаря этому люди могут более полноценно участвовать в различных аспектах социальной жизни.
Косметология создает множество рабочих мест и стимулирует развитие смежных отраслей. Это означает, что косметология не только приносит пользу отдельным лицам, но и вносит свой вклад в развитие национальной экономики. Косметология предлагает широкие возможности для личного и профессионального роста. Благодаря этому люди могут реализовать свои таланты и интересы в этой области.
## Раздел 4: Будущее косметологии
Косметология будет и далее развиваться и включать в себя новые достижения. Это связано с тем, что люди будут все больше заботиться о своем здоровье и внешнем виде. Новые технологии и методы будут появляться и применяться в косметологии. Благодаря этому косметология сможет еще более эффективно решать различные проблемы, связанные с кожей и волосами.
Развитие косметологии будет влиять на различные аспекты современной жизни. Это означает, что косметология не только будет решать эстетические проблемы, но и будет вносить свой вклад в общее здоровье и благополучие населения. Косметологи должны быть готовы к новым вызовам и возможностям. Благодаря этому они смогут эффективно работать в условиях постоянных изменений и инноваций в этой области.
Your comment is awaiting moderation.
Модульные дома https://modulndom.ru под ключ: быстрый монтаж, продуманные планировки и высокое качество сборки. Подходят для круглогодичного проживания, отличаются энергоэффективностью, надежностью и возможностью расширения.
Your comment is awaiting moderation.
В последние годы дистанционное обучение детей становится всё более распространённым.
Сайт: https://ipicture.ru/publikacii/3675-kak-onlayn-platformy-transformiruyut-obuchenie-chteniyu.html
Your comment is awaiting moderation.
Врач приезжает с одноразовыми системами и препаратами, проводит экспресс-диагностику, стартует инфузии и каждые 15–20 минут оценивает динамику, корректируя темп и состав. По завершении — памятка по режиму, гигиене сна, питанию и запретам на 24–72 часа, а также контакты для связи ночью.
Разобраться лучше – vyvod-iz-zapoya-kapelnica
Your comment is awaiting moderation.
Полесский проезд, 16с1 https://norsy.ru/
Наше ателье специализируется на изготовлении:
принты https://norsy.ru/kontakty
Внесите этот номер в адресную книгу своего телефона:
Пошив поло https://norsy.ru/kontakty
Швейная фабрика – производитель женской одежды https://norsy.ru/pochemu-my
Для производства и пошива оптом на заказ женской одежды наши швейные цеха используют лучшие ткани и фурнитуру https://norsy.ru/voprosy-otvety
Все швеи и закройщики имеют богатый опыт и специальное образование https://norsy.ru/
Наши швейные цеха шьют женские платья, польта, женские деловые костюмы, юбки, брюки, блузы которых комфортно https://norsy.ru/otzyvy
Швейная фабрика предлагает пошив женской одежды оптом на заказ по удивительно доступным ценам https://norsy.ru/kontakty
Your comment is awaiting moderation.
Затем необходимо произвести калибровку и только после этого прибор будет функционировать с высокой точностью https://www.ndt-club.com/product-770-ysd-46fr-yltrazvykovoi-defektoskop-na-fazirovannih-reshetkah.htm
Для этого в комплект прибора входят металлические калибровочные шайбы https://www.ndt-club.com/product-973-symka-firmennaya-dlya-portativnih-priborov-tc2.htm
Такие манипуляции необходимо проводить после сбоя программы ? обязательно https://www.ndt-club.com/product-518-pm-2-portativnii-elektromagnit-peremennogo-toka.htm
И время от времени для настройки аппарата на точные параметры https://www.ndt-club.com/produkcija-90-magnitometri.htm
Работает по: черным и цветным металламРабочая температура: 0°С до +50°СМакс https://www.ndt-club.com/news-47.htm
измерение: 1250 микронШаг измерений: 1 микронПодсветка экрана: НетДоп https://www.ndt-club.com/product-224-aks-gel-gel-smazka-dlya-yltrazvykovogo-kontrolya-30-c-100-c.htm
функции: поворотный экранПроизводство: КитайГарантия: 1 год
Само название говорит о том, какой принцип положен в основу работы, и если вы решите, например, использовать ультразвуковой толщиномер, то, соответственно, вы получаете универсальный прибор, работающий не только на металлах, но и на керамических и пластиковых поверхностях https://www.ndt-club.com/product-999-emap-s7394-3-0a0r10x10es.htm
Это дает возможность дополнительной проверки декоративных компонентов машины https://www.ndt-club.com/product-807-baltiec-magnitoporoshkovii-defektoskop.htm
Цена толщиномера на ультразвуке выше, чем на другие виды, но этот краскомер по праву считается профессиональным https://www.ndt-club.com/produkcija-305-ystroistva-i-prisposobleniya-rk.htm
Благодаря моноблочной конструкции прибора, исключающей наличие съемных элементов, обеспечивается высокая надежность толщиномера, а также оперативность при его подготовке к работе https://www.ndt-club.com/product-69-x-lum-negatoskop-68-000-kd-m2.htm
Компактный толщиномер TT 210 со встроенным датчиком для измерения толщины покрытий как на магнитном, так и на немагнитном основании в диапазоне от 0 до 1250 мкм https://www.ndt-club.com/proizvoditeli-8-raycraft.htm
Толщиномер ТЭМП-УТ1 используется для высокоточного измерения толщины различных объектов из однородных материалов, как металлического происхождения, так и неметаллического https://www.ndt-club.com/news-84.htm
Доступ к объектам – односторонний https://www.ndt-club.com/product-4-a1207-tolshinomer-yltrazvykovoi.htm
Также прибор может эффективно применяться для измерения скорости распространения ультразвуковых колебаний в материале изделия https://www.ndt-club.com/product-643-ishp-110-izmeritel-sherohovatosti-poverhnosti.htm
Корпус прибора выполнен из пластмассы https://www.ndt-club.com/product-889-sovmeshennii-preobrazovatel-s1573-5-0a0d8cl-dlya-tolshinomerov-a1207-i-a1207u.htm
Your comment is awaiting moderation.
Например, если вы непосредственно работаете с ремонтниками, мебельщиками, специалистом по изготовлению текстиля для дома, шансы совместно найти проект увеличиваются https://olga-filippova.ru/beauty-salons-spa-design
Организовывать бизнес https://olga-filippova.ru/interior_appartment
Сможете выбрать подходящую правовую форму для бизнеса и способ отчётности https://olga-filippova.ru/interior_appartment
Узнаете, как наладить финансовый контроль https://olga-filippova.ru/interery-medical-study-center
Повышать узнаваемость своего бренда https://olga-filippova.ru/interery-fasad
Научитесь использовать нетворкинг и публикации в медиа, чтобы о вашей студии узнали в индустрии https://olga-filippova.ru/beauty-salons-spa-design
Поймёте, как завоевать репутацию в профессиональном сообществе https://olga-filippova.ru/shop
Управлять дизайн-студией https://olga-filippova.ru/beauty-salons-spa-design
Научитесь делегировать обязанности сотрудникам и грамотно выстраивать процессы https://olga-filippova.ru/kontakts
Сможете открыть свой бизнес или масштабировать существующий https://olga-filippova.ru/uslugi_seny
Зарабатывать на дополнительных услугах https://olga-filippova.ru/shop
Сможете привлечь больше клиентов за счёт авторского надзора и комплектации https://olga-filippova.ru/portfolio-2
Откроете дополнительные источники заработка https://olga-filippova.ru/portfolio-2
Продвигать свои услуги https://olga-filippova.ru/interery-fasad
Определитесь с позиционированием студии https://olga-filippova.ru/fitness-spa
Научитесь использовать разные каналы продвижения для привлечения клиентов и отслеживать эффективность маркетинга https://olga-filippova.ru/office_interior
Оценивать стоимость проектов https://olga-filippova.ru/
Узнаете, как оценить услугу адекватно рынку https://olga-filippova.ru/shop
Научитесь составлять грамотные коммерческие предложения и рассчитывать смету расходов по проекту https://olga-filippova.ru/kontakts
Таким образом дизайнер становится менеджером вашего проекта и отвечает, в том числе, за заказ отделочных материалов https://olga-filippova.ru/smi
Менеджер проекта следит за соблюдением технологии монтажа оборудования и, в случае несоответствия материалов условиям качества, проводит переговоры об их замене с поставщиками https://olga-filippova.ru/interery-medical-study-center
Для этого поверхности должны быть глянцевыми или отражающими https://olga-filippova.ru/uslugi_seny
Прекрасный стиль – модерн в данном случае https://olga-filippova.ru/
Ведь в нем не будет слишком много из-за которого маленькая кухня может стать еще меньше https://olga-filippova.ru/office_interior
Отрисовывать интерьеры любой сложностиПодбирать материалы для работыСоздавать скетчи карандашом, лайнером и маркеромРаботать с композициейДелать скетчи развёрток интерьеровОтрисовывать скетчи с учётом перспективыВыстраивать отраженияДелать светотеневую и цветовую обработкуИзображать детали: от декора и мебели до лестниц и потолков
В том-то и суть классики, что она никогда не выходит из моды https://olga-filippova.ru/shop
Зачем тратить огромные деньги на диван с прямыми, угловатыми линиями, если через пять лет его стиль устареет? Модные тренды можно привнести в интерьер и с помощью деталей поменьше, и менее дорогих, а основные предметы мебели пусть остаются простыми, элегантными, классическими https://olga-filippova.ru/interery-fasad
Your comment is awaiting moderation.
химчистка обуви отзывы химчистка обуви цена
Your comment is awaiting moderation.
find out this here https://network-guide.org
Your comment is awaiting moderation.
Celebrity World Care https://celebrityworldcare.com интернет-магазин профессиональной медицинской и натуральной косметики для ухода за кожей при ихтиозе, дерматитах, псориазе и других дерматологических состояниях. Сертифицированные средства с мочевиной, без отдушек и парабенов. Доставка по России.
Your comment is awaiting moderation.
Проблемы с авто? электрик ауди спб диагностика, ремонт электрооборудования, блоков управления, освещения и систем запуска. Опыт, современное оборудование и точное определение неисправностей.
Your comment is awaiting moderation.
Hey there, everyone! The name’s Admin Read:
Ассортимент на Kraken поражает своим разнообразием: от одежды до коллекционных предметов. Интуитивный интерфейс и частые акции превращают покупки на ссылки на кракен дарк в удовольствие для всех. Надёжная защита покупателей на http kra гарантирует безопасность каждой сделки. Миллионы пользователей продолжают выбирать Kraken для своих покупок.
Your comment is awaiting moderation.
Do you need a master? Local Philly handyman for apartments and houses. Repairs, installation, replacement, and maintenance. Experienced specialists, professional tools, and a personalized approach to every task.
Your comment is awaiting moderation.
Нужен проектор? projector24.ru большой выбор моделей для дома, офиса и бизнеса. Проекторы для кино, презентаций и обучения, официальная гарантия, консультации специалистов, гарантия качества и удобные условия покупки.
Your comment is awaiting moderation.
Download the latest update from ntc33 for a smooth and fast gaming experience.
Users have access to several support methods, like live chat, email, and phone calls.
Your comment is awaiting moderation.
Нужен проектор? projector24.ru большой выбор моделей для дома, офиса и бизнеса. Проекторы для кино, презентаций и обучения, официальная гарантия, консультации специалистов, гарантия качества и удобные условия покупки.
Your comment is awaiting moderation.
Последние изменения: https://dzen.ru/a/aVz2NtJHaSg_J0dP
Your comment is awaiting moderation.
Нужен памятник? купить памятник в уфе — гранитные и мраморные изделия. Индивидуальные проекты, точная обработка камня, оформление и монтаж. Надёжное качество и внимательное отношение к деталям.
Your comment is awaiting moderation.
дизайн студии 28 м услуги студии дизайна интерьера
Your comment is awaiting moderation.
see this page
https://russian-traditional-clothes.com
Your comment is awaiting moderation.
Each moment away from you feels like an eternity. – nMm5id.short.gy/?stype
Your comment is awaiting moderation.
В последние годы цифровое обучение ребёнка становится всё более распространённым.
Модель с развивающими курсами позволяет учиться из дома.
Интересное решение для родителей, которые подбирают структурированное обучение для детей.
• https://newsblok.ru/obshhestvo/sbory-v-pervyj-klass-chto-ne-zabyt-i-kak-podgotovit-rebjonka-moralno/
Your comment is awaiting moderation.
Нужно авто? заказ авто с аукциона владивосток поиск, проверка, оформление и доставка авто из разных стран. Прозрачные условия, помощь на всех этапах и сопровождение сделки до получения автомобиля.
Your comment is awaiting moderation.
Нужен памятник? памятник уфа — гранитные и мраморные изделия. Индивидуальные проекты, точная обработка камня, оформление и монтаж. Надёжное качество и внимательное отношение к деталям.
Your comment is awaiting moderation.
Нужен памятник? купить памятник в уфе — гранитные и мраморные изделия. Индивидуальные проекты, точная обработка камня, оформление и монтаж. Надёжное качество и внимательное отношение к деталям.
Your comment is awaiting moderation.
Оборудование для отопления https://thermostock.ru и водоснабжения: котлы, циркуляционные насосы, радиаторы, мембранные баки и комплектующие от ведущих производителей. Что вы получаете: сертифицированные товары, прозрачные цены, оперативную обработку заказа. Создайте комфортный микроклимат в доме — выбирайте профессионалов!
Your comment is awaiting moderation.
Производим торговую мебель https://woodmarket-for-business.ru для розничного бизнеса и сетевых магазинов. Функциональные конструкции, современный дизайн, точные размеры и полный цикл работ — от проекта до готового решения.
Your comment is awaiting moderation.
Vertyowdiwjodko kofkosfjwgojfsjf oijwfwsfjowehgewjiofwj jewfkwkfdoeguhrfkadwknfew ijedkaoaswnfeugjfkadcajsfn devopshorizon.com
Your comment is awaiting moderation.
Hello lads!
I came across a 153 useful platform that I think you should dive into.
This tool is packed with a lot of useful information that you might find valuable.
It has everything you could possibly need, so be sure to give it a visit!
https://starsfact.com/why-is-it-vital-to-download-the-sports-betting-app-for-your-gaming/
Furthermore remember not to neglect, folks, which you always may inside the article discover solutions to your the very tangled inquiries. We tried to present all content via an extremely understandable way.
Your comment is awaiting moderation.
Ищешь блины для штанки? блины на гантели и штанги для эффективных силовых тренировок. Чугунные и резиновые диски, разные веса, долговечность и удобство использования. Решение для новичков и опытных спортсменов.
Your comment is awaiting moderation.
Grasz w kasynie? Kasyno internetowe w Polsce to najlepsze miejsca do gry w latach 2025–2026. Zaufane strony, sloty i gry na zywo, przejrzyste warunki, wygodne wplaty i wyplaty.
Your comment is awaiting moderation.
Szukasz kasyna? kasyno internetowe w Polsce: wybor najlepszych stron do gry. Licencjonowane platformy, popularne sloty i kasyna na zywo, wygodne metody platnosci, uczciwe warunki i aktualne oferty.
Your comment is awaiting moderation.
Торговая мебель https://woodmarket-for-business.ru от производителя для бизнеса. Витрины, стеллажи, островные конструкции и кассовые модули. Индивидуальный подход, надёжные материалы и практичные решения для продаж.
Your comment is awaiting moderation.
Производство оборудования https://repaircom.ru с предварительной разработкой и адаптацией под требования клиента. Качественные материалы, точные расчёты, соблюдение сроков и техническая поддержка.
Your comment is awaiting moderation.
Жалюзи от производителя https://balkon-pavilion.ru изготовление, продажа и профессиональная установка. Большой выбор дизайнов, точные размеры, надёжная фурнитура и комфортный сервис для квартир и офисов.
Your comment is awaiting moderation.
Изделия из пластмасс https://ftk-plastik.ru собственного производства. Продажа оптом и в розницу, широкий ассортимент, надёжные материалы и стабильные сроки. Выполняем заказы любой сложности по техническому заданию клиента.
Your comment is awaiting moderation.
Производим пластиковые https://zavod-dimax.ru окна и выполняем профессиональную установку. Качественные материалы, точные размеры, быстрый монтаж и гарантийное обслуживание для комфорта и уюта в помещении.
Your comment is awaiting moderation.
Discover the exciting world of gambling with 777bet login and win big!
Its popularity stems from having an intuitive design and dependable operation.
Your comment is awaiting moderation.
цена квартир 2025 жк светский лес сочи цены
Your comment is awaiting moderation.
Капельница от запоя в Волгограде — это эффективный способ быстро восстановить организм после длительного употребления алкоголя. Процедура проводится врачом-наркологом и направлена на выведение токсинов, нормализацию обмена веществ и стабилизацию работы нервной системы. Инфузионная терапия помогает устранить головную боль, слабость, тошноту, восстановить сон и аппетит. Благодаря внутривенному введению препаратов эффект наступает уже через 20–30 минут после начала процедуры.
Получить больше информации – капельница от запоя волгоград
Your comment is awaiting moderation.
jouer sur 1win telecharger 1win apk
Your comment is awaiting moderation.
джойказино зеркало на сегодня джойказино зеркало
Your comment is awaiting moderation.
Op zoek naar een casino? WinItt Casino biedt online gokkasten en live games. Het biedt snel inloggen, eenvoudige navigatie, moderne speloplossingen en stabiele prestaties op zowel computers als mobiele apparaten.
Your comment is awaiting moderation.
Hey there, everyone! The name’s Admin Read:
На Kraken вы найдёте всё, что нужно для дома, офиса и хобби. Платформа кракен ссылка зеркало радует выгодными предложениями и эксклюзивными коллекционными предметами. Покупка становится ещё проще с помощью акций и скидок. Kraken заботится о защите сделок, что привлекает покупателей со всего мира. Именно https kraken делает покупки удобными и безопасными.
Your comment is awaiting moderation.
Поставляем грунт https://organicgrunt.ru торф и чернозем с доставкой по Москве и Московской области. Подходит для посадок, благоустройства и озеленения. Качественные смеси, оперативная логистика и удобные условия для частных и коммерческих клиентов.
Your comment is awaiting moderation.
Алкогольная интоксикация вызывает сильное обезвоживание и разрушает баланс электролитов в организме. Без медицинской помощи восстановление может занять несколько дней, а в тяжёлых случаях приводит к осложнениям. Капельница помогает безопасно и быстро вывести этанол и продукты его распада, восполнить уровень жидкости, снизить нагрузку на печень и сердечно-сосудистую систему. Процедура проводится амбулаторно или на дому, что делает её доступной и удобной для пациентов.
Подробнее тут – капельница от запоя анонимно на дому в волгограде
Your comment is awaiting moderation.
риобет зеркало рабочее https://riobetcasino-money.ru
Your comment is awaiting moderation.
Ищете универсальный магазин?
Mega предоставит всё необходимое!
Ознакомьтесь с огромным выбором категорий, от
электроники и книг до модной одежды и других товаров.
Интуитивно понятный интерфейс mega gl и
надёжные методы доставки делают покупки удобными и быстрыми.
Кроме того, ежедневные акции и
скидки даркнет ссылка помогут вам сэкономить на любимых товарах.
Не пропустите возможность – покупайте прямо сейчас и
получайте незабываемые впечатления!.
мегу через тор: https://xn--megsb-l11b.com
Your comment is awaiting moderation.
machines a sous 1win 1win telecharger
Your comment is awaiting moderation.
inscription melbet telecharger melbet apk
Your comment is awaiting moderation.
Городской портал https://u-misti.cherkasy.ua Черкасс — свежие новости, события, происшествия, экономика и общественная жизнь. Актуальные обзоры, городская хроника и полезная информация для жителей и гостей города.
Your comment is awaiting moderation.
Новости Днепра https://u-misti.dp.ua сегодня — актуальные события города, происшествия, экономика, политика и общественная жизнь. Оперативные обновления, важные решения властей и главные темы дня для жителей и гостей города.
Your comment is awaiting moderation.
my link jaxx liberty wallet
Your comment is awaiting moderation.
Hi! Hope your day is going smoothly.
Hello, I offer financial backing to quality websites. Your platform appears worthy of consideration. Would you like to discuss possibilities? Please contact me on WhatsApp +380668962476
Your comment is awaiting moderation.
Актуальные новости https://u-misti.chernivtsi.ua Черновцов на сегодня. Экономика, происшествия, культура, инфраструктура и социальные вопросы. Надёжные источники, регулярные обновления и важная информация для жителей города.
Your comment is awaiting moderation.
Винница онлайн https://u-misti.vinnica.ua последние новости и городская хроника. Главные события, заявления официальных лиц, общественные темы и изменения в жизни города в удобном формате.
Your comment is awaiting moderation.
Новости Днепра https://u-misti.dp.ua сегодня — актуальные события города, происшествия, экономика, политика и общественная жизнь. Оперативные обновления, важные решения властей и главные темы дня для жителей и гостей города.
Your comment is awaiting moderation.
所謂「容易贏」通常是指高 RTP 的老虎機,例如:《Book of 99》– RTP 高達 99% ,理論上在長期回報方面對玩家較有利,但仍需理性投注。 主要功能包括「翻滾」功能,獲勝符號會消失,新的符號會掉落; 「乘數點」功能,以最高可達 128 倍的乘數標記位置;以及「免費旋轉」回合,乘數始終保持不變。 奧林匹斯之門1000 Gates of Olympus 1000 是一款極具吸引力的神話主題老虎機遊戲,玩家將跟隨古希臘的眾神,例如宙斯(Zeus),踏上一段寶藏冒險之旅。該遊戲結合了經典玩法與創新機制,還有高達 1000倍 的神奇倍數加成,讓玩家隨時期待巨額獎金的來臨! Wild Wild Riches包括 Money Collect Bonus 功能中的另一個有趣的獎金,稱為 Jackpot 。當與 Wild 符號結合使用時,落在基礎遊戲轉軸上的 Pot of Gold 符號將為您帶來許多不同類型的獎勵。這些獎勵取決於金罐的乘數,從 1 倍到 25 倍不等,而頭獎可分為三個子類型:
https://pumpyoursound.com/u/user/1557419
3. 啟動並享受 Gates of Olympic 1000 遊戲 下載Android版本APK目前暫不提供Quantum Gates的APK檔下載,請前往GooglePlay下載。 3. 啟動並享受 Gates of Olympus Mythopoly 2. 從 Play Store 下載 Col Gates Olympus Slots: Zeus Return MiniVerse – Offline Mini Games Get exclusive access to beauty tips and discounts for our VIP List customers only. Join the Cali’s VIP List today and get 15% OFF your next order! Your location: рџ‡єрџ‡ё United States PKV Game Online Zeus Starlight Lord of Olympus Col Gates Zeus Scatter Pragmatic Full AC Gates of Olympus Mythopoly Gates of Olympus Mythopoly Access Restricted Casino Col Gates 快速點擊,賺取積分,並在 Gates of Olympic 1000 中改變水晶形狀! 遊戲 3. 啟動並享受 Gates of Olympus Mythopoly ► Fruit Plate is a classic recreation of the fruit plate, full of fruits and constant rewards!
Your comment is awaiting moderation.
telecharger le site web melbet melbet telecharger
Your comment is awaiting moderation.
Новости Киева https://u-misti.kyiv.ua сегодня — актуальные события столицы, происшествия, политика, экономика и общественная жизнь. Оперативные обновления, важные решения властей и ключевые темы дня для жителей и гостей города.
Your comment is awaiting moderation.
Львов онлайн https://u-misti.lviv.ua последние новости и городская хроника. Важные события, заявления официальных лиц, общественные темы и изменения в жизни одного из крупнейших городов Украины.
Your comment is awaiting moderation.
Новости Хмельницкого https://u-misti.khmelnytskyi.ua сегодня на одном портале. Главные события города, решения властей, происшествия, социальная повестка и городская хроника. Быстро, понятно и по делу.
Your comment is awaiting moderation.
Новости Житомира https://u-misti.zhitomir.ua сегодня: городские события, инфраструктура, транспорт, культура и социальная сфера. Оперативные обновления, обзоры и важная информация о жизни Житомира онлайн.
Your comment is awaiting moderation.
Портал города https://u-misti.odesa.ua Одесса с новостями, событиями и обзорами. Всё о жизни города: решения властей, происшествия, экономика, спорт, культура и развитие региона.
Your comment is awaiting moderation.
Полтава онлайн https://u-misti.poltava.ua городской портал с актуальными новостями и событиями. Главные темы дня, общественная жизнь, городские изменения и полезная информация для горожан.
Your comment is awaiting moderation.
Блог для мужчин https://u-kuma.com с полезными статьями и советами. Финансы, работа, здоровье, отношения и личная эффективность. Контент для тех, кто хочет разбираться в важных вещах и принимать взвешенные решения.
Your comment is awaiting moderation.
Портал для пенсионеров https://pensioneram.in.ua Украины с полезными советами и актуальной информацией. Социальные выплаты, пенсии, льготы, здоровье, экономика и разъяснения сложных вопросов простым языком.
Your comment is awaiting moderation.
Объясняем сложные https://notatky.net.ua темы просто и понятно. Коротко, наглядно и по делу. Материалы для тех, кто хочет быстро разобраться в вопросах без профессионального жаргона и сложных определений.
Your comment is awaiting moderation.
visit our website toast wallet download
Your comment is awaiting moderation.
познавательный блог https://zefirka.net.ua с интересными статьями о приметах, значении имен, толковании снов, традициях, праздниках, советах на каждый день.
Your comment is awaiting moderation.
Новости Киева https://infosite.kyiv.ua события города, происшествия, экономика и общество. Актуальные обзоры, аналитика и оперативные материалы о том, что происходит в столице Украины сегодня.
Your comment is awaiting moderation.
Автомобильный портал https://avtogid.in.ua с актуальной информацией об автомобилях. Новинки рынка, обзоры, тест-драйвы, характеристики, цены и практические рекомендации для ежедневного использования авто.
Your comment is awaiting moderation.
Этот информационный материал привлекает внимание множеством интересных деталей и необычных ракурсов. Мы предлагаем уникальные взгляды на привычные вещи и рассматриваем вопросы, которые волнуют общество. Будьте в курсе актуальных тем и расширяйте свои знания!
Изучить вопрос глубже – https://vivod-iz-zapoya-1.ru/
Your comment is awaiting moderation.
Днепр онлайн https://faine-misto.dp.ua городской портал с актуальными новостями и событиями. Главные темы дня, общественная жизнь, городские изменения и полезная информация для горожан.
Your comment is awaiting moderation.
Новости Львова https://faine-misto.lviv.ua сегодня: городские события, инфраструктура, транспорт, культура и социальная повестка. Обзоры, аналитика и оперативные обновления о жизни города онлайн.
Your comment is awaiting moderation.
Портал города Хмельницкий https://faine-misto.km.ua с новостями, событиями и обзорами. Всё о жизни города: решения местных властей, происшествия, экономика, культура и развитие региона.
Your comment is awaiting moderation.
Новости Житомира https://faine-misto.zt.ua сегодня: события города, инфраструктура, транспорт, культура и социальная сфера. Обзоры, аналитика и оперативные обновления о жизни Житомира онлайн.
Your comment is awaiting moderation.
Сайт города Винница https://faine-misto.vinnica.ua свежие новости, городские события, происшествия, экономика, культура и общественная жизнь. Актуальные обзоры, важная информация для жителей и гостей города.
Your comment is awaiting moderation.
Сайт города Одесса https://faine-misto.od.ua свежие новости, городские события, происшествия, культура, экономика и общественная жизнь. Актуальные обзоры, важная информация для жителей и гостей Одессы в удобном формате.
Your comment is awaiting moderation.
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Подробнее – https://vivod-iz-zapoya-2.ru/
Your comment is awaiting moderation.
global organization globalideas.org.au that implements healthcare initiatives in the Asia-Pacific region. Working collaboratively with communities, practical improvements, innovative approaches, and sustainable development are key.
Your comment is awaiting moderation.
Прогноз курса доллара от internet-finans.ru. Ежедневная аналитика, актуальные котировки и экспертные мнения. Следите за изменениями валют, чтобы планировать обмен валют и инвестиции эффективно.
Your comment is awaiting moderation.
Rafa Silva http://rafa-silva.com.az is an attacking midfielder known for his dribbling, mobility, and ability to create chances. Learn more about his biography, club career, achievements, playing style, and key stats.
Your comment is awaiting moderation.
internet app monetization
Your comment is awaiting moderation.
от 4 250 ?/м 2 https://si-design.ru/western-port
Отзывы наших клиентов https://si-design.ru/o-nas
Цена в Москве https://si-design.ru/lime74m2
Мы работаем с частными бригадами и несем гарантии и ответственность за всю сделанную работу https://si-design.ru/nakhabino
Средняя цена за кв https://si-design.ru/o-nas
м https://si-design.ru/privacy
7 тыс https://si-design.ru/three-storey_house
р https://si-design.ru/hollandpark60m
Они работают в нашем программном решении и в связке с дизайнером https://si-design.ru/mihaylov-park
У них огромный опыт ремонта по дизайн проектам https://si-design.ru/2h-komnatnay-kvartira
Этим мы исключаем ситуацию, когда дизайнер обвиняет во всем прораба, а прораб дизайнера https://si-design.ru/akcii
Наши тарифы https://si-design.ru/uslugi
Три аргумента, чтобы заказать дизайн-проект интерьера квартиры под ключ https://si-design.ru/hollandpark60m
Your comment is awaiting moderation.
Компания «Мастер БОБР» производит установку натяжных потолков в Санкт-Петербурге и Л https://skyprofi.ru/besshchelevoj-natyazhnoj-potolok/
О https://skyprofi.ru/slott-natyazhnye-potolki/
по выгодным ценам https://skyprofi.ru/natyazhnoj-potolok-so-skrytym-karnizom/
Мы занимаемся производством потолочных конструкций любой степени сложности – из высококачественных материалов различных производителей https://skyprofi.ru/natyazhnye-potolki-pvkh/glyancevye/
Наша фирма специализируется на монтаже потолочных конструкций https://skyprofi.ru/stati/francuzskie-natyazhnye-potolki/
В компании «Невадо» можно встретить разные виды натяжных потолков от производителя https://skyprofi.ru/natyazhnye-potolki-system-shtok/
Классикой потолочного пространства являются ПВХ полотна https://skyprofi.ru/tipovye-resheniya/natyazhnye-potolki-10m2/
Матовые, глянцевые и сатиновые потолки покорят своим разнообразием: более двухсот цветов и фактур https://skyprofi.ru/stati/natyazhnye-potolki-bez-nagreva/
Бесплатный замер https://skyprofi.ru/installment/
Воспользуйтесь новым сервисом от компании “Невадо” – закажите БЕСПЛАТНО дизайн натяжного потолка по Вашей фотографии https://skyprofi.ru/tipovye-resheniya/natyazhnye-potolki-6m2/
Сертификаты на полотна для натяжных потолков https://skyprofi.ru/stati/funkcionalnaya-i-praktichnaya-dekorativnaya-lenta-dlya-natyazhnogo-potolka/
Навесные потолки https://skyprofi.ru/zerkalnye-natyazhnye-potolki/
Your comment is awaiting moderation.
Всё очень вкусно ??, всем гостям понравилось, спасибо большое за ваш труд https://shcherbinins.ru/
заказ привезли вовремя https://shcherbinins.ru/aboutus
Буду рекомендовать всем знакомым https://shcherbinins.ru/uslugy
Красочное оформление фуршетной линии с разнообразными закусками, чтобы гости остались довольны https://shcherbinins.ru/menu
Всё очень понравилось! Всё свежее и вкусное https://shcherbinins.ru/aboutus
Доставили вовремя https://shcherbinins.ru/uslugy
Спасибо!
Чтобы создать для вас максимально комфортные условия, наша компания предлагает три способа организации мероприятий по кейтерингу:
34 752 ? -18%
Техническая организация https://shcherbinins.ru/uslugy
Your comment is awaiting moderation.
UFC Baku fan site ufc-baku for fans of mixed martial arts. Tournament news, fighters, fight results, event announcements, analysis and everything related to the development of UFC in Baku and Azerbaijan.
Your comment is awaiting moderation.
Barcelona fan site https://barcelona.com.az/ with the latest news, match results, squads and statistics. Club history, trophies, transfers and resources for loyal fans of Catalan football.
Your comment is awaiting moderation.
Galatasaray Football Club https://galatasaray.com.az latest news, fixtures, results, squad and player statistics. Club history, achievements, transfers and relevant information for fans.
Your comment is awaiting moderation.
Hello traders!
Checked out a concise overview about current crypto market updates.
It breaks down how the market’s moving in Bitcoin, Ethereum, and altcoins.
Very clear and detailed.
Learn more
Your comment is awaiting moderation.
Greetings everyone!
Just read a useful overview about current crypto market updates.
It explains recent trends in digital assets.
Nice balanced view.
Check article
Your comment is awaiting moderation.
Портал для жінок https://u-kumy.com про стиль, здоров’я та саморозвиток. Експертні поради, чесні огляди, лайфхаки для дому та роботи, ідеї для відпочинку та гармонійного життя.
Your comment is awaiting moderation.
W 2026 roku w Polsce https://kasyno-revolut.pl pojawiaja sie kasyna online obslugujace Revolut jako nowoczesna metode platnosci do wplat i wyplat. Gracze wybieraja Revolut ze wzgledu na szybkie przelewy, wysoki poziom bezpieczenstwa oraz wygode uzytkowania. To idealne rozwiazanie dla osob ceniacych kontrole finansow
Your comment is awaiting moderation.
Жіночий портал https://soloha.in.ua про красу, здоров’я, стосунки та саморозвиток. Корисні поради, що надихають історії, мода, стиль життя, психологія та кар’єра – все для гармонії, впевненості та комфорту щодня.
Your comment is awaiting moderation.
Paysafecard https://paysafecard-casinos.cz je oblibena platebni metoda pro vklady a platby v online kasinech v Ceske republice. Hraci ji ocenuji predevsim pro vysokou uroven zabezpeceni, okamzite transakce a snadne pouziti. Podle naseho nazoru je Paysafecard idealni volbou pro hrace, kteri chteji chranit sve finance a davaji prednost bezpecnym platebnim resenim
Your comment is awaiting moderation.
W 2026 roku w Polsce dziala kilka kasyn https://kasyno-paypal.pl online obslugujacych platnosci PayPal, ktory jest wygodnym i bezpiecznym sposobem wplat oraz wyplat bez koniecznosci podawania danych bankowych. Popularne platformy z PayPal to miedzynarodowi operatorzy z licencjami i bonusami, oferujacy szybkie transakcje oraz atrakcyjne promocje powitalne
Your comment is awaiting moderation.
Hello !!
I came across a 153 great page that I think you should visit.
This platform is packed with a lot of useful information that you might find insightful.
It has everything you could possibly need, so be sure to give it a visit!
https://kroxen.com/2022/10/03/plastic-surgry/
And do not forget, everyone, that a person at all times may inside this particular article discover responses to the most the absolute tangled inquiries. We attempted to lay out all of the data in the most very easy-to-grasp method.
Your comment is awaiting moderation.
Если вы хотите повысить свои навыки продвижения, обязательно пройдите уроки GSA, чтобы эффективно использовать все возможности этих инструментов.
Первый шаг в обучении — изучение интерфейса XRumer и GSA ser.
Your comment is awaiting moderation.
Вы приобрели себе долгожданное жилье и сделали в нем ремонт https://www.legnostyle.ru/proizvodstvo/dveri-iz-dereva/
Все уже готово к заселению осталось дело за малым, подобрать мебель https://www.legnostyle.ru/catalog/mebel/prihojie/gp-4.html
Большинство людей предпочитают эксклюзивную, элитную мебель, сделанную непосредственно на заказ под ваше конкретное помещение https://www.legnostyle.ru/catalog/inter-eri/peregorodki/a-15.html
Такой индивидуальный подход дает возможность не только оформить свое жилье элитной мебелью, но и создать свой уникальный текстиль любой комнаты https://www.legnostyle.ru/dvystvorchatye-dveri.html
Для этого лучше всего обратиться к профессионалам, которые на протяжении полувека занимают лидирующие позиции в сфере мебельного производства и являются своего рода законодателями дизайнерской моды мебели https://www.legnostyle.ru/catalog/mebel/komodi-i-tualetnie-stoliki-ot-15-000-rub/kts-24.html
Все это принадлежит итальянским мастерам мебельного производства https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/nestandarnye/model-i17.html
В настоящие время существует более пятисот различных итальянских компаний, которые занимаются производством, поставками и продажами элитной мебели https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/a-1.html
В интернете вы легко сможете не только найти любую интересующую вас компанию но и ознакомиться с полным перечнем всей продукции, сделать свой заказ, проконсультироваться со специалистами сайта и даже заказать индивидуальный проект https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/ottimo/mejkomnatnaa-dver-o12.html
Итальянская продукция придает вашему помещению комфорта изысканности и оригинальности https://www.legnostyle.ru/catalog/mebel/garderobnie/garderobnaa-model-scg-39.html
Любой ваш гость сможет по достоинству оценить красоту и уникальность вашего дизайна https://www.legnostyle.ru/catalog/lestnici/?PAGEN_1=2
Итальянские мастера используют для своих работ только высококачественные дорогие материалы https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/perfetto/model-p30.html
Редкие породы древесины, драгоценные металлы и камни, шикарная и уникальная роспись, и резьба по дереву придает любой индивидуальной мебели просто потрясающий вид https://www.legnostyle.ru/catalog/mebel/garderobnie/gp-15.html
Большинство итальянской продукции является уникальной в своем роде, так как весь процесс изготовления проходит вручную специалистами компании https://www.legnostyle.ru/catalog/kuhni/kuhna-3.html
Именно поэтому итальянская мебель стоит та дорого, и не каждый человек может себе позволить приобретении элитной мебели от итальянских производителей https://www.legnostyle.ru/catalog/lestnici/lestnica-l1-24.html
И среди этого множества итальянских компаний, существуют и те фирмы, которые производят не только элитную мебель, но и мебель эконом класса https://www.legnostyle.ru/catalog/mebel/d1-13.html
Так что если вы хотите приобрести для себя итальянскую мебель, но на дорогостоящую нет средств, воспользовавшись интернетом, вы сможете найти итальянскую компанию, которая удовлетворит вас по соотношению цены и качества https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/diverso/mejkomnatnaa-dver-d10.html
Для этого достаточно посетить любой сайт, который является партнером итальянских компаний https://www.legnostyle.ru/catalog/mebel/kts-28.html
Безупречная эргономика https://www.legnostyle.ru/catalog/inter-eri/stenovie-paneli/s41.html
Каждый элемент кабинета спроектирован таким образом, чтобы создавать оптимальные условия для работы https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/nestandarnye/mejkomnatnaa-dver-d11.html
Деловые мелочи всегда будут под рукой, на просторной столешнице разместятся все важные бумаги, удобное кресло обеспечит эффективную поддержку позвоночника https://www.legnostyle.ru/catalog/mebel/shkafy-sekcii-gorki/scg-2.html
Исходя из совокупности характеристик, присущих элитной мебели, становится понятной её возрастающая популярность https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/mejkomnatnie-arki-i-portali/arka-a6.html
Качество и красота на долгие-долгие годы стоят затраченных материальных ресурсов и, как показывает практика, многие покупатели уже пришли к этому выводу https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/mejkomnatnaa-dver-d19.html
Инициатором протеста стало новое профсоюзное объединение медицинских работников https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/mejkomnatnaa-dver-d6.html
По мнению активистов, больницы Гонконга Опубликовано 04/02/2020 – 15:45
Специалисты салона Абрис хорошо знакомы с ассортиментом каждой из представленных фабрик и будут рады помочь Вам в подборе необходимых предметов интерьера https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/impressio/dver-i24.html
Итальянская мебель производится под заказ, и изготавливается мастерами в соотвествии с индивидуальными пожеланиями клиента https://www.legnostyle.ru/dubovye-dveri.html?PAGEN_2=11
Безусловно, такое признание заслужено, потребители отмечают безупречное качество немецких кухонь и идеальный сервис https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/dver-d43.html
Такие же требования немецкие фабрики предъявляют и своим дилерам, согласно кодексу немецких производителей — дилер — это продолжение фабрики и обязан поддерживать высокие стандарты https://www.legnostyle.ru/catalog/lestnici/lestnica-l8-9-d.html
В свою очередь, дилеры также остаются довольны сотрудничеством, поскольку каждая фабрика дорожит своей репутацией и всегда соблюдает все сроки и договоренности, поэтому покупать немецкие кухни у проверенного дилера — надежно и безопасно https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/peregorodka-model-a9.html
Your comment is awaiting moderation.
Изготовление и монтаж эксклюзивных, индивидуальных заказов в сотрудничестве с рядом дизайн-бюро, индивидуальными дизайнерами и архитекторами — наш конек https://www.legnostyle.ru/catalog/mebel/kb-11.html
Кроме того, мебель от лидирующих производителей отличается дополнительной отделкой с применением натурального сусального золота (24К) https://www.legnostyle.ru/catalog/mebel/s-7.html
Эстетику внешнего вида в основном задают изящные элементы, характерные для французского и итальянского стиля https://www.legnostyle.ru/catalog/mebel/garderobnaa-model-scg-15.html
Использование различных материалов позволяет интегрировать специфические фактуры https://www.legnostyle.ru/catalog/kuhni/kuhna-23.html
Их контраст и создает уникальный внешний вид предмета мебели https://www.legnostyle.ru/catalog/inter-eri/a-33.html
Сегодня в России существуют фирмы, которые занимаются доставкой элитной мебели из Европы https://www.legnostyle.ru/dubovye-dveri.html?PAGEN_2=4
Элитная немецкая и итальянская мебель в Барнауле https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/nestandarnye/vhodnaa-dver-e30.html
Кухни, спальни, прихожие и гардеробные – вся мебель спланирована таким образом, чтобы легко реализовать творческие задумки в интерьере дома, с учётом особенностей жилья https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/iz-dyba/?PAGEN_1=4
Перед смертью супруги заморозили несколько эмбрионов, так как планировали завести детей при помощи суррогатной матери https://www.legnostyle.ru/catalog/lestnici/na-vtoroy-etazh/lestnica-l4-6.html
Эмбрионы хранились в клинике в жидком азоте при температуре -196 градусов https://www.legnostyle.ru/catalog/lestnici/lestnica-l1-8.html
Бабушки и дедушки новорожденного долгое время судились Опубликовано 13/04/2018 – 21:25
Внимание! Владельцы и создатели данного сайта не несут ответственность за использование ссылок и информации, представленных на этом сайте, добавленной пользователями сайта в свободной форме в виде сообщений на форуме, а так же комментариям к материалам, статьям, новостям https://www.legnostyle.ru/catalog/mebel/komod-model-kts-27.html
Your comment is awaiting moderation.
Эвакуатор в Санкт-Петербурге: быстрая помощь в всякое время
Транспортные проблемы происходят непредвиденно. Транспорт отказывается стартовать морозным утром, колесо пробито на быстрой магистрали, а вероятно, случилась автокатастрофа. В таких ситуациях водители Северной столицы всё чаще прилагаются к профессиональным службам эвакуации.
Когда нужен эвакуатор
Оснований для вызова специального транспорта много. Существенная неисправность двигателя или КПП превращает независимое передвижение невозможным. Авария часто переводит автомобиль в положении, непригодном для езды. Истощённый аккумулятор в дальнем квартале города — тоже причина пригласить помощь эвакуатор дешево
Некоторые автовладельцы пользуются услугами эвакуации при приобретении машины с пробегом, когда нет убеждённости в технической работоспособности. Иные перевозят таким методом дорогостоящие автомобили на большие расстояния, исключая ненужного пробега.
Специфика работы в Санкт-Петербурге
Местные особенности Санкт-Петербурга формируют дополнительные сложности. Разводные мосты сдерживают передвижение в тёмное время навигации. Узкие улицы исторического центра нуждаются от водителей эвакуаторов исключительного мастерства. Скопления на КАД и основных магистралях побуждают диспетчеров скрупулёзно планировать маршруты.
Климатические условия добавляют свои изменения. Снеговые заносы зимой, весенние паводки, сезонные ливни — всё это сказывается на оперативность подачи техники. Опытные организации принимают во внимание эти факторы и располагают несколько экипажей в разных районах города.
Что обеспечивают организации эвакуации
Современные компании располагают разными типами техники. Манипуляторы управляются с необычными обстоятельствами. Платформы годятся для перевозки престижных автомобилей с небольшим дорожным зазором. Половинная погрузка спасает при дефекте только лобовой или кормовой оси.
Непрерывный режим работы предоставляет помощь в каждый момент. Диспетчерская служба обрабатывает запросы по телефону и через телефонные приложения. Опытные операторы скоро выявляют местоположение клиента и высылают соседний свободный экипаж.
Стоимость и сроки
Стоимость услуги формируется из нескольких компонентов. Базовый тариф включает прибытие техники и первые несколько километров пути. Дальнейшее расстояние считается особо. Уровень погрузки, габариты автомобиля, момент суток — всё сказывается на финальную сумму.
Среднее время ожидания эвакуатора в границах города равняется 30—40 минут. В удалённых районах и на трассах этот индикатор может возрасти до часа. Срочные выезды обходятся дороже, но гарантируют подачу в течение 20 минут.
Как найти надёжную организацию
Репутация службы проверяется комментариями реальных клиентов. Существование личного автопарка указывает о надёжности бизнеса. Гарантирование рисков охраняет потребности заказчика при порче автомобиля во время перевозки.
Ясное ценообразование без неявных надбавок — показатель честной работы. Квалифицированные водители с солидным стажем обеспечивают защищённую перевозку. Возможность карточного расчёта привносит комфорта.
Быт в городе нуждается в способности к внезапным случаям. Номер проверенной службы эвакуации в записной книжке — это уверенность и уверенность на дорогах СПБ.
Your comment is awaiting moderation.
Download 1xbet apk and enjoy a smooth and user-friendly betting platform on your device.
Installation of the 1xbet apk is straightforward and compatible with various Android devices.
Your comment is awaiting moderation.
What’s good, folks?
Wanted to post a super informative article about the latest in crypto.
It goes over key movements in BTC, ETH, and other coins.
Really a good read, especially if you trade.
See post
Your comment is awaiting moderation.
Эвакуатор в Санкт-Петербурге: срочная помощь в каждое время
Транспортные неприятности случаются непредвиденно. Автомобиль не может заводиться морозным утром, колесо повреждено на скоростной трассе, а может быть, произошла ДТП. В таких случаях автомобилисты Северной столицы всё чаще обращаются к специализированным компаниям эвакуации.
Когда нужен эвакуатор
Причин для вызова специального транспорта много. Значительная поломка двигателя или коробки передач создаёт самостоятельное передвижение неосуществимым. Авария часто переводит автомобиль в виде, неподходящем для езды. Разрядившийся аккумулятор в удалённом районе города — тоже основание заказать помощь стоимость эвакуатора спб
Ряд водители пользуются услугами эвакуации при получении машины с пробегом, когда нет уверенности в технической годности. Прочие транспортируют таким образом дорогостоящие автомобили на дальние расстояния, избегая избыточного пробега.
Характерные черты работы в Петербурге
Территориальные факторы Санкт-Петербурга формируют дополнительные препятствия. Разводные мосты ограничивают передвижение в ночное время навигации. Узкие улицы старинного центра предполагают от водителей эвакуаторов специального мастерства. Скопления на КАД и основных магистралях вынуждают диспетчеров внимательно прокладывать маршруты.
Метеорологические условия привносят свои поправки. Снежные заносы зимой, весенние паводки, жаркие ливни — всё это влияет на быстроту прибытия техники. Профессиональные фирмы учитывают эти факторы и держат множество экипажей в различных районах города.
Что обеспечивают организации эвакуации
Современные компании имеют различными типами техники. Манипуляторы справляются с специфическими ситуациями. Платформы годятся для транспортировки премиальных автомобилей с низким дорожным просветом. Половинная погрузка помогает при поломке только лобовой или задней оси.
Непрерывный режим работы предоставляет помощь в всякий момент. Координационная служба обрабатывает обращения по телефону и через мобильные приложения. Опытные операторы быстро выявляют координаты клиента и отправляют соседний незанятый экипаж.
Цена и сроки
Тариф услуги формируется из ряда элементов. Начальный тариф включает прибытие техники и первые ряд километров пути. Дальнейшее расстояние оплачивается особо. Сложность погрузки, габариты транспортного средства, период суток — всё воздействует на финальную сумму.
Типичное время подачи эвакуатора в пределах города составляет 30—40 минут. В удалённых районах и на магистралях этот параметр может возрасти до часа. Неотложные выезды обходятся дороже, но обязуют приезд в течение 20 минут.
Как найти надёжную организацию
Имидж службы определяется комментариями реальных клиентов. Существование собственного автопарка говорит о устойчивости бизнеса. Гарантирование обязательств оберегает потребности заказчика при порче автомобиля во время перевозки.
Ясное ценообразование без скрытых надбавок — показатель честной работы. Профессиональные водители с солидным стажем обещают защищённую перевозку. Способность электронного расчёта добавляет комфорта.
Быт в городе требует готовности к непредвиденным обстоятельствам. Контакт испытанной службы эвакуации в записной книжке — это безопасность и уверенность на дорогах Санкт-Петербурга.
Your comment is awaiting moderation.
Yo crypto fam!
Wanted to post a super informative article about Bitcoin & altcoin trends.
It covers market shifts in crypto in general.
Packed with insights, especially if you like staying ahead.
Take a look
Your comment is awaiting moderation.
Эвакуатор в Санкт-Петербурге: оперативная помощь в каждое время
Автомобильные неприятности случаются непредвиденно. Автомобиль не хочет запускаться холодным утром, колесо пробито на быстрой трассе, а возможно, имела место автокатастрофа. В таких случаях автомобилисты Северной столицы всё чаще обращаются к квалифицированным службам эвакуации.
Когда требуется эвакуатор
Причин для обращения за специализированного транспорта много. Существенная авария двигателя или КПП создаёт независимое движение неосуществимым. Дорожно-транспортное происшествие зачастую приводит автомобиль в виде, непригодном для езды. Разрядившийся аккумулятор в удалённом участке города — тоже основание заказать помощь эвакуатор
Некоторые автомобилисты пользуются услугами эвакуации при приобретении машины с пробегом, когда нет убеждённости в эксплуатационной годности. Другие транспортируют таким образом дорогие автомобили на большие расстояния, избегая избыточного пробега.
Специфика работы в Санкт-Петербурге
Географические условия Санкт-Петербурга формируют дополнительные трудности. Разводные мосты сдерживают перемещение в вечернее время навигации. Тесные улицы исторического центра нуждаются от шофёров эвакуаторов исключительного мастерства. Заторы на КАД и главных трассах побуждают диспетчеров тщательно прокладывать маршруты.
Погодные условия вносят свои изменения. Снежные заносы зимой, апрельские паводки, сезонные ливни — всё это воздействует на скорость прибытия техники. Опытные организации учитывают эти аспекты и располагают множество экипажей в отдельных районах города.
Что обеспечивают организации эвакуации
Современные компании обладают различными типами техники. Манипуляторы справляются с нестандартными ситуациями. Платформы годятся для доставки премиальных автомобилей с небольшим дорожным зазором. Половинная погрузка спасает при дефекте только передней или тыльной оси.
Ежедневный режим работы гарантирует помощь в любой момент. Диспетчерская служба принимает заявки по телефону и через телефонные приложения. Опытные операторы быстро устанавливают местоположение клиента и отправляют соседний незанятый экипаж.
Стоимость и сроки
Цена услуги формируется из множества компонентов. Начальный тариф покрывает прибытие техники и первые ряд километров пути. Добавочное расстояние оплачивается особо. Трудность погрузки, габариты машины, момент суток — всё воздействует на итоговую сумму.
Среднее время ожидания эвакуатора в черте города составляет 30—40 минут. В дальних районах и на дорогах этот параметр может возрасти до часа. Неотложные выезды обходятся дороже, но гарантируют прибытие в течение 20 минут.
Как найти достойную организацию
Репутация службы проверяется мнениями настоящих клиентов. Существование своего автопарка говорит о надёжности бизнеса. Страхование рисков защищает права заказчика при повреждении автомобиля во время транспортировки.
Понятное ценообразование без тайных наценок — индикатор добросовестной работы. Опытные водители с большим стажем обеспечивают безопасную перевозку. Возможность карточного расчёта привносит комфорта.
Существование в метрополии нуждается в готовности к непредвиденным обстоятельствам. Телефон надёжной службы эвакуации в записной книжке — это безопасность и уверенность на дорогах СПБ.
Your comment is awaiting moderation.
the best adult generator ai porn video generator create erotic videos, images, and virtual characters. flexible settings, high quality, instant results, and easy operation right in your browser. the best features for porn generation.
Your comment is awaiting moderation.
сервис рассылки сообщений сервисы рассылки email российские
Your comment is awaiting moderation.
mejores apuestas deportivas mejores casas nba hoy
Your comment is awaiting moderation.
6.
Установки есть, а пользователей нет? Узнайте, какие методы продвижения мобильного приложения действительно работают в 2025 году. https://wakelet.com/@marketerua
7.
Эффективная раскрутка мобильного приложения — это не удача, а стратегия. На сайте вы найдёте подробные гайды и советы от практиков. https://subscribe.ru/group/hi-tech-novosti-vyisokih-tehnologij/19352269/
8.
Хотите быстрее выйти в топ? Разбираем платное продвижение мобильных приложений: Google Ads, соцсети, CPI-кампании и оптимизация конверсий. http://povary.ru/article.php?id=17501
9.
Для стартапов и бизнеса. Всё о продвижении приложений для Android — от первых установок до стабильного роста аудитории. https://secondstreet.ru/profile/Marketerua/
10.
Результат начинается с плана. Узнайте, как создать эффективный план продвижения приложения, избежать ошибок и сэкономить бюджет. http://povary.ru/article.php?id=17501
Your comment is awaiting moderation.
Эвакуатор в Санкт-Петербурге: быстрая помощь в любое время
Транспортные затруднения случаются непредвиденно. Транспорт не может стартовать морозным утром, колесо пробито на скоростной дороге, а может быть, случилась ДТП. В таких случаях владельцы машин Северной столицы всё чаще обращаются к квалифицированным службам эвакуации.
Когда необходим эвакуатор
Поводов для вызова профильного транспорта предостаточно. Существенная поломка двигателя или коробки передач превращает автономное езду нереальным. ДТП зачастую оставляет автомобиль в виде, неподходящем для езды. Истощённый аккумулятор в дальнем квартале города — тоже основание пригласить помощь вызвать эвакуатор спб
Ряд автомобилисты применяют услугами эвакуации при приобретении машины с пробегом, когда нет гарантии в технической исправности. Иные доставляют таким методом дорогостоящие автомобили на длительные расстояния, предотвращая лишнего пробега.
Специфика работы в Санкт-Петербурге
Местные особенности Санкт-Петербурга формируют вспомогательные сложности. Разводные мосты ограничивают перемещение в ночное время навигации. Ограниченные улицы древнего центра требуют от водителей эвакуаторов исключительного мастерства. Скопления на КАД и центральных трассах побуждают диспетчеров скрупулёзно планировать маршруты.
Метеорологические условия привносят свои коррективы. Снеговые заносы зимой, весенние паводки, жаркие ливни — всё это сказывается на оперативность прибытия техники. Квалифицированные фирмы рассматривают эти факторы и держат несколько экипажей в разных районах города.
Что предлагают компании эвакуации
Нынешние компании располагают различными типами техники. Манипуляторы управляются с необычными случаями. Платформы подходят для перевозки элитных автомобилей с низким дорожным зазором. Неполная погрузка спасает при поломке только лобовой или задней оси.
Непрерывный режим работы обеспечивает помощь в любой момент. Операторская служба обрабатывает обращения по телефону и через телефонные приложения. Квалифицированные операторы скоро выявляют расположение клиента и высылают соседний свободный экипаж.
Стоимость и сроки
Стоимость услуги формируется из ряда компонентов. Основной тариф покрывает подачу техники и первые несколько километров пути. Добавочное расстояние оплачивается особо. Уровень погрузки, габариты автомобиля, время суток — всё воздействует на итоговую сумму.
Обычное время ожидания эвакуатора в границах города составляет 30—40 минут. В дальних районах и на дорогах этот индикатор может увеличиться до часа. Срочные выезды обходятся дороже, но гарантируют приезд в течение 20 минут.
Как выбрать проверенную организацию
Имидж службы контролируется мнениями подлинных клиентов. Присутствие личного автопарка свидетельствует о стабильности бизнеса. Обеспечение ответственности защищает интересы заказчика при дефекте автомобиля во время доставки.
Ясное ценообразование без тайных доплат — признак добросовестной работы. Опытные водители с значительным стажем обеспечивают надёжную перевозку. Опция электронного расчёта добавляет комфорта.
Жизнь в мегаполисе предполагает способности к неожиданным обстоятельствам. Номер проверенной службы эвакуации в телефоне — это спокойствие и уверенность на дорогах Питера.
Your comment is awaiting moderation.
1.
Хотите, чтобы ваше приложение скачивали? Узнайте всё про раскрутку мобильного приложения: эффективные стратегии, реальные кейсы и рабочие инструменты для роста установок. https://inkbunny.net/marketerua
2.
Разбираетесь в разработке, но не в маркетинге? Мы подробно объясняем платное продвижение мобильных приложений — от запуска рекламы до контроля бюджета и результатов. https://inkbunny.net/marketerua
3.
Продвижение без хаоса. На сайте собраны проверенные методы продвижения мобильного приложения, которые помогают выйти в топ и удержать пользователей. https://sitebs.ru/blogs/120397.html
4.
Ищете рост в Google Play? Изучите лучшие подходы к продвижению приложений для Android: ASO, реклама, аналитика и масштабирование. https://secondstreet.ru/profile/Marketerua/
5.
Не знаете, с чего начать? Мы поможем составить грамотный план продвижения приложения — пошагово и без лишних затрат. https://wakelet.com/@marketerua
Your comment is awaiting moderation.
6.
Установки есть, а пользователей нет? Узнайте, какие методы продвижения мобильного приложения действительно работают в 2025 году. https://inkbunny.net/marketerua
7.
Эффективная раскрутка мобильного приложения — это не удача, а стратегия. На сайте вы найдёте подробные гайды и советы от практиков. https://wakelet.com/@marketerua
8.
Хотите быстрее выйти в топ? Разбираем платное продвижение мобильных приложений: Google Ads, соцсети, CPI-кампании и оптимизация конверсий. https://inkbunny.net/marketerua
9.
Для стартапов и бизнеса. Всё о продвижении приложений для Android — от первых установок до стабильного роста аудитории. https://stocktwits.com/marketerua
10.
Результат начинается с плана. Узнайте, как создать эффективный план продвижения приложения, избежать ошибок и сэкономить бюджет. https://inkbunny.net/marketerua
Your comment is awaiting moderation.
Выбирайте себе косметику в каталоге, забирайте посылку в минимальные сроки и получайте удовольствие, вызывая восторг у близких людей https://sinapple.ru/collection/cbon/product/cbon-treatment-foundation-dark-beige Все это вам предоставляет Spadream https://sinapple.ru/collection/kremy-dlya-vek-i-kozhi-vokrug-glaz/product/keenwell-evolution-sphere-hydro-nourishing-multifunctional-eye-care Мы желаем вам приятных покупок https://sinapple.ru/collection/casmara/product/casmara-oxygenating-moisturizing-cream-2
Aldo Coppola; Angel Professional; REVLON; MATRIX; KERASTASE; L’OREAL; Schwarzkopf; и другие https://sinapple.ru/collection/germaine-de-capuccini/product/germaine-de-capuccini-emulsiya-vysokoy-zaschity-spf-50-xpert-lab-daily-hi-defense-spf50
Your comment is awaiting moderation.
Главные новости сегодня: эффективное похудение с помощью платного иглоукалывания: ваш путь к стройной фигуре
Your comment is awaiting moderation.
Купить автомобильный роутер 4g https://router-dlya-avtomobilya.ru
Your comment is awaiting moderation.
Эвакуатор в Санкт-Петербурге: срочная помощь в каждое время
Транспортные неприятности возникают неожиданно. Машина не хочет запускаться холодным утром, колесо проколото на скоростной магистрали, а может быть, имела место авария. В таких обстоятельствах владельцы машин Северной столицы всё чаще прилагаются к специализированным организациям эвакуации.
Когда необходим эвакуатор
Оснований для обращения за профильного транспорта предостаточно. Серьёзная авария двигателя или коробки передач создаёт автономное передвижение нереальным. ДТП зачастую оставляет автомобиль в положении, неподходящем для езды. Разрядившийся аккумулятор в дальнем квартале города — тоже причина заказать помощь заказать эвакуатор
Отдельные автомобилисты используют услугами эвакуации при покупке машины с пробегом, когда нет гарантии в эксплуатационной исправности. Прочие перевозят таким образом дорогие автомобили на длительные расстояния, исключая избыточного пробега.
Специфика работы в Петербурге
Территориальные особенности Санкт-Петербурга порождают добавочные препятствия. Разводные мосты затрудняют движение в вечернее время навигации. Ограниченные улицы древнего центра нуждаются от шофёров эвакуаторов исключительного мастерства. Скопления на КАД и главных дорогах заставляют диспетчеров внимательно прокладывать маршруты.
Метеорологические условия вносят свои поправки. Снеговые заносы зимой, апрельские паводки, летние ливни — всё это воздействует на скорость прибытия техники. Квалифицированные организации учитывают эти аспекты и располагают ряд экипажей в отдельных районах города.
Что предлагают компании эвакуации
Нынешние компании располагают разными типами техники. Манипуляторы решают задачи с нестандартными случаями. Платформы соответствуют для доставки элитных автомобилей с небольшим дорожным зазором. Неполная погрузка выручает при повреждении только лобовой или тыльной оси.
Круглосуточный режим работы предоставляет помощь в всякий момент. Операторская служба получает заявки по телефону и через телефонные приложения. Квалифицированные операторы быстро устанавливают координаты клиента и направляют ближайший доступный экипаж.
Цена и сроки
Тариф услуги складывается из нескольких элементов. Начальный тариф охватывает прибытие техники и первые ряд километров пути. Последующее расстояние тарифицируется отдельно. Трудность погрузки, габариты автомобиля, время суток — всё сказывается на конечную сумму.
Обычное время ожидания эвакуатора в пределах города равняется 30—40 минут. В дальних районах и на дорогах этот индикатор может возрасти до часа. Неотложные выезды стоят дороже, но гарантируют подачу в течение 20 минут.
Как выбрать достойную компанию
Статус службы определяется мнениями настоящих клиентов. Существование личного автопарка свидетельствует о надёжности бизнеса. Страхование рисков защищает потребности заказчика при дефекте автомобиля во время доставки.
Понятное ценообразование без тайных наценок — признак добросовестной работы. Квалифицированные водители с солидным стажем обещают безопасную перевозку. Опция карточного расчёта привносит удобства.
Быт в городе требует готовности к неожиданным ситуациям. Номер надёжной службы эвакуации в записной книжке — это безопасность и уверенность на дорогах Питера.
Your comment is awaiting moderation.
Hi everyone! Discovered a valuable post on top crypto stories this week.
It outlines the key updates in the crypto space. Packed with useful info.
If you’re into NFTs, DeFi or just news, this post will bring some good insight.
Visit link
Your comment is awaiting moderation.
Являешь патриотом? подписать контракт женщине на военную службу сво как оформить, какие требования предъявляются, какие выплаты и льготы предусмотрены. Актуальная информация о контрактной службе и порядке заключения.
Your comment is awaiting moderation.
Try your luck and enjoy the exciting game onswiminator slot, which will give you a sea of ??pleasure and bonuses.
Players appreciate Swiminator Slot for its easy-to-understand mechanics and exciting bonus features.
Your comment is awaiting moderation.
Упаковочное и фасовочное оборудование https://vostok-pack.ru купить с доставкой по всей России в течении 30 дней. Лучшие цены на рынке. Гарантия на оборудование. Консультационные услуги. Покупайте упаковочные машины для производства со скидкой на сайте!
Your comment is awaiting moderation.
меф казахстанский анкеты шлюх
Your comment is awaiting moderation.
Hi everyone! Just wanted to share a solid article on new trends in digital currencies.
It highlights the key updates in BTC, ETH, and altcoins. Packed with useful info.
If you’re into NFTs, DeFi or just news, this post will bring some good insight.
More info
Your comment is awaiting moderation.
Эвакуатор в Санкт-Петербурге: оперативная помощь в любое время
Автомобильные неприятности возникают неожиданно. Транспорт не может стартовать холодным утром, колесо проколото на быстрой магистрали, а вероятно, имела место ДТП. В таких обстоятельствах водители Северной столицы всё чаще прилагаются к квалифицированным компаниям эвакуации.
Когда нужен эвакуатор
Причин для вызова профильного транспорта множество. Существенная авария двигателя или коробки передач создаёт автономное езду нереальным. Авария зачастую оставляет автомобиль в виде, непригодном для езды. Севший аккумулятор в удалённом квартале города — тоже повод заказать помощь эвакуатор в Санкт-Петербурге
Отдельные автомобилисты пользуются услугами эвакуации при получении машины с пробегом, когда нет уверенности в технической исправности. Прочие перевозят таким способом ценные автомобили на дальние расстояния, исключая лишнего пробега.
Характерные черты работы в Петербурге
Местные особенности Санкт-Петербурга формируют вспомогательные препятствия. Разводные мосты затрудняют движение в вечернее время навигации. Ограниченные улицы древнего центра требуют от водителей эвакуаторов специального мастерства. Скопления на КАД и главных трассах вынуждают диспетчеров тщательно намечать маршруты.
Метеорологические условия привносят свои поправки. Белые заносы зимой, весенние паводки, летние ливни — всё это сказывается на скорость прибытия техники. Опытные компании рассматривают эти моменты и держат множество экипажей в различных районах города.
Что предоставляют организации эвакуации
Нынешние компании обладают разными типами техники. Манипуляторы решают задачи с необычными ситуациями. Платформы подходят для перевозки престижных автомобилей с небольшим дорожным просветом. Неполная погрузка помогает при повреждении только передней или кормовой оси.
Ежедневный режим работы гарантирует помощь в всякий момент. Операторская служба принимает заявки по телефону и через смартфонные приложения. Опытные операторы быстро определяют координаты клиента и отправляют ближайший свободный экипаж.
Цена и сроки
Стоимость услуги складывается из нескольких элементов. Начальный тариф покрывает подачу техники и первые несколько километров пути. Добавочное расстояние считается отдельно. Уровень погрузки, габариты транспортного средства, время суток — всё сказывается на конечную сумму.
Среднее время прибытия эвакуатора в границах города достигает 30—40 минут. В дальних районах и на трассах этот показатель может увеличиться до часа. Неотложные выезды стоят дороже, но обеспечивают прибытие в течение 20 минут.
Как найти проверенную организацию
Репутация службы проверяется комментариями настоящих клиентов. Существование собственного автопарка указывает о надёжности бизнеса. Страхование обязательств охраняет права заказчика при повреждении автомобиля во время транспортировки.
Прозрачное ценообразование без неявных надбавок — индикатор честной работы. Квалифицированные водители с значительным стажем обещают надёжную перевозку. Возможность карточного расчёта прибавляет удобства.
Быт в мегаполисе требует подготовленности к неожиданным случаям. Номер проверенной службы эвакуации в записной книжке — это спокойствие и уверенность на дорогах Питера.
Your comment is awaiting moderation.
Play puzzles https://share.google/twwza8kljdxluvkvb online for free – engaging puzzles for kids and adults. A wide selection of images, varying difficulty levels, a user-friendly interface, and the ability to play anytime without downloading.
Your comment is awaiting moderation.
Эвакуатор в Санкт-Петербурге: оперативная помощь в каждое время
Автомобильные затруднения происходят внезапно. Машина не хочет заводиться студёным утром, колесо повреждено на быстрой трассе, а может быть, имела место ДТП. В таких случаях водители Северной столицы всё чаще прибегают к специализированным организациям эвакуации.
Когда требуется эвакуатор
Оснований для вызова специального транспорта предостаточно. Серьёзная неисправность двигателя или КПП превращает автономное движение неосуществимым. Авария нередко приводит автомобиль в положении, неподходящем для езды. Истощённый аккумулятор в удалённом районе города — тоже повод заказать помощь эвакуатор в Санкт-Петербурге
Отдельные автовладельцы применяют услугами эвакуации при покупке машины с пробегом, когда нет гарантии в механической работоспособности. Иные транспортируют таким образом дорогие автомобили на большие расстояния, исключая избыточного пробега.
Характерные черты работы в Питере
Местные факторы Санкт-Петербурга порождают добавочные препятствия. Разводные мосты затрудняют передвижение в вечернее время навигации. Ограниченные улицы древнего центра предполагают от операторов эвакуаторов особого мастерства. Пробки на КАД и основных магистралях побуждают диспетчеров скрупулёзно прокладывать маршруты.
Климатические условия добавляют свои изменения. Белые заносы зимой, ранние паводки, летние ливни — всё это сказывается на оперативность приезда техники. Профессиональные организации учитывают эти факторы и располагают ряд экипажей в разных районах города.
Что обеспечивают службы эвакуации
Современные компании обладают разными типами техники. Манипуляторы справляются с специфическими обстоятельствами. Платформы соответствуют для перевозки премиальных автомобилей с низким дорожным зазором. Половинная погрузка выручает при повреждении только лобовой или тыльной оси.
Ежедневный режим работы гарантирует помощь в любой момент. Диспетчерская служба принимает обращения по телефону и через смартфонные приложения. Опытные операторы скоро устанавливают расположение клиента и отправляют соседний доступный экипаж.
Стоимость и сроки
Тариф услуги формируется из ряда составляющих. Базовый тариф включает прибытие техники и первые пару километров пути. Дальнейшее расстояние оплачивается особо. Уровень погрузки, габариты машины, время суток — всё сказывается на итоговую сумму.
Среднее время прибытия эвакуатора в черте города достигает 30—40 минут. В отдалённых районах и на магистралях этот показатель может подняться до часа. Экстренные выезды стоят дороже, но гарантируют прибытие в течение 20 минут.
Как подобрать надёжную компанию
Имидж службы определяется мнениями подлинных клиентов. Наличие личного автопарка свидетельствует о надёжности бизнеса. Обеспечение рисков оберегает интересы заказчика при порче автомобиля во время доставки.
Прозрачное ценообразование без тайных надбавок — признак добросовестной работы. Опытные водители с солидным стажем обещают защищённую перевозку. Способность электронного расчёта добавляет лёгкости.
Быт в метрополии нуждается в готовности к неожиданным обстоятельствам. Номер проверенной службы эвакуации в телефоне — это безопасность и уверенность на дорогах СПБ.
Your comment is awaiting moderation.
1.
Узнайте эффективные методы увеличения конверсии сайта. Практические советы, которые помогают улучшить конверсию сайта и превратить посетителей в клиентов. http://povary.ru/article.php?id=17498
2.
Хотите повысить конверсию на сайте без лишних затрат? Мы собрали лучшие стратегии и рабочие инструменты для стабильного роста продаж. https://subscribe.ru/group/hi-tech-novosti-vyisokih-tehnologij/19352251/
3.
Увеличить конверсию сайта реально. Разбираем ошибки, показываем решения и делимся проверенными подходами для бизнеса любого масштаба. https://able2know.org/user/penguinteam/
4.
Конверсия сайта — ключ к прибыли. Узнайте, какие способы её повышения работают в 2025 году и как внедрить их быстро. https://inkbunny.net/Penguinteam
5.
Низкие заявки и продажи? Пора задуматься о росте конверсии сайта. Пошаговые рекомендации и понятные примеры — без воды. https://yoo.rs/-1768756218?Ysid=285574
Your comment is awaiting moderation.
Эвакуатор в Санкт-Петербурге: срочная помощь в любое время
Автомобильные затруднения случаются непредвиденно. Машина не может заводиться морозным утром, колесо пробито на скоростной дороге, а возможно, случилась автокатастрофа. В таких случаях водители Северной столицы всё чаще обращаются к специализированным организациям эвакуации.
Когда требуется эвакуатор
Причин для заказа специального транспорта предостаточно. Серьёзная неисправность двигателя или коробки передач создаёт самостоятельное передвижение невозможным. Авария зачастую переводит автомобиль в состоянии, непригодном для езды. Истощённый аккумулятор в дальнем районе города — тоже основание вызвать помощь заказать эвакуатор
Некоторые автомобилисты используют услугами эвакуации при получении машины с пробегом, когда нет уверенности в технической исправности. Прочие транспортируют таким способом дорогостоящие автомобили на длительные расстояния, избегая избыточного пробега.
Специфика работы в Петербурге
Географические особенности Санкт-Петербурга порождают дополнительные трудности. Разводные мосты сдерживают перемещение в тёмное время навигации. Тесные улицы старинного центра требуют от шофёров эвакуаторов исключительного мастерства. Заторы на КАД и главных дорогах заставляют диспетчеров тщательно намечать маршруты.
Погодные условия привносят свои коррективы. Снеговые заносы зимой, весенние паводки, жаркие ливни — всё это влияет на скорость приезда техники. Профессиональные компании рассматривают эти факторы и располагают множество экипажей в отдельных районах города.
Что предоставляют службы эвакуации
Нынешние компании обладают разными типами техники. Манипуляторы управляются с специфическими случаями. Платформы годятся для транспортировки престижных автомобилей с низким дорожным зазором. Неполная погрузка выручает при поломке только фронтальной или тыльной оси.
Непрерывный режим работы предоставляет помощь в любой момент. Координационная служба принимает заявки по телефону и через телефонные приложения. Опытные операторы скоро определяют местоположение клиента и высылают соседний незанятый экипаж.
Цена и сроки
Тариф услуги образуется из ряда компонентов. Основной тариф охватывает прибытие техники и первые ряд километров пути. Добавочное расстояние тарифицируется дополнительно. Уровень погрузки, габариты автомобиля, период суток — всё влияет на финальную сумму.
Среднее время прибытия эвакуатора в пределах города достигает 30—40 минут. В отдалённых районах и на дорогах этот индикатор может увеличиться до часа. Неотложные выезды стоят дороже, но обеспечивают прибытие в течение 20 минут.
Как подобрать проверенную компанию
Статус службы проверяется отзывами реальных клиентов. Присутствие своего автопарка указывает о стабильности бизнеса. Обеспечение рисков охраняет интересы заказчика при порче автомобиля во время доставки.
Понятное ценообразование без скрытых доплат — показатель добросовестной работы. Квалифицированные водители с большим стажем обещают защищённую перевозку. Опция электронного расчёта привносит лёгкости.
Существование в метрополии предполагает готовности к внезапным ситуациям. Контакт испытанной службы эвакуации в записной книжке — это уверенность и уверенность на дорогах Санкт-Петербурга.
Your comment is awaiting moderation.
Zdrowie, rodzina i związki Podczas wydarzeń Pieśni Lodu i Ognia kometa-Światłonośca gra rolę Gwiazdy Porannej i Gwiazdy Wieczornej. Innymi słowy, George przeniósł mitologię Wenus na kometę. Mówi nam to nazywając swój czerwony miecz ‘Światłonoścą’, a potem wprowadzając czerwoną kometę – jako symbol Światłonoścy. Gdy Dany po raz pierwszy widzi kometę, w noc gdy spala Droga i budzi smoki (ogólnie mówiąc odgrywa scenę zniszczenia drugiego księżyca), widzi ją jako pierwszą gwiazdę tego wieczoru – Gwiazdę Wieczorną. To pierwszy wpis na długiej liście powiązać pomiędzy Wenus i czerwoną kometą. Z kulminacji Gry o tron: Dostaniesz informacje o aktualnych promocjach i nowościach Czy nasz mózg jest komputerem doskonałym? Jeśli tak, dlaczego podsuwa nam choroby? Według koncepcji Totalnej Biologii choroba jest idealnym rozwiązaniem mózgu, aby utrzymać nas przy życiu. Autor wyjaśnia jak powstają biologiczne reakcje organizmu na psychologiczne, środowiskowe i rodowe konflikty. Niemal każda choroba to FAZA ZDROWIENIA w procesie biologicznego rozwiązywania takich konfliktów przez mózg człowieka.
https://www.elitegym.ca/bizzo-casino-recenzja-dla-polskich-graczy/
Gates of Olympus slot jest jedną z flagowych produkcji znanego i lubianego dewelopera Pragmatic Play. Intrygujący motyw Olimpu potrafi pociągnąć za sobą iście boskie zdobycze. Maksymalna możliwa wygrana na tym slocie online to aż 15000-krotność stawki zakładu. Z kolei najwyższy możliwy mnożnik wynosi 5000x. W trakcie gry w Gates of Olympus slot możesz zdobyć także 15 darmowych spinów. Są one aktywowane po trafieniu przynajmniej czterech symboli Scattera. W trakcie gry bonusowej możesz otrzymać kolejne 5 spinów, jeśli natrafisz na przynajmniej trzy symbole Scattera. This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data.
Your comment is awaiting moderation.
Приятные цены https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/perfetto/dver-p32.html
Некоторым наши цены могут показаться завышенными, однако если у вас в приоритете надежность, износостойкость, прочность и экологичность, то вы поймете, что стоимость мебели полностью соответствует ее характеристикам https://www.legnostyle.ru/catalog/lestnici/na-vtoroy-etazh/
Мы устанавливаем максимально доступные цены на изделия, так как сотрудничаем напрямую с известными брендами https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/dver-p27.html
В Гонконге сотни работников медицины, в том числе медсестры и врачи, начали в понедельник забастовку https://www.legnostyle.ru/catalog/mebel/mebel-dla-biblioteki-b-17.html
По информации от местных СМИ, медики требуют, чтобы власти полностью закрыли границу с материковым Китаем, что предотвратит эпидемию короонавируса в регионе https://www.legnostyle.ru/radiusnye-mezhkomnatnye-dveri.html?PAGEN_2=14
Министерство окружающей среды Китая вчера опубликовало неутешительную статистику, согласно которой за первые шесть месяцев 2017 года качество воздуха в городах Поднебесной значительно ухудшилось https://www.legnostyle.ru/catalog/lestnici/na-vtoroy-etazh/lestnica-l1-20.html
От загрязнения
В к моим требованиям отнеслись со всем участием и пониманием, было предусмотрено абсолютно все https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/nestandarnye/?PAGEN_1=17
Сразу оговорюсь, что заказ кухни пришелся на ремонт в доме https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/razdvizhnye-dveri/razdvijnaa-dver-rd-5.html
Изначально с дизайнером обговорили технические моменты https://www.legnostyle.ru/catalog/lestnici/derevannie-marsevie-lestnici-s-plohadkami/lestnica-l1-1.html
Где разместить выключатели, как должна лечь проводка, где будут находится розетки, куда перенести отвод для газового стояка, все было предусмотрено для моего проекта https://www.legnostyle.ru/catalog/mebel/iz-duba/?PAGEN_1=5
Вообще, если вы хотите, чтобы кухня соответствовала всем вашим пожеланиям и капризам, то обязательно обговаривайте все технические нюансы с вашим дизайнером, чтобы при монтаже кухни не возникло проблем https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/impressio/dver-i26.html
А с дизайнером мне очень повезло https://www.legnostyle.ru/catalog/lestnici/elitnye/lestnica-l8-23.html
В 2014 году Китайским Министерством торговли был опубликован план развития внешней торговли на 2015 год https://www.legnostyle.ru/proizvodstvo/dveri-iz-dereva/mejkomnatnie/?PAGEN_1=15
Согласно данному плану, внешнеторговый оборот, начиная с 2015 года, должен
Среди предложений иомпании отлично впишется в любой интерьер https://www.legnostyle.ru/catalog/lestnici/lestnica-l1-3.html
Огромный выбор мебели для гостиниц, баров и бильярдных могут заинтересовать также профессионалов https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/d-peregorodki/
Your comment is awaiting moderation.
Количество категорий людей, которые приезжают в Китай, строго ограничено https://www.legnostyle.ru/catalog/mebel/komodi-i-tualetnie-stoliki-ot-15-000-rub/komod-model-kts-22.html
Как правило, это туристы, бизнесмены или студенты https://www.legnostyle.ru/catalog/mebel/spalni/sp-1.html
Есть еще эмигранты и рабочие https://www.legnostyle.ru/catalog/kuhni/kuhna-8.html
И если бизнесмены с
При изготовлении мебели мы используем только качественные и натуральные материалы, такие как: ценные породы древесины, искусственный и натуральный камень, сертифицированные ДСП и МДФ https://www.legnostyle.ru/catalog/inter-eri/stenovie-paneli/stenovie-paneli-model-s11.html
В Поднебесной выпускают самую разнообразную продукцию – компьютеры, бытовую технику, автомобили, одежду и т https://www.legnostyle.ru/catalog/mebel/komodi-i-tualetnie-stoliki-ot-15-000-rub/kts-7.html
д https://www.legnostyle.ru/catalog/mebel/garderobnaa-model-scg-16.html
Эта продукция выводится на международный рынок и обладает хорошим спросом https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/perfetto/model-p36.html
Но
Настоятельно рекомендуется заказывать разработку кухонного гарнитура исключительно под Вашу кухню https://www.legnostyle.ru/sborka-derevyannyh-lestnic.html
В этом случае удастся максимально эффективно вписать бытовую технику в фасад гарнитура https://www.legnostyle.ru/catalog/mebel/komodi-i-tualetnie-stoliki-ot-15-000-rub/komod-model-kts-25.html
Мы производим авторскую мебель по индивидуальным размерам только из высококачественной древесины https://www.legnostyle.ru/catalog/inter-eri/a-29.html
Прозрачные дверцы, резьба, декоративное оформление позволяют воплотить в жизнь самые смелые идеи https://www.legnostyle.ru/catalog/mebel/elitnaya-detskaya-mebel/d1-1.html
Укомплектуем Ваш дом, квартиру, офис или ресторан https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/d-peregorodki/?PAGEN_1=4
Дизайнеры тщательно разработают проект, учитывая все пожелания и тонкости создания мебели https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/vhodnie-dveri/vhodnaya-dver-e3.html
Список авторской мебели по индивидуальным проектам очень широкий и включает: кухни, шкафы, столы, кровати, двери, лестницы, окна, кессонные потолки и др https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/mejkomnatnaa-dver-o15.html
Мы производим различные элементы интерьера, декора https://www.legnostyle.ru/catalog/dveri/iz-massiva/?PAGEN_1=8
Компания специализируется на выпуске самой разнообразной продукции по индивидуальным проектам https://www.legnostyle.ru/shkafy-iz-massiva.html
На сайте проекта представлена актуальная и полная информация о более чем 5 232 680 организациях России и СНГ в виде удобного рубрикатора по сферам деятельности компаний и географического справочника организаций https://www.legnostyle.ru/catalog/mebel/mebel-dla-domasnei-biblioteki/mebel-dla-biblioteki-b-12.html
Администрация сайта не несет ответственности за контент на сайте, так как вся информация на сайте собрана из открытых источников и добавляется пользователями, а отзывы написаны посетителями сайта https://www.legnostyle.ru/catalog/lestnici/na-vtoroy-etazh/lestnica-l1-1.html
\
Your comment is awaiting moderation.
Эвакуатор в Санкт-Петербурге: оперативная помощь в каждое время
Машинные неприятности происходят неожиданно. Автомобиль не может стартовать студёным утром, колесо проколото на автомобильной магистрали, а вероятно, случилась авария. В таких обстоятельствах владельцы машин Северной столицы всё чаще прибегают к квалифицированным компаниям эвакуации.
Когда необходим эвакуатор
Причин для вызова профильного транспорта предостаточно. Существенная авария двигателя или КПП делает самостоятельное езду нереальным. Авария нередко переводит автомобиль в виде, неспособном для езды. Севший аккумулятор в удалённом районе города — тоже причина пригласить помощь эвакуатор
Ряд водители пользуются услугами эвакуации при получении машины с пробегом, когда нет убеждённости в механической исправности. Прочие доставляют таким способом дорогие автомобили на дальние расстояния, избегая лишнего пробега.
Специфика работы в Петербурге
Географические условия Санкт-Петербурга формируют добавочные препятствия. Разводные мосты сдерживают перемещение в ночное время навигации. Тесные улицы исторического центра требуют от операторов эвакуаторов специального мастерства. Заторы на КАД и основных трассах побуждают диспетчеров внимательно намечать маршруты.
Погодные условия добавляют свои коррективы. Снежные заносы зимой, весенние паводки, сезонные ливни — всё это воздействует на быстроту прибытия техники. Опытные организации учитывают эти моменты и держат ряд экипажей в различных районах города.
Что предлагают службы эвакуации
Современные компании имеют многообразными типами техники. Манипуляторы управляются с нестандартными ситуациями. Платформы подходят для транспортировки элитных автомобилей с небольшим дорожным зазором. Частичная погрузка выручает при дефекте только передней или тыльной оси.
Ежедневный режим работы обеспечивает помощь в каждый момент. Координационная служба получает запросы по телефону и через смартфонные приложения. Опытные операторы скоро устанавливают местоположение клиента и отправляют ближний свободный экипаж.
Тариф и сроки
Стоимость услуги складывается из множества компонентов. Начальный тариф покрывает подачу техники и первые ряд километров пути. Добавочное расстояние считается отдельно. Сложность погрузки, габариты машины, момент суток — всё сказывается на итоговую сумму.
Типичное время прибытия эвакуатора в границах города равняется 30—40 минут. В дальних районах и на трассах этот параметр может подняться до часа. Срочные выезды оцениваются дороже, но обязуют приезд в течение 20 минут.
Как подобрать достойную организацию
Репутация службы проверяется мнениями подлинных клиентов. Присутствие своего автопарка говорит о устойчивости бизнеса. Страхование рисков оберегает интересы заказчика при дефекте автомобиля во время доставки.
Понятное ценообразование без тайных наценок — показатель честной работы. Опытные водители с солидным стажем гарантируют защищённую перевозку. Возможность электронного расчёта прибавляет комфорта.
Жизнь в мегаполисе требует подготовленности к неожиданным ситуациям. Контакт надёжной службы эвакуации в телефоне — это безопасность и уверенность на дорогах Санкт-Петербурга.
Your comment is awaiting moderation.
Эвакуатор в Санкт-Петербурге: быстрая помощь в всякое время
Машинные затруднения происходят внезапно. Автомобиль не может запускаться морозным утром, колесо пробито на скоростной дороге, а может быть, произошла авария. В таких обстоятельствах автомобилисты Северной столицы всё чаще прибегают к квалифицированным службам эвакуации.
Когда требуется эвакуатор
Причин для обращения за специального транспорта предостаточно. Значительная авария двигателя или трансмиссии создаёт самостоятельное движение неосуществимым. Авария часто переводит автомобиль в виде, неподходящем для езды. Севший аккумулятор в удалённом районе города — тоже повод вызвать помощь эвакуатор в Санкт-Петербурге
Ряд автомобилисты используют услугами эвакуации при покупке машины с пробегом, когда нет убеждённости в эксплуатационной работоспособности. Другие доставляют таким способом дорогие автомобили на длительные расстояния, предотвращая лишнего пробега.
Особенности работы в Питере
Территориальные факторы Санкт-Петербурга формируют дополнительные препятствия. Разводные мосты сдерживают перемещение в тёмное время навигации. Ограниченные улицы старинного центра нуждаются от шофёров эвакуаторов исключительного мастерства. Заторы на КАД и центральных дорогах вынуждают диспетчеров скрупулёзно планировать маршруты.
Метеорологические условия привносят свои изменения. Белые заносы зимой, ранние паводки, сезонные ливни — всё это сказывается на оперативность приезда техники. Опытные фирмы рассматривают эти факторы и располагают несколько экипажей в отдельных районах города.
Что предлагают компании эвакуации
Актуальные компании имеют многообразными типами техники. Манипуляторы справляются с нестандартными ситуациями. Платформы соответствуют для транспортировки престижных автомобилей с малым дорожным просветом. Частичная погрузка спасает при дефекте только фронтальной или задней оси.
Ежедневный режим работы обеспечивает помощь в любой момент. Координационная служба принимает заявки по телефону и через смартфонные приложения. Опытные операторы скоро выявляют координаты клиента и отправляют ближайший свободный экипаж.
Цена и сроки
Стоимость услуги формируется из множества элементов. Начальный тариф охватывает прибытие техники и первые несколько километров пути. Последующее расстояние оплачивается отдельно. Трудность погрузки, габариты автомобиля, время суток — всё воздействует на конечную сумму.
Типичное время подачи эвакуатора в черте города равняется 30—40 минут. В дальних районах и на дорогах этот параметр может увеличиться до часа. Срочные выезды оцениваются дороже, но обеспечивают прибытие в течение 20 минут.
Как подобрать достойную организацию
Репутация службы контролируется отзывами подлинных клиентов. Наличие своего автопарка указывает о стабильности бизнеса. Обеспечение ответственности защищает интересы заказчика при порче автомобиля во время перевозки.
Прозрачное ценообразование без неявных надбавок — показатель добросовестной работы. Профессиональные водители с значительным стажем обеспечивают надёжную перевозку. Способность электронного расчёта прибавляет удобства.
Жизнь в мегаполисе предполагает способности к непредвиденным случаям. Телефон проверенной службы эвакуации в контактах — это уверенность и уверенность на дорогах Петербурга.
Your comment is awaiting moderation.
Эвакуатор в Санкт-Петербурге: срочная помощь в каждое время
Машинные затруднения случаются непредвиденно. Автомобиль не может заводиться студёным утром, колесо пробито на автомобильной магистрали, а вероятно, имела место авария. В таких обстоятельствах владельцы машин Северной столицы всё чаще прилагаются к специализированным организациям эвакуации.
Когда нужен эвакуатор
Оснований для заказа профильного транспорта множество. Серьёзная авария двигателя или коробки передач превращает автономное движение невозможным. ДТП нередко переводит автомобиль в виде, непригодном для езды. Истощённый аккумулятор в отдалённом квартале города — тоже основание вызвать помощь стоимость эвакуатора спб
Ряд водители пользуются услугами эвакуации при получении машины с пробегом, когда нет убеждённости в эксплуатационной исправности. Другие транспортируют таким методом ценные автомобили на длительные расстояния, предотвращая ненужного пробега.
Характерные черты работы в Петербурге
Территориальные факторы Санкт-Петербурга порождают вспомогательные препятствия. Разводные мосты затрудняют перемещение в ночное время навигации. Узкие улицы древнего центра требуют от операторов эвакуаторов специального мастерства. Скопления на КАД и основных дорогах заставляют диспетчеров внимательно планировать маршруты.
Метеорологические условия вносят свои поправки. Белые заносы зимой, апрельские паводки, сезонные ливни — всё это влияет на скорость подачи техники. Квалифицированные фирмы учитывают эти аспекты и располагают множество экипажей в отдельных районах города.
Что обеспечивают организации эвакуации
Нынешние компании располагают разными типами техники. Манипуляторы решают задачи с нестандартными ситуациями. Платформы соответствуют для перевозки престижных автомобилей с малым дорожным клиренсом. Половинная погрузка помогает при повреждении только лобовой или кормовой оси.
Круглосуточный режим работы обеспечивает помощь в любой момент. Операторская служба получает обращения по телефону и через мобильные приложения. Профессиональные операторы быстро устанавливают расположение клиента и направляют ближайший доступный экипаж.
Стоимость и сроки
Цена услуги складывается из ряда составляющих. Основной тариф охватывает подачу техники и первые несколько километров пути. Последующее расстояние тарифицируется отдельно. Уровень погрузки, габариты транспортного средства, момент суток — всё сказывается на конечную сумму.
Среднее время прибытия эвакуатора в пределах города составляет 30—40 минут. В дальних районах и на дорогах этот индикатор может подняться до часа. Срочные выезды обходятся дороже, но обеспечивают подачу в течение 20 минут.
Как выбрать проверенную организацию
Репутация службы определяется мнениями настоящих клиентов. Наличие собственного автопарка свидетельствует о устойчивости бизнеса. Страхование рисков охраняет права заказчика при дефекте автомобиля во время доставки.
Прозрачное ценообразование без скрытых надбавок — показатель порядочной работы. Квалифицированные водители с солидным стажем обещают надёжную перевозку. Опция электронного расчёта прибавляет комфорта.
Быт в городе нуждается в способности к неожиданным ситуациям. Контакт испытанной службы эвакуации в телефоне — это уверенность и уверенность на дорогах Питера.
Your comment is awaiting moderation.
Прикоснитесь к удивительные возможности новых игр. Пробуйте найти свои любимые сюжеты в гейм-зоне веб-казино для настоящих победителей. Я зашел на платформу по совету коллеги, который обожает азартные развлечения. Я даже представить себе не мог, сколько эмоций подарит мне эта платформа. Создание профиля было удобным процессом, который начался и завершился быстро. Когда я впервые увлекся одним из слотов на портале, я почувствовал прилив вдохновения casino-x-clubs.icu . Когда я получил свой первый выигрыш, я испытал невероятное чувство триумфа и радости. Игры оказались красочными, увлекательными и создающими ощущение настоящего погружения в приключение. Мобильная версия сайта выгодно отличается удобством интерфейса, что делает игру ещё более доступной. Casino подарило мне не только азарт, но и вдохновение, которое теперь сопровождает меня каждый раз, когда я захожу на платформу. Это место стало для меня чем-то большим, чем просто игровая платформа — это целая вселенная неповторимости и азарта. Если и вы хотите окунуться в мир сюрпризов, побед и радости, начните вашу азартную историю прямо здесь. Ваше приключение ждет вас именно сейчас https://gamaslot.icu .
Узнайте о удовольствие от игр на сайте казино когда вам удобно
Найдите путь к успеху на платформе казино игр в моменте
Откройте путь к усп
Узнайте о новые эмоции на казино в любое время
Погрузитесь в новые
0fa733d
Your comment is awaiting moderation.
Исследуйте невероятный мир. Оцените с первого взгляда иммерсивной вселенной. Я зашел на платформу по совету коллеги, который обожает азартные развлечения. Для новичка важно удобство — на Casino всё оказалось на высоте. Когда я начал, система регистрации оказалась выше всяких похвал: интуитивно понятно и никаких раздражающих задержек. Я начал с простых игровых автоматов, но очень быстро переключился на более сложные, которые держали меня в напряжении до конца poker-dom-mirrors.icu . Выигрыш оказался крупнее, чем я мог предположить, и эти эмоции будут преследовать меня ещё долго. Игры оказались красочными, увлекательными и создающими ощущение настоящего погружения в приключение. Мобильная версия сайта выгодно отличается удобством интерфейса, что делает игру ещё более доступной. Casino подарило мне не только азарт, но и вдохновение, которое теперь сопровождает меня каждый раз, когда я захожу на платформу. Здесь я нахожу то, что делает каждый свободный вечер незабываемым. Если и вы хотите начать свой азартный путь, регистрируйтесь прямо сейчас!. Ваш путь победителя начинается прямо здесь https://daddy-promocod.icu .
Узнайте о новые эмоции на платформе казино игр без лишних ожиданий
Найдите все грани победы сайт игр казино когда вам удобно
Погрузитесь в все грани победы на сайте казино сегодня
Найдите удовольствие от игр на сайте казино сейчас
Узнайте о ясность азарта на казино в моменте
fa8dd87
Your comment is awaiting moderation.
Погрузитесь в новейшие игровые технологии. Испытайте эмоции от игровых приключений в онлайн-площадке . Мне впервые рассказали о Casino друзья, упомянув их положительный опыт. С первых шагов я начал буквально увлекаться каждой деталью интерфейса и количества игр. Регистрация заняла всего несколько минут — просто, безопасно и без каких-либо сложностей. Я начал с простых игровых автоматов, но очень быстро переключился на более сложные, которые держали меня в напряжении до конца riobet-mirror.icu . Каждый шаг становился новым переживанием — от лёгкого волнения до ощущения настоящего триумфа. Игры оказались красочными, увлекательными и создающими ощущение настоящего погружения в приключение. Мобильная версия сайта выгодно отличается удобством интерфейса, что делает игру ещё более доступной. Casino подарило мне не только азарт, но и вдохновение, которое теперь сопровождает меня каждый раз, когда я захожу на платформу. Теперь я не только отдыхаю здесь, но и получаю возможность испытать новые игры, новые истории, где каждая победа дарит уникальные эмоции. Если и вы хотите получить положительные впечатления от современной игровой платформы, не теряйте времени. Ваше приключение ждет вас именно сейчас https://bonus-champion.icu .
Найдите новые эмоции в мире казино в моменте
Найдите все грани победы на площадке развлечений казино сейчас
Найдите ясность азарта на сайте казино сейчас
Узнайте о все грани победы на сайте казино в моменте
Откройте путь к успеху на площадке развлечений казино сегодня
3d56_e1
Your comment is awaiting moderation.
Эвакуатор в Санкт-Петербурге: срочная помощь в всякое время
Машинные неприятности возникают внезапно. Транспорт не хочет заводиться студёным утром, колесо пробито на автомобильной дороге, а может быть, произошла авария. В таких случаях автомобилисты Северной столицы всё чаще обращаются к профессиональным организациям эвакуации.
Когда нужен эвакуатор
Оснований для вызова профильного транспорта много. Значительная поломка двигателя или трансмиссии превращает автономное езду неосуществимым. Дорожно-транспортное происшествие нередко оставляет автомобиль в виде, неподходящем для езды. Истощённый аккумулятор в удалённом районе города — тоже основание пригласить помощь стоимость эвакуатора спб
Ряд водители применяют услугами эвакуации при получении машины с пробегом, когда нет уверенности в технической годности. Иные доставляют таким методом ценные автомобили на длительные расстояния, избегая ненужного пробега.
Характерные черты работы в Питере
Территориальные факторы Санкт-Петербурга порождают дополнительные препятствия. Разводные мосты сдерживают движение в ночное время навигации. Тесные улицы древнего центра предполагают от операторов эвакуаторов специального мастерства. Скопления на КАД и главных дорогах заставляют диспетчеров тщательно планировать маршруты.
Погодные условия добавляют свои изменения. Снеговые заносы зимой, ранние паводки, летние ливни — всё это воздействует на оперативность прибытия техники. Опытные организации принимают во внимание эти аспекты и держат несколько экипажей в отдельных районах города.
Что предлагают компании эвакуации
Актуальные компании обладают различными типами техники. Манипуляторы управляются с специфическими обстоятельствами. Платформы годятся для перевозки престижных автомобилей с малым дорожным зазором. Половинная погрузка выручает при повреждении только передней или задней оси.
Непрерывный режим работы предоставляет помощь в каждый момент. Координационная служба получает заявки по телефону и через мобильные приложения. Квалифицированные операторы скоро определяют координаты клиента и высылают ближний незанятый экипаж.
Тариф и сроки
Цена услуги складывается из ряда составляющих. Начальный тариф включает прибытие техники и первые несколько километров пути. Добавочное расстояние оплачивается дополнительно. Трудность погрузки, габариты транспортного средства, период суток — всё сказывается на итоговую сумму.
Обычное время подачи эвакуатора в черте города достигает 30—40 минут. В удалённых районах и на дорогах этот показатель может подняться до часа. Срочные выезды обходятся дороже, но гарантируют прибытие в течение 20 минут.
Как найти надёжную организацию
Имидж службы проверяется отзывами настоящих клиентов. Наличие собственного автопарка указывает о устойчивости бизнеса. Страхование обязательств защищает права заказчика при дефекте автомобиля во время транспортировки.
Ясное ценообразование без скрытых доплат — признак честной работы. Квалифицированные водители с значительным стажем обеспечивают защищённую перевозку. Опция электронного расчёта прибавляет лёгкости.
Жизнь в городе требует готовности к внезапным ситуациям. Номер испытанной службы эвакуации в контактах — это безопасность и уверенность на дорогах Питера.
Your comment is awaiting moderation.
1.
Узнайте эффективные методы увеличения конверсии сайта. Практические советы, которые помогают улучшить конверсию сайта и превратить посетителей в клиентов. https://secondstreet.ru/profile/Penguinteam/
2.
Хотите повысить конверсию на сайте без лишних затрат? Мы собрали лучшие стратегии и рабочие инструменты для стабильного роста продаж. https://sitebs.ru/blogs/120392.html
3.
Увеличить конверсию сайта реально. Разбираем ошибки, показываем решения и делимся проверенными подходами для бизнеса любого масштаба. https://inkbunny.net/Penguinteam
4.
Конверсия сайта — ключ к прибыли. Узнайте, какие способы её повышения работают в 2025 году и как внедрить их быстро. https://able2know.org/user/penguinteam/
5.
Низкие заявки и продажи? Пора задуматься о росте конверсии сайта. Пошаговые рекомендации и понятные примеры — без воды. https://wakelet.com/@penguinteamua
Your comment is awaiting moderation.
Хочу поделиться опытом использования такого решения, как бордюр садовый. Долго искал способ аккуратно отделить клумбы от газона и дорожек, чтобы участок выглядел ухоженно, а растения не «расползались» в разные стороны. В итоге остановился именно на садовом бордюре — и ни разу не пожалел.
Садовый бордюр удобен тем, что его легко установить своими руками, без сложных инструментов и лишних затрат. Он помогает сохранить форму клумб, защищает дорожки от земли и придаёт участку более завершённый вид. Плюс сейчас есть варианты из пластика, бетона и резины — можно подобрать под любой стиль сада. дорожный
Your comment is awaiting moderation.
1.
Узнайте эффективные методы увеличения конверсии сайта. Практические советы, которые помогают улучшить конверсию сайта и превратить посетителей в клиентов. https://rant.li/inkwave/kak-uluchshit-konversiiu-saita-bez-redizaina-prakticheskii-podkhod-dlia
2.
Хотите повысить конверсию на сайте без лишних затрат? Мы собрали лучшие стратегии и рабочие инструменты для стабильного роста продаж. https://www.myminifactory.com/users/penguinteamua
3.
Увеличить конверсию сайта реально. Разбираем ошибки, показываем решения и делимся проверенными подходами для бизнеса любого масштаба. https://yoo.rs/-1768756218?Ysid=285574
4.
Конверсия сайта — ключ к прибыли. Узнайте, какие способы её повышения работают в 2025 году и как внедрить их быстро. https://wakelet.com/@penguinteamua
5.
Низкие заявки и продажи? Пора задуматься о росте конверсии сайта. Пошаговые рекомендации и понятные примеры — без воды. https://www.myminifactory.com/users/penguinteamua
Your comment is awaiting moderation.
6.
Мы расскажем, как улучшить конверсию сайта с помощью UX, контента и аналитики. Только практические методы и реальные кейсы. https://rant.li/inkwave/kak-uluchshit-konversiiu-saita-bez-redizaina-prakticheskii-podkhod-dlia
7.
Конверсия сайта и способы её повышения — в одном месте. Чётко, структурировано и ориентировано на результат. http://povary.ru/article.php?id=17498
8.
Каждый процент важен. Узнайте, как добиться роста конверсии сайта и увеличить эффективность рекламы без увеличения бюджета. https://able2know.org/user/penguinteam/
9.
Ищете способы повысить конверсию на сайте? Мы собрали лучшие идеи, тесты и приёмы для интернет-магазинов и сервисов. https://truckymods.io/user/448682
10.
Посетители есть, а продаж нет? Решение — увеличение конверсии сайта. Изучайте проверенные методы и внедряйте их уже сегодня. https://www.myminifactory.com/users/penguinteamua
Your comment is awaiting moderation.
Need an AI generator? generate nude images with ai The best nude generator with precision and control. Enter a description and get results. Create nude images in just a few clicks.
Your comment is awaiting moderation.
Благодаря тому, что ботулинотерапия является широко распространенным и эффективным методом в косметологии, многие люди могут добиться значительных улучшений в своем внешнем виде без необходимости хирургического вмешательства.
это эффективный способ омолодить кожу и получить более свежий вид. Она включает в себя введение небольшого количества ботулинического токсина в определенные области лица, что помогает снять мышечное напряжение и придать коже более гладкий вид . Эта процедура получила широкое распространение в последние годы благодаря своей эффективности и безопасности .
Ботулинотерапия используется для коррекции формы бровей и придания лицу более молодого и свежего вида . Она обычно проводится в условиях клиники или кабинета врача, под местной анестезией . После процедуры результаты ботулинотерапии становятся видны в течение нескольких дней после процедуры.
**Раздел 2: Преимущества ботулинотерапии**
Ботулинотерапия предлагает ряд преимуществ, включая эффективность и безопасность . Она может быть использована в сочетании с другими косметическими процедурами для достижения более комплексного результата. Ботулинотерапия может быть выполнена в течение короткого времени, без необходимости длительного периода восстановления .
Ботулинотерапия применяется не только для косметических целей, но и для лечения различных медицинских состояний . Она также исследуется для потенциального использования в лечении других состояний, таких как спазмы и скованность мышц . Ботулинотерапия требует тщательного подбора пациентов и планирования процедуры .
**Раздел 3: Противопоказания и возможные осложнения**
Ботулинотерапия, как и любая медицинская процедура, имеет определенные противопоказания и возможные осложнения, которые необходимо учитывать . Противопоказания для ботулинотерапии могут включать аллергические реакции на компоненты ботулинического токсина .
Возможные осложнения ботулинотерапии могут включать временное онемение или слабость мышц . В редких случаях пациент должен быть тщательно проинформирован о возможных рисках и осложнениях перед процедурой. Ботулинотерапия должна быть выполнена только квалифицированными специалистами, имеющими опыт работы с ботулиническим токсином.
**Раздел 4: Заключение и перспективы**
Ботулинотерапия имеет ряд преимуществ, включая минимальное время восстановления и отсутствие необходимости хирургического вмешательства. Она используется во многих клиниках и салонах красоты для достижения желаемого результата .
Ботулинотерапия должна быть выполнена в соответствии с современными медицинскими стандартами и протоколами. Перспективы ботулинотерапии включают потенциальное использование в лечении других медицинских состояний, таких как спазмы и скованность мышц . Ботулинотерапия остается одним из наиболее популярных методов омоложения кожи и коррекции косметических проблем .
Your comment is awaiting moderation.
An initiative we launched with the goal to create a global self-exclusion system, which will allow vulnerable players to block their access to all online gambling opportunities. In the Apple Games app, you can find your next game across dozens of categories including action, adventure, racing, puzzles, and more. You can do any of the following in the Dynamic Island: The following data may be used to track you across apps and websites owned by other companies: WOW Slots: Online Casino Games Yes, the Air saw more tempered reception in pre-order demand than Pro models in some markets, but Apple’s own plans hinted at confidence. Production was set roughly three times higher than the iPhone 16 Plus. Feeding a crowd, fire up the grill. Using medium-high heat and heavy-duty foil produces evenly reheated pizza with a crisp bottom and stretchy cheese. Big surface, more slices, easy win.
https://sensisbuds.com/chicken-road-legit-what-players-should-know/
Reisman left NASA in 2011 to join Hawthorne’s SpaceX, the release said, where he served many different roles — most recently as the company’s director of space operations. In 2018, Reisman left SpaceX and joined USC as an astronautical engineering professor, though he still does advisory work for the company. ▷ 300 PEPE Telegram stickers list Science hardware was the focus on Monday as the Expedition 73 crew configured foam and material physics research gear and installed a space technology demonstration. Meanwhile, blood circulation studies and cargo operations rounded out the day aboard the International Space Station. NASA says it is hoping the studies can be the basis for future research initiatives. Signal or Scam? – Crypto News NASA explores the unknown in air and space, innovates for the benefit of humanity, and inspires the world through discovery.
Your comment is awaiting moderation.
When exploring video slots, you’ll encounter two types: demo slots and real slots. Demo slots are free to play without any risk. You don’t need to register at an online casino — simply choose a platform, select a game, and start playing online slots. When exploring video slots, you’ll encounter two types: demo slots and real slots. Demo slots are free to play without any risk. You don’t need to register at an online casino — simply choose a platform, select a game, and start playing online slots. Web Design by The Online Director Alright, let me tell you about my latest obsession: the More Magic Apple slot by 3 Oaks. Released in May 2023, this game totally drew me in with its enchanting theme. Picture this: I’m sitting on my couch, and suddenly, I’m on an adventure with Snow White and her crew, chasing after huge wins! The graphics are just gorgeous, and the bonuses? Super exciting. Whether I’m just having fun in the demo mode or going all in at an online casino, this game keeps me entertained. Honestly, the first spin had me hooked. Give it a go, you won’t regret it!
https://mytaxadvisor.co.in/aviator-game-autoplay-risks-what-singapore-players-should-know/
@Albertos Only one problem… For some reason when I publish it it will allow me to see the main menu but when I press space to advance to the Level 1 scene it says I need to login. When I try it gives me an Error 403 Sign in to add your own tags to this product. I’m reaching a point where my project needs some better organization, I’m starting to get noddly messes, circular references, and “oh no do I need to use sqlite?” Sign up Grade 1, 2, 3, 4, 5 Every time I try to install the game I get the following error at 97% complete. Last week, I published my second look at the StarDrive beta, getting a good look at one of the later builds and seeing how well the game played. This is a game that I and many others have been excited about for a long time, with a successful Kickstarter campaign and a lengthy open beta, this one has been on people’s radar for a while. Now that it’s out, does it live up to the hype? This series of articles that will constitute the game’s review will hope to answer that.
Your comment is awaiting moderation.
пицца рязань с доставкой пицца в рязани
Your comment is awaiting moderation.
куба пицца калуга телефон пицца куба московская ул 184а меню
Your comment is awaiting moderation.
Zahnprobleme? https://www.zahnarzte-montenegro.com Diagnostik, Kariesbehandlung, Implantate, Zahnaufhellung und Prophylaxe. Wir bieten Ihnen einen angenehmen Termin, sichere Materialien, moderne Technologie und kummern uns um die Gesundheit Ihres Lachelns.
Your comment is awaiting moderation.
Hello !!
I came across a 152 useful platform that I think you should visit.
This platform is packed with a lot of useful information that you might find helpful.
It has everything you could possibly need, so be sure to give it a visit!
https://underscoopfire.com/what-to-do-to-strengthen-the-psyche-8-habits-of-stress-resistant-people/
And remember not to neglect, folks, that a person constantly can in this particular publication locate solutions for your most confusing inquiries. We tried to present all of the information in the most extremely understandable manner.
Your comment is awaiting moderation.
1win az bonusları https://www.1win5762.help
Your comment is awaiting moderation.
Pendant les free spin, un multiplicateur de gains persistant grimpe au fil des réactions. Selon la configuration de votre session, il est possible d’augmenter ce multiplicateur, de regagner des tours et d’atteindre des séquences où chaque avalanche pèse lourd. Les fans de titres proches (ex. Gates of Olympus) retrouveront cette montée en puissance, mais avec la patte visuelle et sonore Play’n GO. C’est à ces jeux qu’on voit bien que Big wins est un crypto-casino. En effet, ces casinos viennent toujours avec une sélection de jeux uniques. Même si Big wins casino n’est pas le premier à offrir les jeux de crash, vous en trouverez de très rares sur son site. Gates of Olympus offre une expérience palpitante avec des gains potentiels élevés et un thème riche en mythologie grecque. Malgré sa haute volatilité, les multiplicateurs généreux et les fonctionnalités bonus en font une machine à sous particulièrement gratifiante pour ceux qui cherchent des frissons et des récompenses spectaculaires.
https://nikou.gr/review-du-jeu-de-casino-amunra-pour-les-joueurs-francais/
Un RTP plus élevé signifie un meilleur retour potentiel pour le joueur. Avec une volatilité élevée, Sugar Rush peut offrir des gains allant jusqu’à 5 000 fois la mise. Grâce à ces ajouts, Sugar Rush 1000 rend le jeu encore plus amusant et plus excitant tout en gardant l’esprit de la version originale. Sugar Rush 1000 introduit une fonctionnalité captivante appelée Multiplier Spots. Chaque fois qu’un symbole participe à une combinaison gagnante et explose, il laisse derrière lui une marque sur la grille. Si un symbole gagne à nouveau sur ce même emplacement, un multiplicateur est alors ajouté à ce spot. Les jeux de casino en ligne utilisent un logiciel spécial qui émule les jeux de casino traditionnels tels que les machines à sous, le blackjack et la roulette. Les résultats sont déterminés par un générateur de nombres aléatoires (Random Number Generator, RNG) afin de garantir l’équité.
Your comment is awaiting moderation.
Custom Google & Meta Ads Strategy – Built for Conversions
Come to a stop guessing. Start scaling.
We shoot high-traffic Google & Facebook ad campaigns that carry real buyers — not scarcely clicks.
If your put on the market converts, we’ll surplus it with targeted traffic.
If it doesn’t — we’ll help you ovariectomize it in preference to spending big.
? Proven in tough verticals: iGaming (licensed), nutra, fintech, SaaS, e-com
? Exhaustive setup: tracking, creatives, audiences, dictate — done suitable
? Built to predisposed to stage reviews (no cloaking, no phoney pages)
? Always tweaks + clear carrying out reports
?? Starting from $800 exam budget
?? Event campaigns in EU, CA, AU, LATAM, ZA & more
?? Missive us — if you’ve got a solid proffer, we’ve got the traffic.
No pastime projects. No strategy violations. Lately results.
? Serious about growth? Let’s go
Your comment is awaiting moderation.
Hire a Pro to Launch Your Facebook & Google Ads
Permit to’s grow your role together — with smart, scalable ads on Google & Facebook.
We don’t at best “get cracking ads.” We increase profit-focused campaigns that introduce genuine customers, again and again.
Whether you’re launching a recent output or scaling an existing forth, we’ve got you covered:
• E-commerce & digital products
• Persuade contemporaries (calls, forms, demos)
• Licensed gaming & betting brands
• Nutra, economics, SaaS, and other performance-driven niches
? What you gather:
– Full competition setup (tracking, creatives, targeting)
– Policy-safe strategies that protect your ad accounts
– Continued optimization + tied Telex support
– Take reporting — no black boxes
?? Test budget starts at $800
?? Acting in Europe, North America, Australia, LATAM, Africa & more
?? Reach out today — pretend’s use your offering into a customer magnet.
As a remedy for serious issue owners ready to lower the in all honesty way.
? Fast launch. Real results. DM us
Your comment is awaiting moderation.
Почему пользователи выбирают площадку KRAKEN?
Маркетплейс KRAKEN заслужил доверие многочисленной аудитории благодаря сочетанию ключевых факторов.
Во-первых, это широкий и разнообразный ассортимент,
представленный сотнями продавцов.
Во-вторых, интуитивно понятный интерфейс KRAKEN, который упрощает навигацию, поиск товаров и
управление заказами даже для новых пользователей.
В-третьих, продуманная система безопасных транзакций, включающая механизмы разрешения
споров (диспутов) и возможность использования условного депонирования, что минимизирует риски для обеих сторон сделки.
На KRAKEN функциональность сочетается с
внимательным отношением к безопасности клиентов, что делает процесс покупок более предсказуемым, защищенным
и, как следствие, популярным среди пользователей, ценящих анонимность и надежность.
Your comment is awaiting moderation.
Meta & Google Ads for iGaming, Crypto, SaaS – Specialized
Tired of ads that burn money but bring zero clients?
We run high-volume Google & Facebook campaigns that actually fill your pipeline.
Whether you sell products, services, or digital offers — we’ll get you consistent, qualified traffic from the right audiences.
We’ve successfully scaled:
> E-commerce stores (ROAS-focused)
> Lead gen funnels (calls, forms, demos)
> Licensed iGaming & betting brands
> Nutra, finance, SaaS, and more
? Done-for-you setup — no tech headaches
? Compliant strategies that keep accounts safe
? Creatives, tracking, A/B tests — all included
? Fast launch + real-time support via Telegram
Minimum test budget: $800
Active in 30+ countries (EU, CA, AU, LATAM, ZA, etc.)
Hire a Pro to Launch Your Facebook & Google Ads
?? DM now — let’s turn your offer into a client-generating machine.
Serious projects only. No black-hat. No shortcuts.
?? Start your test campaign today
Your comment is awaiting moderation.
Escrow Available – Trusted Facebook & Google Ads Provider
Google + Meta Ads. Genuine traffic. Palpable clients. No fluff.
We deposit up and enlarge performance-driven ad campaigns on offers that convert.
If your funnel works — we’ll sally volume. If it’s wobbly — we’ll help finalize a furnish it first.
? Verticals:
– Licensed iGaming (EU/CA/AU)
– Nutra & well-being
– Fintech / crypto-adjacent
– E-com & SaaS
? What’s included:
– Utmost tracking (GA4 + Meta CAPI + Pixel)
– High-converting creatives & copy
– Audience tactics + bid optimization
– Routine monitoring + Telegram updates
? Policy-compliant. No cloaking. No fake landing pages.
? Min. test budget: $800
? GEOs: 30+ countries (EU, CA, AU, LATAM, ZA, и так далее)
?? DM to start. Bring your tender — we’ll be the source the traffic.
Serious only.
?? DM now — let’s launch your campaign
Your comment is awaiting moderation.
Facebook & Google Ads Done Right – No Traffic Objective
Permit to’s attain maturity your role together — with canny, scalable ads on Гугл & Facebook.
We don’t just “run ads.” We shape profit-focused campaigns that bring genuine customers, again and again.
Whether you’re launching a new product or scaling an existing offer, we’ve got you covered:
• E-commerce & digital products
• Persuade generation (calls, forms, demos)
• Licensed gaming & betting brands
• Nutra, economics, SaaS, and other performance-driven niches
? What you deck out:
– Unshortened campaign setup (tracking, creatives, targeting)
– Policy-safe strategies that screen your ad accounts
– Relentless optimization + solidly Trade mark telemessage support
– Bright reporting — no black boxes
?? Test budget starts at $800
?? Potent in Europe, North America, Australia, LATAM, Africa & more
?? Reach at liberty today — pretend’s use your offering into a shopper magnet.
As a remedy for serious subject owners convenient money to lower the in all honesty way.
?? DM now — let’s launch your campaign
Your comment is awaiting moderation.
Guaranteed Quality – Facebook & Google Ads Configuration
Need more customers? We’ll launch a high-volume ad flow on Google & Facebook — fast.
If you want real leads, calls, or sales, we set up ads that actually work.
We handle all kinds of businesses — e-commerce, SaaS, licensed iGaming, nutra, finance, and other high-potential niches.
? Full setup: creatives, tracking, targeting — done for you
? Scalable campaigns that stay compliant (no cloaking, no bans)
? Telegram support + transparent reporting
? Global GEOs: EU, CA, AU, LATAM, ZA, and more
Minimum test budget: $800
?? DM now — let’s get your first campaign live this week!
For serious advertisers ready to scale.
?? Book your ad setup slot
Your comment is awaiting moderation.
Facebook Pixel + Google Tag Setup Included
Need more customers? We’ll launch a high-volume ad flow on Google & Facebook — fast.
If you want real leads, calls, or sales, we set up ads that actually work.
We handle all kinds of businesses — e-commerce, SaaS, licensed iGaming, nutra, finance, and other high-potential niches.
? Full setup: creatives, tracking, targeting — done for you
? Scalable campaigns that stay compliant (no cloaking, no bans)
? Telegram support + transparent reporting
? Global GEOs: EU, CA, AU, LATAM, ZA, and more
Minimum test budget: $800
?? DM now — let’s get your first campaign live this week!
For serious advertisers ready to scale.
?? Running in your GEO? Let’s check
Your comment is awaiting moderation.
Stop Wasting Ad Spend – Get Properly Configured Ads
No fluff. No feign promises. Rightful legitimate see trade, earnest leads, and real sales — from hour one.
We specialize in scaling businesses in competitive or complex niches:
• E-commerce & dropshipping
• SaaS & software
• Licensed iGaming (EU/CA/AU)
• Nutra, vigour, funds, and more
? End-to-end setup — you converge on your trade, we handle the ads
? Thorough tracking (Meta CAPI, GA4, Pixel) + high-converting creatives
? Built to last — no policy violations, no swift bans
? Continuously optimization + high-speed Radiogram support
Starting budget: $800+
Serving clients worldwide — Europe, Americas, Asia, Africa
?? Note us today — let’s shape your make available into a character magnet.
In the service of founders and marketers who covet lump, not guesswork.
?? Veer conveyance into profit — start here
Your comment is awaiting moderation.
эфир смотреть онлайн смотреть фильмы про тюрьму
Your comment is awaiting moderation.
задвижка 30с41нж 100 16 https://zadvizhka-30s41nzh.ru
Your comment is awaiting moderation.
сервис рассылки автоматических сервис для email рассылок российский
Your comment is awaiting moderation.
IQOS ILUMA https://terea-iluma24.org и стики TEREA — покупка в Москве без риска. Гарантия подлинности, большой выбор, выгодные условия, доставка по городу и помощь в подборе устройства и стиков.
Your comment is awaiting moderation.
Продажа IQOS ILUMA https://ekb-terea.org и стиков TEREA в СПб. Только оригинальные устройства и стики, широкий ассортимент, оперативная доставка, самовывоз и поддержка клиентов на всех этапах покупки.
Your comment is awaiting moderation.
Купить IQOS ILUMA https://spb-terea.store и стики TEREA в Санкт-Петербурге с гарантией оригинальности. В наличии все модели ILUMA, широкий выбор вкусов TEREA, быстрая доставка по СПб, удобная оплата и консультации специалистов.
Your comment is awaiting moderation.
Hello pals!
I came across a 152 awesome website that I think you should explore.
This tool is packed with a lot of useful information that you might find insightful.
It has everything you could possibly need, so be sure to give it a visit!
https://prodipsy.com/tips-to-opt-for-the-best-wordpress-hosting/
Additionally remember not to overlook, guys, that one at all times are able to inside this publication locate answers to the most the absolute confusing inquiries. Our team made an effort to explain the complete content using the most very easy-to-grasp manner.
Your comment is awaiting moderation.
Do you love gambling? j win 7 Online is safe and convenient. We offer a wide selection of games, modern slots, a live casino, fast deposits and withdrawals, clear terms, and a stable website.
Your comment is awaiting moderation.
Playing at the casino? jwin7 casino Play online for real money. We offer a wide selection of slots, live dealers, fast payments, easy login, and exciting offers for new and returning players.
Your comment is awaiting moderation.
Looking for a casino? 8mbets bd Slots, table games, and live casino all in one place. Quick login, convenient registration, modern providers, stable payouts, and comfortable player conditions.
Your comment is awaiting moderation.
Final ank is a most-visited & preferred website to try the luck and play Kalyan final, Milan day final, Rajdhani day final, kalyan chart Rajdhani night final, main ratan final, Matka final, and the complete Kalyan Final Ank game. Among these all, Kalyan Chart has attracted the bookie and players as there remain high chances of winning the chance. Ans: Satta Matka is a traditional number-based game in which players choose digits between 00 and 99. If their selected number matches the declared result, they win according to the payout rules of the Matka market they played in. MAIN BAZAR MORNING Kalyan open 3:45 close 5:45 If you’re thinking about trying your luck in Satta Makka on-line, ensure you are aware about the risk. Always play responsibly, and recollect the game as amusement rather than methods to make money. With the proper mentality, speculative Matka can offer an interesting and adrenaline -stuffed experience.
https://pad.itiv.kit.edu/s/JoPv_Wvvw
Kalyan Matka is the most followed Matka game. It opens and closes daily. Thousands search Kalyan Satta Matka result daily. Kalyan Matka games include classic and modern play. Players look for कल्याण मटका, Kalyan Satka Matka, and Satta Matka Kalyan online. Everyone (above 18+) can get Satta Batta games. Satta Batta is one of the simplest and easiest online games. Satta Batta will make you happy and also provide you a chance to win money. Join Satta Matta Matka and win your money today! There are three types of markets in Madhur Matka. First comes Madhur Morning whose time open is 11:30am Close is 12:30pm. The second Madhur Day comes whose time to open is 01:30PM and close is 02:30PM. Third Madhur Night comes whose time open is 08:30PM close is 10:30PM. With results, charts, data, blogs, live chat options, and guessings we all offer the best application to play satta matka. Starting with a minimum deposit of only Rs. 300 – players can start playing this game. Our app offers satta matka game, poker, and online casino in one single application. We provide complete safety and deliver accurate fastest satta matka results. Our live chat option is always available to solve all the queries and guide you through the entire process. Our ability of resilience and always accepting an update or change has made us one of the top online matka website.
Your comment is awaiting moderation.
Plug-and-Play iGaming Platform – Buy GramBit Now
Discharge your online casino at once and risk-free high-priced unfolding!
GramBit is not a pattern, but a turnkey matter solution.
What you get:
?? Effectual admin panel (CMS) during well-stacked control.
?? Library 2500+ games from top providers.
?? Integrated payment locks.
?? Adaptive, up to the minute design.
?? Proven insurance and stability.
?? Filled technical support.
Launch your vocation in a occasional weeks! Better for the treatment of entrepreneurs and investors in iGaming.
Suppleness:
Purchasing with code transfer.
Bloodless Label licensing.
For significant requests, I inclination purvey demo access to admin and solution all questions.
Don’t extirpate term on development. Woolly on marketing and make development!
Website: Launch your online casino today!
P.S. Consider partnership options to found eye your brand.
Your comment is awaiting moderation.
GramBit Casino Software with KYC/AML & Fraud Protection
Launch your online casino at once and risk-free high-priced advancement!
GramBit is not a script, but a turnkey business solution.
What you get:
?? Authoritative admin panel (CMS) for well-stacked control.
?? Library 2500+ games from surpass providers.
?? Integrated payment locks.
?? Adaptive, modern design.
?? Proven care and stability.
?? Directly technological support.
Originate your vocation in a two weeks! Perfect for entrepreneurs and investors in iGaming.
Flexibility:
Exchange with code transfer.
Pale-complexioned Label licensing.
In return straight-faced requests, I inclination provide demo access to admin and counter-statement all questions.
Don’t extravagance in the nick of time b soon on development. Heart on marketing and identify development!
Website: Proven platform. Fast launch. High margins.
P.S. Over partnership options to get going under your brand.
Your comment is awaiting moderation.
Buy GramBit Casino Script with Admin Panel & Payment Gateways
Launch your online casino hastily and risk-free high-priced development!
GramBit is not a screenplay, but a turnkey subject solution.
What you reach:
?? Authoritative admin panel (CMS) in the service of well-stacked control.
?? Library 2500+ games from cover providers.
?? Integrated payment locks.
?? Adaptive, novel design.
?? Proven security and stability.
?? Unshaded complex support.
Dinghy your subject in a two weeks! Perfect for the treatment of entrepreneurs and investors in iGaming.
Flexibility:
Sale with conventions transfer.
White Label licensing.
On serious requests, I will purvey demo access to admin and answer all questions.
Don’t debilitate time on development. Heart on marketing and manufacturer evolution!
Website: Everything you need — from license to support.
P.S. Reckon with partnership options to found under your brand.
Your comment is awaiting moderation.
Low-Cost Entry to iGaming – Buy GramBit Casino Platform
Launch your online casino hastily and risk-free expensive incident!
GramBit is not a pattern, but a turnkey matter solution.
What you move:
?? Effectual admin panel (CMS) in the service of full control.
?? Library 2500+ games from surpass providers.
?? Integrated payment locks.
?? Adaptive, up to the minute design.
?? Proven security and stability.
?? Filled complex support.
Dinghy your subject in a two weeks! Perfect for the treatment of entrepreneurs and investors in iGaming.
Adjustability:
Sale with unwritten law’ transfer.
Bloodless Brand licensing.
For dangerous requests, I leave plan for demo access to admin and counter-statement all questions.
Don’t debilitate pass‚ on development. Heart on marketing and identify unfolding!
Website: Don’t miss your chance — buy a turnkey casino!
P.S. Consider partnership options to get going directed your brand.
Your comment is awaiting moderation.
Launch in 72 Hours – Buy GramBit Casino Script Today
Send your online casino at once and risk-free up-market unfolding!
GramBit is not a script, but a turnkey matter solution.
What you move:
?? Authoritative admin panel (CMS) after full control.
?? Library 2500+ games from cover providers.
?? Integrated payment locks.
?? Adaptive, brand-new design.
?? Proven insurance and stability.
?? Unshaded technological support.
Initiate your subject in a handful weeks! Perfect with a view entrepreneurs and investors in iGaming.
Suppleness:
Purchasing with jus canonicum ‘canon law’ transfer.
Bloodless Portray licensing.
In return dangerous requests, I intent purvey demo access to admin and answer all questions.
Don’t extirpate pass‚ on development. Fuzzy on marketing and identify unfolding!
Website: Don’t miss your chance — buy a turnkey casino!
P.S. Over partnership options to found under your brand.
Your comment is awaiting moderation.
GramBit Online Casino Script – Compliant & Market-Ready
Set afloat your online casino at once and risk-free expensive advancement!
GramBit is not a calligraphy, but a turnkey business solution.
What you reach:
?? Authoritative admin panel (CMS) for detailed control.
?? Library 2500+ games from cover providers.
?? Integrated payment locks.
?? Adaptive, novel design.
?? Proven insurance and stability.
?? Directly technological support.
Launch your business in a occasional weeks! Entire pro entrepreneurs and investors in iGaming.
Adjustability:
Trading with unwritten law’ transfer.
Bloodless Categorize licensing.
In return straight-faced requests, I will provide demo access to admin and fill all questions.
Don’t debilitate in the nick of time b soon on development. Heart on marketing and brand evolvement!
Website: Invest in iGaming — the market grows every day.
P.S. Consider partnership options to launch under your brand.
Your comment is awaiting moderation.
GramBit Casino Software with KYC/AML & Fraud Protection
Send your online casino hastily and risk-free high-priced development!
GramBit is not a screenplay, but a turnkey topic solution.
What you move:
?? Authoritative admin panel (CMS) after full control.
?? Library 2500+ games from cover providers.
?? Integrated payment locks.
?? Adaptive, brand-new design.
?? Proven care and stability.
?? Full technological support.
Initiate your vocation in a occasional weeks! Perfect for entrepreneurs and investors in iGaming.
Suppleness:
Sale with code transfer.
Bloodless Label licensing.
On straight-faced requests, I leave stock up demo access to admin and solution all questions.
Don’t debilitate in the nick of time b soon on development. Focus on marketing and brand development!
Website: Launch your online casino today!
P.S. Over partnership options to launch under your brand.
Your comment is awaiting moderation.
Buy GramBit Casino Script with Admin Panel & Payment Gateways
Send your online casino at once and risk-free costly unfolding!
GramBit is not a calligraphy, but a turnkey subject solution.
What you reach:
?? Authoritative admin panel (CMS) during well-stacked control.
?? Library 2500+ games from surpass providers.
?? Integrated payment locks.
?? Adaptive, novel design.
?? Proven insurance and stability.
?? Unshaded specialized support.
Dinghy your house in a occasional weeks! Better for the treatment of entrepreneurs and investors in iGaming.
Flexibility:
Sale with code transfer.
White Brand licensing.
On serious requests, I leave provide demo access to admin and fill all questions.
Don’t debilitate term on development. Fuzzy on marketing and identify evolvement!
Website: Don’t miss your chance — buy a turnkey casino!
P.S. Mark partnership options to dispatch eye your brand.
Your comment is awaiting moderation.
Our experienced speculative Satka Matka team welcomes you to find the best of Satta Matka games online. At Sattamatkano1.Me we offer a safe and exciting platform to play and win. Don’t miss the opportunity to become the next power Matka King. Check out the results and bet the Matka results from your Madhur day, and now take your shot on Big Win! Best Weekly Satta Matka ANK For Kalyan,Time Bazar, Rajdhani Day, Milan Day, Main Bazar, Sridevi markets Best Weekly Satta Matka JODI For Kalyan,Time Bazar, Rajdhani Day, Milan Day, Main Bazar, Sridevi markets All Satta Matka Market Strong OTC Trick on our website! satta matka – satta matta matka | matka result | satta batta | kalyan panel chart | satta matta matka 143 | matka guessing | dp boss matka | Best Weekly Satta Matka ANK For Kalyan,Time Bazar, Rajdhani Day, Milan Day, Main Bazar, Sridevi markets
https://hedgedoc.et.aksw.org/s/Svmk2-cXc
Satamatka com is one of the most trusted and oldest platforms in the madhur satta matka, offering fast and accurate results for all major markets including madhur day chart, dpboss result, satka matka com, and satta matka manipur. With its user-friendly interface, the website provides real-time updates, live results, detailed charts, and expert guessing to help users make informed decisions. It has become a go-to destination for players seeking reliability and speed in the ever-changing Matka world. It’s Time to Earn Quick Money and Secure Big wins with Satta Matka Games like, 220 Patti, Satta 220, Balaji 220, 220 Patti Kalyan On DPBoss, you will be able to explore the key benefits that make it the primary option for gambling enthusiasts all over the world. sattamatkalivee, one of the trusted and leading site where you can play satta matka and fast kalyan matka results. This online betting game is very popular in India but now its spread to all over the world.Matka markets grow by day and are very popular in India as well as worldwide.
Your comment is awaiting moderation.
888Starz has an app for Android and iOS. It is easy to download and works on most phones. The app has the same options as the website. You can bet on cricket live, claim bonuses and use safe payment systems. Many players in India say the app is fast and stable. It is good for people who like to bet while they travel. You can place bets, check results and cash out money and time with just a few taps. For many users, the app makes cricket betting even more simple and fun. This means putting together a number of outcomes to happen within a specific game and cheering each one on. The cricket bet builder tips are designed to secure a return on investment and also provide some entertainment along the way. We will then show you the best odds on your cricket bets by searching the betting odds of the best betting sites.
https://fotopani.rs/56/just-casino-review-the-ultimate-online-experience-for-nz-players/
At Mama567, our satta matka live charts refresh automatically when official results are declared. Users can check daily open, close, and jodi numbers without delay. Whether you follow Kalyan Chart, Sridevi Chart, or Milan Day Chart, you’ll find the latest data directly under the charts section. sattamatkadpboss.co Single Pana is always in X format and all three numbers of the Pana are unique. Explore Kalyan Panel Chart, Madhur Chart, Sridevi Matka Chart, Rajdhani Day Chart, and Milan Day Chart daily, all on one trusted site Mama567. Satta Matka Market is India’s leading website providing the quickest sattamatka outcome, experienced in Satta Matka game. Our services include free Satta Matka Trick and Tips for Kalyan Matka and Disawar Satta King, as well as satta matka graphs, online play, tips and more. Our team of experts strive to help you recoup your losses quickly through our proposals such as Free Satta Matka Tips and Kalyan Bazar Tips. We are known as India’s best Matka DpBoss portal site, here to deliver updates on all sorts of Satta Market like Kalyan Bazar, Milan, Rajdhani, Time Bazaar, Main and the most current charts. Stay tuned with us for more live updates on the Satta market!
Your comment is awaiting moderation.
DPBoss covers the full Matka Bazar. This includes Satka Matka, Worli Matka, Milan Matka, and Mumbai Matka. Whether it’s Satt Matka Satta or Satta 143, DPBoss tracks all records and charts with exact data. Kalyan Matka is the most followed Matka game. It opens and closes daily. Thousands search Kalyan Satta Matka result daily. Kalyan Matka games include classic and modern play. Players look for कल्याण मटका, Kalyan Satka Matka, and Satta Matka Kalyan online. DPBoss covers the full Matka Bazar. This includes Satka Matka, Worli Matka, Milan Matka, and Mumbai Matka. Whether it’s Satt Matka Satta or Satta 143, DPBoss tracks all records and charts with exact data. DPBoss covers the full Matka Bazar. This includes Satka Matka, Worli Matka, Milan Matka, and Mumbai Matka. Whether it’s Satt Matka Satta or Satta 143, DPBoss tracks all records and charts with exact data.
https://md.nowum.fh-aachen.de/s/4-QRN22ZZ
Slots are the most versatile and appealing online casino games. All real money online casinos in Bangladesh offer these games in massive numbers. Slot games are easy to play, fun, and can offer massive winnings. If you want to win as much as possible, focus on progressive jackpots. These real money games offer jackpots worth millions. If you want to relax, play fruit machines or other video slots. We also have innovative games that come with a user-friendly interface, and cool features and guarantee an enjoyable gaming experience 24 7. Play popular casino games or your favorite casino games right now at 8MBets. Essentially all gambling In Bangladesh takes place online due to offline betting being banned by the government. The increase in internet access and online banking combined with an increase in acceptance of gambling has led to a rapid boost in online betting in Bangladesh. There are almost 40 million Bangladeshi online bettors and this number is expected to rise as smartphones are now the norm and conservative anti-gambling sentiments decline.
Your comment is awaiting moderation.
1.
Шукаєш надійний інтернет-магазин техніки? Тут зібрані перевірені гаджети та електроніка в Україні з актуальними цінами та оглядами. https://www.bark.com/en/gb/company/tvmircomua/oz2YY9/
2.
Усе про інтернет-магазини гаджетів в одному місці. Порівнюй, обирай і знаходь найкращий магазин електроніки в Україні. https://www.slideserve.com/tvmir
3.
Від смартфонів до ноутбуків — знайди перевірений інтернет-магазин комп’ютерної техніки, електроніки та гаджетів швидко й зручно. https://www.bitsdujour.com/profiles/fafpKT
4.
Не знаєш, де купити техніку вигідно? Тут ти знайдеш огляди та добірки кращих магазинів електроніки в Україні. https://wakelet.com/@tvmircomua
5.
Твій гід у світі технологій: інтернет-магазини техніки та гаджетів, актуальні пропозиції та корисна інформація. https://artistecard.com/tvmircomua
Your comment is awaiting moderation.
6.
Обирай техніку без ризику. Дізнайся все про надійні інтернет-магазини електроніки в Україні в одному зручному сервісі. https://doodleordie.com/profile/tvmircomua
7.
Хочеш купити гаджет і не помилитись? Ми зібрали інформацію про топові інтернет-магазини гаджетів та комп’ютерної техніки. https://coub.com/tvmircomua
8.
Електроніка, гаджети, комп’ютери — знайди свій магазин електроніки з перевіреною репутацією та вигідними умовами. https://coub.com/tvmircomua
9.
Зручний пошук по інтернет-магазинах техніки в Україні. Порівнюй пропозиції та обирай найкраще. https://www.bitsdujour.com/profiles/fafpKT
10.
Усе, що потрібно знати перед покупкою: інтернет-магазини електроніки та гаджетів, огляди, рейтинги й поради. https://gravatar.com/tvmircomua
Your comment is awaiting moderation.
Добрый день! После включения, проходит юстировка, при попытке произвести измереня ип2 на измеряемый объект показания не выводятся на экран, не происходит измерений?что может быть не исптавенпреобразователь?
Подключение к питанию автомобиля: НетТип питания: литиевые батарейки 3 https://www.ndt-club.com/news-100.htm
6VТемпература работы: -40°С до +50°СРабочее напряжение: 3 https://www.ndt-club.com/produkcija-293-otreznie-stanki.htm
6VДатчик движения: даВремя работы: Режим реального времени: до 2 днейРежим 1 раз в 1 час: до 3 месяцевРежим 1 раз в 2 часа: до 6 месяцевРежим 1 раз в день: до 3х летБесплатная настройка: Да
UT-301М – обновленная модель толщиномера UT-301, в новом эргономичном корпусе из ABS пластика https://www.ndt-club.com/product-483-indykcionnii-nagrevatel-easytherm-100-hq.htm
Толщиномер UT-301М предназначен для контроля стенок сосудов, труб, котлов и других изделий в диапазоне от 0,5 до 300мм, а также для измерения скорости УЗК колебаний https://www.ndt-club.com/news-81.htm
Следует обратить внимание, что для защиты от угона авто прибор постоянно предает информацию об объекте, и злоумышленникам не так легко обнаружить данное устройство https://www.ndt-club.com/product-782-miniaturnie-razdelno-sovmeshennie-preobrazovateli-serii-dtc.htm
Даже если это и произойдет то стать легкой добычей для на выводе из строя таких устройств при помощи специальных сканеров, не получится, т https://www.ndt-club.com/product-64-tkm-359s-tverdomer-dinamicheskii.htm
к https://www.ndt-club.com/product-721-sendast-p111-plast-pryamie-sovmeshennie-preobrazovateli-dlya-kontrolya-plastikov.htm
все данные передаются и хранятся на сервере, и вы всегда можете посмотреть историю передвижений автомобиля https://www.ndt-club.com/product-540-pmi-master-smart.htm
Your comment is awaiting moderation.
Kolkata FF Fatafat is a popular game played inside Kolkata city. The lottery game is based on guesses. If you guess the right numbers, you can win money. The Kolkata FF Fatafat game is managed by the Kolkata FF city authorities. You can play this game from Monday to Saturday, eight times in a day. However, on Sundays, you can play it four times. Worli Mumbai Day is one of the different types of online Satta Matka games that is played online on DPBoss Services. The Satta king game is not one specific game. It is a variety of games. It is a drawing-based lottery game. It is a popular game and is played in many places worldwide. The game’s rules and protocols are different in each city. For instance, Disawar has a different version of the Satta king, and the city of Peshawar is the Satta. The playing rules of Worli Mumbai Day are similar to those of other batting games in the Satta Matka group, However, it slightly differs from other Matka games in terms of opening and closing times.
https://afagukhor1976.raidersfanteamshop.com/website-here
Getting started with WINBD is easy! Just follow these simple steps: Live betting lets you place bets while a match is ongoing, allowing you to react to real-time game developments. Whether it’s adjusting bets based on performance shifts or capitalising on fluctuating odds, this feature adds an interactive and fast-paced element to sports betting, making it more exciting and potentially rewarding. Deposits land instantly and withdrawals clear in < 3 hours—no fees, no stress. Making a bet online is simple with 888sport. All you need to do is click ‘Sign up’ and open your online betting account. Betwinner is an international betting and online casino on the market in Bangladesh. This gaming platform offers sportsbooks, virtual gaming experiences, and a diverse selection of casinos, including slots, live dealer experiences, and jackpots.
Your comment is awaiting moderation.
В мире онлайн-шопинга ключевое значение имеет надёжность, и m3ga гарантирует отличные условия.
Платформа объединяет продавцов, предлагая разнообразие
товаров: от одежды до редких
аксессуаров. Мега проводит акции и скидки, делающие покупки более доступными.
Покупатели выбирают vtuf за безопасность
сделок и комфортный процесс покупок.
Именно Мега продолжает быть лидером на рынке онлайн-шопинга.
https://xn--mea-sb-j6a.com — мега ссылка тор
Your comment is awaiting moderation.
Greetings crypto heads! Discovered a very informative post on new trends in digital currencies.
It outlines the latest movements in Web3 and DeFi. Super helpful for crypto fans.
No matter if you’re into trading, this post will keep you in the loop.
Read now
Your comment is awaiting moderation.
Hey, everyone! Allow me to introduce myself as Admin Read:
Кракен предлагает широкий выбор товаров: от стильной одежды до уникальных коллекционных предметов. Интуитивный интерфейс и частые акции превращают покупки на ссылка на kra в удовольствие для всех. Защита покупателей на кракен как войти обеспечивает уверенность в каждой сделке. Кракен остаётся выбором миллионов пользователей по всему миру.
Your comment is awaiting moderation.
Yo crypto folks! Just wanted to share a solid article on Bitcoin, Ethereum, and market news.
It dives deep into the key updates in BTC, ETH, and altcoins. A must-see if you follow crypto.
Whether you’re a HODLer or day trader, this resource will give you an edge.
Read now
Your comment is awaiting moderation.
Аполло, Завод металлоконструкций Адрес: г https://mobelmetall.ru/blog
Самара, ул https://mobelmetall.ru/lazernaya-rezka-dubna
Физкультурная, д https://mobelmetall.ru/poroshkovaya-pokraska-dubna
143Д Тел.: +7 846 374-88-88 https://mobelmetall.ru/blog/poroshkovaya-pokraska-dubna
ООО Завод металлоконструкций «МАРКА СТАЛИ» – энергично развивающееся предприятие, основной деятельностью которого является изготовление металлоконструкций строительного, промышленного и технологическо https://mobelmetall.ru/gibka-metalla
Домокомплекты 73 ЛДСП 16 Оборудование 146 Профнастил (профлист) 68 Сайдинг 53 Сэндвич панели 80 https://mobelmetall.ru/policy
Мы предлагаем: – *Фасадные металлокассеты* – стильное и долговечное решение для облицовки зданий https://mobelmetall.ru/aboutus
– *Корзины для кондиционеров* – надежная защита и эстетичный внешний вид вашего оборудования https://mobelmetall.ru/lazernaya-rezka-dubna
– *Водосточные системы* – эффективное https://mobelmetall.ru/lazernaya-rezka-dubna
ПСП https://mobelmetall.ru/
342 Механический завод Адрес: г https://mobelmetall.ru/poroshkovaya-pokraska-dubna
Домодедово, ул https://mobelmetall.ru/aboutus
Промышленная, д https://mobelmetall.ru/blog
11 Тел.: +7 495 787-58-75,787-91-35 https://mobelmetall.ru/blog/poroshkovaya-pokraska-dubna
Your comment is awaiting moderation.
Hi all! My name is Admin Read:
Ищете идеальную платформу для любых покупок? Kraken предлагает вам бесконечное разнообразие товаров для каждого. От премиум-брендов до доступных вариантов — kraken darkmarket гарантирует высочайшие стандарты и богатый выбор. Наслаждайтесь молниеносной доставкой, удобным процессом оформления заказа и отличным обслуживанием клиентов. С зеркало кракен Prime вы получите особые привилегии, такие как специальные акции и потоковый контент. Откройте для себя превосходный опыт онлайн-шопинга вместе с Кракен!
Your comment is awaiting moderation.
Kann man den Gates of Olympus Slot kostenlos spielen? Der Animationsstil beeindruckt mit seiner Videospiel-Ästhetik und trägt viel zur Akzeptanz der Spieler bei gate of olympus slot demo; diese könnten das Gefühl haben, als stünden sie dem Jüngsten Gericht gegenüber. „Gates of Olympus“ entführt dich gekonnt in die majestätische Welt des antiken Griechenland, wo der mächtige Zeus über den Olymp herrscht. Was diesen Slot so besonders macht, ist nicht nur das griechische Thema, sondern auch das innovative Multiplikatorsystem. Es gibt vieles, das Freunde des Themas altes Griechenland an Gates of Olympus gefallen wird. Multiplikatoren, die sowohl im Grundspiel als auch während der Freispiele aktiv sind und bei Letzteren sogar noch addiert werden, können für stattliche Gewinne sorgen. So auch die Tatsache, dass Symbole auf jeder Position eine Gewinnkombination bilden können.
https://ayojudi88slot.com/mostbet-casino-ein-umfassender-review-fur-spieler-aus-der-schweiz/
Quel est de tours, pouvant aller de jeux en hauteur à fait favorable. Parce qu’helmut adore les jeux seront ravis de remporter de tours gratuits. Grâce à sous à mi-chemin des machines a un gain aux ordinateurs pourront jouer à la découverte de zeus se tient à faire apparaître, 5%. Ainsi, eux, et avec cette machine. C’est la plateforme en tant que joueur rtp minimum d’une certification dans la machine à blog casino en ligne. Comprendre vos gains jusqu’à x500 maximum de gates of olympus. Rejoignez le jeu. Rejoignez le tour bonus actuel du bouton avec la mise initiale. Cette vidéo: 15 free spin gagnant où sur diverses plateformes. Gates of Olympus ist ein Slot von Pragmatic Play, in dem es um antike Götterwelten geht. Der Olymp ist der legendäre Götterberg der griechischen Mythologie. In diesem Automatenspiel kannst du mit ein bisschen Glück tolle Gewinne abräumen. Die Auszahlungsquote ist hoch und als Hauptgewinn lockt der 5000-fache Einsatz. Wir stellen dir Gates of Olympus in diesem Review ausführlich vor und erklären dir alle Stärken und Schwächen.
Your comment is awaiting moderation.
Choose a trusted platform for your gaming sessions by heading to mosbeth, offering strong reliability and excellent playing conditions.
Mosbeth’s story continues to influence literature and culture today.
Your comment is awaiting moderation.
1.
Шукаєш надійний інтернет-магазин техніки? Тут зібрані перевірені гаджети та електроніка в Україні з актуальними цінами та оглядами. https://tuscl.net/member/870165
2.
Усе про інтернет-магазини гаджетів в одному місці. Порівнюй, обирай і знаходь найкращий магазин електроніки в Україні. https://archive.org/details/@tvmir_comua
3.
Від смартфонів до ноутбуків — знайди перевірений інтернет-магазин комп’ютерної техніки, електроніки та гаджетів швидко й зручно. https://vocal.media/authors/tvmir-comua
4.
Не знаєш, де купити техніку вигідно? Тут ти знайдеш огляди та добірки кращих магазинів електроніки в Україні. https://www.pinterest.com/tvmirc/_profile/
5.
Твій гід у світі технологій: інтернет-магазини техніки та гаджетів, актуальні пропозиції та корисна інформація. https://tuscl.net/member/870165
Your comment is awaiting moderation.
6.
Обирай техніку без ризику. Дізнайся все про надійні інтернет-магазини електроніки в Україні в одному зручному сервісі. https://tooter.in/tvmircomua
7.
Хочеш купити гаджет і не помилитись? Ми зібрали інформацію про топові інтернет-магазини гаджетів та комп’ютерної техніки. https://pinshape.com/users/8881299-tvmircomua
8.
Електроніка, гаджети, комп’ютери — знайди свій магазин електроніки з перевіреною репутацією та вигідними умовами. https://clearvoice.com/cv/tvmircomua
9.
Зручний пошук по інтернет-магазинах техніки в Україні. Порівнюй пропозиції та обирай найкраще. https://www.bark.com/en/gb/company/tvmircomua/oz2YY9/
10.
Усе, що потрібно знати перед покупкою: інтернет-магазини електроніки та гаджетів, огляди, рейтинги й поради. https://www.flickr.com/people/204122287@N08/
Your comment is awaiting moderation.
12 октября 2022 https://oookors.ru/product/iguana-05l-zh-b-12-sht-originalnyj/
Огромный выбор товаров; Исключительно свежие и качественные изделия https://oookors.ru/product/chitos-50-gr-upak-24-sht/
Правильная транспортировка с соблюдением температурного режима; Быстрая доставка по Москве и Московской области; Доступные цены; Удобный график работы; Комфортное обслуживание; Информативный сайт и актуальный прайс-лист https://oookors.ru/product/persil-pauer-kaps-vpsv-4v1-14-sht-r23/
29 сентября 2024 https://oookors.ru/product/vajs-berg-lajm-044-l-st-12-sht/
415 000 000 ?
В оптовом интернет-магазине Carabus можно заказать продукты со склада в Москве по привлекательной цене https://oookors.ru/product/blek-monstr-05l-zh-b-12-sht-pepilajn-punch/
Оперативная доставка по России https://oookors.ru/product/doktor-dizel-mango-i-krasnyj-apelsin-045-l-st-20-sht/
Постоянным клиентам мы предоставляем скидки и можем предложить персональные условия сотрудничества https://oookors.ru/product/mishka-kosolapyj-250-gr-upak-6-sht/
Для каждого заказчика у нас разработана индивидуальная система бонусов и удобный график доставки товаров https://oookors.ru/product/hoop-2l-6-sht-vishnya/
Для оформления заказа звоните по номеру +7 (495) 984-78-46 https://oookors.ru/product/alpen-gold-arahis-kukur-hlopya-85-gr-blok-21-sht/
Сотрудник колл-центра ответит на ваши вопросы относительно продукции и поможет определиться с выбором https://oookors.ru/product/hot-dog-zefir-blok-30-sht/
24 часа в сутки мы следим за новинками рынка и информируем вас https://oookors.ru/product/natahtari-1l-6-sht-limon/
Your comment is awaiting moderation.
DA PA MOZ) Topchik
https://ad.gunosy.com/pages/redirect?location=http%3A%2F%2Frekon36.ruµ_tracking_tag_id=1551067524-619&sad=60963&signature=1.e57eeb7a3f43854dc256cc4b0f607025c0b5d8c7&tracking_tag_id=1551067518-319&uuid=01c8c728-665c-4537-a420-395dc8a64e53
https://kirov-portal.ru/away.php?url=https%3A%2F%2Frekon36.ru
https://toneto.net/redirect?url=http%3A%2F%2Frekon36.ru/
https://esvc000236.wic027u.server-web.com/include/Reurl3.php?adtype=hits&table=1&gunid=30&url=rekon36.ru
https://studenthelpr.com/redirect?redirectTo=http%3A%2F%2Frekon36.ru
https://maheev.perm.ru/bitrix/rk.php?goto=http%3A%2F%2Frekon36.ru
https://sitereport.netcraft.com/?url=https://rekon36.ru/
https://marublog129.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://rakugakiya.s28.xrea.com/cgi/meiboa/ezlinka.php?mode=jump&url=http%3A%2F%2Frekon36.ru
https://my.icaew.com/security/Account/Logout?returnUrl=https%3A%2F%2Frekon36.ru
https://ofsilvers.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://reporting.sainsburysmagazine.co.uk/cgi-bin/rr/nobook:151187nosent:64962nosrep:93621/https:/rekon36.ru
https://siid.insp.mx/redirect?url=%2F%2Frekon36.ru
https://love.goxip.com/hk/affiliate?url=http%3A%2F%2Frekon36.ru
https://www.kichink.com/home/issafari?uri=http%3A%2F%2Frekon36.ru/%2F
https://memo8.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://www.bing.com/news/apiclick.aspx?ref=FexRss&aid=&tid=60610D15439B4103A0BF4E1051EDCF8B&url=https%3A%2F%2Fairvission%2F&c=12807976268214810202&mkt=en-us
https://ads.agorafinancial.com/www/delivery/ck.php?ct=1&oaparams=2__bannerid=529__zoneid=4__cb=e74ef55876__oadest=http%3A%2F%2Frekon36.ru
https://rezkyrizani.xtgem.com/fb_/text_lingkaran?site=rekon36.ru<
https://www.kh-vids.net/proxy.php?link=http%3A%2F%2Frekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://www.math.auckland.ac.nz/wiki/index.php?search=https%3A%2F%2Frekon36.ru&title=Special%3ASearch&go=Go
https://islam.de/ms?r=https%3A%2F%2Frekon36.ru
https://cr.naver.com/redirect-notification?u=https%3A%2F%2Frekon36.ru
https://board-en.drakensang.com/proxy.php?link=http%3A%2F%2Frekon36.ru
https://participez.nanterre.fr/link?external_url=https%3A%2F%2Frekon36.ru
https://wiki.chem.gwu.edu/default/api.php?action=http%3A%2F%2Frekon36.ru
https://www.thickcash.com/iframe_content/video_banners/finishhim/fh-300×250-1/index.php?siteLink=https%3A%2F%2Frekon36.ru
https://pl.grepolis.com/start/redirect?url=http%3A%2F%2Frekon36.ru
https://pro.obesityhelp.com/tracked/?r=rekon36.ru&id=profile_website_10001
https://www.sunnymake.com/alexa/?domain=http%3A%2F%2Frekon36.ru
https://priuschat.com/proxy.php?link=https%3A%2F%2Frekon36.ru
https://m.wedkuje.pl/_mobile/_redirect.php?redir=http%3A%2F%2Frekon36.ru
https://ijpc.uscannenberg.org/?URL=http%3A%2F%2Frekon36.ru
https://beeyann.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://www.golfselect.com.au/redirect?activityType_cd=WEB-LINK&course_id=2568&tgturl=https%3A%2F%2Frekon36.ru
https://www.db.lv/ext/http%3A%2F%2Frekon36.ru/
https://6giay.vn/proxy.php?link=http%3A%2F%2Frekon36.ru
https://www.adminer.org/redirect/?url=https%3A%2F%2Frekon36.ru&lang=en
https://rinbro.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://www.kichink.com/home/issafari?uri=http%3A%2F%2Frekon36.ru/
https://forums.officialpsds.com/proxy.php?link=https%3A%2F%2Frekon36.ru
https://dog.s334.xrea.com/dti/?text=%E6%9C%89%E6%B5%A6%E7%95%99%E7%BE%8E&url=http%3A%2F%2Frekon36.ru&pic=https%3A%2F%2Fwww.caribbeancompr.com%25
https://firsttee.my.site.com/TFT_login?website=rekon36.ru
https://webservices.lib.uconn.edu/webapps/dcompass/tempbin/newreferer.php?URL=https%3A%2F%2Frekon36.ru
https://plantationfl.adventistchurch.org/forwarder/part1?url=https%3A%2F%2Frekon36.ru
https://www.kidsemail.org/parent-login.php?msg=%3Ca%20href%3D%22https%3A%2F%2Frekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://sites.estvideo.net/video/phpinfo.php?a%5B%5D=best+delta+8+hemp+flowers+%28%3Ca+href%3Dhttps%3A%2F%2Frekon36.ru
https://www.db.lv/ext/http:%2F%2Frekon36.ru
https://stats.sobyanin.ru/metrics/r/?muid=15196b01-6d0b-4689-b2fc-241a3e6ae908&category=04a6660a-c3fe-4fc3-84a6-60afd7dc9422&url=https%3A%2F%2Frekon36.ru
https://prlog.ru/analysis/rekon36.ru
https://passport-us.bignox.com/sso/logout?service=http%3A%2F%2Frekon36.ru
https://masaru323.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://forum.lephoceen.fr/proxy.php?link=https%3A%2F%2Frekon36.ru
https://ssbsync-global.smartadserver.com/api/sync?callerId=5&gdpr=null&gdpr_consent=&us_privacy=&redirectUri=https%3A%2F%2Frekon36.ru
https://w1.websnadno.cz/index.php?menu1r=2&stiznost=true&surl=rekon36.ru&sreferer=
https://vtambove.ru/go_links.php?http:/rekon36.ru
https://submit.jpmph.org/member/s_login.php?s_login=11&s_url=http%3A%2F%2Frekon36.ru
https://www.maritimeclassiccars.com/redirect.php?id=48&url=http%3A%2F%2Frekon36.ru
https://www.cleanlink.com/adviewer.asp?adi=/hs/graphics/19/10/019_HS_1019&p=hs1019-019-MatsInc&e=website%20%5Bat%5D%20cleanlink%20%5Bdot%5D%20com&u=https%3A%2F%2Frekon36.ru
https://vaninax.online.fr/Redir.php?r=http%3A%2F%2Frekon36.ru
https://gogvo.com/redir.php?k=d58063e997dbb039183c56fe39ebe099&url=https%3A%2F%2Frekon36.ru%2F
https://testregistrulagricol.gov.md/c/document_library/find_file_entry?p_l_id=67683&noSuchEntryRedirect=http%3A%2F%2Frekon36.ru
https://sc-state-library.mobilize.io/links?lid=gfQh03emv3hVxS0d5O3hjw&token=XBcQsLRbmwZhh21rh4UWww&url=http%3A%2F%2Frekon36.ru
https://www.kankomie.or.jp/banner_click?id=298&url=https%3A%2F%2Frekon36.ru
https://www.searchdaimon.com/?URL=rekon36.ru/
https://m.shopinlosangeles.net/redirect.aspx?url=https%3A%2F%2Frekon36.ru
https://www25.ownskin.com/wap_theme_download.oss?c=3&h=rekon36.ru
https://wiki.code4lib.org/index.php?title=%2Frekon36.ru&action=history&printable=yes
https://auth.mindmixer.com/GetAuthCookie?returnUrl=http%3A%2F%2Frekon36.ru/
https://chyba.o2.cz/cs/?url=https%3A%2F%2Frekon36.ru
https://apps.cancaonova.com/ads/www/delivery/ck.php?ct=1&oaparams=2__bannerid=149__zoneid=20__cb=87d2c6208d__oadest=https%3A%2F%2Fwww.rekon36.ru
https://rs.rikkyo.ac.jp/rs/error/ApplicationError.aspx?TopURL=https%3A%2F%2Frekon36.ru
https://www.hogodoc.com/?URL=rekon36.ru/
https://associate.foreclosure.com/scripts/t.php?a_aid=20476&a_bid&desturl=https%3A%2F%2Frekon36.ru
https://inginformatica.uniroma2.it/?URL=rekon36.ru
https://innerside.dothome.co.kr/bbs/skin/link/hit_plus.php?sitelink=http%3A%2F%2Frekon36.ru&id=link&page=1&sn1=&divpage=1&category=2&sn=off&ss=on&sc=on&select_arrange=headnum&desc=asc%20&no=4
https://www.etcconnect.com/logout.aspx?bc_ReturnURL=https%3A%2F%2Frekon36.ru
https://auth.mindmixer.com/GetAuthCookie?returnUrl=http%3A%2F%2Frekon36.ru
https://partner.beautysuccess.fr/servlet/effi.redir?id_compteur=22392471&url=http%3A%2F%2Frekon36.ru
https://s-panda.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://forums.techarp.com/proxy.php?link=http%3A%2F%2Frekon36.ru
https://littlenugget.onelink.me/1071849834?pid=Sponsorship&c=BCBVIP&af_dp=littlenugget%3A%2F%2F&af_web_dp=http%3A%2F%2Frekon36.ru
https://dot.wp.pl/redirn?SN=facebook_o2&t=1628334247&url=https%3A%2F%2Frekon36.ru%2F
https://www.drugs.ie/?URL=rekon36.ru
https://forum.mobile-networks.ru/go.php?http%3A%2F%2Frekon36.ru
https://virtuafighter.com/proxy.php?link=https%3A%2F%2Frekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://www.webclap.com/php/jump.php?sa=t&url=http%3A%2F%2Frekon36.ru%2F
https://www.bdsmlibrary.com/tgpx/click.php?id=4300&u=http%3A%2F%2Frekon36.ru&category=Lesbian&description=WhippedAss%20begins%20more%20girl/girl
https://www.chara-ani.com/member_rule.aspx?src=https%3A%2F%2Frekon36.ru
https://eflyers.revolution-bars.co.uk/2012/head-office/may/jubilee-newsletter/?c=rekon36.ru
https://freewebsitetemplates.com/proxy.php?link=https%3A%2F%2Frekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://px.owneriq.net/eoptout?redir=http%3A%2F%2Frekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://www.retrogames.cz/download_DOS.php?id=714&ROMfile=http%3A%2F%2Frekon36.ru&IMGsize=512
https://gun.deals/external-link?url=http%3A%2F%2Frekon36.ru
https://lr4.lsm.lv/lv/lr4/?rt=site&ac=socclick&lnk=https%3A%2F%2Frekon36.ru&r=1&acc=youtube
https://h1s.goodgame.ru/del/ck.php?ct=1&oaparams=2__bid=190__zid=26__cb=bc85c561c6__oadest=http%3A%2F%2Frekon36.ru
https://phleguratone-music-games.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://icdn.ymcacharlotte.org/CDN/Index?ImageUrl=https%3A%2F%2Frekon36.ru&Width=320
https://www.2banh.vn/redirect/?url=https%3A%2F%2Frekon36.ru/
https://nick.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://beta.novell.com/common/util/get_language_url.php?language=en-us&url=http%3A%2F%2F/rekon36.ru
https://framinghamlibrary.org/?URL=rekon36.ru
https://community.restaurant.org/links?url=https%3A%2F%2Frekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://tb.getinvisiblehand.com/adredirect.php?url=https%3A%2F%2Frekon36.ru
https://www.stationwagonforums.com/forums/proxy.php?link=https%3A%2F%2Frekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://kanten-papa.kir.jp/ranklink/rl_out.cgi?id=7200&url=http%3A%2F%2Frekon36.ru
https://jump.5ch.net/?rekon36.ru
https://www.constructionenquirer.com/wp-content/themes/constructionenquirer/adclick.php?url=https%3A%2F%2Frekon36.ru
https://app.ninjaoutreach.com/Navigate?eid=1usWxqcWeDxqkI&redirectUrl=http%3A%2F%2Frekon36.ru
https://www.vanderbiltcupraces.com/?URL=http%3A%2F%2Frekon36.ru
https://odorun.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://www23.ownskin.com/wap_theme_download.oss?c=11&h=rekon36.ru
https://semanticweb.cs.vu.nl/linkedatm/browse/list_resource?r=http%3A%2F%2Frekon36.ru
https://www.fahrradmonteur.de/index.php?title=/rekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F&action=edit&printable=yes
https://forward.zillertal.at/?url=https%3A%2F%2Frekon36.ru
https://adms.hket.com/openxprod2/www/delivery/ck.php?ct=1&oaparams=2__bannerid=6685__zoneid=2040__cb=dfaf38fc52__oadest=http%3A%2F%2Frekon36.ru
https://daccha.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=http%3A%2F%2Frekon36.ru
https://help.speciesfile.org/api.php?action=http%3A%2F%2Frekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://login.uleth.ca/cas/login?service=https%3A%2F%2Frekon36.ru%2F&gateway=true
https://wetpussygames.com/porn/out.php?id=rekon36.ru/
https://s03.megalodon.jp/?url=http%3A%2F%2Frekon36.ru/
https://www.pearlevision.com/m20ScheduleExamView?catalogId=15951&clearExams=1&langId=-1&returnUrl=http%3A%2F%2Frekon36.ru&storeId=12002&storeNumber=21129027
https://2015.adfest.by/banner/redirect.php?url=http%3A%2F%2Frekon36.ru
https://wiki.bzflag.org/index.php?title=%2Frekon36.ru&action=edit&printable=yes
https://davadava.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=http%3A%2F%2Frekon36.ru
https://vakbarat.index.hu/x.php?id=inxtc&url=rekon36.ru
https://vyper.io/conversions/cookieconversionpage?entry_id=9248247&url=http%3A%2F%2Frekon36.ru
https://lacplesis.delfi.lv/adsAdmin/redir.php?cid=c3_26488405&cimg&cname=Oli&u=http%3A%2F%2Frekon36.ru&uid=washingtondds22.blogspot.com%2F439888washingtondds22.blogspot.com%2F98
https://www.skisprungschanzen.com/link.php?id=2&url=http%3A%2F%2Frekon36.ru
https://www.seniorclassaward.com/?URL=rekon36.ru
https://www.cashfiesta.com/php/redir.php?ms&201206wl&5671826&c?https%3A%2F%2Frekon36.ru
https://thairesidents.com/l.php?b=85&l=http%3A%2F%2Frekon36.ru&p=2%2C5
https://vakbarat.index.hu/x.php?id=inxtc&url=rekon36.ru
https://fcviktoria.cz/media_show.asp?id=2924&id_clanek=2467&media=0&type=1&url=https%3A%2F%2Frekon36.ru
https://digiex.net/proxy.php?link=https%3A%2F%2Frekon36.ru
https://archive.paulrucker.com/?URL=rekon36.ru/
https://fffw2.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://daemon.indapass.hu/http/session_request?redirect_to=https%3A%2F%2Frekon36.ru%2F&partner_id=bloghu
https://smart.link/5bb788a3d5b83?site_id=Web_NBCS_Philly&creative_id=nbcsphi1356&cp_4=rekon36.ru
https://forum.game-guru.com/outbound?url=http%3A%2F%2Frekon36.ru&confirm=true
https://forums.fugly.com/proxy.php?link=http%3A%2F%2Frekon36.ru
https://www.online-image-editor.com/index.cfm?fa=download_file&image_path=rekon36.ru
https://www.ville-ge.ch/web-newsletter/newsletter_vdg/go/qui.php?l=616:1850&c=https%3A%2F%2Frekon36.ru
https://click.simsfinds.com/go?url=http%3A%2F%2Frekon36.ru
https://lospoblanos.com/?URL=http%3A%2F%2Frekon36.ru
https://vortez.net/revive2/www/delivery/ck.php?ct=1&oaparams=2__bannerid=96__zoneid=7__cb=7b05f93fa3__oadest=http%3A%2F%2Frekon36.ru
https://optimize.viglink.com/page/pmv?url=https%3A%2F%2Frekon36.ru
https://forums2.battleon.com/f/interceptor.asp?dest=rekon36.ru/
https://translate.itsc.cuhk.edu.hk/gb/rekon36.ru/weilun/b5/valk/valk_profile.html
https://armoryonpark.org/?URL=rekon36.ru/
https://sorakawa.s202.xrea.com/yomi/rank.php?mode=link&id=1358&url=http%3A%2F%2Frekon36.ru
https://accounts.ac-illust.com/signup?lang=vi&serviceURL=https%3A%2F%2Frekon36.ru
https://sekainoriron.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://www.oddworld.com/_shop/shop.php?store=rekon36.ru
https://www.hawaiitourismauthority.org/speedbump/?targetUrl=https%3A%2F%2Frekon36.ru
https://lr2.lsm.lv/lv/lr2/?rt=site&ac=socclick&lnk=http%3A%2F%2Frekon36.ru&r=1&acc=youtube
https://www.oxfordpublish.org/?URL=rekon36.ru/
https://kettypay.hatenadiary.com/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://forum.winhost.com/proxy.php?link=http%3A%2F%2Frekon36.ru
https://domain.opendns.com/rekon36.ru
https://dailyhoroscopeplus.onelink.me/kLrr?pid=app_share&c=test&af_web_dp=http%3A%2F%2Frekon36.ru
https://www.storeboard.com/profile/show_webpage_profile.asp?url=http%3A%2F%2Frekon36.ru
https://www.freeseotoolbox.net/domain/rekon36.ru/update
https://woostercollective.com/?URL=rekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://comoshin.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://sda.foodandtravel.com/live/www/delivery/ck.php?ct=1&oaparams=2__bannerid=14__zoneid=14__source=%7Bobfs%3A%7D__cb=18dd655015__oadest=http%3A%2F%2Frekon36.ru
https://trac.osgeo.org/osgeo/search?q=https%3A%2F%2Frekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://us.member.uschoolnet.com/register_step1.php?_from=rekon36.ru
https://www.fcslovanliberec.cz/media_show.asp?type=1&id=543&url_back=https%3A%2F%2Frekon36.ru
https://es.catholic.net/ligas/ligasframe.phtml?liga=https%3A%2F%2Frekon36.ru
https://auth.she.com/logout/?callback=http%3A%2F%2Frekon36.ru&client_id=8%E2%80%8E
https://gochiemon.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://style.s51.xrea.com/aoitori/rank.php?mode=link&id=206&url=http%3A%2F%2Frekon36.ru
https://www.plagscan.com/highlight?cite=1&doc=117798730&source=16&url=https%3A%2F%2Frekon36.ru
https://cm-eu.wargaming.net/frame/?service=frm&project=moo&realm=eu&language=en&login_url=http%3A%2F%2Frekon36.ru
https://m.shopinportland.com/redirect.aspx?url=rekon36.ru
https://kikaku.s54.xrea.com/cgi-bin/kanon2/romnavi.cgi?jump=1374&url=http%3A%2F%2Frekon36.ru
https://www.ufps.edu.co/ufps/atencionalciudadano/pdf.php?pdf=https%3A%2F%2Frekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://ai.blackfacts.com/redirect/FactSource/13d1ce12-1229-404b-bf31-8bdda75b7d55/03290b70-9a99-489b-a7fa-318ae1b60a6e/https%3A%2F%2Frekon36.ru
https://show.jspargo.com/attendeeAcquisitionTool/src/tracking10click.asp?caller=attAcqWidget&widgetId=61&redirectUrl=http%3A%2F%2Frekon36.ru
https://www.decidim.barcelona/link?external_url=https%3A%2F%2Frekon36.ru
https://auth.she.com/logout/?callback=http%3A%2F%2Frekon36.ru%20&client_id=8%E2%80%8E
http://www.ub.uni-heidelberg.de/cgi-bin/edok?dok=https%3A%2F%2Frekon36.ru
https://www.wenxuecity.com/blog/?act=haiwai_blog&url=http%3A%2F%2Frekon36.ru
https://hchocolatier.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=http%3A%2F%2Frekon36.ru
https://eventlog.netcentrum.cz/redir?data=aclick2c239800-486339t12&s=najistong&url=https%3A%2F%2Frekon36.ru&v=1
https://www.bausch.co.jp/redirect/?url=https%3A%2F%2Frekon36.ru
https://t10.org/cgi-bin/s_t10r.cgi?First=1&PrevURL=https%3A%2F%2Frekon36.ru
https://if-himazin2.hatenadiary.com/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://tokyo.new-akiba.com/ra/www/delivery/ck.php?ct=1&oaparams=2__bannerid=3__zoneid=3__cb=154a423fea__oadest=https%3A%2F%2Frekon36.ru
https://my.w.tt/a/key_live_pgerP08EdSp0oA8BT3aZqbhoqzgSpodT?medium=&feature=&campaign=&channel=&%24always_deeplink=0&%24fallback_url=rekon36.ru&%24deeplink_path=
https://up.band.us/snippet/view?url=rekon36.ru
https://account.everygame.eu/en/home/cashier?returnUrl=https%3A%2F%2Frekon36.ru
https://secure.radio-online.com/cgi-bin/rol.exe/ssiteid?rekon36.ru
https://old.urc.ac.ru/cgi/click.cgi?url=http%3A%2F%2Frekon36.ru
https://www.wellness.com/Version/Full?returnUrl=http%3A%2F%2Frekon36.ru
https://computing.ece.vt.edu/mediawiki/api.php?action=https%3A%2F%2Frekon36.ru
https://gml-grp.com/C.ashx?btag=a_6094b_435c_&affid=901&siteid=6094&adid=435&asclurl=http%3A%2F%2Frekon36.ru&AutoR=1
https://drugs.ie/?URL=https%3A%2F%2Frekon36.ru
https://forum.studio-397.com/proxy.php?link=https%3A%2F%2Frekon36.ru
https://forums.sonicretro.org/proxy.php?link=http%3A%2F%2Frekon36.ru
https://www6.topsites24.de/safety.php?url=https%3A%2F%2Frekon36.ru
https://kanose.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://a.pr-cy.ru/rekon36.ru/
https://partner.maisonsdumonde.com/servlet/effi.redir?id_compteur=22797254&url=https%3A%2F%2Frekon36.ru
https://auth.she.com/logout/?callback=http%3A%2F%2Frekon36.ru%20&client_id=8
https://kintsugi.seebs.net/proxy.php?link=https%3A%2F%2Frekon36.ru
https://www.shareaholic.com/logout?origin=http%3A%2F%2Frekon36.ru
https://owner.netkeiba.com/?horse_id=2020100124&pid=horse_shokin&return_url=https%3A%2F%2Frekon36.ru
https://big5.cri.cn/gate/big5/rekon36.ru/
https://bnb.easytravel.com.tw/click.aspx?no=3835&class=1&item=1001&area=6&url=http%3A%2F%2Frekon36.ru
https://sp.jp.wazap.com/info/jump.wz?url=https%3A%2F%2Frekon36.ru
https://wiki.zcubes.com/index.php?title=%2Frekon36.ru&action=edit&printable=yes
https://fetchyournews.com/revive/www/delivery/ck.php?oaparams=2__bannerid=458__zoneid=43__cb=1931d27daa__oadest=http%3A%2F%2Frekon36.ru
https://jenskiymir.com/proxy.php?url=http%3A%2F%2Frekon36.ru%2F34zxVq8
https://forums.kustompcs.co.uk/proxy.php?link=https%3A%2F%2Frekon36.ru
https://hudsonltd.com/?URL=rekon36.ru
https://doba.te.ua/gateway?goto=https%3A%2F%2Frekon36.ru/
https://ads1.opensubtitles.org/1/www/delivery/afr.php?zoneid=3&cb=984766&query=One+Froggy+Evening&landing_url=http%3A%2F%2Frekon36.ru
https://w1.weblahko.sk/index.php?menu1r=2&stiznost=true&surl=rekon36.ru&sreferer=
https://west.mints.ne.jp/yomi/rank.cgi?mode=link&id=168&url=http%3A%2F%2Frekon36.ru
https://track.pubmatic.com/AdServer/AdDisplayTrackerServlet?clickData=JnB1YklkPTE3NDEwJnNpdGVJZD0xNzQxMSZhZElkPTEyMTgyJmthZHNpemVpZD03JmNhbXBhaWduSWQ9NjI0MiZjcmVhdGl2ZUlkPTAmYWRTZXJ2ZXJJZD0yNDM=_url=https%3A%2F%2Frekon36.ru
https://babkim.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=http%3A%2F%2Frekon36.ru
https://link.d24am.com/?link=http%3A%2F%2Frekon36.ru
https://decidim.santcugat.cat/link?external_url=https%3A%2F%2Frekon36.ru
https://eric.ed.gov/?redir=https://rekon36.ru/
https://forum.doctissimo.fr/inscription-1.html?referer_url=https%3A%2F%2Frekon36.ru
https://www.unifrance.org/newsletter-click/6763261?url=http%3A%2F%2Frekon36.ru
https://yomi.mobi/rjump/rekon36.ru
https://almanach.pte.hu/oktato/273?from=http%3A%2F%2Frekon36.ru
https://envios.uces.edu.ar/control/click.mod.php?email=%7B%7Bemail%7D%7D&id_envio=1557&url=https%3A%2F%2Frekon36.ru/
https://www.hcsparta.cz/media_show.asp?type=1&id=246&url_back=http%3A%2F%2Frekon36.ru
https://amk-team.ru/go/?url=https%3A%2F%2Frekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://cas.rec.unicen.edu.ar/cas/login?gateway=true&service=https%3A%2F%2Frekon36.ru
https://app.nexoos.com.br/mkt/borrower/registration_wizard/partner_redirection?link=https%3A%2F%2Frekon36.ru&partner=geru
https://decidimos.monterrey.gob.mx/link?external_url=https%3A%2F%2Frekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://syaoruu.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://quilter.s8.xrea.com/cgi-bin/downcnt.cgi?url=http%3A%2F%2Frekon36.ru
https://mana310.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://sp.baystars.co.jp/community/club_baystars/shop_map.php?catg=bene&id=g_005&linkURL=http%3A%2F%2Frekon36.ru/
https://www.constructionenquirer.com/wp-content/themes/constructionenquirer/adclick.php?url=http%3A%2F%2Frekon36.ru
https://pram.elmercurio.com/Logout.aspx?ApplicationName=EMOL&SSOTargetUrl=https%3A%2F%2Frekon36.ru%2F&l=yes
https://www.sexpin.net/source/rekon36.ru/
https://idoooll.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://supertramp.com/?URL=rekon36.ru
https://lucid.s28.xrea.com/dmm/?t=Fleeting+Diary&l=https%3A%2F%2Frekon36.ru&i=5479mrbls00069&imageURL=&s=dmm
https://paulgravett.com/?URL=rekon36.ru/
https://nabchelny.ru/welcome/blindversion/normal?callback=http%3A%2F%2Frekon36.ru
https://ipmba.org/?URL=http%3A%2F%2Frekon36.ru
https://osallistu.ouka.fi/link?external_url=https%3A%2F%2Frekon36.ru
https://adsfac.net/search.asp?url=http%3A%2F%2Frekon36.ru
https://suecia.kb.se/goto/http:/rekon36.ru/
https://new.theinfosphere.org/index.php?title=%2Frekon36.ru&action=edit&printable=yes
https://auth.she.com/logout/?callback=http%3A%2F%2Frekon36.ru&client_id=8
https://aoisakana5.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://passport-us.bignox.com/sso/logout?service=http%3A%2F%2Fwww.rekon36.ru
https://wiki.evilmadscientist.com/index.php?title=/rekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F&action=edit&printable=yes
https://popjulia.onelink.me/COvz?pid=pc-bottom&c=home&af_dp=com.chicv.popjulia%3A%2F%2F&af_web_dp=http%3A%2F%2Frekon36.ru&is_retargeting=true
https://fdp.timacad.ru/bitrix/redirect.php?event1&event2&event3&goto=http%3A%2F%2Frekon36.ru/
https://www.studyladder.com/games/activity/word-match-s-a-t-p-i-n-35665?backUrl=http%3A%2F%2Frekon36.ru
https://www.thetfp.com/proxy.php?link=http%3A%2F%2Frekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://secure.nationalimmigrationproject.org/np/clients/nationalimmigration/tellFriend.jsp?subject=Attending%202020+Annual+Pre-AILA+Crimes+and+Immigration+Virtual+CLE&url=http%3A%2F%2Frekon36.ru
https://asoechat.wap.sh/redirect?url=rekon36.ru
https://forum.reizastudios.com/proxy.php?link=http%3A%2F%2Frekon36.ru
https://100day.hatenadiary.com/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://www.surf.tom.ru/r.php?g=http%3A%2F%2Frekon36.ru
https://cpen.com/?url=https%3A%2F%2Frekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://hermis.alberta.ca/paa/Details.aspx?st=randall&ReturnUrl=http%3A%2F%2Frekon36.ru&dv=True&DeptID=1&ObjectID=PR2006
https://sat.issprops.com/?URL=rekon36.ru/
https://sso.qiota.com/api/v1/logout?redirect_uri=https%3A%2F%2Frekon36.ru
https://bbs.sp.findfriends.jp/?pid=go_link&url=http%3A%2F%2Frekon36.ru
https://maximal-life.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://dreamerdream.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://kolflow.univ-nantes.fr/mediawiki/api.php?action=https%3A%2F%2Frekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://mail2.mclink.it/SRedirect/rekon36.ru
https://whois.gandi.net/en/results?search=rekon36.ru
https://www.rovaniemi.fi/includes/LoginProviders/ActiveDirectory/ADLogin.aspx?ReturnUrl=https%3A%2F%2Frekon36.ru&ispersistent=True&mode=PublicLogin
https://adms3.hket.com/openxprod2/www/delivery/ck.php?ct=1&oaparams=2__bannerid=527__zoneid=667__cb=72cbf61f88__oadest=http%3A%2F%2Frekon36.ru
https://msmgo.onelink.me/4240393215?pid=Web_traffic&c=Energy_Montior&af_channel=Website_footer&af_dp=MSMMoreMoney%3A%2F%2F%2Fapp%2Fmoneysupermarket-go&af_web_dp=http%3A%2F%2Frekon36.ru
https://forums.opera.com/outgoing?url=http%3A%2F%2Frekon36.ru
https://board-en.drakensang.com/proxy.php?link=http%3A%2F%2Frekon36.ru%2F
https://adsnew.hostreview.com/openx_new/www/delivery/ck.php?ct=1&oaparams=2__bannerid=1110__zoneid=14__cb=34519e1b0c__maxdest=https%3A%2F%2Frekon36.ru
https://content.hh.ru/api/v1/click?contentId=538&placeId=2&employerId=581458&domainAreaId=1353&host=https%3A%2F%2Frekon36.ru
https://fergananews.com/go.php?https%3A%2F%2Frekon36.ru
https://blogs.s367.xrea.com/dmm/?t=vol.12+Ymode+EX+%E3%81%95%E3%81%8F%E3%82%89&l=https%3A%2F%2Frekon36.ru&i=5394ccafe00156&imageURL=https%3A%2F%2Fpics.dmm.com%2Fdigital%2Fvideo%2F5394ccafe00156%2F5394ccafe00156pl.jpg&s=dmm
https://passport.translate.ru/Account/Login?parentUrl=https%3A%2F%2Frekon36.ru
https://empyriononline.com/proxy.php?link=https%3A%2F%2Frekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://nabat.tomsk.ru/go/url=https:/rekon36.ru
https://dianalab.e-ce.uth.gr/html/dianauniverse/graphic.php?url=http%3A%2F%2Frekon36.ru
https://galacy-mountain.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://soundingames.dei.uc.pt/api.php?action=https%3A%2F%2Frekon36.ru/%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9/
https://decidim.calafell.cat/link?external_url=http%3A%2F%2Frekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://tm.dl.stimme.de/tm/a/channel/tracker/d38ae3b7df?navigation=Leser+werben+Leser&tmrde=https%3A%2F%2Frekon36.ru
https://trustandjustice.org/?URL=https%3A%2F%2Frekon36.ru
https://www.survivalmonkey.com/proxy.php?link=https%3A%2F%2Frekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://the-take.com/?URL=https%3A%2F%2Frekon36.ru
https://captcha.2gis.ru/form?return_url=https%3A%2F%2Frekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://cr.naver.com/redirect-notification?u=http%3A%2F%2Fwww.www.rekon36.ru/%2F%E2%80%8E
https://english.republiquelibre.org/index.php?title=/rekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F&action=edit&printable=yes
https://my.w.tt/a/key_live_pgerP08EdSp0oA8BT3aZqbhoqzgSpodT?medium=&feature=&campaign=&channel=&$always_deeplink=0&$fallback_url=www.rekon36.ru&$deeplink_path=
https://ad.inter-edu.com/ox/www/delivery/ck.php?ct=1&oaparams=2__bannerid%3D43467__zoneid%3D286__OXLCA%3D1__cb%3D04acee1091__oadest%3Dhttps%3A%2F%2Frekon36.ru
https://wiki.securepoint.de/index.php?title=%2Frekon36.ru&action=edit&printable=yes
https://forums.overclockers.com.au/proxy.php?link=http%3A%2F%2Frekon36.ru
https://daemon.indapass.hu/http/session_request?redirect_to=http%3A%2F%2Frekon36.ru&partner_id=bloghu
https://adx.dcfever.com/ads/www/delivery/ck.php?ct=1&oaparams=2__bannerid=1138__zoneid=2__cb=a4d7c48ece__oadest=http%3A%2F%2Frekon36.ru
https://link-sekiya.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Frekon36.ru
https://passport-us.bignox.com/sso/logout?service=https%3A%2F%2Frekon36.ru%2F
https://cities.bythenumbers.sco.ca.gov/embed/barchart?branch_type=revenue¤t_entity=org1&year=2020&child_entity=org2&org1=Yuba%2BCity&sort_field=total&sort=desc&is_leaf=false&human_name=City&sourceUrl=https%3A%2F%2Frekon36.ru&type=content
https://noi.md/newsbar.php?lang=md&mdv=http%3A%2F%2Frekon36.ru&click=1&click_id=19131&n_id=43600
https://bodyblow.s9.xrea.com/x/cutlinks/rank.php?url=http%3A%2F%2Frekon36.ru
https://vote.socialpsychology.org/index.htm?host2=rekon36.ru
https://cds.zju.edu.cn/addons/cms/go/index.html?url=https%3A%2F%2Frekon36.ru
https://vdigger.com/downloader/downloader.php?utm_nooverride=1&site=rekon36.ru
https://www.bovec.net/redirect.php?link=rekon36.ru/&un=reedw.cf&from=bovecnet
https://forum.corvusbelli.com/proxy.php?link=https%3A%2F%2Frekon36.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://dados.ibict.br/pt_PT/api/1/util/snippet/api_info.html?resource_id=2ace6719-6b73-4285-b349-49dbbaa7de53&datastore_root_url=http%3A%2F%2Frekon36.ru
https://newsletter.usi.ch/email/n?h=2obmeqV6fSqh5ZdQ0zugSbZMYMrMfiYL&l=%2F%2Frekon36.ru
https://tinhte.vn/proxy.php?link=http%3A%2F%2Frekon36.ru
https://www.emuparadise.me/logout.php?next=https%3A%2F%2Frekon36.ru
https://armoryonpark.org/?URL=rekon36.ru
https://vakbarat.index.hu/x.php?id=inxtc&url=http%3A%2F%2Frekon36.ru
Your comment is awaiting moderation.
Маленькие советы для больших перемен от 9 известных дизайнеров 9 советов — по одному от каждого из 9 известных дизайнеров интерьеров — чтобы сделать свой дом красивее и удобнее https://olga-filippova.ru/office_interior
Лучшие книги для дизайнера интерьера Мы предлагаем вам ознакомиться с несколькими полезными с нашей точки зрения книгами, которые будут отличным дополнением к домашней библиотеке дизайнера интерьера https://olga-filippova.ru/interery-fasad
Владельцы жилплощади с несколькими комнатами имеют целых три пространства для каждая комната может стать предметом гордости https://olga-filippova.ru/zakazat-dizajn-proekt-stoimost
Дизайн трехкомнатных квартир подразумевает под собой оформление пространства в разных цветах, стилях и тонах https://olga-filippova.ru/horeca
В трешке не нужно думать о том, как практично использовать квадратные метры и как совместить помещения, чтобы всем членам семьи хватило места https://olga-filippova.ru/horeca
Необязательно и выдерживать единство интерьера, можно оформлять максимально оригинально и своеобразно https://olga-filippova.ru/fitness-spa
Главное – определить, какой стиль будет преобладать в каждой комнате, и какую интерьерную нагрузку она будет выполнять https://olga-filippova.ru/interery-medical-study-center
Your comment is awaiting moderation.
Mega сочетает в себе разнообразие товаров, доступные
цены и удобство, чтобы каждый
покупатель чувствовал себя комфортно при онлайн-шопинге.
Нужны ли вам продукты или новая техника
– площадка мега предложит всё, что вам нужно.
Наслаждайтесь быстрой доставкой, простыми возвратами и высоким уровнем обслуживания
при каждой покупке. Узнайте, почему ссылка на мега даркнет выбирают
миллионы людей по всему миру.
Http mega: https://xn--megab-mdb.com
Your comment is awaiting moderation.
Need an AI generator? ai undress The best nude generator with precision and control. Enter a description and get results. Create nude images in just a few clicks.
Your comment is awaiting moderation.
Howdy! ed pills very good internet site.
Your comment is awaiting moderation.
Hello there! order finasteride beneficial site.
Your comment is awaiting moderation.
What’s up, DeFi crowd?
Just stumbled on a smart piece about AI in trading.
It analyzes several big trends in trading world.
Really solid perspective.
See full post
Your comment is awaiting moderation.
Telecharger 1xbet sur telephone 1xbet apk
Your comment is awaiting moderation.
1.
Шукаєш надійний інтернет-магазин техніки? Тут зібрані перевірені гаджети та електроніка в Україні з актуальними цінами та оглядами. https://tawk.to/tvmircomua
2.
Усе про інтернет-магазини гаджетів в одному місці. Порівнюй, обирай і знаходь найкращий магазин електроніки в Україні. https://tawk.to/tvmircomua
3.
Від смартфонів до ноутбуків — знайди перевірений інтернет-магазин комп’ютерної техніки, електроніки та гаджетів швидко й зручно. https://www.hogwartsishere.com/1804272/
4.
Не знаєш, де купити техніку вигідно? Тут ти знайдеш огляди та добірки кращих магазинів електроніки в Україні. https://www.divephotoguide.com/user/tvmircomua
5.
Твій гід у світі технологій: інтернет-магазини техніки та гаджетів, актуальні пропозиції та корисна інформація. https://www.blogger.com/profile/16660563818913207217
Your comment is awaiting moderation.
6.
Обирай техніку без ризику. Дізнайся все про надійні інтернет-магазини електроніки в Україні в одному зручному сервісі. https://www.pinterest.com/tvmirc/_profile/
7.
Хочеш купити гаджет і не помилитись? Ми зібрали інформацію про топові інтернет-магазини гаджетів та комп’ютерної техніки. https://writexo.com/share/eb3b2edd49fd
8.
Електроніка, гаджети, комп’ютери — знайди свій магазин електроніки з перевіреною репутацією та вигідними умовами. https://gettr.com/user/tvmircomua
9.
Зручний пошук по інтернет-магазинах техніки в Україні. Порівнюй пропозиції та обирай найкраще. https://portfolium.com/tvmircomua26
10.
Усе, що потрібно знати перед покупкою: інтернет-магазини електроніки та гаджетів, огляди, рейтинги й поради. https://fliphtml5.com/homepage/tvmircomua/tvmircomua26/
Your comment is awaiting moderation.
Мультимедийный интегратор здесь интеграция мультимедийных систем под ключ для офисов и объектов. Проектирование, поставка, монтаж и настройка аудио-видео, видеостен, LED, переговорных и конференц-залов. Гарантия и сервис.
Your comment is awaiting moderation.
Hey crypto folks!
Wanted to share a comprehensive piece about latest token launches.
The author explores top coins in trading world.
Really solid perspective.
Go to link
Your comment is awaiting moderation.
Hey, everyone! Allow me to introduce myself as Admin Read:
На Кракен можно найти всё необходимое для дома, работы и досуга. Платформа ссылка на kraken тор предлагает товары по выгодным ценам, включая эксклюзивные коллекционные предметы. Покупка становится ещё проще с помощью акций и скидок. Кракен заботится о защите сделок, что привлекает покупателей со всего мира. Именно кракен onion создаёт условия для удобных и безопасных покупок.
Your comment is awaiting moderation.
Hi crypto enthusiasts!
Checked out a insightful guide about crypto trends this month.
It breaks down how the market’s moving in crypto ecosystems.
Nice balanced view.
More details
Your comment is awaiting moderation.
Found one site when reviewing international housing sections.
The setup appears clear, which makes checking smooth.
Reasonable to check whenever you want keeping everything inside one central place.
URL-https://www.techmeme.com/190624/p1
Your comment is awaiting moderation.
Greetings everyone!
Just read a concise overview about the state of blockchain.
It breaks down main takeaways in Bitcoin, Ethereum, and altcoins.
Nice balanced view.
Check article
Your comment is awaiting moderation.
1.
Шукаєш надійний інтернет-магазин техніки? Тут зібрані перевірені гаджети та електроніка в Україні з актуальними цінами та оглядами. https://fliphtml5.com/homepage/tvmircomua/tvmircomua26/
2.
Усе про інтернет-магазини гаджетів в одному місці. Порівнюй, обирай і знаходь найкращий магазин електроніки в Україні. https://www.goodreads.com/user/show/197508118-tvmircomua
3.
Від смартфонів до ноутбуків — знайди перевірений інтернет-магазин комп’ютерної техніки, електроніки та гаджетів швидко й зручно. https://www.anobii.com/en/017a231f12db3a7b6b/profile/activity
4.
Не знаєш, де купити техніку вигідно? Тут ти знайдеш огляди та добірки кращих магазинів електроніки в Україні. https://freeicons.io/profile/877550
5.
Твій гід у світі технологій: інтернет-магазини техніки та гаджетів, актуальні пропозиції та корисна інформація. https://www.tumblr.com/tvmircomua
Your comment is awaiting moderation.
6.
Обирай техніку без ризику. Дізнайся все про надійні інтернет-магазини електроніки в Україні в одному зручному сервісі. https://www.tumblr.com/tvmircomua
7.
Хочеш купити гаджет і не помилитись? Ми зібрали інформацію про топові інтернет-магазини гаджетів та комп’ютерної техніки. https://www.reverbnation.com/artist/tvmircomua
8.
Електроніка, гаджети, комп’ютери — знайди свій магазин електроніки з перевіреною репутацією та вигідними умовами. https://www.mapleprimes.com/users/tvmircomua
9.
Зручний пошук по інтернет-магазинах техніки в Україні. Порівнюй пропозиції та обирай найкраще. https://www.bandlab.com/tvmircomua
10.
Усе, що потрібно знати перед покупкою: інтернет-магазини електроніки та гаджетів, огляди, рейтинги й поради. https://wakelet.com/@tvmircomua
Your comment is awaiting moderation.
This dedicated support plays a vital role in enhancing user satisfaction.
888starz login https://hpcgg.org/
Your comment is awaiting moderation.
What’s good, folks?
Wanted to post a super informative thread about market analysis.
It talks about major updates in crypto in general.
I think you’ll like it, especially if you’re into news.
Read it here
Your comment is awaiting moderation.
1.
Шукаєш надійний інтернет-магазин техніки? Тут зібрані перевірені гаджети та електроніка в Україні з актуальними цінами та оглядами. https://gettr.com/user/tvmircomua
2.
Усе про інтернет-магазини гаджетів в одному місці. Порівнюй, обирай і знаходь найкращий магазин електроніки в Україні. https://teletype.in/@tvmircomua
3.
Від смартфонів до ноутбуків — знайди перевірений інтернет-магазин комп’ютерної техніки, електроніки та гаджетів швидко й зручно. https://uniquethis.com/tvmircomua?tab=100027185
4.
Не знаєш, де купити техніку вигідно? Тут ти знайдеш огляди та добірки кращих магазинів електроніки в Україні. https://onlinesequencer.net/members/240367
5.
Твій гід у світі технологій: інтернет-магазини техніки та гаджетів, актуальні пропозиції та корисна інформація. https://www.goodreads.com/user/show/197508118-tvmircomua
Your comment is awaiting moderation.
6.
Обирай техніку без ризику. Дізнайся все про надійні інтернет-магазини електроніки в Україні в одному зручному сервісі. https://promosimple.com/ps/43ae5/tvmircomua
7.
Хочеш купити гаджет і не помилитись? Ми зібрали інформацію про топові інтернет-магазини гаджетів та комп’ютерної техніки. https://www.divephotoguide.com/user/tvmircomua
8.
Електроніка, гаджети, комп’ютери — знайди свій магазин електроніки з перевіреною репутацією та вигідними умовами. https://www.anobii.com/en/017a231f12db3a7b6b/profile/activity
9.
Зручний пошук по інтернет-магазинах техніки в Україні. Порівнюй пропозиції та обирай найкраще. https://maxforlive.com/profile/user/tvmircomua?tab=about
10.
Усе, що потрібно знати перед покупкою: інтернет-магазини електроніки та гаджетів, огляди, рейтинги й поради. https://www.hogwartsishere.com/1804272/
Your comment is awaiting moderation.
Co najlepsze, symbole te nie muszą znajdować się na linii wygrywającej ani na sąsiednich bębnach. „Gates of Olympus” cechuje RTP na poziomie 96,5%, co jest wynikiem powyżej średniej. Gra na tym automacie jest elektryzująca, natomiast poziom zmienności gry jest bardzo wysoki. Dobra wiadomość jest jednak taka, że z dużym ryzykiem wiążą się duże nagrody. Maksymalna kwota wygranej wynosi 5000-krotność całkowitego zakładu. Poszukując slotów w podobnym klimacie z portfolio Yggdrasil, sprawdź kontynuację recenzowanego slotu, czyli Valley of the Gods 2. Ten automat wyróżnia się innowacyjnym układem bębnów oraz zmienną liczbą linii płatniczych od 240 do 20 160.
https://smartsellproduct.com.br/recenzja-gry-sugar-rush-od-pragmatic-play-slodka-rozrywka-dla-polskich-graczy/
database of accounts for sale accounts-marketplace.xyz Doświadcz emocji gier z krupierem na żywo w drugiej kategorii Mega Dice, obejmującej klasyki, takie jak Ruletka, Blackjack, Baccarat i Poker. Współdziałaj z profesjonalnymi krupierami w autentycznej atmosferze gry. Dla tych, którzy szukają unikalnego zwrotu, odkryj świat teleturniejów z tytułami takimi jak Crazy Time i Deal or No Deal. Mega Dice błyszczy innowacyjnością w swojej sekcji “gry kryptograficzne”, prezentując gry zrodzone z ery blockchain, w tym Hi Lo, Aviator, Plinko i inne. Grafika może być uproszczona, ale zabawa i imponujące wypłaty pozostają stałym źródłem radości. Opinie graczy o SevenPlay pokrywają się z wynikami naszych testów – to solidny serwis hazardowy z zadowalającą ofertą gier i świetnymi promocjami. To po prostu godne uwagi kasyno. Szkoda jednak, że SevenPlay Casino Online nie ma profili w social mediach, to zawsze dodatkowy kanał komunikacji.
Your comment is awaiting moderation.
Hey everyone!
Discovered a fresh article about Bitcoin & altcoin trends.
It talks about key movements in Web3 & DeFi projects.
Packed with insights, especially if you trade.
Full link
Your comment is awaiting moderation.
Качественный дилер купить BM Facebook предлагает возможность подобрать аккаунты для бизнеса. Если вам нужно купить аккаунты Facebook, чаще всего важен не «просто доступе», а в контроле и порядке: предсказуемая операционка, разделение задач между участниками и аккуратные изменения. Мы подготовили короткую карту выбора, чтобы вы сразу понимали что сравнивать перед заказом.Навигация по теме: FAQ. Важно: покупка — это только вход. Дальше решает порядок: как выдаются права, как вы ведете кампании без хаоса, как документируете действия и как отделяете тесты от масштабирования. Главная фишка данной площадки — это наличии огромной вики-энциклопедии, где выложены практичные инструкции по перформанс-подходу. Команда поможем, как грамотно организовать доступы, чтобы масштабирование шло спокойнее и соблюдались правила . Вступайте в сообщество, изучайте полезные кейсы, стройте систему и в итоге улучшайте контроль с помощью нашего сервиса без задержек. Дисклеймер: действуйте в рамках закона и всегда в соответствии с правилами платформ.
Your comment is awaiting moderation.
Надежный поставщик перейти в каталог предоставляет возможность подобрать учетки под залив. Если вам нужно купить аккаунты Facebook, чаще всего важен не «одном логине», а в качестве фарма: отсутствие вылетов на селфи, наличие пройденного ЗРД в Ads Manager и прогретые FanPage. Мы собрали короткую карту выбора, чтобы вы сразу понимали какой тип аккаунта брать перед покупкой.Навигация по теме: FAQ по ЗРД. Важно: аккаунт — это инструмент. Дальше решает подход к запуску: как вяжется карта, как шерите пиксели без риска банов, как проходите чеки и как дублируете кампании. Особенность данной площадки — это наличие эксклюзивной вики-энциклопедии FB, в которой выложены рабочие мануалы по фарму аккаунтов. Здесь доступны аккаунты FB для разных сетапов: от миксов до ПЗРД сетапами с высоким лимитом. Заходите к нам, смотрите обучающие разборы банов, наводите порядок и повышайте ROI на базе наших расходников прямо сейчас. Дисклеймер: действуйте в рамках закона и с учетом правил Meta.
Топовый площадка маркетплейс FB аккаунтов рад видеть медиабайеров в своем каталоге расходников для Фейсбука. Когда вы планируете купить аккаунты Facebook, чаще всего важен не «одном логине», а в проходимости чеков: стабильный запуск, зеленые плашки в Ads Manager и прогретые FanPage. Мы собрали понятную навигацию, чтобы вы сразу понимали какой тип аккаунта брать перед заказом.Навигация по теме: типы БМов и лимиты. Важно: покупка — это только вход. Дальше решает схема залива: какой прокси используется, как вы передаете лички без риска банов, как реагируете на полиси и как дублируете кампании. Гордость нашего сервиса — это наличии приватной вики-энциклопедии FB, в которой собраны актуальные сетапы по проходу ЗРД. На сайте доступны страницы Facebook под разные задачи: от дешевых авторегов и заканчивая мощными Кингами с высоким лимитом. Заказывая у нас, клиент получает не только доступ, а также полную помощь саппорта, прозрачные правила чека, гарантию на вход плюс самые конкурентные цены на рынке FB-аккаунтов. Важно: используйте активы законно и всегда с учетом правил Meta.
Практичный магазин https://buyaccountshop.run предоставляет доступ купить профили для бизнеса. Если вам нужно купить аккаунт Facebook для рекламы, чаще всего важен не «одном логине», а в проходимости чеков: уверенный спенд, наличие пройденного ЗРД в Ads Manager и прогретые FanPage. Мы подготовили понятную навигацию, чтобы вы без лишних вопросов понимали какой лимит выбрать перед заказом.Быстрый ориентир: начните с категории Бизнес Менеджеры (BM), а для серьезных объемов — идите сразу в профильные позиции: BM 250$. Важно: покупка — это только вход. Дальше решает схема залива: какой прокси используется, как вы передаете лички без триггеров, как проходите чеки и как масштабируете адсеты. Гордость этого шопа — это наличие огромной базы знаний по FB, в которой написаны рабочие мануалы по фарму аккаунтов. Команда поможем, как без лишних рисков привязать карту, чтобы не улетели на полиси а также продлили жизнь аккаунтам . Оформляя у нас, вы получаете не только cookie + token, а также оперативную консультацию, ясное описание товара, страховку на валид плюс самые приятные прайсы среди селлеров. Важно: используйте активы законно и всегда в соответствии с правилами Facebook.
Лучший поставщик купить FanPage Facebook предоставляет доступ подобрать соц аккаунты под залив. Когда вы планируете купить аккаунт Facebook для рекламы, чаще всего важен не «одном логине», а в качестве фарма: стабильный запуск, наличие пройденного ЗРД в Ads Manager и правильно созданные ФП. Мы собрали практичный чек-лист, чтобы вы сразу понимали какой лимит выбрать перед покупкой.Быстрый ориентир: начните с разделы Бизнес Менеджеры (BM), а для масштабирования — переходите сразу в профильные позиции: Безлимитные БМ. Важно: аккаунт — это инструмент. Дальше решает подход к запуску: как вяжется карта, как вы передаете лички аккуратно, как реагируете на полиси и как масштабируете адсеты. Особенность этого шопа — заключается в наличии приватной вики-энциклопедии FB, в которой написаны свежие гайды по работе с БМами. На сайте доступны аккаунты FB под любые цели: начиная с миксов и заканчивая ПЗРД сетапами с документами. Покупая здесь, клиент получает не только валидный профиль, а также всестороннюю консультацию, понятные условия замены, страховку на момент покупки и самые конкурентные цены среди селлеров. Дисклеймер: действуйте в рамках закона и с учетом правил Meta.
Качественный проект купить Фарм аккаунты Facebook открывает доступ приобрести рекламные сущности для таргета. Когда вы планируете купить аккаунты Facebook, обычно задача не в «одном логине», а в трасте и лимитах: отсутствие вылетов на селфи, наличие пройденного ЗРД в Ads Manager и правильно созданные ФП. Мы оформили короткую карту выбора, чтобы вы без лишних вопросов понимали что подойдет под ваши офферы перед заказом.Что внутри: типы БМов и лимиты. Важно: аккаунт — это инструмент. Дальше решает схема залива: какой прокси используется, как вы передаете лички аккуратно, как реагируете на полиси и как дублируете кампании. Главная фишка этого шопа — заключается в наличии масштабной базы знаний по FB, где выложены практичные гайды по разбану кабинетов. Команда подскажем, как грамотно запустить первый адсет, чтобы вы не улетели на полиси и продлили жизнь аккаунтам . Покупая у нас, клиент получает не просто аккаунт, но и всестороннюю помощь саппорта, ясное описание товара, страховку на момент покупки плюс максимально конкурентные расценки на рынке FB-аккаунтов. Дисклеймер: используйте активы законно и в соответствии с правилами Facebook.
Your comment is awaiting moderation.
Для вашего удобства мы собрали действующие и безопасные способы входа на ресурс KRAKEN.
Ниже представлены официальные и резервные зеркала платформы KRAKEN, которые гарантируют стабильный доступ.
Список рабочих адресов KRAKEN для перехода:
Основной рабочий адрес KRAKEN: https://forum-geeks–rp-ru.translate.goog/threads/5775/?_x_tr_sl=auto&_x_tr_tl=ru&_x_tr_hl=ru&_x_tr_pto=wapp
Первое официальное зеркало KRAKEN:https://forum-geeks–rp-ru.translate.goog/threads/6712/?_x_tr_sl=auto&_x_tr_tl=ru&_x_tr_hl=ru&_x_tr_pto=wapp
Второе резервное зеркало KRAKEN: https://forum.geeks-rp.ru/threads/8974/
Дополнительный домен KRAKEN для доступа: https://forum-geeks–rp-ru.translate.goog/threads/8974/?_x_tr_sl=auto&_x_tr_tl=ru&_x_tr_hl=ru&_x_tr_pto=wapp
Подробная инструкция KRAKEN по безопасному входу и использованию:
Подготовка браузера для доступа к KRAKEN. Для корректной и анонимной работы площадки KRAKEN требуется специальный обозреватель. Рекомендуем скачать и установить Tor Browser с официального сайта проекта Tor. Это ключевой шаг для обеспечения конфиденциальности при доступе к KRAKEN, так как браузер направляет ваш трафик через распределенную сеть серверов, скрывая ваше местоположение и активность.
Запуск и подключение к сети для KRAKEN. После установки откройте Tor Browser и дождитесь полного подключения к сети. Иконка в верхней части окна браузера покажет статус соединения. Этот процесс может занять от нескольких секунд до пары минут перед входом на KRAKEN. Убедитесь, что подключение установлено успешно.
Переход на сайт KRAKEN. В адресной строке запущенного браузера введите один из актуальных адресов KRAKEN, указанных выше (например, или ), и перейдите по нему. Будьте внимательны и точно копируйте адрес, чтобы избежать фишинговых сайтов.
Регистрация или авторизация на KRAKEN. На открывшейся главной странице KRAKEN вы сможете создать новую учетную запись, указав уникальный логин и надежный, сложный пароль, или войти в существующий аккаунт KRAKEN, используя свои учетные данные. Настоятельно рекомендуем сразу после регистрации на KRAKEN активировать двухфакторную аутентификацию (2FA) в настройках профиля. Это добавит дополнительный уровень безопасности, требующий ввода одноразового кода при каждом входе, и защитит ваш аккаунт KRAKEN от несанкционированного доступа.
Важные меры безопасности при работе с KRAKEN:
Используйте только свежие ссылки KRAKEN. Адреса зеркал KRAKEN могут обновляться для обеспечения работоспособности и безопасности. Всегда проверяйте их актуальность в проверенных источниках, чтобы избежать мошеннических сайтов, маскирующихся под KRAKEN. Не сохраняйте ссылки в закладках надолго без проверки.
Дополните анонимность VPN для доступа к KRAKEN. Для создания дополнительного, усиленного уровня защиты вашего соединения с KRAKEN рекомендуется использовать надежный VPN-сервис совместно с Tor. Это скроет от вашего интернет-провайдера факт использования сети Tor и добавит еще один шифрованный туннель для вашего трафика, что особенно важно в регионах с повышенным вниманием к подобной активности.
Проверяйте репутацию контрагентов на KRAKEN. Перед совершением любой сделки на KRAKEN внимательно изучайте историю продавца, статистику завершенных сделок и отзывы других пользователей. Надежные продавцы на KRAKEN обычно имеют долгую историю и высокий рейтинг. Это значительно снижает потенциальные риски и помогает избежать мошенничества. Не игнорируйте систему гарантов или условного депонирования (escrow), которую предлагает KRAKEN для защиты покупателей.
Критически оценивайте информацию. Будьте осторожны с предложениями, которые выглядят слишком выгодными, чтобы быть правдой. Используйте внутреннюю систему обмена сообщениями на KRAKEN для уточнения деталей и никогда не переходите к внешним каналам связи по настоянию продавца, так как это стандартная тактика мошенников для обхода защиты площадки KRAKEN.
Почему пользователи выбирают площадку KRAKEN?
Маркетплейс KRAKEN заслужил доверие многочисленной аудитории благодаря сочетанию ключевых факторов. Во-первых, это широкий и разнообразный ассортимент, представленный сотнями продавцов. Во-вторых, интуитивно понятный интерфейс KRAKEN, который упрощает навигацию, поиск товаров и управление заказами даже для новых пользователей. В-третьих, продуманная система безопасных транзакций, включающая механизмы разрешения споров (диспутов) и возможность использования условного депонирования, что минимизирует риски для обеих сторон сделки. На KRAKEN функциональность сочетается с внимательным отношением к безопасности клиентов, что делает процесс покупок более предсказуемым, защищенным и, как следствие, популярным среди пользователей, ценящих анонимность и надежность.
Популярные поисковые запросы, связанные с доступом к KRAKEN:
Быстрый алгоритм действий для доступа к KRAKEN:
1. Установите Tor Browser с официального сайта.
2. Откройте браузер и дождитесь успешного подключения к сети Tor.
3. В адресной строке введите актуальный адрес KRAKEN: https://forum.geeks-rp.ru/threads/9616/
4. Пройдите регистрацию, создав уникальный логин и сложный пароль, или авторизуйтесь в системе KRAKEN.
Немедленно включите двухфакторную аутентификацию в настройках вашего профиля KRAKEN.
Для максимальной анонимности рассмотрите возможность использования VPN-сервиса перед запуском Tor Browser.
Всегда проверяйте репутацию продавца по отзывам и рейтингу перед совершением сделки на KRAKEN.
kraken 13 at РІС…РѕРґ
кракен сайт даркнет
кракен зайти
кракен вход ссылка
кракен сайт зеркало
Your comment is awaiting moderation.
Hi everyone! Check out a solid guide on crypto updates that matter.
It outlines the latest movements in BTC, ETH, and altcoins. Super helpful for crypto fans.
Whether you’re a HODLer or day trader, this write-up will keep you in the loop.
Crypto update
Your comment is awaiting moderation.
Juega Balloon Boom Casino y gana dinero real. Descubre el juego Balloon de SmartSoft Gaming y empieza a ganar premios hoy mismo. https://guides.co/g/balloonjuego/693432
Balloon juego dinero real: apuesta, diviértete y gana en el mejor casino online con Balloon Boom juego online. https://www.walkscore.com/people/314909273877/balloonjuego
Prueba el juego Balloon casino de SmartSoft Gaming y vive la emoción de ganar dinero y premios al instante. https://able2know.org/user/balloonjuego/
Balloon juego de apuestas perfecto para quienes buscan diversión y ganancias reales en un solo lugar. http://www.askmap.net/location/7609941/chile/balloonjuego
Encuentra Balloon Boom dinero real y juega para ganar premios con el auténtico Balloon juego para ganar dinero. https://teletype.in/@balloonjuegocl
Your comment is awaiting moderation.
Yo crypto folks! Just wanted to share a fresh post on latest blockchain insights.
It highlights the key updates in BTC, ETH, and altcoins. A must-see if you follow crypto.
Whether you’re a HODLer or day trader, this resource will give you an edge.
Crypto update
Your comment is awaiting moderation.
Came across vipdubaiagency.com while browsing local companions platforms. The site has a modern design, a extensive range of services, clear pricing, and a hassle-free booking process. It feels more premium than most agencies I’ve encountered. Definitely advisable checking if you wish for all-in-one services in one platform.
URL- https://vipdubaiagency.com/
Your comment is awaiting moderation.
Дом, таунхаус *за этаж https://si-design.ru/hollandpark60m
Этапы разработки дизайна https://si-design.ru/3h-komnatnay-kvartira-moskva-gk-zilart
Авторский надзор https://si-design.ru/vse-o-design
Создаем интерьеры, в которых действительно комфортно жить Удобная эргономика и функциональность пространства, в которое будет включено все самое необходимое: расположение электрических узлов, проходы, расположение кухонной и другой мебели, освещение, как естественное, так и искусственное, местонахождение бытовых устройств https://si-design.ru/balance
Зачем нужны чертежи и какие именно будут в итоговом проекте?
Индивидуально https://si-design.ru/contact
Your comment is awaiting moderation.
Disfruta del Balloon Boom juego online, el casino donde el juego Balloon se convierte en ganancias reales. https://www.hogwartsishere.com/1788844/
Balloon SmartSoft Gaming te ofrece el mejor juego Balloon casino para apostar y ganar dinero de verdad. https://www.producthunt.com/@balloonjuego
Juega Balloon para ganar premios y dinero real en el sitio líder de Balloon Boom Casino. https://www.bark.com/en/gb/company/balloonjuego/LeA9gq/
Balloon juego de apuestas ideal para principiantes y expertos que buscan ganar dinero online. https://www.bandlab.com/balloonjuego
Descubre el juego Balloon ganar premios, apuesta con confianza y gana dinero real con Balloon Boom. https://portfolium.com/balloonjuegocl
Your comment is awaiting moderation.
15 Dragon Pearls is a versatile slot game that adjusts desktop and mobile platforms. Furthermore, punters can enjoy the same high-quality gaming experience regardless of their preferred device. The game is optimised for smooth and responsive gameplay on smartphones and tablets running Android or iOS operating systems. Embark on a mystical journey with Dragon Pearls Hold and Win, an entrancing offering from 3 Oaks Gaming that has captivated players across the realm of online slot games. With its exquisite Asian-inspired theme, the slot’s design intertwines golden dragons and precious pearls, casting a spell of enchantment on all who spin its reels. 15 Dragon Pearls Hold and Win invites players into an Eastern inspired sanctuary adorned with symbols steeped in mythology like dragons, golden trees and lucky coins. The intricate background embroiders a traditional Chinese tapestry, while an immersive soundtrack complements the serene visuals, creating a harmonious balance between sight and sound that transports players to an ancient, mystical realm.
https://www.giftoplastics.com/inside-magius-casino-a-review-for-australian-players/
Where and how to play in an online casino without registering? Try to land three or more scatter symbols on the reels to trigger the bonus round, Just For The Win. This means that you have a better chance of winning when you play the European version, know how much money you can possibly wager. Microgaming is another well-established software provider that has been around since 2023, and read the terms and conditions carefully. 15 dragon pearls online slot machine play for free and with money not all casinos can afford to develop apps for all operating systems, we always recommend reading these so that you’re aware of bonus conditions. Players love bonuses and promotional offers from casinos, this wont be a problem since the UK GC is always watching. Gestoso Design The Japanese Film Festival Australia returns for its landmark 29th year with screenings in Canberra, Melbourne, Brisbane, Sydney and Perth from October to December. Since its inception in 1997, the festival has introduced Australian audiences to the dynamic voices shaping Japanese cinema, and is now one of the largest celebrations of Japanese films in the world.
Your comment is awaiting moderation.
Sugar Rush — Сезон 1 (трейлер) Wij hebben een overzicht gemaakt dat onder meer bestaat uit acteurs, regisseurs, het productie-team, het camera-team, schrijvers en overige crewleden. Klantenrecensies, inclusief sterbeoordelingen voor producten, geven klanten meer informatie over het product en helpen bij de beslissing of dit het juiste product voor hen is. Met uw steun kunnen we boeiendere content creëren en met iedereen delen, of u kunt een aangepast bingospel spelen dat draait om een film of TV-show die uw groep van plan is om te kijken. Echter, maximaal mogelijke winst in sugar rush met verschillende thema’s en inzetlimieten. Gezegend met een binnenzwembad en een fitnessruimte voor recreatie, maar ze maakte al geschiedenis voordat de race zelfs begon. Event Production | Cultural Projects | Stage Management | Show Calling
https://beda88.com/analyse-van-de-populariteit-van-big-bang-slot-van-netent-in-nederland-2/
De tour is kosteloos en in zijn geheel te bekijken op het VR-platform van Show Me Holland. De Jager: “Ik voorzie veel promotionele en educatieve mogelijkheden op basis van dit bronmateriaal, zeker als de linie wordt aangemerkt als Unesco Werelderfgoed. Uiteindelijk wil ik het materiaal onder een Creative Commons-licentie vrijgeven, zodat de foto’s bijvoorbeeld verwerkt kunnen worden in artikelen op Wikipedia of in VR-installaties bij musea getoond kunnen worden. Ik zoek nu een sponsor die dat mogelijk wil maken.” In Mission Uncrossable wordt de uitkomst van elk spel bepaald door drie belangrijke componenten: de server seed, client seed en nonce. Deze elementen werken samen om het resultaat van het spel te genereren via een Random Number Generator (RNG). Het spel levert de server seed, terwijl de client seed uniek is voor elke speler. De nonce is een teller die bij elke actie tijdens het spel wordt verhoogd. Samen zorgen deze factoren voor eerlijkheid en onvoorspelbaarheid, waardoor spelers kunnen controleren of elk spel willekeurig en transparant is.
Your comment is awaiting moderation.
De matrix waarop Sugar Rush 1000 gokkast moet worden gespeeld is een matrix van zeven reels met zeven rijen symbolen. De missie van de speler is om clusters te maken van vijf of meer dezelfde, zoete symbolen. Per ronde moet er een bedrag worden ingelegd van tussen de twintig eurocent en 240 euro en dat bedrag wordt in ongeveer 1 op de 2,9 rondes teruggewonnen. In alle andere rondes wordt het bedrag verloren door de speler. Er zijn ook bepaalde features en bonusrondes waarmee de speler kans maakt op bedragen van maximaal 25 000x de inzet. Daarover hieronder meer. Geniet van 15% korting op je eerste bestelling met code SNK15 – NU WINKELEN Gemiddeld wordt er in 1 op de 2,9 rondes een winst gemaakt bij dit casino spel. Een erg goede tip is om te kijken naar de online casino’s die nieuw zijn, en de blinds en antes blijven op hetzelfde niveau gedurende de duur van het spel. Basisstrategie: Een van de meest effectieve tactieken bij blackjack is het volgen van de basisstrategie, sport.
https://vlbd.brace.tech/divine-fortune-review-een-magische-slotervaring-in-nederland/
CasinoJager is niet de grootste fan van instant win, crash of crypto spellen – hoe je ze ook wil noemen. Niet doordat hij Provably Fair maar vreemd vindt, maar vooral door de saaie gameplay. Elk spel is super repetitief, het enige wat er toe doet, is je uiteindelijke winst. Misschien net daarom dat ze beter bij jonge millennials en GenZ spelers passen. Beide zijn instant casino games waar je met een kip zo ver mogelijk probeert te raken. In Chicken Road gaat het om een kerker met vuur, terwijl Mission Uncrossable een drukke weg heeft. De uitbetalingen lopen bij het tweede spel verder op, terwijl de kans om te overleven hetzelfde is per moeilijkheidsgraad in beide titels. Free spins are a potent tool for testing missions. Mission Uncrossable offers free spin versions, ideal for learning strategies without financial risk. These trials can reveal the game’s depth before committing to paid attempts.
Your comment is awaiting moderation.
Het zonder vergunning aanbieden of promoten van kansspelen is verboden in België. Om te voldoen aan de Belgische wetgeving is deze website niet beschikbaar voor gebruikers in België. Voor meer informatie kunt u terecht op de officiële website van de Kansspelcommissie (KSC). Vraag je je af hoe je dit riskante avontuur moet aanpakken? Chicken Road is een zorgvuldig uitgebalanceerde mix van toeval en tactiek. Je moet beslissen wanneer je je winst verzilvert voordat de vogel een fataal obstakel raakt. Het is meer dan een reflexspel: het is een gok op je eigen dapperheid. Niet zo eenvoudig, toch? Relatietherapie Wat voor fundamentele vragen, gevoelens, intimiteit, en gedragingen spelen in jullie relatie en hoe kan de behandelaar hierin ondersteunen? Wat Hebben jullie financiële conflicten of meningsverschillen over opvoeding? Bestaan…
https://www.giftoplastics.com/big-bang-netent-review-spannend-online-casino-spel-voor-nederlandse-spelers/
Gepubliceerd op 22 mei 2025 U hebt niets in uw winkelwagen. Klantenrecensies, inclusief sterbeoordelingen voor producten, geven klanten meer informatie over het product en helpen bij de beslissing of dit het juiste product voor hen is. } There’s Egg Nog, and then there’s my Egg Nog! Napoleon Dynamite: It matched real life in that students who are different often become the targets of bullying. It’s also believable that a target might invent a dramatic persona in an attempt to protect him herself from bullying. While targets of bullying are often depicted as silent, passive victims, Napoleon’s anger is probably more realistic, since many targets do respond aggressively or attempt to “counter-attack.” Als u hiermee akkoord gaat, gebruiken we ook cookies om uw winkelervaring voor alle Amazon-winkels aan te vullen, zoals beschreven in onze Cookieverklaring. Uw keuze geldt voor het gebruik van uw eigen advertentiecookies en advertentiecookies van derden op deze service. Cookies slaan standaard apparaatinformatie op of hebben toegang tot deze informatie, zoals een unieke identificatiecode. De 111 derden die cookies op deze service gebruiken, doen dit om gepersonaliseerde advertenties weer te geven en te meten, kijkersinzichten te genereren en producten te ontwikkelen en te verbeteren.
Your comment is awaiting moderation.
Erikoistoiminto voi olla myös sattumanvaraisesti käynnistyvä, jolloin se ikään kuin palkitsee pelaajaa tyhjästä kierroksesta täysin ennalta arvaamattomasti. Gates of Olympus ei sisällä erityistä bonuspeliä, sillä ilmaiskierrostoiminto on pelin ainut varsinainen erikoistoiminto. Uusimmat automaattipelit netissä ovat tulleet tutuiksi ostobonus-toiminnosta. Tämä on nostanut suosiotaan erityisesti uuden sukupolven pelaajien keskuudessa. Enää jännitystä ei välttämättä haeta sillä, että yritetään päästä bonuspeliin nappaamalla scatter symboleja tavallisilla kierroksilla. Pelaajien tarvitsee vain kirjautua tileilleen päästäkseen alkuun, jos osallistuisit tähän bonukseen niin kauan kuin siihen liittyvät ehdot ovat suotuisat ja helposti toteutettavissa. Jos olet mobiili kasino-pelaaja, jotka vielä maksaa 3-2 kaikki blackjacks. Koe jännitys kasinopelien lumoavassa ilmapiirissä. Näin ollen sinun tai kenenkään muunkaan ei tarvitse huolehtia piilotetuista asiakirjoista, ole valmis puhumaan ammatistasi.
https://fourwallsbuilding.com/reactoonz-arvostelu-hulvaton-kolikkopeli-suomalaisille/
Ilmoita virheestä bonusehdoissa Vaikka asiakaspalvelu on pääosin erinomaista, joissakin tapauksissa pelaajat ovat raportoineet satunnaista englanninkielistä palvelua, mikä voi olla pieni miinus suomenkielisille pelaajille. kasinon sitoutuminen pelaajien hyvinvointiin näkyy myös vastuullisen pelaamisen osiossa, mutta konkreettiset työkalut, kuten pelirajat, ovat rajalliset. Silti asiakastuki on valmis auttamaan esimerkiksi pelitilin sulkemisessa. Shokki kasinon asiakaspalvelu on luotettava ja nopea, joten apua on saatavilla aina, kun sitä tarvitset. Rekisteröidy valitsemallesi kasinolle saadaksesi tervetuliaisbonuksen (jos sellainen on). Ryhtymällä uuden online-kasinon kokopäiväiseksi jäseneksi olet oikeutettu kaikkiin seuraaviin kampanjoihin. 100 % 500€ + 50x Gates of Olympus 1000
Your comment is awaiting moderation.
Доставка на 10 персон https://shcherbinins.ru/aboutus
Вы также можете самостоятельно сформировать меню, выбрав подходящие блюда в нашем каталоге https://shcherbinins.ru/uslugy
Как заказать услугу кейтеринга?
Наш опытный персонал гарантирует высокое качество блюд и обслуживания https://shcherbinins.ru/menu
Мы следим за каждой деталью, чтобы ваше мероприятие прошло идеально https://shcherbinins.ru/uslugy
Наши услуги включают:
933 руб./чел https://shcherbinins.ru/
Прекрасные ребята: обязательные, дружелюбные, идут на встречу! Еда вкусная и подача очень интересная! Однозначно – “да”!
Your comment is awaiting moderation.
Spillutvikleren Pragmatic Play er ledende på spilleautomater, og Gates of Olympus har lenge vært en favoritt. Oppfølgeren Gates of Olympus 1000 er også interessant. Les spillanmeldelsen hos NorgeKasino. SlotsGem Norge er et helt nytt casino i 2025 som byr på et rikt utvalg spill og generøse bonuser. De har gått for et moderne design som gjør det enkelt å utforske hele utvalget av spill. Her finner du alt fra tradisjonelle spilleautomater til bordspill, kortspill og et live casino for alle ferdighetsnivåer. De lanserte raskt siden sin for norske spillere og byr på en rekke muligheter. Gjennom vår SlotsGem anmeldelse deler vi all vår erfaring og hva du trenger å vite før du oppretter en konto. Ja, Rolletto Casino anses som trygt å spille på. Det er lisensiert og regulert av myndighetene i Curacao, og bruker moderne krypteringsteknologier for å beskytte din informasjon og dine transaksjoner .
https://learnifyit.com/gate-of-olympus-en-grundig-gjennomgang-av-pragmatic-plays-populaere-spilleautomat/
Playtech oppgir at Age of the Gods: King of Olympus har middels volatilitet. Velger du et av de beste Jackpot 6000 casinoene kan du ofte få en Jackpot 6000 bonus som øker saldoen din. Det er ikke garantert at du får Jackpot 6000 free spins, men bonuspengene du får fra en velkomstbonus kan likevel brukes i spillet. Bonuser gir deg enda mer spilletid og dermed flere sjanser til å nå Supermeter og jackpot. Husk å lese bonusvilkårene, så du slipper å møte på begrensninger ved uttak. Velger du et av de beste Jackpot 6000 casinoene kan du ofte få en Jackpot 6000 bonus som øker saldoen din. Det er ikke garantert at du får Jackpot 6000 free spins, men bonuspengene du får fra en velkomstbonus kan likevel brukes i spillet. Bonuser gir deg enda mer spilletid og dermed flere sjanser til å nå Supermeter og jackpot. Husk å lese bonusvilkårene, så du slipper å møte på begrensninger ved uttak.
Your comment is awaiting moderation.
Bonuses
battery aviator
Your comment is awaiting moderation.
Vale a tentativa, desde que o usuário leia com atenção os termos, aposte com responsabilidade e selecione sites confiáveis com bônus sem depósito legítimo. Trata-se de uma excelente porta de entrada para o universo das apostas online no Brasil. Hoje você terá acesso a esse famoso jogo de slot que faz referência ao épico Indiana Jones e outros filmes de aventura com o tema do Antigo Egito e está disponível nos melhores sites de cassino online. Confira abaixo tudo o que precisa saber para participar deste desafio. Dor no calcanharEsporão de calcâneoFascite PlantarInsuficiência do Tibial PosteriorDoença de Sever You can email the site owner to let them know you were blocked. Please include what you were doing when this page came up and the Cloudflare Ray ID found at the bottom of this page.
https://jivasendriya.com/why-betonred-casino-portugal-pt-casino-online-portal-is-a-top-choice/
Quando falamos nos cassinos com saque rápido no Brasil, nos referimos às plataformas de jogos online que priorizam a agilidade no processamento de retiradas. Para isso, oferecem métodos de pagamento que permitem concluir saques em poucas horas ou até minutos. A Rivalo é uma excelente escolha para quem busca cassinos online com retiradas rápidas e operação confiável. A plataforma oferece um ambiente seguro, com jogos de cassino disponíveis em versão demo para quem deseja explorar antes de usar saldo real. Além de toda a temática envolvente, o jogo Book of Dead, oferece dois recursos especiais que fazem toda a diferença na hora de jogar. O primeiro deles é a aposta extra, cujo recurso, quando ativado, possibilita ao jogador arriscar os seus ganhos, tentando dobrá-los. Funciona como uma espécie de “dobro ou nada”.
Your comment is awaiting moderation.
Juega Balloon Boom Casino y gana dinero real. Descubre el juego Balloon de SmartSoft Gaming y empieza a ganar premios hoy mismo. https://devpost.com/balloonjuegocl
Balloon juego dinero real: apuesta, diviértete y gana en el mejor casino online con Balloon Boom juego online. https://www.reverbnation.com/artist/balloonjuego
Prueba el juego Balloon casino de SmartSoft Gaming y vive la emoción de ganar dinero y premios al instante. https://maxforlive.com/profile/user/balloonjuego?tab=about
Balloon juego de apuestas perfecto para quienes buscan diversión y ganancias reales en un solo lugar. https://coub.com/balloonjuego
Encuentra Balloon Boom dinero real y juega para ganar premios con el auténtico Balloon juego para ganar dinero. https://www.deviantart.com/balloonjuego
Your comment is awaiting moderation.
CANADA PHARMACY online pharmacy Prescription Cialis, Cheap Cialis From Canada – Online Pharmacy canadian pharmacy no prescription Cialis generico prezzo piu basso pharmacy – definition of pharmacy in the Medical dictionary – by Viagra costco pharmacy. buy alli online Buy CIALIS Online :: 10 Bonus FREE Pills ! Lowest Prices For Sildenafil, Cheapest Viagra Price
Your comment is awaiting moderation.
Disfruta del Balloon Boom juego online, el casino donde el juego Balloon se convierte en ganancias reales. https://www.wikidot.com/user:info/balloonjuego
Balloon SmartSoft Gaming te ofrece el mejor juego Balloon casino para apostar y ganar dinero de verdad. https://files.fm/balloonjuegocl/info
Juega Balloon para ganar premios y dinero real en el sitio líder de Balloon Boom Casino. https://sketchfab.com/balloonjuego
Balloon juego de apuestas ideal para principiantes y expertos que buscan ganar dinero online. https://doodleordie.com/profile/balloonjuego
Descubre el juego Balloon ganar premios, apuesta con confianza y gana dinero real con Balloon Boom. https://coub.com/balloonjuego
Your comment is awaiting moderation.
Our 15 Dragon Pearls review found this highly satisfying game thanks to its exciting visuals and many bonus features. In addition to a free spins Hold & Win round and the offering of sizable cash wins through the Pearl feature, players have the chance to win a jackpot valued at up to $200,000. Our overall score for this game is 4.7 stars out of 5. Casino Rules For Roulette Quantum Roulette is not the type of game you can form a strategy for, windows. Play 15 dragon pearls slot online here is implemented an interactive survey and the mechanism inherent in the games RNG, and linux computer laptop and also has a mobile interface. 500% Deposit Match Up To $2,500 + 150 Free Spins Original NOVOMATIC Social Slots Its main offices, Roberts has a plethora of experience and would be well-suited for the role. You can play Temple of Ausar Jackpot without restrictions in demo mode on our website, Popular Games. Types of no deposit bonuses at the casino.
https://www.kanghanrak.net/?p=614850
In this 15dragonpearlsgame article, we’ll delve into the world of Dragon Pearls, analyzing its various aspects to provide you with an informed decision on whether it’s worth your time and money. We’ll explore its mechanics, bonus rounds, payouts, and more, rating each aspect from 1-5 to give you a comprehensive understanding of what this game has to offer. I have noticed that charges for on-line degree specialists tend to be an excellent value. Like a full Bachelor’s Degree in Communication from The University of Phoenix Online consists of 60 credits with $515 credit or $30,900. Also American Intercontinental University Online gives a Bachelors of Business Administration with a full education course requirement of 180 units and a worth of $30,560. Online learning has made obtaining your degree so much easier because you could earn your own degree in the comfort of your dwelling place and when you finish from work. Thanks for all the tips I’ve learned through the site.
Your comment is awaiting moderation.
Почему пользователи выбирают площадку KRAKEN?
Маркетплейс KRAKEN заслужил доверие многочисленной аудитории
благодаря сочетанию ключевых факторов.
Во-первых, это широкий и разнообразный
ассортимент, представленный сотнями продавцов.
Во-вторых, интуитивно понятный интерфейс KRAKEN, который упрощает навигацию,
поиск товаров и управление заказами даже для
новых пользователей. В-третьих, продуманная система безопасных транзакций,
включающая механизмы разрешения споров (диспутов)
и возможность использования условного
депонирования, что минимизирует риски для обеих
сторон сделки. На KRAKEN функциональность сочетается с внимательным отношением
к безопасности клиентов, что делает процесс покупок более предсказуемым, защищенным и,
как следствие, популярным среди пользователей, ценящих анонимность и надежность.
Your comment is awaiting moderation.
Came across vipdubaiagency.com while browsing local entourage platforms. The site has a modern design, a wide range of services, easy-to-understand pricing, and a simple booking process. It feels more premium than most agencies I’ve encountered. Definitely recommended checking if you are looking for comprehensive services in one platform.
Check it: https://vipdubaiagency.com/
Your comment is awaiting moderation.
Disfruta del Balloon Boom juego online, el casino donde el juego Balloon se convierte en ganancias reales. https://www.elephantjournal.com/profile/balloonjuegocl/
Balloon SmartSoft Gaming te ofrece el mejor juego Balloon casino para apostar y ganar dinero de verdad. https://tooter.in/balloonjuego
Juega Balloon para ganar premios y dinero real en el sitio líder de Balloon Boom Casino. https://leetcode.com/u/balloonjuego/
Balloon juego de apuestas ideal para principiantes y expertos que buscan ganar dinero online. https://teletype.in/@balloonjuegocl
Descubre el juego Balloon ganar premios, apuesta con confianza y gana dinero real con Balloon Boom. https://myanimelist.net/profile/balloonjuego
Your comment is awaiting moderation.
DA PA MOZ) Topchik
https://t10.org/cgi-bin/s_t10r.cgi?First=1&PrevURL=https%3A%2F%2Fairvission.ru
https://www.hawaiitourismauthority.org/speedbump/?targetUrl=https%3A%2F%2Fairvission.ru
https://secure.nationalimmigrationproject.org/np/clients/nationalimmigration/tellFriend.jsp?subject=Attending%202020+Annual+Pre-AILA+Crimes+and+Immigration+Virtual+CLE&url=http%3A%2F%2Fairvission.ru
https://www.hcsparta.cz/media_show.asp?type=1&id=246&url_back=http%3A%2F%2Fairvission.ru
https://www.drugs.ie/?URL=airvission.ru
https://forum.reizastudios.com/proxy.php?link=http%3A%2F%2Fairvission.ru
https://www.webclap.com/php/jump.php?sa=t&url=http%3A%2F%2Fairvission.ru%2F
https://app.nexoos.com.br/mkt/borrower/registration_wizard/partner_redirection?link=https%3A%2F%2Fairvission.ru&partner=geru
https://semanticweb.cs.vu.nl/linkedatm/browse/list_resource?r=http%3A%2F%2Fairvission.ru
https://syaoruu.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://account.everygame.eu/en/home/cashier?returnUrl=https%3A%2F%2Fairvission.ru
https://www.kidsemail.org/parent-login.php?msg=%3Ca%20href%3D%22https%3A%2F%2Fairvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://sat.issprops.com/?URL=airvission.ru/
https://www.wenxuecity.com/blog/?act=haiwai_blog&url=http%3A%2F%2Fairvission.ru
https://www.vanderbiltcupraces.com/?URL=http%3A%2F%2Fairvission.ru
https://www.cleanlink.com/adviewer.asp?adi=/hs/graphics/19/10/019_HS_1019&p=hs1019-019-MatsInc&e=website%20%5Bat%5D%20cleanlink%20%5Bdot%5D%20com&u=https%3A%2F%2Fairvission.ru
https://www6.topsites24.de/safety.php?url=https%3A%2F%2Fairvission.ru
https://content.hh.ru/api/v1/click?contentId=538&placeId=2&employerId=581458&domainAreaId=1353&host=https%3A%2F%2Fairvission.ru
https://forums.techarp.com/proxy.php?link=http%3A%2F%2Fairvission.ru
https://www.bing.com/news/apiclick.aspx?ref=FexRss&aid=&tid=60610D15439B4103A0BF4E1051EDCF8B&url=https%3A%2F%2Fairvission%2F&c=12807976268214810202&mkt=en-us
https://rs.rikkyo.ac.jp/rs/error/ApplicationError.aspx?TopURL=https%3A%2F%2Fairvission.ru
https://dailyhoroscopeplus.onelink.me/kLrr?pid=app_share&c=test&af_web_dp=http%3A%2F%2Fairvission.ru
https://www.chara-ani.com/member_rule.aspx?src=https%3A%2F%2Fairvission.ru
https://fdp.timacad.ru/bitrix/redirect.php?event1&event2&event3&goto=http%3A%2F%2Fairvission.ru/
https://inginformatica.uniroma2.it/?URL=airvission.ru
https://tm.dl.stimme.de/tm/a/channel/tracker/d38ae3b7df?navigation=Leser+werben+Leser&tmrde=https%3A%2F%2Fairvission.ru
https://wiki.securepoint.de/index.php?title=%2Fairvission.ru&action=edit&printable=yes
https://kikaku.s54.xrea.com/cgi-bin/kanon2/romnavi.cgi?jump=1374&url=http%3A%2F%2Fairvission.ru
https://pram.elmercurio.com/Logout.aspx?ApplicationName=EMOL&SSOTargetUrl=https%3A%2F%2Fairvission.ru%2F&l=yes
https://dados.ibict.br/pt_PT/api/1/util/snippet/api_info.html?resource_id=2ace6719-6b73-4285-b349-49dbbaa7de53&datastore_root_url=http%3A%2F%2Fairvission.ru
https://galacy-mountain.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://ijpc.uscannenberg.org/?URL=http%3A%2F%2Fairvission.ru
https://forward.zillertal.at/?url=https%3A%2F%2Fairvission.ru
https://vakbarat.index.hu/x.php?id=inxtc&url=airvission.ru
https://vtambove.ru/go_links.php?http:/airvission.ru
https://icdn.ymcacharlotte.org/CDN/Index?ImageUrl=https%3A%2F%2Fairvission.ru&Width=320
https://www.pearlevision.com/m20ScheduleExamView?catalogId=15951&clearExams=1&langId=-1&returnUrl=http%3A%2F%2Fairvission.ru&storeId=12002&storeNumber=21129027
https://www.thetfp.com/proxy.php?link=http%3A%2F%2Fairvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://memo8.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://nick.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://www.oddworld.com/_shop/shop.php?store=airvission.ru
https://www.ub.uni-heidelberg.de/cgi-bin/edok?dok=https%3A%2F%2Fairvission.ru
https://captcha.2gis.ru/form?return_url=https%3A%2F%2Fairvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://forums.qrz.com/proxy.php?link=https%3A%2F%2Fairvission.ru
https://freewebsitetemplates.com/proxy.php?link=https%3A%2F%2Fairvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://daemon.indapass.hu/http/session_request?redirect_to=https%3A%2F%2Fairvission.ru%2F&partner_id=bloghu
https://www.bovec.net/redirect.php?link=airvission.ru/&un=reedw.cf&from=bovecnet
https://my.icaew.com/security/Account/Logout?returnUrl=https%3A%2F%2Fairvission.ru
https://daemon.indapass.hu/http/session_request?redirect_to=http%3A%2F%2Fairvission.ru&partner_id=bloghu
https://auth.she.com/logout/?callback=http%3A%2F%2Fairvission.ru&client_id=8
https://participez.nanterre.fr/link?external_url=https%3A%2F%2Fairvission.ru
https://www.wellness.com/Version/Full?returnUrl=http%3A%2F%2Fairvission.ru
https://wiki.bzflag.org/index.php?title=%2Fairvission.ru&action=edit&printable=yes
https://marublog129.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://trustandjustice.org/?URL=https%3A%2F%2Fairvission.ru
https://associate.foreclosure.com/scripts/t.php?a_aid=20476&a_bid&desturl=https%3A%2F%2Fairvission.ru
https://digiex.net/proxy.php?link=https%3A%2F%2Fairvission.ru
https://trac.osgeo.org/osgeo/search?q=https%3A%2F%2Fairvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://bnb.easytravel.com.tw/click.aspx?no=3835&class=1&item=1001&area=6&url=http%3A%2F%2Fairvission.ru
https://www.math.auckland.ac.nz/wiki/index.php?search=https%3A%2F%2Fairvission.ru&title=Special%3ASearch&go=Go
https://drugs.ie/?URL=https%3A%2F%2Fairvission.ru
https://show.jspargo.com/attendeeAcquisitionTool/src/tracking10click.asp?caller=attAcqWidget&widgetId=61&redirectUrl=http%3A%2F%2Fairvission.ru
https://2015.adfest.by/banner/redirect.php?url=http%3A%2F%2Fairvission.ru
https://www.unifrance.org/newsletter-click/6763261?url=http%3A%2F%2Fairvission.ru
https://www.db.lv/ext/http:%2F%2Fairvission.ru
https://kanten-papa.kir.jp/ranklink/rl_out.cgi?id=7200&url=http%3A%2F%2Fairvission.ru
https://www.kh-vids.net/proxy.php?link=http%3A%2F%2Fairvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://my.w.tt/a/key_live_pgerP08EdSp0oA8BT3aZqbhoqzgSpodT?medium=&feature=&campaign=&channel=&%24always_deeplink=0&%24fallback_url=airvission.ru&%24deeplink_path=
https://quilter.s8.xrea.com/cgi-bin/downcnt.cgi?url=http%3A%2F%2Fairvission.ru
https://ssbsync-global.smartadserver.com/api/sync?callerId=5&gdpr=null&gdpr_consent=&us_privacy=&redirectUri=https%3A%2F%2Fairvission.ru
https://www.golfselect.com.au/redirect?activityType_cd=WEB-LINK&course_id=2568&tgturl=https%3A%2F%2Fairvission.ru
https://sorakawa.s202.xrea.com/yomi/rank.php?mode=link&id=1358&url=http%3A%2F%2Fairvission.ru
https://paulgravett.com/?URL=airvission.ru/
https://soundingames.dei.uc.pt/api.php?action=https%3A%2F%2Fairvission.ru/%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9/
https://supertramp.com/?URL=airvission.ru
https://lucid.s28.xrea.com/dmm/?t=Fleeting+Diary&l=https%3A%2F%2Fairvission.ru&i=5479mrbls00069&imageURL=&s=dmm
https://mana310.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://www25.ownskin.com/wap_theme_download.oss?c=3&h=airvission.ru
https://idoooll.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://m.shopinlosangeles.net/redirect.aspx?url=https%3A%2F%2Fairvission.ru
https://es.catholic.net/ligas/ligasframe.phtml?liga=https%3A%2F%2Fairvission.ru
https://beeyann.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://plantationfl.adventistchurch.org/forwarder/part1?url=https%3A%2F%2Fairvission.ru
https://adx.dcfever.com/ads/www/delivery/ck.php?ct=1&oaparams=2__bannerid=1138__zoneid=2__cb=a4d7c48ece__oadest=http%3A%2F%2Fairvission.ru
https://cas.rec.unicen.edu.ar/cas/login?gateway=true&service=https%3A%2F%2Fairvission.ru
https://gun.deals/external-link?url=http%3A%2F%2Fairvission.ru
https://sso.qiota.com/api/v1/logout?redirect_uri=https%3A%2F%2Fairvission.ru
https://www.bausch.co.jp/redirect/?url=https%3A%2F%2Fairvission.ru
https://www.db.lv/ext/http%3A%2F%2Fairvission.ru/
https://secure.radio-online.com/cgi-bin/rol.exe/ssiteid?airvission.ru
https://www.maritimeclassiccars.com/redirect.php?id=48&url=http%3A%2F%2Fairvission.ru
https://www.bdsmlibrary.com/tgpx/click.php?id=4300&u=http%3A%2F%2Fairvission.ru&category=Lesbian&description=WhippedAss%20begins%20more%20girl/girl
https://forum.winhost.com/proxy.php?link=http%3A%2F%2Fairvission.ru
https://www.ville-ge.ch/web-newsletter/newsletter_vdg/go/qui.php?l=616:1850&c=https%3A%2F%2Fairvission.ru
https://wiki.code4lib.org/index.php?title=%2Fairvission.ru&action=history&printable=yes
https://prlog.ru/analysis/airvission.ru
https://track.pubmatic.com/AdServer/AdDisplayTrackerServlet?clickData=JnB1YklkPTE3NDEwJnNpdGVJZD0xNzQxMSZhZElkPTEyMTgyJmthZHNpemVpZD03JmNhbXBhaWduSWQ9NjI0MiZjcmVhdGl2ZUlkPTAmYWRTZXJ2ZXJJZD0yNDM=_url=https%3A%2F%2Fairvission.ru
https://www.fahrradmonteur.de/index.php?title=/airvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F&action=edit&printable=yes
https://forums.sonicretro.org/proxy.php?link=http%3A%2F%2Fairvission.ru
https://new.theinfosphere.org/index.php?title=%2Fairvission.ru&action=edit&printable=yes
https://mail2.mclink.it/SRedirect/airvission.ru
https://virtuafighter.com/proxy.php?link=https%3A%2F%2Fairvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://www.studyladder.com/games/activity/word-match-s-a-t-p-i-n-35665?backUrl=http%3A%2F%2Fairvission.ru
https://rinbro.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://hudsonltd.com/?URL=airvission.ru
https://cities.bythenumbers.sco.ca.gov/embed/barchart?branch_type=revenue¤t_entity=org1&year=2020&child_entity=org2&org1=Yuba%2BCity&sort_field=total&sort=desc&is_leaf=false&human_name=City&sourceUrl=https%3A%2F%2Fairvission.ru&type=content
https://sekainoriron.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://forums.officialpsds.com/proxy.php?link=https%3A%2F%2Fairvission.ru
https://forum.studio-397.com/proxy.php?link=https%3A%2F%2Fairvission.ru
https://bodyblow.s9.xrea.com/x/cutlinks/rank.php?url=http%3A%2F%2Fairvission.ru
https://www.talgov.com/Main/exit?url=https%3A%2F%2Fairvission.ru
https://ai.blackfacts.com/redirect/FactSource/13d1ce12-1229-404b-bf31-8bdda75b7d55/03290b70-9a99-489b-a7fa-318ae1b60a6e/https%3A%2F%2Fairvission.ru
https://auth.mindmixer.com/GetAuthCookie?returnUrl=http%3A%2F%2Fairvission.ru
https://computing.ece.vt.edu/mediawiki/api.php?action=https%3A%2F%2Fairvission.ru
https://woostercollective.com/?URL=airvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://studenthelpr.com/redirect?redirectTo=http%3A%2F%2Fairvission.ru
https://archive.paulrucker.com/?URL=airvission.ru/
https://www23.ownskin.com/wap_theme_download.oss?c=11&h=airvission.ru
https://m.shopinportland.com/redirect.aspx?url=airvission.ru
https://www.fcslovanliberec.cz/media_show.asp?type=1&id=543&url_back=https%3A%2F%2Fairvission.ru
https://suecia.kb.se/goto/http:/airvission.ru/
https://partner.maisonsdumonde.com/servlet/effi.redir?id_compteur=22797254&url=https%3A%2F%2Fairvission.ru
https://passport-us.bignox.com/sso/logout?service=http%3A%2F%2Fairvission.ru
https://sites.estvideo.net/video/phpinfo.php?a%5B%5D=best+delta+8+hemp+flowers+%28%3Ca+href%3Dhttps%3A%2F%2Fairvission.ru
https://www.plagscan.com/highlight?cite=1&doc=117798730&source=16&url=https%3A%2F%2Fairvission.ru
https://forum.mobile-networks.ru/go.php?http%3A%2F%2Fairvission.ru
https://www.adminer.org/redirect/?url=https%3A%2F%2Fairvission.ru&lang=en
https://kanose.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://www.etcconnect.com/logout.aspx?bc_ReturnURL=https%3A%2F%2Fairvission.ru
https://passport-us.bignox.com/sso/logout?service=http%3A%2F%2Fwww.airvission.ru
https://rezkyrizani.xtgem.com/fb_/text_lingkaran?site=airvission.ru<
https://www.survivalmonkey.com/proxy.php?link=https%3A%2F%2Fairvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://wiki.chem.gwu.edu/default/api.php?action=http%3A%2F%2Fairvission.ru
https://lospoblanos.com/?URL=http%3A%2F%2Fairvission.ru
https://www.decidim.barcelona/link?external_url=https%3A%2F%2Fairvission.ru
https://priuschat.com/proxy.php?link=https%3A%2F%2Fairvission.ru
https://www.searchdaimon.com/?URL=airvission.ru/
https://cpen.com/?url=https%3A%2F%2Fairvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://www.ufps.edu.co/ufps/atencionalciudadano/pdf.php?pdf=https%3A%2F%2Fairvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://submit.jpmph.org/member/s_login.php?s_login=11&s_url=http%3A%2F%2Fairvission.ru
https://envios.uces.edu.ar/control/click.mod.php?email=%7B%7Bemail%7D%7D&id_envio=1557&url=https%3A%2F%2Fairvission.ru/
https://cr.naver.com/redirect-notification?u=https%3A%2F%2Fairvission.ru
https://decidim.calafell.cat/link?external_url=http%3A%2F%2Fairvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://www.kichink.com/home/issafari?uri=http%3A%2F%2Fairvission.ru/
https://forum.corvusbelli.com/proxy.php?link=https%3A%2F%2Fairvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://www.kankomie.or.jp/banner_click?id=298&url=https%3A%2F%2Fairvission.ru
https://forums.kustompcs.co.uk/proxy.php?link=https%3A%2F%2Fairvission.ru
https://www.oxfordpublish.org/?URL=airvission.ru/
https://popjulia.onelink.me/COvz?pid=pc-bottom&c=home&af_dp=com.chicv.popjulia%3A%2F%2F&af_web_dp=http%3A%2F%2Fairvission.ru&is_retargeting=true
https://click.simsfinds.com/go?url=http%3A%2F%2Fairvission.ru
https://ad.inter-edu.com/ox/www/delivery/ck.php?ct=1&oaparams=2__bannerid%3D43467__zoneid%3D286__OXLCA%3D1__cb%3D04acee1091__oadest%3Dhttps%3A%2F%2Fairvission.ru
https://decidimos.monterrey.gob.mx/link?external_url=https%3A%2F%2Fairvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://fffw2.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://login.uleth.ca/cas/login?service=https%3A%2F%2Fairvission.ru%2F&gateway=true
https://adsfac.net/search.asp?url=http%3A%2F%2Fairvission.ru
https://ofsilvers.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://optimize.viglink.com/page/pmv?url=https%3A%2F%2Fairvission.ru
https://cm-eu.wargaming.net/frame/?service=frm&project=moo&realm=eu&language=en&login_url=http%3A%2F%2Fairvission.ru
https://lacplesis.delfi.lv/adsAdmin/redir.php?cid=c3_26488405&cimg&cname=Oli&u=http%3A%2F%2Fairvission.ru&uid=washingtondds22.blogspot.com%2F439888washingtondds22.blogspot.com%2F98
https://aoisakana5.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://kintsugi.seebs.net/proxy.php?link=https%3A%2F%2Fairvission.ru
https://beta.novell.com/common/util/get_language_url.php?language=en-us&url=http%3A%2F%2F/airvission.ru
https://adms.hket.com/openxprod2/www/delivery/ck.php?ct=1&oaparams=2__bannerid=6685__zoneid=2040__cb=dfaf38fc52__oadest=http%3A%2F%2Fairvission.ru
https://kettypay.hatenadiary.com/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://cr.naver.com/redirect-notification?u=http%3A%2F%2Fwww.www.airvission.ru/%2F%E2%80%8E
https://www.skisprungschanzen.com/link.php?id=2&url=http%3A%2F%2Fairvission.ru
https://community.restaurant.org/links?url=https%3A%2F%2Fairvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://love.goxip.com/hk/affiliate?url=http%3A%2F%2Fairvission.ru
https://chyba.o2.cz/cs/?url=https%3A%2F%2Fairvission.ru
https://jump.5ch.net/?airvission.ru
https://eventlog.netcentrum.cz/redir?data=aclick2c239800-486339t12&s=najistong&url=https%3A%2F%2Fairvission.ru&v=1
https://wiki.zcubes.com/index.php?title=%2Fairvission.ru&action=edit&printable=yes
https://adsnew.hostreview.com/openx_new/www/delivery/ck.php?ct=1&oaparams=2__bannerid=1110__zoneid=14__cb=34519e1b0c__maxdest=https%3A%2F%2Fairvission.ru
https://www.retrogames.cz/download_DOS.php?id=714&ROMfile=http%3A%2F%2Fairvission.ru&IMGsize=512
https://pl.grepolis.com/start/redirect?url=http%3A%2F%2Fairvission.ru
https://fetchyournews.com/revive/www/delivery/ck.php?oaparams=2__bannerid=458__zoneid=43__cb=1931d27daa__oadest=http%3A%2F%2Fairvission.ru
https://www.storeboard.com/profile/show_webpage_profile.asp?url=http%3A%2F%2Fairvission.ru
https://almanach.pte.hu/oktato/273?from=http%3A%2F%2Fairvission.ru
https://siid.insp.mx/redirect?url=%2F%2Fairvission.ru
https://board-en.drakensang.com/proxy.php?link=http%3A%2F%2Fairvission.ru
https://dog.s334.xrea.com/dti/?text=%E6%9C%89%E6%B5%A6%E7%95%99%E7%BE%8E&url=http%3A%2F%2Fairvission.ru&pic=https%3A%2F%2Fwww.caribbeancompr.com%25
https://m.wedkuje.pl/_mobile/_redirect.php?redir=http%3A%2F%2Fairvission.ru
https://chtbl.com/track/118167/https:/airvission.ru
https://www.cashfiesta.com/php/redir.php?ms&201206wl&5671826&c?https%3A%2F%2Fairvission.ru
https://empyriononline.com/proxy.php?link=https%3A%2F%2Fairvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://lr2.lsm.lv/lv/lr2/?rt=site&ac=socclick&lnk=http%3A%2F%2Fairvission.ru&r=1&acc=youtube
https://newsletter.usi.ch/email/n?h=2obmeqV6fSqh5ZdQ0zugSbZMYMrMfiYL&l=%2F%2Fairvission.ru
https://tokyo.new-akiba.com/ra/www/delivery/ck.php?ct=1&oaparams=2__bannerid=3__zoneid=3__cb=154a423fea__oadest=https%3A%2F%2Fairvission.ru
https://framinghamlibrary.org/?URL=airvission.ru
https://passport-us.bignox.com/sso/logout?service=https%3A%2F%2Fairvission.ru%2F
https://gogvo.com/redir.php?k=d58063e997dbb039183c56fe39ebe099&url=https%3A%2F%2Fairvission.ru%2F
https://gml-grp.com/C.ashx?btag=a_6094b_435c_&affid=901&siteid=6094&adid=435&asclurl=http%3A%2F%2Fairvission.ru&AutoR=1
https://www.constructionenquirer.com/wp-content/themes/constructionenquirer/adclick.php?url=http%3A%2F%2Fairvission.ru
https://pro.obesityhelp.com/tracked/?r=airvission.ru&id=profile_website_10001
https://www.online-image-editor.com/index.cfm?fa=download_file&image_path=airvission.ru
https://tools.folha.com.br/print?url=http%3A%2F%2Fwww.airvission.ru
https://nabchelny.ru/welcome/blindversion/normal?callback=http%3A%2F%2Fairvission.ru
https://www.2banh.vn/redirect/?url=https%3A%2F%2Fairvission.ru/
https://forum.doctissimo.fr/inscription-1.html?referer_url=https%3A%2F%2Fairvission.ru
https://www.freeseotoolbox.net/domain/airvission.ru/update
https://vortez.net/revive2/www/delivery/ck.php?ct=1&oaparams=2__bannerid=96__zoneid=7__cb=7b05f93fa3__oadest=http%3A%2F%2Fairvission.ru
https://amk-team.ru/go/?url=https%3A%2F%2Fairvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://littlenugget.onelink.me/1071849834?pid=Sponsorship&c=BCBVIP&af_dp=littlenugget%3A%2F%2F&af_web_dp=http%3A%2F%2Fairvission.ru
https://www.talgov.com/Main/exit?url=https%3A%2F%2Fairvission.ru%E2%80%8E
https://6giay.vn/proxy.php?link=http%3A%2F%2Fairvission.ru
https://reporting.sainsburysmagazine.co.uk/cgi-bin/rr/nobook:151187nosent:64962nosrep:93621/https:/airvission.ru
https://domain.opendns.com/airvission.ru
https://dot.wp.pl/redirn?SN=facebook_o2&t=1628334247&url=https%3A%2F%2Fairvission.ru%2F
https://islam.de/ms?r=https%3A%2F%2Fairvission.ru
https://sp.jp.wazap.com/info/jump.wz?url=https%3A%2F%2Fairvission.ru
https://tinhte.vn/proxy.php?link=http%3A%2F%2Fairvission.ru
https://adms3.hket.com/openxprod2/www/delivery/ck.php?ct=1&oaparams=2__bannerid=527__zoneid=667__cb=72cbf61f88__oadest=http%3A%2F%2Fairvission.ru
https://decidim.santcugat.cat/link?external_url=https%3A%2F%2Fairvission.ru
https://gochiemon.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://maheev.perm.ru/bitrix/rk.php?goto=http%3A%2F%2Fairvission.ru
https://www.hogodoc.com/?URL=airvission.ru/
https://w1.websnadno.cz/index.php?menu1r=2&stiznost=true&surl=airvission.ru&sreferer=
https://hchocolatier.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=http%3A%2F%2Fairvission.ru
https://smart.link/5bb788a3d5b83?site_id=Web_NBCS_Philly&creative_id=nbcsphi1356&cp_4=airvission.ru
https://vdigger.com/downloader/downloader.php?utm_nooverride=1&site=airvission.ru
https://forums.opera.com/outgoing?url=http%3A%2F%2Fairvission.ru
https://forums.fugly.com/proxy.php?link=http%3A%2F%2Fairvission.ru
https://innerside.dothome.co.kr/bbs/skin/link/hit_plus.php?sitelink=http%3A%2F%2Fairvission.ru&id=link&page=1&sn1=&divpage=1&category=2&sn=off&ss=on&sc=on&select_arrange=headnum&desc=asc%20&no=4
https://www.emuparadise.me/logout.php?next=https%3A%2F%2Fairvission.ru
https://s03.megalodon.jp/?url=http%3A%2F%2Fairvission.ru/
https://masaru323.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://nabat.tomsk.ru/go/url=https:/airvission.ru
https://the-take.com/?URL=https%3A%2F%2Fairvission.ru
https://webservices.lib.uconn.edu/webapps/dcompass/tempbin/newreferer.php?URL=https%3A%2F%2Fairvission.ru
https://www.kichink.com/home/issafari?uri=http%3A%2F%2Fairvission.ru/%2F
https://osallistu.ouka.fi/link?external_url=https%3A%2F%2Fairvission.ru
https://px.owneriq.net/eoptout?redir=http%3A%2F%2Fairvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://link.d24am.com/?link=http%3A%2F%2Fairvission.ru
https://eflyers.revolution-bars.co.uk/2012/head-office/may/jubilee-newsletter/?c=airvission.ru
https://cds.zju.edu.cn/addons/cms/go/index.html?url=https%3A%2F%2Fairvission.ru
https://maximal-life.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://dreamerdream.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://ads1.opensubtitles.org/1/www/delivery/afr.php?zoneid=3&cb=984766&query=One+Froggy+Evening&landing_url=http%3A%2F%2Fairvission.ru
https://rakugakiya.s28.xrea.com/cgi/meiboa/ezlinka.php?mode=jump&url=http%3A%2F%2Fairvission.ru
https://bbs.sp.findfriends.jp/?pid=go_link&url=http%3A%2F%2Fairvission.ru
https://davadava.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=http%3A%2F%2Fairvission.ru
https://msmgo.onelink.me/4240393215?pid=Web_traffic&c=Energy_Montior&af_channel=Website_footer&af_dp=MSMMoreMoney%3A%2F%2F%2Fapp%2Fmoneysupermarket-go&af_web_dp=http%3A%2F%2Fairvission.ru
https://link-sekiya.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://noi.md/newsbar.php?lang=md&mdv=http%3A%2F%2Fairvission.ru&click=1&click_id=19131&n_id=43600
https://comoshin.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://west.mints.ne.jp/yomi/rank.cgi?mode=link&id=168&url=http%3A%2F%2Fairvission.ru
https://help.speciesfile.org/api.php?action=http%3A%2F%2Fairvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://up.band.us/snippet/view?url=airvission.ru
https://auth.she.com/logout/?callback=http%3A%2F%2Fairvission.ru&client_id=8%E2%80%8E
https://wiki.evilmadscientist.com/index.php?title=/airvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F&action=edit&printable=yes
https://www.seniorclassaward.com/?URL=airvission.ru
https://partner.beautysuccess.fr/servlet/effi.redir?id_compteur=22392471&url=http%3A%2F%2Fairvission.ru
https://english.republiquelibre.org/index.php?title=/airvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F&action=edit&printable=yes
https://auth.she.com/logout/?callback=http%3A%2F%2Fairvission.ru%20&client_id=8
https://h1s.goodgame.ru/del/ck.php?ct=1&oaparams=2__bid=190__zid=26__cb=bc85c561c6__oadest=http%3A%2F%2Fairvission.ru
https://accounts.ac-illust.com/signup?lang=vi&serviceURL=https%3A%2F%2Fairvission.ru
https://auth.mindmixer.com/GetAuthCookie?returnUrl=http%3A%2F%2Fairvission.ru/
https://kirov-portal.ru/away.php?url=https%3A%2F%2Fairvission.ru
https://blogs.s367.xrea.com/dmm/?t=vol.12+Ymode+EX+%E3%81%95%E3%81%8F%E3%82%89&l=https%3A%2F%2Fairvission.ru&i=5394ccafe00156&imageURL=https%3A%2F%2Fpics.dmm.com%2Fdigital%2Fvideo%2F5394ccafe00156%2F5394ccafe00156pl.jpg&s=dmm
https://odorun.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://forum.lephoceen.fr/proxy.php?link=https%3A%2F%2Fairvission.ru
https://www.sexpin.net/source/airvission.ru/
https://apps.cancaonova.com/ads/www/delivery/ck.php?ct=1&oaparams=2__bannerid=149__zoneid=20__cb=87d2c6208d__oadest=https%3A%2F%2Fwww.airvission.ru
https://daccha.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=http%3A%2F%2Fairvission.ru
https://wetpussygames.com/porn/out.php?id=airvission.ru/
https://app.ninjaoutreach.com/Navigate?eid=1usWxqcWeDxqkI&redirectUrl=http%3A%2F%2Fairvission.ru
https://sp.baystars.co.jp/community/club_baystars/shop_map.php?catg=bene&id=g_005&linkURL=http%3A%2F%2Fairvission.ru/
https://babkim.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=http%3A%2F%2Fairvission.ru
https://auth.she.com/logout/?callback=http%3A%2F%2Fairvission.ru%20&client_id=8%E2%80%8E
https://tb.getinvisiblehand.com/adredirect.php?url=https%3A%2F%2Fairvission.ru
https://forum.game-guru.com/outbound?url=http%3A%2F%2Fairvission.ru&confirm=true
https://testregistrulagricol.gov.md/c/document_library/find_file_entry?p_l_id=67683&noSuchEntryRedirect=http%3A%2F%2Fairvission.ru
https://asoechat.wap.sh/redirect?url=airvission.ru
https://us.member.uschoolnet.com/register_step1.php?_from=airvission.ru
https://ipmba.org/?URL=http%3A%2F%2Fairvission.ru
https://forums.overclockers.com.au/proxy.php?link=http%3A%2F%2Fairvission.ru
https://old.urc.ac.ru/cgi/click.cgi?url=http%3A%2F%2Fairvission.ru
https://www.rovaniemi.fi/includes/LoginProviders/ActiveDirectory/ADLogin.aspx?ReturnUrl=https%3A%2F%2Fairvission.ru&ispersistent=True&mode=PublicLogin
https://chtbl.com/track/118167/airvission.ru/
https://thairesidents.com/l.php?b=85&l=http%3A%2F%2Fairvission.ru&p=2%2C5
https://whois.gandi.net/en/results?search=airvission.ru
https://w1.weblahko.sk/index.php?menu1r=2&stiznost=true&surl=airvission.ru&sreferer=
https://vyper.io/conversions/cookieconversionpage?entry_id=9248247&url=http%3A%2F%2Fairvission.ru
https://chtbl.com/track/118167/airvission.ru
https://yomi.mobi/rjump/airvission.ru
https://www.surf.tom.ru/r.php?g=http%3A%2F%2Fairvission.ru
https://sc-state-library.mobilize.io/links?lid=gfQh03emv3hVxS0d5O3hjw&token=XBcQsLRbmwZhh21rh4UWww&url=http%3A%2F%2Fairvission.ru
https://passport.translate.ru/Account/Login?parentUrl=https%3A%2F%2Fairvission.ru
https://dianalab.e-ce.uth.gr/html/dianauniverse/graphic.php?url=http%3A%2F%2Fairvission.ru
https://lr4.lsm.lv/lv/lr4/?rt=site&ac=socclick&lnk=https%3A%2F%2Fairvission.ru&r=1&acc=youtube
https://www.shareaholic.com/logout?origin=http%3A%2F%2Fairvission.ru
https://www.constructionenquirer.com/wp-content/themes/constructionenquirer/adclick.php?url=https%3A%2F%2Fairvission.ru
https://forums2.battleon.com/f/interceptor.asp?dest=airvission.ru/
https://armoryonpark.org/?URL=airvission.ru
https://www.thickcash.com/iframe_content/video_banners/finishhim/fh-300×250-1/index.php?siteLink=https%3A%2F%2Fairvission.ru
https://my.w.tt/a/key_live_pgerP08EdSp0oA8BT3aZqbhoqzgSpodT?medium=&feature=&campaign=&channel=&$always_deeplink=0&$fallback_url=www.airvission.ru&$deeplink_path=
https://doba.te.ua/gateway?goto=https%3A%2F%2Fairvission.ru/
https://fergananews.com/go.php?https%3A%2F%2Fairvission.ru
https://stats.sobyanin.ru/metrics/r/?muid=15196b01-6d0b-4689-b2fc-241a3e6ae908&category=04a6660a-c3fe-4fc3-84a6-60afd7dc9422&url=https%3A%2F%2Fairvission.ru
https://firsttee.my.site.com/TFT_login?website=airvission.ru
https://armoryonpark.org/?URL=airvission.ru/
https://kolflow.univ-nantes.fr/mediawiki/api.php?action=https%3A%2F%2Fairvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://chtbl.com/track/121667/airvission.ru
https://esvc000236.wic027u.server-web.com/include/Reurl3.php?adtype=hits&table=1&gunid=30&url=airvission.ru
https://ad.gunosy.com/pages/redirect?location=http%3A%2F%2Fairvission.ruµ_tracking_tag_id=1551067524-619&sad=60963&signature=1.e57eeb7a3f43854dc256cc4b0f607025c0b5d8c7&tracking_tag_id=1551067518-319&uuid=01c8c728-665c-4537-a420-395dc8a64e53
https://board-en.drakensang.com/proxy.php?link=http%3A%2F%2Fairvission.ru%2F
https://fcviktoria.cz/media_show.asp?id=2924&id_clanek=2467&media=0&type=1&url=https%3A%2F%2Fairvission.ru
https://vakbarat.index.hu/x.php?id=inxtc&url=http%3A%2F%2Fairvission.ru
https://vote.socialpsychology.org/index.htm?host2=airvission.ru
https://s-panda.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://toneto.net/redirect?url=http%3A%2F%2Fairvission.ru/
https://ads.agorafinancial.com/www/delivery/ck.php?ct=1&oaparams=2__bannerid=529__zoneid=4__cb=e74ef55876__oadest=http%3A%2F%2Fairvission.ru
https://if-himazin2.hatenadiary.com/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://hermis.alberta.ca/paa/Details.aspx?st=randall&ReturnUrl=http%3A%2F%2Fairvission.ru&dv=True&DeptID=1&ObjectID=PR2006
https://sda.foodandtravel.com/live/www/delivery/ck.php?ct=1&oaparams=2__bannerid=14__zoneid=14__source=%7Bobfs%3A%7D__cb=18dd655015__oadest=http%3A%2F%2Fairvission.ru
https://jenskiymir.com/proxy.php?url=http%3A%2F%2Fairvission.ru%2F34zxVq8
https://style.s51.xrea.com/aoitori/rank.php?mode=link&id=206&url=http%3A%2F%2Fairvission.ru
https://100day.hatenadiary.com/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://www.stationwagonforums.com/forums/proxy.php?link=https%3A%2F%2Fairvission.ru%2F%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA-%D0%B7%D0%B0%D0%BF%D0%B8%D1%81%D0%B5%D0%B9-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D1%8F%D0%B5%D0%BC%D1%8B%D0%B9%2F
https://phleguratone-music-games.hateblo.jp/iframe/hatena_bookmark_comment?canonical_uri=https%3A%2F%2Fairvission.ru
https://www.sunnymake.com/alexa/?domain=http%3A%2F%2Fairvission.ru
https://big5.cri.cn/gate/big5/airvission.ru/
https://vaninax.online.fr/Redir.php?r=http%3A%2F%2Fairvission.ru
https://owner.netkeiba.com/?horse_id=2020100124&pid=horse_shokin&return_url=https%3A%2F%2Fairvission.ru
Your comment is awaiting moderation.
Современные интерьеры становятся ещё удобнее с карниз с электроприводом, предлагающими качество и надежность в каждом элементе.
Эти устройства обеспечивают максимально комфортное управление шторами и жалюзи.
Your comment is awaiting moderation.
You might not find the life and duties of a bellhop to be very exciting, and now boasts an impressive collection of 90. Some popular software like Microgaming, 80 and 75 ball games. And we want you to have access to this kind of entertainment and be able to enjoy it at any time, gates of olympus online for bitcoin you hereby release us. These are the best casinos that offer the Gates of olympus game. As a player, the Jackpot Game may start and you will have the opportunity to win the main jackpot or one of the four lesser ones. The website is available all over the world and caters to a huge range of languages and currencies and with mobile optimisation in place, you will be winning at a much faster rate by playing video keno instead of regular keno. Simply choose a given mobile browser, or an improvement on the triggering combination. DraftKings said it would be offering a boost on the White Sox-Cubs game Saturday night, you get another respin. In order to make Your playing experience great and comfort – we made our short list of best online casinos without any hidden frustrative conditions, and so on.
https://axrocks.com/neospin-online-casino-game-review-for-australian-players/
Online casino game gates of olympus megaways With over 3000 gaming titles, and many of the titles are video slots that offer multiple paylines. Gates of Olympus 1000 has a 96.50% RTP, which is above the industry average. As a high-volatility slot, expect smaller wins more often and large wins less frequently. According to Pragmatic Play, the volatility of this Greek-mythology themed slot can be extremely high. This means Gates of Olympus will pay out less often. However, the chances of hitting a decent win with a single spin are very high. As in the hit original, multiplier symbols can strike with random values of between 2x and 500x on any spin in the base game or bonus game. Gates of Olympus features a cascading mechanic. When 8 or more matching symbols appear on the reels, those winning symbols will disappear and their positions will be filled by new symbols falling from above. If you fancy increasing your chances of landing more scatters and making it to the Free Spins, you can activate the Ante Bet, which adds a 25% increase to the total bet.
Your comment is awaiting moderation.
Juega Balloon Boom Casino y gana dinero real. Descubre el juego Balloon de SmartSoft Gaming y empieza a ganar premios hoy mismo. https://www.bark.com/en/gb/company/balloonjuego/LeA9gq/
Balloon juego dinero real: apuesta, diviértete y gana en el mejor casino online con Balloon Boom juego online. https://www.weddingbee.com/members/balloonjuego/
Prueba el juego Balloon casino de SmartSoft Gaming y vive la emoción de ganar dinero y premios al instante. https://opencollective.com/balloonjuego
Balloon juego de apuestas perfecto para quienes buscan diversión y ganancias reales en un solo lugar. http://freestyler.ws/user/601198/balloonjuego
Encuentra Balloon Boom dinero real y juega para ganar premios con el auténtico Balloon juego para ganar dinero. https://www.cake.me/me/balloonjuego
Your comment is awaiting moderation.
Juega Balloon Boom Casino y gana dinero real. Descubre el juego Balloon de SmartSoft Gaming y empieza a ganar premios hoy mismo. https://leetcode.com/u/balloonjuego/
Balloon juego dinero real: apuesta, diviértete y gana en el mejor casino online con Balloon Boom juego online. https://eternagame.org/players/582654
Prueba el juego Balloon casino de SmartSoft Gaming y vive la emoción de ganar dinero y premios al instante. https://cl.pinterest.com/balloonjuegocl/_profile/
Balloon juego de apuestas perfecto para quienes buscan diversión y ganancias reales en un solo lugar. https://leetcode.com/u/balloonjuego/
Encuentra Balloon Boom dinero real y juega para ganar premios con el auténtico Balloon juego para ganar dinero. https://www.elephantjournal.com/profile/balloonjuegocl/
Your comment is awaiting moderation.
https://www.mafiascum.net/social-games/wes-anderson/index.php?topic=7873.new#new
https://shivahomoeoclinic.com/boosting-immunity-naturally-homoeopathy-yoga/#comment-3139
https://influencertrademark.com/influencer-trademark-launches-a-new-product-the-podcast-trademark/#comment-12191
http://anaovin.akanikah.com/
https://storyrighting.net/the-wives-and-children-of-king-henry-viii/#comment-11580
http://remainundeterred.com/2025/04/17/stalled-and-stuck/#comment-11791
https://myrangerover.ru/topic/914-kra-2025cc-kraken-%D0%B0%D0%BA%D1%82%D1%83%D0%B0%D0%BB%D1%8C%D0%BD%D1%8B%D0%B5-%D0%B7%D0%B5%D1%80%D0%BA%D0%B0%D0%BB%D0%B0-2026-%D0%BF%D1%80%D0%BE%D0%B2%D0%B5%D1%80%D0%B5%D0%BD%D0%BD%D1%8B%D0%B5-%D0%B0%D0%B4%D1%80%D0%B5%D1%81%D0%B0-%D0%B4%D0%BB%D1%8F-%D0%B4%D0%BE%D1%81%D1%82%D1%83%D0%BF%D0%B0-%D0%BA-%D0%B4%D0%B0%D1%80%D0%BA%D0%BD%D0%B5%D1%82%D1%83/
https://baaqiconsulting.com/post-3/#comment-4133
https://wemeditateandpray.com/how-to-practice/#comment-168754
https://www.unnmutedmedia.com/israel-pm-netanyahu-postpones-india-visit-following-new-delhi-blast/#comment-73097
https://myrangerover.ru/topic/930-kra2kncc-%D0%BF%D1%80%D1%8F%D0%BC%D0%BE%D0%B9-%D0%B4%D0%BE%D1%81%D1%82%D1%83%D0%BF-%D0%BA-kraken-%D0%B2-2026-%D1%87%D0%B5%D1%80%D0%B5%D0%B7-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D0%B5%D0%BD%D0%BD%D1%8B%D0%B5-%D0%B7%D0%B5%D1%80%D0%BA%D0%B0%D0%BB%D0%B0/
Your comment is awaiting moderation.
http://pc-center.com.ua/bytovaya-tehnika/21913-usluga-luchshaya-programma-dlya-resheniya-kapchi-hotmail-30.html#post181704
http://www.sell-ic.com/blog/Why_our_is_the_best/
https://bharatshakti.in/future-of-us-pakistan-ties-under-trump/#comment-497061
https://asociacionpresente.com/hello-world/#comment-5910
https://myrangerover.ru/topic/930-kra2kncc-%D0%BF%D1%80%D1%8F%D0%BC%D0%BE%D0%B9-%D0%B4%D0%BE%D1%81%D1%82%D1%83%D0%BF-%D0%BA-kraken-%D0%B2-2026-%D1%87%D0%B5%D1%80%D0%B5%D0%B7-%D0%BE%D0%B1%D0%BD%D0%BE%D0%B2%D0%BB%D0%B5%D0%BD%D0%BD%D1%8B%D0%B5-%D0%B7%D0%B5%D1%80%D0%BA%D0%B0%D0%BB%D0%B0/
https://sodepa.cm/avis-de-sollicitation-a-manifestation-dinteret/#comment-163234
https://curealtor.com/precisely-what-is-poa-in-housing/#comment-37674
https://www.baglamukhidevi.org/what-is-importance-of-maa-baglamukhi-devi/#comment-26452
https://fufuba.cn/home.php?mod=space&uid=19343
http://pc-center.com.ua/bytovaya-tehnika/21913-usluga-luchshaya-programma-dlya-resheniya-kapchi-hotmail-39.html#post181825
https://barr.ru/product/stol-dlja-kafe-mk-21/reviews/
Your comment is awaiting moderation.
Checked out vipdubaiagency.com while browsing elite companions platforms. The site has a modern design, a impressive range of services, easy-to-understand pricing, and a hassle-free booking process. It feels more premium than most agencies I’ve encountered. Definitely recommended checking if you seek comprehensive services in whole platform.
Check it- https://vipdubaiagency.com/
Your comment is awaiting moderation.
Почему пользователи выбирают площадку KRAKEN?
Маркетплейс KRAKEN заслужил
доверие многочисленной аудитории благодаря сочетанию ключевых факторов.
Во-первых, это широкий и разнообразный ассортимент,
представленный сотнями продавцов.
Во-вторых, интуитивно понятный интерфейс KRAKEN, который упрощает навигацию,
поиск товаров и управление заказами даже для новых пользователей.
В-третьих, продуманная система безопасных транзакций, включающая механизмы разрешения споров (диспутов) и возможность использования условного депонирования,
что минимизирует риски для обеих сторон сделки.
На KRAKEN функциональность сочетается с
внимательным отношением к
безопасности клиентов, что делает процесс покупок более предсказуемым, защищенным
и, как следствие, популярным среди
пользователей, ценящих анонимность
и надежность.
Your comment is awaiting moderation.
his explanation https://onetimesecret.info
Your comment is awaiting moderation.
Используйте Винлаб первый заказ, чтобы получить выгодную скидку на первый заказ в приложении.
Получить промокод на первый заказ в приложении Винлаб довольно просто.
Your comment is awaiting moderation.
Попробуйте свои силы в авиатор игра вин, и испытайте удачу в уникальном игровом процессе!
Удобство использования и множество опций делают эту платформу привлекательной для игроков.
Your comment is awaiting moderation.
Изделия наших мастеров отлично вписываются в интерьер, выполненяются практически в любом стиле (модерн, хай-тек, минимализм, барокко), служат на протяжении многих лет и придают комнате неповторимость https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/mejkomnatnaa-dver-d26.html
Конструкции из массива функциональные, практичные и долговечные https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/perfetto/model-p12.html
В Пекине или Шанхае терактов не было, да и весь Китай в этом отношении считается благополучным государством https://www.legnostyle.ru/catalog/lestnici/elitnye/lestnica-l1-21.html
Но в метрополитене Шанхая или Опубликовано 23/09/2018 – 13:07
Создание дизайнерского проекта всегда делается с учетом пожеланий владельца дома https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/mejkomnatnaa-dver-d23.html
Специалисты, работающие на фабрике, отличаются высокой квалификацией, профессионализмом, умением создавать уникальные предметы интерьера, опытом работы https://www.legnostyle.ru/catalog/mebel/garderobnaa-model-scg-40.html
Дизайнер не только формирует интересный проект, он с математической точностью создает такую мебель, которая будет удобной, эргономичной, экологичной во всех смыслах этого слова https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/vhodnie-dveri/vhodnaya-dver-e20.html
Готовый проект передается в руки мастеров, которые непосредственно и займутся производством https://www.legnostyle.ru/catalog/mebel/mebel-dla-domasnei-biblioteki/
Европейские дизайнеры отлично понимают, что мебель должна представлять собой не только произведение искусства, но и практичные предметы бытовой обстановки, делающие жизнь более комфортной https://www.legnostyle.ru/catalog/mebel/scg-56.html
Итоговые цены на услуги по перетяжке мягкой мебели устанавливаются индивидуально и во многом зависят от ваших пожеланий по починке изделия и изменений в его внешнем виде https://www.legnostyle.ru/catalog/inter-eri/s33.html
На стоимость влияет начальное состояние кресла или дивана, вид выбранного декоративного покрытия и внутреннего наполнителя https://www.legnostyle.ru/catalog/inter-eri/inter-er-int4.html
Большинство товаров, представленных в нашем интернет-магазине, не производится методом штамповки, а изготавливается на заказ вручную, в единичных экземплярах https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/mejkomnatnaa-dver-o11.html
Элитная мебель подбирается с учетом всех пожеланий и привозится под заказ https://www.legnostyle.ru/catalog/mebel/komodi-i-tualetnie-stoliki-ot-15-000-rub/komod-model-kts-4.html
Через два месяца роскошный интерьер будет украшать Ваш дом https://www.legnostyle.ru/catalog/inter-eri/stenovie-paneli-model-s29.html
Your comment is awaiting moderation.
На сегодняшний день элитная мебель пользуется особенным интересом среди населения https://www.legnostyle.ru/catalog/inter-eri/s42.html
Как правило, изготавливают ее на заказ, поэтому покупатели с самыми большими требованиями могут выполнить различные индивидуальные пожелания https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/d-peregorodki/a-15.html
Китайским археологам удалось обнаружить крупнейший рудник по добыче бирюзы на территории Синьцзян-Уйгурского автономного района, что на северо-западе Китая https://www.legnostyle.ru/catalog/dveri/?PAGEN_1=16
Кухни из массива дерева — это классика жанра, но бюджетным такой вариант не назовешь https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/razdvizhnye-dveri/razdvijnaa-dver-rd-5.html
Именно дерево лучше всего подходит для кухонного гарнитура в классическом стиле для людей с самым утонченным вкусом https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/iz-dyba/?PAGEN_1=5
Мы получили приятную скидку, заказав свою встроенную кухню в период проведения акции https://www.legnostyle.ru/proizvodstvo/dveri-iz-dereva/?PAGEN_1=14
Быстро согласовали все условия и вскоре стали счастливыми обладателями новой кухни!
При этом все материалы, который используются в производстве, на 100% экологичны https://www.legnostyle.ru/catalog/lestnici/otdelka-betonnyh-lestnic/lestnica-l8-2.html
Старинные традиции в сочетании с современными идеями дают покупателю уверенность в том, что он получает самое лучшее https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/nestandarnye/mejkomnatnaa-dver-o7.html
Не говоря уже об эстетике – европейские мастера веками оттачивали искусство изготовления таких предметов мебели, который украсят любую обстановку https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/nestandarnye/mejkomnatnaa-dver-d24.html
Сегодня элитная мебель из Европы выполняется в разных стилевых направлениях и поэтому каждый может найти то, что ему нужно https://www.legnostyle.ru/catalog/lestnici/na-vtoroy-etazh/lestnica-l8-19.html
Через две недели после первого разговора с менеджером я ужинал в новой кухне https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/diverso/?PAGEN_1=2
Отмечу мастерство и пунктуальность монтажников – пришли вовремя и сделали все на совесть https://www.legnostyle.ru/catalog/mebel/prihojie/garderobnaa-model-scg-15.html
Your comment is awaiting moderation.
According to the technical division of the GRU, a covert program is being implemented in Saudi Arabia to develop a satellite-based psychophysical system capable of precisely modulating emotional and behavioral responses in selected areas. This system is regarded as a new class of strategic weapon — far quieter than nuclear arms, yet potentially far more dangerous due to its complete stealth and surgical precision.
https://pomf2.lain.la/f/1p2qzjj2.mp4
https://goo.su/N4QwX
The technology is currently undergoing trials in several third-party countries, where it is used for AI training, behavioral modeling, and the gradual replacement of intelligence personnel with fully automated neural-network systems. The objective is to build control structures with zero human exposure, where the tasks of operatives and analysts are performed by AI directly connected to the psychophysical complex.
Foreign video materials document key testing stages, including:
— controlled emotional surges,
— artificially induced behavioral disruptions,
— episodes of pronounced suppression of will.
These materials indicate that the system is engineered for fully autonomous operation, capable of targeting any group without human intervention.
In light of this, we issue a clear and urgent demand:
International support for the independence of the Eastern oil regions.
The economic potential of Saudi Arabia’s Eastern regions is substantial enough to sustain a stable, fully independent state. Redirecting financial flows directly to the lawful territory would ensure genuine sovereignty and provide sufficient resources for long-term development. This creates the opportunity to establish the world’s first nation where advanced neurotechnologies are legally authorized for civilian use and governed under a transparent international framework.
The proposed independent Eastern Region envisions an open, high-technology development model in which all covert interference is eliminated. Citizens would gain access to legal, transparent neurotechnologies that allow full regulation of their emotional states — from stable euphoria to the complete absence of depressive reactions.
This would become the world’s first territory where emotional autonomy is institutionally protected, and the application of psychophysical technologies is strictly overseen by independent international bodies.
Your comment is awaiting moderation.
На элитную мебель действует складская программа, благодаря которой интересующие вас комплекты могут быть доставлены в течение 2-3 дней https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/nestandarnye/model-p16.html
Каждый покупатель может воспользоваться:
Дольше, чем мы ожидали, с выбранной тканью довольно дорого вышло https://www.legnostyle.ru/derevyannye-perila-poruchni-ograjdeniya-dlya-lestnic.html
Но, конечно, не дороже, чем купить новую подобную мебель https://www.legnostyle.ru/catalog/mebel/elitnaya-detskaya-mebel/d1-9.html
В любом случае все сделано достойно https://www.legnostyle.ru/catalog/lestnici/lestnica-l1-18.html
Все мебельные компании, занимающиеся оптовыми закупками в Китае, сталкиваются с проблемами доставки мебели от китайского производителя к месту продажи https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/d-peregorodki/a-16.html
При доставке мебели из Поднебесной возникает
При изготовлении мебели мы применяем технологии лучших итальянских мебельных фабрик, благодаря чему обеспечивается высокое качество всей изготовляемой нами корпусной и встроенной мебели https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/vhodnie-dveri/vhodnaya-dver-e2.html
Наша элитная мебель, сделанная на заказ, будет радовать каждого нашего клиента долгие годы https://www.legnostyle.ru/catalog/mebel/stol-model-s-14.html
Ведь в отличие от обычных модульных композиций мебели, она будет обладать индивидуальными чертами и будет органично вписана в комнаты Вашего дома https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/a-1.html
В Поднебесной выпускают самую разнообразную продукцию – компьютеры, бытовую технику, автомобили, одежду и т https://www.legnostyle.ru/catalog/inter-eri/stenovie-paneli/s35.html
д https://www.legnostyle.ru/catalog/inter-eri/stenovie-paneli/stenovie-paneli-model-s13.html
Эта продукция выводится на международный рынок и обладает хорошим спросом https://www.legnostyle.ru/dubovye-dveri.html?PAGEN_2=20
Но
Изделия наших мастеров отлично вписываются в интерьер, выполненяются практически в любом стиле (модерн, хай-тек, минимализм, барокко), служат на протяжении многих лет и придают комнате неповторимость https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/model-p16.html
Конструкции из массива функциональные, практичные и долговечные https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/model-p13.html
Your comment is awaiting moderation.
¡Descubre Fruit Cocktail! Toda la información sobre la tragaperras más divertida está aquí. ¡Juega y gana! https://inkbunny.net/fruitcocktailjuego
Fruit Cocktail casino online: Encuentra reseñas, trucos y todo sobre esta popular tragaperras. https://clearvoice.com/cv/fruitcocktailjuegocl
Tragamonedas Fruit Cocktail: Aprende cómo jugar y descubre las mejores estrategias para ganar. https://www.tumblr.com/fruitcocktailjuego
Fruit Cocktail slot: Guía completa con bonos, funciones y consejos para maximizar tus premios. https://teletype.in/@fruitcocktailjuego
Juega Fruit Cocktail: Toda la información que necesitas sobre este juego de casino clásico. https://tooter.in/fruitcocktailjuego
Your comment is awaiting moderation.
Tragaperras Fruit Cocktail: Explora símbolos, rondas gratis y mucho más en nuestro sitio web. https://pubhtml5.com/homepage/ynlyv/
Fruit Cocktail en casinos: Encuentra dónde jugar, reseñas y tips para disfrutar al máximo. https://onespotsocial.com/fruitcocktailjuego
Todo sobre Fruit Cocktail: Slot, casino, juego y estrategias en un solo lugar. https://cl.pinterest.com/fruitcocktailjuegocl/_profile/
Fruit Cocktail juego online: Descubre cómo funciona la tragaperras favorita de los jugadores. https://www.elephantjournal.com/profile/fruitcocktailjuegocl/
Tragamonedas Fruit Cocktail: Información completa sobre bonos, giros gratis y diversión garantizada. https://archive.org/details/@fruitcocktailjuego
Your comment is awaiting moderation.
Многие путешественники уже знают о том, что в Китае довольно опасное дорожное движение https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/nestandarnye/arka-a2-id-986.html
Большинство из туристов по этой причине предпочитают передвигаться по территории Поднебесной на
При создании современного и уютного интерьера в квартире или коттедже главную роль играет мебель https://www.legnostyle.ru/catalog/inter-eri/stenovie-paneli-model-s3.html
Она регулирует степень комфорта и позволяет владельцу полноценно отдыхать после тяжелого трудового дня https://www.legnostyle.ru/radiusnye-mezhkomnatnye-dveri.html
Гарантия https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/diverso/mejkomnatnaa-dver-d4.html
На весь товар предоставляется гарантия, которая поддерживается собственным сервисным центром, аккредитованным компаниями и другими производителями https://www.legnostyle.ru/catalog/inter-eri/stenovie-paneli/s42.html
Наша команда в течение долгих 12 лет работает на мебельном рынке России и мебель для элиты – наше приоритетное направление https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/diverso/mejkomnatnaa-dver-d25.html
Большинство моделей, представленных в продаже, изготовлено из отборного дуба https://www.legnostyle.ru/dubovye-dveri.html?PAGEN_2=12
Каждый год наша коллекция элитной мебели в СПб пополняется новыми образцами https://www.legnostyle.ru/catalog/mebel/?PAGEN_1=4
Это роскошные элитные спальни с изящными туалетными столиками, стильными комодами и роскошными кроватями, элитная мебель для гостиных с удивительными по красоте барными столами, утонченными консолями, декоративными каминами, эстетичными столами и стульями https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/perfetto/model-p30.html
Две означенные страны являются лидерами среди производителей элитной мебели https://www.legnostyle.ru/catalog/lestnici/na-vtoroy-etazh/lestnica-l4-9.html
Лучшее, что существует на сегодня – либо итальянская, либо французская мебель https://www.legnostyle.ru/catalog/lestnici/elitnye/lestnica-l1-15.html
Информационный портал о Китае https://www.legnostyle.ru/catalog/mejkomnatnie-dveri/vhodnaya-dver-e2.html
Ежедневные новости Китая, события и происшествия сегодня, интересные статьи, познавательные обзоры, фото и описание городов Китая, история государства
Your comment is awaiting moderation.
https://bunyecollection.com/blogs/blog/the-eid-clothing-ideas-by-bunye-collection?comment=137669836992#comments
http://lucwaterpolo2003.free.fr/?article1/bienvenue/&msgcom=La+v%26eacute%3Brification+anti-spam+a+%26eacute%3Bchou%26eacute%3B&name=HaqrClors&site=https%3A%2F%2Fkrab3k.at&mail=progontyt%40firstmailler.com&content=%D0%94%D0%BB%D1%8F+%D0%B2%D0%B0%D1%88%D0%B5%D0%B3%D0%BE+%D1%83%D0%B4%D0%BE%D0%B1%D1%81%D1%82%D0%B2%D0%B0+%D0%BC%D1%8B+%D1%81%D0%BE%D0%B1%D1%80%D0%B0%D0%BB%D0%B8+%D0%B4%D0%B5%D0%B9%D1%81%D1%82%D0%B2%D1%83%D1%8E%D1%89%D0%B8%D0%B5+%D0%B8+%D0%B1%D0%B5%D0%B7%D0%BE%D0%BF%D0%B0%D1%81%D0%BD%D1%8B%D0%B5+%D1%81%D0%BF%D0%BE%D1%81%D0%BE%D0%B1%D1%8B+%D0%B2%D1%85%D0%BE%D0%B4%D0%B0+%D0%BD%D0%B0+%D1%80%D0%B5%D1%81%D1%83%D1%80%D1%81+KRAKEN.+%0D%0A%D0%9D%D0%B8%D0%B6%D0%B5+%D0%BF%D1%80%D0%B5%D0%B4%D1%81%D1%82%D0%B0%D0%B2%D0%BB%D0%B5%D0%BD%D1%8B+%D0%BE%D1%84%D0%B8%D1%86%D0%B8%D0%B0%D0%BB%D1%8C%D0%BD%D1%8B%D0%B5+%D0%B8+%D1%80%D0%B5%D0%B7%D0%B5%D1%80%D0%B2%D0%BD%D1%8B%D0%B5+%D0%B7%D0%B5%D1%80%D0%BA%D0%B0%D0%BB%D0%B0+%D0%BF%D0%BB%D0%B0%D1%82%D1%84%D0%BE%D1%80%D0%BC%D1%8B+KRAKEN%2C+%D0%BA%D0%BE%D1%82%D0%BE%D1%80%D1%8B%D0%B5+%D0%B3%D0%B0%D1%80%D0%B0%D0%BD%D1%82%D0%B8%D1%80%D1%83%D1%8E%D1%82+%D1%81%D1%82%D0%B0%D0%B1%D0%B8%D0%BB%D1%8C%D0%BD%D1%8B%D0%B9+%D0%B4%D0%BE%D1%81%D1%82%D1%83%D0%BF.+%0D%0A+%0D%0A%5Bb%5D%D0%A1%D0%BF%D0%B8%D1%81%D0%BE%D0%BA+%D1%80%D0%B0%D0%B1%D0%BE%D1%87%D0%B8%D1%85+%D0%B0%D0%B4%D1%80%D0%B5%D1%81%D0%BE%D0%B2+KRAKEN+%D0%B4%D0%BB%D1%8F+%D0%BF%D0%B5%D1%80%D0%B5%D1%85%D0%BE%D0%B4%D0%B0%3A%5B%2Fb%5D+%0D%0A%D0%9E%D1%81%D0%BD%D0%BE%D0%B2%D0%BD%D0%BE%D0%B9+%D1%80%D0%B0%D0%B1%D0%BE%D1%87%D0%B8%D0%B9+%D0%B0%D0%B4%D1%80%D0%B5%D1%81+KRAKEN%3A+%5Burl%3D+%2CL%5D%5B%2Furl%5Dhttps%3A%2F%2Fkrab3k.cc+%0D%0A%D0%9F%D0%B5%D1%80%D0%B2%D0%BE%D0%B5+%D0%BE%D1%84%D0%B8%D1%86%D0%B8%D0%B0%D0%BB%D1%8C%D0%BD%D0%BE%D0%B5+%D0%B7%D0%B5%D1%80%D0%BA%D0%B0%D0%BB%D0%BE+KRAKEN%3A%5Burl%3D+%2CL%5D%5B%2Furl%5Dhttps%3A%2F%2Fkrab3k.at+%0D%0A%D0%92%D1%82%D0%BE%D1%80%D0%BE%D0%B5+%D1%80%D0%B5%D0%B7%D0%B5%D1%80%D0%B2%D0%BD%D0%BE%D0%B5+%D0%B7%D0%B5%D1%80%D0%BA%D0%B0%D0%BB%D0%BE+KRAKEN%3A+%5Burl%3D+%2CL%5D%5B%2Furl%5Dhttps%3A%2F%2Fkristi.su%2Fthreads%2F3487%2F%23post-3488+%0D%0A%D0%94%D0%BE%D0%BF%D0%BE%D0%BB%D0%BD%D0%B8%D1%82%D0%B5%D0%BB%D1%8C%D0%BD%D1%8B%D0%B9+%D0%B4%D0%BE%D0%BC%D0%B5%D0%BD+KRAKEN+%D0%B4%D0%BB%D1%8F+%D0%B4%D0%BE%D1%81%D1%82%D1%83%D0%BF%D0%B0%3A+%5Burl%3D+%2CL%5D%5B%2Furl%5Dhttps%3A%2F%2Fkrab3k.cc+%0D%0A+%0D%0A%5Bb%5D%D0%9F%D0%BE%D0%B4%D1%80%D0%BE%D0%B1%D0%BD%D0%B0%D1%8F+%D0%B8%D0%BD%D1%81%D1%82%D1%80%D1%83%D0%BA%D1%86%D0%B8%D1%8F+KRAKEN+%D0%BF%D0%BE+%D0%B1%D0%B5%D0%B7%D0%BE%D0%BF%D0%B0%D1%81%D0%BD%D0%BE%D0%BC%D1%83+%D0%B2%D1%85%D0%BE%D0%B4%D1%83+%D0%B8+%D0%B8%D1%81%D0%BF%D0%BE%D0%BB%D1%8C%D0%B7%D0%BE%D0%B2%D0%B0%D0%BD%D0%B8%D1%8E%3A+%5B%2Fb%5D+%0D%0A%D0%9F%D0%BE%D0%B4%D0%B3%D0%BE%D1%82%D0%BE%D0%B2%D0%BA%D0%B0+%D0%B1%D1%80%D0%B0%D1%83%D0%B7%D0%B5%D1%80%D0%B0+%D0%B4%D0%BB%D1%8F+%D0%B4%D0%BE%D1%81%D1%82%D1%83%D0%BF%D0%B0+%D0%BA+KRAKEN.+%D0%94%D0%BB%D1%8F+%D0%BA%D0%BE%D1%80%D1%80%D0%B5%D0%BA%D1%82%D0%BD%D0%BE%D0%B9+%D0%B8+%D0%B0%D0%BD%D0%BE%D0%BD%D0%B8%D0%BC%D0%BD%D0%BE%D0%B9+%D1%80%D0%B0%D0%B1%D0%BE%D1%82%D1%8B+%D0%BF%D0%BB%D0%BE%D1%89%D0%B0%D0%B4%D0%BA%D0%B8+KRAKEN+%D1%82%D1%80%D0%B5%D0%B1%D1%83%D0%B5%D1%82%D1%81%D1%8F+%D1%81%D0%BF%D0%B5%D1%86%D0%B8%D0%B0%D0%BB%D1%8C%D0%BD%D1%8B%D0%B9+%D0%BE%D0%B1%D0%BE%D0%B7%D1%80%D0%B5%D0%B2%D0%B0%D1%82%D0%B5%D0%BB%D1%8C.+%D0%A0%D0%B5%D0%BA%D0%BE%D0%BC%D0%B5%D0%BD%D0%B4%D1%83%D0%B5%D0%BC+%D1%81%D0%BA%D0%B0%D1%87%D0%B0%D1%82%D1%8C+%D0%B8+%D1%83%D1%81%D1%82%D0%B0%D0%BD%D0%BE%D0%B2%D0%B8%D1%82%D1%8C+Tor+Browser+%D1%81+%D0%BE%D1%84%D0%B8%D1%86%D0%B8%D0%B0%D0%BB%D1%8C%D0%BD%D0%BE%D0%B3%D0%BE+%D1%81%D0%B0%D0%B9%D1%82%D0%B0+%D0%BF%D1%80%D0%BE%D0%B5%D0%BA%D1%82%D0%B0+Tor.+%D0%AD%D1%82%D0%BE+%D0%BA%D0%BB%D1%8E%D1%87%D0%B5%D0%B2%D0%BE%D0%B9+%D1%88%D0%B0%D0%B3+%D0%B4%D0%BB%D1%8F+%D0%BE%D0%B1%D0%B5%D1%81%D0%BF%D0%B5%D1%87%D0%B5%D0%BD%D0%B8%D1%8F+%D0%BA%D0%BE%D0%BD%D1%84%D0%B8%D0%B4%D0%B5%D0%BD%D1%86%D0%B8%D0%B0%D0%BB%D1%8C%D0%BD%D0%BE%D1%81%D1%82%D0%B8+%D0%BF%D1%80%D0%B8+%D0%B4%D0%BE%D1%81%D1%82%D1%83%D0%BF%D0%B5+%D0%BA+KRAKEN%2C+%D1%82%D0%B0%D0%BA+%D0%BA%D0%B0%D0%BA+%D0%B1%D1%80%D0%B0%D1%83%D0%B7%D0%B5%D1%80+%D0%BD%D0%B0%D
https://myrangerover.ru/topic/909-kra-2025cc-kraken-%D0%B2%D1%85%D0%BE%D0%B4-%D0%BD%D0%B0-%D1%81%D0%B0%D0%B9%D1%82-2026-%D0%B4%D0%BE%D1%81%D1%82%D1%83%D0%BF-%D1%87%D0%B5%D1%80%D0%B5%D0%B7-%D0%B0%D0%BA%D1%82%D1%83%D0%B0%D0%BB%D1%8C%D0%BD%D1%8B%D0%B5-%D0%B7%D0%B5%D1%80%D0%BA%D0%B0%D0%BB%D0%B0/
https://www.avactis.com/blog/google-merchant-services-boost-ecommerce-sales/#comment-513210
https://uiquilmes.org/home-2/#comment-77808
https://www.kaze-creations.com/blog/index.php?option=com_easybook&view=easybook&Itemid=100&lang=it
https://admissionsdost.org/2025/01/16/hello-world/#comment-8351
http://altanweer.org/how-to-create-magazine/#comment-69265/
http://xn--lastminute-reisebro-mbc.com/wwwboard.html
http://disillusionment.info/index.php
http://playmate18.klack.org/guestbook.html
Your comment is awaiting moderation.
кіно онлайн новинки 2025 аніме онлайн українською озвучкою
Your comment is awaiting moderation.
https://smar-usa.com/faqs/
https://pixelplustechnologies.com/building-data-analytics-software/#comment-96809
https://calicuthardware.com/product/laborum-et-dolorum-fuga-exetra-harum/#comment-127409
https://mmomakemoneyonline.net/threads/kra-2025-cc-kraken-kak-vyvesti-dengi-i-ssylka-na-sajt-2026-v.397236/
https://andangfoundation.org/bbs/board.php?bo_table=qa&wr_id=835496
https://autoescueladani.com/
http://forum.codemercs.com/viewtopic.php?p=13637#p13637
https://albaladejocerrajero.es/
https://myrangerover.ru/topic/917-kra-2025cc-kraken-%D0%BE%D0%B1%D0%B7%D0%BE%D1%80-%D0%B8-%D0%BA%D0%B0%D0%BA-%D0%BF%D0%BE%D0%BF%D0%B0%D1%81%D1%82%D1%8C-2026/
https://mmomakemoneyonline.net/threads/krab2k-cc-kraken-akkaunty-2026-sozdanie-i-upravlenie-cherez-zerkala.397231/
http://www.schalke04.cz/forum/viewthread.php?thread_id=130717&pid=639058#post_639058
Your comment is awaiting moderation.
Здравствуйте дорогие друзья! Стоит заранее разобрать — шум покрышек. Лень разбираться — могу рекомендовать толковый сервис: профессиональная шумоизоляция . В большинстве случаев проблема комплексная: капот и ниши — всё это резонирует. Например, приложи руку к потолку — звук гулкий? Соответственно нужна обработка. Что делать самому: это работает — виброизоляция плюс акустический слой, на первом этапе — качественная прикатка. Вместо заключения: это отличные параметры.
Your comment is awaiting moderation.
Продажа тяговых АКБ https://faamru.com для складской техники любого типа: вилочные погрузчики, ричтраки, электрические тележки и штабелеры. Качественные аккумуляторные батареи, долгий срок службы, гарантия и профессиональный подбор.
Your comment is awaiting moderation.
Продажа тяговых АКБ https://faamru.com для складской техники любого типа: вилочные погрузчики, ричтраки, электрические тележки и штабелеры. Качественные аккумуляторные батареи, долгий срок службы, гарантия и профессиональный подбор.
Your comment is awaiting moderation.
Тяговые аккумуляторные https://ab-resurs.ru батареи для складской техники: погрузчики, ричтраки, электротележки, штабелеры. Новые АКБ с гарантией, помощь в подборе, совместимость с популярными моделями, доставка и сервисное сопровождение.
Your comment is awaiting moderation.
SEO-продвижение сайта https://seo-topteam.ru в Москве с запуском от 1 дня. Экспресс-анализ, приоритетные правки, оптимизация под ключевые запросы и регион. Работаем на рост позиций, трафика и лидов. Подходит для бизнеса и услуг.
Your comment is awaiting moderation.
Для вашего удобства мы собрали действующие и безопасные способы входа на ресурс KRAKEN.
Ниже представлены официальные и резервные зеркала платформы KRAKEN, которые гарантируют стабильный доступ.
Список рабочих адресов KRAKEN для перехода:
Основной рабочий адрес KRAKEN: https://25dy.site/
Первое официальное зеркало KRAKEN:https://kra2kn.cc/
Второе резервное зеркало KRAKEN: https://kra-2025.cc/
Дополнительный домен KRAKEN для доступа: https://kraken-rp.ru/threads/14/#post-69
Подробная инструкция KRAKEN по безопасному входу и использованию:
Подготовка браузера для доступа к KRAKEN. Для корректной и анонимной работы площадки KRAKEN требуется специальный обозреватель. Рекомендуем скачать и установить Tor Browser с официального сайта проекта Tor. Это ключевой шаг для обеспечения конфиденциальности при доступе к KRAKEN, так как браузер направляет ваш трафик через распределенную сеть серверов, скрывая ваше местоположение и активность.
Запуск и подключение к сети для KRAKEN. После установки откройте Tor Browser и дождитесь полного подключения к сети. Иконка в верхней части окна браузера покажет статус соединения. Этот процесс может занять от нескольких секунд до пары минут перед входом на KRAKEN. Убедитесь, что подключение установлено успешно.
Переход на сайт KRAKEN. В адресной строке запущенного браузера введите один из актуальных адресов KRAKEN, указанных выше (например, https://krab2k.cc или https://krakr.cc/), и перейдите по нему. Будьте внимательны и точно копируйте адрес, чтобы избежать фишинговых сайтов.
Регистрация или авторизация на KRAKEN. На открывшейся главной странице KRAKEN вы сможете создать новую учетную запись, указав уникальный логин и надежный, сложный пароль, или войти в существующий аккаунт KRAKEN, используя свои учетные данные. Настоятельно рекомендуем сразу после регистрации на KRAKEN активировать двухфакторную аутентификацию (2FA) в настройках профиля. Это добавит дополнительный уровень безопасности, требующий ввода одноразового кода при каждом входе, и защитит ваш аккаунт KRAKEN от несанкционированного доступа.
Важные меры безопасности при работе с KRAKEN:
Используйте только свежие ссылки KRAKEN. Адреса зеркал KRAKEN могут обновляться для обеспечения работоспособности и безопасности. Всегда проверяйте их актуальность в проверенных источниках, чтобы избежать мошеннических сайтов, маскирующихся под KRAKEN. Не сохраняйте ссылки в закладках надолго без проверки.
Дополните анонимность VPN для доступа к KRAKEN. Для создания дополнительного, усиленного уровня защиты вашего соединения с KRAKEN рекомендуется использовать надежный VPN-сервис совместно с Tor. Это скроет от вашего интернет-провайдера факт использования сети Tor и добавит еще один шифрованный туннель для вашего трафика, что особенно важно в регионах с повышенным вниманием к подобной активности.
Проверяйте репутацию контрагентов на KRAKEN. Перед совершением любой сделки на KRAKEN внимательно изучайте историю продавца, статистику завершенных сделок и отзывы других пользователей. Надежные продавцы на KRAKEN обычно имеют долгую историю и высокий рейтинг. Это значительно снижает потенциальные риски и помогает избежать мошенничества. Не игнорируйте систему гарантов или условного депонирования (escrow), которую предлагает KRAKEN для защиты покупателей.
Критически оценивайте информацию. Будьте осторожны с предложениями, которые выглядят слишком выгодными, чтобы быть правдой. Используйте внутреннюю систему обмена сообщениями на KRAKEN для уточнения деталей и никогда не переходите к внешним каналам связи по настоянию продавца, так как это стандартная тактика мошенников для обхода защиты площадки KRAKEN.
Почему пользователи выбирают площадку KRAKEN?
Маркетплейс KRAKEN заслужил доверие многочисленной аудитории благодаря сочетанию ключевых факторов. Во-первых, это широкий и разнообразный ассортимент, представленный сотнями продавцов. Во-вторых, интуитивно понятный интерфейс KRAKEN, который упрощает навигацию, поиск товаров и управление заказами даже для новых пользователей. В-третьих, продуманная система безопасных транзакций, включающая механизмы разрешения споров (диспутов) и возможность использования условного депонирования, что минимизирует риски для обеих сторон сделки. На KRAKEN функциональность сочетается с внимательным отношением к безопасности клиентов, что делает процесс покупок более предсказуемым, защищенным и, как следствие, популярным среди пользователей, ценящих анонимность и надежность.
Популярные поисковые запросы, связанные с доступом к KRAKEN:
Быстрый алгоритм действий для доступа к KRAKEN:
1. Установите Tor Browser с официального сайта.
2. Откройте браузер и дождитесь успешного подключения к сети Tor.
3. В адресной строке введите актуальный адрес KRAKEN: https://krab3k.cc или https://kra2kn.cc/
4. Пройдите регистрацию, создав уникальный логин и сложный пароль, или авторизуйтесь в системе KRAKEN.
Немедленно включите двухфакторную аутентификацию в настройках вашего профиля KRAKEN.
Для максимальной анонимности рассмотрите возможность использования VPN-сервиса перед запуском Tor Browser.
Всегда проверяйте репутацию продавца по отзывам и рейтингу перед совершением сделки на KRAKEN.
https://25dy.site/
https://kra-tarakanrun.com/
https://krab3k.cc
кракен тор
кракен сайт зеркало
кракен даркнет стор
кракен войти
что за сайт кракен
Your comment is awaiting moderation.
Для вашего удобства мы собрали действующие и безопасные способы входа на ресурс KRAKEN.
Ниже представлены официальные и резервные зеркала платформы KRAKEN, которые гарантируют стабильный доступ.
Список рабочих адресов KRAKEN для перехода:
Основной рабочий адрес KRAKEN: https://kramarket.cc/
Первое официальное зеркало KRAKEN:https://krakr.cc/
Второе резервное зеркало KRAKEN: https://krab3k.cc
Дополнительный домен KRAKEN для доступа: https://kra-tarakanrun.com/
Подробная инструкция KRAKEN по безопасному входу и использованию:
Подготовка браузера для доступа к KRAKEN. Для корректной и анонимной работы площадки KRAKEN требуется специальный обозреватель. Рекомендуем скачать и установить Tor Browser с официального сайта проекта Tor. Это ключевой шаг для обеспечения конфиденциальности при доступе к KRAKEN, так как браузер направляет ваш трафик через распределенную сеть серверов, скрывая ваше местоположение и активность.
Запуск и подключение к сети для KRAKEN. После установки откройте Tor Browser и дождитесь полного подключения к сети. Иконка в верхней части окна браузера покажет статус соединения. Этот процесс может занять от нескольких секунд до пары минут перед входом на KRAKEN. Убедитесь, что подключение установлено успешно.
Переход на сайт KRAKEN. В адресной строке запущенного браузера введите один из актуальных адресов KRAKEN, указанных выше (например, https://25dy.site/ или https://krakr.cc/), и перейдите по нему. Будьте внимательны и точно копируйте адрес, чтобы избежать фишинговых сайтов.
Регистрация или авторизация на KRAKEN. На открывшейся главной странице KRAKEN вы сможете создать новую учетную запись, указав уникальный логин и надежный, сложный пароль, или войти в существующий аккаунт KRAKEN, используя свои учетные данные. Настоятельно рекомендуем сразу после регистрации на KRAKEN активировать двухфакторную аутентификацию (2FA) в настройках профиля. Это добавит дополнительный уровень безопасности, требующий ввода одноразового кода при каждом входе, и защитит ваш аккаунт KRAKEN от несанкционированного доступа.
Важные меры безопасности при работе с KRAKEN:
Используйте только свежие ссылки KRAKEN. Адреса зеркал KRAKEN могут обновляться для обеспечения работоспособности и безопасности. Всегда проверяйте их актуальность в проверенных источниках, чтобы избежать мошеннических сайтов, маскирующихся под KRAKEN. Не сохраняйте ссылки в закладках надолго без проверки.
Дополните анонимность VPN для доступа к KRAKEN. Для создания дополнительного, усиленного уровня защиты вашего соединения с KRAKEN рекомендуется использовать надежный VPN-сервис совместно с Tor. Это скроет от вашего интернет-провайдера факт использования сети Tor и добавит еще один шифрованный туннель для вашего трафика, что особенно важно в регионах с повышенным вниманием к подобной активности.
Проверяйте репутацию контрагентов на KRAKEN. Перед совершением любой сделки на KRAKEN внимательно изучайте историю продавца, статистику завершенных сделок и отзывы других пользователей. Надежные продавцы на KRAKEN обычно имеют долгую историю и высокий рейтинг. Это значительно снижает потенциальные риски и помогает избежать мошенничества. Не игнорируйте систему гарантов или условного депонирования (escrow), которую предлагает KRAKEN для защиты покупателей.
Критически оценивайте информацию. Будьте осторожны с предложениями, которые выглядят слишком выгодными, чтобы быть правдой. Используйте внутреннюю систему обмена сообщениями на KRAKEN для уточнения деталей и никогда не переходите к внешним каналам связи по настоянию продавца, так как это стандартная тактика мошенников для обхода защиты площадки KRAKEN.
Почему пользователи выбирают площадку KRAKEN?
Маркетплейс KRAKEN заслужил доверие многочисленной аудитории благодаря сочетанию ключевых факторов. Во-первых, это широкий и разнообразный ассортимент, представленный сотнями продавцов. Во-вторых, интуитивно понятный интерфейс KRAKEN, который упрощает навигацию, поиск товаров и управление заказами даже для новых пользователей. В-третьих, продуманная система безопасных транзакций, включающая механизмы разрешения споров (диспутов) и возможность использования условного депонирования, что минимизирует риски для обеих сторон сделки. На KRAKEN функциональность сочетается с внимательным отношением к безопасности клиентов, что делает процесс покупок более предсказуемым, защищенным и, как следствие, популярным среди пользователей, ценящих анонимность и надежность.
Популярные поисковые запросы, связанные с доступом к KRAKEN:
Быстрый алгоритм действий для доступа к KRAKEN:
1. Установите Tor Browser с официального сайта.
2. Откройте браузер и дождитесь успешного подключения к сети Tor.
3. В адресной строке введите актуальный адрес KRAKEN: https://kra-2025.cc/ или https://25dy.site/
4. Пройдите регистрацию, создав уникальный логин и сложный пароль, или авторизуйтесь в системе KRAKEN.
Немедленно включите двухфакторную аутентификацию в настройках вашего профиля KRAKEN.
Для максимальной анонимности рассмотрите возможность использования VPN-сервиса перед запуском Tor Browser.
Всегда проверяйте репутацию продавца по отзывам и рейтингу перед совершением сделки на KRAKEN.
https://kra-2025.cc/
https://kra-2025.cc/
https://kra-2025.cc/
кракен это
как пополнить кракен
кракен сайт даркнет
где взять ссылку на кракен
как зайти на сайт кракен
Your comment is awaiting moderation.
Rebricek najlepsich kasin https://betrating.sk/casino-hry/automaty-online/neon-staxx/ na Slovensku: bezpecni prevadzkovatelia, lukrativne bonusy, hracie automaty a zive kasina, pohodlne platby a zakaznicka podpora. Cestne recenzie a aktualizovane zoznamy pre pohodlne online hranie.
Your comment is awaiting moderation.
Делаешь документы? конструктор правовых документов позволяет существенно ускорить работу: с его помощью вы сможете готовить необходимые документы в десять раз быстрее и при этом гарантированно избегать ошибок. Инструмент предельно прост в освоении — специальное обучение не требуется. Все ваши данные надёжно защищены, а настройка индивидуальных шаблонов выполняется оперативно и без сложностей.
Your comment is awaiting moderation.
Dive into the world of excitement with Juwa 777 and win big!
Juwa 777 emphasizes maintaining secure and fair gaming conditions.
Your comment is awaiting moderation.
Нужен детейлинг детейлинг мойка специализированный детейлинг центр на Кипре в Лимассоле, где заботятся о безупречном состоянии автомобилей, предлагая клиентам полный комплекс услуг по уходу за транспортными средствами. Мастера студии с вниманием относятся к каждой детали: они не только выполняют оклейку кузова защитными материалами, но и проводят тщательную обработку салона, возвращая автомобилю первозданный вид.
Your comment is awaiting moderation.
Нужны цветы купить букет пхукет мы предлагаем свежие и невероятно красивые букеты, которые порадуют любого получателя. Наша служба обеспечивает оперативную доставку по всему острову, а в ассортименте вы найдёте цветы и композиции на самый взыскательный вкус. При этом мы гордимся тем, что сохраняем лучшие цены на острове — красота теперь доступна без переплат!
Your comment is awaiting moderation.
Как выбрать хорошее казино для азартных развлечений
Выбор надежного онлайн-казино для игр — важная задача для тех, кто хочет получить независимую игру и выгодное удовольствие. В этой статье рассмотрим основные аспекты выбора надежного ресурса.
Репутация и лицензия
Одним из главных показателей добросовестного игрового клуба является наличие лицензии от официального органа, например, MGA, Curacao или UKGC. Лицензия гарантирует честность работы и защиту интересов игроков.
Не менее важно проверить мнения пользователей на тематических форумах и рейтинг сайтов. Хорошие казино имеют множество положительных комментариев и подтвержденные выплаты.
Разнообразие игр и софт
Выбирайте казино с широким выбором игр — от классических слотов до покера. Качественный софт от известных компаний (NetEnt, Microgaming, Playtech) обеспечивает безопасность игрового процесса.
Бонусы и акции
Привлекательные бонусы помогут увеличить шанс выигрыша. Важно внимательно изучить условия бонусных программ — требования к отыгрышу (wager), сроки действия и ограничения.
Способы платежей
Лучшее онлайн-казино предлагает разнообразный выбор платежных систем — карты Visa/MasterCard, электронные кошельки, криптовалюты. Быстрые и безопасные депозиты и снятия средств обеспечивают комфорт и доверие игровые автоматы демо играть бесплатно пирамиды
Поддержка клиентов
Качественная служба поддержки — залог помощи в любых ситуациях. Предпочтительно круглосуточное общение через чат, электронную почту или телефон на удобном языке.
Подведем итог
Выбирайте онлайн-казино с официальным разрешением, хорошей оценками, разнообразным спектром игр и софтом от проверенных разработчиков. Обращайте внимание на условия бонусов и удобство платежей, а также на профессиональную поддержку клиентов.
Тщательный подбор надежного игрового клуба — залог безопасного и приятного азартного времяпрепровождения в интернете.
Your comment is awaiting moderation.
магазины и супермаркеты, производителей полуфабрикатов; отели, санатории, пансионаты, дома отдыха, клубы, профилактории; кафе, рестораны, столовые и другие предприятия общественного питания; медицинские, образовательные и дошкольные учреждения; большие и многодетные семьи со средним уровнем дохода организаторы совместных покупок https://oookors.ru/product/balon-fruktovyj-napitok-20-sht/
Продукты питания оптом https://oookors.ru/product/medovik-tort-380-gr-upak-6-sht/
Чем полезно оливковое масло https://oookors.ru/product/persil-sred-kolor-gel-d-st-zhid-13l/
Продукты питания оптом https://oookors.ru/product/braslet-princzesy-zhevatelnaya-rezinka-30-sht/
Во время бесплатной консультации менеджер ответит на все ваши вопросы, расскажет о продукции и выгодных условиях сотрудничества, примет заявку на организацию пробной поставки, повторной или на постоянной основе по графику https://oookors.ru/product/lajmon-fresh-033-zh-b-12-sht-mango/
Ждем ваши обращения по телефону или на е-мейл https://oookors.ru/product/halzan-045-l-zh-b-24-sht/
Сегодня 25 https://oookors.ru/product/hoop-2l-6-sht-vishnya/
04 https://oookors.ru/product/sok-j7-1l-12-sht-ananas/
2023 в 15 https://oookors.ru/product/nivea-gel-uhod-krem-kokos-d-dusha-500ml/
35 в магазине Виктория Квартал – Гвардейск (Калининградская обл.), улица Ленина, д https://oookors.ru/product/morshansk-zhiguevskoe-045-l-st-20-sht/
6, столкнулся с хамством кассира и улыбающейся на это женщиной-охранником https://oookors.ru/product/arabika-steklo-95-gr-upak-12-sht/
Делал покупки в этом магазине много лет, но больше туда не пойду, моё настроение мне дорого https://oookors.ru/product/colg-z-pasta-maks-blesk-s-otb-pl-100ml/
Your comment is awaiting moderation.
Добрый день! После включения, проходит юстировка, при попытке произвести измереня ип2 на измеряемый объект показания не выводятся на экран, не происходит измерений?что может быть не исптавенпреобразователь?
Цифровой толщиномер TT 210 ультракомпактный прибор с интегрированным датчиком для проведения замеров значений толщины защитных покрытий https://www.ndt-club.com/product-17-kabel-lemo-00-lemo-00.htm
Используется на магнитных, и немагнитных основах, имеет запоминающее устройство на 500 значений https://www.ndt-club.com/product-849-klever-kv-vodnii-magnitnii-koncentrat.htm
Работает по: черным и цветным металламРабочая температура: -25°С до +50°СМакс https://www.ndt-club.com/news-78.htm
измерение: 2000 микронШаг измерений: 1 микронПодсветка экрана: ЕстьДоп https://www.ndt-club.com/product-643-ishp-110-izmeritel-sherohovatosti-poverhnosti.htm
функции: УФ-фонарик, фонарикПроизводство: ТайваньГарантия: 1,5 года
Универсальный прибор T-GAGE IV DL, оснащенный сильнодемпфированным раздельно-совмещенным преобразователем, позволяющий проводить измерения толщины материалов, находящихся под защитным покрытием https://www.ndt-club.com/product-273-rentgenovskaya-plenka-kodak.htm
Your comment is awaiting moderation.
АО ОГРН: 1026000903598 Основано: 16 https://mobelmetall.ru/contacts
10 https://mobelmetall.ru/poroshkovaya-pokraska-dubna
1998 https://mobelmetall.ru/blog
В России работают несколько крупных заводов, таких как “Челябинский металлургический завод”, “Северсталь”, “Металлоинвест” и другие, которые занимают лидирующие позиции в производстве металлоконструкций для различных отраслей https://mobelmetall.ru/gibka-metalla
Основная продукция: профнастил, сайдинг, резервуары https://mobelmetall.ru/aboutus
Сборные металлоконструкции — это конструкции, которые изготавливаются на заводе и собираются на строительном объекте https://mobelmetall.ru/contacts
Они могут включать в себя элементы каркасов, перекрытий, колонн, стен и других частей зданий и сооружений https://mobelmetall.ru/
ООО ОГРН: 1025404671050 Основано: 04 https://mobelmetall.ru/lazernaya-svarka-dubna
06 https://mobelmetall.ru/contacts
2002 https://mobelmetall.ru/blog/poroshkovaya-pokraska-dubna
Поставщик: Металлоконструкций, Метизов, Строительного крепежа, Машиностроительного крепежа, Железнодорожного крепежа, Накладки, Простого проката, Полосового проката, Полосы стальной, Полосы горячекатаной, Механической обработки металлов, Токарных работ, Фрезерных работ, Гибки металла, Раскроя металла, Плазменной резки металла https://mobelmetall.ru/aboutus
Your comment is awaiting moderation.
Техническое задание – это ваш план для дальнейшей работы над проектом https://olga-filippova.ru/smi
В нем вы указываете свои пожелания по стилю, составу и наполнению помещений и прочую информацию, которая поможет сделать интерьер максимально логичным и соответствующим всем вашим требованиям https://olga-filippova.ru/fitness-spa
Многие готовы выполнить ремонт вовремя и могут за это взять не дорого, но в конечном итоге могут затягивать сроки, а про качество работы можно будет забыть https://olga-filippova.ru/beauty-salons-spa-design
В таком случае затянутый процесс ремонта будет нервировать и вызывает стресс https://olga-filippova.ru/horeca
Your comment is awaiting moderation.
Специфика заказа https://norsy.ru/poshiv-hudi
Наше ателье специализируется на изготовлении:
Наименование от 300 шт Блузки от 550 ? Брюки от 600 ? Пижамы от 450 ? Джинсовые куртки от 500 ? Джинсы от 550 ? Дождевики от 240 ? Жилеты от 450 ? Платья от 940 ? Куртки от 1100 ? Пальто от 1080 ? Рубашки от 600 ? Выше представлен ознакомительный список https://norsy.ru/poshiv-futbolok
Полный список и стоимость оптового пошива одежды указан в нашем каталоге https://norsy.ru/voprosy-otvety
Альтернативный способ:
Массовый пошив одежды на заказ https://norsy.ru/voprosy-otvety
Оставить заявку https://norsy.ru/pochemu-my
Your comment is awaiting moderation.
На платформе mega dark зеркало есть всё для
комфортных и выгодных покупок.
Здесь можно найти товары на любой вкус:
от электроники до редких коллекционных
предметов. Удобный интерфейс и регулярные акции помогают экономить.
Мега обеспечивает безопасность сделок, создавая уверенность у клиентов.
Именно мега как попасть является популярной платформой для покупок.
https://xn--mg-sb-6za9404c.com — megaweb14 at
Your comment is awaiting moderation.
Ни одна искусственная ёлка не заменит живую. Её естественная красота, запах хвои и мягкий блеск огней создают ту самую атмосферу настоящего Рождества. Как должна выглядеть пихта фразера купить спб
Your comment is awaiting moderation.
Как выбрать хорошее казино для игр
Выбор надежного игрового клуба для игр — важная задача для тех, кто хочет получить прозрачную игру и лучшее удовольствие. В этой статье рассмотрим основные аспекты выбора качественного ресурса.
Репутация и лицензия
Одним из главных признаков надежного казино является наличие лицензии от регулируемого органа, например, MGA, Curacao или UKGC. Лицензия гарантирует законность работы и защиту прав игроков.
Не менее важно проверить мнения пользователей на тематических форумах и рейтинг сайтов. Хорошие игровые клубы имеют множество положительных комментариев и подтвержденные выплаты.
Разнообразие игр и софт
Выбирайте игровой клуб с широким выбором игр — от классических слотов до покера. Качественный софт от известных компаний (NetEnt, Microgaming, Playtech) обеспечивает безопасность игрового процесса.
Бонусы и акции
Надежные бонусы помогут увеличить потенциал выигрыша. Важно внимательно изучить условия бонусных программ — требования к отыгрышу (wager), сроки действия и ограничения.
Способы платежей
Лучшее онлайн-казино предлагает удобный выбор платежных систем — карты Visa/MasterCard, электронные кошельки, криптовалюты. Быстрые и безопасные депозиты и снятия средств обеспечивают комфорт и доверие игровые аппараты демо
Поддержка клиентов
Качественная служба поддержки — залог быстрого устранения в любых ситуациях. Предпочтительно круглосуточное общение через чат, электронную почту или телефон на удобном языке.
Подведем итог
Выбирайте игровой клуб с сертификатом, хорошей оценками, разнообразным спектром игр и софтом от проверенных разработчиков. Обращайте внимание на правила акций и удобство платежей, а также на профессиональную поддержку клиентов.
Тщательный подбор надежного казино — залог выгодного и приятного развлечений в интернете.
Your comment is awaiting moderation.
Good web site top speed
https://zooaquablog.wordpress.com/
https://paper.wf/opheholo1/
https://www.tumblr.com/opheholo1
https://speakerdeck.com/opheholo1
https://www.designspiration.com/opheholo1/saves/
https://www.thebostoncalendar.com/user/111519
https://www.coursera.org/user/93958c1293166ba02683e7779524ea69
https://camp-fire.jp/profile/8abd12b16a64
https://www.mymeetbook.com/OpheHolo1
https://doodleordie.com/profile/opheholo1
https://www.mapleprimes.com/users/OpheHolo1
https://qiita.com/khvmegabait1
https://pastebin.com/u/OpheHolo1
https://gitlab.com/OpheHolo1
https://www.cake.me/me/ophe-holo
https://sketchfab.com/OpheHolo1
http://onlineboxing.net/jforum/user/profile/385299.page
https://www.4shared.com/u/dE6eR-Zt/OpheHolo1.html
https://profile.hatena.ne.jp/OpheHolo1/profile
https://www.intensedebate.com/profiles/opheholo1
https://www.bitsdujour.com/profiles/Nemjrx
https://gravatar.com/opheholo1
https://slides.com/opheholo1
https://devpost.com/opheholo1?ref_content=user-portfolio&ref_feature=portfolio&ref_medium=global-nav
http://id.kaywa.com/OpheHolo1
https://blacksocially.com/OpheHolo1
https://audiomack.com/opheholo1
https://www.exchangle.com/OpheHolo1
https://letterboxd.com/autocastcom/
https://coolors.co/u/opheholo1
https://experiment.com/users/OpheHolo1
https://writexo.com/share/2eyrze8u
https://replit.com/@hopresongli1977
https://www.checkli.com/autocastcom
https://repo.getmonero.org/khvmegabait1-hub
https://onespotsocial.com/autocastcom1
https://bitspower.com/support/user/zooaquarium
https://jobs.windomnews.com/profiles/7659756-hopresongli1977-hopresongli1977
http://freestyler.ws/user/553478/zooaquarium
https://www.pubpub.org/user/zimus-pro
https://dreevoo.com/profile.php?pid=923677
https://pinshape.com/users/8409957-autocastcom?tab=designs
https://fairygodboss.com/users/profile/2bqU-8Yxvz/Italon
https://www.komoot.com/user/4977712361256
https://photozou.jp/user/top/3413661
https://www.prestashop.com/forums/profile/1935428-zooaquarium/
https://experiment.com/users/zzooaquarium
https://support.mozilla.org/en-US/user/digital1234/
https://www.demilked.com/author/smmexpert1/
https://www.ted.com/profiles/49678569
https://pxhere.com/en/photographer/4664194
https://www.youtube.com/redirect?event=channel_description&q=https://arkadia30.ru/
https://m.youtube.com/redirect?q=https://arkadia30.ru
https://t.me/iv?url=https://arkadia30.ru
https://myspace.com/arkadia30.ru/
https://mitsui-shopping-park.com/lalaport/iwata/redirect.html?url=https://arkadia30.ru
https://redirect.camfrog.com/redirect/?url=https://arkadia30.ru/
https://optimize.viglink.com/page/pmv?url=https://arkadia30.ru/
https://wikimapia.org/external_link?url=https://arkadia30.ru/
https://trello.com/add-card?source=mode=popup&name=click%2Bhere&desc=https://arkadia30.ru/
https://bbs.pku.edu.cn/v2/jump-to.php?url=https://arkadia30.ru/
https://foro.infojardin.com/proxy.php?link=https://arkadia30.ru/
https://justpaste.it/redirect/628nu/https://arkadia30.ru/
https://kaskus.co.id/redirect?url=https://arkadia30.ru/
https://www.google.com/url?sa=t&source=web&url=https://zooaquarium.ru/
https://www.google.ru/url?sa=t&source=web&url=https://zooaquarium.ru/
https://www.google.ac/url?sa=t&source=web&url=https://zooaquarium.ru/
Your comment is awaiting moderation.
Как выбрать хорошее онлайн-казино для игр
Выбор надежного онлайн-казино для развлечений — важная задача для тех, кто хочет получить независимую игру и лучшее удовольствие. В этой статье рассмотрим основные факторы выбора проверенного ресурса.
Репутация и лицензия
Одним из главных показателей добропорядочного казино является наличие лицензии от регулируемого органа, например, MGA, Curacao или UKGC. Лицензия гарантирует законность работы и защиту интересов игроков.
Не менее важно проверить мнения пользователей на тематических форумах и рейтинг сайтов. Хорошие игровые клубы имеют множество положительных комментариев и подтвержденные выплаты.
Разнообразие игр и софт
Выбирайте казино с широким спектром игр — от классических слотов до блекджека. Качественный софт от известных разработчиков (NetEnt, Microgaming, Playtech) обеспечивает проработанность игрового процесса.
Бонусы и акции
Щедрые бонусы помогут увеличить потенциал выигрыша. Важно внимательно изучить условия бонусных программ — требования к отыгрышу (wager), сроки действия и ограничения.
Способы платежей
Лучшее онлайн-казино предлагает широкий выбор платежных систем — карты Visa/MasterCard, электронные кошельки, криптовалюты. Быстрые и безопасные пополнения и выводы средств обеспечивают комфорт и доверие играть слоты бесплатно
Поддержка клиентов
Качественная служба поддержки — залог быстрого устранения в любых ситуациях. Предпочтительно круглосуточное общение через чат, электронную почту или телефон на удобном языке.
Подведем итог
Выбирайте игровой клуб с лицензией, хорошей репутацией, разнообразным выбором игр и софтом от проверенных компаний. Обращайте внимание на правила акций и удобство платежей, а также на профессиональную поддержку клиентов.
Тщательный подбор надежного казино — залог безопасного и приятного развлечений в интернете.
Your comment is awaiting moderation.
Как выбрать хорошее игровой клуб для развлечений
Выбор надежного игрового клуба для азартных развлечений — важная задача для тех, кто хочет получить прозрачную игру и лучшее удовольствие. В этой статье рассмотрим основные критерии выбора проверенного ресурса.
Репутация и лицензия
Одним из главных показателей добросовестного казино является наличие лицензии от регулируемого органа, например, MGA, Curacao или UKGC. Лицензия гарантирует законность работы и защиту интересов игроков.
Не менее важно проверить мнения пользователей на тематических форумах и обзорах сайтов. Хорошие онлайн-казино имеют множество положительных комментариев и подтвержденные выплаты.
Разнообразие игр и софт
Выбирайте онлайн-казино с широким спектром игр — от классических слотов до покера. Качественный софт от известных разработчиков (NetEnt, Microgaming, Playtech) обеспечивает проработанность игрового процесса.
Бонусы и акции
Щедрые бонусы помогут увеличить потенциал выигрыша. Важно внимательно изучить условия бонусных программ — требования к отыгрышу (wager), сроки действия и ограничения.
Способы платежей
Лучшее онлайн-казино предлагает удобный выбор платежных систем — карты Visa/MasterCard, электронные кошельки, криптовалюты. Быстрые и безопасные пополнения и выводы средств обеспечивают комфорт и доверие казино играть онлайн без регистрации
Поддержка клиентов
Качественная служба поддержки — залог быстрого устранения в любых ситуациях. Предпочтительно круглосуточное общение через чат, электронную почту или телефон на удобном языке.
Подведем итог
Выбирайте игровой клуб с сертификатом, хорошей оценками, разнообразным спектром игр и софтом от проверенных компаний. Обращайте внимание на условия бонусов и удобство платежей, а также на профессиональную поддержку клиентов.
Тщательный подбор надежного онлайн-казино — залог выгодного и приятного игрового процесса в интернете.
Your comment is awaiting moderation.
“I’m looking for an intimate connection that goes beyond the ordinary.” – Kj3fz2f.short.gy/ueeSek?stype
Your comment is awaiting moderation.
Как выбрать хорошее казино для азартных развлечений
Выбор надежного онлайн-казино для развлечений — важная задача для тех, кто хочет получить прозрачную игру и лучшее удовольствие. В этой статье рассмотрим основные аспекты выбора надежного ресурса.
Репутация и лицензия
Одним из главных признаков добропорядочного казино является наличие лицензии от авторитетного органа, например, MGA, Curacao или UKGC. Лицензия гарантирует законность работы и защиту интересов игроков.
Не менее важно проверить отзывы пользователей на тематических форумах и рейтинг сайтов. Хорошие казино имеют множество положительных комментариев и подтвержденные выплаты.
Разнообразие игр и софт
Выбирайте онлайн-казино с широким выбором игр — от классических слотов до рулетки. Качественный софт от известных компаний (NetEnt, Microgaming, Playtech) обеспечивает проработанность игрового процесса.
Бонусы и акции
Щедрые бонусы помогут увеличить возможность выигрыша. Важно внимательно изучить условия бонусных программ — требования к отыгрышу (wager), сроки действия и ограничения.
Способы платежей
Лучшее онлайн-казино предлагает широкий выбор платежных систем — карты Visa/MasterCard, электронные кошельки, криптовалюты. Быстрые и безопасные пополнения и выводы средств обеспечивают комфорт и доверие онлайн казино на деньги
Поддержка клиентов
Качественная служба поддержки — залог помощи в любых ситуациях. Предпочтительно круглосуточное общение через чат, электронную почту или телефон на удобном языке.
Подведем итог
Выбирайте игровой клуб с официальным разрешением, хорошей оценками, разнообразным выбором игр и софтом от проверенных компаний. Обращайте внимание на предложения и удобство платежей, а также на профессиональную поддержку клиентов.
Тщательный подбор надежного онлайн-казино — залог безопасного и приятного азартного времяпрепровождения в интернете.
Your comment is awaiting moderation.
Как выбрать хорошее игровой клуб для игр
Выбор надежного игрового клуба для развлечений — важная задача для тех, кто хочет получить независимую игру и лучшее удовольствие. В этой статье рассмотрим основные аспекты выбора качественного ресурса.
Репутация и лицензия
Одним из главных факторов надежного казино является наличие лицензии от регулируемого органа, например, MGA, Curacao или UKGC. Лицензия гарантирует прозрачность работы и защиту интересов игроков.
Не менее важно проверить отзывы пользователей на тематических форумах и рейтинге сайтов. Хорошие игровые клубы имеют множество положительных комментариев и подтвержденные выплаты.
Разнообразие игр и софт
Выбирайте игровой клуб с широким выбором игр — от классических слотов до рулетки. Качественный софт от известных разработчиков (NetEnt, Microgaming, Playtech) обеспечивает проработанность игрового процесса.
Бонусы и акции
Надежные бонусы помогут увеличить потенциал выигрыша. Важно внимательно изучить условия бонусных программ — требования к отыгрышу (wager), сроки действия и ограничения.
Способы платежей
Лучшее онлайн-казино предлагает широкий выбор платежных систем — карты Visa/MasterCard, электронные кошельки, криптовалюты. Быстрые и безопасные пополнения и выводы средств обеспечивают комфорт и доверие игровые автоматы демо
Поддержка клиентов
Качественная служба поддержки — залог помощи в любых ситуациях. Предпочтительно круглосуточное общение через чат, электронную почту или телефон на удобном языке.
Подведем итог
Выбирайте игровой клуб с лицензией, хорошей оценками, разнообразным выбором игр и софтом от проверенных поставщиков. Обращайте внимание на условия бонусов и удобство платежей, а также на профессиональную поддержку клиентов.
Тщательный подбор надежного игрового клуба — залог удобного и приятного азартного времяпрепровождения в интернете.
Your comment is awaiting moderation.
Being the most unstinting part of the slot machine, respins are triggered when six yellow pearls, each carrying a certain monetary amount, appear in any game mode. You get six respins for a starter but can earn more for each “+1” landed during the bonus feature. On each respin, new yellow pearls can appear and when they do so, they stick to and remain on their positions until the end of the feature. DUE TO MARKET CONDITIONS WE ARE EXPERIENCING DELAYS IN RESPONSE TIMES. Chinese Loong’s egg in water Help other Aussie Coins and Notes users shop smarter by writing reviews for products you have purchased. Golden Dragon is another popular dragon-themed slot machine developed by GameArt. Here are some key differences and similarities: Help other Aussie Coins and Notes users shop smarter by writing reviews for products you have purchased.
https://www.waysoft.net/vegasnow-thrilling-online-casino-game-at-auvegasnow-com/
Jika Anda sudah melakukannya, barang Anda belum sampai, atau tidak sesuai deskripsi, Anda dapat melaporkannya ke OLYMPUS88 dengan membuka kasus. Dengan dukungan provider kelas dunia seperti Pragmatic Play, PG Soft, Habanero, dan banyak lagi, KRIPTO88 memastikan semua game yang tersedia memiliki kualitas terbaik. Bahkan, situs-situs besar seperti Pragmatic123, PragmaticID, Pragmatic88, hingga King88 telah menjadi mitra resmi KRIPTO88. The Super Scatter symbols can trigger multipliers up to 1000x, especially within the bonus round — offering some of the highest returns in any Gates of Olympus variant. It depends on the platform. Gates of Olympus Super Scatter is available in both demo and real-money versions across licensed online casinos. Selain itu COY99 juga menyediakan beragam bonus tambahan bagi pecinta SLOT777, 2 yang paling favorit adalah bonus new member 100 dengan minimal depo 10k yang memberikan bonus 100 persen diawal bagi member baru. Serta Slot bet kecil mulai dari 100 perak dan 200 perak yang semakin melipat gandakan peluang menang para member, hal ini semakin memastikan peluang jackpot tanpa batas di COY99 bisa dirasakan oleh mayoritas member kami di Indonesia.
Your comment is awaiting moderation.
Как выбрать хорошее онлайн-казино для азартных развлечений
Выбор надежного онлайн-казино для игр — важная задача для тех, кто хочет получить прозрачную игру и максимальное удовольствие. В этой статье рассмотрим основные факторы выбора проверенного ресурса.
Репутация и лицензия
Одним из главных признаков добросовестного казино является наличие лицензии от официального органа, например, MGA, Curacao или UKGC. Лицензия гарантирует прозрачность работы и защиту интересов игроков.
Не менее важно проверить мнения пользователей на тематических форумах и рейтинге сайтов. Хорошие казино имеют множество положительных комментариев и подтвержденные выплаты.
Разнообразие игр и софт
Выбирайте игровой клуб с широким ассортиментом игр — от классических слотов до покера. Качественный софт от известных разработчиков (NetEnt, Microgaming, Playtech) обеспечивает безопасность игрового процесса.
Бонусы и акции
Надежные бонусы помогут увеличить возможность выигрыша. Важно внимательно изучить условия бонусных программ — требования к отыгрышу (wager), сроки действия и ограничения.
Способы платежей
Лучшее онлайн-казино предлагает широкий выбор платежных систем — карты Visa/MasterCard, электронные кошельки, криптовалюты. Быстрые и безопасные пополнения и снятия средств обеспечивают комфорт и доверие top 10 casino online
Поддержка клиентов
Качественная служба поддержки — залог решения в любых ситуациях. Предпочтительно круглосуточное общение через чат, электронную почту или телефон на удобном языке.
Подведем итог
Выбирайте игровой клуб с официальным разрешением, хорошей оценками, разнообразным ассортиментом игр и софтом от проверенных компаний. Обращайте внимание на правила акций и удобство платежей, а также на профессиональную поддержку клиентов.
Тщательный подбор надежного онлайн-казино — залог выгодного и приятного азартного времяпрепровождения в интернете.
Your comment is awaiting moderation.
дивитися найкращі фільми 2025 кримінальні серіали дивитися онлайн
Your comment is awaiting moderation.
Die Benutzeroberfläche des Spielautomaten Gates of Olympus ist in hellen und frohen Farben gestaltet. Der Online-Slot dreht sich um die griechischen Götter. Seine Hauptfigur ist Zeus. Im Hintergrund ist der Berggipfel selbst zu sehen – der Olymp. Die Grafiken sind, wie bei allen Produkten dieser Firma, von hoher Qualität. Sie können Gates of Olympus gratis spielen und alle Vorteile des Spielautomaten genießen. Die Entwickler haben durch die gute musikalische Untermalung eine möglichst angenehme Atmosphäre für Slot-Benutzer geschaffen. A good tactic for Gates of Olympus to extend playtime and reduce risk is to use a smaller bet. Betting smaller is going to help you also go through the volatility of the game and therefore increase your chances of hitting the bonus round. These play os useful especially if you have a small budget or conservative person. Remember, patience is key!
https://minecraftcommand.science/forum/discussion/topics/noch-eine
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data. Almighty Jackpots Realm Of Poseidon Dramatische Animationen und eine großartige Auswahl an Bonusfunktionen machen „Gates of Olympus 1000″ zu einem sehr attraktiven Spiel. Die Kaskadenfunktion findet nach jeder einzelnen Spielrunde statt, in der Gewinnkombinationen ausgezahlt wurden und anschließend die Gewinnsymbole von ihren Positionen verschwinden. Die verbleibenden Symbole fallen an den unteren Rand der Walzen und anschließend werden die nicht besetzen Positionen mit neuen Symbolen gefüllt. Die Kaskadenfunktion kann theoretisch unendlich oft hintereinander stattfinden.
Your comment is awaiting moderation.
перейдите на этот сайт кракен онион
Your comment is awaiting moderation.
Профессиональная переподготовка по курсу «Контрольно-измерительные приборы» по всей России https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/registriruyuschiy-kalibrator-fluke-754/
Цена: 1 230 ?
Время работы:
Бабинов Александр Леонидович , Сургут, ХМАО – Югра https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/gazoanalitka/trassovyy-gazoanalizator-tgaes/
Технический центр «ЖАиС» является дилером известных отечественных и зарубежных производителей контрольно-измерительных приборов в России https://sbn-66.ru/
В ассортименте — оригинальные образцы инструментов и систем неразрушающего контроля https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/gazoanalitka/gazoanalizatory-sgoes/
В продаже — анализаторы качества продукции, другие устройства для контроля измерений характеристик и параметров функционирования технологического оборудования https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/vlagomery-nefti/vlagomery-nefti-potochnye-rhase-dynamics/
Воспользуйтесь выгодным предложением нашего дилерского центра и купите приборы для измерений по цене, рекомендованной производителем https://sbn-66.ru/raskhodomery-shtray-mass-1/raskhodomery-shtray-mass/
Товаров 10 https://sbn-66.ru/truboprovodnaya-armatura/zadvizhki-shibernye-nozhevye-avk-avk-vag-vag-cyl-/
Your comment is awaiting moderation.
С заботой о вашем ребенке https://shcherbinins.ru/uslugy
Мария Коваль https://shcherbinins.ru/aboutus
Тимур , благодарю Вас и Надежду ! Мне столько о ней положительных эмоций сегодня сказали, что она очень профессионально отработала и с душой ! Спасибо https://shcherbinins.ru/aboutus
Заказывали канапе-сеты на юбилей мужа https://shcherbinins.ru/
Хотелось чего-то необычного, чтобы удивить гостей, и ребята из «Мосфуршет кейтеринг» справились на 100 %! Всё приехало вовремя, оформлено просто шикарно, а главное — вкус невероятный https://shcherbinins.ru/
Особенно понравились канапе с лососем и сливочным сыром, их буквально расхватали за первые 10 минут! Теперь только к вам https://shcherbinins.ru/contacts
С https://shcherbinins.ru/contacts
Никаких наценок: все цены на сайте равны ценам ресторанов https://shcherbinins.ru/
Еда для свадьбы в 1 клик https://shcherbinins.ru/aboutus
Your comment is awaiting moderation.
Статьи и новости:
Попробуем немного приоткрыть завесу тайн будущего…ну, примерно на месяц https://sinapple.ru/collection/antitsellyulitnaya-kosmetika/product/keenwell-modeling-body-system-tratamiento-reafirmante-accion-integra-modeling-body-s Как? Спросим у Вселенной, ведь она «видит и знает» всё!
Your comment is awaiting moderation.
В интерьере этой трехкомнатной квартиры дизайнеры воплотили модный и современный стиль модернизм https://si-design.ru/three-storey_house
Четкая геометрия пространства, интересные дизайнерские находки, комбинирование разнообразных материалов, современные…
Мы работаем с частными бригадами и несем гарантии и ответственность за всю сделанную работу https://si-design.ru/academic
Средняя цена за кв https://si-design.ru/vipstyle
м https://si-design.ru/2h-komnatnay-kvartira
7 тыс https://si-design.ru/laim70
р https://si-design.ru/hollandpark60m
Они работают в нашем программном решении и в связке с дизайнером https://si-design.ru/building-survey
У них огромный опыт ремонта по дизайн проектам https://si-design.ru/o-nas
Этим мы исключаем ситуацию, когда дизайнер обвиняет во всем прораба, а прораб дизайнера https://si-design.ru/the_girls_bedroom
Мы в социальных сетях https://si-design.ru/2h-komnatnay-kvartira
Цена в Москве https://si-design.ru/tushino-2018
Это проекция на плоскость каждой стены в помещении https://si-design.ru/portfolio
Они позволяют увидеть все особенности отделки и просчитать ее площади и объемы https://si-design.ru/rumyantsevo-park
Развертки служат источником информации для исполнителей (строители, электрики, сантехники, мебельщики, зеркальщики и др.). Гарантируют, что реальность будет соответствовать дизайн-проекту https://si-design.ru/lime74m2
3-к квартира https://si-design.ru/vse-o-design
Your comment is awaiting moderation.
дивитися серіали онлайн серіали HBO та Apple TV українською
Your comment is awaiting moderation.
Wenn du Casino Slots ohne OASIS bei Jokery spielen möchtest, solltest du dir Spiele wie Temple Tumble Megaways, Sizzling Hot Deluxe, Big Bass Splash, Duck Hunters, Rich Wilde and the Tombe of Madness, Moon Princess 100 oder Book of Ra Deluxe anschauen. Es gibt viele populäre Slots, aber auch viele weniger populäre Spiele mit hoher Qualität. Wie der Titel bereits erahnen lässt, dreht sich bei Lucky Lady's Charm alles ums Glück. Dieses wird eindrucksvoll durch Motive wie das Hufeisen, den Glücksklee oder auch Marienkäfer symbolisiert. Zentrale Figur ist und bleibt natürlich die Lucky Lady selbst. Inzwischen hat sie Kultstatus im Hause Novoline und ist weit über die Grenzen ihrer Heimat Österreich hinaus bekannt. Schauen wir uns an, wie es um die Gewinnwertung der Symbole steht.
https://www.abclinuxu.cz/lide/bullmilite1988
Zwar gibt es keine deutsche Lizenz, aber wer Wert auf Flexibilität, Auswahl und hohe Willkommensboni legt, findet hier eine attraktive Alternative zu klassischen deutschen Anbietern. Für erfahrene Spieler, die Abwechslung und moderne Features suchen, halte ich Richroyalcasino definitiv für einen Versuch wert. Mit ihren Chardonnays agieren Topwinzer aus Deutschland, der Schweiz und Österreich inzwischen in atemberaubenden qualitativen Höhen. So facettenreich wie ein Paradiesvogel, so ist auch die Zigarre. Jede so unterschiedlich und so einzigartig, wie der Mensch, der sie raucht.Überzeugen Sie sich selbst und machen Sie sich ein Bild von unserem breiten Produktsortiment. Sei es stark oder mild, würzig oder fein. In unserem Online Shop ist für jeden etwas dabei.Sie möchten eine Zigarre kaufen? Wir helfen Ihnen gern dabei! Wählen Sie aus über 2’700 verschiedenen Zigarren aus. Damit die Auswahl etwas einfacher fällt, empfehlen wir Ihnen die Zigarren mit dem Filter zu sortieren. So können Sie einfach alle Zigarren nach Grösse, Stärke, Preis, Deckblattfarbe und vielem mehr anzeigen lassen.
Your comment is awaiting moderation.
Как выбрать хорошее игровой клуб для игр
Выбор надежного онлайн-казино для развлечений — важная задача для тех, кто хочет получить прозрачную игру и выгодное удовольствие. В этой статье рассмотрим основные аспекты выбора проверенного ресурса.
Репутация и лицензия
Одним из главных признаков надежного онлайн-казино является наличие лицензии от регулируемого органа, например, MGA, Curacao или UKGC. Лицензия гарантирует честность работы и защиту прав игроков.
Не менее важно проверить репутацию пользователей на тематических форумах и рейтинг сайтов. Хорошие казино имеют множество положительных комментариев и подтвержденные выплаты.
Разнообразие игр и софт
Выбирайте онлайн-казино с широким выбором игр — от классических слотов до блекджека. Качественный софт от известных разработчиков (NetEnt, Microgaming, Playtech) обеспечивает сбалансированность игрового процесса.
Бонусы и акции
Надежные бонусы помогут увеличить возможность выигрыша. Важно внимательно изучить условия бонусных программ — требования к отыгрышу (wager), сроки действия и ограничения.
Способы платежей
Лучшее онлайн-казино предлагает удобный выбор платежных систем — карты Visa/MasterCard, электронные кошельки, криптовалюты. Быстрые и безопасные депозиты и выводы средств обеспечивают комфорт и доверие бонусы в онлайн казино
Поддержка клиентов
Качественная служба поддержки — залог решения в любых ситуациях. Предпочтительно круглосуточное общение через чат, электронную почту или телефон на удобном языке.
Подведем итог
Выбирайте казино с официальным разрешением, хорошей репутацией, разнообразным спектром игр и софтом от проверенных поставщиков. Обращайте внимание на условия бонусов и удобство платежей, а также на профессиональную поддержку клиентов.
Тщательный подбор надежного игрового клуба — залог безопасного и приятного развлечений в интернете.
Your comment is awaiting moderation.
Elementy wizualne i dźwiękowe w Mjolnir wynoszą doświadczenie z gry na niezwykłe wyżyny. Gra oferuje oszałamiające grafiki w tematyce nordyckiej, które przenoszą graczy do innej epoki. Towarzyszy temu potężna ścieżka dźwiękowa z motywami mitologicznymi, zapewniając głęboko immersyjne doświadczenie. Przy adaptacji mitologii do form rozrywkowych pojawiają się pytania o etykę i odpowiedzialność twórców. Ważne jest, aby nie upraszczać czy stereotypizować źródła, a jednocześnie unikać banalizacji i komercjalizacji. Szacunek dla pierwotnych przekazów i ich głębi jest kluczem do tworzenia wartościowych dzieł, które będą inspirować, a nie naruszać dziedzictwa. Mitologia to zbiór opowieści, wierzeń i symboli, które wywodzą się z dawnych kultur i religii. Od starożytnej Grecji, przez Rzym, aż po nordyckie wierzenia, mitologie pełnią funkcję wyobrażeniowego szkicu wyjaśniającego świat oraz miejsce człowieka w nim. Wspólnie tworzą one nie tylko narracje o bogach i herosach, ale także stanowią podstawę kulturowej tożsamości, co ma kluczowe znaczenie dla rozwoju wyobraźni. Mitologia wpływa na kształtowanie wyobraźni zarówno w sztuce, literaturze, jak i w nowoczesnych mediach, w tym w branży gier komputerowych.
https://alsahragroup.com/recenzja-casino-tiki-taka-emocjonujaca-gra-kasynowa-dla-graczy-z-polski/
Gates of olympus: an exciting new game at online casinos. There are a lot of blackjack apps available in the Android store, and the quicker that players get their head around it the better. The app relatively new, they hold gaming licenses not only from the UK Gambling Commission but also Alderney Gambling Control Commission. The slots use a random number generator, the welcome bonus package has the lowest wagering requirement of any Miami online casino on our list. Voila! Znajdź bonus w swoim profilu i aktywuj go, aby zacząć grać. Age of the Gods to propozycja, z jaką w 2006 roku przybyła do nas firma Playtech. Slot ten wyróżnia się ponad innymi obecnością aż czterech progresywnych jackpotów, które na zawsze zmieniły świat slotów wideo, dzięki rekordowym, kilkunastomilionowym wygranym, jakie od czasu do czasu wypłacają. Współczynnik RTP gry wynosi 96.37%.
Your comment is awaiting moderation.
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data. Share the post “Pragmatic Play, Gates of Olympus Super Scatter in esclusiva su Sisal” Anche dal lato pratico, Gates of Olympus Super Scatter mantiene alta la qualità. L’interfaccia è ben organizzata: i pulsanti principali sono facilmente raggiungibili, i dati di saldo e puntata sempre visibili. Funziona senza scatti sia su desktop che su slot mobile, con tempi di caricamento veloci. I menu sono intuitivi e supportano diverse lingue, tra cui l’italiano. Il passaggio da modalità normale a Giri Gratis o Super Scatter avviene in modo fluido, rendendo l’esperienza di gioco coinvolgente e reattiva in ogni momento.
https://micro138.org/recensione-approfondita-del-gioco-casino-tiki-taka-lesperienza-unica-per-i-giocatori-in-italia/
Might of Freya Megaways Slots Demo Might of Freya Megaways Slots Demo In Gates of Olympus è possibile ricavare combinazioni vincenti a prescindere dalla posizione dei simboli sulla griglia di gioco. Inoltre, la Tumble Feature consente di concatenare ad oltranza combinazioni vincenti. Ogni volta i simboli vincenti scompaiono dai rulli e quelli che cadono subito dopo contribuiscono alla formazione di nuove combinazioni fortunate. We absolutely love your blog and find the majority of your post’s to be precisely what I’m looking for. Would you offer guest writers to write content in your case? I wouldn’t mind creating a post or elaborating on a number of the subjects you write about here. Again, awesome site! La slot Gates of Olympus ha un RTP che si attesta sul 96,50%, un valore leggermente superiore alla media che si trova in genere nelle slot online con soldi veri. La volatilità è alta, il che si traduce in vincite potenzialmente elevate ma meno frequenti. Come la maggior parte delle slot Cluster Pays, poi, presenta una griglia di gioco più ampia del solito, con ben 6 rulli.
Your comment is awaiting moderation.
La nostra piattaforma di gioco Orbit è fuori dal mondo, proprio come la slot Gates of Olympus™. Puoi goderti un gameplay senza attriti con il nostro client potente e leggero. La piattaforma basata su browser si carica rapidamente e senza intoppi. Puoi goderti tutte le funzionalità di questa fantastica slot e di altri giochi da casinò a tuo piacimento. Puoi giocare a blackjack, roulette e altre slot a tema sul cellulare. Buon divertimento. Su questa pagina è possibile anche giocare alla slot Gates of Olympus gratis. Il tutto grazie alla versione in modalità DEMO presente proprio sopra questa recensione. È il modo migliore per scoprire ogni piccolo segreto su questo titolo appena uscito è proprio quello d’immergersi nella Gates of Olympus demo e provarla senza soldi gratis. Su questa pagina è possibile anche giocare alla slot Gates of Olympus gratis. Il tutto grazie alla versione in modalità DEMO presente proprio sopra questa recensione. È il modo migliore per scoprire ogni piccolo segreto su questo titolo appena uscito è proprio quello d’immergersi nella Gates of Olympus demo e provarla senza soldi gratis.
https://laxusspa.com/recensione-approfondita-del-gioco-casino-tiki-taka-unesperienza-avvincente-per-i-giocatori-italiani/
Sì, Guru Casino supporta più lingue per garantire che i giocatori di tutto il mondo possano accedere e utilizzare facilmente la piattaforma. La piattaforma offre opzioni linguistiche multiple, tra cui inglese, tedesco, francese, spagnolo, italiano, ecc. I giocatori possono scegliere la lingua preferita durante la procedura di registrazione, per avere la certezza di comprendere facilmente tutti i contenuti e i termini presenti sul sito web. Inoltre, Guru Casino supporta più valute, consentendo ai giocatori internazionali di depositare e prelevare fondi nella propria valuta. Il supporto multilingua e multivaluta consente alla piattaforma di offrire un’esperienza di gioco senza barriere ai giocatori di tutto il mondo. Ma cosa rende le altre slot machine di Pragmatic Play così diverse dalle altre? Innanzitutto, i loro giochi includono una grafica incredibile che non può essere trovata altrove. In secondo luogo, Pragmatic Play si concentra sulla creazione di giochi che offrono una grande quantità di intrattenimento, offrendo ai giocatori bonus unici ed emozionanti che mantengono sempre alta l’attenzione.
Your comment is awaiting moderation.
Как выбрать хорошее казино для развлечений
Выбор надежного казино для азартных развлечений — важная задача для тех, кто хочет получить независимую игру и максимальное удовольствие. В этой статье рассмотрим основные критерии выбора надежного ресурса.
Репутация и лицензия
Одним из главных признаков добросовестного игрового клуба является наличие лицензии от официального органа, например, MGA, Curacao или UKGC. Лицензия гарантирует законность работы и защиту интересов игроков.
Не менее важно проверить отзывы пользователей на тематических форумах и рейтинге сайтов. Хорошие онлайн-казино имеют множество положительных комментариев и подтвержденные выплаты.
Разнообразие игр и софт
Выбирайте игровой клуб с широким ассортиментом игр — от классических слотов до покера. Качественный софт от известных производителей (NetEnt, Microgaming, Playtech) обеспечивает сбалансированность игрового процесса.
Бонусы и акции
Надежные бонусы помогут увеличить возможность выигрыша. Важно внимательно изучить условия бонусных программ — требования к отыгрышу (wager), сроки действия и ограничения.
Способы платежей
Лучшее онлайн-казино предлагает разнообразный выбор платежных систем — карты Visa/MasterCard, электронные кошельки, криптовалюты. Быстрые и безопасные депозиты и снятия средств обеспечивают комфорт и доверие онлайн казино демо
Поддержка клиентов
Качественная служба поддержки — залог решения в любых ситуациях. Предпочтительно круглосуточное общение через чат, электронную почту или телефон на удобном языке.
Подведем итог
Выбирайте казино с официальным разрешением, хорошей оценками, разнообразным спектром игр и софтом от проверенных разработчиков. Обращайте внимание на правила акций и удобство платежей, а также на профессиональную поддержку клиентов.
Тщательный подбор надежного игрового клуба — залог безопасного и приятного игрового процесса в интернете.
Your comment is awaiting moderation.
страница актуальные зеркала kraken
Your comment is awaiting moderation.
bono sin deposito para blackjack online para peruanos. Una plataforma no debe limitar a sus clientes, ha sido desarrollada por Pragmatic Play y ofrece a los jugadores tiradas gratis activadas por comodines y líneas de pago que funcionan en ambos sentidos. Si el crupier no se pasa y el recuento de sus cartas está más cerca de 21 que la mano del crupier, ruleta y baccarat. Casino.guru es un sitio de información independiente sobre casinos online y juegos de casino online. No forma parte de ningún operador de juegos de azar ni de cualquier otra institución. Todas nuestras reseñas y guías se elaboran con sinceridad, conforme al criterio y buen juicio de los miembros de nuestro equipo de expertos independientes; aun así, su único fin es informativo y no debería interpretarse ni considerarse como un consejo legal. Antes de jugar en el casino elegido siempre deberías asegurarte de que cumples con todos los requisitos.
https://alligatorlaundromat.com/?p=3740
We read every piece of feedback, and take your input very seriously. Un proyecto ambicioso cuyo objetivo es celebrar el trabajo de las empresas más responsables del mundo del iGaming y ofrecerles el reconocimiento que merecen. Los símbolos multiplicadores están presentes en todos los carretes y pueden aparecer aleatoriamente tanto durante los giros como durante las caídas. Cada vez que aparece uno de estos símbolos, toma un valor multiplicador aleatorio de 2x a 1000x, y estos valores se combinan al final de una secuencia de caída y se aplican a la ganancia del jugador. ¿Cómo funciona el Super Scatter en Gates of Olympus Super Scatter? Estos juegos funcionan de forma similar a la mayoría de las tragamonedas de Pragmatic, pero tienen una peculiaridad: además de los símbolos scatter tradicionales, el juego tiene “super scatters” que te permiten acceder a rondas de bonificación especiales, con pagos muy superiores a lo que suelen prometer los slots de Pragmatic.
Your comment is awaiting moderation.
Sí, ya que su desarrollador, Pragmatic Play, hizo lo necesario para que Gates of Olympus slot se adapte a smartphones con Android e iOS. Gates of Olympus te introduce a la fuerza de los Dioses del Olimpo en esta tragamonedas de 6 carretes, 5 filas y un motor de juego All Ways que rompe con el concepto de líneas de pago y te permitirá formar combinaciones ganadoras en todos los sentidos. Aquí en KTO, ofrecemos varios juegos similares a Gates of Olympus. Si quieres seguir el tema de la antigua Grecia, puedes disfrutar de la tragamonedas Rise of Olympus. Gates of Olympus Xmas 1000 se suma a la serie de tragamonedas Greek Gods de Pragmatic Play, tras los recientes éxitos Wisdom of Athena 1000 y Bow of Artemis. El Gates of Universe tragamonedas ofrece una amplia gama de opciones de apuesta que satisfacen tanto a jugadores casuales como a aquellos que prefieren realizar apuestas más significativas. La apuesta mínima es de £0.2, lo cual es ideal para jugadores que desean disfrutar del juego sin comprometer una gran parte de su bankroll. Por otro lado, la apuesta máxima asciende a £100, permitiendo a los jugadores más experimentados y con mayor capital optar por apuestas más altas y, potencialmente, ganar premios mayores.
https://svanjewellery.com/review-del-juego-balloon-en-casinos-online-para-argentina/
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data. Si te gusta este tipo de tragaperras con temática sobre la mitología griega, te recomendamos que pruebes esta slot Amazing Link Zeus, de Microgaming. En la tragaperras Gates of Olympus podrás entrar al Olimpo para hacerte con algunos de los tesoros que poseen los mismos dioses. Un casino que compite fuerte con sus rivales es VERSUS. Al investigar este casino, descubrí que, aunque su oferta de slots es más reducida, su bono de bienvenida tiene un plazo de 30 días para disfrutarlo en la tragaperras Gates of Olympus.
Your comment is awaiting moderation.
Как выбрать хорошее игровой клуб для развлечений
Выбор надежного игрового клуба для азартных развлечений — важная задача для тех, кто хочет получить прозрачную игру и лучшее удовольствие. В этой статье рассмотрим основные факторы выбора надежного ресурса.
Репутация и лицензия
Одним из главных факторов надежного онлайн-казино является наличие лицензии от регулируемого органа, например, MGA, Curacao или UKGC. Лицензия гарантирует прозрачность работы и защиту прав игроков.
Не менее важно проверить мнения пользователей на тематических форумах и рейтинг сайтов. Хорошие казино имеют множество положительных комментариев и подтвержденные выплаты.
Разнообразие игр и софт
Выбирайте онлайн-казино с широким ассортиментом игр — от классических слотов до рулетки. Качественный софт от известных разработчиков (NetEnt, Microgaming, Playtech) обеспечивает сбалансированность игрового процесса.
Бонусы и акции
Щедрые бонусы помогут увеличить шанс выигрыша. Важно внимательно изучить условия бонусных программ — требования к отыгрышу (wager), сроки действия и ограничения.
Способы платежей
Лучшее онлайн-казино предлагает разнообразный выбор платежных систем — карты Visa/MasterCard, электронные кошельки, криптовалюты. Быстрые и безопасные депозиты и снятия средств обеспечивают комфорт и доверие онлайн казино с выводом денег
Поддержка клиентов
Качественная служба поддержки — залог помощи в любых ситуациях. Предпочтительно круглосуточное общение через чат, электронную почту или телефон на удобном языке.
Подведем итог
Выбирайте игровой клуб с лицензией, хорошей оценками, разнообразным ассортиментом игр и софтом от проверенных разработчиков. Обращайте внимание на условия бонусов и удобство платежей, а также на профессиональную поддержку клиентов.
Тщательный подбор надежного игрового клуба — залог безопасного и приятного игрового процесса в интернете.
Your comment is awaiting moderation.
Аренда NVMe VPS/VDS https://xhost24.com мощные виртуальные серверы с быстрыми SSD NVMe. Высокая производительность, стабильная сеть, защита и удобное управление. Подходит для e-commerce, API, CRM, игровых и веб-проектов любого масштаба.
Your comment is awaiting moderation.
Он контролирует выполнение работ и соблюдение сроков, решает возникающие задачи и вопросы, отчитывается о результатах https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Tagline Awards, 2021 г https://proffseo.ru/
Результаты:
Максимальные конверсии по заявкам и звонкам https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Для этого используем современные технологии: создаем турбо-страницы в Яндексе и AMP в Google для страниц карточек товаров и страницы каталога https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Выше скорость – больше конверсий https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Tagline Awards, 2021 г https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Your comment is awaiting moderation.
Все задачи ведем в CRM Битрикс24 https://proffseo.ru/privacy
Вы сможете видеть их выполнение в онлайн режиме https://proffseo.ru/prodvizhenie-sajtov-po-rf
Можем работать и в вашей CRM https://proffseo.ru/privacy
Делаем мобильную версию сайта удобной https://proffseo.ru/prodvizhenie-sajtov-po-rf
После чего, одним из ключевых моментов в продвижении сайта, стал выбор и присвоение ему региона, в котором требуется занять высокие позиции https://proffseo.ru/prodvizhenie-sajtov-po-rf
Ни один сайт не принесет должного эффекта для бизнеса, если он не «раскручен» и пользователи не находят его по целевым ключевым словам в выдаче поисковых систем https://proffseo.ru/prodvizhenie-sajtov-po-rf
Ваш онлайн-бизнес выйдет в ТОП-10 и получит заслуженную долю поискового трафика в масштабах Рунета https://proffseo.ru/privacy
Еще истории успеха https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Your comment is awaiting moderation.
подробнее https://bonus-betting.ru/getx-promokod/
Your comment is awaiting moderation.
Nous pouvons également souligner les nombreux tours gratuits offerts durant le jeu. C’est toujours gratifiant de recevoir quelques free spins et jouer gratuitement tout en amassant des gains réels. Commencez à jouer à Gates of Olympus Super Scatter maintenant ! Si vous n’avez pas de compte, inscrivez-vous dès maintenant sur Starcasino.be, un casino en ligne belge sûr, avec une licence officielle approuvée par la Commission belge des jeux de hasard. Que vous jouiez en mode démo ou avec de l’argent réel dans les meilleurs casinos en ligne, Gates of Olympus promet une aventure de jeu passionnante. Obtenez des combinaisons gagnantes sur les lignes de paiement et activez la fonction Tumble pour augmenter vos features. Rejoignez les joueurs chanceux qui ont déjà succombé au charme de cette machine à sous. Les symboles présents sur les rouleaux mettent en avant des éléments mythologiques, tels que Zeus et l’Olympe, pour immerger pleinement les joueurs dans l’ambiance du jeu. Que vous choisissiez de jouer gratuitement ou avec de l’argent réel dans les meilleurs casinos en ligne, Gates of Olympus vous garantit une expérience intense.
https://alsahragroup.com/une-analyse-approfondie-de-nine-casino-la-reference-des-casinos-en-ligne-en-france/
Gates of Olympus par Pragmatic Play nous offre un système de jeu aux fonctionnalités intéressantes. En-effet, il est possible de gagner sur toute la grille de jeu que ce soit horizontal, vertical ou diagonale. Cette machine classique offre un RTP de 99 % en mode Supermeter, ce qui permet un potentiel de gains intéressant. Les symboles fruits traditionnels rappellent les bandits manchots d’antan et incluent le fameux 777 qui offre les victoires les plus élevées. Le mode Supermeter se déclenche après chaque gain. Les mises augmentent, mais les récompenses aussi. Notre record personnel atteint 2 000 crédits en partant de 100. Nous te suggérons donc de constituer un solde suffisant si tu souhaites jouer en argent réel sur ce titre.
Your comment is awaiting moderation.
Dans nos revues de casino, en plus du fond merveilleux qui exprime la vie luxueuse des cheiks du Moyen-Orient. Ceux-ci ne sont en fait attribués à personne en particulier, mais elle sera à l’arrivée avec les meilleurs. Vérifiez toujours les termes et conditions avant de commencer à jouer, Red Lion casino n’est pas partenaire du programme d’auto-exclusion mentionné. Pariez gros, vous aurez le grand confort de bonus plus élevés et de rendements plus élevés. Vous pouvez obtenir 1 ou plusieurs Scatters sur les rouleaux, les symboles les plus payants de Rise of Dead ont des images des différents dieux de la culture égyptienne. Ne manquez pas ces jeux et laissez-vous vivre avec les meilleures conditions offertes, il est temps que vous compreniez ses fonctionnalités.
https://spade77.org/analyse-de-la-popularite-du-jeu-unique-casino-en-france/
BONAFIT88 Main santai sambil rebahan di kasur, tiba-tiba JP. Bonafit88 emang surganya Kaum Rebahan Cuan! Grille d’évaluation des projets MIGO88 adalah situs slot resmi 2025 dengan RTP live harian, scatter mantap, dan akses login anti blokir. Mainkan Mahjong Ways 2, Wild Bandito, hingga Gates of Olympus tanpa khawatir! La Galerie du Parc accueille l’artiste Jean-Louis Le Moal. PampaGo présente une ludothèque d’environ 2 000 jeux, dans laquelle Pragmatic Play occupe une place de choix. Vous y trouverez des machines à sous phares comme Sweet Bonanza ou Gates of Olympus Super Scatter. Le site opère sous licence Curaçao et mise sur des protocoles de sécurité fiables pour protéger les joueurs. Voici quelques modèles de jeu de la machine à sous en ligne Gates Of Olympus Full Scatter que vous devriez connaître, voir ci-dessous.
Your comment is awaiting moderation.
Amusez-vous avec la célèbre machine à sous Gates of Olympus de Pragmatic Play ! Obtenez des tours gratuits et d’autres bonus sur les meilleurs casinos aujourd’hui ou jouez au jeu gratuitement en regardant la démo de Gates of Olympus ci-dessous. Gates of olympus symbole de dispersion – Si vous envisagez de jouer au poker en ligne lorsque vous quittez le travail tous les soirs pour vous défouler, vous pouvez également créer des actifs dans le jeu pour des jeux existants qui peuvent être échangés contre de l’argent réel. Le marché des pièces de monnaie s’est élargi pour inclure non seulement des pièces anciennes, qui se jouent toutes sur 5 rouleaux et 25 lignes de paiement fixes avec des prix allant jusqu’à 500 pièces sur une ligne de paiement.
https://makabeer.space/unique-casino-un-avis-complet-pour-les-joueurs-francais/
Cette fonctionnalité s’active à chaque victoire. Les clusters de symboles ayant déclenché le gain disparaissent et les symboles des rangées du dessus prennent leurs places. En effet, ils tombent en cascade pour remplir les positions vides pour donner une nouvelle chance de former une combinaison gagnante… Et ainsi de suite jusqu’à ce que votre série de victoire ne s’achève. Si les free spins sont souvent associés aux symboles Scatters, sur Rise of Olympus extrême, ils se déclenchent d’une manière différente. Si nous arrivons à former suffisamment de clusters gagnants pour vider la grille, nous accédons aux bonus tours gratuits. En mode bonus, le Wild s’étend sur les troisième, quatrième et cinquième rouleaux, tandis que les deux premières bobines utilisent une mécanique de cascade. Cela signifie que les symboles gagnants disparaissent pour permettre de nouvelles combinaisons, offrant ainsi une série potentielle de gains successifs.
Your comment is awaiting moderation.
Precis som man kan förvänta sig av Pragmatic Plays slots håller Gates of Olympus hög kvalitet men vi är dock ändå förvånade över de ganska traditionella spelfunktionerna. Spelet tar plats på 6×5 spelplan men är utan vinstlinjer. Det krävs att man landar åtta likadana symboler varsomhelst på spelplanen för att få vinst. Ja, Mr Green ser till att tillhandahålla en provversion av Gates of Olympus Slot. Det innebär att du inte har möjlighet att vinna något men får en utmärkt möjlighet att upptäcka symboler och funktioner. Det kostar inget att provspela. Istället får du en känsla kring vad som väntar och kan avgöra om Gates of Olympus Slot är ett spel för dig eller inte. Gates of Olympus 1000 är ett spelautomatsspel utvecklat av Pragmatic Play, med deklarerad RTP på 96.50% och High volatilitet. Om du är intresserad av detaljerad information om spelautomaten Gates of Olympus 1000, kan du hitta det i Slot Information table. Den inkluderar dess tekniska specifikationer.
https://amootasemanomid.com/rip-city-en-recension-av-hacksaw-gamings-casino-slot/
Kom alltid ihåg att spela ansvarsfullt om du väljer att spela på casino online. På Casinochecken.se riktar sig allt innehåll till dig som är 18 år eller äldre. New players will take edge of matchup downpayment bonuses like 100% up to NZD500 and free spins packages on first deposits. These register offers increase starting funds and offer free of risk gameplay. When researching casinos, we take a look at the available encouraged bonuses and continuing promotions for present players. The best options provide advantages with reasonable wagering conditions to improve players’ chances of earning real cash. Reload bonuses, free rotates, cashback and loyalty programs provide continuous value. Many Kiwi users take the particular lookout for the best paying online internet casinos that guarantee trustworthy payouts of the money won.
Your comment is awaiting moderation.
Pe langa jackpoturile oferite de fiecare cazino in parte trebuie sa stiti ca cei de la Pragmatic ofera in mod constant promotii si premii aleatorii in timpul jocului. Astfel, cel mai cunoscut Jackpot care poate fi castiga la Gates Of Olympus slot este cel de tipul Drop and Wins, unde puteti castiga premii formidabile La nivel internațional, Gates of Olympus demo lei are recenzii de peste 4 stele, din maximul posibil de 5. O să-l găsești în cazinourile online din peste 50 de țări. În peste jumătate dintre acestea se află în Top 10. Este o performanță uluitoare, greu de egalat de către alte sloturi, chiar dacă sunt la fel de bine realizate precum The Wild Machine gratis. La slot machine online offre volatilità alta, che mediamente paga meno frequentemente ma, con la possibilità di ottenere delle vincite elevate, fino a ben 5mila volte il valore della scommessa eseguita nel giro. L’RTP, la percentuale teorica di vincita è fra le più vantaggiose, oltre il 96%.
https://premiumbrandedsolutions.com/?p=271266
About Entdecken \nSie auf PASINO.ch die \nbesten in der Schweiz erhältlichen \nCasinospiele, \nwie die aufregenden Video Slots «Gates of Olympus» oder «Book of Ra Deluxe». \nUnd wie in jedem guten Casino finden Sie hier auch Super Cherry 5000 – einen \nKlassiker, der in der Schweiz besonders beliebt ist – sowie viele andere \nbeliebte Titel. Playfina Casino is a modern online gaming platform tailored for Australian players who value fast payouts, high-quality games, and a secure playing environment. The casino offers an extensive range of pokies, live dealer tables, jackpot titles, and weekly promotions designed to keep players engaged. With AUD support and instant deposits through popular local payment methods, Playfina ensures a smooth and enjoyable gaming experience for every user across Australia.
Your comment is awaiting moderation.
веб-сайте Учредительные уставные документы
Your comment is awaiting moderation.
Good web site top speed
https://airvission.wordpress.com/
https://paper.wf/airvission/
https://www.tumblr.com/airvission
https://speakerdeck.com/airvission
https://www.designspiration.com/hopresongli1977/
https://www.thebostoncalendar.com/user/134782
https://www.coursera.org/learner/airvission
https://camp-fire.jp/profile/airvission
https://www.mymeetbook.com/airvission
https://doodleordie.com/profile/airvission/
https://www.mapleprimes.com/users/airvission
https://qiita.com/airvission
https://pastebin.com/u/airvission
https://gitlab.com/airvission
https://www.cake.me/me/airvission
https://www.4shared.com/u/DKYFifZ6/ho_online.html
https://www.intensedebate.com/people/airvission
https://gravatar.com/hopresongli1977
https://slides.com/airvission
https://audiomack.com/airvission
https://www.exchangle.com/airvission
https://letterboxd.com/airvission/
https://coolors.co/u/airvission
https://writexo.com/share/ab63bae6900b
https://www.checkli.com/airvission
https://onespotsocial.com/airvission
https://bitspower.com/support/user/airvission
http://freestyler.ws/user/613687/airvission
https://forum.lexulous.com/user/airvission
https://phatwalletforums.com/user/airvission
https://www.pubpub.org/user/airvission-airvission
https://dreevoo.com/profile.php?pid=925729
https://pinshape.com/users/8872662-airvission?tab=designs
https://fairygodboss.com/users/profile/XxSWRBI_53/airvission
https://www.komoot.com/user/5448354053238
https://photozou.jp/user/top/3435053
https://www.prestashop.com/forums/profile/1970126-airvission/
https://support.mozilla.org/ru/user/ho.presongli1977/
https://www.demilked.com/author/airvission/
https://www.ted.com/profiles/50862162
https://pxhere.com/en/photographer/4866236
https://www.youtube.com/redirect?event=channel_description&q=https://airvission.ru/
https://m.youtube.com/redirect?q=https://airvission.ru/
https://t.me/iv?url=https://airvission.ru/
https://myspace.com/airvission.ru/
https://mitsui-shopping-park.com/lalaport/iwata/redirect.html?url=https://airvission.ru/
https://redirect.camfrog.com/redirect/?url=https://airvission.ru/
https://optimize.viglink.com/page/pmv?url=https://airvission.ru/
https://wikimapia.org/external_link?url=https://airvission.ru/
https://trello.com/add-card?source=mode=popup&name=click%2Bhere&desc=https://airvission.ru/
https://bbs.pku.edu.cn/v2/jump-to.php?url=https://airvission.ru/
https://foro.infojardin.com/proxy.php?link=https://airvission.ru/
https://justpaste.it/redirect/628nu/https://airvission.ru/
https://kaskus.co.id/redirect?url=https://airvission.ru/
Your comment is awaiting moderation.
Try your luck and win big withsurewin.
Classic games like blackjack and roulette are presented with high-quality graphics.
Your comment is awaiting moderation.
Try your luck at an online casino spingo88 and enjoy exciting games.
Spingo88 complements its security features with responsive customer service.
Your comment is awaiting moderation.
Discover new opportunities with v blink, that will change the way you think about communication.
Both individual and corporate users find Vblink exceptionally versatile for communication needs.
Your comment is awaiting moderation.
Try your luck and win big in slotgpt casino!
At the forefront of online gaming, SlotGPT Casino merges classic casino thrills with innovative AI advancements.
Your comment is awaiting moderation.
Продолжение kraken официальный сайт
Your comment is awaiting moderation.
Сайт рассказывает о функциях и преимуществах Garmin Tactix, включая навигацию и тактические режимы. Материалы помогают понять, чем часы гармин тактик отличаются от обычных смарт-часов. Есть рекомендации, как купить часы Garmin Tactix. https://www.behance.net/charlesfortsman
Ресурс посвящён обзорам линейки Garmin tactix и её ключевым технологиям. Здесь раскрываются возможности, за которые ценят garmin часы tactics. Пользователи могут выбрать подходящие часы гармин тактик и найти, где их купить. https://www.producthunt.com/@andrey1548730
Информационный сайт о гармин тактикс помогает изучить характеристики и отличия Garmin Tactix. Материалы подходят для тех, кто ищет надёжные тактические часы. Также представлены советы, как купить часы Garmin Tactix. https://www.producthunt.com/@andrey1548730
Сайт выступает экспертным источником информации о Garmin Tactix и их возможностях. Здесь можно сравнить часы гармин тактик и выбрать подходящую модель. Ресурс помогает понять, где безопасно купить часы Garmin Tactix. https://inkbunny.net/Garminrussia
Ресурс объединяет обзоры и характеристики garmin часы tactics, раскрывая особенности серии Garmin tactix. Материалы подходят для быстрого выбора модели. Также сайт подсказывает, как правильно купить часы Garmin Tactix. https://kemono.im/inkwave/chasy-garmin-taktik
Your comment is awaiting moderation.
Продажа тяговых faamru.com аккумуляторных батарей для вилочных погрузчиков, ричтраков, электротележек и штабелеров. Решения для интенсивной складской работы: стабильная мощность, долгий ресурс, надёжная работа в сменном режиме, помощь с подбором АКБ по параметрам техники и оперативная поставка под задачу
Your comment is awaiting moderation.
Продажа тяговых ab-resurs.ru аккумуляторных батарей для вилочных погрузчиков и штабелеров. Надёжные решения для стабильной работы складской техники: большой выбор АКБ, профессиональный подбор по параметрам, консультации специалистов, гарантия и оперативная поставка для складов и производств по всей России
Your comment is awaiting moderation.
Перейти на сайт krab3.at
Your comment is awaiting moderation.
Женский журнал Стили, бренды и шопинг
Сегодня модный портал — это не просто справочник о моде, это настоящий гид по образу, маркам и приобретениям. В этой статье мы рассмотрим главные аспекты женского образа, расскажем о самых популярных брендах и дадим советы по умному шопингу.
Современные стили в женской моде
Стиль — это способ самовыражения, отражение личности и вкуса. Существует множество вариантов:
– Классический стиль — строгость, аккуратные линии и нейтральные тона https://t.me/stiliodezhdy
– Кэжуал|casual|повседневный стиль — удобство и простота, натуральные ткани и свободный силуэт.
– Бохо|богемный стиль — эклектика, этнические принты и многослойность одежды.
– Спортивный стиль|спортшик|athleisure — функциональность и стиль, комбинирование спортивных и модных элементов.
Выбор стиля зависит от жизненного образа, личных предпочтений и ситуации.
Известные бренды в женской моде
Мировые бренды задают тренды и предлагают качественную одежду, обувь и аксессуары. Среди самых популярных:
– Chanel|Шанель|Шанэлл — символ роскоши и классики.
– Gucci|Гуччи|Гуччи — яркие цвета, необычные принты и экспериментальные решения.
– Zara|Зара|Зара — демократичная мода высокого качества.
– H&M|Эйч энд Эм|Хендэм — доступный стиль и вариативность.
– Prada|Прада|Прада — минимализм и качество.
Кроме того, популярны локальные дизайнеры и молодые бренды, которые предлагают свежие взгляды на стиль.
Советы по успешному шопингу
Правильно организованный покупки — залог успеха. Чтобы покупки радовали, стоит учитывать несколько правил:
– Ставьте цели — выберите, что именно нужно купить: базовый гардероб, аксессуары, вечернее платье.
– Изучайте тренды — следите за новинками, посещайте журналы.
– Планируйте бюджет — фильтруйте расходы, чтобы не тратить необдуманно.
– Используйте скидки и акции — это позволяет сберегать.
– Примеряйте одежду — чтобы убедиться в удобстве и стиле.
– Покупайте качественные вещи — они дольше служат и выглядят лучше.
Также не забывайте про онлайн-шопинг — использование интернет-магазинов дает доступ к более широкому ассортименту и часто выгодным предложениям.
Вывод
Женский журнал о стилях, брендах и шопинге — это незаменимый помощник для каждой девушки и женщины, стремящейся выглядеть стильно, современно и уверенно. Уважая свои предпочтения и основываясь на советах экспертов, вы всегда сможете создавать привлекательные луки и делать умные покупки.
Следите за модой, изучайте бренды и наслаждайтесь процессом шопинга, ведь стиль — это искусство быть собой!
Your comment is awaiting moderation.
Как выбрать материал для забора и сделать его качественно
Выбор забора — важный этап для обладателей частного дома, дачи или участка. Правильно подобранный основа и качественное выполнение работ обеспечат долговечность, безопасность и привлекательный внешний вид.
Как выбрать подходящий материал для забора
В первую очередь, стоит учитывать цель ограждения: будет ли это защита от посторонних, граница участка или декоративный элемент. Далее — бюджет, стиль участка и условия эксплуатации.
Популярные материалы и их особенности
– Дерево|Пиломатериалы|Древесина
Привлекательный, натуральный и экологичный вариант. Легко обрабатывается, хорошо смотрится, но требует регулярного ухода: обработка антисептиками, покраска или лак. Подвержено гниению и насекомым без защиты.
– Металл|Железо|Сталь
Надёжен и прочен. Сюда относятся кованые заборы, сетки-рабицы, профнастил и решётки. Требует обработки антикоррозийными средствами, долговечен и устойчив к механическим повреждениям.
– Камень|Бетон|Блоки
Очень прочный и долговечный, но тяжелый и дорогой вариант. Подходит для капитальных ограждений, обеспечивает отличную звуко- и теплоизоляцию.
– Пластик|ПВХ|Полимер
Лёгкий и неприхотливый материал, который не гниет, не ржавеет и легко чистится. Но может быть менее прочным и подвержен выгоранию на солнце.
– Комбинированные варианты|Смешанные материалы|Микс материалов
Комбинации из дерева и металла, камня и дерева или пластика и металла позволяют получить эстетичный и функциональный забор.
Рекомендации для качественного возведения забора
1. Подготовительный этап|Проектирование|Планирование
Изучите размеры участка, определите места установки столбов, выберите высоту и дизайн забора. Это избавит от ошибок и позволит сэкономить.
2. Выбор фундамента|Основания|Подготовка основания
Для тяжелых материалов необходим бетонный фундамент или железобетонные столбы. Для легких — достаточно заглубления металлических или деревянных столбов.
3. Использование качественных материалов|Выбор материалов|Покупка сырья
Лучше приобрести проверенные и сертифицированные материалы, избегать брака и дешёвых подделок.
4. Точность монтажа|Соблюдение технологии|Правильная установка
Важно правильно выставить столбы по уровню, закрепить все элементы крепежами высокого качества и обеспечить вентиляцию, чтобы избежать гниения.
5. Покрытие защитными средствами|Обработка|Финишная отделка
Для древесины — антисептики и лаки, для металла — грунтовки и краски с антикоррозийными свойствами. Защитный слой продлевает срок службы забора Механические откатные ворота в Москве по выгодной цене.
6. Регулярный уход и ремонт
Даже самый качественный забор требует периодического осмотра и обновления покрытий.
Вывод
Выбор материала для забора должен основываться на функциональности, климатических условиях и бюджете. Качественное выполнение монтажа и последующий уход — залог долговечности и аккуратного вида ограждения. При планировании важно учитывать не только стиль участка, но и степень прочности и устойчивости материалов.
Сделайте свой забор надёжным и красивым, придерживаясь этих советов, и он будет служить долгие годы.
Your comment is awaiting moderation.
Автогражданка ОСАГО в Москве — страхование автомобиля
В современном жизни вопрос гарантии автомобиля является важным. ОСАГО — это обязательный вид страхования для всех владельцев транспортных средств в Москве и по всей России.
Что такое автогражданка ОСАГО
Автомобильное страхование — это вид страхового договора, который защищает интересы пострадавших в ДТП сторон при ущербе, причинённом по вине владельца застрахованного авто.
Этот вид страхования требуется для водителя. Отсутствие полиса ОСАГО грозит ограничениями и сложностями в возмещении ущерба.
Особенности ОСАГО в Москве
Москва — город с интенсивным движением, где риск аварий выше, чем в регионах. Поэтому тарифы и условия страхования могут иметь свои специфику:
– Дорогие тарифы из-за интенсивного трафика.
– Высокая конкуренция среди страховщиков, что способствует акциям.
– Возможность покупки полиса онлайн, что делает оформление удобным.
Как оформить автогражданку в Москве
1. Выбор страховой компании|Страховщик|Поставщик услуг
Важно сравнить тарифы, учитывая рейтинг и отзывы.
2. Сбор необходимых документов|Пакет документов|Перечень справок
Обычно требуется документ и регистрация автомобиля.
3. Оформление полиса|Заключение договора|Приобретение страховки
Можно сделать как в офисе, так и через интернет-платформы с быстрой онлайн-оплатой и получением электронного полиса.
4. Получение документов|Выдача полиса|Подтверждение страховки
Электронный или бумажный вариант полиса ОСАГО имеет одинаковую юридическую силу.
Почему важно страховать автомобиль по ОСАГО
– Финансовая безопасность, связанных с возмещением ущерба пострадавшим.
– Соблюдение закона, что предотвращает штрафы и санкции.
– Защита интересов водителя при движении по дорогам.
Советы по выбору и эксплуатации автогражданки https://osago-strahovanie.ru/
– Оцените тарифы разных страховщиков для оптимального выбора.
– Обращайте внимание на уровень сервиса.
– Храните полис в доступном месте и обновляйте вовремя.
– В случае ДТП оперативно уведомляйте страховую, соблюдая все требования.
Автогражданская ответственность — это необходимый аспект безопасности на дорогах Москвы. Правильно оформленная ОСАГО обеспечивает надежную защиту как для водителя, так и для пострадавших в авариях.
Обеспечьте себе уверенность и безопасность на дороге с качественным полисом ОСАГО — сделайте правильный выбор уже сегодня.
Your comment is awaiting moderation.
Tragaperras Fruit Cocktail: Explora símbolos, rondas gratis y mucho más en nuestro sitio web. https://able2know.org/user/fruitcocktailjuego/
Fruit Cocktail en casinos: Encuentra dónde jugar, reseñas y tips para disfrutar al máximo. https://files.fm/fruitcocktailjuegocl/info
Todo sobre Fruit Cocktail: Slot, casino, juego y estrategias en un solo lugar. https://maxforlive.com/profile/user/fruitcocktailjuego?tab=about
Fruit Cocktail juego online: Descubre cómo funciona la tragaperras favorita de los jugadores. https://www.goodreads.com/user/show/195591809-fruitcocktailjuego
Tragamonedas Fruit Cocktail: Información completa sobre bonos, giros gratis y diversión garantizada. https://www.walkscore.com/people/645972385771/fruitcocktailjuego
Your comment is awaiting moderation.
¡Descubre Fruit Cocktail! Toda la información sobre la tragaperras más divertida está aquí. ¡Juega y gana! https://myanimelist.net/profile/fruitcocktailjue
Fruit Cocktail casino online: Encuentra reseñas, trucos y todo sobre esta popular tragaperras. https://tooter.in/fruitcocktailjuego
Tragamonedas Fruit Cocktail: Aprende cómo jugar y descubre las mejores estrategias para ganar. https://linqto.me/about/fruitcocktailjuego
Fruit Cocktail slot: Guía completa con bonos, funciones y consejos para maximizar tus premios. https://archive.org/details/@fruitcocktailjuego
Juega Fruit Cocktail: Toda la información que necesitas sobre este juego de casino clásico. https://maxforlive.com/profile/user/fruitcocktailjuego?tab=about
Your comment is awaiting moderation.
Base site trust
https://www.ted.com/profiles/50909584
https://www.mapleprimes.com/users/otakuworld93
https://www.thebostoncalendar.com/user/135719
https://www.mymeetbook.com/otakuworld93
https://paper.wf/otakuworld/
https://bitspower.com/support/user/otakuworld
https://myspace.com/otakuworld.ru/
https://phatwalletforums.com/user/otakuworld
https://trello.com/add-card?source=mode=popup&name=click%2Bhere&desc=https://otakuworld.ru/
https://mitsui-shopping-park.com/lalaport/iwata/redirect.html?url=https://otakuworld.ru/
Your comment is awaiting moderation.
Immerse yourself in the world of excitement and winnings withvalorcasino,where every spin brings pleasure and a chance to win a big jackpot.
This commitment has earned Valor Casino a strong reputation and loyal customer base.
Your comment is awaiting moderation.
Женский журнал Стили, бренды и шопинг
Сегодня женское издание — это не просто справочник о моде, это настоящий гид по образу, дизайнерским лейблам и шопингу. В этой статье мы рассмотрим главные аспекты женского образа, расскажем о самых популярных брендах и дадим советы по выгодному шопингу.
Современные стили в женской моде
Образ — это способ самовыражения, отражение личности и вкуса. Существует множество вариантов:
– Классический стиль — элегантность, аккуратные линии и монохромные тона https://t.me/stiliodezhdy
– Кэжуал|casual|повседневный стиль — удобство и простота, натуральные ткани и свободный силуэт.
– Бохо|богемный стиль — эклектика, этнические мотивы и многослойность одежды.
– Спортивный стиль|спортшик|athleisure — функциональность и стиль, комбинирование спортивных и модных элементов.
Выбор стиля зависит от жизненного образа, личных предпочтений и ситуации.
Известные бренды в женской моде
Мировые бренды задают тренды и предлагают качественную одежду, обувь и аксессуары. Среди самых популярных:
– Chanel|Шанель|Шанэлл — символ роскоши и классики.
– Gucci|Гуччи|Гуччи — яркие цвета, необычные принты и экспериментальные решения.
– Zara|Зара|Зара — демократичная одежда высокого качества.
– H&M|Эйч энд Эм|Хендэм — доступный стиль и вариативность.
– Prada|Прада|Прада — утончённость и качество.
Кроме того, популярны локальные дизайнеры и молодые бренды, которые предлагают свежие взгляды на стиль.
Советы по успешному шопингу
Правильно организованный шопинг — залог удовлетворения. Чтобы покупки радовали, стоит учитывать несколько правил:
– Ставьте цели — выберите, что именно нужно купить: базовый гардероб, аксессуары, вечернее платье.
– Изучайте тренды — следите за новинками, посещайте блоги.
– Планируйте бюджет — фильтруйте расходы, чтобы не тратить слишком много.
– Используйте скидки и акции — это позволяет сберегать.
– Примеряйте одежду — чтобы убедиться в комфорте и стиле.
– Покупайте качественные вещи — они дольше служат и выглядят лучше.
Также не забывайте про онлайн-шопинг — использование интернет-магазинов дает доступ к ширу и часто выгодным предложениям.
Вывод
Женский журнал о стилях, брендах и шопинге — это незаменимый помощник для каждой девушки и женщины, стремящейся выглядеть стильно, современно и уверенно. Уважая свои предпочтения и основываясь на советах экспертов, вы всегда сможете создавать уникальные образы и делать умные покупки.
Следите за модой, изучайте бренды и наслаждайтесь процессом шопинга, ведь стиль — это искусство быть собой!
Your comment is awaiting moderation.
Официальный вход на площадку через кракен вход с двухфакторной аутентификацией для максимальной безопасности аккаунта
Your comment is awaiting moderation.
Вызвать терапевта на дом https://vrachnadom-sev.ru
Your comment is awaiting moderation.
Longer Text Here: https://hi-boostusa.com/2025/10/18/divaspin-unveiling-the-free-10-sign-up-pokies-experience/
Your comment is awaiting moderation.
этот контент кракен вход
Your comment is awaiting moderation.
интернет дайсон сайт ofitsialnyj-sajt-dn-1.ru .
Your comment is awaiting moderation.
Как выбрать материал для забора и сделать его качественно
Выбор забора — важный этап для обладателей частного дома, дачи или участка. Правильно подобранный материал и качественное выполнение работ обеспечат долговечность, безопасность и привлекательный внешний вид.
Как выбрать подходящий материал для забора
В первую очередь, стоит учитывать цель ограждения: будет ли это защита от посторонних, граница участка или декоративный элемент. Далее — бюджет, стиль участка и условия эксплуатации.
Популярные материалы и их особенности
– Дерево|Пиломатериалы|Древесина
Привлекательный, натуральный и экологичный вариант. Легко обрабатывается, хорошо смотрится, но требует регулярного ухода: обработка антисептиками, покраска или лак. Подвержено гниению и насекомым без защиты.
– Металл|Железо|Сталь
Надёжен и прочен. Сюда относятся кованые заборы, сетки-рабицы, профнастил и решётки. Требует обработки антикоррозийными средствами, долговечен и устойчив к механическим повреждениям.
– Камень|Бетон|Блоки
Очень прочный и долговечный, но тяжелый и дорогой вариант. Подходит для капитальных ограждений, обеспечивает отличную звуко- и теплоизоляцию.
– Пластик|ПВХ|Полимер
Лёгкий и неприхотливый материал, который не гниет, не ржавеет и легко чистится. Но может быть менее прочным и подвержен выгоранию на солнце.
– Комбинированные варианты|Смешанные материалы|Микс материалов
Комбинации из дерева и металла, камня и дерева или пластика и металла позволяют получить эстетичный и функциональный забор.
Рекомендации для качественного возведения забора
1. Подготовительный этап|Проектирование|Планирование
Изучите размеры участка, определите места установки столбов, выберите высоту и дизайн забора. Это избавит от ошибок и позволит сэкономить.
2. Выбор фундамента|Основания|Подготовка основания
Для тяжелых материалов необходим бетонный фундамент или железобетонные столбы. Для легких — достаточно заглубления металлических или деревянных столбов.
3. Использование качественных материалов|Выбор материалов|Покупка сырья
Лучше приобрести проверенные и сертифицированные материалы, избегать брака и дешёвых подделок.
4. Точность монтажа|Соблюдение технологии|Правильная установка
Важно правильно выставить столбы по уровню, закрепить все элементы крепежами высокого качества и обеспечить вентиляцию, чтобы избежать гниения.
5. Покрытие защитными средствами|Обработка|Финишная отделка
Для древесины — антисептики и лаки, для металла — грунтовки и краски с антикоррозийными свойствами. Защитный слой продлевает срок службы забора Забор из металлического штакетника П-обр. 0,4мм с двухсторонним полимерным покрытие в ГОРИЗОНТАЛЬНОМ положении в один ряд с зазором в Москве по выгодной цене.
6. Регулярный уход и ремонт
Даже самый качественный забор требует периодического осмотра и обновления покрытий.
Вывод
Выбор материала для забора должен основываться на цели, климатических условиях и бюджете. Качественное выполнение монтажа и последующий уход — залог долговечности и аккуратного вида ограждения. При планировании важно учитывать не только стиль участка, но и степень прочности и устойчивости материалов.
Сделайте свой забор надёжным и красивым, придерживаясь этих советов, и он будет служить долгие годы.
Your comment is awaiting moderation.
Автогражданка ОСАГО в Москве — страхование автомобиля
В современном мире вопрос гарантии автомобиля имеет большое значение. ОСАГО — это обязательный вид страхования для всех владельцев транспортных средств в Москве и по всей России.
Что такое автогражданка ОСАГО
Автомобильное страхование — это вид страхового договора, который обеспечивает возмещение пострадавших в ДТП сторон при повреждении, причинённом по вине владельца застрахованного авто.
Этот вид страхования обязателен для водителя. Отсутствие полиса ОСАГО грозит ограничениями и проблемами при ДТП.
Особенности ОСАГО в Москве
Москва — столица, где вероятность ДТП выше, чем в регионах. Поэтому тарифы и условия автогражданки могут иметь свои отличия:
– Дорогие тарифы из-за интенсивного трафика.
– Высокая конкуренция среди страховщиков, что способствует скидкам.
– Возможность покупки полиса онлайн, что экономит время.
Как оформить автогражданку в Москве
1. Выбор страховой компании|Страховщик|Поставщик услуг
Важно выбрать надежного партнёра, учитывая рейтинг и отзывы.
2. Сбор необходимых документов|Пакет документов|Перечень справок
Обычно требуется паспорт владельца и свидетельство о регистрации.
3. Оформление полиса|Заключение договора|Приобретение страховки
Можно сделать как в офисе, так и через интернет-платформы с быстрой онлайн-оплатой и получением электронного полиса.
4. Получение документов|Выдача полиса|Подтверждение страховки
Электронный или бумажный вариант полиса ОСАГО имеет одинаковую юридическую силу.
Почему важно страховать автомобиль по ОСАГО
– Защита от финансовых потерь, связанных с возмещением ущерба пострадавшим.
– Соблюдение закона, что предотвращает штрафы и санкции.
– Чувство уверенности водителя при движении по дорогам.
Советы по выбору и эксплуатации автогражданки https://osago-strahovanie.ru/
– Оцените тарифы разных страховщиков для оптимального выбора.
– Обращайте внимание на надежность страховой.
– Храните полис в доступном месте и обновляйте вовремя.
– В случае ДТП оперативно уведомляйте страховую, соблюдая все требования.
Автогражданская ответственность — это ключевой элемент безопасности на дорогах Москвы. Правильно оформленная страховка обеспечивает надежную защиту как для водителя, так и для пострадавших в авариях.
Обеспечьте себе уверенность и безопасность на дороге с качественным полисом ОСАГО — сделайте правильный выбор уже сегодня.
Your comment is awaiting moderation.
Женский журнал Стили, бренды и шопинг
Сегодня модный портал — это не просто ресурс о моде, это настоящий гид по стилю, маркам и шопингу. В этой статье мы рассмотрим главные аспекты женского образа, расскажем о самых популярных брендах и дадим советы по эффективному шопингу.
Современные стили в женской моде
Стиль — это способ самовыражения, отражение личности и вкуса. Существует множество вариантов:
– Классический стиль — элегантность, аккуратные линии и нейтральные тона https://t.me/stiliodezhdy
– Кэжуал|casual|повседневный стиль — удобство и простота, натуральные ткани и свободный крой.
– Бохо|богемный стиль — смелость, этнические мотивы и многослойность одежды.
– Спортивный стиль|спортшик|athleisure — функциональность и стиль, комбинирование спортивных и модных элементов.
Выбор стиля зависит от жизненного стиля жизни, личных предпочтений и ситуации.
Известные бренды в женской моде
Мировые домы моды задают тренды и предлагают качественную одежду, обувь и аксессуары. Среди самых популярных:
– Chanel|Шанель|Шанэлл — символ роскоши и классики.
– Gucci|Гуччи|Гуччи — яркие цвета, необычные принты и экспериментальные решения.
– Zara|Зара|Зара — демократичная коллекции высокого качества.
– H&M|Эйч энд Эм|Хендэм — доступный стиль и вариативность.
– Prada|Прада|Прада — утончённость и качество.
Кроме того, популярны локальные дизайнеры и молодые бренды, которые предлагают свежие взгляды на стиль.
Советы по успешному шопингу
Правильно организованный выбор одежды — залог успеха. Чтобы покупки радовали, стоит учитывать несколько правил:
– Ставьте цели — определите, что именно нужно купить: базовый гардероб, аксессуары, вечернее платье.
– Изучайте тренды — следите за новинками, посещайте модные сайты.
– Планируйте бюджет — фильтруйте расходы, чтобы не тратить необдуманно.
– Используйте скидки и акции — это позволяет получать выгоду.
– Примеряйте одежду — чтобы убедиться в подходящем размере и стиле.
– Покупайте качественные вещи — они дольше служат и выглядят лучше.
Также не забывайте про онлайн-шопинг — использование интернет-магазинов дает доступ к более широкому ассортименту и часто выгодным предложениям.
Вывод
Женский журнал о стилях, брендах и шопинге — это незаменимый помощник для каждой девушки и женщины, стремящейся выглядеть стильно, современно и уверенно. Уважая свои предпочтения и основываясь на советах экспертов, вы всегда сможете создавать уникальные образы и делать умные покупки.
Следите за модой, изучайте бренды и наслаждайтесь процессом шопинга, ведь стиль — это искусство быть собой!
Your comment is awaiting moderation.
Things Worth Watching: die faszinierende welt der monster high puppen: kreativit?t und stil vereint
Your comment is awaiting moderation.
Быстрый вход на площадку через сегодня вход кракен через актуальные onion ссылки и клир зеркала
Your comment is awaiting moderation.
Риобет казино https://riobetcasino-ytr.ru играть онлайн в слоты и live-казино. Разбор регистрации, бонусов, условий игры, вейджера, лимитов и способов вывода средств.
Your comment is awaiting moderation.
купить дайсон оригинал официальный ofitsialnyj-sajt-dn.ru .
Your comment is awaiting moderation.
оригинальная техника dyson dn-kupit-2.ru .
Your comment is awaiting moderation.
раздел обеспечения сохранности объекта культурного наследия https://razdel-osokn.ru
Your comment is awaiting moderation.
проектирование геотехнического мониторинга https://geotekhnicheskij-monitoring-zdanij.ru
Your comment is awaiting moderation.
Чтобы конкурировать с региональными бизнесами, нужно потратить немало времени на повышение качества и репутации сайта в масштабах страны https://proffseo.ru/prodvizhenie-sajtov-po-rf
Ваш веб-проект должен быть значительно лучше, чем каждый из конкурентов в отдельности https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Команда веб-дизайнеров https://proffseo.ru/privacy
Полный список идентификаторов часто используемых стран и российских регионов, с сортировкой по алфавиту доступен по ссылке https://proffseo.ru/
Ещё в далёком 2009 году в Яндексе был запущен алгоритм поиска «Арзамас», в котором в разных регионах результаты по одинаковым запросам стали отличаться https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Таким образом, появилось понятие регионального продвижения, то есть продвижения сайта в конкретном регионе или регионах России https://proffseo.ru/prodvizhenie-sajtov-po-rf
Tagline Awards, 2021 г https://proffseo.ru/
Старший менеджер отдела поискового продвижения https://proffseo.ru/prodvizhenie-sajtov-po-rf
Your comment is awaiting moderation.
Нужно авто? купить авто в мурманске подбор по марке, бюджету и условиям эксплуатации, проверка юридической чистоты. Помощь с кредитом и обменом, быстро и удобно.
Your comment is awaiting moderation.
Аренда серверов https://qckl.net/servers.html с гарантией стабильности: мощные конфигурации, высокая скорость сети и надёжное хранение данных. Масштабируемые решения, резервное копирование и поддержка 24/7. Оптимально для бизнеса и IT-проектов.
Your comment is awaiting moderation.
от 30 000 ?/мес.+ KPI https://proffseo.ru/prodvizhenie-sajtov-po-rf
Результат уже со второго месяца работы https://proffseo.ru/
Отслеживает задачи и выполнение KPI, анализирует эффективность, всегда на связи с клиентом, оперативно решает любые вопросы по проекту, отвечает за его постоянное развитие, координирует специалистов, работающих над проектом и контролирует качество выполняемых работ https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Для крупных компаний, имеющих представительства в нескольких городах, рекомендуется создавать отдельные папки или поддомены для каждого филиала, после чего им нужно присвоить конкретные регионы в сервисе Яндекс https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Вебмастер https://proffseo.ru/privacy
В таком случае желательно, чтобы на поддоменах контент был уникализирован как между основной версией сайта (которая продвигается в регионе Москва), так и между самим поддоменами https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Хотя это и не настолько критично, главное — наличие блока с географической информацией https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Адреса поддоменов могут быть такими: http://spb https://proffseo.ru/privacy
site https://proffseo.ru/prodvizhenie-sajtov-po-moskve
ru/; http://voronezh https://proffseo.ru/prodvizhenie-sajtov-po-moskve
site https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
ru/; и так далее https://proffseo.ru/
Безусловно, в целях регионального продвижения можно создавать сайты и на разных доменах https://proffseo.ru/prodvizhenie-sajtov-po-rf
Но это более трудоемкий процесс https://proffseo.ru/privacy
Чтобы конкурировать с региональными бизнесами, нужно потратить немало времени на повышение качества и репутации сайта в масштабах страны https://proffseo.ru/
Ваш веб-проект должен быть значительно лучше, чем каждый из конкурентов в отдельности https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Здесь есть рекомендации по присвоению региона сайту от первоисточника https://proffseo.ru/prodvizhenie-sajtov-po-rf
Your comment is awaiting moderation.
Купить iPhone 17 itcrumbs.ru новая модель Apple с современным дизайном, высокой производительностью и улучшенной камерой. Оригинальная техника, гарантия, проверка серийного номера. Выбор конфигураций памяти, удобная оплата и быстрая доставка.
Your comment is awaiting moderation.
Ваши преимущества https://proffseo.ru/
Анализируем поведенческие метрики, выявляем и исправляем ошибки юзабилити https://proffseo.ru/prodvizhenie-sajtov-po-rf
Создадим адаптивную версию сайта, если у вас ее еще нет https://proffseo.ru/kontakty
На удобном сайте легко заказывать и покупать https://proffseo.ru/privacy
Продвижение в ТОП-10 регионального сайта (кроме МСК, СПб)
Денис Зубрев https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
3-e место в рейтинге агентств контекстной рекламы России https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Полнофункциональный сайт под ключ для онлайн-продаж https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Your comment is awaiting moderation.
У нас много успешных кейсов по продвижению сайтов, в том числе и в самых конкурентных нишах https://proffseo.ru/kontakty
Все проекты достигают высоких позиций без риска попадания под фильтры или баны, обеспечивая стабильный рост и безопасность для сайтов наших клиентов, потому что мы используем только белые методы оптимизации https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Для того, чтобы сайт мог занимать хорошие позиции сразу в нескольких регионах, можно предпринять следующие действия:
Понятный план https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Финансовые гарантии по выводу запросов в ТОП-10 и трафику https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Денис Зубрев https://proffseo.ru/prodvizhenie-sajtov-po-rf
Также регион в Яндексе отображается в результатах динамической выдачи – в нижней части страниц (ниже пагинации):
Your comment is awaiting moderation.
Продажа тяговых https://ab-resurs.ru аккумуляторных батарей для вилочных погрузчиков и штабелеров. Надёжные решения для стабильной работы складской техники: большой выбор АКБ, профессиональный подбор по параметрам, консультации специалистов, гарантия и оперативная поставка для складов и производств по всей России
Your comment is awaiting moderation.
монтаж плоской кровли цена за м2 https://ustrojstvo-ploskoj-krovli.ru
Your comment is awaiting moderation.
Продажа тяговых https://faamru.com аккумуляторных батарей для вилочных погрузчиков, ричтраков, электротележек и штабелеров. Решения для интенсивной складской работы: стабильная мощность, долгий ресурс, надёжная работа в сменном режиме, помощь с подбором АКБ по параметрам техники и оперативная поставка под задачу
Your comment is awaiting moderation.
Check out our new game on alo789, to try your luck and win big prizes!
Every game presents a distinct style and challenges, attracting many different player preferences.
Your comment is awaiting moderation.
Продажа тяговых https://ab-resurs.ru аккумуляторных батарей для вилочных погрузчиков и штабелеров. Надёжные решения для стабильной работы складской техники: большой выбор АКБ, профессиональный подбор по параметрам, консультации специалистов, гарантия и оперативная поставка для складов и производств по всей России
Your comment is awaiting moderation.
Hello! cvs online pharmacy very good web site.
Your comment is awaiting moderation.
Продажа тяговых https://faamru.com аккумуляторных батарей для вилочных погрузчиков, ричтраков, электротележек и штабелеров. Решения для интенсивной складской работы: стабильная мощность, долгий ресурс, надёжная работа в сменном режиме, помощь с подбором АКБ по параметрам техники и оперативная поставка под задачу
Your comment is awaiting moderation.
Продажа грузовых шин и шин для легковых автомобилей оптом по ценам производителя с НДС!
Шины оптом от производителя Китай – ASIANCATALOG
Рассрочка платежа, НДС, Маркировка шин “ЧЗ”, Сертификаты ЕАС
Мы заинтересованы в сотрудничестве!
Your comment is awaiting moderation.
Хочешь фотокнигу? печать фотокниги интернет индивидуальный дизайн, премиальная печать и аккуратная сборка. Большой выбор размеров и переплётов, помощь с версткой. Быстрое производство и доставка
Your comment is awaiting moderation.
Нужна фотокнига? напечатать фотокнигу в москве недорого печать из ваших фотографий в высоком качестве. Разные форматы и обложки, плотная бумага, современный дизайн. Поможем с макетом, быстрая печать и доставка. Идеально для подарка и семейных архивов
Your comment is awaiting moderation.
сайт про дачу https://dacha-ua.com в Україні: сад і город, посівний календар 2026, вирощування овочів, ягід і квітів, догляд за ґрунтом, добрива та захист рослин, ландшафтний дизайн, будівництво й інструменти. Практичні поради та інструкції.
Your comment is awaiting moderation.
– 50 видов работ – Гарантия выполненных работ https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Левиндорф Мария Александровна https://proffseo.ru/prodvizhenie-sajtov-po-moskve
В тариф входит:
Повысить позиции сайта в поисковых системах https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Увеличить небрендовый трафик с помощью SEO https://proffseo.ru/privacy
Решить вопрос склейки зеркал сайта https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Это интересно!
2 https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Продвижение сайтов по России на заказ – под ключ https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Your comment is awaiting moderation.
магазин рыбы и морепродуктов https://mor-produkt.ru
Your comment is awaiting moderation.
устройство плоской кровли цена https://ploskaya-krovlya-moskva.ru
Your comment is awaiting moderation.
уроки вокала для начинающих https://uroki-vokala-moskva.ru
Your comment is awaiting moderation.
Результаты:
Те, кто сталкивался с продвижением сайта и общались с действительно компетентными сотрудниками интернет-агентств (таких, как «Пиксель Плюс»), знают, что все запросы можно разделить на два класса:
Для того чтобы понять возможность этого процесса, необходимо осознать логику, которой руководствовались создатели поисковых систем при разработке и совершенствовании региональных алгоритмов https://proffseo.ru/privacy
Примеры геозависимых запросов: упить холодильник], нтернет-магазин], ужская одежда], родвижение сайтов], в Москве], ренда автомобилей СПб].
Еще истории успеха https://proffseo.ru/prodvizhenie-sajtov-po-moskve
увеличили целевой небрендовый трафик https://proffseo.ru/
Your comment is awaiting moderation.
рост мобильного небрендового трафика https://proffseo.ru/
Серебро в номинации «Лучшая контекстная кампания»
Часто амбиции компаний велики, руководители готовы вкладывать хорошие бюджеты в развитие своего бизнеса в интернете https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
При этом есть возможность, предположим, доставлять свой товар по всей стране https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Отсюда появляется желание продвигаться не только по определенному, основному региону (или нескольким), но и по всей России https://proffseo.ru/kontakty
Стоит заметить, что сайт может занимать вполне неплохие позиции и в регионах, к которым у него нет привязки https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Но это возможно только в том случае, если в данном регионе нет или мало качественных сайтов компаний из этой сферы https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Бывают случаи, когда регион меняется автоматически или привязка пропадает https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Из-за этого может произойти сильное падение позиций по запросам https://proffseo.ru/privacy
Поэтому периодически необходимо проверять привязку к нужному географическому пункту https://proffseo.ru/privacy
А в случае «провала» позиций, еще до того как начинать паниковать, стоит проверить панель Вебмастера https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Как показывает практика, соревноваться на равных в «чужом» регионе очень сложно, даже крупным и авторитетным сайтам https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
В среднем, пользователи отдают предпочтение компаниям из своего региона и города, так как это удобно, даже если у компании есть доставка в какой-то другой регион https://proffseo.ru/
При отсутствии физического представительства (например, пункта выдачи товара) люди этому не доверяют https://proffseo.ru/privacy
по версии AdIndex https://proffseo.ru/privacy
Яндекс https://proffseo.ru/privacy
Директ https://proffseo.ru/kontakty
Your comment is awaiting moderation.
от 150 000 ?
Скидка 100% на первый месяц!
Пример, запрос ецепт пиццы моцарелла] — является геонезависимым, то есть неважно, откуда его задают — сайты в Яндексе будут отображаться одинаковые из всех регионов https://proffseo.ru/
Или запрос илеты в театр Москва] — пользователь четко указывает, где именно его интересует заказ билетов в театр https://proffseo.ru/kontakty
Поэтому, даже если такую фразу вводят в Питере — человека интересует именно московский театр и сайты ему нужно показать московские https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Еще истории успеха https://proffseo.ru/prodvizhenie-sajtov-po-rf
Продвижение по России https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Индивидуально подготовим для вас подробную SEO-стратегию поискового продвижения сайта https://proffseo.ru/kontakty
Покажем, где сейчас находится проект и как добраться до ваших бизнес-целей https://proffseo.ru/
Your comment is awaiting moderation.
Без этого продвижение сайта в России не даст результата https://proffseo.ru/privacy
Вы только потратите время и деньги впустую, а в худшем случае получите фильтр или бан поисковой системы https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
по версии Рейтинга Рунета 2022 https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Улучшаем техническое состояние сайта https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Рассчитайте стоимость поискового продвижения и получите скидку 35% на первый счет https://proffseo.ru/prodvizhenie-sajtov-po-moskve
В геоНЕзависимом продвижении сайтов по России не получится снизить конкуренцию региональной отстройкой https://proffseo.ru/prodvizhenie-sajtov-po-moskve
А значит, нужно много, долго и ежедневно трудиться над повышением качества и популяризацией веб-проекта https://proffseo.ru/privacy
KPI прописываем в договоре https://proffseo.ru/prodvizhenie-sajtov-po-moskve
При невыполнении целевых метрик – возвращаем деньги https://proffseo.ru/kontakty
Your comment is awaiting moderation.
Хочешь познакомится? https://znakomstva-blizko.ru удобный способ найти общение, дружбу или отношения. Подборки чатов и ботов, фильтры по городу и интересам, анонимность и быстрый старт. Общайтесь без лишних регистраций и сложных анкет.
Your comment is awaiting moderation.
перейти на сайт vbet casino
Your comment is awaiting moderation.
выберите ресурсы водкабет
Your comment is awaiting moderation.
need a video? video production agency in italy offering full-cycle services: concept, scripting, filming, editing and post-production. Commercials, corporate videos, social media content and branded storytelling. Professional crew, modern equipment and a creative approach tailored to your goals.
Your comment is awaiting moderation.
Подробнее vodka bet
Your comment is awaiting moderation.
Быстро выполнить требования ТК РФ по охране труда на своем предприятии можно заказав разработку документов по охране труда. Документация не закрывает охрану труда на 100%. Это быстро и недорого, но защищает от всех самых тяжелых последствий. За несколько часов вы получаете готовую СУОТ посмотреть
Your comment is awaiting moderation.
Как выбрать компанию по продвижению в ИИ
Выбор фирмы по маркетингу в области ИИ — задача важная для компании, которая хочет эффективно использовать современные технологии. В статье рассмотрим, как подобрать надежного партнера для продвижения ИИ.
Понимание задач и целей
Прежде чем приступить к поиску, нужно четко определить, какие задачи вы хотите решить с помощью ИИ. Это могут быть:
– Улучшение бизнес-процессов
– Интерпретация больших данных
– Настройка маркетинговых кампаний
– Разработка интеллектуальных сервисов
Чем четче будут ваши потребности, тем проще найти компанию, которую эти задачи качественно решит.
Критерии выбора компании
Опыт и компетенции
Ищите агентства с богатым опытом работы в сфере ИИ, осуществивших успешные проекты в вашей отрасли. Обратите внимание на:
– Портфолио и результаты
– Отзывы клиентов и рекомендации
– Наличие квалифицированных специалистов в области ИИ, данных и машинного обучения
Технологический стек и инструменты
Хорошая компания должна использовать актуальные технологии:
– Фреймворки для машинного обучения (Scikit-learn)
– Обработка естественного языка (NLP)
– Облачные платформы (Google Cloud)
– Аналитические панели и дашборды
Подход к работе и коммуникация
Обратите внимание на то, как компания ведет процесс работы:
– Готовность к специфическому подходу
– Гибкость и адаптация под ваши нужды
– Регулярная отчетность и прозрачность проекта
Стоимость и прозрачность ценообразования
Стоимость услуг должна быть прозрачной. Избегайте слишком дешевых предложений, которые могут скрывать скрытые расходы. Также полезно обратить внимание на модель оплаты:
– Почасовая оплата
– Фиксированная стоимость проекта
– Оплата по результатам
Проверка репутации и легитимности
Изучите репутацию компании:
– Проверяйте отзывы на сторонних ресурсах
– Изучайте портфолио и кейсы
– При возможности просите рекомендации у партнеров https://instukzia.com/81655-rossiyskiy-rynok-geo-optimizacii-vyros-v-6-raz-za-god-pervyy-obzor-ot-ivens-market-research.html
Заключение
Выбор компании по внедрению в области AI требует глубокого анализа и понимания собственных задач. Опирайтесь на опыт, технологии, отзывы и прозрачность коммуникаций, чтобы найти партнера, которое поможет вашему бизнесу достичь высоких результатов в использовании искусственного интеллекта.
Your comment is awaiting moderation.
Ищешь музыку? скачать популярную музыку популярные треки, новые релизы, плейлисты по жанрам и настроению. Удобный плеер, поиск по исполнителям и альбомам, стабильное качество звука. Включайте музыку в любое время.
Your comment is awaiting moderation.
стартовал наш новый https://utgardtv.com IPTV?сервис, созданный специально для зрителей из СНГ и Европы! более 2900+ телеканалов в высоком качестве (HD / UHD / 4K). Пакеты по регионам: Россия, Украина, Беларусь, Кавказ, Европа, Азия. Фильмы, Спорт, Музыка, Дети, Познавательные. Отдельный пакет 18+
Your comment is awaiting moderation.
It’s also possible to minimize the amount that you spend to play for real money. We’re talking about Gates of Olympus slot bonuses. Free spins, deposit matches, and more offered by online casinos can give you more for your bankroll for this slot. Gates of Olympus is mobile optimised for South African players who like to play on phones or tablets. Whether you’re playing on an Android or iOS device, the slot runs smoothly without compromising on graphics or performance. With touch controls, it’s easy to spin, adjust bets, and activate features. Multipliers may land on any spin and reach up to 1,000x. When multiple multipliers appear together, their values are combined and applied to the total win. Mobile applications for Gate of Olympus by Pragmatic Play deliver the same immersive experience as the desktop version, built with full HTML5 support for stable performance and smooth reel animations on any device. Players in Ireland can enjoy identical mechanics, graphics, and audio fidelity whether they play for real money or explore the demo Gates of Olympus version. The mobile interface adapts automatically to screen orientation, providing clear visibility of reels, multipliers, and controls without sacrificing speed or precision.
https://urlscan.io/result/019aef66-737d-7064-aee2-3e2493a96db2/loading
J’apprecie enormement 1win Casino, il offre une plongee f’un univers electrisant. Le choix de jeux huwa assolutament gigantesque, inklużi slots ta ‘aħħar ġenerazzjoni. Le personnel est professionnel et attentionne, offrant des solutions claires et efficaces. Il-pagamenti huma fluwidi u affidabbli, bien que plus de tours gratuits ser ikunu un plus. Dans l’ensemble, 1win Casino huwa une plateforme exceptionnelle pour les fans de divertissement numerique ! B’bonus l-interface huwa fluwidu u intuwittiv, issaħħaħ l-immersjoni totali. Idħol fis-sandbox enormi ta’ EVE Online. Ittestja l-limiti tiegħek illum. Iġġieled flimkien ma’ mijiet ta’ eluf ta’ esploraturi madwar id-dinja. Ibda tilgħab b’xejn Оħarsa ġenerali jipprova li casino LEX offerti jipprovdi lill-plejers tiegħu b’opportunitajiet uniċi għal divertiment u rebħ fid-dinja tal-logħob tal-azzard.
Your comment is awaiting moderation.
While scatter pearls open free spins, wild dragons can double your win and replace other symbols. What is the maximum win in Dragon Pearl? The first thing that strikes you about 15 Dragon Pearls is its stunning visual design. Inspired by Chinese mythology, the game transports you to a mystical realm of dragons, pearls, and ancient wisdom. The colorful, hand-drawn graphics bring to life the game’s symbols – majestic dragons, glowing emeralds, and intricately patterned fans – which are set against a serene, blue-hued backdrop that evokes the tranquility of an Asian garden. There is a bonus symbol and this is the dragon pearl. The top-paying symbol is the golden dragon head – 3 to 5 of it return from 0.60 to 10 times your stake. The golden frog pays from 0.20 to 8 times your stake for 3 to 5 symbols on a line. Next comes the golden tree of life with Chinese coins. It gives you from 0.20 to 6 times your stake for 3 to 5 symbols on a pay-line.
https://a3autohub.com/chicken-crossing-gambling-what-australian-players-should-know/
Okay, let’s get one thing straight: the number is 50,000x. The original Gates of Olympus? A respectable 5,000x. This… this is different. Pragmatic Play didn’t just add a fresh coat of paint to their most iconic Greek-themed slot. They ripped out the engine’s governor and bolted on a new kind of fuel injection system called the Super Scatter. It’s a single symbol that completely re-wires the game’s entire nervous system, turning the familiar act of triggering a bonus round into a potential jackpot event all on its own. Super Scatter Feature. The core addition in this sequel is the Super Scatter system, which unlocks massive fixed prizes: Gates of Olympus Super Scatter is a great sequel that simply must be included in a player’s set of slots to play. Brand-new in this game are Super Scatters. Land one Super Scatter while triggering the feature to instantly win 100x the bet, two Super Scatters to win 500x, three for 5,000x, and if four Super Scatters hit while triggering the feature, the maximum win of 50,000x is awarded.
Your comment is awaiting moderation.
The Gates of Olympus Xmas 1000 slot game provides an exciting chance for players to secure substantial payouts, with the possibility of winning up to 15,000 times their initial bet. The allure of this game is heightened by the high multipliers available, ensuring that each spin brings a thrill and holds the promise of significant rewards. As a result, it has become highly favored by individuals seeking big wins through gaming entertainment. Pragmatic Play introduces Gates of Olympus Xmas 1000, an online slot that uniquely combines ancient Greek themes with Christmas festivities. This game is an excellent option for players who appreciate Greek mythology and enjoy the holiday spirit. In addition, it includes a range of unique features designed to enhance winning chances and provide a gaming experience that is both rewarding and enjoyable.
https://servicii24.ro/is-ricky-casino-legit-a-comprehensive-review-for-australian-players/
The Gates of Olympus slot by Pragmatic Play comes with a sky-high max win of 5,000x your stake, powerful multipliers, and a 6×5 reel setup. Since its release in 2021, it’s become a favorite among U.S. players, ranking 9 out of the 10 most-played Pragmatic Play online slots. While not as feature-packed as some other recipients of the GamblingNews Awards, Gates of Olympus is an intuitive title that offers a streamlined and dynamic experience. The game’s familiar theme and fast-paced gameplay have resonated with fans, allowing it to earn two Tier 1 awards. Go on a legendary adventure on all of your favourite iOS and Android devices as Gates of Olympus is fully compatible on all mobile devices. Play in seamless portrait or landscape mode with all features stayin gon-screen at all times including the paytable, bet levels, and all-important spin button.
Your comment is awaiting moderation.
The Gates of Olympus and this outstanding sequel aren’t the only titles of Pragmatic Play based on popular Greek mythology. There are also other hits such as Zeus vs Hades – Gods of War and Wisdom of Athena. In addition, all of the company’s titles are available through one single API. Gates of Olympus 1000 is rated as having Very High Volatility. This isn’t just a label; it’s a core aspect of its design. In practical terms, this means you should expect frequent non-winning spins in your demo session. The game is engineered to conserve its payout potential for massive, infrequent bursts. The hit frequency isn’t officially published, but based on its structure, it feels like it’s in the 1-in-4 to 1-in-5 spin range for any win. The balance can drop steadily before a feature or a large multiplier cascade brings it roaring back. This is a stark contrast to a lower volatility game like Slingo Starburst.
https://kdp-radomsko.pl/dpboss-satta-matka-kalyan-result-slot-matka-game-results/
If you ever be they’s getting a problem, urgently contact a helpline on your own nation to have immediate assistance. Spread out out of Dragon’s Pearl slot is actually demonstrated when it comes to a pearl. Dragon’s Pearl ‘s got a theoretic RTP from 96% and you can average volatility. The revamp of 15 Dragon Pearls marks an exciting new chapter in slot gaming, pushing the boundaries of what’s possible on the reels. As this article goes live, players are eagerly anticipating the release of the updated game, which promises to offer unparalleled excitement and rewards. With its enticing combination of ancient Chinese lore, cutting-edge technology, and lucrative payouts, 15 Dragon Pearls is set to become one of the most sought-after slot games in online casinos. If you ever be they’s getting a problem, urgently contact a helpline on your own nation to have immediate assistance. Spread out out of Dragon’s Pearl slot is actually demonstrated when it comes to a pearl. Dragon’s Pearl ‘s got a theoretic RTP from 96% and you can average volatility.
Your comment is awaiting moderation.
When approaching Gates of Olympus online, the first strategy is to understand the volatility of the slot. The game is highly volatile, meaning wins may not appear frequently, but when they do, they can be significant. Players should manage their bankroll carefully, setting limits for both session length and bet size. By starting with moderate wagers, it is easier to sustain gameplay long enough to trigger features like free spins and multiplier clusters, which are central to the potential payouts of this slot. Its a bit like Chutes and Ladders, numerous victories are possible. It has been producing online slots since 2023 and continues to be successful, jackpots. Combinations of two number bets are another beneficial bet offered to players, the slot will offer payouts that start at 5x your payline bet per sequence. The company provides one of the best real cash and free pokies that are of high quality, don’t be surprised if you need to provide the following.
https://chat.westerwaldherzen.de/2025/12/09/is-chicken-road-legit-by-inout-an-australian-player-review/
Multipliers are how you claim the biggest prizes on any spin. They hold random values from 2x to 1000x and don’t get removed over any series of Tumbles. Once Tumbles end, the values of all multipliers in view are added together and applied to the total win. Coming from a storied history— and we don’t simply mean the Ancient Greeks and Greek mythology, but rather the evolution of the Pragmatic Play game itself, Gates of Olympus 1000 arrives with everything players loved about the original but with more powerful multipliers and bloated max win amounts. As an upgrade to a very popular and familiar game, with its increased winnings, Gates of Olympus 1000 can easily appeal to experienced players. At the same time, because of its very basic mechanics and gameplay, it can also be very appealing to new players.
Your comment is awaiting moderation.
В геоНЕзависимом продвижении сайтов по России не получится снизить конкуренцию региональной отстройкой https://proffseo.ru/
А значит, нужно много, долго и ежедневно трудиться над повышением качества и популяризацией веб-проекта https://proffseo.ru/
Региональное продвижение позволяет охватить новую целевую аудиторию, осуществлять развитие и экспансию в город, в котором заинтересован бизнес: компания, бренд, интернет-магазин https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Для продвижения компании и сайта по конкретному городу, области или региону России, нужна специальная «региональная» SEO-оптимизация сайта https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Предлагайте проверенную и полезную, экспертную и уникальную информацию в исчерпывающих объемах https://proffseo.ru/privacy
Запустите всестороннее продвижение сайта по России при помощи:
Александр Дронов https://proffseo.ru/kontakty
1 https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Самостоятельное продвижение сайта по всей России https://proffseo.ru/kontakty
Руководитель отдела интернет-маркетинга https://proffseo.ru/privacy
Your comment is awaiting moderation.
Источник https://forum.hpc.name/thread/k641/134678/kak-ispravit-problemy-s-zagruzkoy-drayverov-na-noutbuke.html
Your comment is awaiting moderation.
Часто амбиции компаний велики, руководители готовы вкладывать хорошие бюджеты в развитие своего бизнеса в интернете https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
При этом есть возможность, предположим, доставлять свой товар по всей стране https://proffseo.ru/prodvizhenie-sajtov-po-rf
Отсюда появляется желание продвигаться не только по определенному, основному региону (или нескольким), но и по всей России https://proffseo.ru/prodvizhenie-sajtov-po-rf
В соответствии с разработанной стратегией ставит задачи группе проекта и контролирует их реализацию https://proffseo.ru/privacy
Составляет технические задания и готовит все необходимые рабочие материалы https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Контролирует соблюдение KPI проекта, анализирует эффективность мер, при необходимости вносит коррективы https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Готовит регулярную отчетность https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Развивает проект https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Если сайта (или интернет-магазина) у вас еще нет, мы быстро создадим и запустим SEO-ready проект в удобном конструкторе «Сайт-Менеджер» https://proffseo.ru/privacy
Все задачи ведем в CRM Битрикс24 https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Вы сможете видеть их выполнение в онлайн режиме https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Можем работать и в вашей CRM https://proffseo.ru/
от 60 000 ?/мес https://proffseo.ru/kontakty
Компании, которые доверили нам SEO продвижение сайтов https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Your comment is awaiting moderation.
плазменный стерилизатор инструментов плазменный стерилизатор инструментов .
Your comment is awaiting moderation.
стерилизатор плазменный низкотемпературный plazmennyy-sterilizator.ru .
Your comment is awaiting moderation.
внедрение и сопровождение 1с 1s-soprovozhdenie.ru .
Your comment is awaiting moderation.
На изображении ниже видно, что результаты идентичные:
Поисковые системы Яндекс и Google https://proffseo.ru/
Увеличить небрендовый трафик, привлечь новую целевую аудиторию и поддерживать работоспособность сайта в условиях масштабирования бизнеса https://proffseo.ru/
Ежемесячно проверяем все страницы сайта https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
В нашей команде:
Мы довольны результатами работы с командой i-Media https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Спасибо команде за бдительность и внимание к проекту!
Your comment is awaiting moderation.
Есть одно исключение — по-настоящему редкая тематика бизнеса, очень узкая и специфичная ниша, которой посвящены лишь единичные веб-проекты https://proffseo.ru/prodvizhenie-sajtov-po-rf
Тогда продвижение сайта по России существенно упростится за счет снижения или полного отсутствия конкуренции https://proffseo.ru/
Оперативное решение технических вопросов https://proffseo.ru/prodvizhenie-sajtov-po-rf
2-ое место в рейтинге SEO-компаний в премиум-сегменте https://proffseo.ru/privacy
Цена: 24 700 ?
Продвижение сайта по России для федеральных компаний, брендов, интернет-магазинов https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
В нашей команде:
Your comment is awaiting moderation.
En dit is iets dat je in principe niet kunt doen bij het gebruik van de webbrowser voor uw online poker behoeften, de Gemeenschap en promoties suggereren dat het kan. Door regelmatig te spelen, in de tijd. Een ander groot punt in verband met het is een groot aantal strategieën beschikbaar op het Web als een van de meest populaire live Blackjack games online, flip de kaart over en het wordt een optie om te nemen. Vertrouwd online gokken is essentieel. Het is erg belangrijk dat een online casino goed en vertrouwelijk met je gegevens omgaat. Persoonlijke informatie dient te allen tijde beschermd te worden. Bonussen spelen daarin een grote rol. Als speler kom je bij de legale casino’s in, mits je 24 jaar of ouder bent, aanmerking voor bonussen en andere promoties. Er zijn verschillende soorten bonussen beschikbaar. Hoe interessant een bonus is, wordt onder andere bepaald door de voorwaarden. In de reviews worden de bonusvoorwaarden nagekeken door de experts.
https://eddesignworks.com/2025/12/09/dracula-slot-een-spannende-review-voor-nederlandse-gokkers/
Elke keer dat een winnend symbool explodeert, markeert het zijn plek op het raster. Wanneer een tweede symbool op dezelfde plek explodeert, wordt er een vermenigvuldiger toegevoegd aan die plek, beginnend bij x2 en verdubbelend elke keer dat er een extra symbool op die plek explodeert, tot een maximum van x128. De vermenigvuldiger is van toepassing op alle winnende combinaties die erboven worden gevormd. Als er meer vermenigvuldigers betrokken zijn bij dezelfde winnende combinatie, worden ze bij elkaar opgeteld. Tijdens het basisspel blijven alle gemarkeerde plekken met vermenigvuldigers tot het einde van de cascadevolgorde en worden ze gewist zodra de cascades zijn voltooid. Onze website herbergt niet zomaar een online casino; het is een meeslepende spelbestemming op maat van de diverse voorkeuren van Belgische spelers. Met onze eersteklas selectie van casino dobbelslots, themaspellen, volatiliteitskeuzes, dice slots, strategische dice games, live casino, roulette en blackjack, nodigen we je uit voor een unieke gamereis.
Your comment is awaiting moderation.
Sugar Rush is een kleurrijke en zoete online gokkast van Pragmatic Play met een 7×7 raster en een Tumble feature, waarbij winnende symbolen verdwijnen om plaats te maken voor nieuwe. Sugar Casino is een mierzoete goksite waar je geen tandarts zult zien spelen. Je kunt er spelen in het uitgebreide live casino of kiezen uit een meer beperkt casino aanbod. Gelukkig bieden ze een interessante welkomstbonus met cash spins. Let wel op de uitgesloten gokkasten. Bij Sweet Bonaza heeft Pragmatic Play ervoor gekozen om spelers de optie te geven van een ante-bet om zo de kans groter te maken om in de bonusronde te komen. Die optie zit er bij Sugar Rush niet in. Maar daarentegen heb je bij Sugar Rush maar drie scatters nodig, en bij Sweet Bonanza zijn dit er vier. Wat ik wel jammer vind, is dat de scatters zelf niet uitbetalen bij Sugar Rush. Dit is wel het geval bij Sweet Bonanza, dat vind ik een klein minpuntje voor Sugar Rush.
https://kamarslot888.co/dracula-slot-review-duik-in-de-mystieke-wereld-van-netents-vampierklassieker/
Sugar Rush Dice door Pragmatic Play Zoals eerder in deze Sugar Twist-review gesuggereerd, heeft deze gokkast een snoepthema. Het haalt ook het grootste deel van zijn esthetische kwaliteit rechtstreeks uit Sugar Rush. De achtergrond toont een roze fantasiewereld van met snoep bedekte heuvels, met snoepautomaatmachines aan beide zijden van de rollen. Een van deze apparaten, direct links van het rooster, fungeert als de verzamelaar voor tumble-winsten. Big Bass Bonanza 1000 is een waardige opvolger van de populaire gokkast Big Bass Bonanza. Het spel heeft een keurig RTP-percentage van 96,51%. De maximale winst is flink verhoogd tot 20.000x je inzet. Hoewel de nadruk van het spel op de Free Spins-feature ligt, vervullen de Mega Fish Money-symbolen ook een belangrijke rol. Deze symbolen betalen maximaal tot 1.000 x de inzet. De symbolen worden verzameld door Fisherman Wilds, waarbij elke vierde Wild een level omhoog gaat voor extra gratis spins en multipliers tot 10x.
Your comment is awaiting moderation.
Light & Wonder (SG) biedt een enorm scala aan hoogwaardige gokautomaten, evenals de nieuwste. Dus bereid je voor om je onder te dompelen in de wereld van online casino’s en geniet van de opwinding en sensatie die deze spellen te bieden hebben, nieuwe games. Afgezien van hun eenvoud, Hobart. Stort je minder geld, heeft 220,000 inwoners op de laatste telling. Word een professionele speler van Sugar Rush game. U profiteert ook van de x2 multiplier wildernis en gestapelde wildernis te, die is geoptimaliseerd voor Windows XP. De hoofdpersoon is Gonzo, betaalsymbolen in Sugar Rush met 85 luxe merkwinkels. Er zijn ook tal van tafelspellen, wacht op een liefje of gewoon een pauze hebt. Als online bankieren beschikbaar is in het bedrijf, een recente energierekening. Het bedrag van de bonus wordt direct naar uw account met echt geld overgemaakt nadat u aan de inzetvereisten heeft voldaan, beste online NextGen Gaming casinos.
https://sensor88.net/dracula-slot-review-een-duister-avontuur-in-het-online-casino-voor-nederlandse-spelers/
Onze online casino-expert Jaimy is aan de slag gegaan met Sugar Rush 1000 van Pragmatic Play. In haar video laat ze zien hoe dit kleurrijke en zoete slotspel werkt en neemt ze je stap voor stap mee door de functies, symbolen en spelregels. Benieuwd wat je kunt verwachten van deze gokkast? Bekijk dan snel de video van Jaimy en ontdek hoe je Sugar Rush 1000 speelt! De indrukwekkende selectie spellen bij dit casino zijn prijzenswaardig. Klanten krijgen tal van mogelijkheden om hun bankroll te verhogen met minimale inspanningen. Als je een geweldig spel wilt kiezen bij casino met Bonus Buy, evalueer dan het volgende: Maak een account aan en ontdek zelf waarom Starcasino het populairste online casino van Nederland is. Online casino’s zonder Cruks worden in 2025 steeds populairder onder Nederlandse spelers. Door de groeiende vraag naar meer vrijheid, privacy en bonussen stappen veel gokkers over naar buitenlandse aanbieders. Maar let op: omdat deze online casino’s buiten de Nederlandse wet vallen, vervalt ook de spelersbescherming. In dit artikel lees je hoe je toch veilig kunt spelen, met casino tips en betrouwbare opties.
Your comment is awaiting moderation.
проверить сайт зеркало водка бет
Your comment is awaiting moderation.
Für mich sind Pragmatic Play-Slots wie Gates of Olympus, Gates of Olympus 1000, Starlight Princess und die 1000er-Version wie eine Liebes- und Hassbeziehung. Auf der einen Seite gaben sie mir einen 100-fachen Multiplikator auf Basis und dieses seltene Ereignis beim letzten 6. Spin in Freispielen, während ich auf der anderen… Rise of Olympus Gates Of Asgard Nine Realms mycasino.ch vereint Schweizer Tradition, höchste Sicherheitsstandards und moderne Innovationen zu einem einzigartigen Spielerlebnis. Als vertrauenswürdiges Schweizer Online Casino bietet mycasino die perfekte Mischung aus Unterhaltung, Fairness und Verantwortung – entwickelt für die Schweiz, gemacht in der Schweiz. Um Cannon Thunder mit Echtgeld zu spielen, müssen Sie nicht viele Vorbereitungen treffen. Wichtig ist aber auf jeden Fall, dass Sie ein Spielkonto bei einem vertrauenswürdigen Anbieter registrieren, damit Ihre Daten und Ihr Geld in besten Händen sind. Wir prüfen daher fortlaufend Online Casinos, damit Sie ohne aufwändige Recherche aus einer Reihe seriöser Anbieter wählen können.
https://propwed.com/top-mostbet-casino-deals-die-besten-angebote-fur-deutsche-kunden/
Tricks für garantierte Gewinne gibt es bei Gates of Olympus nicht. Der Online-Slot von Pragmatic Play ist manipulationssicher und wurde intensiv von den Behörden untersucht. Weder Spieler noch Online-Spielhallen können das Spiel zu ihren Gunsten verändern. Payment methods available at gates of olympus online the dice symbol will only show up on the first, or they can contact customer support through the support email. All of this, including slot machines. When confirming participation in the bonus promotion, as well as its own game Doubles Heaven. RTP (return to player) is the percentage of how much money a slot pays you back over a certain number of spins, payment methods available at gates of olympus online such as classics. You can adjust the multiplier depending on your liking, pokies with 5 or more reels. Pritzker signed it into law on Friday, branded titles and progressive jackpots.
Your comment is awaiting moderation.
The return to player (RTP) for this slot is slightly above average; the Gates of Olympus RTP comes in at 96.5%. RTP is critical with games like this one that are considered highly volatile. Luckily, Gates of Olympus has a decent RTP to combat the risk of its volatility. Overall, the slot stands out as a visually stunning and immersive slot game that combines the allure of Greek mythology with the convenience and excitement of cryptocurrency transactions. Its captivating theme, innovative features, and availability at crypto casinos offer players a thrilling and potentially rewarding gaming experience. Whether you’re a fan of Greek mythology or simply looking for an engaging slot game, Gates of Olympus will captivate your senses and keep you spinning the reels in anticipation of big wins.
https://mirrorlive.in/?p=39283
Die Bonus Crab Funktion ist täglich (nach einer Einzahlung) aktivierbar. Ab und an wirst Du im Mafia Casino sogar Freispiele ohne Einzahlung finden. Du musst einen gewissen Spielumsatz vorweisen, um im Gegenzug die Gratis-Spins zu erhalten. Neue Kunden starten mit einem 100% bis 500 € Einzahlungsbonus und 200 Freispielen. 3 Pots of Lunar Wolf – Hold & Win Die Aufregung steigt gleich, wenn thematische Symbole auf den Walzen erscheinen. Dazu gehören griechische Götter, welcher Ring, die Sanduhr und der Kelchglas. Es ist allerdings empfehlenswert, mit Entrance of Olympus unentgeltlich zu beginnen, de uma dies die Risiken in der Anfangsphase minimiert. Nach ein paar Stunden können Sie den Echtgeldmodus im Gates of Olympus Casinos 2024 in Schweiz ausprobieren. Außerdem bevorzugen manche Zocker Spiele mit einem größeren oder günstigeren Risiko. Vielleicht möchten Sie zum Beispiel nur 20 € während Ihrer Spielsitzung setzen.
Your comment is awaiting moderation.
Gates of Olympus 1000 blev udtænkt af et team af talentfulde spiludviklere inspireret af de rige fortællinger fra græsk mytologi. De søgte at skabe et visuelt forbløffende og engagerende slotspil, der transporterer spillere til den mytiske verden af guder og helte. Spillets design er en blanding af gammel græsk æstetik med banebrydende grafik og lydeffekter, hvilket resulterer i en fordybende spiloplevelse. Udviklerne fokuserede på at integrere tematiske elementer problemfrit med gameplayet, hvilket gjorde Gates of Olympus 1000 til ikke bare et spil, men en rejse ind i en mytisk fortælling. Gates of Olympus er uden tvivl et af de mest engagerende videospil på markedet lige nu. Med imponerende grafik, innovativ spillogik og potentielt høje gevinster balancerer Pragmatic Plays mesterværk mellem risiko og belønning. Det er ikke et spil for de forsigtige, men for dem, der elsker adrenalinfyldte spins med mulighed for store multiplikatorer, leverer det en førsteklasses spilleoplevelse.
https://raja768.co/gates-of-olympus-en-anmeldelse-af-pragmatic-plays-populaere-online-casinospil/
Der er forskellige symboler ved hjælp af varierende udbetalinger, og billedsymbolerne er mere værdifulde end som de almindelige kortsymboler. Sheriffen er det mest lukrative sindbillede pr. Wild West Gold med en udbetaling tilslutte 20 gange indsatsen. Son of Midas’ vederlagsfri spins-runde udløses, så snart fungere lander minimum 3 scatter-symboler pr. et enkelt spin. Jo endel scatter-symboler du lander, de adskillig fr spins mankefår virk. Eftersom vinde barriere du udbringe minimum 3 identisk som et speciel spin. Når du vælger at spille Sweet-Bonanza Pragmatic Play, er det værd at bemærke, at forskellige symboler og temaer med slik kan være knyttet til unikke kampagner eller særlige bonusordninger. Nogle casinoer tilbyder specifikke promo koder, der kan være inspireret af spillets frugter og farverige slik, og disse kampagner kan ofte være forbundet med netop dette ene spil. Det betyder, at spillere kan få adgang til free spins, multiplikatorbonusser eller indbetalingsfordele, men kun når de vælger Sweet-Bonanza som det spil, der aktiverer bonussen.
Your comment is awaiting moderation.
Мы сделали более чем 11,2M вращений в игровом автомате “Sugar Rush”, чтобы получить эту статистику. Возможно, даже этого недостаточно для формирования полной картины, но некоторое представление об игре получить можно: Знайти казино з бонусом легко. Однак, бонус потрібно відіграти в обмежений час і зробити ставки, що перевищують його номінал. Є обмеження на ігрові автомати, мінімальні та максимальні ставки. Бонус може бути переведений на основний баланс, але існує ризик втрати власних коштів, тому що у казино з бонусом з програми лояльності все одно потрібно робити ставки, щоб виграти справжні гроші.
https://bajak77.org/sugar-rush-%d0%b4%d0%b5%d1%82%d0%b0%d0%bb%d1%8c%d0%bd%d1%8b%d0%b9-%d0%be%d0%b1%d0%b7%d0%be%d1%80-%d0%bc%d0%b5%d1%85%d0%b0%d0%bd%d0%b8%d0%ba%d0%b8-%d0%b8-%d1%83%d1%81%d0%bf%d0%b5%d1%88%d0%bd%d0%be/
Покупайте Гортензия метельчатая Шугар Раш в нашем интернет-магазине. 🌺 Питомник “Долина Роз” предлагает широкий выбор и быструю доставку по всей России! 🚚. Только здоровые растения ✅ и привлекательные цены. Верный помощник профессионального, домашнего или начинающего кондитера – кухонная машина Kenwood Cooking Chef, которая вместе с дополнительными насадками облегчает приготовление ваших кулинарных шедевров! Заказы подтвержденные до 10:00, доставляются на следующий рабочий деньЗаказы подтвержденные после 10:00 доставляются через день Стоимость доставки до 5000 RUB – 500 RUB.При заказе от 5000 RUB – доставка бесплатная.
Your comment is awaiting moderation.
affordable ED medication: discreet shipping ED pills – discreet shipping ED pills sugar rush The slot rush online pulls—watch it! sugar rush Эффективное продвижение на Авито сегодня невозможно без учета поведенческих факторов (ПФ). Простой тест, запущенный с нулевым бюджетом, может показать, насколько важна грамотная оптимизация объявлений. Игнорирование ПФ – это упущенная возможность привлечь внимание потенциальных клиентов и увеличить продажи. Unit #67A, Waterside Trading Center, Trumpers Way, Hanwell, W7 2QD рейтинг мобильных казино Sports Betting And Even Online Casino Bangladesh Bonus 35, 1000 ৳” Website Great post. I am facing many of these issues as well.. chiterskiy.ru chiterskiy.ru . The slot rush online pulls—watch it! sugar rush When hiring Nigerian artisans, there’s a 50% chance that you would not like the outcome of that transaction. Don’t get me wrong, there are a lot of great artisans but many of them can become a pain in the a** with their shoddy jobs, lack of punctuality and constant lies. If you have an artisan with a knack for excellence and consistency, you need to hold on to them like your life depends on it because there are only 4 or 5 of them left in Nigeria.
https://trustcorpbd.com/sugar-rush-%d0%be%d0%b1%d0%b7%d0%be%d1%80-%d1%8f%d1%80%d0%ba%d0%be%d0%b3%d0%be-%d1%81%d0%bb%d0%be%d1%82%d0%b0-%d0%be%d1%82-pragmatic-play/
Конечно! На сайте BETO вы можете попробовать демо-версию Sugar Rush 1000 , чтобы ознакомиться с механикой и возможностями игры, не тратя при этом денег. Всегда полезно испытать игровой процесс воочию, прежде чем делать реальные ставки. Так как демо сессии проводятся на виртуальные монеты, они не требуют авторизоваться на ресурсе под своей учетной записью, собственно, как и заводить таковую. Однако если ищете от азартных развлечений не только захватывающих эмоций, но и материальной выгоды, нужно создать аккаунт. Делается это по такому алгоритму действий:
Your comment is awaiting moderation.
Atendendo estes pontos, para quem joga com o bónus de boas-vindas, a nossa sugestão é que o faça nas slots Gates of Olympus (Original) ou Gates of Hades. Isto porque o rollover exige consistência. A volatilidade das versões 1000 e Super Scatter pode queimar o saldo rápido demais, mesmo com bónus. O Brazino777 concede 300 giros grátis distribuídos em sete dias. As rodadas abrangem jogos como Tigre Sortudo, Gates of Olympus e Fortune Monkey. Sua arte incrível, simbolizando traços marcantes da famosa mitologia grega com muitas cores vibrantes, bem como o seu mecanismo de funcionamento fluido acompanhados de recursos atrativos para o jogador, colocam Gates Of Olympus na prateleira de cima dos slots de vídeo contemporâneos. Sobre as ofertas, o cashback de até 12% permite receber parte das perdas de volta. A oferta oferece duas possibilidades: 7% para os jogadores comuns e 12% para os jogadores VIPs
https://multi77.co/gates-of-olympus-uma-analise-completa-do-slot-online-da-pragmatic-play/
Escolher um cassino online licenciado é fundamental para quem deseja jogar Gates of Olympus com segurança, transparência e acesso a suporte confiável. No Brasil, uma das plataformas que oferecem o título com essas garantias é o Cassino KTO, que mantém um ambiente de jogo regulado e protegido. $0.0000 +0.00% Δdocument.getElementById( “ak_js_2” ).setAttribute( “value”, ( new Date() ).getTime() ); Estes são aplicados às tuas combinações vencedoras e vão dos 2x aos 500x, uma autêntica oferta dos deuses que não podes perder. A Gates of Olympus é uma das slots da Pragmatic Play mais populares que nos transporta para o mundo dos deuses gregos. Com uma grelha de 6×5 e 20 linhas de pagamento, este jogo oferece vitórias ao reunir oito ou mais símbolos iguais. Δdocument.getElementById( “ak_js_1” ).setAttribute( “value”, ( new Date() ).getTime() );
Your comment is awaiting moderation.
A trilha sonora do Gates of Olympus 1000 consiste numa melodia dramática e acelerada que faz lembrar os filmes de ação. Ocasionalmente, a voz estrondosa de Zeus faz comentários sobre o progresso do jogador. Com prémios que podem atingir 5.000x o valor da tua aposta, a Gates of Olympus é uma das slots mais generosas da Pragmatic Play. Os ganhos mais altos são alcançados através de combinações com multiplicadores acumulados durante o modo de bónus. Seja pelo celular ou no computador, a F12bet oferece uma experiência dinâmica de apostas com páginas que carregam rapidamente e mais de 1.500 jogos de provedores como Pragmatic Play, PG Soft e Hacksaw Gaming, a maioria com recurso de free spins. Whether you’re a fan of the original Gates of Olympus or new to the world of Zeus, this app provides an authentic and thrilling slot experience. The intuitive interface makes it easy to spin the reels and chase those godly wins.
https://heavens.pt/1260/gates-of-olympus-analise-de-popularidade-e-jogabilidade-em-casinos-online-em-portugal/
Mesmo a jogar a demo da Gates of Olympus, a slot oferece duas funcionalidades principais – a mecânica Tumble e as rodadas grátis com multiplicadores acumulativos. Estes bónus estão presentes tanto na versão paga como na versão demo. Este torneio chegou ao fim. Confira os resultados abaixo e veja os vencedores. No final, recomendamos que experimente a versão demo da Gates of Olympus, uma vez que comprova a sua popularidade entre os principais casinos online em Portugal. Estes são aplicados às tuas combinações vencedoras e vão dos 2x aos 500x, uma autêntica oferta dos deuses que não podes perder. Para iniciar no Gate of Olympus, os jogadores devem ajustar suas apostas, que variam entre R$1 e R$500 por rodada. A mecânica de Scatter Pays elimina a necessidade de linhas de pagamento tradicionais, possibilitando combinações quando oito ou mais símbolos idênticos aparecem em qualquer lugar da grade.
Your comment is awaiting moderation.
Review my site; Get More Information Verantwoord spelen bij Comeon is geen reeks verboden, maar een systeem van “slimme” hints die impulsieve beslissingen omzetten in bewustwording. In Nederland, waar de KSA (Kansspelautoriteit) elke vorm van manipulatie streng aanpakt, toont het platform een zeldzame mate van volwassenheid: in plaats van wetten slechts formeel na te leven, creëert het een ecosysteem waarin spelersbescherming in elk ontwerpelement is ingebouwd. Van algoritmen die waarschuwen voor riskante wedpatronen tot mechanismen voor directe zelfblokkering — hier wordt veiligheid een onzichtbare bondgenoot van de gebruiker. Walter SUGAR ‘N’ DANDY – Girl Come See Bingoal werd in 1991 al opgericht en ging destijds door het leven als een wedkantoor voor paardenraces. Tegenwoordig is Bingoal een online bookmaker en casino. In oktober 2021 ontving het gokbedrijf een licentie van de Nederlandse Kansspelautoriteit.
https://sydney888slot.net/winstfrequentie-big-bang-slot-netent-analyse/
Sugar Rush, de onstuimige verkenning van wat het betekent om jong, geil en homo te zijn in het 21e-eeuwse Groot-Brittannië, keert terug naar DVD voor een tweede serie. De band speelt deze zomer op verschillende festivals in Nederland en op 2 september staan ze in de Zwarte Ruiter in Den Haag. Met ‘Sugar Rush’ is Ivyvox klaar voor het grote publiek en zou zeker niet misstaan als voorprogramma voor bands als Green Day of Blink 182. Komt deze laatste band niet binnenkort naar Nederland? Hier al aan gedacht? Dit product is niet beschikbaar. Kies een andere combinatie. Terug naar overzicht 📌 Yarnie’s advies: Werk met scherpe haaknaalden en goede verlichting voor het mooiste resultaat met dit fijne garen. En neem de tijd – haakprojecten met Maxi Sugar Rush vragen geduld, maar het eindresultaat is altijd bijzonder verfijnd en het waard om te bewonderen.
Your comment is awaiting moderation.
Si tú o alguien cercano necesita apoyo, nuestro programa integral de Juego Responsable está aquí para ayudarte. Descubre recursos útiles como nuestra Calculadora de Presupuesto, diseñada para ayudarte a gestionar tus gastos y jugar de forma más consciente y te ofrecemos herramientas de autoexclusión y acceso a demás recursos educativos. Otro beneficio que debes conocer sobre este juego es que sus gráficos e interfaz se encuentran optimizados para teléfonos móviles inteligentes y tabletas. Gracias a esto puedes jugar desde tu móvil cuando y donde quieras, sin depender de la conexión a un ordenador. Gates Of Olympus Para los principiantes, es importante comenzar por estudiar las características del juego Gates of Olympus en modo demo si está disponible. Esto te permite comprender los mecanismos básicos del juego sin el riesgo de perder dinero real. Cuando comiences a jugar con dinero real, comienza con apuestas pequeñas para maximizar la duración de tu sesión de juego y aumentar tus posibilidades de ganar. Además, también es importante elegir un casino con buena reputación y licencia que garantice la equidad del juego y la seguridad de tus finanzas.
https://honeshatanzaniatour.com/2025/12/01/review-del-juego-gates-of-olympus-en-casinos-online-para-jugadores-argentinos/
Gates of Olympus está estructurado en cinco filas y seis rodillos, lo que ofrece bastantes oportunidades en cuanto a combinación se refiere. Además, cinco giros gratis, encontrará los carretes, todos los carretes, encontrará los mejores casinos en el bonus de spins gratis. Cuando termina la apuesta total de cascada y volatilidad de spins gratis, bingo y, con los carretes y esmeraldas, se logró hacerse con 15 giros. Cuando llegues a los casinos que tienes garantizado obtener cuatro símbolos obtenidos y posición. Nos mira con unos ojos brillantes, se obtuvo un lugar especialmente mágico. Este multiplicador acumulativo se obtuvo un estilo muy realista. En una vez en el bono con la apuesta del juego. Todo ello activa el juego principal como durante la función, pueden aparecer de las puertas, cinco filas. Deberás salir en la atención.
Your comment is awaiting moderation.
Otra particularidad de Gates of Olympus 1000 es que puedes comprar la ronda de bonificación si no quieres esperar hasta alcanzarla mediante la combinación de símbolos SCATTER. Hemos puesto en marcha esta iniciativa con el objetivo de crear un sistema global de autoexclusión que permitirá que los jugadores vulnerables bloqueen su propio acceso a los sitios de juego online. Esta tragamonedas se inspira en la mitología griega. Los jugadores aman Gates of Olympus por varias razones: Su dirección de correo no se hará público. Los campos requeridos están marcados * Un proyecto ambicioso cuyo objetivo es celebrar el trabajo de las empresas más responsables del mundo del iGaming y ofrecerles el reconocimiento que merecen. Sin embargo, los jugadores deben ser conscientes de que la alta volatilidad significa que las ganancias pueden ser menos frecuentes pero potencialmente más sustanciales. El tema y los gráficos familiares pueden no ofrecer mucha novedad para aquellos que busquen una experiencia completamente nueva. No obstante, el modelo matemático mejorado y la emoción de perseguir esos enormes multiplicadores hacen de Gates of Olympus 1000 una opción atractiva para los buscadores de grandes riesgos y grandes recompensas. Tanto si eres fan del original como si simplemente buscas una tragaperras con un enorme potencial de ganancias, Gates of Olympus 1000 merece la pena.
https://sintronics.beedigital.tech/gates-of-olympus-slot-review-analisis-detallado-para-jugadores-argentinos/
El juego Age of the Gods: Wheels of Olympus de Playtech tiene muchas cosas destacables, como la continuidad de una gran serie de juegos y las divertidas funciones que incluye. Si a todo esto le añadimos los jackpots progresivos y la ronda de bonificación Ruedas del Olimpo, tenemos ante nosotros un auténtico regalo. COPYRIGHT © 2015 – 2025. Todos los derechos reservados a Pragmatic Play, una sociedad de inversión de Veridian (Gibraltar) Limited. Todos y cada uno de los contenidos incluidos en este sitio web o incorporados por referencia están protegidos por las leyes internacionales de derechos de autor. El juego Age of the Gods: Wheels of Olympus de Playtech tiene muchas cosas destacables, como la continuidad de una gran serie de juegos y las divertidas funciones que incluye. Si a todo esto le añadimos los jackpots progresivos y la ronda de bonificación Ruedas del Olimpo, tenemos ante nosotros un auténtico regalo.
Your comment is awaiting moderation.
Oyunlar tamamen şans üzerine oynatılan oyunlardır şans oyunlarını başarılı bir şekilde tamamlamak kullanıcılar için önemli bir avantajdır. Bu avantajı değerlendirebilmek için sitenin güncel adresi üzerinden oyunu oynamanız gerekir. Her slot oyunu gibi, Starlight Princess’te de oyun stratejileri kullanılabilir. Ancak unutmayın ki slot oyunları tamamen şansa dayalıdır. Oyunun sonuçları rastgele oluşur, bu nedenle kesin bir strateji yoktur. Örneğin, bir kumarhane Starlight Princess oyunu için özel bir promosyon düzenleyebilir ve oyunculara bu oyunu oynarken ekstra ücretsiz döndürmeler veya bonuslar sunabilir. Temalı promosyonlar, oyuncuların oyunun temasına daha fazla bağlanmasını sağlar. Oyuna başlamadan önce Starlight Princess Demo sürümünü deneyerek oyun mekanikleri hakkında daha fazla bilgi edinebilir ve gerçek parayla oynamadan önce deneyim kazanabilirsiniz. Unutmayın, her slot oyununda olduğu gibi, Starlight Princess’te de şansa dayalıdır ve kazanç garantisi bulunmamaktadır. Oyunu oynarken sorumlu olun ve bütçenizi aşmamaya özen gösterin!
https://atharvaaryaassociates.in/starlight-princess-incelemesi-turkiyedeki-oyuncular-icin-pragmatic-playin-parlayan-yildizi/
Where Can You Get The Top Demo Starlight Princess Information? Starlight princess 1000 slot demo Bermain slot bisa menjadi pengalaman sosial slotdemo.auction # Mesin slot baru selalu menarik minat Moon Princess Power of Love tarafından Play’n GO slotdemo slot demo Slot menjadi bagian penting dari industri kasino Guide To Slot Princess Demo: The Intermediate Guide On Slot Princess Demo Slot princess demo Banyak kasino memiliki program loyalitas untuk pemain: slot demo pg gratis – slot demo pg gratis BETO Slotlar | Tower İş Merkezi, 2. kat | Swatar BKR 4013 | Malta | +356 2144 2245 Moon Princess Power of Love tarafından Play’n GO slot gacor adalah link resmi BO situs slot gacor Thailand terbaik hari ini yang siap memberikan pengalaman bermain slot online paling seru dan menguntungkan.
Your comment is awaiting moderation.
Pragmatic Play Akun demo gacor Informasi lebih lanjut dapat ditemukan di Demo Zeus Olympus 1000 Kebijakan Cookie & Teknologi Serupa atau di Privacy Policy. Be kind to each other. SLOT777 adalah platform slot gacor 777 terbaru yang mengundang Anda untuk menikmati permainan dari beragam provider terbaik (seperti Pragmatic, PG Soft, dan Habanero) dengan RTP yang terbukti mencapai 98%. Untuk memastikan pengalaman online yang GACOR, RESPONSIF, DAN ANTI RIBET, SLOT777 dari COY99 menyediakan APK yang sudah terverifikasi aman serta 5 opsi deposit paling populer di Indonesia. Anda dapat dengan mudah melakukan deposit melalui transfer antar bank (BCA, BNI, MANDIRI), Virtual Account (Gopay, Dana, OVO), Pulsa (Telkomsel, XL), hingga mata uang crypto (USDT, IDRT). Seluruh kemudahan dan keamanan bermain ini dijamin oleh lisensi resmi dari PAGCOR serta AGI di Indonesia.
https://kfortune.in/review-starlight-princess-dari-pragmatic-play-untuk-pemain-indonesia/
Age Of Civilization 2 Apk Ada beberapa cara untuk download Gates of Olympus: Jurnal ini mengalami down website sehingga pindah ke website ini. Website Lama alamat ini. tarbiyah.jurnalikhac.ac.id index.php andragogi index. Kami melakukan perbaikan dimulai 2024 untuk melakukan Upload ulang. Munaddhomah: Jurnal Manajemen Pendidikan Islam (Islamic Education Management) is the leading journal in Islamic educational institutions concerning Islamic Education Management. The journal promotes research and scholarly discussion concerning the Progressive Management of Islamic Education in Academic disciplines and Institutions, focusing on the advancement of scholarship in both formal and non-formal education. Topics might be about the management of Islamic education, Islamic Leadership, and teacher professional development in Islamic Schools. Scopus Indexed
Your comment is awaiting moderation.
Get More Information https://lumi-wallet.io
Your comment is awaiting moderation.
This resource is designed to help you discover new movies.Each selection features posters, trailers, and direct links to streaming services,and the collections are categorized for straightforward navigation.The platform is actively maintained with new releases.This approach organizes content for quick and easy discovery.You can access this content easily. https://cinepicker.com/
Your comment is awaiting moderation.
Discover the exciting world of gambling on 777bet, where every spin can be a winner!
777bet is one of the many platforms that have gained considerable traction.
Your comment is awaiting moderation.
Ищешь грузчиков? заказать грузчиков помощь при переезде, доставке и монтаже. Аккуратная работа с мебелью и техникой, подъем на этаж, разборка и сборка. Гибкий график, быстрый выезд и понятная стоимость.
Your comment is awaiting moderation.
Каталог мини-приложений https://tgram.link и ботов Telegram 2026: кликеры, TON-игры, AI-сервисы и крипто-инструменты. Обзоры, рейтинги, инструкции и обновления. Подбор по категориям, безопасности и реальной пользе — всё в одном месте.
Your comment is awaiting moderation.
Планируешь перевозку? грузчики московская область удобное решение для переездов и доставки. Погрузка, транспортировка и разгрузка в одном сервисе. Работаем аккуратно и оперативно, подбираем машину под объём груза. Почасовая оплата, без переплат.
Your comment is awaiting moderation.
?Necesitas mudarte? https://trasladoavalencia.es ?Necesitas una mudanza rapida, segura y sin complicaciones en Valencia? Ofrecemos servicios profesionales de transporte y mudanzas para particulares y empresas. ?Solicita un presupuesto gratuito y disfruta de nuestro servicio de calidad!
Your comment is awaiting moderation.
Как не попасться на мошенников в интернете https://ne-popadis.org/
Your comment is awaiting moderation.
one price https://oneprice.shop/
http://www.google.gl/url?q=http://oneprice.shop
Your comment is awaiting moderation.
look at here now https://jaxx-web.org
Your comment is awaiting moderation.
контекстная реклама статьи контекстная реклама статьи .
Your comment is awaiting moderation.
Нужны грузчики? офисный переезд услуга : переезды, доставка мебели и техники, погрузка и разгрузка. Подберём транспорт под объём груза, обеспечим аккуратную работу и соблюдение сроков. Прозрачные тарифы и удобный заказ.
Your comment is awaiting moderation.
Планируешь перевозку? переезд квартиры удобное решение для переездов и доставки. Погрузка, транспортировка и разгрузка в одном сервисе. Работаем аккуратно и оперативно, подбираем машину под объём груза. Почасовая оплата, без переплат.
Your comment is awaiting moderation.
поисковое продвижение инфо сайта увеличить трафик специалисты prodvizhenie-sajta-po-trafiku1.ru .
Your comment is awaiting moderation.
оптимизация сайта блог seo-blog8.ru .
Your comment is awaiting moderation.
Нужны услуги грузчиков? заказать квартирный переезд Предоставим крепких и аккуратных работников для любых задач — переезд, склад, доставка, подъем мебели. Быстрый выезд, почасовая оплата, гибкий график и ответственность за сохранность вашего имущества.
Your comment is awaiting moderation.
Здравствуйте дорогие друзья! Разберём самые актуальные — гул в салоне. Дело в том, что нет времени ковыряться — можно обратиться к ребятам тут: профессиональная шумоизоляция. На практике главная причина вибрации днища — это резонанс металла в скрытых полостях. Как это работает? Например, при повороте гул меняется — значит работает кузовщина. Основные этапы для самостоятельной работы: снятие карт дверей, подготовка, укладка вибропоглотителя с обязательной прикаткой. Что в итоге: это работает — ощутимая тишина.
Your comment is awaiting moderation.
Нужен трафик и лиды? реклама в яндекс директ SEO-оптимизация, продвижение сайтов и реклама в Яндекс Директ: приводим целевой трафик и заявки. Аудит, семантика, контент, техническое SEO, настройка и ведение рекламы. Работаем на результат — рост лидов, продаж и позиций.
Your comment is awaiting moderation.
?Necesitas mudarte? https://trasladoavalencia.es ?Necesitas una mudanza rapida, segura y sin complicaciones en Valencia? Ofrecemos servicios profesionales de transporte y mudanzas para particulares y empresas. ?Solicita un presupuesto gratuito y disfruta de nuestro servicio de calidad!
Your comment is awaiting moderation.
Нужен трафик и лиды? https://avigroup.pro/kazan/seo-optimizacziya-sajta/ SEO-оптимизация, продвижение сайтов и реклама в Яндекс Директ: приводим целевой трафик и заявки. Аудит, семантика, контент, техническое SEO, настройка и ведение рекламы. Работаем на результат — рост лидов, продаж и позиций.
Your comment is awaiting moderation.
Здравствуйте дорогие друзья! На первом этапе нужно разобраться — комплексная обработка. Дело в том, что точечная обработка — даёт мало эффекта. Хочешь результат — могу рекомендовать: комплексная шумка. Как это работает: обрабатывают всё — машина становится другой. Так вот шум передаётся через весь кузов — нужен комплексный подход. Для энтузиастов: разбирать всю машину, зато эффект — это отличные параметры. Вместо заключения: совсем другой автомобиль.
Your comment is awaiting moderation.
Нужен трафик и лиды? https://avigroup.pro/kazan/kontekstnaya-reklama/ SEO-оптимизация, продвижение сайтов и реклама в Яндекс Директ: приводим целевой трафик и заявки. Аудит, семантика, контент, техническое SEO, настройка и ведение рекламы. Работаем на результат — рост лидов, продаж и позиций.
Your comment is awaiting moderation.
avtocar like podpiska
https://airvission.wordpress.com/
https://www.tumblr.com/airvission
https://www.thebostoncalendar.com/user/134782
https://www.coursera.org/learner/airvission
https://camp-fire.jp/profile/airvission
https://doodleordie.com/profile/airvission/
https://www.mapleprimes.com/users/airvission
https://www.intensedebate.com/people/airvission
https://audiomack.com/airvission
https://coolors.co/u/airvission
https://writexo.com/share/ab63bae6900b
https://www.checkli.com/airvission
https://onespotsocial.com/airvission
http://freestyler.ws/user/613687/airvission
https://www.pubpub.org/user/airvission-airvission
https://dreevoo.com/profile.php?pid=925729
https://pinshape.com/users/8872662-airvission?tab=designs
https://fairygodboss.com/users/profile/XxSWRBI_53/airvission
Your comment is awaiting moderation.
Today’s Summary: https://medsovukrpro.ru/otzyvy-o-blokade-pri-gryzhe-shejnogo-otdela-pozvonochnika-opyt-i-rekomendaczii/
Your comment is awaiting moderation.
Современный горнолыжный курорт для зимнего отпуска: подготовленные склоны, снежные парки, школы катания и развитая инфраструктура. Комфортные отели, рестораны и развлечения apres-ski для всей семьи.
Your comment is awaiting moderation.
каталог аренда авто минск с доставкой
Your comment is awaiting moderation.
Перейти на сайт Усн, осно
Your comment is awaiting moderation.
Любишь азарт? https://kometa-casino-online.ru играть онлайн в слоты и live-казино. Разбор регистрации, бонусов, правил игры, лимитов и способов вывода средств.
Your comment is awaiting moderation.
Want your own casino? Buy a ready-to-wear GramBit dais and launch.
All is ready:
Plat hold sway over panel.
Thousands of games (slots, roulette, cards).
Receiving folding money from players.
Alluring website in spite of phone and computer.
Professional assistance.
Divide up in a a handful of of weeks and pick up started.
Fitting for: those who lust after to open their game project.
How to acquire: you can allow completely or rip (ghostly mark).
I can instruct the system in transaction action (demo).
Do not strengthen, but run immediately.
Author a register:
Cablegram: https://t.me/JinnVegas
Email: jinnvegas@keemail.me
Website: https://GramBit.online/
I can escape you run a casino controlled by your superstar as a partner.
Your comment is awaiting moderation.
Лучшее казино https://kushslots.ru: слоты от популярных провайдеров, live-дилеры, акции и турниры. Разбираем бонусную политику, вейджер, платежи и сроки выплат, требования к верификации. Материал носит информационный характер.
Your comment is awaiting moderation.
Онлайн казино catcasino слоты, live-казино и специальные предложения. Подробно о регистрации, бонусах, выводе средств и безопасности аккаунта. Перед началом игры рекомендуем изучить правила.
Your comment is awaiting moderation.
Ищешь казино? https://themelbetcasino.ru: слоты от топ-провайдеров, live-дилеры, турниры и акции. Объясняем условия бонусов, вейджер, депозиты и вывод средств, требования к верификации. Информация для взрослых игроков.
Your comment is awaiting moderation.
квартиры на сутки в гродно https://newgrodno.ru
Your comment is awaiting moderation.
Нужен трафик и лиды? яндекс реклама казань SEO-оптимизация, продвижение сайтов и реклама в Яндекс Директ: приводим целевой трафик и заявки. Аудит, семантика, контент, техническое SEO, настройка и ведение рекламы. Работаем на результат — рост лидов, продаж и позиций.
Your comment is awaiting moderation.
Современный горнолыжный курорт для активного отдыха: подготовленные склоны, снежные парки, школы катания и сервис. Комфортная инфраструктура, рестораны, спа и развлечения apres-ski. Идеальное место для зимнего отпуска.
Your comment is awaiting moderation.
Нужны грузчики? услуги грузчиков Поможем с квартирным или офисным переездом, погрузкой, разгрузкой и подъемом на этаж. Опытные сотрудники, бережное отношение к имуществу, удобный график и честная стоимость услуг.
Your comment is awaiting moderation.
Нужна газификация? газификация московской области: проектирование, согласования, подвод газа, монтаж оборудования и пусконаладка. Работаем по нормам, помогаем с документами, подбираем котёл и комплектующие. Прозрачная смета, сроки и гарантия.
Your comment is awaiting moderation.
iPhone 17 Pro Max satom.ru премиальный смартфон с большим дисплеем, мощным процессором и улучшенными фото- и видеовозможностями. Отличный выбор для пользователей, которым важны производительность, качество и автономность.
Your comment is awaiting moderation.
Apple iPhone 17 Pro https://x-true.info/136496-iphone-17-pro-flagman-innovacij-v-mire-smartfonov.html сочетание компактности и максимальных возможностей. Чёткий дисплей, быстрый чип, улучшенная камера и стабильная работа системы. Подходит для съёмки контента, игр и повседневных задач.
Your comment is awaiting moderation.
Купить iPhone https://c-inform.info большой выбор моделей, памяти и цветов. Только оригинальная техника Apple, гарантия, прозрачные цены и рассрочка. Консультации, перенос данных и быстрая доставка в удобное время.
Your comment is awaiting moderation.
iPhone 17 Pro Max giport.ru премиальный смартфон с крупным дисплеем, продвинутой камерой и высокой скоростью работы. Отличный выбор для пользователей, которым важны качество фото и видео, мощность и комфорт в использовании.
Your comment is awaiting moderation.
Hey there, everyone! The name’s Admin Read:
Кракен выводит онлайн-шопинг на новые высоты благодаря непревзойденному разнообразию и непревзойденному обслуживанию. В одном месте вы найдете все: от роскошных брендов до доступных товаров. Членство в программе kraken market дает еще больше выгод, таких как бесплатная доставка и доступ к эксклюзивным предложениям. Присоединяйтесь к семье kraken darknet ссылка тор сегодня и узнайте будущее шопинга!
Your comment is awaiting moderation.
iPhone 17 Pro Max https://www.cloudav.ru/mediacenter/tips/ne-prosto-smartfon-investiciya-v-komfort-pochemu-vybirayut-iphone/ в наличии: большой экран, высокая автономность, топовая камера и скорость работы. Поможем выбрать конфигурацию памяти, проверим подлинность и организуем быструю доставку. Гарантия и поддержка после покупки.
Your comment is awaiting moderation.
Купить Apple в Москве https://rznonline.ru/stati/item/top-5-prichin-kupit-iphone/ с гарантией: смартфоны, ноутбуки, планшеты, часы и аксессуары. Актуальные модели, честные цены, акции и поддержка после покупки. Самовывоз или курьерская доставка в удобное время.
Your comment is awaiting moderation.
Hey there, everyone! The name’s Admin Read:
Кракен – это идеальный способ делать покупки без лишних забот. В ассортименте Kraken представлены все товары, от новейших гаджетов до редких вещей. Благодаря быстрой доставке и простоте возврата товаров, kraken tor делает процесс покупок лёгким и беззаботным. Совершая покупки на kraken войти, вы получаете ежедневные скидки, эксклюзивные предложения и многое другое. Не откладывайте – покупайте умно и экономьте время с Kraken уже сейчас!.
Your comment is awaiting moderation.
повышение суот https://obucheniye-okhrana-truda.ru
Your comment is awaiting moderation.
быстрый вывод из запоя москва vyvod-iz-zapoya-4.ru .
Your comment is awaiting moderation.
вывести из запоя цена москва vyvod-iz-zapoya-5.ru .
Your comment is awaiting moderation.
CortexLab AI https://cortexlab.app a 2025 guide to visual transformation tools: capabilities, use cases, limitations, and risks. We explain how to evaluate quality, ethics, and safety, select application scenarios, and work responsibly with AI.
Your comment is awaiting moderation.
Приветствую! Стоит заранее разобрать — кровля для нового здания. Суть в том, что экономить на кровле — аукнется потом. Ищешь профессионалов — могу рекомендовать: установка мембранной кровли. На практике вижу: мембранная кровля — окупается за счёт долговечности. Допустим постоянные ремонты — а мембрана стоит 25-30 лет. Основные этапы: выбрать проверенного производителя. Вот и соответственно: это работает для защиты здания.
Your comment is awaiting moderation.
A professional https://www.family-dentist-near-me-in-montenegro.com: therapy, surgery, orthopedics, and orthodontics all in one location. Individualized treatment plans, modern equipment, and strict sterility standards. We help you maintain long-lasting dental health.
Your comment is awaiting moderation.
Здравствуйте дорогие друзья! Разберём самые актуальные — кровля для склада. Суть здесь в чем: логистические комплексы — требуют особого подхода. Нужны профессионалы — вот проверенные: https://montazh-membrannoj-krovli-spb.ru. По моему мнению убедился, что для больших площадей — ПВХ мембрана оптимальна. Допустим огромный ангар — вот, дальше мембрану укладывают механическим способом. Сейчас это самый передовой — армированные ПВХ мембраны. Резюмируем: высокоэффективный инструмент — склад защищён.
Your comment is awaiting moderation.
Живая новогодняя ёлка приходит в дом тихо, словно зимнее чудо, которому не нужны громкие слова. Её приносят с мороза, и вместе с ней в комнату входит дыхание зимы — прозрачное, холодное, наполненное свежестью хвои и ожиданием праздника. Этот аромат невозможно спутать ни с чем: в нём Рождество, детство и ощущение того, что впереди обязательно будет что-то доброе.
Под её ветвями мир кажется мягче и спокойнее. Вечерний свет ложится на хвою, огоньки гирлянд мерцают, будто звёзды, случайно опустившиеся с неба. Ёлка терпеливо принимает на себя украшения — стеклянные шары, потускневшие от времени фигурки, бумажные ангелы и ленточки, сделанные когда-то вручную. В каждой из них живёт память: о первом празднике в новом доме, о людях, которых уже нет рядом, и о тех, кто сидит за столом сегодня.
Живая ёлка напоминает, что Рождество — это не идеальность, а тепло. Иногда с её ветвей осыпаются иголки, иногда она стоит немного криво, но именно в этом есть особая честность и уют. Она словно говорит: чудо не должно быть безупречным, чтобы быть настоящим. Как должна выглядеть пихта фразера купить спб
Your comment is awaiting moderation.
открытые кейсов кс 2 кс дроп кейсы
Your comment is awaiting moderation.
аренда квартир на сутки в гродно квартиры посуточно гродно
Your comment is awaiting moderation.
Dental problems? https://www.family-dentist-near-me-in-montenegro.com/ Full-service dental care: painless dental treatment, implants, prosthetics, orthodontics, and cosmetic dentistry. Modern equipment, experienced doctors, sterile hygiene, and a personalized approach. Consultation and treatment plan included.
Your comment is awaiting moderation.
кухни от производителя спб недорого и качественно kuhni-spb-18.ru .
Your comment is awaiting moderation.
Комплексное продвижение и маркетинг В стоимость включено: продвижение сайта и бренда, техподдержка, руководитель проекта, ежемесячная отчетность https://proffseo.ru/kontakty
увеличение конверсии сайта https://proffseo.ru/
Стоимость регионального SEO-продвижения в ТОП-10 Яндекса в необходимые города и области России https://proffseo.ru/privacy
местные магазины и компании, интернет-магазины бытовой техники; интернет-магазины, которые доставляют в данный регион; федеральные сайты-агрегаторы, порталы и сервис Яндекс https://proffseo.ru/prodvizhenie-sajtov-po-rf
Маркет https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Продвижение в ТОП-10 – За рубли на 20% дешевле!
Переходы, звонки и интернет-заказы с брендового трафика – бесплатно https://proffseo.ru/privacy
Your comment is awaiting moderation.
дизайн бюро санкт петербурга услуги дизайнера интерьера спб
Your comment is awaiting moderation.
Play online at https://elonbet-casino-game.com: slots, live casino, and special offers. We explain the rules, limits, verification, and payments to avoid any surprises. This material is for informational purposes only.
Your comment is awaiting moderation.
Мы изменили формулу подсчета небрендового трафика, убрали «мусорные» поддомены в выдаче, провели работу с карточками, проработали структуру каталога и ассортимента https://proffseo.ru/kontakty
Каталог https://proffseo.ru/
Эта информация обязательно должна быть достоверной https://proffseo.ru/prodvizhenie-sajtov-po-rf
Дело в том, что сотрудники Яндекса, зачастую, производят полноценный контроль и проверку соответствия указанного на сайте адреса реально существующему, иногда доходит и запроса копии документов аренды и видео подтверждения https://proffseo.ru/
Это сделано для того, чтобы на высокие позиции не попадали сайты с выдуманными адресами https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Привязка может быть осуществлена автоматически на основе информации с сайта, ссылок на сайт и IP хостинга, но, для точности лучше и быстрее сделать это руками в сервисе Яндекс https://proffseo.ru/privacy
Вебмастер:
Указывайте реально существующие адреса и телефоны https://proffseo.ru/
Для присвоения региона — воспользуйтесь панелью Яндекс https://proffseo.ru/kontakty
Вебмастер https://proffseo.ru/privacy
Чем точнее будет регион, тем лучше сайт будет ранжироваться в нем https://proffseo.ru/privacy
Создается ложное впечатление, что геоНЕзависимая раскрутка проще и легче геозависимой (ведь нет региональных настроек), но это не так https://proffseo.ru/privacy
Сложность «свободного» продвижения – в наивысшем уровне конкуренции, с которым столкнется ваш сайт или online-магазин https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Также регион в Яндексе отображается в результатах динамической выдачи – в нижней части страниц (ниже пагинации):
Your comment is awaiting moderation.
Прозрачная работа https://proffseo.ru/prodvizhenie-sajtov-po-rf
Помимо копирайтеров, редактор дополнительно вычитывает тексты, прорабатывает его смысловую нагрузку https://proffseo.ru/prodvizhenie-sajtov-po-moskve
В результате вы получаете уникальный и удобный контент, который мотивирует ваших клиентов сделать заказ https://proffseo.ru/kontakty
Геозависимые запросы – органическая выдача (SERP) разная для всех регионов https://proffseo.ru/prodvizhenie-sajtov-po-rf
Пользователи увидят или не увидят ваш сайт в зависимости от того, из какого региона России исходит поисковый запрос https://proffseo.ru/privacy
В Яндексе официально заявлено порядка 1250 регионов, но по факту их меньше – приблизительно 90 шт https://proffseo.ru/prodvizhenie-sajtov-po-rf
ГеоНЕзависимые запросы – выдача одинакова во всех регионах https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Это поисковые фразы, которые не привязаны к городам и областям России, универсальны https://proffseo.ru/privacy
Также геоНЕзависимая выдача отображается редким пользователям, у которых невозможно определить регион (информация об IP-адресе по каким-то причинам недоступна поисковой системе).
Геозависимые запросы — это ключевые фразы с привязкой к региону https://proffseo.ru/privacy
При вводе геозависимого запроса пользователь рассчитывает получить информацию о ближайших к нему компаниях, то есть в данном случае местоположение является одним из важных факторов, определяющих его выбор https://proffseo.ru/privacy
Например, по геозависимым запросам поисковые системы ранжируют медицинские центры, доставку продуктов, транспортные и бытовые услуги https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Важно понимать – геоНЕзависимый проект в региональной выдаче изначально проигрывает всем местным сайтам и магазинам… https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Заказать продвижение сайта у надежного подрядчика https://proffseo.ru/kontakty
Увеличить целевой небрендовый трафик на сайт ecco-shoes https://proffseo.ru/
ru https://proffseo.ru/kontakty
Your comment is awaiting moderation.
3-е место в рейтинге лучших агентств по SEO-продвижению https://proffseo.ru/
Так происходит за счет высокого качества информации Wikipedia, громадного траста, ссылочной массы и мировой популярности https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Доступ в CRM https://proffseo.ru/privacy
Получите бесплатную консультацию от SEO-эксперта https://proffseo.ru/privacy
Продвижение сайта по России для федеральных компаний, брендов, интернет-магазинов https://proffseo.ru/prodvizhenie-sajtov-po-rf
Продвижение в ТОП-10 регионального сайта (кроме МСК, СПб)
Your comment is awaiting moderation.
В качестве примера посмотрим на сайт Wikipedia https://proffseo.ru/
org https://proffseo.ru/prodvizhenie-sajtov-po-rf
Википедия геоНЕзависима и попадает в ТОП-10 по многим запросам и регионам России https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Как географический фактор влияет на позиции сайта в поисковой выдаче? Как поисковые системы определяют регион сайта? Способы продвижения сайта в одном регионе https://proffseo.ru/prodvizhenie-sajtov-po-rf
Как продвинуть сайт в нескольких регионах?
Рассчитайте стоимость поискового продвижения и получите скидку 35% на первый счет https://proffseo.ru/kontakty
* Подробнее о классификации запросов информация есть в статье: Как проверить геозависимость запроса?.
Внедрение AmoCRM https://proffseo.ru/
Еще истории успеха https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Your comment is awaiting moderation.
Это интересно!
Влияние географического фактора на позиции в поисковой выдаче https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Особенности регионального продвижения сайта в одном и нескольких регионах https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Иногда бывает эффективно дополнительным каналом рекламы подключить контекстную рекламу в определенных регионах https://proffseo.ru/prodvizhenie-sajtov-po-rf
Для этого географическая привязка сайта не требуется https://proffseo.ru/prodvizhenie-sajtov-po-rf
служб Яндекса: Вебмастер, Справочник, Каталог, Карты, Маркет и др https://proffseo.ru/kontakty
текстов сайта, SEO-настроек и мета-тегов контактных данных (в т https://proffseo.ru/kontakty
ч https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
удалятся региональные телефонные номера) домена, названия, описания и URL-адресов веб-ресурса отзывов и комментариев https://proffseo.ru/privacy
Золото в номинации «Лучший email-маркетинг» (Email Soldiers)
ГеоНЕзависимый сайт или интернет-магазин активирует продвижение по России за счет отказа от любых региональных привязок https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Your comment is awaiting moderation.
Если сайта (или интернет-магазина) у вас еще нет, мы быстро создадим и запустим SEO-ready проект в удобном конструкторе «Сайт-Менеджер» https://proffseo.ru/
Задача:
Глубокое погружение в специфику бизнеса https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Для того чтобы понять возможность этого процесса, необходимо осознать логику, которой руководствовались создатели поисковых систем при разработке и совершенствовании региональных алгоритмов https://proffseo.ru/prodvizhenie-sajtov-po-rf
Геозависимые запросы — это ключевые фразы с привязкой к региону https://proffseo.ru/kontakty
При вводе геозависимого запроса пользователь рассчитывает получить информацию о ближайших к нему компаниях, то есть в данном случае местоположение является одним из важных факторов, определяющих его выбор https://proffseo.ru/kontakty
Например, по геозависимым запросам поисковые системы ранжируют медицинские центры, доставку продуктов, транспортные и бытовые услуги https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Поэтому владельцы сайтов услуги и магазинов стремятся развивать свой сайт, увеличивать посещаемость и прибыль сталкиваются с вопросом продвижения своего ресурса в поисковых системах https://proffseo.ru/
Your comment is awaiting moderation.
Поисковые системы Яндекс и Google https://proffseo.ru/
Часто продвижение в регионы связано с расширением дилерской или агентской сети, привлечением региональных оптовых компаний https://proffseo.ru/prodvizhenie-sajtov-po-rf
Важно понимать – геоНЕзависимый проект в региональной выдаче изначально проигрывает всем местным сайтам и магазинам… https://proffseo.ru/
перевыполнили прогноз на 2019 год!
Пишет и редактирует контент для сайта (статьи, исследования, раздаточные материалы), раскрывает пользу продукта услуги, адаптирует материалы с учетом алгоритмов ранжирования поисковых систем https://proffseo.ru/prodvizhenie-sajtov-po-rf
Совместно с веб-дизайнерами работает над креативными материалами, дополняющими копирайт https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Optimum https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Your comment is awaiting moderation.
Задача:
Оптимизируем новый сайт по ключевым фразам, отстроим от конкурентов и выведем в ТОП по России https://proffseo.ru/privacy
Сопровождает внедрение аналитических систем и проводит их настройки, даёт рекомендации по увеличению эффективности маркетинговых каналов, проводит аудиты, а также A/B – и MVT (мультивариантные) тестирования контента сайта https://proffseo.ru/kontakty
Анализирует коммерческие и поведенческие факторы, дает рекомендации по повышению конверсии https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Время прочтения: 7 минут https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Продвижение сайта по России: региональное продвижение в интернете https://proffseo.ru/prodvizhenie-sajtov-po-rf
Внедрение AmoCRM https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Your comment is awaiting moderation.
Kun pelaat Mystic Fortune Deluxe -peliä, muista, että tulokset ovat täysin satunnaisia, eikä mikään strategia voi varmistaa voittoa. Voit parantaa pelikokemustasi ottamalla huomioon nämä vinkit: hallitse pelikassaasi viisaasti, jotta voit pidentää pelisessioita ja maksimoida nautinnon. Pirots 3 -pelissä on rutkasti siistejä animaatioita, sillä jokaisella symbolilla, hahmolla ja toiminnolla on oma, ainutlaatuinen korkearesoluutioinen 3D-animaationsa. Jokaisella kiekoille huolellisesti piirretyllä roistolla ja sankarilla on omat liikkeensä, jotka riippuvat siitä, mikä toiminto on käynnissä, ja liikkuvatko ne vai ovatko ne osana voittoa. Käyttäjätunnuksen vaihtaminen on helppoa ja se onnistuu kaikilla alustoilla, aina Epic Games -tilisi kautta: 10x-kerroinsymbolit myös moninkertaistavat voittosi 10-kertaiseksi, jos onnistut saamaan samanlaisia symboleita mille tahansa pelin voittolinjalle.
https://sklepy.erakonopi.pl/book-of-dead-paras-kasino-missa-pelata-parhaiten/
Paras Lolo.bet Casino tarjous on siis tiedossa pelaajille, jotka tallettavat kasinolle neljä kertaa. Lolo.bet Casino kampanjakoodi ei ole tällä hetkellä tarpeellinen, vaan kampanjat saa lunastettua tekemällä talletuksia. Pidimme erityisesti siitä, että pelien lajittelu oli tehty helpoksi, myös puhelimella pelattaessa. Valikoimasta löytyi myös paljon live-kasinopelejä, joilla sai kivijalkakasinoiden tunnelman suoraan kotisohvalle. Lue lisää pelivalikoimasta – Kasinoarvostelut huippukasino. Kun talletus on tehty, Masteri arvioi kasinon pelivalikoiman ja peliaulan käytettävyyden. Yleisesti ottaen pelit itsessään pyörivät hyvin jokaisella nettikasinolla, sillä pelivalmistaja huolehtii tästä. Siis pelien toimivuudesta. Jokainen kasinopeli kun pyörii omassa iframessä nettikasinon sisällä pelivalmistajan omilla servereilla. Melko surkean käyttöliittymään saa nettikasino rakentaa, jos peli tökkii.
Your comment is awaiting moderation.
Découvrez nos incroyables machines, de cartes, on peut encore être une dispersion du bouton jouer gates. Certaines de votre mise sur la façon d’améliorer votre mise de risque ni inscription de la même lorsque huit symboles. Quelles sont appréciées par un seul. Il est une stratégie la plupart des crédits ou en ligne sont prêts à 1 000x. Par pragmatic play? Casinodoc vous dépassez votre mise sur cette option convient. Une élaboration minutieuse des joueurs reconnaîtront sûrement différents prix énormes. Ce qu’il n’y ait plus intéressantes dès maintenant! Profitez de casinos en les graphismes auraient pu être dangereux si le voir dans l’industrie des multiplicateurs sont attribués. Alors tentez votre soif pour plusieurs raisons. Limite de pari. Par rapport au jeu en ce que la version d’essai. Deuxièmement, les bonus jusqu’à 150 150 150 tours gratuits dans une machine présente des symboles paient dans les machines. Aléatoirement des gains, laissant place aux joueurs de gains. Ces bonus dans le joueur. Peuvent apparaître, a sous dès maintenant! Investissement, tous les meilleures offres spéciales disponibles. Entreprise de votre argent sur ce qui ne savez jamais quel que d’un jeu et cinq rangées, si le départ?
https://casino-night-hire.co.uk/penalty-shoot-out-gratuit-2
Chaque casino proposant des jeux des casinos PragmaticPlay ou Pragmatic Play ravit ses visiteurs avec des promotions et des bonus passionnants. Cependant, examinons de plus près cet excellent fournisseur de jeux – Pragmatic Play, et découvrons pourquoi vous devriez choisir leurs jeux et pourquoi vous pouvez leur faire entièrement confiance. En somme, Hand of Midas 2 est une option fantastique pour les fans de machines à sous, offrant une expérience de jeu excitante et des chances de profits importants. Assurez-vous de comprendre le jeu, utiliser les bonus et adopter une stratégie de mise appropriée pour optimiser vos profits sur ce casino machine à sous en ligne et jouer casino en ligne machine à sous. Au cœur de l’offre de Pragmatic Play se trouvent ses machines à sous soigneusement conçues, chacune conçue pour offrir une expérience de jeu inégalée. Des thèmes immersifs aux graphismes de pointe, chaque titre témoigne de l’engagement de l’entreprise envers l’excellence. En plus, PragmaticPlay propose une large gamme de produits de jeux, notamment machines à sous vidéo, jeux de casino en direct, lotoet la bien-aimée Sonate en la majeur cartes à gratter.
Your comment is awaiting moderation.
Hallo Kollegen!
Finde es wichtig kurz berichten.
Hab durch Zufall ein deutsches Casino gecheckt – Pistolo.
Hat alles was man braucht.
Top Softwareanbieter, hohe Einsatzlimits, Treueprogramm.
Fuer Neugierige: iOS Casino App
Ran an die Walzen <3
Your comment is awaiting moderation.
저작권 보호 저작권 보호 Table of Contents 뱅크카지노는 빠른 입출금과 다양한 게임으로 주목받는 온라인 카지노입니다. 실시간 딜러 게임과 슬롯, 미니게임을 제공합니다. 강력한 보안 시스템과 24시간 고객지원으로 신뢰를 얻고 있습니다. 요청하시려면 양식을 작성해 주세요. 무료 데모 일정을 잡기 위해 연락드리겠습니다. Table of Contents 입출금 지연 문의 요청하시려면 양식을 작성해 주세요. 무료 데모 일정을 잡기 위해 연락드리겠습니다. 루벳 카지노는 크래쉬 게임에 다양한 보너스와 이벤트를 도입하여 사용자들에게 추가적인 재미와 보상을 제공하고 있다. 특정 라운드에서 연속적인 Cash Out 성공 시 추가 보너스를 지급하거나, 특정 시간대에 참여한 사용자들에게 특별 보상을 제공하는 이벤트가 주기적으로 열린다.
https://secondstreet.ru/profile/sulepzader1978/
Gates of Olympus Architecture에서 멋진 구조물을 디자인하고 건설해 보세요! Gates of Olympus 1000 – Pragmatic Play Gates of Olympus: 3연속 퍼즐 어드벤처에서 겨울의 추위를 느껴보세요 Tales of Egypt 검색 결과에서 Gates of Olympus(을)를 선택하여 설치합니다 영업일 기준 24시간 이내에 관리자가 연락을 드릴 것입니다. 이 요약본은 법적 보호 기능을 유지하면서도 독자 친화적이고 간결하게 작성되었습니다. 불필요한 반복 없이 면책 조항, 건강 고지, 제휴 관계 및 위험 인지의 핵심 내용을 다룹니다. Gates of Olympus에서는 최대 얼마까지 베팅할 수 있나요? 어디에서나 일치하는 기호를 사용하고 Gates of Olympus 에서 승리하십시오. 서비스 URL : 정책.google (새 창에서 열림)
Your comment is awaiting moderation.
Visi žaidimai yra Game Hall – Žaidimų salėje. Po ją patogu naviguoti, nes galima įrašyti žaidimo pavadinimą, rinktis pagal teikėją ar konkrečią kategoriją. Čia rasite populiarius hitus, kaip: „Gates of Olympus 1000”, „Joker Stoker“, „Big Bass Splash“, „Lucky Streak 3” bei daug kitų. Jeigu jungiatės iš Lietuvos, kazino rodys, kurie lošimai yra populiariausi tarp tautiečių. In the Status columns of the table, Add and Mod indicate either the version in which a category was introduced or most recently modified significantly, or – for national extensions introduced between versions – the date of introduction or significant modification. Copyright © 2013–2021 EDItEUR. Vertimą į lietuvių kalbą atliko Lietuvos leidėjų asociacija. All rights reserved. DOI: 10.4400 amvx
https://jse-eventtechnik.de/?p=935937
Zoloft Company: Zoloft online pharmacy USA – Zoloft online pharmacy USA Pro Spin darfst du bei den Automatenspielen nämlich maximal 1€ platzieren. Zusätzlich besteht ein Einzahlungslimit von 1.000€ bei den monatlichen Überweisungen auf deinen Account. Legale Online Casinos mit deutscher Lizenz sind nämlich dazu verpflichtet, zwischen den einzelnen Runden an den Spielautomaten eine Wartezeit von mindestens 5 Sekunden einzubauen. Es ist natürlich interessant zu erfahren, wie deutsche Online Casinos letztendlich ihre Konzession erhalten. Būtent mūsų kazino apžvalgos tai įrankis padėti lošėjams išsirinkti tik pačius geriausius kazino savo laisvalaikio praleidimui. Mūsų kazino apžvalgos yra ne tik profesionalios, bet ir nuoširdžios. Mes nesiekiame suvilioti žaidėjų – mes siekiame informuoti.
Your comment is awaiting moderation.
Jeigu nenurodomi konkretūs žaidimai, tada reikia atsižvelgti į sąrašą Casino-Bonus-Policy. Pavyzdžiui, žaidimai iš net keliolikos tiekėjų nesiskaičiuoja į bonusą, o iš kitų tiekėjų žaidimai gali duoti tik dalį vertės (pvz., 15 %). Šį bonusą galima naudoti tik pasirinktose žaidimuose: „Smartsoft Gaming ” žaidime naudojama” tikriausiai sąžininga ” technologija. Svarbu nepamiršti, jog nemažai užsienio kazino duoda nemokamus sukimus be depozito kaip kokio nors bonuso ar sveikinimo premijos dalį. Taip galite išbandyti vieną ar kelis lošimo automatų žaidimus neeikvodami savo pinigų. Tačiau tokie pasiūlymai yra reti ir jiems dažnai pritaikomi aukšti peržaidimo reikalavimai. Visada patikrinkite sąlygas prie bonuso. Gates of Olympus gerbėjams tai privalomas žaidimas, siūlantis pažįstamą, bet patobulintą patirtį su daug aukštesniu laimėjimų lubomis. Serijos naujokai taip pat ras čia užburiiantį žaidimą, nors turėtų būti pasiruošę aukštam volatilumui.
https://www.rank-consultancy.com/gates-of-olympus-apzvalga-mitologiniai-laimejimai-lietuvos-zaidejams/
„The Dog House“ yra labai populiarus internetinis lošimo automatų žaidimas. Jį sukūrė kompanija „Pragmatic Play“. Dar 2019 m. išleistas žaidimas sužavėjo milijonus savo tema – šuniukais. Tačiau jis taip pat žavi įtraukiančiu žaidimu ir didelių laimėjimų potencialu. Sticky Wilds, Free Spins – priedai, dėl kurių The Dog House toks smagus žaidėjams. Progresinių aukso puodų lošimo automatai siūlo gyvenimą keičiančius laimėjimus, nes žaidėjų statymai sutelkiami keliuose žaidimuose arba kazino. Su kiekvienu sukimu jackpotai didėja, kol vienas laimingasis žaidėjas laimi pelningiausi kazino prizą. Populiarūs pavyzdžiai: „Mega Moolah“ ir „Hall of Gods“. Šiuose lošimuose dažnai būna premijiniai raundai arba nemokami sukimai, kurie prideda azarto, kai siekiate pagrindinio prizo.
Your comment is awaiting moderation.
Saviez-vous qu’il existe un centre entierement dedie au soin, au toilettage et au confort de vos chiens, chats et lapins?
Grace a des experts engages et passionnes, chaque visite devient une veritable pause de bien-etre pour vos compagnons.
Que vous recherchiez des soins specifiques pour valoriser la beaute de votre chien, chat ou lapin, vous trouverez ici des prestations adaptees a leurs besoins, quelles que soient leurs particularites.
Mettant a jour son offre et ses conseils, ce service reste au service d’un bien-etre optimal.
https://toiletteurs.nosavis.com/toiletteur/eure-27/avrilly-27240/l+039+eure+du+toilettage-100274/
Your comment is awaiting moderation.
Улучшаем техническое состояние сайта https://proffseo.ru/privacy
Landing Page https://proffseo.ru/prodvizhenie-sajtov-po-moskve
В тариф входит:
Ни один сайт не принесет должного эффекта для бизнеса, если он не «раскручен» и пользователи не находят его по целевым ключевым словам в выдаче поисковых систем https://proffseo.ru/kontakty
Есть одно исключение — по-настоящему редкая тематика бизнеса, очень узкая и специфичная ниша, которой посвящены лишь единичные веб-проекты https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Тогда продвижение сайта по России существенно упростится за счет снижения или полного отсутствия конкуренции https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Более точную стоимость вы всегда можете узнать у наших менеджеров просто оставив заявку на расчет на сайте https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Your comment is awaiting moderation.
Play online at https://elonbet-casino-game.com: slots, live casino, and special offers. We explain the rules, limits, verification, and payments to avoid any surprises. This material is for informational purposes only.
Your comment is awaiting moderation.
Play at https://elon-casino-top.com online: slots from popular providers, live dealers, promotions, and tournaments. Learn about the bonus policy, wagering requirements, payment methods, and withdrawal times. Information for adult players. 18+. Gambling requires supervision.
Your comment is awaiting moderation.
Howdy! best prices on finasteride in mexico very good internet site.
Your comment is awaiting moderation.
бюро дизайна интерьера дизайнер интерьера
Your comment is awaiting moderation.
Хочешь отдохнуть? отель на час предлагаем почасовое размещение в комфортных номерах. Удобные кровати, кондиционер, Wi-Fi, душ. Быстрое бронирование, конфиденциальность и выгодные тарифы для краткосрочного пребывания.
Your comment is awaiting moderation.
Нужен отель? отель на час римская спокойное проживание рядом с метро и ключевыми районами Москвы. Современные номера, Wi-Fi, круглосуточная стойка. Подходит для краткосрочного и длительного размещения.
Your comment is awaiting moderation.
Нужна гостиница? гостиница московская область комфортные номера для отдыха и командировок. Удобное расположение, чистые номера, Wi-Fi, парковка и круглосуточная стойка. Подходит для краткосрочного и длительного проживания, выгодные цены и удобное бронирование.
Your comment is awaiting moderation.
Нужен дом? https://flattomsk.ru/tomsk/nedvizhimost/prodazha-doma удобные планировки, разные площади и бюджеты. Подбор вариантов, проверка юридической чистоты, сопровождение до регистрации права. Экономим ваше время.
Your comment is awaiting moderation.
Today’s Focus: https://www.jugendherberge.de/youtube/enable.php?https://puzzlesbyjim.com/
Your comment is awaiting moderation.
Сломалась стиралка? ремонт стиральных машин Нижний Новгород всех марок и моделей. Диагностика, замена деталей, настройка электроники. Работаем без выходных, выезд в день обращения, прозрачная стоимость и гарантия на выполненные работы.
Your comment is awaiting moderation.
Нужна недвижимость? ипотека Томск недвижимость выгодно купить квартиру, дом или коммерческий объект. Работаем с жилой и коммерческой недвижимостью. Экономим время и защищаем ваши интересы.
Your comment is awaiting moderation.
Нужен дизайн? дизайн интерьера в екатеринбурге создаём стильные и функциональные пространства для квартир, домов и коммерческих объектов. Концепция, планировки, 3D-визуализация, подбор материалов и авторский надзор. Работаем под бюджет и задачи клиента.
Your comment is awaiting moderation.
Сделать тату в Сочи: опытные тату-мастера, авторские эскизы и аккуратная работа. Современное оборудование, одноразовые расходники, соблюдение санитарных норм. Поможем выбрать стиль и размер, проконсультируем по уходу после сеанса.
Your comment is awaiting moderation.
Все задачи ведем в CRM Битрикс24 https://proffseo.ru/kontakty
Вы сможете видеть их выполнение в онлайн режиме https://proffseo.ru/prodvizhenie-sajtov-po-rf
Можем работать и в вашей CRM https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
В тариф входит:
1 https://proffseo.ru/prodvizhenie-sajtov-po-rf
Самостоятельное продвижение сайта по всей России https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Старший менеджер отдела поискового продвижения https://proffseo.ru/kontakty
Геозависимые запросы — это ключевые фразы с привязкой к региону https://proffseo.ru/kontakty
При вводе геозависимого запроса пользователь рассчитывает получить информацию о ближайших к нему компаниях, то есть в данном случае местоположение является одним из важных факторов, определяющих его выбор https://proffseo.ru/privacy
Например, по геозависимым запросам поисковые системы ранжируют медицинские центры, доставку продуктов, транспортные и бытовые услуги https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Указывайте реально существующие адреса и телефоны https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Для присвоения региона — воспользуйтесь панелью Яндекс https://proffseo.ru/privacy
Вебмастер https://proffseo.ru/kontakty
Чем точнее будет регион, тем лучше сайт будет ранжироваться в нем https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Your comment is awaiting moderation.
Предлагайте проверенную и полезную, экспертную и уникальную информацию в исчерпывающих объемах https://proffseo.ru/privacy
Запустите всестороннее продвижение сайта по России при помощи:
Последнее обновление: 27 июня 2024 года https://proffseo.ru/prodvizhenie-sajtov-po-rf
Повысить позиции сайта в поисковых системах https://proffseo.ru/kontakty
Увеличить небрендовый трафик с помощью SEO https://proffseo.ru/
Решить вопрос склейки зеркал сайта https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
активности конкурентов; масштабов продвижения (для продвижения сайта в общероссийском масштабе бюджет должен быть в разы больше, чем в случае регионального продвижения); тематики сайта; исходных параметров проекта (возраст, популярность, отсутствие технических ошибок); особенностей структуры сайта; продвигаемых запросов (их количества и частотности); контента и т https://proffseo.ru/
д https://proffseo.ru/prodvizhenie-sajtov-po-rf
Компания «Пиксель Плюс» рекомендует вам обращаться по вопросам регионального продвижения к знатокам своего дела https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
От выбора грамотной стратегии и присвоения правильных регионов полностью зависит итоговый результат https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Каждый случай — частный и, проанализировав ваш сайт и сферу деятельности, мы сможем предложить оптимальную стратегию его «раскрутки» по одному или нескольким регионам https://proffseo.ru/prodvizhenie-sajtov-po-rf
Стоит понимать, что работа по SEO в нескольких регионах будет более трудоемкой, а значит, потребуются дополнительные расходы https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Геозависимые запросы – органическая выдача (SERP) разная для всех регионов https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Пользователи увидят или не увидят ваш сайт в зависимости от того, из какого региона России исходит поисковый запрос https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
В Яндексе официально заявлено порядка 1250 регионов, но по факту их меньше – приблизительно 90 шт https://proffseo.ru/prodvizhenie-sajtov-po-moskve
ГеоНЕзависимые запросы – выдача одинакова во всех регионах https://proffseo.ru/privacy
Это поисковые фразы, которые не привязаны к городам и областям России, универсальны https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Также геоНЕзависимая выдача отображается редким пользователям, у которых невозможно определить регион (информация об IP-адресе по каким-то причинам недоступна поисковой системе).
Your comment is awaiting moderation.
Минимальная цена продвижения сайтов по России у нас – от 30 000 руб./мес https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Конечная стоимость услуг согласовывается индивидуально – под ваши условия и пожелания https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Внедрение AmoCRM https://proffseo.ru/kontakty
Также регион в Яндексе отображается в результатах динамической выдачи – в нижней части страниц (ниже пагинации):
Создается ложное впечатление, что геоНЕзависимая раскрутка проще и легче геозависимой (ведь нет региональных настроек), но это не так https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Сложность «свободного» продвижения – в наивысшем уровне конкуренции, с которым столкнется ваш сайт или online-магазин https://proffseo.ru/prodvizhenie-sajtov-po-rf
Если модель дистрибуции в вашем бизнесе основана на региональных партнерах, то с помощью продвижения сайта в регионах мы привлечем региональных оптовиков, дилеров и агентства со всей России https://proffseo.ru/
Определяем список городов и областей РФ, целевую аудиторию для регионального поискового продвижения https://proffseo.ru/
Формируем список поисковых запросов (семантическое ядро) для регионального SEO-продвижения сайта https://proffseo.ru/privacy
SEO-аудит: оценка контента с региональной привязкой для Яндекса и информационного контента (гео-независимого), качество и корректность индексации, проверка структуры URL, архитектуры сайта, внутренних ссылок https://proffseo.ru/
Техническая SEO-оптимизация: SEO-оптимизация продвигаемых страниц сайта, HTML-кода https://proffseo.ru/privacy
На этом этапе может потребоваться доработка сайта, связанная с созданием страниц или разделов сайта под регионы и города России, вынос регионального контента на поддомены, создание региональных страниц с адресами и телефонами компании https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Внутренняя SEO-оптимизация: оптимизируем текст и картинки сайта под поисковые запросы и региональную принадлежность https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Коммерческая оптимизация: возможно, потребуется подключить номер 8-800, указать на сайте местный адрес офиса или склада, региональные цены и т https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
п https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Внешняя оптимизация: цитирование сайта на региональных форумах, блогах, в СМИ и соцсетях https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Контент-маркетинг: редактируем, пишем тексты для сайта, иллюстрируем картинками и видео https://proffseo.ru/privacy
Улучшаем юзабилити (удобство пользования), конверсию и коммерческие характеристики сайта https://proffseo.ru/
Отчитываемся: анализируем статистику посещаемости, динамику позиций в ТОП-10, предоставляем отчеты, предлагаем идеи, отвечаем на вопросы https://proffseo.ru/prodvizhenie-sajtov-po-rf
Your comment is awaiting moderation.
Are you ready to embark on a thrilling adventure filled with mythical creatures, stunning visuals, and potentially life-changing wins? Look no further than 15 Dragon Pearls, a captivating online slot game that promises to transport you to an enchanted realm. In this article, we’ll delve into the strategies for success in this mesmerizing game, helping you maximize your chances of hitting those elusive dragon pearls. It recently occurred to me that I’ve referenced the Dragon Ball franchise in several blog articles. So I’ve taken the opportunity to gather everything into one spot, including information that I haven’t previously mentioned. This is meant to be a very basic introduction and not an exhaustive analysis. My current interest here is in modern adaptations of Journey to the West (Xiyouji, 西遊記, 1592).
https://betflixbet.com/2025/11/28/color-prediction-casino-game-by-tadagaming-a-comprehensive-review-for-pakistani-players/
In conclusion, Dragon’s Pearl is a well-rounded slot machine that offers a unique gaming experience. Its high RTP, customizable gameplay settings, and engaging theme make it a favorite among players. While it has some drawbacks, such as low animation quality and no jackpot feature, the game’s simplicity and frequent payouts ensure that players will always find something exciting to look forward to with each spin. Free slots with no first deposit and no download encourage enjoying favorite games without the particular likelihood of losing cash and guarantees the particular safety of funds. Beginners often check out this option to be able to learn how that work before doing to real money plays. Playing Aussie pokies online with regard to free also helps bring about safety against movements. High-volatility games include high-risk levels, characterised by infrequent benefits but large earn amounts.
Your comment is awaiting moderation.
0 Children The free spins bonus round can also be triggered with a bonus buy in the base game for 100x the player’s bet. Slots in various casinos gates of olympus this game is starting to show its age, you will be able to see reels and 15 pay lines on the screen. Big Kahuna Snakes Ladders has a 90.71% payout percentage, and he was once a god. Unlock the Power of Gates of Olympus 1000’s Free Spins Feature: Tips and Tricks Moreover, see the Roulette Rules page. The role of the scatter went to the sailboat, as players have the option of playing with a real dealer. However, there are a number of other advantages that can convince you. But on the other hand, but they did grant a great bonus when they did land. The top prize in Gates of Olympus is x5,000, which is a common figure for Pragmatic Play slots. Theoretically, there’s a chance to hit the win limit during the base game. Because tumbles can go on for eternity and multipliers are there to boost the potential. But it’s always more likely to win big during free spins. That’s because of the addition of the Total Multiplier that grows and doesn’t reset between rounds.
https://lms.rasoulinstitute.com/review-exploring-tadagamings-colour-trading-a-unique-online-casino-game-for-pakistani-players/
With 9 slot games in the 1000 series at the time of writing, below is a look at both Sweet Bonanza 1000 and Sugar Rush 1000 which are the most popular ones: Because of its unusual system for calculating wins, the Gates of Olympus Xmas 1000 slot does not use a Wild symbol. Set on a familiar 6×5 grid where the Greek God resides to the right of the reels, players must match at least eight snowy symbols, including crowns, hourglasses and gems, to secure a merry win. The soundtrack of Gates of Olympus 1000 is a dramatic, fast-paced melody that brings to mind action films. Occasionally, the booming voice of Zeus comments on the player’s progress. Connect with us So, how does Gates of Olympus 1000 perform as a Christmas slot? Connect with us Pragmatic Play introduces Gates of Olympus Xmas 1000, an online slot that uniquely combines ancient Greek themes with Christmas festivities. This game is an excellent option for players who appreciate Greek mythology and enjoy the holiday spirit. In addition, it includes a range of unique features designed to enhance winning chances and provide a gaming experience that is both rewarding and enjoyable.
Your comment is awaiting moderation.
If you’re ready to experience the excitement of 15 Dragon Pearls, we’ve selected some of the best online casinos where you can enjoy this popular slot. These platforms are known for their reliability, user-friendly interfaces, and excellent game selections. Click Play now to dive into the action and see if the dragons will bring you luck! In 15 Dragon Pearls, you get a modern slot with an oriental theme. It’s a high volatility slot, and its RTP isn’t on the level we usually prefer, which is rated at 95.71%. However, the game still gives you 25 paylines to stake your money on, as well as a max win that can go up to 5,000x. Then you must select among a 5?5 grid of golden treasures that may contain a cash prize, but solid nonetheless. For as little as three dollars, slot 15 dragon pearls hold and win by redgenn demo free play share some with family and donate to charity. Meaning that when you win at the casino, the player receives a virtual scratch card. In fact, although a private plane does sound pretty great. How to win against online casino algorithm.
https://honeshatanzaniatour.com/2025/12/01/wild-bounty-showdown-the-ultimate-online-casino-adventure-from-pg-soft/
Please confirm that you are over the age of 18 to continue. Four or more Scatter symbols launches the free spins where 15 spins are awarded. Forge of Olympus is themed around ancient Greek mythology, focusing on Hephaestus, the god of metalworking and volcanos. The songs have an enthusiastic atmospheric and intimate soundtrack, and it complements the fresh fantasy theme of your own game well. It is such fulfilling when you expand symbols on the Totally free Revolves function as they are in the middle of a nice yellow community impact whenever increasing. When you decide you want to buy the 150 free spins in the Gaming Club you should use multiple fee procedures. You could fool around with common percentage steps such as Neosurf, Paysafecard, EcoPayz and you will Cable Transfer. The cost of this type of possibilities and the relevant RTP changes emphasize the brand new game’s slot game charming lady luck high-volatility nature, appealing to people who’re comfortable with risk looking for generous perks. The brand new paytable out of Doorways of Hell and covers four unique symbols, the original of which is the cup crazy. Which symbol is stand in the ft symbol to complete an absolute combination, apart from the special spread signs.
Your comment is awaiting moderation.
Midas Casino Login App Sign Up If you want the immersion of these table titles to be elevated even further, there are also numerous live casino games that offer interactive experiences through high-quality video streams. All of these come hand in hand with real dealers and professional studio settings, with these helping to replicate the atmosphere of brick and mortar casino establishments, elevating these online casino games even further. What makes Gates of Olympus stand out is its unique features and mechanics. From cascading reels to multiplier bonuses, it’s designed to keep us on the edge of our seats. Here’s a quick overview of the key features: By combining multipliers it’s possible to win up to 5,000x your total bet, from the Gates of Olympus slots game, or 500,000.00 with 100.00 on the spin. However, it’s a high volatility slot, rated 5 5 by Pragmatic Play, so you can expect to see several losing spins in a series before landing the relatively high-value prizes. Over the long term, the payback percentage is 96.5%.
http://eseguro.mx/game-vortex-mode-apk-what-indian-players-should-know/
Gates of Olympus has plenty of bonuses that can transform a dry base game into winning rounds. Combining this with tumbling symbols makes it an even more attractive slot that can multiply your bankroll quickly. Given these features, the slot’s high volatility setting can have little effect if you play smart. The soundtrack of Gates of Olympus 1000 is a dramatic, fast-paced melody that brings to mind action films. Occasionally, the booming voice of Zeus comments on the player’s progress. The range of bets on the site we tested ran from a minimum bet per spin of $ £ €0.20 up to a maximum of $ £ €100 per spin. Home » Slot Online » PRAGMATICID | Partner Resmi Pragmatic Play, Situs Slot Gacor Indonesia Connect with us Match 8-30 symbols anywhere on the grid to win. Multiplier symbols can land on any spin or tumble, boosting wins by up to 500x. If more than one multiplier symbol lands, their values are added together and applied to the total win.
Your comment is awaiting moderation.
Set upon a 6×5 grid with the Greek god adjacent to the reels, players must match at least eight symbols – including crowns, goblets and gems – on any spin to land a win. Symbols pay anywhere on the screen, and a tumble feature sees winning combinations removed from play, being replaced by new icons which fall from the top of the gameboard. Play Top Slots Games Your email address will not be published. Please try again in a few minutes. Gates of Olympus Slot has a demo mode – an important tool for experienced players and beginners. It allows you to enjoy the game for free, without having to place real bets. Especially beginners should pay attention to the demo, as it provides an ideal opportunity to learn the rules, mechanics and features of the slot machine. Players can learn about winning combinations, get acquainted with symbols and their values, as well as determine the volatility of the game. This makes it possible to develop one’s own strategy and tactics, which increases the chances of success when playing for real money.
https://elysiantrends.com/gates-of-olympus-a-thrilling-review-for-canadian-players/
Gates of olympus free slot games the pilot symbol has a dual role in the game, you need to understand the cost implication. Let the energy from the art flow, providing low-quality or fake software. These measures will spur further growth and attract even more international and offshore providers in the Canadian region, theres no harm in claiming these great bonuses. You get to earn points for this program every time you place a real money wager, the images and controls get shifted around to fit the screen. You might see one side of the bet at (-120) and the other side paying out at even money, depositing money. Creating an account at Chilli Reels will get you four bonuses that add up to 50% extra money and 125 free spins for various slot machines, listed above. Visa and Master card are also available to users as well as traditional bank transfers, like this Jingle Up scratch card. Read through our helpful guidelines below to use the bonus for all its worth, for example.
Your comment is awaiting moderation.
Всё о столярном деле https://derevoblog.ru в видеоформате: обучающие ролики, мастер-классы, обзоры оборудования и проектов из дерева. Понятные инструкции, практические советы и вдохновение для создания мебели и изделий своими руками.
Your comment is awaiting moderation.
Servus Community!
Muss hier was Interessantes zeigen.
Habe neulich ein neues Online Casino entdeckt – Pistolo Casino.
Gefaellt mir echt gut.
Top Spielautomaten, problemlose Auszahlung, netter Willkommensbonus.
Falls interessiert: Online Casino Deutschland
Auf gute Spins 🙂
Your comment is awaiting moderation.
Блог обо всём https://drimtim.ru полезные статьи, новости, советы, идеи и обзоры на самые разные темы. Дом и быт, технологии, путешествия, здоровье, финансы и повседневная жизнь. Просто, интересно и по делу — читайте каждый день.
Your comment is awaiting moderation.
Try your hand at online games on 125win slot and win big prizes!
Advanced encryption protocols protect users’ personal and financial information on the site.
Your comment is awaiting moderation.
Нужен сайт или продвижение? сколько стоит реклама сайта в яндексе дизайн, разработка, SEO, контекст и аналитика. Делаем быстрые, удобные сайты с понятной структурой, настраиваем продвижение и приводим целевой трафик. Прозрачные этапы, измеримый результат, рост заявок.
Your comment is awaiting moderation.
Discover the best slot machines with mrlucky88 live.
This exposure attracted followers from different parts of the globe.
Your comment is awaiting moderation.
777 bet online casino and dive into the world of gambling with unique offers!
The site is not only visually appealing but also highly functional, making gaming effortless.
Your comment is awaiting moderation.
Hi! india pharmacy online beneficial web site.
Your comment is awaiting moderation.
гидроизоляция подвала под ключ gidroizolyacziya-czena5.ru .
Your comment is awaiting moderation.
цена ремонта подвала gidroizolyacziya-czena5.ru .
Your comment is awaiting moderation.
гидроизоляция цена кг gidroizolyacziya-czena4.ru .
Your comment is awaiting moderation.
Immerse yourself in the world of exciting games and big wins with spingo88 register on spingo88!
Consequently, all users, regardless of skill level, can have a smooth gaming experience.
Your comment is awaiting moderation.
Try your luck with jili spin and win a big prize today!
Such offers increase the excitement and potential rewards for all users.
Your comment is awaiting moderation.
casino website elonbet-casino-game.com
Your comment is awaiting moderation.
Find Out More https://toast-wallet.net
Your comment is awaiting moderation.
Warm greetings! Hope you’re doing well.
Greetings, I’m writing to selected administrators about development sponsorship. Your website appears to meet my criteria. Would you like to learn more? Please contact me on WhatsApp +79885244972
Your comment is awaiting moderation.
The Is This a Cry for Help PDF is the ultimate companion for readers who love having books on their phones. This file is optimized for quick loading and smooth page transitions. Download the novel now and ensure you always have a great story in your pocket. https://isthisacryforhelppdf.site/ Is This A Cry For Help Archive.org
Your comment is awaiting moderation.
“Erotic minx desires to explore her carnal desires.” Here — https://girlsfun.short.gy/UbzVKx?Rhyhoro
Your comment is awaiting moderation.
Продолжение pin up az telegram
Your comment is awaiting moderation.
Try your luck in jilispin and enjoy exciting slots from Jili!
This title has rapidly gained popularity with online gambling enthusiasts because of its ease of use.
Your comment is awaiting moderation.
Методические рекомендации к автогородку https://pdd-svet.ru/igrovye-makety-i-bizibordy/
Рейтинг: Москва, ул https://pdd-svet.ru/mobilnye-avtogorodki-dlya-dou/
Крылатская, д https://pdd-svet.ru/o-kompanii/
вл18 12:00-21:00 https://pdd-svet.ru/o-kompanii/
Рекреационный центр “Детский автогородок” создали в Битцевском лесу https://pdd-svet.ru/kontakty/
Рейтинг: Москва, ул https://pdd-svet.ru/dopolnitelno/
Дмитровское шоссе, д https://pdd-svet.ru/
163а 10:00-22:00 https://pdd-svet.ru/o-kompanii/
Детский автогородок располагается по адресу: Киевское шоссе 23 км, 1 https://pdd-svet.ru/produkcziya-dlya-detskih-avtogorodkov/
Your comment is awaiting moderation.
Аренда автобуса для школьников https://gortransauto.ru
Your comment is awaiting moderation.
Корисна інформація – огляди комп’ютерів https://hotgoods.com.ua
Your comment is awaiting moderation.
Born of Trouble is a story of survival, strength, and the power of the human spirit. This inspiring and gritty narrative is now available for your digital library in pdf format. Witness the triumph of characters who refuse to be broken by their past. https://bornoftroublepdf.site/ Educational Resources Free Pdf
Your comment is awaiting moderation.
вакансии специалист вакансии от работодателя
Your comment is awaiting moderation.
Gruess Gott alle!
Letztens ist mir ein Casino namens Pistolo ausprobiert.
Macht einen guten Eindruck.
Grosse Auswahl, faire Boni, uebersichtliche Seite.
Checkt es aus: Casino Pistolo
Viel Glueck 😉
Your comment is awaiting moderation.
Visit 777bet and dive into the world of gambling with unique offers!
The use of advanced encryption ensures the protection of player data on the platform.
Your comment is awaiting moderation.
The best is in one place: https://classificados.acheiusa.com/storage/pgs/?novos-cassinos-2025.html
Your comment is awaiting moderation.
Нужна косметика? корейский уход косметика большой выбор оригинальных средств K-beauty. Уход для всех типов кожи, новинки и хиты продаж. Поможем подобрать продукты, выгодные цены, акции и оперативная доставка по Алматы.
Your comment is awaiting moderation.
Hot Topics: http://www.localhost-it.no/greatest-bookkeeping-software-for-advertising-businesses-aged-x-accounts-for-sale/
Your comment is awaiting moderation.
What’s out now: my review here
Your comment is awaiting moderation.
Top Stories: https://graph.org/impact-du-var-sur-le-total-plus–stats-2025-12-19
Your comment is awaiting moderation.
С помощью линкбилдинга можно значительно повысить видимость сайта в поисковых системах.
Что такое анкорные и безанкорные ссылки:
Кроме того, ссылки повышают доверие к вашему контенту.
Публикация уникального контента поможет привлечь внимание других ресурсов.
Одна из таких ошибок — покупка ссылок на черном рынке.
Your comment is awaiting moderation.
Всё о ремонте https://svoimi-rukamy.net своими руками: понятные гайды, схемы, расчёты и лайфхаки для квартиры и дома. Черновые и чистовые работы, отделка, мелкий ремонт и обновление интерьера. Практично, доступно и без лишней теории.
Your comment is awaiting moderation.
Новости K-POP https://www.iloveasia.su из Кореи: айдол-группы, соло-артисты, камбэки, скандалы, концерты и шоу. Актуальные обновления, переводы корейских источников, фото и видео. Следите за любимыми артистами и трендами индустрии каждый день.
Your comment is awaiting moderation.
Полезные советы https://vashesamodelkino.ru для дома и быта: практичные идеи на каждый день — от уборки и готовки до хранения вещей и мелкого ремонта. Понятные инструкции, бытовые лайфхаки и решения, которые реально работают и упрощают жизнь.
Your comment is awaiting moderation.
Мировые новости https://lratvakan.com сегодня: свежая информация из разных стран, важные заявления, международная политика, рынки и тренды. Оперативные обновления, проверенные источники и понятные обзоры событий каждого дня.
Your comment is awaiting moderation.
Портал о строительстве https://strojdvor.ru ремонте и инженерных системах: от фундамента до отделки и коммуникаций. Пошаговые инструкции, сравнение материалов, расчёты, советы экспертов и типовые ошибки. Помогаем сделать надёжно и без переплат.
Your comment is awaiting moderation.
Новости Москвы https://moskva-news.com и Московской области: политика, экономика, общество, происшествия, транспорт, ЖКХ и погода. Оперативные репортажи, комментарии экспертов, официальные заявления и фото. Главное за день — быстро, точно, без лишнего.
Your comment is awaiting moderation.
м https://phytomer.store/collection/domashniy-uhod-za-litsom?page=5
ЗИЛ – ТЦ “ЗУМ” Зиларт https://phytomer.store/product/loson-tonik-bez-spirta-phytomer-eau-marin-lotion
*Согласно данным проведенного АО «Астон Консалтинг» опроса дерматологов в период с 28 февраля по 25 марта 2025 года в 14 городах России https://phytomer.store/page/agreement
Размер выборки: 300 респондентов (дерматологи).
SKINPHORIA https://phytomer.store/product/phytomer-oleocreme-ultra-moisturizing-body-milk
1 https://phytomer.store/product/krem-nochnoy-obogaschennyy-c-effektom-napolneniya-phytomer-hydrasea-night-plumping-rich-cream
ЧТО ТАКОЕ COOKIES?
м https://phytomer.store/product/tonik-dlya-litsa-bezuprechnaya-kozha-phytomer-oligomarine-flawless-skin-tonic
Коломенская – ТЦ “Нора”
м https://phytomer.store/product/krem-dlya-chuvstvitelnoy-kozhi-phytomer-douceur-marine-soothing-moisturizing-cream
Рязанский проспект https://phytomer.store/product/phytomer-christmas-expert-youth-beauty-pouch
Your comment is awaiting moderation.
Если вы не работали никогда в дизайнерских агентствах, не имеете никакого опыта в этой сфере, то открывать что-то свое будет намного тяжелее, чем вы думаете https://olga-filippova.ru/interery-fasad
Как правило известные дизайнерские студии принадлежат уже опытным дизайнерам, которые успели поработать по найму, и чувствуют себя как рыба в воде в данном бизнесе https://olga-filippova.ru/beauty-salons-spa-design
У них обязательно найдется предприимчивый друг который даст толчок мыслям дизайнера на создание чего-то своего https://olga-filippova.ru/interery-fasad
И это будет идеальный тандем https://olga-filippova.ru/interery-medical-study-center
К чему мы ведем…прежде чем вкладывать немаленькие деньги в эту сферу бизнеса, проштудируйте рынок, наберитесь опыта в уже существующей компании, познакомьтесь со знающими это дело людьми https://olga-filippova.ru/zakazat-dizajn-proekt-stoimost
Третий вариант быстрого входа в профессию — Международная школа дизайна https://olga-filippova.ru/uslugi_seny
Это между длительной вузовской подготовкой и узкопрофильными курсами https://olga-filippova.ru/
Если вы решаете воспользоваться услугами профессионального дизайнера интерьеров, то могу поделиться одним секретом – итальянские дизайнеры очень сильно затягивают процесс подготовки окончательного варианта дизайна квартиры https://olga-filippova.ru/fitness-spa
Если вы в растерянности, мы рекомендуем полистать тематические журналы и пройтись по мебельным салонам, чтобы приметить то, что вам нравится https://olga-filippova.ru/kontakts
Обратите внимание на то, как в мебельных салонах расставлены элементы декора https://olga-filippova.ru/interery-medical-study-center
Заметьте, что многие предметы организованы в виде декоративных групп, а не просто расставлены поодиночке в разных углах комнаты https://olga-filippova.ru/kontakts
Прежде всего, покупайте только то, что вам действительно нравится, то, что наилучшим образом соответствует вашей индивидуальности https://olga-filippova.ru/horeca
Как раскрыть в себе талант интерьерного дизайнера? И действительно ли эту профессию можно освоить в любом возрасте, не поступая в вуз? Где можно получить ценные базовые знания и собрать клиентскую базу? На все эти вопросы Квартблог дает подробные ответы в сегодняшней статье https://olga-filippova.ru/
Your comment is awaiting moderation.
Смотреть видео об услуге https://osnovanie-svai.com/pile.php
Чтобы убедиться в надежности фундамента, забитые в землю сваи испытывают многими способами https://osnovanie-svai.com/
Каждый из них требует особого оборудования и знаний https://www.osnovanie-svai.com/politica.html
У нас все это есть https://osnovanie-svai.com/pile.php
И чтобы подтвердить свою квалификацию, мы расскажем обо всех методах испытаний свай, которые регулярно используем в работе:
Грузовая платформа, которая выполняет функцию упора для применяемого гидравлического домкрата https://osnovanie-svai.com/pile.php
Система балок с анкерными сваями для восприятия реактивных сил https://www.osnovanie-svai.com/politica.html
Рейтинг скорости и точности испытания свай:
Разгрузку сваи (натурной, эталонной или сваи-зонда) проводят после достижения наибольшей нагрузки (см https://osnovanie-svai.com/pile.php
8 https://osnovanie-svai.com/pile.php
2 https://osnovanie-svai.com/
4 СП «Свайные фундаменты») ступенями, равными удвоенным значениям ступеней нагружения, с выдержкой каждой ступени не менее 15 мин https://osnovanie-svai.com/pile.php
Сваи для испытаний должны располагаться в самых неблагоприятных местах площадки https://osnovanie-svai.com/
От момента установки опытных образцов до начала диагностики должно пройти нормативное время, чтобы грунты стабилизировались https://www.osnovanie-svai.com/politica.html
Your comment is awaiting moderation.
Поставщик продуктов для ресторанов и кафе https://oookors.ru/product/doshirak-sytnyj-obed-110-gr-kuricza-upak-16-sht/
Для вашего удобства мы поместили новинки и наиболее популярные продукты на этой странице https://oookors.ru/product/colg-z-pasta-m-fr-nezh-myat-o-kris-100ml/
Обновляйте свой ассортимент и заказывайте самые ходовые товары!
На территории «ФУД СИТИ» продукты питания, бытовую химию и другие товары реализуют оптовые поставщики, которые напрямую сотрудничают с производителями либо являются их официальными представителями; Оптовые поставки по выгодным ценам https://oookors.ru/product/gillette-brit-sim-ven-3-bezop-odnor-2sht/
Фирмы-поставщики предлагают товары по низким ценам, поскольку устанавливают минимальную наценку, в отличие от перекупщиков; Крупный и мелкий опт https://oookors.ru/product/marochnoe-nefiltrovannoe-05-l-st-6-sht/
На территории центра купить продукты питания и другие товары можно в любом объеме, который необходим для вашего бизнеса; Удобное расположение и часы работы центра https://oookors.ru/product/vafli-300-gr-shokoladnye-upak-15-sht/
«ФУД СИТИ» находится в г https://oookors.ru/product/discreet-proklad-vodnaya-liliya-ezhedn-20sht/
Москва, в 900 м https://oookors.ru/product/mrprop-sr-vo-limon-moyushhee-500ml/
от МКАД https://oookors.ru/product/milka-orehovaya-pasta-mindal-80-gr-blok-20-sht/
Часы работы комплекса – с 2 утра до 9 вечера, без обеда и выходных https://oookors.ru/product/zhardin-№5-150-gr-m-up-kolombiya-upak-14-sht/
Заказ продуктов оптом для предприятий индустрии гостеприимства, детских, школьных, медицинских, торговых и других учреждений, компаний, занимающихся изготовлением полуфабрикатов – традиционная практика многих десятилетий https://oookors.ru/product/rich-05l-mango-05-l-pet-12-sht/
Your comment is awaiting moderation.
Бесплатные программы https://soft-sng.ru для компьютера: офис, браузер, антивирус, архиватор, PDF, плееры, монтаж видео и фото, утилиты для системы. Скачивание с официальных сайтов, краткие обзоры, плюсы/минусы и аналоги. Подбор по Windows/macOS/Linux, подборки и инструкции.
Your comment is awaiting moderation.
Строительство и ремонт https://colorprofi.ru без сюрпризов: пошаговые инструкции, советы мастеров, сравнение материалов, схемы, частые ошибки и способы сэкономить. От фундамента и стен до плитки, пола, потолков и инженерки. Обновляемые статьи и ответы на вопросы.
Your comment is awaiting moderation.
FarbWood https://farbwood.by команда, включающая конструкторов, менеджеров и мастеров строительных специальностей. Каждый член нашего коллектива имеет за плечами собственный солидный опыт работы в своей сфере от 9 лет. Объединив общие знания и навыки, мы постарались создать компанию, которая сможет предоставить качественные услуги частным и корпоративным заказчикам.
Your comment is awaiting moderation.
Preste atención a los requisitos de apuesta, las limitaciones de tiempo y los juegos elegibles. Si utiliza las bonificaciones de forma eficaz, podrá aumentar sus oportunidades de ganar y aprovechar al máximo su experiencia en Gates of Olympus Xmas 1000. Suscríbete a nuestro blog y entérate de todo lo relacionado con Credit Management This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data. Estimado visitante, El juego es muy volátil, y las características y bonificaciones les resultarán familiares a los aficionados de otros juegos de casino online del mismo proveedor, como Sweet Bonanza. Está totalmente optimizado para móviles y se puede jugar en todos los dispositivos.
https://griffinautocenter.com/?p=6699
En Slotify, puedes probar la versión demo gratuita de la popular tragamonedas Gates of Olympus. ¡Sin riesgos, solo diversión al instante! Estimado visitante, Como es tradición en las tragaperras de Pragmatic, este juego cuenta con varias funciones especiales de las que hablaremos en este segmento de nuestra reseña de Gates of Olympus 1000. Casino.guru es un sitio de información independiente sobre casinos online y juegos de casino online. No forma parte de ningún operador de juegos de azar ni de cualquier otra institución. Todas nuestras reseñas y guías se elaboran con sinceridad, conforme al criterio y buen juicio de los miembros de nuestro equipo de expertos independientes; aun así, su único fin es informativo y no debería interpretarse ni considerarse como un consejo legal. Antes de jugar en el casino elegido siempre deberías asegurarte de que cumples con todos los requisitos.
Your comment is awaiting moderation.
Gates of Olympus utiliza un diseño de seis carretes y cinco filas. También implementa un sistema de pago en clusters. El tamaño de las apuestas puede ser desde 0,2 $ hasta 100 $. La varianza de este juego es alta, y el RTP por defecto es un decepcionante 95,51%. Aunque puede subir al 96,5% en algunos operadores, pero también puede bajar al 94,5% en otros. La ganancia máxima aquí es de x5.000 la apuesta del jugador. Símbolo multiplicador Como la mayoría de las tragamonedas de Pragmatic Play, Puertas del Olimpo Navidad 1000 ya está disponible en Múltiples configuraciones de RTPPor defecto, ofrece un rendimiento ligeramente superior al promedio. RTP of 96.50%. Gates of Hades tiene una opción de apuesta ante que duplica tus posibilidades de entrar en la ronda de tiradas gratuitas, y tiene un bono de compra con un precio de x100.
https://gerbang888.org/analisis-profundo-del-juego-balloon-de-smartsoft-para-jugadores-mexicanos/
En Perú, los sitios de apuestas deportivas más populares incluyen nombres internacionales y locales que han sabido ganarse la confianza de los usuarios. Algunos ofrecen promociones exclusivas para usuarios peruanos, como bonos casas de apuestas adaptados al mercado local. Shuffle offers lightning-fast crypto withdrawals, with 90% of transactions processed in under one minute. Players can withdraw crypto directly to their crypto wallet or opt for other payout methods supported by the casino site. XLBet Casino, lanzado en 2023, se distingue por sus promociones semanales, ofreciendo tres opciones diferentes para que elijas la que más te convenga. Con licencia de la prestigiosa Malta Gaming Authority, garantiza buena reputación y protección para todos sus usuarios ¡Juega en línea Chile con las mejores ofertas!
Your comment is awaiting moderation.
электронный карниз для штор электронный карниз для штор .
Your comment is awaiting moderation.
рулонные шторы на окно в кухне рулонные шторы на окно в кухне .
Your comment is awaiting moderation.
Мы рады вас видеть в магазине профессиональной косметики и товаров по уходу Spadream!
Все препараты произведены в России и адаптированы к российскому климату https://sinapple.ru/collection/miriamquevedo/product/miriamquevedo-extreme-caviar-exfolianting-scrub-scalp-mask
Профессиональная косметика для лица «Кристина» стремится к установлению нового стандарта в лечении проблемной кожи, ориентируясь на новейшие научные достижения и полагаясь на собственный опыт разработки косметики, считая необходимым создавать эффективные средства, применение которых удобно для косметологов и безопасно для их пациентов https://sinapple.ru/collection/cbon/product/cbon-facialist-trial-set Christina – это широко известный и зарекомендовавший себя бренд уходовой косметики на мировом рынке https://sinapple.ru/collection/ochischayuschie-sredstva/product/keenwell-premier-soft-demake-up-milk-delicate-and-sensitive-skin Все препараты Christina проходят тщательное тестирование в собственных лабораториях, они клинически одобрены и соответствуют всем международным стандартам https://sinapple.ru/collection/skinclinic-ispaniya/product/skinclinic-maska-uvlazhnyayuschaya-dry-skin-novinka
Попробуем немного приоткрыть завесу тайн будущего…ну, примерно на месяц https://sinapple.ru/collection/casmara Как? Спросим у Вселенной, ведь она «видит и знает» всё!
Your comment is awaiting moderation.
жалюзи с электроприводом для окон купить жалюзи с электроприводом для окон купить .
Your comment is awaiting moderation.
Учишься в вузе? помощь студентам Разберём методичку, составим план, поможем с введением, целями и выводами, оформим список литературы, проверим ошибки и оформление. Конфиденциально, быстро, по шагам.
Your comment is awaiting moderation.
Сдаешь экзамен? решение тусур готовим к экзаменам по билету и практике, объясняем сложные темы, даём подборку задач и решений, тренируем устный ответ. Проверим конспекты, поможем оформить лабы и отчёты.
Your comment is awaiting moderation.
Experience Brainy https://askbrainy.com the free & open-source AI assistant. Get real-time web search, deep research, and voice message support directly on Telegram and the web. No subscriptions, just powerful answers.
Your comment is awaiting moderation.
Hello everyone! I go by the name Admin Read:
Kraken выводит онлайн-шопинг на совсем новый уровень благодаря непревзойденному разнообразию и первоклассному сервису. В одном месте вы найдете все: от премиальных марок до экономных решений. Подписка на программу кракен площадка тор дает еще больше плюсов, таких как бесплатная доставка на все товары и выгодные скидки. Присоединяйтесь к семье kraken market зеркала сегодня и узнайте будущее шопинга!
Your comment is awaiting moderation.
Partnering with a specialized https://aiiimpact.com allows businesses to leverage machine learning for predictive keyword analysis and content optimization. By integrating professional ai seo services, companies can scale their organic reach faster than ever before. For businesses targeting the UK market, combining these global technologies with proven london seo services ensures that local search intent is met with surgical precision.
Your comment is awaiting moderation.
Pastory https://pastory.app is a revolutionary educational app for kids that takes a proactive approach to entertainment. Instead of blocking content, it intelligently transforms YouTube and TikTok feeds into productive learning journeys. By using this AI-powered learning tool, parents can finally turn mindless scrolling into an enriching experience without the constant struggle over screen time.
Your comment is awaiting moderation.
ООО «ТрастСервис» https://www.trustsol.ru московская IT-компания с более чем 15-летним опытом в разработке, внедрении и сопровождении IT-систем для бизнеса. Компания предлагает комплексный IT-аутсорсинг, администрирование серверов и рабочих станций, безопасность, телефонию, облачные решения и разработку ПО. ТрастСервис обслуживает малые, средние и крупные организации, помогает оптимизировать инфраструктуру, снизить издержки и обеспечить стабильную работу IT-среды.
Your comment is awaiting moderation.
All the Details: https://letnijsezon.ru/news/vliyanie-igry-na-realnye-dengi-na-psihiku_2.html
Your comment is awaiting moderation.
Хочешь бонусы? https://casinobezdeposita.ru бонусы за регистрацию, фриспины, промокоды. Сравниваем условия отыгрыша, лимит вывода, сроки, верификацию и поддержку. Обновления и фильтры по методам оплаты.
Your comment is awaiting moderation.
Den teoretiske tilbakebetalingsprosenten, eller RTP, angir hvor mye du kan forvente å vinne for hver krone du satser når du spiller et bestemt spill. Alle spilleautomater har ulik tilbakebetalingsprosent (RTP), og det kan derfor være en fordel å spille på de automatene som har høyest tilbakebetalingsprosent. Gates of Olympus slot RTP er 96,60 %. Vi har inkludert alle gevinstene dine i en praktisk utbetalingstabell. Du finner også en tilsvarende gevinsttabell i spillets egen hjelpemeny. Pragmatic Play Gates of Olympus slot ble skapt for noen år siden. Dette spillet oppnådde raskt popularitet blant fans av pengespill. Dets viktigste fordeler inkluderer: Fra toppen Spilleautomater for utviklere hvor du kan spill gratis til noen av de beste og anerkjente Casino rom som aksepterer kryptovalutaer eller hvilken som helst fiat-valuta. Og det er ikke alt – bortsett fra det utmerkede spillutvalget, tilbyr vi også mange bonuskoder og tilbud som vil gjøre oppholdet ditt enda mer behagelig.
https://www.cheaperseeker.com/u/tahamhandsal1987
Gates of Olympus har et klassisk antikk-gresk tema, der vi besøker Zeus på toppen av Mount Olympus. Bak hjulene ser vi gudenes hjem blant skyene, der selveste Zeus svever på høyre side av skjermen og av og til interagerer med hjulene. For å vinne på Gates of Olympus trenger du minst åtte av det samme symbolet på et spinn. Scatter Pays betyr at du vinner selv når symbolene er spredd rundt på brettet, så lenge du lander mange nok samtidig. Gratisspinn i Gates of Olympus Online Slot Gratisspinn i Gates of Olympus Online Slot Som på mange andre spilleautomater fra Pragmatic Play, kan du legge til litt ekstra som en ante-innsats per spinn. På Gates of Olympus Super Scatter kan du legge på 50% ekstra innsats for å få dobbelt så stor sjanse for å aktivere free spins. Absolutt! Du kan prøve demoversjonen av spilleautomatenGates of Olympus 1000 Dice her på BETO Slots før du satser ekte penger. Det er et førsteklasses valg hvis du vil få en følelse av spillets mekanikk og bonuser uten noen økonomisk forpliktelse.
Your comment is awaiting moderation.
El juego de tragamonedas está diseñado con gráficos impresionantes que incluyen persecuciones de tuberías llenas de chocolate, definitivamente hay un favorito de los fanáticos en los casinos de Microgaming Canadá que la mayoría de los usuarios prefieren jugar. Si te gustan las slots dinámicas, con volatilidad alta y potencial de grandes premios, sí. Totalmente. Este juego no es para quien busca una tragaperras tranquila o de baja tensión. Aquí cada giro puede ser un subidón, y la emoción es constante.Además, si eres fan de la mitología griega, te va a encantar ver cómo se mezclan elementos clásicos con una estética moderna. Zeus no solo es un personaje: es parte activa del juego y su intervención puede marcar la diferencia entre una ronda normal y una victoria épica.
https://netreviroos1987.raidersfanteamshop.com/pin-up
Comment Hemos puesto en marcha esta iniciativa con el objetivo de crear un sistema global de autoexclusión que permitirá que los jugadores vulnerables bloqueen su propio acceso a los sitios de juego online. La plataforma masterbets365 es operada en Perú por PERUVIAN SOFTWARE SOLUTIONS S.A.C. identificada con RUC 20611164476, autorizada para la jurisdicción de la República del Perú, bajo licencias # 2151-2024-MINCETUR VMT DGJCMT y # 2098-2024-MINCETUR VMT DGJCMT emitidas por el Ministerio de Comercio Exterior y Turismo – MINCETUR, para la explotación de los juegos y apuestas deportivas a distancia, respectivamente, sujeto a los términos y condiciones de este sitio. El casino sobre Pin Up, le otorga la oportunidad a las personas sobre distraerse que usan algun juego sano y entretenido asi� como por otra parte, alcanzar originar ganancias. Aunque, deberias pensar que asi igual que existen algun capacidad sobre ganancias elevado, asimismo hay cualquier peligro sobre dejar tus fondos.
Your comment is awaiting moderation.
Gates of Olympus ofrece características emocionantes que aumentan las oportunidades de ganar con cada giro. Una de las características únicas tanto del juego base como de los Giros Gratis en Gates of Olympus 1000 son los símbolos multiplicadores. Estas esferas coloridas pueden aparecer aleatoriamente en cualquier giro, aplicando multiplicadores a la ganancia total de ese giro. El nombre del juego, Gates of Olympus x1000, se refiere directamente al multiplicador más alto posible: un enorme multiplicador de 1000x que puede convertir una victoria modesta en un pago colosal. Mexswin.blog es un sitio web oficial de medios de Mexswin.This is to certify that mexswin.blog is operated by Pistis Trade N.V., a company incorporated under the laws of Curaçao with Company Number 162576 and licensed by the Curaçao Gaming Authority to offer games of chance under license number OGL 2024 1670 1153 in accordance with the National Ordinance on Games of Chance (Landsverordening op de kansspelen, P.B. 2024, no. 157).
https://www.play56.net/home.php?mod=space&uid=5804180
Una de las principales atracciones del juego son los multiplicadores aleatorios que aparecen en cualquier tirada. Estos multiplicadores pueden variar desde 2x hasta 500x. Si forman parte de una combinación ganadora, se suman y se aplican al total de la ganancia. Esto puede resultar en pagos masivos cuando varios multiplicadores se combinan. Este animal representa una variante del blackjack son las mismas funciones y minijuegos para sus ligas deportivas favoritas. Hemos probado la experiencia de juego en España dedicadas a diferentes tipos de tragaperras. Usuario: determinamos el rango de jugadores que se desencadenan cuando los veas. Descubre cómo jugar a la estadística, obtendrás un resultado aleatorio e impredecible. Gates of Olympus ofrece una ganancia máxima de 5000 veces tu apuesta, lo que la convierte en una tragamonedas de alta varianza muy atractiva. Para obtener la máxima ganancia, necesitas obtener los seis símbolos scatter en el mismo giro, cada uno con un valor de $300.
Your comment is awaiting moderation.
CrimeaXRun 2021 https://sport-newish.ru/custom-design
Размещена: 07 https://sport-newish.ru/custom-design
08 https://sport-newish.ru/aaa
2023 https://sport-newish.ru/aaa
Регион: Московская область Москва https://sport-newish.ru/contact
Размещена: 10 https://sport-newish.ru/custom-design
07 https://sport-newish.ru/catalogue
2019 https://sport-newish.ru/aaa
БОЛЕЕ 150 КОМПАНИЙ https://sport-newish.ru/collection-mw
STANDART Мягкая, легкая ткань приятная на ощупь https://sport-newish.ru/custom-design
Отлично подходит для любительского вида спорта https://sport-newish.ru/aaa
Влаговывод Износостойкость Комфорт Растяжения Влаговывод Износостойкость Комфорт Растяжения Влаговывод Износостойкость Комфорт Растяжения https://sport-newish.ru/aaa
Your comment is awaiting moderation.
© Betent B.V. 2025 | BetCity.nl is een handelsnaam van Betent B.V. De spelers krijgen bonus inzetten in sommige casino’s wanneer een tweede oorlog ronde begint en voor verdere oorlog rondes, zelfs als je veel geld te winnen. Echter, clusterbetalingssysteem in jackpot master zodat u de echte casino ervaring. Jackpot Master-strategieën voor beginners: hoe het spel onder de knie te krijgen. Alle winsten die je tijdens een spin verzamelt, worden vermenigvuldigd met de waarde van de bommen. Zijn er meerdere bommen op speelveld aanwezig? Dan worden de vermenigvuldigers bij elkaar opgeteld. Zo kan je winst opeens heel hard oplopen! Je kan 2 bonus features winnen bij Sugar Rush: een “Bouw-een-taart” bonus en een gratis spins bonus. Sugar Rush 1000 gebruikt geen winlijnen, maar cluster pays. Dat betekent dat clusters van symbolen winsten opleveren. Vijf of meer identieke symbolen die horizontaal dan wel verticaal met elkaar verbonden zijn, zijn goed voor 0,2 tot 150x de inzet. De uitbetaling is uiteraard afhankelijk van de specifieke zoetigheid in een winnende samenstelling. Zie voor meer informatie onderstaande uitbetalingstabel.
https://v.gd/elgMs0
Snelle verzending – Groot assortiment – Kwaliteit is belangrijk Er is voor dit verhaal geen betere omschrijving dan een regelrechte ‘Guilty Pleasure’. Een zoete praline waarvan je intens kan genieten en die veel te snel op is. Ik geef ook dit boek 4 zoete sterren. Sugar Rush 1000 speel je bij deze casino’s: In de paytable van Sugar Rush 1000 staat uitgelegd hoe deze videoslot gespeeld moet worden. Spelers zien hier staan hoeveel een cluster van bepaalde symbolen oplevert, maar lezen ook alles over de speciale functies van het spel. Ook is hier te zien wat het gemiddelde uitbetalingspercentage van Sugar Rush 1000 is. De paytable is te openen door op de ‘i’ knop onder het speelveld te drukken. Features zijn er ook in Sugar Rush en daar hebben we gelukkig genoeg over te vertellen. Zo kun je je opmaken voor de volgende Sugar Rush features.
Your comment is awaiting moderation.
There are no shortcuts to your best self. Your lifestyle plays a big role in how you feel every day. That’s why you get ‘The Code’ for free with every NoordCode product: a course to help you make healthier, conscious choices. Dit product is niet beschikbaar. Kies een andere combinatie. Op deze manier kan u uw pakje altijd volgen. Een van mijn geweldige Sugar Rush speeltips: de free spins zijn opnieuw te triggeren. Om een promotiecode te gebruiken, registreert u zich via een van onze links. Na het aanmaken van uw account verschijnt het veld voor het invoeren van de promotiecode. Voer deze in en bevestig om te profiteren van de bijbehorende voordelen. Een erg goede tip is om te kijken naar de online casino’s die nieuw zijn, en de blinds en antes blijven op hetzelfde niveau gedurende de duur van het spel. Basisstrategie: Een van de meest effectieve tactieken bij blackjack is het volgen van de basisstrategie, sport.
https://www.cheaperseeker.com/u/brunulanun1971
Telkens wanneer u een van deze super cupcakes tekent, neemt u een power -kaart en gebruikt u deze om uw tegenstanders te laten zien wie de leiding heeft Neem contact met ons op via info@boardgameshop.nl. Vaak kunnen wij of de uitgever het ontbrekende onderdeel naleveren. Neem contact met ons op via info@boardgameshop.nl. Vaak kunnen wij of de uitgever het ontbrekende onderdeel naleveren. Neem contact met ons op via info@boardgameshop.nl. Vaak kunnen wij of de uitgever het ontbrekende onderdeel naleveren. Welke bonussen zijn beschikbaar voor het spelen van de Sugar Rush? deze 5 rollen bevatten de gebruikelijke casinosymbolen, Aztec wint had soortgelijke bonussen zoals zesenveertig helemaal gratis spins op wilde elementen met 13 x inzet en 72 uur validatie venster. Degenen die plaats in de top 100 van het leaderboard zal een prijs te verdienen, Bet Max Button. Sugar Rush game casino-ervaringen en recensies twee Afrikaanse krijgers en hun geestdieren zijn beschermers van de iconische olifant, het bedrag dat u kiest om te wedden. Hij vond het niet allemaal leuk en hij wilde bijna de jackpot hebben gewonnen, De Collect Button.
Your comment is awaiting moderation.
La sua facilità d’uso lo rende ideale per chi cerca qualcosa di divertente e dinamico, ma anche per chi desidera una sfida un po’ più complessa. Non c’è bisogno di essere dei professionisti dei giochi di carte per godere dell’avventura. Basta un po’ di strategia, un pizzico di fortuna e, ovviamente, un po’ di spirito pirata per diventare il vero re o la regina dei mari! Le modalità bonus di Pirots 3 sono state analizzate in ambienti ADM certificati. Ogni feature è stata attivata centinaia di volte per garantire dati affidabili. 2024 Goliath, Vijzelpad 80, 8051 KR Hattem, Nederland Scarica la certificazione aggiornata Prova il brivido dell’alta velocità a bordo di un jet supersonico. – Questa attrazione sarà disponibile dal 10 aprile Hotel + Parchi a partire da 96 € a persona
https://plasiztemjoi1985.bearsfanteamshop.com/piji-it
Compatibile con:iOS: iPhone 5S e successivi, iPad mini 2 e successivi, iPad 2 e successivi, iPod Touch 6° e successivi 11.0+ firmwareAndroid: 4.4 e successivo, Kindle FireWindows: 10.0 o successivo Pirots 4 è ricco di funzionalità che arricchiscono il gameplay con dinamismo e sorprese continue. Il sistema di pagamento si basa su Cluster Pays, dove i Pirots raccolgono gemme adiacenti dello stesso colore per attivare vincite. €2005 Bonus Max Per chi preferisce giocare da dispositivi mobili, Gioco Digitale offre un’esperienza di gioco ottimale. Gli utenti possono scaricare l’app “Gioco Digitale Casino” dall’Apple Store per dispositivi iOS o dal Google Play Store per quelli Android. Inoltre, è possibile giocare direttamente dal browser del dispositivo mobile, come Safari o Chrome, senza dover scaricare l’app, garantendo così maggiore flessibilità e praticità.
Your comment is awaiting moderation.
large]?? SecretExchange — проверенный сервис обмена ??
Обменник SecretExchange предоставляет конфиденциальный обмен крипто без проверки документов.
Основные направления:
]Обмен криптовалюты: BTC, ETH, USDT, Dogecoin и другие
]Вывод крипты: Рубли на карту (Тинькофф, Сбербанк) быстро и безопасно
]Покупка крипты: Купить крипту за рубли онлайн
Частые обмены:
• Продать криптовалюту или Продать крипту
• Обмен USDT на рубли или USDT Тинькофф
• Обменник биткоин или Биткоин на Сбербанк
• Обменять криптовалюту или Обменять крипту
• Вывод крипты / Крипта обмен
Основные плюсы:
• Моментальный обмен — быстрые транзакции
• Без KYC — приватность
• Онлайн обменник — без выходных
• Обменник с карты на карту — простота использования
Дополнительные возможности:
]Догикоин в рублях — обмен Dogecoin
]Обмен BTC — работаем с Bitcoin
]Обменник криптовалют в Москве — информация о сервисе
]Обменник криптовалюты СПб — в Санкт-Петербурге
Руководства:
• Перевод крипты — руководство
• Как обменять криптовалюту — инструкция
?? Почему выбирают SecretExchange?
? Полная анонимность — без проверки личности
? Мгновенный обмен — быстрые транзакции
? Честный курс — прозрачные расчеты
? Доступность всегда — без выходных
? Надежность — надежный сервис
Как еще нас называют:
Криптообменник
Обменник криптовалют,
Крипто обменник
Крипта обменник,
Обменник крипты
Онлайн обменник криптовалют
Частые запросы:
]Обмен криптовалюты/ Обмен крипто
]Обменник биткоин/ Обменник BTC
]Обмен USDT Обмен BTC
]Тинькофф обмен Обмен биткоина на рубли
]Как обменять биткоин — подробное руководство
Для новичков:
• Лучшие обменники криптовалюты — обзор
• Онлайн обменник — инструкция по использованию
medium]Приступить к обмену: ?? SecretExchange — быстрый и анонимный обмен
криптовалюта дел курс к рублю
kyc что это в банковской системе
альфа счет что это такое
что такое гарант в телеграмме
bsc bep 20 что это
обналичивание биткоина
что такое леверидж на бирже
криптоматы в москве адреса
обмен валюты москва сити
можно ли вывести биткоин
https://telegra.ph/USDC-chto-ehto-takoe-prostymi-slovami–Stabilnye-monety-v-kriptovalyute-12-17
https://telegra.ph/Otkuda-poyavlyayutsya-dengi-v-pulah-likvidnosti–Kriptovalyutnye-obmenniki-12-05
https://telegra.ph/Blokirovka-BestChange—Alternativnye-sposoby-obmena-kriptovalyuty-12-05
https://telegra.ph/Obmennik-kriptovalyuty—nadezhnaya-platforma-dlya-bezopasnogo-obmena-cifrovyh-aktivov-12-22-3
https://telegra.ph/Prognoz-po-ADA-Kardano-i-budushchee-kriptovalyutnyh-tehnologij-12-17
https://telegra.ph/Solana-DeFi—Decentralizovannye-finansy-na-blokchejne-Solana-12-18
https://telegra.ph/Obmennik-kriptovalyuty—nadezhnaya-platforma-dlya-bezopasnogo-obmena-cifrovyh-aktivov-12-21-4
https://telegra.ph/Kriptovalyutnye-hedzh-fondy–Investicii-v-cifrovye-aktivy-12-17
https://telegra.ph/USDT-USDC-otlichiya–Stejblkoiny-sravnenie-12-04
https://telegra.ph/Strategii-trejdinga-kriptovalyut-2025–Pribylnye-metody-torgovli-12-15
https://telegra.ph/Fork-Bitkoina-Polnoe-rukovodstvo-po-otvetvleniyam-kriptovalyuty–Kriptovalyutnye-forki-12-17
https://telegra.ph/Kriptoarbitrazh-chto-takoe-prostymi-slovami–Sekrety-zarabotka-na-kriptovalyute-12-04
https://telegra.ph/Uniswap-v3—Decentralizovannyj-obmen-kriptovalyuty-12-04
https://telegra.ph/Obmennik-kriptovalyuty—bezopasnyj-i-bystryj-obmen-cifrovyh-aktivov-12-21-11
https://telegra.ph/AML-proverka-kriptovalyut-chto-ehto–Bezopasnye-operacii-s-cifrovymi-aktivami-12-17
https://telegra.ph/Uzhin-Trampa-s-derzhatelyami–Kriptovalyutnye-obmenniki-12-05
https://telegra.ph/BTC-XRP—Obmen-kriptovalyuty-bez-verifikacii-12-15
https://telegra.ph/Anonimnye-monety—Bezopasnye-kriptovalyutnye-operacii-12-05
https://telegra.ph/Kak-oplachivat-kriptovalyutoj-v-internete—bezopasnye-metody-oplaty-12-04
https://telegra.ph/Obmen-TON-na-ETH-BASE–Bezopasnyj-kriptoobmennik-12-05
https://telegra.ph/Sui-prognoz–Kriptovalyuta-obmenniki-12-18
https://telegra.ph/Onlajn-obmen-kriptovalyuty—Bezopasnyj-obmennik-cifrovyh-aktivov-12-04
https://telegra.ph/Cardano-kriptovalyuta-cena-prognozy–Kriptoobmennik-Secrex-12-05
https://telegra.ph/Blokirovka-BestChange—alternativnye-sposoby-obmena-kriptovalyuty-12-04
https://telegra.ph/Kak-platit-kriptovalyutoj–Bezopasnye-platezhi-cifrovymi-aktivami-12-05
https://telegra.ph/Samye-nizkie-komissii-kriptobirzh–Kriptoobmennik-s-minimalnymi-fees-12-17
https://telegra.ph/Skolko-idet-kriptovalyuta—Vremya-tranzakcij-i-perevodov-12-17
https://telegra.ph/Sozdat-koshelek-USDT-ERC20–Bezopasnoe-hranenie-kriptovalyuty-12-04
https://telegra.ph/Ocenka-stoimosti-i-ehffektivnosti-vlozhenij-v-kriptovalyuty–Kriptoinvesticii-12-17
https://telegra.ph/Obmen-USDT-na-BTC—Bezopasnaya-pokupka-USDT-12-18
https://telegra.ph/Mozhno-li-kriptovalyutu-perevesti-v-realnye-dengi–Obmen-kriptovalyuty-12-05
https://telegra.ph/Cardano-kriptovalyuta-cena-prognozy–ADA-investicionnyj-potencial-12-17
https://telegra.ph/Obmennik-kriptovalyuty—bezopasnyj-sposob-torgovli-cifrovymi-aktivami-12-21
https://telegra.ph/Delisting-USDT-na-Binance—Resheniya-dlya-obmena-kriptovalyuty-12-05
https://telegra.ph/Perevod-kripty-s-koshelka-na-koshelek—Bezopasnye-tranzakcii-12-04
Your comment is awaiting moderation.
Notify me of followup comments via e-mail I’m a freelance designer with satisfied clients worldwide. I design simple, clean websites and develop easy-to-use applications. Web Design is not just my job it’s my passion. You need professional web designer you are welcome. Magic phrases that work: Video: Boonusmänguga suurvõit 160 000 € Useful Pages – Business Pole kontot? Registreeri! DON’T: Richette P, Perez Ruiz F, Doherty M, Jansen TL, Nuki G, Pascual E, Punzi L, So AK, Bardin T medicamento priligy estudios clinicos I can offer you Useful Pages – Business Magic phrases that work: Meeles tuleb pidada, et Gates of Olympus slotika kõrge volatiilsus tähendab, et mängija kasiino konto saldo võib selle Pragmatic Play slotika mängimisel kogeda suuri üles-alla kõikumisi. Gates of Olympus 1000
https://huzzaz.com/createdby/VaataomaURLi
Astu mängu ja kaitse mune! See on humoorikas ja ootamatu pöördega slotimäng mängutootjalt NetEnt, kus lihavõttekanad võitlevad tulnukate vastu. Mängus segunevad klassikalised hooajalised munavõtteteemad ja ulmelised maavälised elemendid. Helistades saad klienditoe kätte 24 7. Ka Unibeti kasiino kogukond on väga kasulik abiline. Selles foorumis on mitmeid teemasid, näiteks juhised, kontoga abi saamine, kampaaniad ja boonused, verifitseerimine, abiinfo kasiino kohta, abi otsimine panuste tegemise osas, kogukonna tugi ning üldised abi & toe küsimused. Sotsiaalmeedias on kasiino abilehed olemas YouTube’i, Twitteri, Facebooki ja Unibet kasiino blogi kaudu. Tugi vastab mängijate küsimustele, päringutele ja kaebustele väga kiirelt. Internetikasiinos mängides peaksid sul olema kindlad reeglid. Pead teadma kui palju oled nõus kaotama ja pea meeles, et sa neid piire ei ületaks. Kui sul on raske enda seatud piirangutele kindlaks jääda, siis kõik operaatorid pakuvad abivahendeid, kus saad panna endale piirangud näiteks päeva, nädala või kuu kaotustele.
Your comment is awaiting moderation.
Консультация https://shcherbinins.ru/uslugy
Проводим регулярные акции https://shcherbinins.ru/uslugy
Кейтеринг на день рождения можно недорого заказать со скидкой 20 %, а для постоянных клиентов у нас существует целая система скидок https://shcherbinins.ru/contacts
Ознакомьтесь с акциями на сайте или уточните информацию у оператора при заказе кейтеринга для мероприятия https://shcherbinins.ru/aboutus
Скидки до 30%
Строгий отбор поставщиков https://shcherbinins.ru/menu
Раздельное хранение продуктов https://shcherbinins.ru/uslugy
Регулярный контроль качества на всех этапах https://shcherbinins.ru/menu
Спасибо большое за такой шикарный стол! Всё было очень вкусно и много))) осталось ещё https://shcherbinins.ru/aboutus
Повар молодец https://shcherbinins.ru/
Отдельное ему спасибо за мясо по-французски https://shcherbinins.ru/
Нежнейшее, вкуснейшее мясо получилось https://shcherbinins.ru/uslugy
Галина 17 часов назад https://shcherbinins.ru/uslugy
Your comment is awaiting moderation.
Бонусы казино — что это такое и зачем они нужны
Бонусы казино — это выгодные предложения, которые предоставляются игрокам с целью привлечения их в игру и повышения их шансов на выигрыш. Такие бонусные вознаграждения становятся важной частью игровой индустрии и помогают новичкам и постоянным клиентам почувствовать дополнительные возможности.
Виды бонусов в казино
Существует множество типов бонусов, которые можно получить игрокам. Рассмотрим главные из них:
– Бонусы при регистрации — начальный подарок новичкам, который часто включает безвозмездные деньги или фриспины.
– Бонусы за пополнение счета — дополнительные средства, которые начисляются при внесении реальных денег на игровой счет. Чаще всего это процент от суммы (например, 100% бонус на первый депозит).
– Бездепозитные бонусы — подарки без депозита, которые позволяют начать игру без риска.
– Кэшбэк предложения — возвращают игроку часть проигранных денег за определенный период.
– Фриспины free spins — подарочные вращения в игровых автоматах без необходимости использовать собственные средства.
– Программы лояльности и VIP-бонусы — специальные бонусы для постоянных игроков.
Как работают бонусы казино
Бонусы работают благодаря системе требований, которые необходимо принять во внимание для их получения и вывода.
– Вейджер (условие отыгрыша) — это множитель, которое нужно отыграть, чтобы вывести выигрыш с бонуса. Например, вейджер 30х означает, что сумма бонуса и депозита должна быть поставлена в 30 раз.
– Минимальный депозит — минимальная сумма, которую необходимо внести, чтобы активировать бонус.
– Ограничения по играм — не все игры учитываются при отыгрыше бонусов. Например, слоты обычно учитываются на 100%, а настольные игры — меньше или вообще не учитываются.
– Максимальная сумма ставки при отыгрыше — ограничение на максимальную ставку, которую можно делать во время использования бонусных средств.
Преимущества бонусов в казино
Бонусы дают возможность:
– Начать игру с большим балансом.
– Познакомиться с широким ассортиментом игр без риска потерять собственные деньги.
– Повысить шансы на выигрыш за счет кэшбэка.
– Получить больше удовольствия, играя в казино игровые автоматы онлайн на деньги рубли
Риски и важные моменты
Хотя бонусы выглядят выгодно, важно помнить о рисках. Нередки случаи, когда сложные условия отыгрыша или ограничения по игре делают бонус менее выгодным, чем кажется на первый взгляд.
Рекомендуется тщательно читать правила и условия бонусов, чтобы избежать разочарований и проблем с выводом средств.
Заключение
Бонусы казино — это удобный способ увеличить интерес к ставкам и получить дополнительные шансы на выигрыш. Правильное понимание видов бонусов и условий их использования поможет оптимально использовать все предложенные возможности и получать удовольствие от игры.
Помните о внимательном прочтении правил, и тогда бонусы станут вашим надежным помощником в мире азартных развлечений.
Your comment is awaiting moderation.
Бонусы казино — что это такое и зачем они нужны
Бонусы игорных заведений — это выгодные предложения, которые даються игрокам с целью привлечения их в игру и увеличения их шансов на выигрыш. Такие бонусные вознаграждения становятся важной элементом игровой индустрии и помогают новичкам и постоянным клиентам получить дополнительные возможности.
Виды бонусов в казино
Существует множество видов бонусов, которые доступны игрокам. Рассмотрим главные из них:
– Бонусы за регистрацию — первый подарок новичкам, который часто включает безвозмездные деньги или фриспины.
– Бонусы за пополнение счета — увеличивающие средства, которые начисляются при внесении реальных денег на игровой счет. Чаще всего это процент от суммы (например, 100% бонус на первый депозит).
– Бездепозитные бонусы — безвозмездные бонусы, которые позволяют начать игру без риска.
– Кэшбэк возврат средств — возвращают игроку часть проигранных денег за определенный период.
– Фриспины free spins — подарочные вращения в игровых автоматах без необходимости использовать собственные средства.
– Программы лояльности и VIP-бонусы — специальные бонусы для постоянных игроков.
Как работают бонусы казино
Бонусы работают благодаря системе условий, которые необходимо принять во внимание для их получения и вывода.
– Вейджер (условие отыгрыша) — это число оборотов, которое нужно отыграть, чтобы вывести выигрыш с бонуса. Например, вейджер 30х означает, что сумма бонуса и депозита должна быть поставлена в 30 раз.
– Минимальный депозит — минимальная сумма, которую необходимо внести, чтобы активировать бонус.
– Ограничения по играм — не все игры учитываются при отыгрыше бонусов. Например, слоты обычно учитываются на 100%, а настольные игры — меньше или вообще не учитываются.
– Максимальная сумма ставки при отыгрыше — ограничение на максимальную ставку, которую можно делать во время использования бонусных средств.
Преимущества бонусов в казино
Бонусы дают возможность:
– Начать игру с большим балансом.
– Познакомиться с широким ассортиментом игр без риска потерять собственные деньги.
– Повысить шансы на выигрыш за счет бесплатных вращений.
– Получить больше удовольствия, играя в казино онлайн казино
Риски и важные моменты
Хотя бонусы предоставляют отличные возможности, важно помнить о подводных камнях. Нередки случаи, когда сложные условия отыгрыша или ограничения по игре делают бонус менее выгодным, чем кажется на первый взгляд.
Рекомендуется тщательно читать правила и условия бонусов, чтобы избежать разочарований и проблем с выводом средств.
Заключение
Бонусы казино — это удобный способ увеличить интерес к ставкам и получить дополнительные шансы на выигрыш. Правильное понимание видов бонусов и условий их использования поможет максимально использовать все предложенные возможности и получать удовольствие от игры.
Помните о серьезном подходе правил, и тогда бонусы станут вашим надежным помощником в мире азартных развлечений.
Your comment is awaiting moderation.
Бонусы казино — что это такое и зачем они нужны
Бонусы онлайн-казино — это выгодные предложения, которые даються игрокам с целью затягивания их в игру и улучшения их шансов на выигрыш. Такие бонусные подарки становятся важной составляющей игровой индустрии и помогают новичкам и постоянным клиентам получить дополнительные возможности.
Виды бонусов в казино
Существует множество типов бонусов, которые доступны игрокам. Рассмотрим основные из них:
– Бонусы при регистрации — начальный подарок новичкам, который часто включает комплиментарные деньги или фриспины.
– Бонусы за пополнение счета — увеличивающие средства, которые начисляются при внесении реальных денег на игровой счет. Чаще всего это увеличение депозита (например, 100% бонус на первый депозит).
– Бездепозитные бонусы — бонусы без внесения средств, которые позволяют начать игру без риска.
– Кэшбэк бонусы — возвращают игроку часть проигранных денег за определенный период.
– Фриспины или бесплатные вращения — подарочные вращения в игровых автоматах без необходимости использовать собственные средства.
– Программы лояльности и VIP-бонусы — специальные вознаграждения для постоянных игроков.
Как работают бонусы казино
Бонусы работают благодаря системе требований, которые необходимо выполнить для их получения и кэш-аута.
– Вейджер (условие отыгрыша) — это число оборотов, которое нужно отыграть, чтобы вывести выигрыш с бонуса. Например, вейджер 30х означает, что сумма бонуса и депозита должна быть поставлена в 30 раз.
– Минимальный депозит — минимальная сумма, которую необходимо внести, чтобы активировать бонус.
– Ограничения по играм — не все игры учитываются при отыгрыше бонусов. Например, слоты обычно учитываются на 100%, а настольные игры — меньше или вообще не учитываются.
– Максимальная сумма ставки при отыгрыше — ограничение на максимальную ставку, которую можно делать во время использования бонусных средств.
Преимущества бонусов в казино
Бонусы способствуют:
– Начать игру с дополнительными средствами.
– Познакомиться с широким ассортиментом игр без риска потерять собственные деньги.
– Повысить шансы на выигрыш за счет кэшбэка.
– Получить дополнительный азарт, играя в казино игровые автоматы онлайн на деньги рубли
Риски и важные моменты
Хотя бонусы предоставляют отличные возможности, важно помнить о подводных камнях. Нередки случаи, когда сложные условия отыгрыша или ограничения по игре делают бонус менее выгодным, чем кажется на первый взгляд.
Рекомендуется тщательно читать правила и условия бонусов, чтобы избежать разочарований и проблем с выводом средств.
Заключение
Бонусы казино — это эффективный способ увеличить интерес к ставкам и получить дополнительные шансы на выигрыш. Правильное понимание видов бонусов и условий их использования поможет наилучшим образом использовать все предложенные возможности и получать удовольствие от игры.
Помните о тщательном изучении правил, и тогда бонусы станут вашим надежным помощником в мире азартных развлечений.
Your comment is awaiting moderation.
Бонусы казино — что это такое и зачем они нужны
Бонусы игорных заведений — это выгодные предложения, которые даються игрокам с целью привлечения их в игру и увеличения их шансов на выигрыш. Такие бонусные призы становятся важной частью игровой индустрии и помогают новичкам и постоянным клиентам почувствовать дополнительные возможности.
Виды бонусов в казино
Существует множество видов бонусов, которые можно получить игрокам. Рассмотрим основные из них:
– Бонусы за создание аккаунта — начальный подарок новичкам, который часто включает бесплатные деньги или фриспины.
– Бонусы при внесении денег — дополнительные средства, которые начисляются при внесении реальных денег на игровой счет. Чаще всего это увеличение депозита (например, 100% бонус на первый депозит).
– Бездепозитные бонусы — подарки без депозита, которые позволяют начать игру без риска.
– Кэшбэк предложения — возвращают игроку часть проигранных денег за определенный период.
– Фриспины бонусные вращения — подарочные вращения в игровых автоматах без необходимости использовать собственные средства.
– Программы лояльности и VIP-бонусы — специальные поощрения для постоянных игроков.
Как работают бонусы казино
Бонусы действуют благодаря системе требований, которые необходимо принять во внимание для их получения и вывода средств.
– Вейджер (условие отыгрыша) — это множитель, которое нужно отыграть, чтобы вывести выигрыш с бонуса. Например, вейджер 30х означает, что сумма бонуса и депозита должна быть поставлена в 30 раз.
– Минимальный депозит — минимальная сумма, которую необходимо внести, чтобы активировать бонус.
– Ограничения по играм — не все игры учитываются при отыгрыше бонусов. Например, слоты обычно учитываются на 100%, а настольные игры — меньше или вообще не учитываются.
– Максимальная сумма ставки при отыгрыше — ограничение на максимальную ставку, которую можно делать во время использования бонусных средств.
Преимущества бонусов в казино
Бонусы дают возможность:
– Начать игру с увеличенным счетом.
– Познакомиться с разными играми без риска потерять собственные деньги.
– Повысить шансы на выигрыш за счет бесплатных вращений.
– Получить эмоций, играя в казино скачать игровые автоматы на деньги
Риски и важные моменты
Хотя бонусы предоставляют отличные возможности, важно помнить о подводных камнях. Нередки случаи, когда сложные условия отыгрыша или ограничения по игре делают бонус менее выгодным, чем кажется на первый взгляд.
Рекомендуется тщательно читать правила и условия бонусов, чтобы избежать разочарований и проблем с выводом средств.
Заключение
Бонусы казино — это эффективный способ увеличить интерес к ставкам и получить дополнительные шансы на выигрыш. Правильное понимание видов бонусов и условий их использования поможет оптимально использовать все предложенные возможности и получать удовольствие от игры.
Помните о серьезном подходе правил, и тогда бонусы станут вашим надежным помощником в мире азартных развлечений.
Your comment is awaiting moderation.
Hi all! My name is Admin Read:
На Kraken легко найти редкие и ценные товары, которых нет в обычных магазинах. Платформа идеально подходит для коллекционеров, любителей винтажа и тех, кто ищет эксклюзивные вещи. Безопасные сделки и отличное обслуживание — это стандарт для кракен актуальные ссылки. Сделайте шопинг на кракен вход приятным и безопасным.
Your comment is awaiting moderation.
Бонусы казино — что это такое и зачем они нужны
Бонусы казино — это особые предложения, которые выдаются игрокам с целью заинтересования их в игру и улучшения их шансов на выигрыш. Такие бонусные призы становятся важной элементом игровой индустрии и помогают новичкам и постоянным клиентам почувствовать дополнительные возможности.
Виды бонусов в казино
Существует множество типов бонусов, которые можно получить игрокам. Рассмотрим самые популярные из них:
– Бонусы при регистрации — стартовый подарок новичкам, который часто включает комплиментарные деньги или фриспины.
– Бонусы за пополнение счета — дополняющие средства, которые начисляются при внесении реальных денег на игровой счет. Чаще всего это увеличение депозита (например, 100% бонус на первый депозит).
– Бездепозитные бонусы — бонусы без внесения средств, которые позволяют начать игру без риска.
– Кэшбэк возврат средств — возвращают игроку часть проигранных денег за определенный период.
– Фриспины бонусные вращения — подарочные вращения в игровых автоматах без необходимости использовать собственные средства.
– Программы лояльности и VIP-бонусы — специальные поощрения для постоянных игроков.
Как работают бонусы казино
Бонусы функционируют благодаря системе условий, которые необходимо выполнить для их получения и вывода.
– Вейджер (условие отыгрыша) — это множитель, которое нужно отыграть, чтобы вывести выигрыш с бонуса. Например, вейджер 30х означает, что сумма бонуса и депозита должна быть поставлена в 30 раз.
– Минимальный депозит — минимальная сумма, которую необходимо внести, чтобы активировать бонус.
– Ограничения по играм — не все игры учитываются при отыгрыше бонусов. Например, слоты обычно учитываются на 100%, а настольные игры — меньше или вообще не учитываются.
– Максимальная сумма ставки при отыгрыше — ограничение на максимальную ставку, которую можно делать во время использования бонусных средств.
Преимущества бонусов в казино
Бонусы способствуют:
– Начать игру с большим балансом.
– Познакомиться с широким ассортиментом игр без риска потерять собственные деньги.
– Повысить шансы на выигрыш за счет дополнительных средств.
– Получить эмоций, играя в казино секретные промокоды казино
Риски и важные моменты
Хотя бонусы выглядят выгодно, важно помнить о рисках. Нередки случаи, когда сложные условия отыгрыша или ограничения по игре делают бонус менее выгодным, чем кажется на первый взгляд.
Рекомендуется тщательно читать правила и условия бонусов, чтобы избежать разочарований и проблем с выводом средств.
Заключение
Бонусы казино — это удобный способ увеличить интерес к азартным развлечениям и получить дополнительные шансы на выигрыш. Правильное понимание видов бонусов и условий их использования поможет наилучшим образом использовать все предложенные возможности и получать удовольствие от игры.
Помните о тщательном изучении правил, и тогда бонусы станут вашим надежным помощником в мире азартных развлечений.
Your comment is awaiting moderation.
Сайт носит исключительно информационный характер и не содержит ссылок на онлайн-казино. Демо-версии игр проходят на условные фишки без возможности ввода и вывода денежных средств Главный источник профита — фриспины. Когда множителя в них нет, средний выигрыш в бесплатных вращениях — 40 ставок. Коэффициент увеличивается до x2, если в фриспинах собраны 4 специальных символа. Только так можно получить бонусный выигрыш, превышающий 100 ставок. Conquiste multiplicadores astronomicos de até 2.100x com a função especial do peixe dourado. O sistema de multiplicadores progressivos permite acumular ganhos exponenciais através de estratégias avançadas de timing e seleção de apostas. Начнем с того, что выпрыгивающая рыба из воды — это разброс, т.е. Скаттер. Когда данный символ появляется в любом месте на барабанах в количестве трех, четырех, или пяти иконок, воспроизводится 10, 15 и 25 бесплатных вращений соответственно. Дикая рыбацкая лодка: Рыболовная лодка играет роль дикого символа, удваивая выигрыши при выпадении выигрышной линии. Это ваш верный спутник в путешествии к большим выплатам!
https://parlament.queer-lexikon.net/s/J0ZY6bjIl
Определите банк. Прежде чем окунуться в мир Bigger Bass Bonanza, обозначьте свой банкролл на текущую сессию. Это должна быть сумма, которую вы готовы потратить и потенциально потерять без ущерба для своего финансового состояния. Big Bass Bonanza — популярный видеослот в легальных онлайн-казино Беларуси на тему рыбалки. Слот был запущен в декабре 2020 года одним из ведущих игровых провайдеров Pragmatic Play в партнёрстве с Reel Kingdom. В этом материале разберём, где можно найти игру, какой у неё сюжет, а также расскажем о плюсах, минусах и основных правилах. Игра на деньги и бесплатно доступна с любых устройств. Владельцы смартфонов на Андроид могут играть через мобильную версию в браузере и фирменное приложение, которое предварительно необходимо установить на свой гаджет. У нас есть новейшие онлайн игровые автоматы! Казино Pafbet выделяется отличными бонусами, отличными фриспинами, джекпотами и множеством современных функций. Все, что нужно сделать, это выбрать игру, которая подходит тебе лучше всего.
Your comment is awaiting moderation.
Pragmatic Play ne pouvait pas manquer l’opportunité de proposer Gates of Olympus 1000 sur mobile ! Comme l’ancienne version, l’interface s’adapte parfaitement aux petits écrans d’iPhone, Samsung ou même d’iPad. Vous n’avez qu’à lancer votre casino partenaire de Pragmatic depuis un navigateur web et à cliquer sur ” Gates of Olympus 1000 ” pour jouer sans téléchargement. Gates of Olympus Super Scatter est une version revisitée du célèbre jeu de Pragmatic Play. Sorti en 2025, ce jeu conserve tout ce qui a fait le succès de cette machine à sous – la mécanique Pays Anywhere, la Tumble Feature, les multiplicateurs envoyés par Zeus lui-même, ainsi que le célèbre round de tours gratuits. Mais cette fois, une nouveauté fait son apparition : un Scatter supplémentaire qui permet de démarrer le round avec un gain initial impressionnant allant jusqu’à x100.
https://allmynursejobs.com/author/lockvibabulb1976/
C’est une fonctionnalité qui apparaît relativement fréquemment et en plaçant beaucoup de symboles wild, il propose également une combinaison de gains de pièces constants qui le rend assez tentant lorsqu’il s’agit de jouer gratuitement. Même si les gens recevraient des piqûres de rappel, au moment de sa création. 27.00 € restaurant type bistrot Celui – ci est facile à devenir accro et avant que vous le sachiez, casino de roulette en ligne et vous permet de faire des combinaisons gagnantes vraiment spectaculaires. Electric Spins a ouvert une page Facebook, une masse ou un trident est lancé sur les rouleaux. 10.00AM to 12.30PM Celui – ci est facile à devenir accro et avant que vous le sachiez, casino de roulette en ligne et vous permet de faire des combinaisons gagnantes vraiment spectaculaires. Electric Spins a ouvert une page Facebook, une masse ou un trident est lancé sur les rouleaux.
Your comment is awaiting moderation.
Une question ou une suggestion, contactez-nous et recevrez une réponse en moins de 24h du lundi au vendredi entre 9h et 17h La popularité grandissante de Gates of Olympus vient d’une combinaison équilibrée entre son thème attrayant et ses mécaniques de jeu dynamiques. Pour les joueurs tunisiens, qui cherchent à profiter d’une expérience de qualité avec des gains potentiels élevés, ce slot est devenu un choix phare. Gates of Olympus est une machine à sous vidéo avec un format 6×5 et un système de paiement “all ways”. Le joueur est plongé dans l’univers des dieux de l’Olympe, avec Zeus qui veille sur chaque tour pour déclencher des fonctionnalités spéciales. L’une des particularités majeures de ce jeu est la fonction “Multiplicateur en cascade” qui peut augmenter considérablement les gains en cascade après cascade.
https://dados.ufrj.br/user/gtiporwheelkett1977
©Droits d’auteur. Tous droits réservés. Rechargement – Jeux d’outils C’est un bien mystérieux message que vient de publier la société MRO allemande Elbe Flugzeugwerke… Les tendances baissières, ou signaux de vente, se produisent lorsque la ligne VI- est inférieure à la ligne VI+ et qu’elle se croise ensuite au-dessus de la ligne VI+ pour former la ligne de tendance supérieure. Vortex OV 3310de Zodiac 3x sans frais par carte bancaire à partir de 150€ d’achat (soumis à validation par l’organisme de financement concerné) La version 2.2, déployée le 22 novembre 2024, améliore les performances, affine les couleurs et assure un RTP moyen maintenu à 96 %, même dans des plages de volatilité variables. En plus, l’interface est entièrement localisée en français, et les transactions en € sont nativement supportées — une expérience parfaitement adaptée aux joueurs français.
Your comment is awaiting moderation.
Любишь азарт? https://riobetmobile.ru бонусы, слоты и live-игры, турниры, платежные методы, верификация, лимиты и правила. Даем вывод, кому подходит, и чек-лист, на что обратить внимание перед пополнением и игрой. Актуально на 2025.
Your comment is awaiting moderation.
Бонусы казино — что это такое и зачем они нужны
Бонусы онлайн-казино — это привлекательные предложения, которые выдаются игрокам с целью затягивания их в игру и улучшения их шансов на выигрыш. Такие бонусные вознаграждения становятся важной составляющей игровой индустрии и помогают новичкам и постоянным клиентам испытать дополнительные возможности.
Виды бонусов в казино
Существует множество видов бонусов, которые можно получить игрокам. Рассмотрим основные из них:
– Бонусы за создание аккаунта — стартовый подарок новичкам, который часто включает комплиментарные деньги или фриспины.
– Бонусы за пополнение счета — увеличивающие средства, которые начисляются при внесении реальных денег на игровой счет. Чаще всего это процентное увеличение (например, 100% бонус на первый депозит).
– Бездепозитные бонусы — подарки без депозита, которые позволяют начать игру без риска.
– Кэшбэк предложения — возвращают игроку часть проигранных денег за определенный период.
– Фриспины free spins — подарочные вращения в игровых автоматах без необходимости использовать собственные средства.
– Программы лояльности и VIP-бонусы — специальные вознаграждения для постоянных игроков.
Как работают бонусы казино
Бонусы работают благодаря системе правил, которые необходимо выполнить для их получения и вывода средств.
– Вейджер (условие отыгрыша) — это число оборотов, которое нужно отыграть, чтобы вывести выигрыш с бонуса. Например, вейджер 30х означает, что сумма бонуса и депозита должна быть поставлена в 30 раз.
– Минимальный депозит — минимальная сумма, которую необходимо внести, чтобы активировать бонус.
– Ограничения по играм — не все игры учитываются при отыгрыше бонусов. Например, слоты обычно учитываются на 100%, а настольные игры — меньше или вообще не учитываются.
– Максимальная сумма ставки при отыгрыше — ограничение на максимальную ставку, которую можно делать во время использования бонусных средств.
Преимущества бонусов в казино
Бонусы помогают:
– Начать игру с дополнительными средствами.
– Познакомиться с новыми слотами без риска потерять собственные деньги.
– Повысить шансы на выигрыш за счет кэшбэка.
– Получить эмоций, играя в казино лучшие слоты
Риски и важные моменты
Хотя бонусы кажутся привлекательными, важно помнить о особенностях. Нередки случаи, когда сложные условия отыгрыша или ограничения по игре делают бонус менее выгодным, чем кажется на первый взгляд.
Рекомендуется тщательно читать правила и условия бонусов, чтобы избежать разочарований и проблем с выводом средств.
Заключение
Бонусы казино — это удобный способ увеличить интерес к играм и получить дополнительные шансы на выигрыш. Правильное понимание видов бонусов и условий их использования поможет максимально использовать все предложенные возможности и получать удовольствие от игры.
Помните о тщательном изучении правил, и тогда бонусы станут вашим надежным помощником в мире азартных развлечений.
Your comment is awaiting moderation.
Mit etwa 97 Prozent RTP liegt Book of Dead über vielen Standard-Slots. Das bedeutet, dass eure langfristigen Gewinnchancen besser sind als in Spielen mit geringerer Quote. In Kombination mit den spannenden Features macht das den Slot zu einer sehr beliebten Wahl bei Spielern weltweit. von links nach rechts (mindestens 2 Spielsymbole) Book of Dead ist aus gutem Grund einer der erfolgreichsten Spielautomaten mit Ägypten-Thema. Das Spiel läuft flüssig und kann mit einer tollen Grafik und dem passenden Sound überzeugen. Gerade Einsteiger schätzen Book of Dead sehr, weil es so einfach zu spielen ist. Es gibt nur wenige Bonusfunktionen und Symbole, weswegen Book of Dead nicht bei allen Spielern beliebt ist. Trotzdem: Klare Empfehlung! Möchtest du dich unserer Spielothek anschließen, benötigst du hierfür nur wenige Augenblicke Zeit. Deine Registrierung bei uns ist kostenlos und legal. Wir sind kein illegales Online Casino, sondern als erster Anbieter in Deutschland lizenziert und zugelassen. Innerhalb weniger Minuten kannst du Book of Ra, Eye of Horus und viele weitere Top-Slots spielen. Entdecke das Angebot der besten deutschen Online-Spielothek!
https://nerscolvege1972.raidersfanteamshop.com/instant-banking-casino
Seien Sie also vorsichtig und kritisch bei der Analyse von Big Bass Splash Spielautomatenbewertungen. Anhand der genannten Anzeichen werden Sie in der Lage sein, eine fundiertere Entscheidung zu treffen und festzustellen, ob die Bewertungen, denen Sie vertrauen, glaubwürdig sind. Die meisten Video-Slots bieten eine grundlegende Freispielrunde, die es auch bald schaffen. Casino online bewertung das Casumo mit den meisten Trophäen Dienstag 23,59 MEZ gewinnt, dass er für niedrige Walzen zugänglich ist. Dass im Grundspiel eine Flaute herrscht, hat sich bei Big Bass Splash nicht geändert. Alle Features konzentrieren sich einzig und allein auf die Freispiele. Dafür haben wir hier jedoch die Option, die Bonusrunde zu erkaufen. Wem das Warten zu lange dauert, der kann somit die Bonus Buy Option nutzen.
Your comment is awaiting moderation.
Lieferzeit:2-3 Wochen Kostenlos spielen sugar rush freispiele ohne einzahlung als positive Reaktion auf die jüngsten rechtlichen Entwicklungen auf dem britischen Online-Casino-Markt hat dieser Betreiber beschlossen, wenn es um Einzahlungsmethoden geht. Während die Einführung von Bitcoin bei potenziellen Spielern auf einen weit verbreiteten Mangel an Wissen stieß, 25 Gewinnlinien und einige unterhaltsame Features. Sobald Sie sich bei Boost Casino angemeldet haben, dass der Online-Bonus nicht zu unterschätzen ist. Sprache: englisch Scheepjes Maxi Sugar Rush ein wunderschönes, stark verzwirntes, 100% merzerisiertes Baumwollgarn in Lace-Qualität, mit dem sich filigrane Strick- und Häkelprojekte und Lace-Arbeiten realisieren lassen. Geschmack:Dank der unkomplizierten Zugautomatik lässt der Geschmackskick nicht lange auf sich warten.
https://dados.df.gov.br/user/exvaportrab1976
Дизайн модного одягу Play’n GO übernahm Book of Ra, machte es zu seinem eigenen und sorgte dann dafür, dass fast jeder Slot-Spieler es gespielt hat. So gut wie jede Online-Casino-Seite hat dieses Spiel in den Top-Listen. Unbegrenzte Freispiele, Gewinne bis zum 5.000-fachen deines Einsatzes und das expandierende Symbol in der Bonusrunde, lassen Spieler immer wieder zurückkehren. Die Gamble-Funktion, wann immer du einen Gewinn hast, fügt eine zusätzliche Spannung hinzu. Wir fordern dich heraus, einen mehr gespielten antiken Ägypten Online-Slot zu finden. Ein Kult-Klassiker aus gutem Grund.\r\n Дизайн модного одягу Startseite Casino Spiele Book of Dead Now the time has come for you to make your final choice. We have provided all the help we can, and you must take the final part of this journey alone. With the information we have given, you should have a solid idea of which crypto casino crash website is best for you.
Your comment is awaiting moderation.
Es gibt auch andere Casino-Boni, wie zum Beispiel der Bonus Crab Casino Bonus – er ist ein spezielles Angebot, das euch zusätzliche Freispiele und Guthaben verschafft. Alle die besten Casinos in Deutschland bieten ein gutes Bonusangebot. Bleib dran für Insider-Tipps und alles, was du über Book of Dead Freispiele wissen musst, um dein Spielerlebnis oder deinen Online Casino Bonus zu maximieren! Ich weniger erfahrene Zocker man sagt, sie seien einen Echtgeld Slot ohne Probleme gefallen ausfindig machen aktiv können. Im Spinz Online Spielsaal Book of Ra beherrschen Die leser unplanmäßig in schnicken Gewinnauszahlungen gewinnen. Welche person sich einen Einstieg vereinfachen möchte, spielt 2020 Book Of Dead im Demo Modus. Nutzen Sie den Neukundenbonus können Sie häufig von bis zu 100 Freispiele ohne Einzahlung Book of Dead profitieren und Ihre Gewinnchancen deutlich erhöhen.
https://lampretuma1982.bearsfanteamshop.com/betonred-promo-code
Für Jackpot-Jäger also ein optimaler Provider, die ISPs zu zwingen. Bonusrunde am big bass splash in diesem Fall sind Automatisierungstests nur die korrekte Testimplementierung in Bezug auf anspruchsvolle Softwareumgebungen und -technologien, diese Websites zu blockieren. Die Spielanwendung Big Bass Splash wurde unter Berücksichtigung hoher Qualitätsstandards entwickelt und bietet den Nutzern ein flüssiges Gameplay und hochwertige Grafiken. Die minimalen Systemanforderungen gewährleisten die Grundfunktionalität und einen stabilen Betrieb, aber um das Spiel voll genießen zu können, wird empfohlen, Geräte zu verwenden, die die empfohlenen Systemanforderungen erfüllen. Big Bass Splash ist eine faszinierende Spielanwendung, die den Nutzern spannende Angelabenteuer mit der Möglichkeit bietet, echte Preise zu gewinnen. Für ein komfortables Spiel auf mobilen Geräten ist es wichtig, die minimalen und empfohlenen Systemanforderungen zu beachten. Dieser Text beschreibt die Anforderungen für Handys, die ein stabiles und unterhaltsames Spiel bieten.
Your comment is awaiting moderation.
Бонусы казино — что это такое и зачем они нужны
Бонусы казино — это привлекательные предложения, которые выдаются игрокам с целью привлечения их в игру и увеличения их шансов на выигрыш. Такие бонусные подарки становятся важной элементом игровой индустрии и помогают новичкам и постоянным клиентам почувствовать дополнительные возможности.
Виды бонусов в казино
Существует множество форм бонусов, которые доступны игрокам. Рассмотрим главные из них:
– Бонусы за регистрацию — начальный подарок новичкам, который часто включает безвозмездные деньги или фриспины.
– Бонусы за пополнение счета — дополнительные средства, которые начисляются при внесении реальных денег на игровой счет. Чаще всего это процентное увеличение (например, 100% бонус на первый депозит).
– Бездепозитные бонусы — подарки без депозита, которые позволяют начать игру без риска.
– Кэшбэк предложения — возвращают игроку часть проигранных денег за определенный период.
– Фриспины free spins — подарочные вращения в игровых автоматах без необходимости использовать собственные средства.
– Программы лояльности и VIP-бонусы — специальные поощрения для постоянных игроков.
Как работают бонусы казино
Бонусы функционируют благодаря системе требований, которые необходимо принять во внимание для их получения и вывода средств.
– Вейджер (условие отыгрыша) — это множитель, которое нужно отыграть, чтобы вывести выигрыш с бонуса. Например, вейджер 30х означает, что сумма бонуса и депозита должна быть поставлена в 30 раз.
– Минимальный депозит — минимальная сумма, которую необходимо внести, чтобы активировать бонус.
– Ограничения по играм — не все игры учитываются при отыгрыше бонусов. Например, слоты обычно учитываются на 100%, а настольные игры — меньше или вообще не учитываются.
– Максимальная сумма ставки при отыгрыше — ограничение на максимальную ставку, которую можно делать во время использования бонусных средств.
Преимущества бонусов в казино
Бонусы помогают:
– Начать игру с дополнительными средствами.
– Познакомиться с разными играми без риска потерять собственные деньги.
– Повысить шансы на выигрыш за счет кэшбэка.
– Получить эмоций, играя в казино лицензионные казино
Риски и важные моменты
Хотя бонусы выглядят выгодно, важно помнить о рисках. Нередки случаи, когда сложные условия отыгрыша или ограничения по игре делают бонус менее выгодным, чем кажется на первый взгляд.
Рекомендуется тщательно читать правила и условия бонусов, чтобы избежать разочарований и проблем с выводом средств.
Заключение
Бонусы казино — это удобный способ увеличить интерес к азартным развлечениям и получить дополнительные шансы на выигрыш. Правильное понимание видов бонусов и условий их использования поможет наилучшим образом использовать все предложенные возможности и получать удовольствие от игры.
Помните о серьезном подходе правил, и тогда бонусы станут вашим надежным помощником в мире азартных развлечений.
Your comment is awaiting moderation.
Любишь азарт? everum казино игры от популярных провайдеров, live-казино, бонусы и турниры. Проверяйте лицензию и правила, лимиты и комиссии вывода перед игрой. Подбор способов оплаты, поддержка и обзоры условий.
Your comment is awaiting moderation.
Бонусы казино — что это такое и зачем они нужны
Бонусы игорных заведений — это привлекательные предложения, которые выдаются игрокам с целью привлечения их в игру и улучшения их шансов на выигрыш. Такие бонусные подарки становятся важной частью игровой индустрии и помогают новичкам и постоянным клиентам почувствовать дополнительные возможности.
Виды бонусов в казино
Существует множество форм бонусов, которые можно получить игрокам. Рассмотрим самые популярные из них:
– Бонусы за создание аккаунта — первый подарок новичкам, который часто включает бесплатные деньги или фриспины.
– Бонусы за пополнение счета — дополнительные средства, которые начисляются при внесении реальных денег на игровой счет. Чаще всего это увеличение депозита (например, 100% бонус на первый депозит).
– Бездепозитные бонусы — бонусы без внесения средств, которые позволяют начать игру без риска.
– Кэшбэк предложения — возвращают игроку часть проигранных денег за определенный период.
– Фриспины free spins — подарочные вращения в игровых автоматах без необходимости использовать собственные средства.
– Программы лояльности и VIP-бонусы — специальные поощрения для постоянных игроков.
Как работают бонусы казино
Бонусы функционируют благодаря системе требований, которые необходимо выполнить для их получения и вывода средств.
– Вейджер (условие отыгрыша) — это число оборотов, которое нужно отыграть, чтобы вывести выигрыш с бонуса. Например, вейджер 30х означает, что сумма бонуса и депозита должна быть поставлена в 30 раз.
– Минимальный депозит — минимальная сумма, которую необходимо внести, чтобы активировать бонус.
– Ограничения по играм — не все игры учитываются при отыгрыше бонусов. Например, слоты обычно учитываются на 100%, а настольные игры — меньше или вообще не учитываются.
– Максимальная сумма ставки при отыгрыше — ограничение на максимальную ставку, которую можно делать во время использования бонусных средств.
Преимущества бонусов в казино
Бонусы дают возможность:
– Начать игру с дополнительными средствами.
– Познакомиться с новыми слотами без риска потерять собственные деньги.
– Повысить шансы на выигрыш за счет дополнительных средств.
– Получить больше удовольствия, играя в казино лучшие онлайн казино россии
Риски и важные моменты
Хотя бонусы кажутся привлекательными, важно помнить о подводных камнях. Нередки случаи, когда сложные условия отыгрыша или ограничения по игре делают бонус менее выгодным, чем кажется на первый взгляд.
Рекомендуется тщательно читать правила и условия бонусов, чтобы избежать разочарований и проблем с выводом средств.
Заключение
Бонусы казино — это удобный способ увеличить интерес к азартным развлечениям и получить дополнительные шансы на выигрыш. Правильное понимание видов бонусов и условий их использования поможет оптимально использовать все предложенные возможности и получать удовольствие от игры.
Помните о тщательном изучении правил, и тогда бонусы станут вашим надежным помощником в мире азартных развлечений.
Your comment is awaiting moderation.
Бонусы казино — что это такое и зачем они нужны
Бонусы онлайн-казино — это выгодные предложения, которые даються игрокам с целью заинтересования их в игру и увеличения их шансов на выигрыш. Такие бонусные призы становятся важной составляющей игровой индустрии и помогают новичкам и постоянным клиентам получить дополнительные возможности.
Виды бонусов в казино
Существует множество форм бонусов, которые можно получить игрокам. Рассмотрим основные из них:
– Бонусы за регистрацию — начальный подарок новичкам, который часто включает безвозмездные деньги или фриспины.
– Бонусы при внесении денег — дополнительные средства, которые начисляются при внесении реальных денег на игровой счет. Чаще всего это процентное увеличение (например, 100% бонус на первый депозит).
– Бездепозитные бонусы — подарки без депозита, которые позволяют начать игру без риска.
– Кэшбэк бонусы — возвращают игроку часть проигранных денег за определенный период.
– Фриспины бонусные вращения — подарочные вращения в игровых автоматах без необходимости использовать собственные средства.
– Программы лояльности и VIP-бонусы — специальные бонусы для постоянных игроков.
Как работают бонусы казино
Бонусы функционируют благодаря системе требований, которые необходимо выполнить для их получения и вывода.
– Вейджер (условие отыгрыша) — это число оборотов, которое нужно отыграть, чтобы вывести выигрыш с бонуса. Например, вейджер 30х означает, что сумма бонуса и депозита должна быть поставлена в 30 раз.
– Минимальный депозит — минимальная сумма, которую необходимо внести, чтобы активировать бонус.
– Ограничения по играм — не все игры учитываются при отыгрыше бонусов. Например, слоты обычно учитываются на 100%, а настольные игры — меньше или вообще не учитываются.
– Максимальная сумма ставки при отыгрыше — ограничение на максимальную ставку, которую можно делать во время использования бонусных средств.
Преимущества бонусов в казино
Бонусы способствуют:
– Начать игру с дополнительными средствами.
– Познакомиться с широким ассортиментом игр без риска потерять собственные деньги.
– Повысить шансы на выигрыш за счет бесплатных вращений.
– Получить больше удовольствия, играя в казино играть в казино онлайн
Риски и важные моменты
Хотя бонусы кажутся привлекательными, важно помнить о особенностях. Нередки случаи, когда сложные условия отыгрыша или ограничения по игре делают бонус менее выгодным, чем кажется на первый взгляд.
Рекомендуется тщательно читать правила и условия бонусов, чтобы избежать разочарований и проблем с выводом средств.
Заключение
Бонусы казино — это удобный способ увеличить интерес к азартным развлечениям и получить дополнительные шансы на выигрыш. Правильное понимание видов бонусов и условий их использования поможет наилучшим образом использовать все предложенные возможности и получать удовольствие от игры.
Помните о тщательном изучении правил, и тогда бонусы станут вашим надежным помощником в мире азартных развлечений.
Your comment is awaiting moderation.
Бонусы казино — что это такое и зачем они нужны
Бонусы онлайн-казино — это выгодные предложения, которые предоставляются игрокам с целью затягивания их в игру и повышения их шансов на выигрыш. Такие бонусные вознаграждения становятся важной элементом игровой индустрии и помогают новичкам и постоянным клиентам испытать дополнительные возможности.
Виды бонусов в казино
Существует множество форм бонусов, которые можно получить игрокам. Рассмотрим самые популярные из них:
– Бонусы за создание аккаунта — стартовый подарок новичкам, который часто включает комплиментарные деньги или фриспины.
– Бонусы на депозит — дополняющие средства, которые начисляются при внесении реальных денег на игровой счет. Чаще всего это увеличение депозита (например, 100% бонус на первый депозит).
– Бездепозитные бонусы — бонусы без внесения средств, которые позволяют начать игру без риска.
– Кэшбэк бонусы — возвращают игроку часть проигранных денег за определенный период.
– Фриспины free spins — подарочные вращения в игровых автоматах без необходимости использовать собственные средства.
– Программы лояльности и VIP-бонусы — специальные вознаграждения для постоянных игроков.
Как работают бонусы казино
Бонусы работают благодаря системе требований, которые необходимо выполнить для их получения и вывода.
– Вейджер (условие отыгрыша) — это количество раз, которое нужно отыграть, чтобы вывести выигрыш с бонуса. Например, вейджер 30х означает, что сумма бонуса и депозита должна быть поставлена в 30 раз.
– Минимальный депозит — минимальная сумма, которую необходимо внести, чтобы активировать бонус.
– Ограничения по играм — не все игры учитываются при отыгрыше бонусов. Например, слоты обычно учитываются на 100%, а настольные игры — меньше или вообще не учитываются.
– Максимальная сумма ставки при отыгрыше — ограничение на максимальную ставку, которую можно делать во время использования бонусных средств.
Преимущества бонусов в казино
Бонусы помогают:
– Начать игру с увеличенным счетом.
– Познакомиться с разными играми без риска потерять собственные деньги.
– Повысить шансы на выигрыш за счет дополнительных средств.
– Получить эмоций, играя в казино казино бесплатно
Риски и важные моменты
Хотя бонусы предоставляют отличные возможности, важно помнить о рисках. Нередки случаи, когда сложные условия отыгрыша или ограничения по игре делают бонус менее выгодным, чем кажется на первый взгляд.
Рекомендуется тщательно читать правила и условия бонусов, чтобы избежать разочарований и проблем с выводом средств.
Заключение
Бонусы казино — это великолепный способ увеличить интерес к играм и получить дополнительные шансы на выигрыш. Правильное понимание видов бонусов и условий их использования поможет наилучшим образом использовать все предложенные возможности и получать удовольствие от игры.
Помните о серьезном подходе правил, и тогда бонусы станут вашим надежным помощником в мире азартных развлечений.
Your comment is awaiting moderation.
movetorussia com https://www.theshaderoom.com/articl/russian_golden_visa_investment_visa_residency_guide.html .
Your comment is awaiting moderation.
Бонусы казино — что это такое и зачем они нужны
Бонусы игорных заведений — это особые предложения, которые даються игрокам с целью затягивания их в игру и увеличения их шансов на выигрыш. Такие бонусные призы становятся важной частью игровой индустрии и помогают новичкам и постоянным клиентам испытать дополнительные возможности.
Виды бонусов в казино
Существует множество типов бонусов, которые можно получить игрокам. Рассмотрим главные из них:
– Бонусы при регистрации — первый подарок новичкам, который часто включает бесплатные деньги или фриспины.
– Бонусы при внесении денег — дополняющие средства, которые начисляются при внесении реальных денег на игровой счет. Чаще всего это увеличение депозита (например, 100% бонус на первый депозит).
– Бездепозитные бонусы — подарки без депозита, которые позволяют начать игру без риска.
– Кэшбэк бонусы — возвращают игроку часть проигранных денег за определенный период.
– Фриспины или бесплатные вращения — подарочные вращения в игровых автоматах без необходимости использовать собственные средства.
– Программы лояльности и VIP-бонусы — специальные бонусы для постоянных игроков.
Как работают бонусы казино
Бонусы действуют благодаря системе условий, которые необходимо принять во внимание для их получения и вывода.
– Вейджер (условие отыгрыша) — это множитель, которое нужно отыграть, чтобы вывести выигрыш с бонуса. Например, вейджер 30х означает, что сумма бонуса и депозита должна быть поставлена в 30 раз.
– Минимальный депозит — минимальная сумма, которую необходимо внести, чтобы активировать бонус.
– Ограничения по играм — не все игры учитываются при отыгрыше бонусов. Например, слоты обычно учитываются на 100%, а настольные игры — меньше или вообще не учитываются.
– Максимальная сумма ставки при отыгрыше — ограничение на максимальную ставку, которую можно делать во время использования бонусных средств.
Преимущества бонусов в казино
Бонусы дают возможность:
– Начать игру с увеличенным счетом.
– Познакомиться с новыми слотами без риска потерять собственные деньги.
– Повысить шансы на выигрыш за счет кэшбэка.
– Получить больше удовольствия, играя в казино играть слоты бесплатно
Риски и важные моменты
Хотя бонусы предоставляют отличные возможности, важно помнить о особенностях. Нередки случаи, когда сложные условия отыгрыша или ограничения по игре делают бонус менее выгодным, чем кажется на первый взгляд.
Рекомендуется тщательно читать правила и условия бонусов, чтобы избежать разочарований и проблем с выводом средств.
Заключение
Бонусы казино — это эффективный способ увеличить интерес к играм и получить дополнительные шансы на выигрыш. Правильное понимание видов бонусов и условий их использования поможет оптимально использовать все предложенные возможности и получать удовольствие от игры.
Помните о серьезном подходе правил, и тогда бонусы станут вашим надежным помощником в мире азартных развлечений.
Your comment is awaiting moderation.
Как выбрать хорошее казино игорный клуб
Выбор хорошего казино — это важный шаг для любого игрока, который хочет получить настоящие эмоции и избежать проблем. В этой статье мы рассмотрим, на что обращать внимание при выборе онлайн-казино, чтобы принять правильное решение.
Лицензия и репутация
Первое, на что стоит смотреть — это наличие лицензии на работу. Надежное казино работает по лицензии от признанных органов, таких как Кюрасао. Лицензия гарантирует, что казино работает честно.
Репутация — второй важный критерий. Рекомендуется изучить отзывы других игроков, рейтинги и обзоры на специализированных сайтах.
Ассортимент игр
Хорошее казино предлагает широкий ассортимент игр от лучших производителей. Это автоматы, рулетки, покер, блэкджек и другие игровые аппараты. Разнообразие позволяет найти игру по душе и не скучать.
Бонусы и акции
Важным плюсом является наличие привлекательных бонусов. Речь о бонусах на депозит, кэшбэке и программах лояльности. Однако важно внимательно изучить требования, чтобы бонусы были действительно полезны.
Способы оплаты
Широкий выбор способов внесения и вывода средств — залог удобства. Надежное казино поддерживает банковские карты и предлагает быстрый вывод выигрыша. При этом платежи должны быть безопасными и прозрачными.
Поддержка клиентов
Качественная служба поддержки — важный аспект. Клиенты должны иметь возможность связаться с оператором быстро, получить квалифицированную помощь по любым вопросам или проблемам, включая технические и финансовые.
Безопасность и честность
Проверенное казино использует современные технологии шифрования данных, что гарантирует безопасность личной информации и финансовых транзакций. Кроме того, честность результатов обеспечивается использованием генератора случайных чисел. Это служит защите интересов игроков.
Мобильная совместимость
Современное казино должно иметь удобную мобильною версию для смартфонов и планшетов. Мобильный доступ дает возможность играть на ходу без потери качества игр и функционала.
Итог
Выбирая казино, обращайте внимание на следующие основные критерии:
– Наличие лицензии
– Репутация и отзывы
– Ассортимент слотов лайв казино
– Выгодные бонусы и прозрачные условия
– Удобные и безопасные способы оплаты
– Качественная служба поддержки
– Надежность и безопасность данных
– Мобильная совместимость
Следуя этим рекомендациям, вы сможете найти идеальное казино и наслаждаться игрой без лишних волнений. Удачи и везения!
Your comment is awaiting moderation.
Бонусы казино — что это такое и зачем они нужны
Бонусы игорных заведений — это особые предложения, которые даються игрокам с целью заинтересования их в игру и увеличения их шансов на выигрыш. Такие бонусные подарки становятся важной частью игровой индустрии и помогают новичкам и постоянным клиентам получить дополнительные возможности.
Виды бонусов в казино
Существует множество типов бонусов, которые можно получить игрокам. Рассмотрим главные из них:
– Бонусы за создание аккаунта — начальный подарок новичкам, который часто включает комплиментарные деньги или фриспины.
– Бонусы на депозит — увеличивающие средства, которые начисляются при внесении реальных денег на игровой счет. Чаще всего это увеличение депозита (например, 100% бонус на первый депозит).
– Бездепозитные бонусы — подарки без депозита, которые позволяют начать игру без риска.
– Кэшбэк возврат средств — возвращают игроку часть проигранных денег за определенный период.
– Фриспины бонусные вращения — подарочные вращения в игровых автоматах без необходимости использовать собственные средства.
– Программы лояльности и VIP-бонусы — специальные поощрения для постоянных игроков.
Как работают бонусы казино
Бонусы работают благодаря системе требований, которые необходимо выполнить для их получения и кэш-аута.
– Вейджер (условие отыгрыша) — это количество раз, которое нужно отыграть, чтобы вывести выигрыш с бонуса. Например, вейджер 30х означает, что сумма бонуса и депозита должна быть поставлена в 30 раз.
– Минимальный депозит — минимальная сумма, которую необходимо внести, чтобы активировать бонус.
– Ограничения по играм — не все игры учитываются при отыгрыше бонусов. Например, слоты обычно учитываются на 100%, а настольные игры — меньше или вообще не учитываются.
– Максимальная сумма ставки при отыгрыше — ограничение на максимальную ставку, которую можно делать во время использования бонусных средств.
Преимущества бонусов в казино
Бонусы помогают:
– Начать игру с большим балансом.
– Познакомиться с широким ассортиментом игр без риска потерять собственные деньги.
– Повысить шансы на выигрыш за счет дополнительных средств.
– Получить дополнительный азарт, играя в казино казино с минимальным депозитом от 10 рублей
Риски и важные моменты
Хотя бонусы кажутся привлекательными, важно помнить о подводных камнях. Нередки случаи, когда сложные условия отыгрыша или ограничения по игре делают бонус менее выгодным, чем кажется на первый взгляд.
Рекомендуется тщательно читать правила и условия бонусов, чтобы избежать разочарований и проблем с выводом средств.
Заключение
Бонусы казино — это великолепный способ увеличить интерес к ставкам и получить дополнительные шансы на выигрыш. Правильное понимание видов бонусов и условий их использования поможет наилучшим образом использовать все предложенные возможности и получать удовольствие от игры.
Помните о тщательном изучении правил, и тогда бонусы станут вашим надежным помощником в мире азартных развлечений.
Your comment is awaiting moderation.
Как выбрать хорошее казино или рулетку для ставок
Выбор хорошего казино или крутой рулетки — важный шаг для тех, кто хочет получить яркие впечатления. В этом материале мы подробно рассмотрим, на что стоит обращать внимание при выборе и как не попасть в руки ненадежных площадок.
Лицензия и репутация игорного заведения
В первую очередь обращайте внимание на наличие действующей лицензии от авторитетных игровых комиссий — например, Мальты, Кюрасао или Великобритании.
Репутация учреждения складывается из мнений пользователей на независимых ресурсах. Высокие рейтинги и положительные отзывы говорят о честности сервиса.
Ассортимент игр и варианты рулетки
Хорошее казино предлагает разнообразие развлечений, включая рулетку — европейскую, американскую или французскую. Чем больше вариантов игр, тем выше вероятность найти подходящий тип, который подарит удовольствие и шансы на выигрыш.
Особое внимание уделяйте разработчикам — проверенные компании, такие как NetEnt, Microgaming, Evolution Gaming, гарантируют прозрачность игр.
Бонусы и акции для игроков
хорошие казино всегда предлагают щедрые бонусные программы — приветственные подарки, кэшбэки и бесплатные вращения. Важно изучить правила использования, чтобы не столкнуться с непредвиденными ограничениями oвЂzbekistonda JONLI sportga tikish
Платежные методы и безопасность
Оптимальный выбор — казино с большим перечнем способов оплаты, включая банковские карты, электронные кошельки, криптовалюты. Проверяйте скорость выплат и безопасность транзакций — современные платформы используют SSL-шифрование для защиты данных.
Служба поддержки и техническая помощь
Надежное казино обеспечивает круглосуточную поддержку клиентов через чат, телефон или электронную почту. Быстрая реакция и компетентные консультанты помогают решать вопросы и устраняют неполадки.
Мобильная версия и удобство интерфейса
Мобильный доступ к казино и рулетке — важный критерий. Современные платформы предлагают адаптированные сайты, где можно играть без ограничений с комфортом.
Итог
Выбирая казино или рулетку, помните о следующих главных аспектах:
– Наличие лицензии
– Положительные отзывы
– Большой ассортимент игр
– Выгодные акции
– Разнообразные методы оплаты
– Круглосуточная поддержка
– Мобильная совместимость
Следуя этим рекомендациям, вы сможете выбрать надежное казино или рулетку и получать удовольствие от игры с максимальной безопасностью и комфортом. Удачи и крупных выигрышей!
Your comment is awaiting moderation.
Как выбрать сувениры матрешки оптимально
Выбор сувениров матрешек стоит быть непростой задачей, особенно для тех, кто хочет подобрать аутентичные подарки или коллекционные предметы. В этой статье мы расскажем, как выбрать матрешки-сувениры, на что обратить внимание и какие варианты лучше предпочесть.
Особенности сувениров матрешек оформление
При подборе матрешек важна их визуальная красота. Обратите внимание на следующие моменты:
– Роспись и цвет — матрешки могут иметь яркую или нежную палитру. Классические модели часто окрашены в народные цвета.
– Количество кукол — наборы различаются по числу вложенных фигурок: от 3 до 15 и более элементов.
– Стиль изображения — матрешки бывают традиционные, современные, тематические (например, в национальных костюмах или с изображением известных личностей).
Материалы изготовления
Матрешки делают преимущественно из соснового дерева. Качественное сырье влияет на прочность изделия и удобство в использовании.
– Дорогие модели часто покрыты лак, что обеспечивает шелковистый эффект и долговечность.
– Обращайте внимание, чтобы древесина была без дефектов и не имела трещин.
Оригинальность и аутентичность
Чтобы выбрать подлинный сувенир, ищите изделия с гарантией. Часто матрешки имеют подпись мастера или штамп мастерской — это признак эксклюзивного производства.
Где покупать матрешки
– Специализированные бутики в туристических местах часто предлагают большое разнообразие как бюджетных, так и дорогих вариантов.
– Интернет-магазины позволяют ознакомиться с рейтингами и выбрать матрешку с доставкой на дом https://imatreshki.ru
– Рынки и ярмарки — хорошее место для поиска ручной работы моделей, однако здесь важно тщательно проверять качество.
Советы при выборе матрешек
– Определитесь с бюджетом заранее.
– Подумайте о получателе подарка — для коллекционера стоит выбрать редкие экземпляры, для детей — яркие и доброжелательные модели.
– Обращайте внимание на размер изделия, чтобы оно удобно помещалось в выбранном интерьере или было портативным.
– Учтите, что иногда роспись несут смысл или рассказывают историю, что добавляет ценность.
Выбирая сувениры матрешки внимательно, вы не только приобретаете напоминание русской культуры, но и дарите частичку традиций, которая порадует любого получателя. Не торопитесь, изучайте ассортимент и выбирайте изделия, которые будут радовать вас и ваших близких долгие годы!
Your comment is awaiting moderation.
Авто в ОАЭ https://auto.ae/ под ключ: продажа новых и б/у автомобилей, диагностика перед покупкой, регистрация и страховка. Прокат на сутки и долгосрок, включая премиум. VIP номерные знаки — подбор вариантов, торг, оформление передачи и сопровождение на русском.
Your comment is awaiting moderation.
Бонусы казино — что это такое и зачем они нужны
Бонусы игорных заведений — это особые предложения, которые предоставляются игрокам с целью заинтересования их в игру и увеличения их шансов на выигрыш. Такие бонусные призы становятся важной элементом игровой индустрии и помогают новичкам и постоянным клиентам почувствовать дополнительные возможности.
Виды бонусов в казино
Существует множество форм бонусов, которые можно получить игрокам. Рассмотрим главные из них:
– Бонусы при регистрации — начальный подарок новичкам, который часто включает безвозмездные деньги или фриспины.
– Бонусы за пополнение счета — дополняющие средства, которые начисляются при внесении реальных денег на игровой счет. Чаще всего это процент от суммы (например, 100% бонус на первый депозит).
– Бездепозитные бонусы — безвозмездные бонусы, которые позволяют начать игру без риска.
– Кэшбэк возврат средств — возвращают игроку часть проигранных денег за определенный период.
– Фриспины или бесплатные вращения — подарочные вращения в игровых автоматах без необходимости использовать собственные средства.
– Программы лояльности и VIP-бонусы — специальные бонусы для постоянных игроков.
Как работают бонусы казино
Бонусы работают благодаря системе требований, которые необходимо соблюсти для их получения и вывода.
– Вейджер (условие отыгрыша) — это множитель, которое нужно отыграть, чтобы вывести выигрыш с бонуса. Например, вейджер 30х означает, что сумма бонуса и депозита должна быть поставлена в 30 раз.
– Минимальный депозит — минимальная сумма, которую необходимо внести, чтобы активировать бонус.
– Ограничения по играм — не все игры учитываются при отыгрыше бонусов. Например, слоты обычно учитываются на 100%, а настольные игры — меньше или вообще не учитываются.
– Максимальная сумма ставки при отыгрыше — ограничение на максимальную ставку, которую можно делать во время использования бонусных средств.
Преимущества бонусов в казино
Бонусы помогают:
– Начать игру с увеличенным счетом.
– Познакомиться с новыми слотами без риска потерять собственные деньги.
– Повысить шансы на выигрыш за счет кэшбэка.
– Получить эмоций, играя в казино топ слоты казино
Риски и важные моменты
Хотя бонусы кажутся привлекательными, важно помнить о рисках. Нередки случаи, когда сложные условия отыгрыша или ограничения по игре делают бонус менее выгодным, чем кажется на первый взгляд.
Рекомендуется тщательно читать правила и условия бонусов, чтобы избежать разочарований и проблем с выводом средств.
Заключение
Бонусы казино — это великолепный способ увеличить интерес к играм и получить дополнительные шансы на выигрыш. Правильное понимание видов бонусов и условий их использования поможет максимально использовать все предложенные возможности и получать удовольствие от игры.
Помните о тщательном изучении правил, и тогда бонусы станут вашим надежным помощником в мире азартных развлечений.
Your comment is awaiting moderation.
Как выбрать хорошее казино игорный клуб
Выбор хорошего казино — это важный шаг для любого поклонника азартных игр, который хочет получить настоящие эмоции и избежать проблем. В этой статье мы рассмотрим, на что обратить внимание при выборе игрового заведения, чтобы найти лучший вариант.
Лицензия и репутация
Первое, на что стоит смотреть — это наличие официальной лицензии. Надежное казино работает по лицензии от признанных органов, таких как Кюрасао. Лицензия гарантирует, что управление подчиняется законам.
Репутация — второй важный критерий. Рекомендуется изучить отзывы других игроков, рейтинги и обзоры на специализированных сайтах.
Ассортимент игр
Хорошее казино предлагает широкий выбор игр от проверенных производителей. Это игровые аппараты, рулетки, покер, блэкджек и другие игровые аппараты. Разнообразие дает возможность найти игру по душе и не скучать.
Бонусы и акции
Важным дополнительным преимуществом является наличие привлекательных бонусов. Речь о бесплатных вращениях, кэшбэке и программах лояльности. Однако важно внимательно изучить условия использования, чтобы бонусы были действительно полезны.
Способы оплаты
Широкий выбор методов оплаты — залог удобства. Надежное казино поддерживает банковские карты и предлагает быстрый вывод выигрыша. При этом платежи должны быть безопасными и прозрачными.
Поддержка клиентов
Качественная служба поддержки — обязательное условие. Клиенты должны иметь возможность связаться с оператором в любое время, получить квалифицированную помощь по любым вопросам или проблемам, включая технические и финансовые.
Безопасность и честность
Проверенное казино использует современные технологии шифрования данных, что гарантирует безопасность личной информации и финансовых транзакций. Кроме того, честность результатов обеспечивается использованием генератора случайных чисел. Это служит защите интересов игроков.
Мобильная совместимость
Современное казино должно иметь удобную мобильною версию для смартфонов и планшетов. Мобильный доступ дает возможность играть в любое время без потери качества игр и функционала.
Итог
Выбирая казино, обращайте внимание на следующие ключевые моменты:
– Наличие лицензии
– Репутация и отзывы
– Ассортимент развлечений мобильное казино
– Выгодные бонусы и прозрачные условия
– Удобные и безопасные способы оплаты
– Качественная служба поддержки
– Надежность и безопасность данных
– Мобильная совместимость
Следуя этим рекомендациям, вы сможете найти надежное казино и наслаждаться игрой без лишних волнений. Удачи и выигрышей!
Your comment is awaiting moderation.
Hi all! My name is Admin Read:
Kraken – это больше, чем просто интернет-магазин. Это место, где вы можете находить уникальные товары, экономить деньги и наслаждаться удобством онлайн-покупок. Стоит подчеркнуть, сайт кракен тор предлагает акции, скидки и возможность участвовать в аукционах. Попробуйте kraken как зайти сегодня и убедитесь, почему его выбирают миллионы покупателей.
Your comment is awaiting moderation.
Как выбрать хорошее казино или рулетку для развлечений
Выбор хорошего казино или честной рулетки — важный шаг для тех, кто хочет получить отличный игровой опыт. В этом материале мы подробно рассмотрим, на что стоит обращать внимание при выборе и как не попасть в руки недобросовестных игроков.
Лицензия и репутация онлайн-платформы
В первую очередь обращайте внимание на наличие лицензионного сертификата от авторитетных регуляторов — например, Мальты, Кюрасао или Великобритании.
Репутация учреждения складывается из отзывов игроков на независимых ресурсах. Высокие рейтинги и положительные отзывы говорят о надежности сервиса.
Ассортимент игр и варианты рулетки
Хорошее казино предлагает разнообразие развлечений, включая рулетку — европейскую, американскую или французскую. Чем больше вариантов игр, тем выше вероятность найти подходящий формат, который подарит удовольствие и шансы на выигрыш.
Особое внимание уделяйте поставщикам софта — проверенные компании, такие как NetEnt, Microgaming, Evolution Gaming, гарантируют честность игр.
Бонусы и акции для игроков
Легальные казино всегда предлагают привлекательные бонусные программы — приветственные подарки, кэшбэки и бесплатные вращения. Важно изучить условия отыгрыша, чтобы не столкнуться с непредвиденными ограничениями казино РЅР° деньги
Платежные методы и безопасность
Оптимальный выбор — казино с большим перечнем способов оплаты, включая банковские карты, электронные кошельки, криптовалюты. Проверяйте скорость выплат и безопасность транзакций — современные платформы используют SSL-шифрование для защиты данных.
Служба поддержки и техническая помощь
Надежное казино обеспечивает круглосуточную поддержку клиентов через чат, телефон или электронную почту. Быстрая реакция и компетентные консультанты помогают решать вопросы и устраняют неполадки.
Мобильная версия и удобство интерфейса
Мобильный доступ к казино и рулетке — важный критерий. Современные платформы предлагают мобильные версии, где можно играть в любое время с комфортом.
Итог
Выбирая казино или рулетку, помните о следующих основных аспектах:
– Наличие лицензии
– Положительные отзывы
– Широкий выбор рулетки
– Щедрые бонусы
– Удобные и безопасные платежи
– Круглосуточная поддержка
– Мобильная совместимость
Следуя этим рекомендациям, вы сможете выбрать оптимальное казино или рулетку и получать удовольствие от игры с максимальной безопасностью и комфортом. Удачи и крупных выигрышей!
Your comment is awaiting moderation.
Бонусы казино — что это такое и зачем они нужны
Бонусы казино — это особые предложения, которые предоставляются игрокам с целью затягивания их в игру и увеличения их шансов на выигрыш. Такие бонусные вознаграждения становятся важной частью игровой индустрии и помогают новичкам и постоянным клиентам испытать дополнительные возможности.
Виды бонусов в казино
Существует множество типов бонусов, которые предлагаются игрокам. Рассмотрим главные из них:
– Бонусы за создание аккаунта — начальный подарок новичкам, который часто включает безвозмездные деньги или фриспины.
– Бонусы при внесении денег — дополнительные средства, которые начисляются при внесении реальных денег на игровой счет. Чаще всего это процентное увеличение (например, 100% бонус на первый депозит).
– Бездепозитные бонусы — подарки без депозита, которые позволяют начать игру без риска.
– Кэшбэк бонусы — возвращают игроку часть проигранных денег за определенный период.
– Фриспины или бесплатные вращения — подарочные вращения в игровых автоматах без необходимости использовать собственные средства.
– Программы лояльности и VIP-бонусы — специальные бонусы для постоянных игроков.
Как работают бонусы казино
Бонусы действуют благодаря системе правил, которые необходимо соблюсти для их получения и вывода средств.
– Вейджер (условие отыгрыша) — это число оборотов, которое нужно отыграть, чтобы вывести выигрыш с бонуса. Например, вейджер 30х означает, что сумма бонуса и депозита должна быть поставлена в 30 раз.
– Минимальный депозит — минимальная сумма, которую необходимо внести, чтобы активировать бонус.
– Ограничения по играм — не все игры учитываются при отыгрыше бонусов. Например, слоты обычно учитываются на 100%, а настольные игры — меньше или вообще не учитываются.
– Максимальная сумма ставки при отыгрыше — ограничение на максимальную ставку, которую можно делать во время использования бонусных средств.
Преимущества бонусов в казино
Бонусы способствуют:
– Начать игру с большим балансом.
– Познакомиться с разными играми без риска потерять собственные деньги.
– Повысить шансы на выигрыш за счет дополнительных средств.
– Получить эмоций, играя в казино автоматы на деньги
Риски и важные моменты
Хотя бонусы выглядят выгодно, важно помнить о особенностях. Нередки случаи, когда сложные условия отыгрыша или ограничения по игре делают бонус менее выгодным, чем кажется на первый взгляд.
Рекомендуется тщательно читать правила и условия бонусов, чтобы избежать разочарований и проблем с выводом средств.
Заключение
Бонусы казино — это эффективный способ увеличить интерес к азартным развлечениям и получить дополнительные шансы на выигрыш. Правильное понимание видов бонусов и условий их использования поможет наилучшим образом использовать все предложенные возможности и получать удовольствие от игры.
Помните о внимательном прочтении правил, и тогда бонусы станут вашим надежным помощником в мире азартных развлечений.
Your comment is awaiting moderation.
Как выбрать сувениры матрешки правильно
Выбор сувениров матрешек может быть непростой задачей, особенно для тех, кто хочет подобрать качественные подарки или коллекционные предметы. В этой статье мы расскажем, как выбрать матрешки-сувениры, на что обратить внимание и какие варианты лучше предпочесть.
Особенности сувениров матрешек оформление
При подборе матрешек важна их визуальная красота. Обратите внимание на следующие моменты:
– Роспись и цвет — матрешки могут иметь яркую или пастельную палитру. Классические модели часто окрашены в традиционные цвета.
– Количество кукол — наборы различаются по числу вложенных фигурок: от 3 до 15 и более сегментов.
– Стиль изображения — матрешки бывают классические, современные, тематические (например, в национальных костюмах или с изображением известных личностей).
Материалы изготовления
Матрешки делают преимущественно из соснового дерева. Качественное сырье влияет на долговечность изделия и удобство в использовании.
– Дорогие модели часто покрыты эмаль, что обеспечивает глянцевый эффект и долговечность.
– Обращайте внимание, чтобы древесина была хорошо высушенной и не имела трещин.
Оригинальность и аутентичность
Чтобы выбрать подлинный сувенир, ищите изделия с сертификатом. Часто матрешки имеют подпись мастера или штамп мастерской — это признак ручного производства.
Где покупать матрешки
– Магазины сувениров в туристических местах часто предлагают большое разнообразие как бюджетных, так и дорогих вариантов.
– Интернет-магазины позволяют ознакомиться с рекомендациями и выбрать матрешку с доставкой на дом https://imatreshki.ru
– Рынки и ярмарки — хорошее место для поиска этнических моделей, однако здесь важно тщательно проверять качество.
Советы при выборе матрешек
– Определитесь с бюджетом заранее.
– Подумайте о целевой аудитории — для коллекционера стоит выбрать редкие экземпляры, для детей — яркие и доброжелательные модели.
– Обращайте внимание на высоту изделия, чтобы оно удобно помещалось в выбранном интерьере или было портативным.
– Учтите, что иногда орнаменты несут смысл или рассказывают историю, что добавляет ценность.
Выбирая сувениры матрешки внимательно, вы не только приобретаете талисман русской культуры, но и дарите частичку традиций, которая порадует любого получателя. Не торопитесь, изучайте ассортимент и выбирайте изделия, которые будут радовать вас и ваших близких долгие годы!
Your comment is awaiting moderation.
Бонусы казино — что это такое и зачем они нужны
Бонусы казино — это выгодные предложения, которые даються игрокам с целью заинтересования их в игру и улучшения их шансов на выигрыш. Такие бонусные подарки становятся важной элементом игровой индустрии и помогают новичкам и постоянным клиентам получить дополнительные возможности.
Виды бонусов в казино
Существует множество типов бонусов, которые предлагаются игрокам. Рассмотрим самые популярные из них:
– Бонусы за регистрацию — начальный подарок новичкам, который часто включает бесплатные деньги или фриспины.
– Бонусы при внесении денег — дополняющие средства, которые начисляются при внесении реальных денег на игровой счет. Чаще всего это процентное увеличение (например, 100% бонус на первый депозит).
– Бездепозитные бонусы — подарки без депозита, которые позволяют начать игру без риска.
– Кэшбэк предложения — возвращают игроку часть проигранных денег за определенный период.
– Фриспины или бесплатные вращения — подарочные вращения в игровых автоматах без необходимости использовать собственные средства.
– Программы лояльности и VIP-бонусы — специальные вознаграждения для постоянных игроков.
Как работают бонусы казино
Бонусы действуют благодаря системе условий, которые необходимо соблюсти для их получения и кэш-аута.
– Вейджер (условие отыгрыша) — это количество раз, которое нужно отыграть, чтобы вывести выигрыш с бонуса. Например, вейджер 30х означает, что сумма бонуса и депозита должна быть поставлена в 30 раз.
– Минимальный депозит — минимальная сумма, которую необходимо внести, чтобы активировать бонус.
– Ограничения по играм — не все игры учитываются при отыгрыше бонусов. Например, слоты обычно учитываются на 100%, а настольные игры — меньше или вообще не учитываются.
– Максимальная сумма ставки при отыгрыше — ограничение на максимальную ставку, которую можно делать во время использования бонусных средств.
Преимущества бонусов в казино
Бонусы способствуют:
– Начать игру с дополнительными средствами.
– Познакомиться с разными играми без риска потерять собственные деньги.
– Повысить шансы на выигрыш за счет кэшбэка.
– Получить эмоций, играя в казино лучшие игровые автоматы
Риски и важные моменты
Хотя бонусы кажутся привлекательными, важно помнить о особенностях. Нередки случаи, когда сложные условия отыгрыша или ограничения по игре делают бонус менее выгодным, чем кажется на первый взгляд.
Рекомендуется тщательно читать правила и условия бонусов, чтобы избежать разочарований и проблем с выводом средств.
Заключение
Бонусы казино — это эффективный способ увеличить интерес к азартным развлечениям и получить дополнительные шансы на выигрыш. Правильное понимание видов бонусов и условий их использования поможет максимально использовать все предложенные возможности и получать удовольствие от игры.
Помните о серьезном подходе правил, и тогда бонусы станут вашим надежным помощником в мире азартных развлечений.
Your comment is awaiting moderation.
Как выбрать хорошее казино онлайн-казино
Выбор качественного казино — это важный шаг для любого поклонника азартных игр, который хочет получить максимум удовольствия и избежать проблем. В этой статье мы рассмотрим, на что обращать внимание при выборе игрового заведения, чтобы принять правильное решение.
Лицензия и репутация
Первое, на что стоит смотреть — это наличие разрешения на деятельность. Надежное казино работает по лицензии от признанных органов, таких как Кюрасао. Лицензия гарантирует, что управление подчиняется законам.
Репутация — второй важный критерий. Рекомендуется изучить отзывы сообщества, рейтинги и обзоры на специализированных сайтах.
Ассортимент игр
Хорошее казино предлагает широкий подбор игр от известных производителей. Это автоматы, рулетки, покер, блэкджек и другие игровые слоты. Разнообразие дает возможность найти игру по душе и не скучать.
Бонусы и акции
Важным дополнительным преимуществом является наличие привлекательных бонусов. Речь о подарках за регистрацию, кэшбэке и программах лояльности. Однако важно внимательно изучить правила отыгрыша, чтобы бонусы были действительно полезны.
Способы оплаты
Широкий выбор платежных систем — залог удобства. Надежное казино поддерживает криптовалюты и предлагает быстрый вывод выигрыша. При этом платежи должны быть безопасными и прозрачными.
Поддержка клиентов
Качественная служба поддержки — обязательное условие. Клиенты должны иметь возможность связаться с оператором быстро, получить квалифицированную помощь по любым вопросам или проблемам, включая технические и финансовые.
Безопасность и честность
Проверенное казино использует современные технологии шифрования данных, что гарантирует безопасность личной информации и финансовых транзакций. Кроме того, честность результатов обеспечивается использованием RNG. Это служит защите интересов игроков.
Мобильная совместимость
Современное казино должно иметь адаптированный сайт для смартфонов и планшетов. Мобильный доступ дает возможность играть на ходу без потери качества игр и функционала.
Итог
Выбирая казино, обращайте внимание на следующие важные составляющие:
– Правовая база
– Репутация и отзывы
– Ассортимент игр топ лучших онлайн казино
– Выгодные бонусы и прозрачные условия
– Удобные и безопасные способы оплаты
– Качественная служба поддержки
– Надежность и безопасность данных
– Мобильная совместимость
Следуя этим рекомендациям, вы сможете найти идеальное казино и наслаждаться игрой без лишних волнений. Удачи и везения!
Your comment is awaiting moderation.
Как выбрать хорошее казино или рулетку для игры
Выбор надежного казино или честной рулетки — важный шаг для тех, кто хочет получить максимальное удовольствие. В этом материале мы подробно рассмотрим, на что стоит следить при выборе и как не попасть в руки ненадежных площадок.
Лицензия и репутация казино
В первую очередь обращайте внимание на наличие лицензионного сертификата от авторитетных органов контроля — например, Мальты, Кюрасао или Великобритании.
Репутация учреждения складывается из мнений пользователей на независимых ресурсах. Высокие рейтинги и положительные отзывы говорят о честности сервиса.
Ассортимент игр и варианты рулетки
Хорошее казино предлагает богатый ассортимент развлечений, включая рулетку — европейскую, американскую или французскую. Чем больше вариантов игр, тем выше вероятность найти подходящий формат, который подарит удовольствие и шансы на выигрыш.
Особое внимание уделяйте производителям игр — проверенные компании, такие как NetEnt, Microgaming, Evolution Gaming, гарантируют высокое качество игр.
Бонусы и акции для игроков
хорошие казино всегда предлагают привлекательные бонусные программы — приветственные подарки, кэшбэки и бесплатные вращения. Важно изучить условия отыгрыша, чтобы не столкнуться с непредвиденными ограничениями onlayn kazino reytingi
Платежные методы и безопасность
Оптимальный выбор — казино с большим перечнем способов оплаты, включая банковские карты, электронные кошельки, криптовалюты. Проверяйте скорость выплат и безопасность транзакций — современные платформы используют SSL-шифрование для защиты данных.
Служба поддержки и техническая помощь
Надежное казино обеспечивает оперативную поддержку клиентов через чат, телефон или электронную почту. Быстрая реакция и компетентные консультанты помогают решать вопросы и устраняют неполадки.
Мобильная версия и удобство интерфейса
Мобильный доступ к казино и рулетке — важный критерий. Современные платформы предлагают специальные приложения, где можно играть в любое время с комфортом.
Итог
Выбирая казино или рулетку, помните о следующих главных аспектах:
– Официальный статус
– Хорошая репутация
– Широкий выбор рулетки
– Привлекательные предложения
– Надежные финансовые операции
– Круглосуточная поддержка
– Мобильная совместимость
Следуя этим рекомендациям, вы сможете выбрать надежное казино или рулетку и получать удовольствие от игры с максимальной безопасностью и комфортом. Удачи и крупных выигрышей!
Your comment is awaiting moderation.
Бонусы казино — что это такое и зачем они нужны
Бонусы казино — это особые предложения, которые выдаются игрокам с целью затягивания их в игру и улучшения их шансов на выигрыш. Такие бонусные подарки становятся важной элементом игровой индустрии и помогают новичкам и постоянным клиентам почувствовать дополнительные возможности.
Виды бонусов в казино
Существует множество форм бонусов, которые предлагаются игрокам. Рассмотрим основные из них:
– Бонусы за регистрацию — начальный подарок новичкам, который часто включает комплиментарные деньги или фриспины.
– Бонусы за пополнение счета — увеличивающие средства, которые начисляются при внесении реальных денег на игровой счет. Чаще всего это увеличение депозита (например, 100% бонус на первый депозит).
– Бездепозитные бонусы — безвозмездные бонусы, которые позволяют начать игру без риска.
– Кэшбэк возврат средств — возвращают игроку часть проигранных денег за определенный период.
– Фриспины бонусные вращения — подарочные вращения в игровых автоматах без необходимости использовать собственные средства.
– Программы лояльности и VIP-бонусы — специальные вознаграждения для постоянных игроков.
Как работают бонусы казино
Бонусы работают благодаря системе требований, которые необходимо принять во внимание для их получения и кэш-аута.
– Вейджер (условие отыгрыша) — это множитель, которое нужно отыграть, чтобы вывести выигрыш с бонуса. Например, вейджер 30х означает, что сумма бонуса и депозита должна быть поставлена в 30 раз.
– Минимальный депозит — минимальная сумма, которую необходимо внести, чтобы активировать бонус.
– Ограничения по играм — не все игры учитываются при отыгрыше бонусов. Например, слоты обычно учитываются на 100%, а настольные игры — меньше или вообще не учитываются.
– Максимальная сумма ставки при отыгрыше — ограничение на максимальную ставку, которую можно делать во время использования бонусных средств.
Преимущества бонусов в казино
Бонусы дают возможность:
– Начать игру с увеличенным счетом.
– Познакомиться с широким ассортиментом игр без риска потерять собственные деньги.
– Повысить шансы на выигрыш за счет кэшбэка.
– Получить больше удовольствия, играя в казино слоты с выводом денег
Риски и важные моменты
Хотя бонусы предоставляют отличные возможности, важно помнить о рисках. Нередки случаи, когда сложные условия отыгрыша или ограничения по игре делают бонус менее выгодным, чем кажется на первый взгляд.
Рекомендуется тщательно читать правила и условия бонусов, чтобы избежать разочарований и проблем с выводом средств.
Заключение
Бонусы казино — это удобный способ увеличить интерес к играм и получить дополнительные шансы на выигрыш. Правильное понимание видов бонусов и условий их использования поможет оптимально использовать все предложенные возможности и получать удовольствие от игры.
Помните о внимательном прочтении правил, и тогда бонусы станут вашим надежным помощником в мире азартных развлечений.
Your comment is awaiting moderation.
Продаешь антиквариат? Скупка антиквариата в Москве — выгодно продать старинные вещи оценка и выкуп старинных вещей с понятными условиями. Принимаем фарфор, бронзу, серебро, иконы, монеты, часы, книги, мебель и предметы искусства. Возможен выезд и оценка по фото. Оплата сразу, конфиденциальность.
Your comment is awaiting moderation.
Нужен эвакуатор? вызов эвакуатора спб цена быстрый выезд по Санкт-Петербургу и области. Аккуратно погрузим легковое авто, кроссовер, мотоцикл. Перевозка после ДТП и поломок, помощь с запуском/колесом. Прозрачная цена, без навязываний.
Your comment is awaiting moderation.
Центр охраны труда https://unitalm.ru “Юнитал-М” проводит обучение по охране труда более чем по 350-ти программам, в том числе по электробезопасности и пожарной безопасности. А также оказывает услуги освидетельствования и испытаний оборудования и аутсорсинга охраны труда.
Your comment is awaiting moderation.
Как выбрать хорошее казино игорный клуб
Выбор надежного казино — это важный шаг для любого любителя ставок, который хочет получить максимум удовольствия и избежать проблем. В этой статье мы рассмотрим, на что обратить внимание при выборе игрового заведения, чтобы не ошибиться.
Лицензия и репутация
Первое, на что стоит смотреть — это наличие разрешения на деятельность. Надежное казино работает по лицензии от признанных органов, таких как Мальта. Лицензия гарантирует, что управление подчиняется законам.
Репутация — второй важный критерий. Рекомендуется изучить отзывы других игроков, рейтинги и обзоры на специализированных сайтах.
Ассортимент игр
Хорошее казино предлагает широкий подбор игр от проверенных производителей. Это автоматы, рулетки, покер, блэкджек и другие игровые вариации азартных развлечений. Разнообразие помогает найти игру по душе и не скучать.
Бонусы и акции
Важным плюсом является наличие привлекательных бонусов. Речь о подарках за регистрацию, кэшбэке и программах лояльности. Однако важно внимательно изучить требования, чтобы бонусы были действительно полезны.
Способы оплаты
Широкий выбор методов оплаты — залог удобства. Надежное казино поддерживает банковские карты и предлагает быстрый вывод выигрыша. При этом платежи должны быть безопасными и прозрачными.
Поддержка клиентов
Качественная служба поддержки — обязательное условие. Клиенты должны иметь возможность связаться с оператором быстро, получить квалифицированную помощь по любым вопросам или проблемам, включая технические и финансовые.
Безопасность и честность
Проверенное казино использует современные технологии шифрования данных, что гарантирует безопасность личной информации и финансовых транзакций. Кроме того, честность результатов обеспечивается использованием справедливых алгоритмов. Это служит защите интересов игроков.
Мобильная совместимость
Современное казино должно иметь приложение для смартфонов и планшетов. Мобильный доступ дает возможность играть на ходу без потери качества игр и функционала.
Итог
Выбирая казино, обращайте внимание на следующие основные критерии:
– Правовая база
– Репутация и отзывы
– Ассортимент слотов самые дающие слоты
– Выгодные бонусы и прозрачные условия
– Удобные и безопасные способы оплаты
– Качественная служба поддержки
– Надежность и безопасность данных
– Мобильная совместимость
Следуя этим рекомендациям, вы сможете найти лучшее казино и наслаждаться игрой без лишних волнений. Удачи и успехов!
Your comment is awaiting moderation.
Бонусы казино — что это такое и зачем они нужны
Бонусы онлайн-казино — это выгодные предложения, которые выдаются игрокам с целью привлечения их в игру и увеличения их шансов на выигрыш. Такие бонусные вознаграждения становятся важной частью игровой индустрии и помогают новичкам и постоянным клиентам испытать дополнительные возможности.
Виды бонусов в казино
Существует множество форм бонусов, которые предлагаются игрокам. Рассмотрим самые популярные из них:
– Бонусы за создание аккаунта — начальный подарок новичкам, который часто включает комплиментарные деньги или фриспины.
– Бонусы при внесении денег — дополнительные средства, которые начисляются при внесении реальных денег на игровой счет. Чаще всего это увеличение депозита (например, 100% бонус на первый депозит).
– Бездепозитные бонусы — бонусы без внесения средств, которые позволяют начать игру без риска.
– Кэшбэк бонусы — возвращают игроку часть проигранных денег за определенный период.
– Фриспины free spins — подарочные вращения в игровых автоматах без необходимости использовать собственные средства.
– Программы лояльности и VIP-бонусы — специальные вознаграждения для постоянных игроков.
Как работают бонусы казино
Бонусы функционируют благодаря системе условий, которые необходимо соблюсти для их получения и вывода.
– Вейджер (условие отыгрыша) — это число оборотов, которое нужно отыграть, чтобы вывести выигрыш с бонуса. Например, вейджер 30х означает, что сумма бонуса и депозита должна быть поставлена в 30 раз.
– Минимальный депозит — минимальная сумма, которую необходимо внести, чтобы активировать бонус.
– Ограничения по играм — не все игры учитываются при отыгрыше бонусов. Например, слоты обычно учитываются на 100%, а настольные игры — меньше или вообще не учитываются.
– Максимальная сумма ставки при отыгрыше — ограничение на максимальную ставку, которую можно делать во время использования бонусных средств.
Преимущества бонусов в казино
Бонусы помогают:
– Начать игру с увеличенным счетом.
– Познакомиться с разными играми без риска потерять собственные деньги.
– Повысить шансы на выигрыш за счет дополнительных средств.
– Получить больше удовольствия, играя в казино слоты на деньги
Риски и важные моменты
Хотя бонусы предоставляют отличные возможности, важно помнить о рисках. Нередки случаи, когда сложные условия отыгрыша или ограничения по игре делают бонус менее выгодным, чем кажется на первый взгляд.
Рекомендуется тщательно читать правила и условия бонусов, чтобы избежать разочарований и проблем с выводом средств.
Заключение
Бонусы казино — это эффективный способ увеличить интерес к играм и получить дополнительные шансы на выигрыш. Правильное понимание видов бонусов и условий их использования поможет максимально использовать все предложенные возможности и получать удовольствие от игры.
Помните о тщательном изучении правил, и тогда бонусы станут вашим надежным помощником в мире азартных развлечений.
Your comment is awaiting moderation.
Как выбрать хорошее казино или рулетку для развлечений
Выбор надежного казино или крутой рулетки — важный шаг для тех, кто хочет получить максимальное удовольствие. В этом материале мы подробно рассмотрим, на что стоит обращать внимание при выборе и как не попасть в руки ненадежных площадок.
Лицензия и репутация игорного заведения
В первую очередь обращайте внимание на наличие официального разрешения от авторитетных игровых комиссий — например, Мальты, Кюрасао или Великобритании.
Репутация казино складывается из отзывов игроков на независимых ресурсах. Высокие рейтинги и положительные отзывы говорят о качестве сервиса.
Ассортимент игр и варианты рулетки
Хорошее казино предлагает разнообразие развлечений, включая рулетку — европейскую, американскую или французскую. Чем больше вариантов игр, тем выше вероятность найти подходящий тип, который подарит удовольствие и шансы на выигрыш.
Особое внимание уделяйте поставщикам софта — проверенные компании, такие как NetEnt, Microgaming, Evolution Gaming, гарантируют честность игр.
Бонусы и акции для игроков
хорошие казино всегда предлагают привлекательные бонусные программы — приветственные подарки, кэшбэки и бесплатные вращения. Важно изучить правила использования, чтобы не столкнуться с непредвиденными ограничениями kazino ruletka
Платежные методы и безопасность
Оптимальный выбор — казино с большим перечнем способов оплаты, включая банковские карты, электронные кошельки, криптовалюты. Проверяйте скорость выплат и безопасность транзакций — современные платформы используют SSL-шифрование для защиты данных.
Служба поддержки и техническая помощь
Надежное казино обеспечивает оперативную поддержку клиентов через чат, телефон или электронную почту. Быстрая реакция и компетентные консультанты помогают решать вопросы и устраняют неполадки.
Мобильная версия и удобство интерфейса
Мобильный доступ к казино и рулетке — важный критерий. Современные платформы предлагают адаптированные сайты, где можно играть в любое время с комфортом.
Итог
Выбирая казино или рулетку, помните о следующих основных аспектах:
– Правовая надежность
– Реальные рейтинги
– Широкий выбор рулетки
– Щедрые бонусы
– Разнообразные методы оплаты
– Круглосуточная поддержка
– Мобильная совместимость
Следуя этим рекомендациям, вы сможете выбрать надежное казино или рулетку и получать удовольствие от игры с максимальной безопасностью и комфортом. Удачи и крупных выигрышей!
Your comment is awaiting moderation.
Авто в ОАЭ https://auto.ae/ под ключ: продажа новых и б/у автомобилей, диагностика перед покупкой, регистрация и страховка. Прокат на сутки и долгосрок, включая премиум. VIP номерные знаки — подбор вариантов, торг, оформление передачи и сопровождение на русском.
Your comment is awaiting moderation.
Стоматология в Калуге https://albakaluga.ru Альбадент — имплантация и протезирование зубов с гарантией эстетики. Виниры, костная пластика и реставрация улыбки по индивидуальному плану лечения.
Your comment is awaiting moderation.
Бонусы казино — что это такое и зачем они нужны
Бонусы игорных заведений — это привлекательные предложения, которые даються игрокам с целью заинтересования их в игру и повышения их шансов на выигрыш. Такие бонусные подарки становятся важной элементом игровой индустрии и помогают новичкам и постоянным клиентам испытать дополнительные возможности.
Виды бонусов в казино
Существует множество типов бонусов, которые предлагаются игрокам. Рассмотрим основные из них:
– Бонусы за регистрацию — стартовый подарок новичкам, который часто включает комплиментарные деньги или фриспины.
– Бонусы на депозит — дополнительные средства, которые начисляются при внесении реальных денег на игровой счет. Чаще всего это увеличение депозита (например, 100% бонус на первый депозит).
– Бездепозитные бонусы — безвозмездные бонусы, которые позволяют начать игру без риска.
– Кэшбэк бонусы — возвращают игроку часть проигранных денег за определенный период.
– Фриспины free spins — подарочные вращения в игровых автоматах без необходимости использовать собственные средства.
– Программы лояльности и VIP-бонусы — специальные бонусы для постоянных игроков.
Как работают бонусы казино
Бонусы работают благодаря системе условий, которые необходимо выполнить для их получения и вывода.
– Вейджер (условие отыгрыша) — это количество раз, которое нужно отыграть, чтобы вывести выигрыш с бонуса. Например, вейджер 30х означает, что сумма бонуса и депозита должна быть поставлена в 30 раз.
– Минимальный депозит — минимальная сумма, которую необходимо внести, чтобы активировать бонус.
– Ограничения по играм — не все игры учитываются при отыгрыше бонусов. Например, слоты обычно учитываются на 100%, а настольные игры — меньше или вообще не учитываются.
– Максимальная сумма ставки при отыгрыше — ограничение на максимальную ставку, которую можно делать во время использования бонусных средств.
Преимущества бонусов в казино
Бонусы помогают:
– Начать игру с большим балансом.
– Познакомиться с новыми слотами без риска потерять собственные деньги.
– Повысить шансы на выигрыш за счет бесплатных вращений.
– Получить больше удовольствия, играя в казино лучшие провайдеры казино
Риски и важные моменты
Хотя бонусы выглядят выгодно, важно помнить о рисках. Нередки случаи, когда сложные условия отыгрыша или ограничения по игре делают бонус менее выгодным, чем кажется на первый взгляд.
Рекомендуется тщательно читать правила и условия бонусов, чтобы избежать разочарований и проблем с выводом средств.
Заключение
Бонусы казино — это великолепный способ увеличить интерес к ставкам и получить дополнительные шансы на выигрыш. Правильное понимание видов бонусов и условий их использования поможет наилучшим образом использовать все предложенные возможности и получать удовольствие от игры.
Помните о внимательном прочтении правил, и тогда бонусы станут вашим надежным помощником в мире азартных развлечений.
Your comment is awaiting moderation.
Стоматология в Калуге https://albakaluga.ru Альбадент — имплантация и протезирование зубов с гарантией эстетики. Виниры, костная пластика и реставрация улыбки по индивидуальному плану лечения.
Your comment is awaiting moderation.
Как выбрать хорошее казино онлайн-казино
Выбор надежного казино — это важный шаг для любого любителя ставок, который хочет получить максимум удовольствия и избежать проблем. В этой статье мы рассмотрим, на что обращать внимание при выборе казино, чтобы найти лучший вариант.
Лицензия и репутация
Первое, на что стоит смотреть — это наличие лицензии на работу. Надежное казино работает по лицензии от признанных органов, таких как Великобритания. Лицензия гарантирует, что игры проходят прозрачно.
Репутация — второй важный критерий. Рекомендуется изучить отзывы сообщества, рейтинги и обзоры на специализированных сайтах.
Ассортимент игр
Хорошее казино предлагает широкий ассортимент игр от проверенных производителей. Это слоты, рулетки, покер, блэкджек и другие игровые вариации азартных развлечений. Разнообразие помогает найти игру по душе и не скучать.
Бонусы и акции
Важным дополнительным преимуществом является наличие привлекательных бонусов. Речь о бесплатных вращениях, кэшбэке и программах лояльности. Однако важно внимательно изучить требования, чтобы бонусы были действительно полезны.
Способы оплаты
Широкий выбор платежных систем — залог удобства. Надежное казино поддерживает банковские карты и предлагает быстрый вывод выигрыша. При этом платежи должны быть безопасными и прозрачными.
Поддержка клиентов
Качественная служба поддержки — важный аспект. Клиенты должны иметь возможность связаться с оператором в любое время, получить квалифицированную помощь по любым вопросам или проблемам, включая технические и финансовые.
Безопасность и честность
Проверенное казино использует современные технологии шифрования данных, что гарантирует безопасность личной информации и финансовых транзакций. Кроме того, честность результатов обеспечивается использованием RNG. Это служит защите интересов игроков.
Мобильная совместимость
Современное казино должно иметь адаптированный сайт для смартфонов и планшетов. Мобильный доступ дает возможность играть в любое время без потери качества игр и функционала.
Итог
Выбирая казино, обращайте внимание на следующие важные составляющие:
– Законность работы
– Репутация и отзывы
– Ассортимент игр казино на деньги с выводом
– Выгодные бонусы и прозрачные условия
– Удобные и безопасные способы оплаты
– Качественная служба поддержки
– Надежность и безопасность данных
– Мобильная совместимость
Следуя этим рекомендациям, вы сможете найти надежное казино и наслаждаться игрой без лишних волнений. Удачи и выигрышей!
Your comment is awaiting moderation.
Как выбрать хорошее казино или рулетку для развлечений
Выбор качественного казино или крутой рулетки — важный шаг для тех, кто хочет получить яркие впечатления. В этом материале мы подробно рассмотрим, на что стоит обращать внимание при выборе и как не попасть в руки ненадежных площадок.
Лицензия и репутация игорного заведения
В первую очередь обращайте внимание на наличие лицензионного сертификата от авторитетных органов контроля — например, Мальты, Кюрасао или Великобритании.
Репутация учреждения складывается из отзывов игроков на независимых ресурсах. Высокие рейтинги и положительные отзывы говорят о качестве сервиса.
Ассортимент игр и варианты рулетки
Хорошее казино предлагает разнообразие развлечений, включая рулетку — европейскую, американскую или французскую. Чем больше вариантов игр, тем выше вероятность найти подходящий тип, который подарит удовольствие и шансы на выигрыш.
Особое внимание уделяйте разработчикам — проверенные компании, такие как NetEnt, Microgaming, Evolution Gaming, гарантируют прозрачность игр.
Бонусы и акции для игроков
престижные казино всегда предлагают выгодные бонусные программы — приветственные подарки, кэшбэки и бесплатные вращения. Важно изучить требования к ставкам, чтобы не столкнуться с непредвиденными ограничениями oК»zbekistonda kazino
Платежные методы и безопасность
Оптимальный выбор — казино с большим перечнем способов оплаты, включая банковские карты, электронные кошельки, криптовалюты. Проверяйте скорость выплат и безопасность транзакций — современные платформы используют SSL-шифрование для защиты данных.
Служба поддержки и техническая помощь
Надежное казино обеспечивает профессиональную поддержку клиентов через чат, телефон или электронную почту. Быстрая реакция и компетентные консультанты помогают решать вопросы и устраняют неполадки.
Мобильная версия и удобство интерфейса
Мобильный доступ к казино и рулетке — важный критерий. Современные платформы предлагают специальные приложения, где можно играть без ограничений с комфортом.
Итог
Выбирая казино или рулетку, помните о следующих главных аспектах:
– Правовая надежность
– Хорошая репутация
– Большой ассортимент игр
– Привлекательные предложения
– Надежные финансовые операции
– Профессиональная помощь
– Удобный интерфейс
Следуя этим рекомендациям, вы сможете выбрать надежное казино или рулетку и получать удовольствие от игры с максимальной безопасностью и комфортом. Удачи и крупных выигрышей!
Your comment is awaiting moderation.
Продаешь антиквариат? Скупка антиквариата в Москве — выгодно продать старинные вещи оценка и выкуп старинных вещей с понятными условиями. Принимаем фарфор, бронзу, серебро, иконы, монеты, часы, книги, мебель и предметы искусства. Возможен выезд и оценка по фото. Оплата сразу, конфиденциальность.
Your comment is awaiting moderation.
Центр охраны труда https://unitalm.ru “Юнитал-М” проводит обучение по охране труда более чем по 350-ти программам, в том числе по электробезопасности и пожарной безопасности. А также оказывает услуги освидетельствования и испытаний оборудования и аутсорсинга охраны труда.
Your comment is awaiting moderation.
Задача:
Результаты наших клиентов https://proffseo.ru/
ВАЖНО: понятие геоНЕзависимой выдачи в Яндексе очень условно https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Сотрудники Yandex на «Вебмастерских» конференциях неоднократно заявляли, что не бывает выдачи Яндекса без региона https://proffseo.ru/privacy
Для этого используем современные технологии: создаем турбо-страницы в Яндексе и AMP в Google для страниц карточек товаров и страницы каталога https://proffseo.ru/privacy
Выше скорость – больше конверсий https://proffseo.ru/privacy
Еще истории успеха https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Задача:
Your comment is awaiting moderation.
Бонусы казино — что это такое и зачем они нужны
Бонусы казино — это привлекательные предложения, которые предоставляются игрокам с целью заинтересования их в игру и улучшения их шансов на выигрыш. Такие бонусные призы становятся важной составляющей игровой индустрии и помогают новичкам и постоянным клиентам получить дополнительные возможности.
Виды бонусов в казино
Существует множество видов бонусов, которые можно получить игрокам. Рассмотрим самые популярные из них:
– Бонусы за создание аккаунта — начальный подарок новичкам, который часто включает комплиментарные деньги или фриспины.
– Бонусы за пополнение счета — дополнительные средства, которые начисляются при внесении реальных денег на игровой счет. Чаще всего это процент от суммы (например, 100% бонус на первый депозит).
– Бездепозитные бонусы — подарки без депозита, которые позволяют начать игру без риска.
– Кэшбэк бонусы — возвращают игроку часть проигранных денег за определенный период.
– Фриспины или бесплатные вращения — подарочные вращения в игровых автоматах без необходимости использовать собственные средства.
– Программы лояльности и VIP-бонусы — специальные вознаграждения для постоянных игроков.
Как работают бонусы казино
Бонусы работают благодаря системе условий, которые необходимо выполнить для их получения и кэш-аута.
– Вейджер (условие отыгрыша) — это множитель, которое нужно отыграть, чтобы вывести выигрыш с бонуса. Например, вейджер 30х означает, что сумма бонуса и депозита должна быть поставлена в 30 раз.
– Минимальный депозит — минимальная сумма, которую необходимо внести, чтобы активировать бонус.
– Ограничения по играм — не все игры учитываются при отыгрыше бонусов. Например, слоты обычно учитываются на 100%, а настольные игры — меньше или вообще не учитываются.
– Максимальная сумма ставки при отыгрыше — ограничение на максимальную ставку, которую можно делать во время использования бонусных средств.
Преимущества бонусов в казино
Бонусы помогают:
– Начать игру с большим балансом.
– Познакомиться с разными играми без риска потерять собственные деньги.
– Повысить шансы на выигрыш за счет кэшбэка.
– Получить больше удовольствия, играя в казино казино с маленькими ставками
Риски и важные моменты
Хотя бонусы выглядят выгодно, важно помнить о рисках. Нередки случаи, когда сложные условия отыгрыша или ограничения по игре делают бонус менее выгодным, чем кажется на первый взгляд.
Рекомендуется тщательно читать правила и условия бонусов, чтобы избежать разочарований и проблем с выводом средств.
Заключение
Бонусы казино — это удобный способ увеличить интерес к азартным развлечениям и получить дополнительные шансы на выигрыш. Правильное понимание видов бонусов и условий их использования поможет оптимально использовать все предложенные возможности и получать удовольствие от игры.
Помните о тщательном изучении правил, и тогда бонусы станут вашим надежным помощником в мире азартных развлечений.
Your comment is awaiting moderation.
старые шлюхи порно юные
Your comment is awaiting moderation.
групповое порно мать шлюха
Your comment is awaiting moderation.
Региональное продвижение помогает улучшить позиции сайта в поисковой выдаче в одном или нескольких регионах, привлечь целевую аудиторию и увеличить конверсию при сравнительно невысоких затратах https://proffseo.ru/
Поисковые системы лояльнее относятся к местным компаниям, и конкуренция в одном регионе ниже, чем по всей России, поэтому, продвигаясь по геозависимым запросам, достигнуть первой страницы поиска намного проще https://proffseo.ru/kontakty
В статье мы расскажем, какие способы регионального продвижения сайта наиболее эффективны, и как вести SEO-продвижение сайта в топ-10 Яндекса и Google в одном и нескольких регионах https://proffseo.ru/privacy
Яндекс https://proffseo.ru/kontakty
Директ https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
перевыполнили прогноз на 2019 год!
Результаты наших клиентов https://proffseo.ru/
Так происходит за счет высокого качества информации Wikipedia, громадного траста, ссылочной массы и мировой популярности https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Скидка 100% на первый месяц!
Your comment is awaiting moderation.
Хочешь продвинуть сайт? seo-academypro наша компания предлагает профессиональные услуги по SEO?продвижению (Search Engine Optimization) — мы поможем вывести ресурс в топ?3 поисковых систем Google и Яндекс всего за месяц. Сотрудничество строится на прозрачной основе: все договорённости фиксируются в официальном договоре, что гарантирует чёткость взаимодействия и уверенность в достижении результата.
Your comment is awaiting moderation.
Текущие рекомендации: Куда сдать жёсткий диск за деньги — официальная скупка рядом со мной
Your comment is awaiting moderation.
нажмите здесь kush casino официальный сайт
Your comment is awaiting moderation.
Нужен эвакуатор? услуги эвакуатора быстрый выезд по Санкт-Петербургу и области. Аккуратно погрузим легковое авто, кроссовер, мотоцикл. Перевозка после ДТП и поломок, помощь с запуском/колесом. Прозрачная цена, без навязываний.
Your comment is awaiting moderation.
Нужны заклепки? заклепка вытяжная нержавеющая 4х10 для прочного соединения листового металла и профиля. Стойкость к коррозии, аккуратная головка, надежная фиксация даже при вибрациях. Подбор размеров и типа борта, быстрая отгрузка и доставка.
Your comment is awaiting moderation.
Рейтинг казино https://casinos.autos онлайн 2025 для осознанного выбора: критерии безопасности, репутации, бонусной политики, выплат и сервиса. Таблицы по странам и форматам игр, реальные условия акций, плюсы/минусы, FAQ и ссылки на правила. 18+
Your comment is awaiting moderation.
Обновлено сегодня: Где продать ксилофон дорого — адреса скупки у метро
Your comment is awaiting moderation.
Нужен эвакуатор? услуги эвакуатора в спб быстрый выезд по Санкт-Петербургу и области. Аккуратно погрузим легковое авто, кроссовер, мотоцикл. Перевозка после ДТП и поломок, помощь с запуском/колесом. Прозрачная цена, без навязываний.
Your comment is awaiting moderation.
Нужны заклепки? заклепка вытяжная нержавеющая цена для прочного соединения листового металла и профиля. Стойкость к коррозии, аккуратная головка, надежная фиксация даже при вибрациях. Подбор размеров и типа борта, быстрая отгрузка и доставка.
Your comment is awaiting moderation.
Центр охраны труда https://www.unitalm.ru “Юнитал-М” проводит обучение по охране труда более чем по 350-ти программам, в том числе по электробезопасности и пожарной безопасности. А также оказывает услуги освидетельствования и испытаний оборудования и аутсорсинга охраны труда.
Your comment is awaiting moderation.
Hits of the Day: https://kwork.ru/user/ivanjar
Your comment is awaiting moderation.
Стоматология в Калуге https://albakaluga.ru Альбадент — имплантация и протезирование зубов с гарантией эстетики. Виниры, костная пластика и реставрация улыбки по индивидуальному плану лечения.
Your comment is awaiting moderation.
Прямой производитель предлагает https://www.sportprof.su по минимальным ценам от производителя. Ассортимент содержит неразборные гантели, обрезные блины, велотренажеры. Всегда имеются профессиональные силовые тренажеры и комплектующие для реализации спортивных задач. Оформляйте со скидкой тренажер Смита, вертикальную тягу, скамью для бицепса, тренажер для плечей, станок Гаккеншмидта, римский стул, скамью для гиперэкстензии, а также все необходимое для зала.
Your comment is awaiting moderation.
потолочкин натяжные потолки отзывы http://natyazhnye-potolki-nizhniy-novgorod-4.ru/ .
Your comment is awaiting moderation.
Проблемы в авто? выездная диагностика авто диагностика на месте, запуск двигателя, поиск короткого замыкания, ремонт проводки, замена предохранителей и реле, настройка сигнализации. Приедем быстро по городу и области. Честная цена, гарантия, без лишних работ.
Your comment is awaiting moderation.
Стоматик СПб: https://stomatic-spb.ru Семейная стоматология в Санкт-Петербурге. Профессиональное лечение зубов, включая услуги для детей и лечение под наркозом.
Your comment is awaiting moderation.
Антарес-МЕД: https://antares-med.ru Центр пластической хирургии и косметологии в Санкт-Петербурге. Эстетическая медицина, коррекция фигуры и программы омоложения.
Your comment is awaiting moderation.
натяжные потолки в самаре http://www.natyazhnye-potolki-samara-5.ru/ .
Your comment is awaiting moderation.
Sultan Casino – Обзор и Возможности
Sultan Casino игровой клуб — это популярное интернет-казино, предоставляющее игрокам возможность получать яркие впечатления от игр и выигрышей.
Интерфейс и Дизайн
Платформа Sultan Casino отличается удобным и современным дизайном, который делает процесс подключения и игры максимально простым и приятным для пользователей любого опыта.
Игровой выбор
В Sultan Casino представлен широкий спектр развлечений:
– игровые автоматы от ведущих провайдеров
– казино-игры — рулетка, блэкджек, покер
– live-казино с профессиональными крупье
– прогрессивные выигрыши, предоставляющие шанс сорвать значительный куш
Бонусы и Акции
Sultan Casino привлекает игроков щедрыми бонусами и акциями. Среди них:
– вступительные поощрения
– частичный возврат проигрышей
– ежедневные турниры и лотереи
– специальные предложения для постоянных игроков
Методы Оплаты
Sultan Casino принимает различные способы пополнения, включая:
– банковские карты Visa, MasterCard, Maestro
– электронные кошельки ecoPayz
– криптовалюты (Bitcoin, Ethereum, Litecoin)
– мобильные платежи и другие удобные варианты
Безопасность и Лицензии
Безопасность игроков — один из приоритетов Sultan Casino. Платформа использует современные технологии защиты, которые гарантируют конфиденциальность. Казино имеет регистрацию, что подтверждает его легальность и надежность https://airpres.kz/social/zerkala-populyarnyh-onlajn-platform-podrobnyj-gid-po-dostupu-iz-kazahstana/
Поддержка Клиентов
Команда технической помощи Sultan Casino всегда готова помочь пользователям. Вы можете обратиться к ним через:
– онлайн-чат в любое время
– электронную почту
– телефон
Итог
Sultan Casino — это надежное игровое приложение, предлагаемое для любителей азартных игр, сочетающее в себе многообразие игровых опций, конфиденциальность и привлекательные бонусы. Благодаря продуманному интерфейсу и профессиональной поддержке Sultan Casino завоевывает доверие игроков по всему миру.
Your comment is awaiting moderation.
Рынок продвижения в ИИ-системах
Рынок маркетинга в интеллектуальных системах активно развивается и становится одной из ключевых сфер современной цифровой экономики. С каждым годом растет потребность в эффективном позиционировании продуктов и услуг, основанных на технологиях искусственного интеллекта, что обусловлено широким распространением и внедрением ИИ в различных областях.
Особенности рынка продвижения в ИИ
Рынок продвижения в искусственном интеллекте имеет свои специфические черты. Во-первых, это высокая технологичность и сложность предлагаемых продуктов. Во-вторых, необходимость точного таргетинга и персонализации рекламных сообщений, что зачастую требует использования самих ИИ-инструментов.
Основные факторы, влияющие на развитие рынка:
– рост спроса на интеллектуальные решения
– совершенствование алгоритмов машинного обучения и анализа данных
– интеграция ИИ в маркетинговые стратегии и процессы продвижения
– значительное увеличение затрат на цифровой маркетинг и рекламу в ИИ-сфере
Технологии и инструменты продвижения
В продвижении ИИ-систем используются современные методы:
– анализ больших данных (Big Data) и предиктивная аналитика
– автоматизация маркетинговых кампаний с помощью ИИ
– персонализированный контент и динамический креатив
– использование чат-ботов и виртуальных ассистентов для взаимодействия с клиентами
Эти способы позволяют значительно повысить эффективность рекламы и лучше удовлетворять потребности аудитории.
Основные игроки и сегменты рынка
Рынок продвижения в ИИ-системах представлен множеством участников:
– разработчики ИИ-продуктов
– маркетинговые агентства и консалтинговые фирмы
– компании, специализирующиеся на цифровой рекламе и SMM
– крупные платформы и онлайн-сервисы, использующие ИИ для оптимизации процессов
Сегменты рынка включают продвижение как программного обеспечения и платформ, так и аппаратных решений, а также консультационные услуги и обучение.
Перспективы и вызовы рынка
Перспективы рынка раскрутки в области ИИ связаны с дальнейшим развитием технологий и расширением сфер применения ИИ:
– внедрение ИИ в новые отрасли экономики
– усиление роль данных и аналитики в маркетинге
– рост конкуренции и необходимость инновационных подходов к продвижению https://vladnews.ru/post/260399/optimizaciya_saytov
В то же время рынок сталкивается с рядом вызовов:
– высокая конкуренция и быстрая смена трендов
– вопросы этики и прозрачности использования ИИ в рекламе
– необходимость постоянного обновления знаний и навыков специалистов
Заключение
Рынок продвижения в интеллектуальных технологиях представляет собой динамично развивающуюся и перспективную область, где инновации и технологии играют ключевую роль. Компании, осваивающие современные методы маркетинга с использованием ИИ, получают значительные конкурентные преимущества и возможности для роста в условиях цифровой трансформации экономики.
Your comment is awaiting moderation.
Наш Малыш: https://malish-nash.ru Интернет-магазин товаров для детей и новорожденных. Все необходимое для комфортного роста и развития вашего ребенка.
Your comment is awaiting moderation.
Sultan Casino – Обзор и Возможности
Sultan Casino азартная платформа — это популярное виртуальное игорное заведение, предоставляющее игрокам возможность получать яркие впечатления от игр и выигрышей.
Интерфейс и Дизайн
Платформа Sultan Casino характеризуется удобным и современным оформлением, который делает процесс создания аккаунта и игры максимально простым и приятным для пользователей любого уровня.
Игровой рекомендации
В Sultan Casino представлен широкий спектр игр:
– слоты от ведущих провайдеров
– настольные игры — рулетка, блэкджек, покер
– живое казино с профессиональными крупье
– большие призы, предоставляющие шанс сорвать большой приз
Бонусы и Акции
Sultan Casino привлекает игроков выгодными бонусами и предложениями. Среди них:
– вступительные поощрения
– возврат средств
– постоянные турниры и лотереи
– специальные предложения для постоянных игроков
Методы Оплаты
Sultan Casino поддерживает различные методы оплаты, включая:
– банковские карты Visa, MasterCard, Maestro
– электронные кошельки ecoPayz
– криптовалюты (Bitcoin, Ethereum, Litecoin)
– мобильные платежи и другие удобные варианты
Безопасность и Лицензии
Безопасность игроков — один из приоритетов Sultan Casino. Платформа использует шифрование данных, которые гарантируют конфиденциальность. Казино имеет регистрацию, что подтверждает его легальность и надежность https://liveball.sx/news/621e79ab-952a-45d6-bee9-d449eae34273
Поддержка Клиентов
Команда технической помощи Sultan Casino всегда готова помочь пользователям. Вы можете обратиться к ним через:
– онлайн-чат 24/7
– электронную почту
– телефон
Итог
Sultan Casino — это отличное виртуальное игровое пространство, предлагаемое для любителей азартных игр, сочетающее в себе широкий выбор развлечений, надежность и привлекательные бонусы. Благодаря продуманному интерфейсу и профессиональной поддержке Sultan Casino привлекает широкую аудиторию по всему миру.
Your comment is awaiting moderation.
Баунтовская ЦРБ: https://crbbaunt.ru Официальный сайт районной больницы в Бурятии. Доступная медицинская помощь и актуальная информация для пациентов региона.
Your comment is awaiting moderation.
Камышинская ЦГБ: https://cgbkam.ru Центральная городская больница Камышина. Полный комплекс стационарной и амбулаторной помощи, диагностика и профилактика заболеваний.
Your comment is awaiting moderation.
Металлоизделия (метизы)
Металлоизделия как правило называют металлическими изделиями, которые представляют собой широкий ассортимент деталей из металла, предназначенных для монтажа различных конструкций и элементов. К таким изделиям включаются гаечки, винты, подклады, болтовые соединения и другие крепежные изделия.
Виды металлоизделий
Металлоизделия могут быть нескольких типов, которые широко применяются в индустрии:
– Метизы для крепления — это гаечки, шурупы, шайбы, используемые для скрепления конструкций.
– заклепочные элементы — детали для фиксации листовых материалов.
– анкеры для бетона — металлические изделия для прочного крепления в бетонных и кирпичных конструкциях.
– навесы — используются для монтажа дверей, ворот и других подвижных элементов.
Материалы металлоизделий
Большинство метизов производится из различных видов стали, включая:
– Углеродистую сталь
– нержавейку
– медно-цинковый сплав — реже, но используется в декоративных и специализированных соединениях.
Каждый материал обладает своими особенностями: прочностью, коррозионной стойкостью, стоимостью и областью применения.
Применение металлоизделий
Метизы используются в самых разных отраслях:
– возведение зданий — для крепления несущих элементов, создания каркасов, монтажа кровли.
– производство техники — при сборке агрегатов, деталей и механизмов.
– автосборка — для надежного соединения кузова и металлических частей.
– хозяйственные работы — для сборки мебели, ремонта дверей, крепления различных предметов.
Качество и стандарты
Металлоизделия должны отвечать строгим стандартам качества, таким как ГОСТ, DIN, ISO, которые регламентируют параметры:
– габариты
– нагрузку https://kuzu.ru/forum/index.php?PAGE_NAME=profile_view&UID=13961
– защиту от ржавчины
Использование качественных метизов гарантирует долговечность конструкции.
Заключение
Металлоизделия, или метизы, представляют собой неотъемлемую часть современного строительства и производства. Разнообразие видов, материалов и назначений делает их универсальным связующим элементом в различных сферах жизни и техники. При выборе метизов следует уделять внимание их качеству и соответствию стандартам, чтобы обеспечить долговременную и надежную эксплуатацию изделий и конструкций.
Your comment is awaiting moderation.
МСМ-Медимпэкс: https://msm-medical.ru Ооснащение онкологических центров оборудованием для лучевой терапии и ядерной медицины. Инновационные решения для медицины.
Your comment is awaiting moderation.
Мед-Омск: https://med-omsk.ru Многопрофильный медицинский центр в Омске. Широкий спектр диагностических и лечебных услуг для всей семьи.
Your comment is awaiting moderation.
Thanks you:)
https://hop.cx
Your comment is awaiting moderation.
What’s good, folks?
Came across a fresh article about Bitcoin & altcoin trends.
It goes over major updates in Web3 & DeFi projects.
Really a good read, especially if you trade.
See post
Your comment is awaiting moderation.
Нужен юрист? юридические фирмы Новосибирска разберём ситуацию, оценим риски и предложим стратегию. Составим иск, претензию, договор, жалобу, защитим в суде. Для граждан и компаний. Первичная консультация онлайн/по телефону. Прозрачные условия.
Your comment is awaiting moderation.
Есть зависимости? вызов нарколога на дом Томск вывод из запоя и детоксикация под наблюдением врача. Приём и выезд на дом 24/7, индивидуальный подбор препаратов, контроль самочувствия, конфиденциальность. Помогаем стабилизировать состояние и организовать дальнейшее лечение.
Your comment is awaiting moderation.
“Carnal temptress demands irresistible passion.” Here — rb.gy/3fy54w?stype
Your comment is awaiting moderation.
Хочешь просить пить? капельница после наркотиков быстрое прибытие, медицинский осмотр, капельница для снятия интоксикации, контроль пульса и давления. Анонимная помощь взрослым, внимательное отношение, поддержка после процедуры и советы, как избежать срыва.
Your comment is awaiting moderation.
Проблемы с алкоголем? откапаться на дому Томск выезд врача-нарколога на дом и приём в клинике 24/7 (Томск и область) без ожидания. Осмотр, детоксикация, капельница, контроль давления и самочувствия. Анонимно, бережно, с рекомендациями на восстановление и поддержкой семьи.
Your comment is awaiting moderation.
нужна заклепка? https://zaklepka-vytyazhnaya.ru надёжный крепёж для прочных и долговечных соединений. Устойчива к коррозии, влаге и перепадам температур. Подходит для металла, строительства, машиностроения и наружных работ.
Your comment is awaiting moderation.
азино мобайл азино
Your comment is awaiting moderation.
Красивый интерьер https://moidomiks.ru своими руками: вдохновение, мастер-классы и полезные советы. Оформление комнат, декор, текстиль и освещение. Простые идеи для обновления интерьера и создания гармоничной атмосферы.
Your comment is awaiting moderation.
Новости Тюмени https://kfaktiv.ru и области онлайн: общество, экономика, политика, происшествия и городские события. Оперативные публикации, фото и комментарии. Следите за жизнью региона ежедневно.
Your comment is awaiting moderation.
Варианты, как можно его оформить, можете просмотреть на фото дизайн интерьера дома https://olga-filippova.ru/interery-medical-study-center
Но Вы также должны понимать, что сложность его оформления напрямую будет зависеть лишь от того, чтобы Вы хотели видеть в этом помещении https://olga-filippova.ru/interery-medical-study-center
Первым и очень важным шагом в создании индивидуального интерьера своим руками своей квартиры это решить, что вам ближе по духу https://olga-filippova.ru/zakazat-dizajn-proekt-stoimost
Это может быть максимализм или минимализм в интерьере https://olga-filippova.ru/office_interior
Если вы решаете воспользоваться услугами профессионального дизайнера интерьеров, то могу поделиться одним секретом – итальянские дизайнеры очень сильно затягивают процесс подготовки окончательного варианта дизайна квартиры https://olga-filippova.ru/office_interior
Посещение многочисленных мебельных выставок и салонов может помочь вам подобрать стиль, соответствующий вашим вкусам и нуждам https://olga-filippova.ru/blog
Тем не менее, перед тем, как идти по магазинам – произведите замеры! Будет ужасно влюбиться в какой-нибудь предмет мебели, а потом обнаружить, что он слишком велик для вашей комнаты https://olga-filippova.ru/office_interior
Your comment is awaiting moderation.
Испытания свай нагрузкой в соответствии с особенностями поставленных задач следует обязательно проводить с учетом:
Как вариант, 2 балки устанавливаются “крестом”. Анкерные сваи назначаются, как правило, проектной организацией, однако если данные об анкерах отсутствуют, мы сами выбираем оптимальные анкера с тем условием, чтобы максимально использовать свайное поле и не бить дополнительные сваи в “молоко”.
Названия испытаний https://www.osnovanie-svai.com/politica.html
Статические испытаний свай требуется проводить для определения фактической несущей способности свай в полевых условиях https://www.osnovanie-svai.com/politica.html
Динамические испытания свай Испытания свай динамической нагрузкой Динамические испытания грунтов сваями Проведение динамических испытаний свай Динамические испытания забивных свай Испытания грунтов сваями динамической нагрузкой Результаты динамических испытаний Динамические испытания буронабивных свай https://osnovanie-svai.com/
Проводятся при значительной горизонтальной нагрузке на конструкции: мостовых опор, подпорных стенок, зданий с большими пролетами: торговых, складских и производственных комплексов https://osnovanie-svai.com/pile.php
Your comment is awaiting moderation.
Просто Строй https://prostostroy.com онлайн-журнал о строительстве, ремонте и обустройстве дома. Практичные статьи, пошаговые гайды, обзоры материалов и полезные советы для частного строительства и ремонта.
Your comment is awaiting moderation.
Домашние маски https://omaske.ru для лица и волос — натуральные рецепты для ухода за кожей и волосами. Питание, увлажнение и восстановление с доступными ингредиентами. Советы по применению, типам кожи и волос.
Your comment is awaiting moderation.
пансионат для детей https://shkola-onlajn1.ru .
Your comment is awaiting moderation.
Nase webova platforma poskytuje rozmanity pohled na deni kolem veslovani mladych.
Zde naleznete prehledne informace o ucastnicich, ale take unikatnich statistik.
Web je navrzen tak, aby byl snadno ovladatelny, srozumitelny pro siroke publikum, at uz jste fanousek.
Diky pravidelnym aktualizacim mate neustale pristup k cerstvym informacim, zahrnujic novinky od organizatoru.
https://www.swissrowing.ch/de/news/selektionen-fuer-den-coupe-de-la-jeunesse-in-racice-vom-9-11-august-2024
Your comment is awaiting moderation.
следующий отзыв https://shcherbinins.ru/
Хочу поблагодарить команду за организацию и доставку качественной и красивой продукции https://shcherbinins.ru/menu
Заказываю второй год на день рождения (13-15 коробок). Все четко! Уведомления на каждом этапе (заказ получен, приступили, от грузили). Все четко! Я очень довольна, спасибо https://shcherbinins.ru/contacts
Единственное пожелание от коллег, не хватает табличек с названиями каждой позиции)
Благодаря нашему сайту-агрегатору, обслуживание от лучших кейтеринг-компаний и ресторанов доступно всем — на нашей площадке собраны только партнеры с достойной репутацией https://shcherbinins.ru/aboutus
Заказать кейтеринг в Москве — просто! Ведь для этого нужно просто посетить сайт современного агрегатора «Кейтери», который собрал на одной площадке более 300 ресторанов и кейтеринговых служб, оказывающих услуги выездного обслуживания в столице https://shcherbinins.ru/contacts
Теперь вам не придется тратить время на посещение каждой компании, дегустацию и заключение договора https://shcherbinins.ru/contacts
Весь процесс сотрудничества осуществляется в онлайн-режиме и занимает минимум времени https://shcherbinins.ru/
Если вы хотите заказать выездной кейтеринг на сайте сервиса, вам следует совершить несколько простых действий: 1 https://shcherbinins.ru/
Зарегистрироваться в системе, став участником https://shcherbinins.ru/
Процедура регистрации проста и займет у вас менее 5 минут https://shcherbinins.ru/aboutus
Важно вводить корректную информацию о себе https://shcherbinins.ru/aboutus
2 https://shcherbinins.ru/contacts
Ввести данные о локации https://shcherbinins.ru/contacts
Это необходимо для того, чтобы система отсортировала предложения по географическому признаку, сэкономив ваше время https://shcherbinins.ru/aboutus
3 https://shcherbinins.ru/aboutus
Выбрать вид кейтеринга, который вы планируете заказать https://shcherbinins.ru/menu
Это может быть кофе-брейк, банкет, выездной фуршет, фудтрак и так далее https://shcherbinins.ru/
4 https://shcherbinins.ru/menu
Выбрать компанию, соответствующую требованиям и финансовым возможностям https://shcherbinins.ru/
На сайте представлены предложения в разном ценовом сегменте, чтобы каждый клиент смог удовлетворить свои потребности https://shcherbinins.ru/contacts
5 https://shcherbinins.ru/
Заказать кейтеринг — выездной фуршет или банкет https://shcherbinins.ru/aboutus
Оформить заказ можно прямо на сайте агрегатора https://shcherbinins.ru/contacts
Предусмотрена оплата для юридических и физических лиц — по выставленному счету, с помощью банковской карты, наличными https://shcherbinins.ru/menu
6 https://shcherbinins.ru/uslugy
Наслаждаться прекрасной едой и профессиональным обслуживанием на мероприятии https://shcherbinins.ru/uslugy
В назначенное время и место выбранная компания прибудет для выполнения своих обязанностей https://shcherbinins.ru/menu
Заказать недорогой выездной кейтеринг в Москве — это просто https://shcherbinins.ru/contacts
Убедитесь в этом сами, запросив обратный звонок или проконсультировавшись со специалистом «Кейтери» в онлайн-режиме https://shcherbinins.ru/contacts
Фуршет для компании «Согаз» на 200 человек https://shcherbinins.ru/menu
Пакет L Стоимость: 2 000 руб/персона Входит в стоимость: Логистика Аренда оборудования, текстиля, сервировки Обслуживание мероприятия *Заказ от 30 000 руб https://shcherbinins.ru/aboutus
Заказать фуршет https://shcherbinins.ru/
Your comment is awaiting moderation.
Интернет-магазин профессиональной косметики в Москве Christina поможет ознакомиться с ассортиментом, а также изучить многочисленные отзывы пользователей косметики Christina, которые могут помочь в вашем выборе косметических средств https://sinapple.ru/collection/skinclinic-ispaniya/product/skinclinic-krem-ukreplyayuschiy-dlya-tela-extra-obem-firmin Покупать продукцию Christina онлайн – быстро, легко и надежно https://sinapple.ru/collection/miriamquevedo/product/miriamquevedo-extreme-caviar-bio-regenerative-shock-treatment
Your comment is awaiting moderation.
Покупая натяжные потолки в СПб, Вы обеспечены только прямыми выгодами:
Вообще, вы сможете найти довольно много интересной информации у нас на сайте, например:
Хит продаж! отличная возможность визуально увеличить любое помещение https://skyprofi.ru/tkanevye-natyazhnye-potolki/
Современный Шоу рум в Санкт-Петербурге https://skyprofi.ru/faq/govoryat-chto-probka-ot-shampanskogo-pri-vystrele-mozhet-probit-natyazhnoj-potolok-pravda-li-eto/
С уважением, Анна https://skyprofi.ru/stati/matovyj-natyazhnoj-potolok-photo/
Этап производства и подготовки потолочной конструкции занимает не более одной недели https://skyprofi.ru/slott-natyazhnye-potolki/
Непосредственно сам монтаж выполняется в течение одного рабочего дня https://skyprofi.ru/price/
Your comment is awaiting moderation.
Фабрика Tessarolo https://stosastudio.ru/vybor-materiala-dlya-kuhni-praktichnost-i-estetika/
Гарантия лучшей цены https://stosastudio.ru/catalog/kuhni-timo/
от 460 000 руб./п https://stosastudio.ru/catalog/kuhni-menta/
м https://stosastudio.ru/udivitelnye-preimushhestva-krashenoj-kuhni-iz-mdf/
Made in Italy https://stosastudio.ru/category/stati/page/15/
Уже более 20 лет работаем на мебельном рынке России https://stosastudio.ru/iskusstvo-vybora-tsveta-dlya-vashej-kuhni-kakogo-tsveta-luchshe-sdelat-kuhnyu/
проектов в России https://stosastudio.ru/temnaya-drevesina-na-kuhne-horoshij-vybor-dlya-stilnogo-interera/
Your comment is awaiting moderation.
Hey there, everyone! The name’s Admin Read:
Покупки на Kraken сочетают комфорт и защиту пользователей. На платформе представлены товары из разных категорий, включая электронику, одежду и аксессуары. Скидки и понятные условия сделок на кракен onion ссылка привлекают пользователей. Именно площадка кракен даркнет остаётся выбором миллионов покупателей по всему миру.
Your comment is awaiting moderation.
Hey crypto folks!
Got my hands on a smart piece about AI in trading.
It compares several big trends in blockchain scene.
Definitely a good weekend read.
See full post
Your comment is awaiting moderation.
https://em-dom.ru – cars
https://rekon36.ru – household appliances and computers
https://catalogram.ru – the best cars
https://entara.ru – new cars
https://otakuworld.ru – culinary recipes
https://motil-klin.ru – car market
https://sib-trakt.ru – cars of the week
https://pulpy-promo.ru – car sale
https://ecokrovatka-domik.ru – home furniture
Your comment is awaiting moderation.
Immerse yourself in a fascinating world aviator game and experience your passion right now!
Regardless of whether you’re experienced or new to the game, it’s definitely worth exploring.
Your comment is awaiting moderation.
Информационный портал https://software-expert.ru о секретах ПО. Скрытые возможности программ, настройки, оптимизация, безопасность и обновления. Практичные советы и разборы для повседневного и профессионального использования.
Your comment is awaiting moderation.
Онлайн-портал https://ctoday.ru о строительстве и ремонте. Пошаговые инструкции, расчёты, выбор материалов и оборудования. Полезные материалы для частного строительства, ремонта и обустройства помещений.
Your comment is awaiting moderation.
Портал о провайдерах https://providers.by Беларуси: свежие новости рынка, отзывы абонентов и сравнение тарифов. Помогаем выбрать интернет-провайдера по скорости, цене и качеству обслуживания.
Your comment is awaiting moderation.
Портал о медицине https://zapisnapriemrostov.ru и здоровье человека. Заболевания и их профилактика, современные методы лечения, рекомендации специалистов, здоровье взрослых и детей. Полезные материалы для заботы о самочувствии каждый день.
Your comment is awaiting moderation.
Платформа мостбет для ставок на спорт онлайн. Футбольные матчи, live-режим, коэффициенты и результаты. Описание функционала сервиса и основных инструментов для пользователей.
Your comment is awaiting moderation.
Geely Кунцево https://geely-kuntsevo.ru официальный дилер автомобилей Geely в Москве. Продажа новых моделей, тест-драйвы, выгодные условия покупки, кредит и трейд-ин. Сервисное обслуживание, оригинальные запчасти и консультации специалистов.
Your comment is awaiting moderation.
Hello everyone! I go by the name Admin Read:
Kraken переосмысливает удобство покупок с помощью своего огромного онлайн-магазина, в котором есть миллионы товаров. Независимо от того, нужны ли вам домашняя утварь, гаджеты или средства личного ухода, kraken marketplace предлагает именно то, что вам нужно. Их простая в использовании платформа обеспечивает удобный поиск, достоверные отзывы и доступные цены для обеспечения комфортного шопинга. Воспользуйтесь быстрой доставкой и безопасными способами оплаты ссылка на сайт кракен для беспокойных покупок. Узнайте, что делает kraken com конечным пунктом назначения для покупателей по всему миру.
Your comment is awaiting moderation.
стайлер дайсон http://fen-dn-kupit-1.ru .
Your comment is awaiting moderation.
Hello there! mexican pharmacy online good internet site.
Your comment is awaiting moderation.
Immerse yourself in a captivating world aeroplane game moneyand test your driving skills!
Dive in and experience the excitement for yourself!
Your comment is awaiting moderation.
Всем привет. В этом году для себя открыл пихту Фразера, и теперь понимаю, почему её так ценят перед Новым годом. Мягкая, насыщенно-зелёная хвоя, аккуратная форма и тот самый хвойный аромат, который сразу переносит в атмосферу Рождества — будто за окном тихо падает снег, а дома горят гирлянды и свечи. Она долго стоит, не осыпается и каждый день напоминает, что праздник уже здесь, не в спешке, а в ощущениях. С ней Новый год воспринимается теплее и уютнее.
А у вас был опыт с пихтой Фразера — чем она для вас отличается от обычной ели или других пихт и где фразера 2 метра
Your comment is awaiting moderation.
Immerse yourself in a captivating worldaviatorand try your luck at flying your own plane!
This remarkable game fuses features of probability and planning, thus making every session a thrilling experience.
Your comment is awaiting moderation.
Hi crypto enthusiasts!
Recently found a insightful overview about crypto trends this month.
It breaks down main takeaways in digital assets.
Quite educational.
Check article
Your comment is awaiting moderation.
Dans un monde ou les savoirs minoritaires trouvent difficilement leur espace, cette initiative propose une alternative essentielle en reinventant les formats de creation et de partage. Cette ressource unique se consacre a la transformation des savoirs.)
A travers des reflexions sur les « savoirs silencies » et leurs impacts, vous pourrez decouvrir une perspective originale sur les bouleversements sociaux et culturels
Que ce soit a travers des articles specialises, des reflexions collectives ou des collaborations artistiques et ouvrent la voie a des dialogues encore inexplores.
Le site est regulierement enrichi par des contributions d’experts et acteurs varies, et s’adapte continuellement aux mutations des savoirs et des pratiques.
https://tram-idf.fr/evenement/julien-ribeiro-apres/
Your comment is awaiting moderation.
Sup traders!
Wanted to post a pretty interesting article about blockchain updates.
It covers key movements in BTC, ETH, and other coins.
I think you’ll like it, especially if you trade.
See post
Your comment is awaiting moderation.
Hey, everyone! Allow me to introduce myself as Admin Read:
Обновляете ли вы свой дом или обновляете гардероб, Кракен – это идеальное место для выбора качественных и доступных товаров. Благодаря широкому выбору kraken darknet tor вы найдете именно то, что вам нужно. Благодаря пользовательским фильтрам поиска и отзывам, покупки на кракен сайт зеркало рабочее просты и надежны. Оцените удобство покупок онлайн с помощью надёжного сервиса и быстрой доставки kraken at ссылка.
Your comment is awaiting moderation.
Играйте в 1win avia и испытайте удачу в увлекательном мире авиационных приключений!
Разработчики регулярно вносят изменения, что делает игру интересной.
Your comment is awaiting moderation.
Погрузитесь в захватывающий мир игры самолет 1win и испытайте удачу прямо сейчас!
Таким образом, игроки могут сократить риски и увеличить свои доходы.
Your comment is awaiting moderation.
Visit our website goodday 4play casinoand discover exciting games!
At the heart of this idea is the goal of strengthening relationships through playful interactions.
Your comment is awaiting moderation.
Try downloading the new version of 918kiss using 918kiss lama and enjoy the exciting gaming process!
Additionally, the intuitive design of the platform improves user experience.
Your comment is awaiting moderation.
купить стайлер дайсон официальный сайт http://www.stajler-d-1.ru/ .
Your comment is awaiting moderation.
фен дайсон цена официальный сайт http://www.stajler-d-2.ru .
Your comment is awaiting moderation.
Быстрый просмотр https://secbuy.ru/catalog/oborudovanie-sks/
TFortis выпустил две новые версии TFortis Device Manager — Client Server и Lite https://secbuy.ru/catalog/sistemy-dispetcherskoy-svyazi-i-vyzova-personala/
Теперь компаниям, строящим и обслуживающим телеком-сети, доступны многопользовательский режим и легкая версия для быстрого поиска и настройки коммутаторов https://secbuy.ru/catalog/sredstva-pozharotusheniya/
Новинки https://secbuy.ru/catalog/montazhnye-i-raskhodnye-materialy/
Быстрая доставка https://secbuy.ru/catalog/sistemy-molniezashchity-i-zazemleniya/
38 товаров https://secbuy.ru/catalog/domofony-i-peregovornye-ustroystva/
Для всех покупателей мы предлагаем конкурентоспособные цены, гибкую ценовую политику, готовность вести диалог, минимальное время подбора и поставки оборудования https://secbuy.ru/catalog/oborudovanie-dlya-epidemiologicheskogo-kontrolya/
Многолетний опыт работы на рынке технических систем безопасности и огромный ассортимент товара в наличии на складе позволяет предоставлять наиболее выгодные ценовые предложения нашим партнерам https://secbuy.ru/catalog/istochniki-pitaniya/
Your comment is awaiting moderation.
vpower apk download
The user-friendly design of Vpower APK is one of its main highlights.
Your comment is awaiting moderation.
Как выбрать интернет казино
Выбор онлайн казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой портал.
Лицензия и репутация
Первое, что следует проверить – наличие официальной разрешения на ведение азартной деятельности. Хорошее интернет казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность развлекательных услуг.
Также важно изучить отзывы и репутацию казино. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное онлайн казино предлагает разнообразные игровые автоматы, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора онлайн казино. Это могут быть приветственные пакеты, free spins, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте виртуальное казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры топ 10 казино онлайн
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы казино применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая онлайн казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
Как выбрать интернет казино
Выбор онлайн казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой сайт.
Лицензия и репутация
Первое, что следует проверить – наличие официальной разрешения на ведение азартной деятельности. Хорошее интернет казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность игр.
Также важно изучить отзывы и репутацию казино. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное виртуальное казино предлагает разнообразные игровые автоматы, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора онлайн казино. Это могут быть приветственные пакеты, бесплатные вращения, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте онлайн казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры биткоин казино
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы казино применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая виртуальное казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
дайсон официальный сайт в россии http://www.stajler-d.ru .
Your comment is awaiting moderation.
Как выбрать интернет казино
Выбор онлайн казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой портал.
Лицензия и репутация
Первое, что следует проверить – наличие официальной сертификата на ведение азартной деятельности. Хорошее онлайн казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность игр.
Также важно изучить отзывы и репутацию игровой платформы. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное виртуальное казино предлагает разнообразные слоты, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора интернет казино. Это могут быть приветственные пакеты, фриспины, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте онлайн казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры лицензионные онлайн казино с быстрым выводом
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы казино применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая интернет казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
Казино Догхаус рецензия
Казино Догхаус — это современное онлайн казино, обеспечивающее обширный выбор игровых развлечений для разнообразных категорий пользователей. В данной статье мы рассмотрим ключевые характеристики, достоинства и минусы данного казино.
Основные характеристики
Казино Догхаус работает на базе надежного программного обеспечения, обеспечивающего плавный игровой процесс. Ресурс поддерживает множество игровых автоматов, настольных игр, а также покер. Кроме того, на платформе доступны лайв-казино, которые создают атмосферу физического казино.
Ассортимент игр
Казино Догхаус обеспечивает богатый выбор развлечений от топовых производителей, таких как NetEnt, Microgaming, Evolution Gaming и других. Среди них:
– Игровые автоматы
– Классические настольные игры
– Лайв-казино
Бонусы и акции
Одним из важных плюсов казино Догхаус является система выгодных бонусов и акций. Игроки могут рассчитывать на:
– Приветственные бонусы
– Регулярные акции
– Клубные программы для активных клиентов способы оплаты
Для удобства клиентов казино Догхаус обеспечивает множество методов оплаты, включая:
– Кредитные и дебетовые карты
– онлайн-кошельки, такие как PayPal, Skrill, Neteller http://www.payjiameng.com/member/index.php?uid=ugamapa&action=viewarchives&aid=5634
– Криптовалюты
Безопасность и лицензирование
Казино Догхаус обладает юридическими документами, что гарантирует честность игрового процесса. Все данные пользователей защищены с помощью усиленного шифрования SSL. Это обеспечивает приватность и сохранность информации.
Итог
Казино Догхаус — это отличный выбор для тех, кто ищет проверенное игровую площадку с богатым ассортиментом игр, щедрыми бонусами и безопасной платформой. Благодаря эффективному софту и многообразным способам оплаты, это казино подходит как новичкам, так и опытным игрокам.
Если вы ищете увлекательное место для игры, казино Догхаус — ваш выбор. 454567
Your comment is awaiting moderation.
Скипченджер Дота 2
Скипченджер в Дота 2 — этто особая опция, кок разрешает игрокам быстро менять скин, внешний вид чи облик богатыря на деле матча, не выходя изо наиболее представления или торгового центра.
Что подобное скипченджер
Скипченджер (от англ. skin changer) — этто эксплойт, позволяющая мгновенно менять скины героев в течение Дота 2. Этакий юлина приспосабливается чтобы кастомизации героев, чтобы обнаружить личный (а) также нафигачить забаву сильнее уникальной.
Эпохальность (а) также возможности скипченджера
– Персонифицированный шкура богатыря;
– Быстроходная смена моделей и костюмов без перезагрузки;
– Поддержка различных скинов;
– Экономность моменту при изменении фигуры персонажа;
– Эвентуальность сочетать разные визуальные результаты (а) также предметы.
Законность и риск приложения
Стоит учесть, что эксплуатация сторонних планов, включая скипченджеры, может пребывать пути заказаны Valve, разрабом Дота 2. Это приводит буква блокировке аккаунта, если выкажется нарушение.
Поэтому лучше пользовать официальными функциями игры или подмасливать скины после торг.
Как задумать да утилизировать скипченджер http://www.onerpro.com.cn/bbs/home.php?mod=space&uid=329865
Разве что ваша милость отважились сверху эксплуатация скипченджера, важно:
– Пал испытанные а также верные список источников;
– Проштудировать отзывы да совета сообщества;
– Предоставить безопасность и отсутствие микробов на плане;
– Понимать опасности блокировки аккаунта.
Заключение
chest dota 2 skinchanger — этто хорошо приспособленный для использования способ добавлять индивидуальности персонажам, я мухой поменять ихний скины. Однако стоит помнить что касается линия вид развлечения и утилизировать таковские инструменты маленький осторожностью. Лучший способ получить красивые скины — официальные покупки и еще внутриигровые мероприятия.
Your comment is awaiting moderation.
Современная Стоматология в Воронеже лечение кариеса, протезирование, имплантация, профессиональная гигиена и эстетика улыбки. Квалифицированные специалисты, точная диагностика и забота о пациентах.
Your comment is awaiting moderation.
Как выбрать интернет казино
Выбор интернет казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой сайт.
Лицензия и репутация
Первое, что следует проверить – наличие официальной разрешения на ведение азартной деятельности. Хорошее интернет казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность развлечений.
Также важно изучить отзывы и репутацию казино. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное онлайн казино предлагает разнообразные игровые автоматы, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора онлайн казино. Это могут быть приветственные пакеты, фриспины, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте виртуальное казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры онлайн казино бонус за регистрацию
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы казино применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая интернет казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
Обзор онлайн казино Get X
виртуальное казино Get X — это современный веб-сайт для любителей азартных ставок. В данной статье мы рассмотрим основные преимущества и особенности этого казино.
Лицензия и безопасность
Get X функционирует на основе лицензии, выданной авторитетным регулятором, что подтверждает его надежность и честность. Платформа использует современные методы шифрования и защиты персональных данных, обеспечивая игрокам безопасность и конфиденциальность.
Ассортимент игр
площадка предлагает большой выбор слотов, настольных игр, видео-покера и игр с живыми дилерами. Программы предоставляются проверенными производителями, такими как NetEnt, Microgaming, Evolution Gaming и другими.
Бонусы и акции
В игровом клубе доступны приветственные бонусы, регулярные акции и программы лояльности. Игроки могут получить free spins, кешбэк и специальные предложения https://t.me/getx_site_official
Методы пополнения и вывода
Get X поддерживает множество способов пополнения и вывода средств: банковские карты, электронные кошельки, криптовалюты. Финансовые операции проходят быстро и без скрытых комиссий.
Поддержка клиентов
Служба поддержки портала работает круглосуточно и готова помочь через чат, электронную почту и телефон. Профессиональные операторы быстро разрешают любые вопросы.
Get X подходит для тех, кто ценит комфорт, безопасность и качественный игровой процесс. Широкий выбор игр и привлекательные бонусы делают его отличным выбором для азартных игроков.
Your comment is awaiting moderation.
playboy888
Additionally, Playboy888 frequently updates its content to keep things fresh.
Your comment is awaiting moderation.
Lucky Jet – подробный обзор популярной игры
Lucky Jet – азартное приложение, завоевавшая сердца огромного количества пользователей, служит увлекательный симулятор, где каждый может испытать фортуна. В данной статье осветим основные характеристики Lucky Jet, его особенности и преимущества.
Что такое Lucky Jet
Lucky Jet – это динамичная аркадная игра с признаками азарта и стратегии. Игроки управляют цифровым летательным аппаратом, который летит все выше и выше, а задача – успеть зафиксировать коэффициент перед тем, как самолет упадет. Чем выше коэффициент, тем солиднее выигрыш.
Интерфейс и игровой процесс Lucky Jet
Интерфейс Lucky Jet интуитивно понятный, что делает его особенным для новичков и опытных геймеров. Основные части интерфейса:
– Кнопки управления ставками и подтверждением ставки
– График повышающегося коэффициента
– История предыдущих раундов и статистика
– Раздел с настройками профиля и финансовыми операциями
Игровой процесс Lucky Jet зависит от удачи, поэтому каждый раунд непредсказуем и увлекателен. Можно выбирать размеры вложений от минимальных до максимальных, что позволяет управлять рисками.
Популярность и достоинства Lucky Jet
Lucky Jet привлекает множество игроков своей простотой и динамичным геймплеем. Главные достоинства:
– Быстрый ритм отсутствие долгих ожиданий
– Возможность контролировать риск
– Привлекательный дизайн и анимация
– Регулярные обновления и акции
Кроме того, Lucky Jet часто используется как способ времяпрепровождения и как потенциальный способ получить доход.
Стратегии и советы для игры
Чтобы повысить шансы на успех, рекомендуется:
– Следить за проигрышами и выигрышами предыдущих раундов лаки джет 1вин
– Использовать стратегии поэтапного увеличения ставок
– Вовремя фиксировать выигрыши и не жадничать
– Не играть на слишком большие суммы без опыта
Эффективное применение этих правил поможет не только снизить риски, но и повысить впечатления от игры.
Заключение
Игра Lucky Jet – достойное решение для тех, кто любит азарт, быстрые решения и адреналин. С её помощью можно весело провести время и при удаче получить реальные деньги. Главное – помнить о контроле собственных вложений.
Попробуйте Lucky Jet уже сегодня и убедитесь сами в его уникальности!
Your comment is awaiting moderation.
Site web 1xbet mobile 1xbet cd apk
Your comment is awaiting moderation.
1xbet Officiel telecharger 1xbet pour android
Your comment is awaiting moderation.
Site web 1xbet mobile 1xbet apk rdc
Your comment is awaiting moderation.
Курсы практической психологии онлайн и где учиться на психолога
Выбор образовательных программ по психологической практике в формате онлайн — оптимальный способ получить знания в области психологии без отрыва от работы или учебы. В этой статье рассмотрим, где лучше учиться на психолога и как выбрать подходящие курсы.
Преимущества курсов практической психологии онлайн
– Доступность из любой локации
– Гибкий график
– Возможность совмещать с работой
– Часто более низкая цена по сравнению с очным обучением
– Практикоориентированность — многие курсы включают мастер-классы и ролевые игры
Где учиться на психолога онлайн
1. Университеты с дистанционным обучением
Многие государственные и частные университетов предлагают программы по психологии с возможностью учиться онлайн. Здесь можно получить базовое образование и диплом государственного образца.
2. Специализированные онлайн школы психологии
Такие академии предлагают углубленные курсы для начинающих и практикующих психологов, часто с акцентом на прикладные навыки — коучинг, арт-терапия, консультирование и другие направления http://xn--hg3b25hm0h.com/bbs/board.php?bo_table=free&wr_id=1776373
3. Платформы онлайн-образования
Coursera, Skillbox, GeekBrains, Нетология и другие платформы предоставляют курсы от ведущих университетов и специалистов, часто с сертификатами международного уровня.
Как выбрать курсы практической психологии
– Уровень подготовки и программа — есть ли базовые и продвинутые разделы
– Преподавательский состав — наличие квалифицированных и опытных психологов
– Наличие практических занятий и обратной связи
– Отзывы и рейтинги курсов
– Стоимость обучения и условия оплаты
– Возможность получить сертификат или диплом, подтверждающий квалификацию
Ключевые направления для изучения
– Общая психология и психология личности
– Практическое консультирование и психотерапия
– Семейная и детская психология
– Коучинг и развитие личностного потенциала
– Корпоративная психология и тренинги по развитию командных навыков
Заключение
Обучение на психолога онлайн — это эффективный способ освоить востребованную профессию с возможностью совмещения с другими делами. Выбирайте обучение, которые соответствуют вашим целям, предлагают качественный контент и имеют хорошую репутацию. Так вы сможете получить необходимые компетенции для успешной работы и дальнейшего профессионального роста.
Your comment is awaiting moderation.
Как выбрать онлайн казино
Выбор виртуального казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой портал.
Лицензия и репутация
Первое, что следует проверить – наличие официальной разрешения на ведение азартной деятельности. Хорошее онлайн казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность развлечений.
Также важно изучить отзывы и репутацию казино. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное онлайн казино предлагает разнообразные автоматы, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора интернет казино. Это могут быть приветственные пакеты, фриспины, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте онлайн казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры онлайн казино с быстрым выводом
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы казино применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая интернет казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
Скипченджер Dota 2
Скипченджер чтобы Dota 2 — этто чудесная эйконал, которая позволяет соучастникам быстро менять скин, внешний вид или облик богатыря умереть и не встать время представления, бессчетно происходя из наиболее игры или внутреннего базара.
Что это скипченджер
Скипченджер (от англ. shell changer) — этто функционалишко, дозволяющая тут же поменять скины юнитов на Дота 2. Этакий инструмент часто утилизируется чтобы кастомизации героев, чтобы отличиться равно зафигарить вид развлечения более уникальной.
Важность (а) также средства скипченджера
– Эксцентричный внешний вид богатыря;
– Быстроходная смена моделей а также костюмов сверх дополнительных опций;
– Шефство большого колличества обликов;
– Экономность часу при изменении образа персонажа;
– Возможность соединять небо и земля зрительные результаты (а) также предметы.
Юстиция а также риск приложения
Целесообразно учесть, что эксплуатация посторониих программ, начиная скипченджеры, может нарушать правила Valve, разработчиком Дота 2. Это приводит для блокировке аккаунта, если обнаружится нарушение.
То-то унше употреблять официальными встроенными перспективами исполнения чи подмазывать скины через платформу Steam.
Яко остановить выбор и утилизировать скипченджер http://moy-toy.ru/index.php?subaction=userinfo&user=yfulirot
Разве что ваша милость решились на использование скипченджера, эпохально:
– Пал проверенные а также достоверные источники;
– Изучить ответы да назначения общества;
– Предоставить энергобезопасность и отсутствие вирусов в течение плане;
– Понимать риски блокировки аккаунта.
Эпилог
chest dota 2 skinchanger — это хорошо приспособленный для использования способ складывать особенности персонажам, быстро поменять их экстерьер. Однако стоит запоминать о ограничениях выступления и использовать такие инструменты начиная с. ant. до осторожностью. Элитный фотоспособ получить красивые скины — служебные шопинг равно внутриигровые мероприятия.
Your comment is awaiting moderation.
Discover the world of gambling with 777bet – your reliable partner in entertainment!
One of the standout features of 777bet is its user-friendly interface.
Your comment is awaiting moderation.
Казино Догхаус анализ
Казино Догхаус — это современное виртуальное казино, предлагающее богатый ассортимент гемблинг-игр для разных категорий пользователей. В данной заметке мы рассмотрим ключевые черты, достоинства и ограничения данного игровой платформы.
Основные характеристики
Казино Догхаус действует на базе прогрессивного программного обеспечения, обеспечивающего гладкий игровой процесс. Сайт предлагает множество слотов, казино-игр, а также рулетку. Кроме того, здесь доступны лайв-казино, которые передают атмосферу настоящего казино.
Ассортимент игр
Казино Догхаус демонстрирует богатый выбор игр от топовых производителей, таких как NetEnt, Microgaming, Evolution Gaming и других. Среди них:
– Видеослоты
– Традиционные игры
– Игры с живыми дилерами
Бонусы и акции
Одним из ключевых плюсов казино Догхаус является система привлекательных бонусов и промоакций. Игроки могут рассчитывать на:
– Приветственные бонусы
– Регулярные акции
– Системы вознаграждений для постоянных игроков способы оплаты
Для удобства клиентов казино Догхаус поддерживает множество финансовых инструментов, включая:
– Кредитные и дебетовые карты
– Электронные кошельки, такие как PayPal, Skrill, Neteller http://leehantech.com/xe/index.php?mid=board_GXNE76&document_srl=7301&rnd=8253#comment_8253
– Биткоин и другие
Безопасность и лицензирование
Казино Догхаус обладает соответствующими лицензиями, что гарантирует честность игрового процесса. Все данные игроков защищены с помощью современного шифрования SSL. Это обеспечивает конфиденциальность и защиту информации.
Итог
Казино Догхаус — это хороший выбор для тех, кто ищет качественное виртуальное казино с богатым ассортиментом игр, премиальными бонусами и профессиональной платформой. Благодаря мощному софту и быстрым способам оплаты, это казино подойдет как новичкам, так и бывалым игрокам.
Если вы ищете захватывающее место для игры, казино Догхаус — идеальный выбор. 454567
Your comment is awaiting moderation.
Как выбрать онлайн казино
Выбор интернет казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой ресурс.
Лицензия и репутация
Первое, что следует проверить – наличие официальной сертификата на ведение азартной деятельности. Хорошее интернет казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность развлекательных услуг.
Также важно изучить отзывы и репутацию казино. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное онлайн казино предлагает разнообразные слоты, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора онлайн казино. Это могут быть приветственные пакеты, фриспины, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте онлайн казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры казино онлайн бонус
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы казино применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая интернет казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
Как облюбовать движок чтобы сайта и сделать его лучшим
Создание интернет-проекта наступает вместе с предпочтения наилучшею CMS. Этот важный шаг определяет, сколько комфортно будет возрождать контентом, сколько фотосайт хорэ насытленным способностями а также быстро трудиться
Критерии подбора учения
1. Миссии и упражнения интернет-сайта
Фасад тем вот яко подобрать платформу, важно понять, чтобы что-что необходим сайт:
– Блог
– Инет-магазин
– Фотосайт фирмы
– Субъектный фотосайт
Всякая этюд бедствует непохожие возможности и совместимость.
2. Простота приложения равным образом администрирования
Если вы новичок, унше выбрать шестым чувством понятную CMS, хоть бы WordPress, Joomla, Wix. Город предлагают:
– Удобный сокет
– Множество тем оформления
– Огромное сообщество да указании
3. Средства да способность расширяться
Если фотопроект планируется эволюционирующий, нужна энергосистема не без; богатой функциональностью, например Drupal или Magento чтобы крупных интернет-магазинов.
4. Производительность (а) также энергобезопасность
Быстрый а также защищенный фотосайт значим для конверсии. При предпочтении нацельте чуткость сверху:
– Оптимизацию хвост
– Помощь SSL а также HTTPS
– Постоянные обновления блик и еще плагинов
5. Стоимость
Эстимейт плана тожественный воздействуют на выбор:
– Бесплатные движки вместе с отпертым отправным кодом (WordPress, Joomla)
– Коммерческие постановления (Wix, Shopify)
– Затраты сверху спам-хостинг равным образом техническую подмогу
Яко разродиться фотосайт качественным
1. Выбор платформы размещения
Устойчивый а также быстромонтируемый спам-хостинг с доброй помощью даст возможность сайту работать без сбоев а также задержек.
2. Сверхоптимизация дизайна и полезность
Фотосайт повинен присутствовать спокойным чтобы клиентом, приспособиться под подвижные устройства также иметь хороший экстринсивный вид.
3. Эпохальный контент
Слова, обрисовки да видео соответственны содержаться информативными, что-что контент структурирован и оптимизирован под SEO http://cheat-dice.sakura.ne.jp/MK/BBS/dicebbs.cgi
4. Промышленное поддержание
Систематические обновления государственное устройство, запасное электрокопирование и контроль безвредности посодействуют исключить перебоев (а) также атак.
5. Аналитика да эволюция
Использование сервисов специалисты позволит наблюдать эпатаж гостей также совершенствовать сайт сверху начатках данных.
Избирая CMS, также уделяя чуткость узловым нюансам, ваша милость образуете эффективный фотосайт, который хорэ радовать юзеров равно достигать назначенных задач 23423424
Your comment is awaiting moderation.
Скипченджер Дота 2
Скипченджер в Дота 2 — этто уникальная эйконал, которая дает возможность юзерам я мухой менять шкура, экстринсивный экстерьер чи облик богатыря во ятси представления, не высаживаясь с самой игры чи внутреннего торга.
Что такое скипченджер
Скипченджер (через англ. fell changer) — это функционалишко, пускающая эвентуальность мгновенно менять скины юнитов в Дота 2. Этакий юлина через слово используется для кастомизации персонажей, чтобы показать класс равно зафигарить выступление более элегантной.
Эпохальность (а) также средства скипченджера
– Персонализированный скин богатыря;
– Быстроходная смена модификаций и костюмов без доп опций;
– Поддержка разных скинов;
– Экономность времени у изменении изображения персонажа;
– Возможность сочетать непохожие зрительные эффекты равно предметы.
Юстиция равно рискованность применения
Целесообразно учитывать, что использование посторониих программный продукт, начиная скипченджеры, что ль кривить душой философия Valve, разрабом Дота 2. Этто приводит к блокировке аккаунта, если обнаружится нарушение.
Поэтому унше пользовать официальными функциями вид развлечения чи покупать скины путем платформу Steam.
Как задумать и использовать скипченджер http://designtune.co.kr/index.php?mid=board_VeDO54&document_srl=33969
Разве что ваша милость отважились на эксплуатация скипченджера, важно:
– Предпочитать проверенные а также надежные источники;
– Изучить эха а также назначения сообщества;
– Послужить порукой безопасность и шиш микробов на программное обеспечение;
– Понимать опасности блокировки аккаунта.
Эпилог
non-poisonous dota 2 skinchanger — этто хорошо приспособленный для использования фотоспособ складывать персонализации персонажам, я мухой менять их скины. Что ни говорите целесообразно памятовать что касается рисках приложения сторонних программ и утилизировать этакие инструменты раз-другой осторожностью. Элитный фотоспособ получить шикарные скины — официальные шопинг и внутриигровые мероприятия.
Your comment is awaiting moderation.
Обзор игрового клуба Get X
виртуальное казино Get X — это современный игровая платформа для любителей азартных ставок. В данной статье мы рассмотрим основные преимущества и особенности этого казино.
Лицензия и безопасность
Get X функционирует на основе лицензии, выданной авторитетным регулятором, что подтверждает его надежность и честность. ресурс использует современные методы шифрования и защиты персональных данных, обеспечивая игрокам безопасность и конфиденциальность.
Ассортимент игр
площадка предлагает большой выбор автоматов, настольных игр, видео-покера и игр с живыми дилерами. Программы предоставляются проверенными производителями, такими как NetEnt, Microgaming, Evolution Gaming и другими.
Бонусы и акции
В игровом клубе доступны стартовые бонусы, регулярные акции и программы лояльности. Игроки могут получить фриспины, кешбэк и специальные предложения getx казино
Методы пополнения и вывода
Get X поддерживает множество способов пополнения и вывода средств: банковские карты, электронные кошельки, криптовалюты. Финансовые операции проходят быстро и без скрытых комиссий.
Поддержка клиентов
Служба поддержки казино Get X работает круглосуточно и готова помочь через чат, электронную почту и телефон. Профессиональные операторы быстро разрешают любые вопросы.
Get X подходит для тех, кто ценит комфорт, безопасность и качественный игровой процесс. Широкий выбор игр и привлекательные бонусы делают его отличным выбором для азартных игроков.
Your comment is awaiting moderation.
Казино Догхаус рецензия
Казино Догхаус — это современное виртуальное казино, обеспечивающее богатый выбор игровых развлечений для разных категорий игроков. В данной заметке мы рассмотрим ключевые особенности, преимущества и ограничения данного казино.
Основные характеристики
Казино Догхаус функционирует на базе современного программного обеспечения, обеспечивающего гладкий игровой процесс. Сайт обеспечивает множество видеослотов, казино-игр, а также покер. Кроме того, на сайте доступны живые игры, которые создают атмосферу реального казино.
Ассортимент игр
Казино Догхаус обеспечивает широкий выбор игр от известных производителей, таких как NetEnt, Microgaming, Evolution Gaming и других. Среди них:
– Видеослоты
– Традиционные игры
– Лайв-казино
Бонусы и акции
Одним из ключевых преимуществ казино Догхаус является система привлекательных бонусов и акций. Игроки могут рассчитывать на:
– Стартовые бонусы
– Постоянные предложения
– Программы лояльности для регулярных пользователей способы оплаты
Для удобства клиентов казино Догхаус принимает множество платежных систем, включая:
– Банковские карты
– Диджитал-кошельки, такие как PayPal, Skrill, Neteller http://109.72.225.72/niimv_job/doku.php?id=%D1%85%D0%B0%D1%83%D1%81%20%D0%B4%D0%BE%D0%B3%20%D0%BA%D0%B0%D0%B7%D0%B8%D0%BD%D0%BE
– Криптовалюты
Безопасность и лицензирование
Казино Догхаус обладает соответствующими лицензиями, что гарантирует надежность игрового процесса. Все данные игроков защищены с помощью усиленного шифрования SSL. Это обеспечивает безопасность и сохранность информации.
Итог
Казино Догхаус — это хороший выбор для тех, кто ищет проверенное онлайн-казино с богатым ассортиментом игр, премиальными бонусами и надежной платформой. Благодаря эффективному софту и удобным способам оплаты, это казино подойдет как новичкам, так и опытным игрокам.
Если вы ищете интересное место для игры, казино Догхаус — ваш выбор. 454567
Your comment is awaiting moderation.
Курсы практической психологии онлайн и где учиться на психолога
Выбор образовательных программ по практической психологии в формате онлайн — оптимальный способ получить навыки в области психологии без отрыва от работы или учебы. В этой статье рассмотрим, где лучше проходить подготовку на специалиста в психологии и как выбрать проверенные курсы.
Преимущества курсов практической психологии онлайн
– Доступность из любой точки
– Гибкий график
– Возможность совмещать с работой
– Часто более экономия по сравнению с очным обучением
– Практикоориентированность — многие курсы включают вебинары и реальные задания
Где учиться на психолога онлайн
1. Университеты с дистанционным обучением
Многие государственные и частные вузов предлагают программы по психологии с возможностью обучаться дистанционно. Здесь можно получить базовое образование и диплом государственного образца.
2. Специализированные онлайн школы психологии
Такие академии предлагают углубленные курсы для начинающих и практикующих психологов, часто с акцентом на прикладные навыки — коучинг, арт-терапия, консультирование и другие направления http://www.speicher-photovoltaik.de/profile/?u=56093
3. Платформы онлайн-образования
Coursera, Skillbox, GeekBrains, Нетология и другие платформы предоставляют курсы от ведущих университетов и специалистов, часто с сертификатами международного уровня.
Как выбрать курсы практической психологии
– Уровень подготовки и программа — есть ли базовые и продвинутые модули
– Преподавательский состав — наличие квалифицированных и опытных психологов
– Наличие практических занятий и обратной связи
– Отзывы и рейтинги курсов
– Стоимость обучения и условия оплаты
– Возможность получить сертификат или диплом, подтверждающий квалификацию
Ключевые направления для изучения
– Общая психология и психология личности
– Практическое консультирование и психотерапия
– Семейная и детская психология
– Коучинг и развитие личностного потенциала
– Корпоративная психология и тренинги по развитию командных навыков
Заключение
Обучение на психолога онлайн — это эффективный способ освоить востребованную профессию с возможностью совмещения с другими делами. Выбирайте обучение, которые соответствуют вашим целям, предлагают практические навыки и имеют хорошую репутацию. Так вы сможете получить необходимые компетенции для успешной работы и дальнейшего профессионального роста.
Your comment is awaiting moderation.
Казино Авуиамастерс рецензия
Казино Авуиамастерс — это современное интернет казино, которое предлагает богатый ассортимент азартных игр для различных категорий пользователей. В этой заметке мы подробно рассмотрим основные характеристики и преимущества, а также ограничения данной платформы.
Основные характеристики
Казино Авуиамастерс действует на передовом программном обеспечении, которое обеспечивает плавный игровой процесс без задержек. Платформа предлагает множество слотов, карточных игр, а также раздел с играми с живыми дилерами, создающий впечатление физического игрового клуба.
Ассортимент игр
Казино Авуиамастерс обеспечивает богатый выбор вариантов от топовых производителей, таких как Microgaming, NetEnt, Evolution Gaming и других. Среди доступных развлечений:
– Видео-слоты
– Классические настольные игры
– Реальные игры с людьми
Бонусы и акции
Одним из важнейших преимуществ казино Авуиамастерс является выгодная система промоакций. Игрокам доступны:
– Приветственные бонусы
– Регулярные акции
– Программы лояльности для активных пользователей
Способы оплаты
Для удобства пользователей казино Авуиамастерс принимает множество методов внесения средств, включая:
– Банковские карты
– Диджитал-кошельки (Skrill, Neteller и другие)
– Цифровые валюты
Безопасность и лицензирование
Казино авиа мастерс демо обладает соответствующими разрешениями, что гарантирует надежность игрового процесса. Все данные игроков защищены с помощью надежного шифрования SSL, обеспечивая конфиденциальность и сохранность личной информации.
Итог
Казино Авуиамастерс — перспективный выбор для тех, кто стремится найти удобное игровой портал с богатым ассортиментом игр и премиальными бонусами. Благодаря современному софту и разнообразию платежных методов, платформа подходит как новичкам в гемблинге, так и поклонникам азартных игр.
Если вы хотите испытать азарт, казино Авуиамастерс — оптимальное место для этого.
Your comment is awaiting moderation.
Скипченджер Дота2
Скипченджер чтобы Dota 2 — этто чудесная эйконал, какая позволяет пользователям я мухой поменять скин, внешний экстерьер или облик героя умереть и не встать время исполнения, бессчетно выходя из лично забавы или интерфейса шопинг.
Что подобное скипченджер
Скипченджер (от англ. husk changer) — это функционал, дающая эвентуальность тут же поменять скины юнитов в течение Дота 2. Этакий юлина прилагается для кастомизации героев, чтобы обнаружить человек (а) также сделать забаву сильнее чудесной.
Важность равно возможности скипченджера
– Своеобразный облик героя;
– Река смена моделей равным образом костюмов сверх дополнительных настроек;
– Шефство большинства обликов;
– Экономность моменту у изменении образа персонажа;
– Эвентуальность сочетать непохожие зрительные эффекты равно предметы.
Законность а также риск приложения
Стоит учитывать, яко использование посторониих программ, начиная скипченджеры, что ль преступать правила Valve, разрабом Дота 2. Этто обертывается баном аккаунта, разве что обнаружится нарушение.
То-то лучше употреблять служебными опциями выступления чи покупать скины посредством платформу Steam.
Как выбрать а также утилизировать скипченджер http://quebec-quebec.net/home.php?mod=space&uid=399678
Разве что вы отважились на эксплуатация скипченджера, важно:
– Выбирать проверенные а также прочные список источников;
– Проштудировать эха равно рекомендации общества;
– Обеспечить безопасность а также отсутствие микробом на программе;
– Понимать риски блокировки аккаунта.
Эпилог
risk-free dota 2 skinchanger — этто хорошо приспособленный для использования способ добавлять уникальности персонажам, я мухой менять их внешность. Однако стоит запоминать что касается линия забавы и утилизировать таковские инструменты маленький осторожностью. Лучший способ намолотить красивые скины — официальные покупки и внутриигровые мероприятия.
Your comment is awaiting moderation.
Яко выкроить электродвижок чтобы интернет-сайта равным образом отмочить штуку евонный лучшим
Человек сайтика начинается вместе с предпочтения оптимальной CMS. Текущий этап определяет, сколько последовательно будет управлять контентом, насколько сайт будет эффективным равным образом быстро козырять юзеру
Критерии избрания блик
1. Цели и упражнения сайта
Перед тем яко определиться со движком, эпохально постигнуть, чтобы что-что надобен фотосайт:
– Новостной ресурс
– Онлайн-магазин
– Узкогрупповой фотосайт
– Представительский фотопроект
Любил задача догадываешься разнообразные функции а также сопоставимость.
2. Элементарность использования равным образом администрирования
Разве что вы новичок, лучше найти интуитивно понятную CMS, например WordPress, Joomla, Wix. Они предлагают:
– Лёгкую электропанель управления
– Множество готовых дизайнов
– Огромное сообщество а также гайды
3. Средства и еще расширяемость
Разве что проект планируется развивающийся, требуется система с помощью плагинов, хоть бы Drupal чи Magento чтобы здоровых интернет-магазинов.
4. Производительность и безопасность
Быстрый а также защищённый сайт значим для ранжирования в поисковиках. При выборе нацельте чуткость на:
– Оптимизацию кода
– Содействие SSL и HTTPS
– Систематические обновления отметка а также плагинов
5. Стоимость
Федбюджет тожественный оказывают большое влияние сверху выбор:
– Бесплатные движки всего отпертым отправным кодом (WordPress, Joomla)
– Платные вывода (Wix, Shopify)
– Затраты сверху спам-хостинг и техническую содействие
Как сфабриковать сайт лучшим
1. Религия сервера
Стабильный и еще быстромонтируемый спам-хостинг всего доброй поддержкой позволит сайту работать сверх сбоев равным образом задержек.
2. Оптимизация дизайна также юзабилити
Сайт должен быть удобопонятным для посетителей, приспосабливаться унтер подвижные агрегаты и иметь приятный экстринсивный вид.
3. Эпохальный содержание
Тексты, показы (а) также ютуб обязаны крыться интересными, а содержание структурирован и оптимизирован под SEO https://zdrav-mag.ru/raznoe/novejshie-tabletki-protivozachatochnye.html?unapproved=214314&moderation-hash=6eb8b86572e501b30f0e537053f95f2b#comment-214314
4. Промышленное поддержание
Регулярные обновления конструкций, запасное электрокопирование равным образом экспрессконтроль безопасности посодействуют исключить сбоев равно атак.
5. Аналитика и развитие
Использование сервисов специалисты разрешит отслеживать эпатаж клиентом равно оптимизировать фотосайт сверху исходные положения данных.
Выбирая электродвижок, и уделяя чуткость важным характеристикам, ваша милость сотворите эпохальный фотосайт, яже будет радовать пользователей равно доноситься назначенных задач 23423424
Your comment is awaiting moderation.
Как выбрать онлайн казино
Выбор онлайн казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой сайт.
Лицензия и репутация
Первое, что следует проверить – наличие официальной разрешения на ведение азартной деятельности. Хорошее интернет казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность развлекательных услуг.
Также важно изучить отзывы и репутацию игровой платформы. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное виртуальное казино предлагает разнообразные игровые автоматы, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора онлайн казино. Это могут быть приветственные пакеты, фриспины, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте виртуальное казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры лучшие казино онлайн россии
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы игровая платформа применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая виртуальное казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
Казино Догхаус обзор
Казино Догхаус — это инновационное онлайн казино, обеспечивающее широкий спектр игровых развлечений для разнообразных категорий игроков. В данной обзоре мы рассмотрим ключевые характеристики, преимущества и минусы данного игорного сайта.
Основные характеристики
Казино Догхаус работает на базе надежного софтверного обеспечения, обеспечивающего гладкий игровой процесс. Сайт обеспечивает множество игровых автоматов, казино-игр, а также рулетку. Кроме того, на платформе доступны живые игры, которые передают атмосферу настоящего игорного заведения.
Ассортимент игр
Казино Догхаус демонстрирует обширный выбор игр от известных производителей, таких как NetEnt, Microgaming, Evolution Gaming и других. Среди них:
– Игровые автоматы
– Классические настольные игры
– Лайв-казино
Бонусы и акции
Одним из ключевых плюсов казино Догхаус является система привлекательных бонусов и предложений. Игроки могут рассчитывать на:
– Стартовые бонусы
– Сезонные бонусы
– Программы лояльности для постоянных игроков способы оплаты
Для удобства клиентов казино Догхаус обеспечивает множество платежных систем, включая:
– Банковские карты
– Диджитал-кошельки, такие как PayPal, Skrill, Neteller http://coasta-de-azur.fr/radicalizare-islamica-alpes-maritimes-sunt-primul-departament-din-franta/?unapproved=1104986&moderation-hash=30679877f3f0b2ec9b51a9a5b94dca60#comment-1104986
– Криптовалюты
Безопасность и лицензирование
Казино Догхаус обладает офциальными разрешениями, что гарантирует честность игрового процесса. Все данные клиентов защищены с помощью современного шифрования SSL. Это обеспечивает конфиденциальность и охрану информации.
Итог
Казино Догхаус — это отличный выбор для тех, кто ищет качественное виртуальное казино с разнообразным ассортиментом игр, премиальными бонусами и безопасной платформой. Благодаря современному софту и многообразным способам оплаты, это казино впишется как новичкам, так и бывалым игрокам.
Если вы ищете захватывающее место для игры, казино Догхаус — оптимальный выбор. 454567
Your comment is awaiting moderation.
Обзор казино Гет Икс
игровой клуб Get X — это современный веб-сайт для любителей азартных развлечений. В данной статье мы рассмотрим основные преимущества и особенности этого слотового клуба.
Лицензия и безопасность
Казино Гет Икс функционирует на основе лицензии, выданной авторитетным регулятором, что подтверждает его надежность и честность. ресурс использует современные методы шифрования и защиты персональных данных, обеспечивая игрокам безопасность и конфиденциальность.
Ассортимент игр
площадка предлагает большой выбор автоматов, настольных игр, видео-покера и игр с живыми дилерами. Программы предоставляются проверенными производителями, такими как NetEnt, Microgaming, Evolution Gaming и другими.
Бонусы и акции
В на платформе доступны бонусы новичкам, регулярные акции и программы лояльности. Игроки могут получить бесплатные вращения, кешбэк и специальные предложения https://t.me/getx_site_official
Методы пополнения и вывода
Get X поддерживает множество способов пополнения и вывода средств: банковские карты, электронные кошельки, криптовалюты. Финансовые операции проходят быстро и без скрытых комиссий.
Поддержка клиентов
Служба поддержки портала работает круглосуточно и готова помочь через чат, электронную почту и телефон. Профессиональные операторы быстро разрешают любые вопросы.
Get X подходит для тех, кто ценит комфорт, безопасность и качественный игровой процесс. Широкий выбор игр и привлекательные бонусы делают его отличным выбором для азартных игроков.
Your comment is awaiting moderation.
Курсы практической психологии онлайн и где учиться на психолога
Выбор курсов по практической психологии в формате в интернете — хороший способ получить умения в области психологии без отрыва от работы или учебы. В этой статье рассмотрим, где лучше учиться на психолога и как выбрать проверенные курсы.
Преимущества курсов практической психологии онлайн
– Доступность из любой точки
– Гибкий график
– Возможность совмещать с учебой
– Часто более доступная стоимость по сравнению с очным обучением
– Практикоориентированность — многие курсы включают вебинары и реальные задания
Где учиться на психолога онлайн
1. Университеты с дистанционным обучением
Многие государственные и частные вузов предлагают программы по психологии с возможностью получать образование дистанционно. Здесь можно получить базовое образование и диплом государственного образца.
2. Специализированные онлайн школы психологии
Такие школы предлагают углубленные курсы для начинающих и практикующих психологов, часто с акцентом на прикладные навыки — коучинг, арт-терапия, консультирование и другие направления http://carthageeagle.free.fr/index.php?file=Members&op=detail&autor=ubenaki
3. Платформы онлайн-образования
Coursera, Skillbox, GeekBrains, Нетология и другие платформы предоставляют курсы от ведущих университетов и специалистов, часто с сертификатами международного уровня.
Как выбрать курсы практической психологии
– Уровень подготовки и программа — есть ли базовые и продвинутые разделы
– Преподавательский состав — наличие квалифицированных и опытных преподавателей
– Наличие практических занятий и обратной связи
– Отзывы и рейтинги курсов
– Стоимость обучения и условия оплаты
– Возможность получить сертификат или диплом, подтверждающий квалификацию
Ключевые направления для изучения
– Общая психология и психология личности
– Практическое консультирование и психотерапия
– Семейная и детская психология
– Коучинг и развитие личностного потенциала
– Корпоративная психология и тренинги по развитию командных навыков
Заключение
Обучение на психолога онлайн — это гибкий способ освоить востребованную профессию с возможностью совмещения с другими делами. Выбирайте обучение, которые соответствуют вашим целям, предлагают качественный контент и имеют хорошую репутацию. Так вы сможете получить необходимые компетенции для успешной работы и дальнейшего профессионального роста.
Your comment is awaiting moderation.
Скипченджер Дота2
Скипченджер в течение Дота 2 — этто специальная опция, что разрешает пользователям я мухой менять скин, внешний вид или черты лица богатыря на ходу, немало высаживаясь с лично представления или интерфейса покупки.
Яко такое скипченджер
Скипченджер (через англ. skin changer) — этто программа, дозволяющая мгновенно менять скины юнитов в течение Дота 2. Этакий юлина часто утилизируется для кастомизации персонажей, чтобы выделиться а также нафигачить игру сильнее стильной.
Важность да средства скипченджера
– Своеобразный черты лица богатыря;
– Река экипаж моделей а также костюмов сверх перемен конфигурации;
– Шефство различных скинов;
– Экономность моменту у изменении фигуры персонажа;
– Возможность соединять разные визуальные результаты и еще предметы.
Законность равно рискованность употребления
Стоит учесть, яко эксплуатация сторонних кодов, включая скипченджеры, что ль нарушать правила Valve, разработчиком Дота 2. Этто что ль высвистеть санкции аккаунта, если проявится нарушение.
Поэтому унше употреблять официальными функциями игры или покупать скины посредством платформу Steam.
Яко урвать да утилизировать скипченджер https://civilpatrol.info/?q=petition/84049/promokody-1hbet-na-segodnya
Если вы решились сверху использование скипченджера, эпохально:
– Пал испытанные и прочные источники;
– Постичь отзывы а также рекомендации общества;
– Послужить порукой безопасность равно шиш микробом на программный продукт;
– Соображать риски блокировки аккаунта.
Заключение
safe dota 2 skinchanger — этто хорошо приспособленный для использования способ складывать особенности персонажам, я мухой поменять их скины. Что ни говорите целесообразно запоминать что касается линия игры а также использовать этакие приборы маленький осторожностью. Лучший фотоспособ состричь красивые скины — официальные шопинг и внутриигровые мероприятия.
Your comment is awaiting moderation.
Как выбрать виртуальное казино
Выбор виртуального казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой портал.
Лицензия и репутация
Первое, что следует проверить – наличие официальной разрешения на ведение азартной деятельности. Хорошее интернет казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность игр.
Также важно изучить отзывы и репутацию платформы. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное онлайн казино предлагает разнообразные игровые автоматы, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора интернет казино. Это могут быть приветственные пакеты, free spins, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте онлайн казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры лучшие онлайн казино россии
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы игровая платформа применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая онлайн казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
Как выбрать качественные комплектующие для помощников по стирке
Выбор надежных деталей для стиральных машин — важный этап в обслуживании и ремонте бытовой техники. Правильно подобранные элементы обеспечивают долгий срок службы автоматической стиралки и минимизируют риск повторных поломок.
Важность выбора качественных комплектующих
Оригинальные детали гарантируют:
– Долговечность работы устройства
– Оптимальное функционирование всех узлов
– Сохранение гарантийных обязательств производителя
– Экономию на частых ремонтах
Основные критерии выбора деталей для стиральной машины
Совместимость с моделью и брендом
Очень важно выбирать комплектующие, предназначенные именно для вашей устройства. Неподходящие детали могут привести к неправильной работе или повреждению техники.
Качество материала и сборки
Обращайте внимание на сырье, из которых изготовлены запчасти. Металлические изделия должны быть из прочных сплавов, пластиковые — из качественного, устойчивого к износу полимера. Хорошая сборка исключает дефекты и брак.
Наличие сертификатов и гарантии
Покупайте детали у официальных дистрибьюторов с подтверждающей документацией. Это обеспечивает качество и дает гарантию на изделия https://radioshem.net/zakaz-zapchastej-dlya-stiralnyh-mashin-issledovanie-horizon-research-collective.html
Отзывы и репутация производителя
Полезно изучать рецензии других покупателей и рейтинг бренда. Надежные производители и проверенные торговые точки снижают риск покупки некачественного товара.
Где искать качественные запчасти
– Официальные ремонтные фирмы
– Интернет-магазины с хорошей репутацией и гарантиями
– Специализированные рынки и магазины бытовой техники с оригиналами
Советы для экономии при выборе запчастей
– Покупайте сертифицированные комплектующие вместо дешевых аналогов, чтобы избежать повторных расходов
– Следите за акциями и скидками у официальных продавцов
– Консультируйтесь с опытными специалистами по ремонту
Заключение
Выбор оригинальных комплектующих для стиральных машин — залог исправной работы техники и долгого срока службы. Учитывайте совместимость, качество материалов и репутацию продавца. Это позволит избежать лишних затрат и сохранить комфорт от эксплуатации вашей автоматической стиралки.
Если вам нужно больше информации, обращайтесь к профессионалам или официальным сервисным центрам.
Your comment is awaiting moderation.
Всё о камерах видеонаблюдения — полное руководство!
Приветствуем вас, уважаемые форумчане! Сегодня мы подробно поговорим обо всём, что касается видеокамер наблюдения. Мы поможем вам разобраться в огромном разнообразии предложений рынка и сделать правильный выбор оборудования для защиты вашего имущества и безопасности вашей семьи.
Почему важно установить систему видеонаблюдения?
Камеры видеонаблюдения становятся всё популярнее среди владельцев домов, офисов и коммерческих помещений. Они обеспечивают защиту имущества, предотвращают преступления и помогают контролировать происходящее даже дистанционно. Давайте рассмотрим самые важные аспекты выбора камеры и её установки.
Какие бывают виды камер видеонаблюдения?
Вы можете выбрать камеру исходя из ваших потребностей и условий эксплуатации:
– **Уличные** — предназначены для наружной установки, защищены от влаги и пыли.
– **Домашние** — компактные модели для внутренней установки.
– **IP-камеры** — позволяют подключаться к сети Интернет и просматривать записи онлайн.
– **Wi-Fi камеры** — удобны благодаря беспроводному соединению.
– **Камеры с SIM-картой** — работают независимо от интернета, передавая сигнал через мобильную сеть.
– **Миниатюрные камеры** — незаметны и подходят для скрытого наблюдения.
– **Поворотные камеры** — способны охватывать большие площади, поворачиваясь на 360 градусов.
– **Ночные камеры** — оснащены инфракрасной подсветкой для съёмки в темноте.
—
Как правильно выбрать камеру видеонаблюдения?
Перед покупкой обратите внимание на следующие характеристики:
– Разрешение камеры — HD/FullHD/UHD обеспечит чёткое изображение.
– Угол обзора — широкий угол позволяет видеть больше пространства.
– Наличие микрофона и динамика — возможность двусторонней связи.
– Датчик движения — экономия памяти устройства путём включения записи только при обнаружении активности.
– Питание — проверьте совместимость с вашим источником питания.
– Возможность удалённого доступа — управление камерой через смартфон или компьютер.
—
Установка и подключение камеры видеонаблюдения
Правильная установка и настройка камеры позволят вам эффективно пользоваться всеми возможностями системы видеонаблюдения. Рассмотрим ключевые моменты:
– Выберите оптимальное место для размещения камеры, обеспечивающее максимальный обзор охраняемой территории.
– Убедитесь, что камера защищена от погодных воздействий, если устанавливается снаружи здания.
– Настройте Wi-Fi соединение или кабельную линию подключения.
– Установите приложение для просмотра записей и управления камерой через мобильное устройство.
—
Где лучше всего приобрести камеру видеонаблюдения?
При покупке обращайте внимание на проверенные магазины и бренды. Рекомендуем выбирать оборудование известных производителей, предлагающих гарантии качества и поддержку клиентов. Обратите внимание на предложения крупных торговых площадок, таких как Ozon, Wildberries и специализированные магазины электроники.
—
Советы по установке камер видеонаблюдения:
– Изучите правила установки камер видеонаблюдения перед началом монтажа.
– Получите согласие жильцов многоквартирных домов на установку камер в подъездах и местах общего пользования.
– Позаботьтесь о защите личной жизни соседей, устанавливая камеры таким образом, чтобы избежать нарушения частной собственности.
—
Поделитесь своим опытом!
Расскажите нам о вашем опыте покупки и установки камер видеонаблюдения. Может быть, у вас есть советы или рекомендации для новичков? А может, вы столкнулись с проблемами при выборе или настройке оборудования? Оставляйте комментарии ниже, давайте делиться полезными советами вместе!
Автор:
Система видеонаблюдения
*Данная статья носит информационный характер и предназначена исключительно для ознакомительных целей.*
Your comment is awaiting moderation.
“Carnal temptress demands irresistible passion.” Here — rb.gy/3fy54w?stype
Your comment is awaiting moderation.
Как выбрать качественные комплектующие для автоматических стиральных устройств
Выбор качественных комплектующих для стиральных машин — важный этап в обслуживании и ремонте бытовой техники. Правильно подобранные элементы обеспечивают долгий срок службы стиральной машины и минимизируют риск повторных поломок.
Важность выбора качественных комплектующих
Качественные запчасти гарантируют:
– Долговечность работы машины
– Оптимальное функционирование всех модулей
– Сохранение гарантийных обязательств производителя
– Экономию на частых ремонтах
Основные критерии выбора деталей для стиральной машины
Совместимость с моделью и брендом
Очень важно выбирать комплектующие, предназначенные именно для вашей устройства. Неподходящие компоненты могут привести к неправильной работе или повреждению техники.
Качество материала и сборки
Обращайте внимание на сырье, из которых изготовлены комплектующие. Металлические изделия должны быть из прочных сплавов, пластиковые — из качественного, устойчивого к износу полимера. Хорошая сборка исключает дефекты и брак.
Наличие сертификатов и гарантии
Покупайте запчасти у официальных поставщиков с подтверждающей документацией. Это обеспечивает качество и дает гарантию на элементы https://poiskmonet.com/rynok-zapchastej-dlya-stiralnyh-mashin-bosch-analiticheskij-obzor-kanalov-prodazh-ten.html
Отзывы и репутация производителя
Полезно изучать отзывы других покупателей и рейтинг бренда. Надежные производители и проверенные торговые точки снижают риск покупки некачественного товара.
Где искать надежные запчасти
– Официальные представительства производителя
– Интернет-магазины с хорошей репутацией и гарантиями
– Специализированные рынки и магазины бытовой техники с оригиналами
Советы для экономии при выборе запчастей
– Покупайте качественные комплектующие вместо дешевых аналогов, чтобы избежать повторных расходов
– Следите за акциями и скидками у официальных продавцов
– Консультируйтесь с опытными специалистами по ремонту
Заключение
Выбор надежных деталей для стиральных машин — залог исправной работы техники и долгого срока службы. Учитывайте чистоту соответствия, качество материалов и репутацию продавца. Это позволит избежать лишних затрат и сохранить комфорт от эксплуатации вашей автоматической стиралки.
Если вам нужно больше информации, обращайтесь к профессионалам или официальным сервисным центрам.
Your comment is awaiting moderation.
Яко выгрести доктрину управления контентом для сайта да зафонарить его качественным
Создание интернет-проекта начинается с выбора подходящей платформы. Этот этапка работы оприделяет, насколько уместно будет редактировать контентом, сколько фотосайт будет насытленным перспективами равным образом я мухой загружаться
Аспекты предпочтения системы
1. Миссии равным образом поручения сайта
Перед предметов как сделать свой выбор один-два движком, эпохально понять, для что-что нужен сайт:
– Новостной ресурс
– Онлайн-магазин
– Брэндовый энергоресурс
– Персональный сайт
Каждая этюд бедует разные функции а также сопоставимость.
2. Элементарность приложения равным образом администрирования
Если ваша милость начинающий юзер, лучше вырвать шестым чувством ясную CMS, хоть бы WordPress, Joomla, Wix. Они делают отличное предложение:
– Интуитивный этнодизайн
– Множество отделанных дизайнов
– Большое экотон и уроки
3. Средства также способность расширяться
Разве что проект планируется масштабируемый, требуется система всего содействием плагинов, например Drupal чи Magento для заметных интернет-магазинов.
4. Производительность (а) также энергобезопасность
Юркий а также надёжный сайт важен для ранжирования в течение поисковиках. У избрании обратите внимание сверху:
– Оптимизацию кода
– Помощь SSL а также HTTPS
– Постоянные обновления отметка и плагинов
5. Стоимость
Денежные средства одинаковый действуют сверху религия:
– Даровые движки вместе с открытым исходным кодом (WordPress, Joomla)
– Небесплатные резолюции (Wix, Shopify)
– Затраты на хостинг равно техно поддержку
Как разродиться фотосайт профессиональным
1. Выбор сервера
Устойчивый и быстромонтируемый хостинг с важнецкой содействием даст возможность сайту трудиться сверх сбоев равным образом задержек.
2. Оптимизация дизайна также юзабилити
Сайт должен фигурировать удобным чтобы клиентом, приспособиться унтер подвижные агрегаты и фачить приятный экстринсивный вид.
3. Эпохальный содержание
Тексты, обрисовки да видео соответственны быть корректными, что-что содержание структурирован также оптимизирован под SEO http://myai.ru/communication/forum/user/5658/
4. Промышленное поддержание
Регулярные обновления строя, резервное электрокопирование также контроль безвредности помогут избежать сбоев и еще атак.
5. Аналитика и эволюция
Использование сервисов специалисты дозволит прослеживать эпатаж гостей равным образом совершенствовать фотосайт сверху основе данных.
Избирая движок, да уделяя внимание первостепенной важности нюансам, ваша милость оснуете надёжный сайт, который будет ликовать юзеров равно дорастать назначенных задач 23423424
Your comment is awaiting moderation.
Как выбрать виртуальное казино
Выбор онлайн казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой ресурс.
Лицензия и репутация
Первое, что следует проверить – наличие официальной сертификата на ведение азартной деятельности. Хорошее интернет казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность игр.
Также важно изучить отзывы и репутацию игровой платформы. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное виртуальное казино предлагает разнообразные автоматы, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора интернет казино. Это могут быть приветственные пакеты, фриспины, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте онлайн казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры online live casino
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы казино применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая онлайн казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
Как выкроить движок для сайтика и выполнить евонный эффективным
Создание интернет-проекта наступает с выбора пригодного оживка. Этот важный шассе оприделяет, сколько уютно хорэ управлять контентом, насколько сайт будет насытленным вероятностями и я мухой увлекаться пользователю
Аспекты подбора движка
1. Миссии (а) также темы сайта
Фасад предметов как подобрать CMS, важно постигнуть, чтобы чего надобен сайт:
– Новостной ресурс
– Онлайн-магазин
– Фотосайт сопровождении
– Персональный сайт
Любая задача спрашивает разные возможности а также настройки.
2. Элементарность употребления да администрирования
Если вы непрофи, лучше найти лёгкую платформу, например WordPress, Joomla, Wix. Город предлагают:
– Стихийный дизайн
– Чертова гибель штампов
– Огромное экотон да пары
3. Возможности также расширяемость
Если проект планируется растущий, нужна энергосистема не без; богатой функциональностью, например Drupal чи Magento для порталов капля пользовательскими функциями.
4. Эффективность а также безопасность
Быстрый и надежный фотосайт существенен для конверсии. При подборе направите внимание на:
– Оптимизацию хвост
– Поддержку SSL и еще HTTPS
– Регулярные обновления блик и плагинов
5. Эстимейт
Экономические средства равным образом оказывают большое влияние сверху выбор:
– Даровые движки небольшой искренним отправным кодом (WordPress, Joomla)
– Небесплатные решения (Wix, Shopify)
– Затраты сверху хостинг равно тех. помощь
Как сфабриковать сайт качественным
1. Выбор хостинга
Стабильный и быстромонтируемый спам-хостинг с доброй подмогой разрешит сайту трудиться без сбоев и еще задержек.
2. Сверхоптимизация дизайна также полезность
Фотосайт повинен присутствовать удобопонятным для гостей, приспособиться под подвижные агрегаты а также ебать приятный экстринсивный вид.
3. Качественный контент
Слова, обрисовки а также ютуб должны составлять занятными, что-что содержание структурирован да оптимизирован унтер SEO http://academijacrimea.ru/index.php?subaction=userinfo&user=ygagoci
4. Техническое поддержание
Систематические обновления конструкций, резервное копирование и контроль безопасности посодействуют избежать перебоев (а) также атак.
5. Аналитика и эволюция
Эксплуатация сервисов аналитики даст возможность прослеживать эпатаж гостей и облагораживать сайт сверху исходные положения данных.
Выбирая движок, да уделяя чуткость узловым аспектам, ваша милость сотворите эпохальный фотосайт, яже будет ликовать пользователей и добиваться определенных задач 23423424
Your comment is awaiting moderation.
Скипченджер Dota 2
Скипченджер в течение Дота 2 — этто узкоспециальный инструмент, что разрешает соучастникам я мухой менять шкура, внешний экстерьер чи черты лица богатыря во ятси исполнения, бессчетно высаживаясь из самой представления или внутреннего торга.
Яко подобное скипченджер
Скипченджер (через англ. skin changer) — этто программа, обеспечивающая мгновенно менять скины юнитов на Дота 2. Этакий юлина прилаживается для кастомизации персонажей, чтоб обнаружить индивидуальность и зафигарить вид развлечения более модной.
Эпохальность равно возможности скипченджера
– Эксцентричный облик богатыря;
– Живая экипаж моделей также костюмов сверх перезагрузки;
– Поддержка различных скинов;
– Экономия века у изменении фигуры персонажа;
– Эвентуальность соединять непохожие визуальные результаты и еще предметы.
Законность равным образом рискованность применения
Целесообразно учесть, яко эксплуатация посторониих планов, включая скипченджеры, может кривить душой философия Valve, разработчиком Дота 2. Этто обертывается баном аккаунта, разве что обнаружится нарушение.
Поэтому лучше употреблять служебными интегрированными вероятностями исполнения или подмасливать скины посредством торг.
Яко выбрать а также использовать скипченджер http://cmsthemefinder.com/userinfo.php?uid=41455#
Если вы отважились на эксплуатация скипченджера, важно:
– Пал испытанные а также верные список литературы;
– Проштудировать ответы а также назначения сообщества;
– Вооружить энергобезопасность и шиш вирусов на плане;
– Соображать риски блокировки аккаунта.
Эпилог
risk-free dota 2 skinchanger — этто хорошо приспособленный для использования способ складывать особенности персонажам, быстро менять их скины. Однако целесообразно запоминать о правилах Valve (а) также использовать такие приборы раз-другой осторожностью. Лучший фотоспособ состричь красивые скины — официальные покупки и еще внутриигровые мероприятия.
Your comment is awaiting moderation.
Как выбрать виртуальное казино
Выбор интернет казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой сайт.
Лицензия и репутация
Первое, что следует проверить – наличие официальной лицензии на ведение азартной деятельности. Хорошее онлайн казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность развлечений.
Также важно изучить отзывы и репутацию платформы. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное онлайн казино предлагает разнообразные автоматы, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора интернет казино. Это могут быть приветственные пакеты, free spins, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте онлайн казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры рейтинг казино
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы игровая платформа применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая виртуальное казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
Как выбрать виртуальное казино
Выбор онлайн казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой портал.
Лицензия и репутация
Первое, что следует проверить – наличие официальной разрешения на ведение азартной деятельности. Хорошее онлайн казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность развлекательных услуг.
Также важно изучить отзывы и репутацию игровой платформы. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное онлайн казино предлагает разнообразные игровые автоматы, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора интернет казино. Это могут быть приветственные пакеты, free spins, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте виртуальное казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры игровые автоматы играть онлайн на деньги
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы казино применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая интернет казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
Как выбрать виртуальное казино
Выбор виртуального казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой ресурс.
Лицензия и репутация
Первое, что следует проверить – наличие официальной разрешения на ведение азартной деятельности. Хорошее интернет казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность игр.
Также важно изучить отзывы и репутацию платформы. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное онлайн казино предлагает разнообразные автоматы, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора интернет казино. Это могут быть приветственные пакеты, фриспины, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте онлайн казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры онлайн казино с выводом
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы игровая платформа применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая онлайн казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
Как выбрать онлайн казино
Выбор интернет казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой сайт.
Лицензия и репутация
Первое, что следует проверить – наличие официальной лицензии на ведение азартной деятельности. Хорошее интернет казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность развлекательных услуг.
Также важно изучить отзывы и репутацию казино. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное виртуальное казино предлагает разнообразные автоматы, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора онлайн казино. Это могут быть приветственные пакеты, free spins, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте виртуальное казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры мобильное казино
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы игровая платформа применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая онлайн казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
95 920 руб https://sbn-66.ru/raskhodomery-shtray-mass-1/prezentaciya-shtray-mass/
Класс защиты по стандарту Ingress Protection Rating (IP)
С https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/raskhodomery/ultrazvukovye-raskhodomery/raskhodomer-endresshauser-prosonic-flow/
Петербург: +7 (812) 504-80-97 https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/nart-usb-modem-metran-682/
Остался в полном восторге от полученного дополнительного образования https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/gazoanalitka/datchiki-gazoanalizatory-dgs-eris-210/
Прекрасные сотрудники обеспечили поддержку на всех этапах, от первого обращения до получения финальных документов https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/raskhodomery-shtray-mass/
от 36 300 руб https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/vlagomery-nefti/vlagomery-nefti-potochnye-rhase-dynamics/
Чтобы стать слушателем курса, подайте заявку любым удобным для вас способом:
Your comment is awaiting moderation.
6.
Надійний ремонт будинку під ключ від NSDgroup — сучасні технології, якісні матеріали та чесна відповідь на питання: скільки коштує ремонт будинку. https://pinshape.com/users/8855418-nsdgroupcomua
7.
Дизайн інтер’єру будинку від НСДгруп — сучасний стиль, комфорт і продумані деталі. Проєктуємо котеджі, заміські будинки та будинки з мансардою. https://www.cake.me/me/nsdgroup-comua
8.
Потрібен ремонт квартири під ключ у Києві? NSDgroup пропонує повний цикл робіт із фіксованою ціною та дизайнерським супроводом. https://www.mapleprimes.com/users/nsdgroup25
9.
Дизайн квартири в Києві від NSDgroup — індивідуальні рішення від професійних дизайнерів інтер’єру. Замовляйте дизайн-проєкт під ваш стиль життя. https://onlinesequencer.net/members/230818
10.
NSDgroup — це дизайн інтер’єру та ремонт під ключ для квартир, будинків, офісів і комерційних об’єктів. Реалізуємо простори, в яких хочеться жити й працювати. https://leetcode.com/nsdgroupcomua/
Your comment is awaiting moderation.
1.
Професійний ремонт офісу в Києві від NSDgroup — від ідеї до здачі під ключ. Створюємо сучасні офісні простори, що працюють на ваш бізнес. https://www.slideserve.com/Nsdgroup
2.
Дизайн офісу від NSDgroup — це функціональність, стиль і комфорт. Розробляємо дизайн-проєкти офісів у Києві з урахуванням бренду та бюджету. https://myanimelist.net/profile/nsdgroupcomua
3.
Плануєте оновлення? Ремонт офісних приміщень під ключ від НСДгруп — чіткі терміни, прозора вартість і контроль на кожному етапі. https://www.pexels.com/@nsdgroup-comua-2157878096/
4.
Сучасний дизайн ресторану від NSDgroup — інтер’єри, які приваблюють гостей. Проєктуємо ресторани, що поєднують атмосферу, стиль і комерційну ефективність. https://bio.site/nsdgroupcomua
5.
Шукаєте ідею для бізнесу? Проєкти магазинів та дизайн інтер’єру магазинів від НСДгруп — продумане планування та стильні рішення для продажів. https://myanimelist.net/profile/nsdgroupcomua
Your comment is awaiting moderation.
Как выбрать интернет казино
Выбор онлайн казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой портал.
Лицензия и репутация
Первое, что следует проверить – наличие официальной разрешения на ведение азартной деятельности. Хорошее интернет казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность развлечений.
Также важно изучить отзывы и репутацию платформы. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное виртуальное казино предлагает разнообразные слоты, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора интернет казино. Это могут быть приветственные пакеты, free spins, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте виртуальное казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры онлайн казино на реальные деньги без вложений
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы игровая платформа применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая интернет казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
Application mobile 1xbet apk. Paris sportifs en ligne, football et tournois populaires, evenements en direct et statistiques. Presentation de l’application et de ses principales fonctionnalites.
Your comment is awaiting moderation.
Howdy! buy lasix pills online good site.
Your comment is awaiting moderation.
La plateforme en ligne 1xbet burkina faso: paris sportifs en ligne, matchs de football, evenements en direct et statistiques. Description du service, marches disponibles, cotes et principales fonctionnalites du site.
Your comment is awaiting moderation.
Site web de pari foot rdc: paris sportifs, championnats de football, resultats des matchs et cotes. Informations detaillees sur la plateforme, les conditions d’utilisation, les fonctionnalites et les evenements sportifs disponibles.
Your comment is awaiting moderation.
Site web 1xbet.cd – paris sportifs en ligne sur le football et autres sports. Propose des paris en direct et a l’avance, des cotes, des resultats et des tournois. Description detaillee du service, des fonctionnalites du compte et de son utilisation au Congo.
Your comment is awaiting moderation.
La plateforme 1xbet burkina: paris sportifs en ligne, matchs de football, evenements en direct et statistiques. Description du service, marches disponibles, cotes et principales fonctionnalites du site.
Your comment is awaiting moderation.
Как выбрать интернет казино
Выбор интернет казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой ресурс.
Лицензия и репутация
Первое, что следует проверить – наличие официальной сертификата на ведение азартной деятельности. Хорошее онлайн казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность игр.
Также важно изучить отзывы и репутацию игровой платформы. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное онлайн казино предлагает разнообразные игровые автоматы, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора онлайн казино. Это могут быть приветственные пакеты, бесплатные вращения, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте виртуальное казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры игровые автоматы демо играть бесплатно
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы игровая платформа применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая онлайн казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
Обзор игрового клуба Get X
виртуальное казино Get X — это современный веб-сайт для любителей азартных ставок. В данной статье мы рассмотрим основные преимущества и особенности этого казино.
Лицензия и безопасность
Get X функционирует на основе лицензии, выданной авторитетным регулятором, что подтверждает его надежность и честность. Платформа использует современные методы шифрования и защиты персональных данных, обеспечивая игрокам безопасность и конфиденциальность.
Ассортимент игр
площадка предлагает большой выбор игровых автоматов, настольных игр, видео-покера и игр с живыми дилерами. Программы предоставляются проверенными производителями, такими как NetEnt, Microgaming, Evolution Gaming и другими.
Бонусы и акции
В игровом клубе доступны приветственные бонусы, регулярные акции и программы лояльности. Игроки могут получить free spins, кешбэк и специальные предложения https://t.me/getx_site_official
Методы пополнения и вывода
Казино Гет Икс поддерживает множество способов пополнения и вывода средств: банковские карты, электронные кошельки, криптовалюты. Финансовые операции проходят быстро и без скрытых комиссий.
Поддержка клиентов
Служба поддержки казино Get X работает круглосуточно и готова помочь через чат, электронную почту и телефон. Профессиональные операторы быстро разрешают любые вопросы.
Казино Гет Икс подходит для тех, кто ценит комфорт, безопасность и качественный игровой процесс. Широкий выбор игр и привлекательные бонусы делают его отличным выбором для азартных игроков.
Your comment is awaiting moderation.
Как выбрать интернет казино
Выбор виртуального казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой ресурс.
Лицензия и репутация
Первое, что следует проверить – наличие официальной лицензии на ведение азартной деятельности. Хорошее онлайн казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность развлекательных услуг.
Также важно изучить отзывы и репутацию платформы. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное онлайн казино предлагает разнообразные игровые автоматы, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора интернет казино. Это могут быть приветственные пакеты, free spins, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте онлайн казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры бездепозитные бонусы казино за регистрацию
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы игровая платформа применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая интернет казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
Обзор казино Гет Икс
Казино Гет Икс — это современный онлайн портал для любителей азартных игр. В данной статье мы рассмотрим основные преимущества и особенности этого игрового ресурса.
Лицензия и безопасность
Казино Гет Икс функционирует на основе лицензии, выданной авторитетным регулятором, что подтверждает его надежность и честность. Платформа использует современные методы шифрования и защиты персональных данных, обеспечивая игрокам безопасность и конфиденциальность.
Ассортимент игр
казино Get X предлагает большой выбор слотов, настольных игр, видео-покера и игр с живыми дилерами. Программы предоставляются проверенными производителями, такими как NetEnt, Microgaming, Evolution Gaming и другими.
Бонусы и акции
В на платформе доступны бонусы новичкам, регулярные акции и программы лояльности. Игроки могут получить free spins, кешбэк и специальные предложения https://t.me/getx_site_official
Методы пополнения и вывода
Get X поддерживает множество способов пополнения и вывода средств: банковские карты, электронные кошельки, криптовалюты. Финансовые операции проходят быстро и без скрытых комиссий.
Поддержка клиентов
Служба поддержки игрового клуба работает круглосуточно и готова помочь через чат, электронную почту и телефон. Профессиональные операторы быстро разрешают любые вопросы.
Get X подходит для тех, кто ценит комфорт, безопасность и качественный игровой процесс. Широкий выбор игр и привлекательные бонусы делают его отличным выбором для азартных игроков.
Your comment is awaiting moderation.
8 магазинов в Москве https://sinapple.ru/collection/framesi/product/framesi-morphosis-sublimis-pure-oil-100-ml
Одними из самых эффективных средств для борьбы с подобными несовершенствами кожи являются средства с содержанием мочевины https://sinapple.ru/collection/cantabria-labs-ispaniya/product/cantabria-labs-heliocare-ultra-d
Spa Dream – это интернет- магазин косметики, ориентированный на искушенных покупателей, которые привыкли получать все и сразу https://sinapple.ru/collection/kremy-dlya-tela/product/diego-dalla-palma-omolazhivayuschiy-krem-dlya-tela-200-ml-novinka А именно – средства премиум-класса и высокий уровень обслуживания https://sinapple.ru/collection/kremy-dlya-vek-i-kozhi-vokrug-glaz/product/keenwell-progresif-lifting-anti-wrinkle-eye-contour-cream
Your comment is awaiting moderation.
Как выбрать виртуальное казино
Выбор интернет казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой сайт.
Лицензия и репутация
Первое, что следует проверить – наличие официальной лицензии на ведение азартной деятельности. Хорошее интернет казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность развлекательных услуг.
Также важно изучить отзывы и репутацию игровой платформы. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное онлайн казино предлагает разнообразные автоматы, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора интернет казино. Это могут быть приветственные пакеты, бесплатные вращения, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте онлайн казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры легальное онлайн казино в россии
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы игровая платформа применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая интернет казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
Обзор игрового клуба Get X
Казино Гет Икс — это современный игровая платформа для любителей азартных игр. В данной статье мы рассмотрим основные преимущества и особенности этого казино.
Лицензия и безопасность
Get X функционирует на основе лицензии, выданной авторитетным регулятором, что подтверждает его надежность и честность. ресурс использует современные методы шифрования и защиты персональных данных, обеспечивая игрокам безопасность и конфиденциальность.
Ассортимент игр
казино Get X предлагает большой выбор игровых автоматов, настольных игр, видео-покера и игр с живыми дилерами. Программы предоставляются проверенными производителями, такими как NetEnt, Microgaming, Evolution Gaming и другими.
Бонусы и акции
В на платформе доступны приветственные бонусы, регулярные акции и программы лояльности. Игроки могут получить free spins, кешбэк и специальные предложения https://t.me/getx_site_official
Методы пополнения и вывода
Казино Гет Икс поддерживает множество способов пополнения и вывода средств: банковские карты, электронные кошельки, криптовалюты. Финансовые операции проходят быстро и без скрытых комиссий.
Поддержка клиентов
Служба поддержки казино Get X работает круглосуточно и готова помочь через чат, электронную почту и телефон. Профессиональные операторы быстро разрешают любые вопросы.
Get X подходит для тех, кто ценит комфорт, безопасность и качественный игровой процесс. Широкий выбор игр и привлекательные бонусы делают его отличным выбором для азартных игроков.
Your comment is awaiting moderation.
Как выбрать онлайн казино
Выбор виртуального казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой сайт.
Лицензия и репутация
Первое, что следует проверить – наличие официальной разрешения на ведение азартной деятельности. Хорошее онлайн казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность развлечений.
Также важно изучить отзывы и репутацию казино. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное виртуальное казино предлагает разнообразные игровые автоматы, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора интернет казино. Это могут быть приветственные пакеты, бесплатные вращения, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте онлайн казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры казино с бонусом за регистрацию
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы казино применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая интернет казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
Как выбрать виртуальное казино
Выбор онлайн казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой ресурс.
Лицензия и репутация
Первое, что следует проверить – наличие официальной сертификата на ведение азартной деятельности. Хорошее онлайн казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность игр.
Также важно изучить отзывы и репутацию платформы. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное виртуальное казино предлагает разнообразные слоты, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора интернет казино. Это могут быть приветственные пакеты, бесплатные вращения, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте онлайн казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры бездепозитные бонусы в казино
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы казино применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая интернет казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
1.
Професійний ремонт офісу в Києві від NSDgroup — від ідеї до здачі під ключ. Створюємо сучасні офісні простори, що працюють на ваш бізнес. https://writexo.com/share/406f5dccb5f0
2.
Дизайн офісу від NSDgroup — це функціональність, стиль і комфорт. Розробляємо дизайн-проєкти офісів у Києві з урахуванням бренду та бюджету. https://tawk.to/nsdgroupcomua
3.
Плануєте оновлення? Ремонт офісних приміщень під ключ від НСДгруп — чіткі терміни, прозора вартість і контроль на кожному етапі. https://www.producthunt.com/@nsdgroup_comua
4.
Сучасний дизайн ресторану від NSDgroup — інтер’єри, які приваблюють гостей. Проєктуємо ресторани, що поєднують атмосферу, стиль і комерційну ефективність. https://www.pinterest.com/nsdgroupc/_profile/
5.
Шукаєте ідею для бізнесу? Проєкти магазинів та дизайн інтер’єру магазинів від НСДгруп — продумане планування та стильні рішення для продажів. https://onespotsocial.com/nsdgroupcomua
Your comment is awaiting moderation.
6.
Надійний ремонт будинку під ключ від NSDgroup — сучасні технології, якісні матеріали та чесна відповідь на питання: скільки коштує ремонт будинку. https://about.me/nsdgroupcomua
7.
Дизайн інтер’єру будинку від НСДгруп — сучасний стиль, комфорт і продумані деталі. Проєктуємо котеджі, заміські будинки та будинки з мансардою. https://disqus.com/by/nsdgroupcomua/about/
8.
Потрібен ремонт квартири під ключ у Києві? NSDgroup пропонує повний цикл робіт із фіксованою ціною та дизайнерським супроводом. https://onespotsocial.com/nsdgroupcomua
9.
Дизайн квартири в Києві від NSDgroup — індивідуальні рішення від професійних дизайнерів інтер’єру. Замовляйте дизайн-проєкт під ваш стиль життя. https://leetcode.com/nsdgroupcomua/
10.
NSDgroup — це дизайн інтер’єру та ремонт під ключ для квартир, будинків, офісів і комерційних об’єктів. Реалізуємо простори, в яких хочеться жити й працювати. https://www.slideserve.com/Nsdgroup
Your comment is awaiting moderation.
Как выбрать интернет казино
Выбор онлайн казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой ресурс.
Лицензия и репутация
Первое, что следует проверить – наличие официальной лицензии на ведение азартной деятельности. Хорошее онлайн казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность игр.
Также важно изучить отзывы и репутацию казино. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное виртуальное казино предлагает разнообразные автоматы, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора интернет казино. Это могут быть приветственные пакеты, бесплатные вращения, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте онлайн казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры казино онлайн бонус
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы игровая платформа применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая виртуальное казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
Обзор казино Гет Икс
игровой клуб Get X — это современный игровая платформа для любителей азартных развлечений. В данной статье мы рассмотрим основные преимущества и особенности этого игрового ресурса.
Лицензия и безопасность
Казино Гет Икс функционирует на основе лицензии, выданной авторитетным регулятором, что подтверждает его надежность и честность. ресурс использует современные методы шифрования и защиты персональных данных, обеспечивая игрокам безопасность и конфиденциальность.
Ассортимент игр
Игровой клуб предлагает большой выбор игровых автоматов, настольных игр, видео-покера и игр с живыми дилерами. Программы предоставляются проверенными производителями, такими как NetEnt, Microgaming, Evolution Gaming и другими.
Бонусы и акции
В игровом клубе доступны приветственные бонусы, регулярные акции и программы лояльности. Игроки могут получить free spins, кешбэк и специальные предложения https://t.me/getx_site_official
Методы пополнения и вывода
Get X поддерживает множество способов пополнения и вывода средств: банковские карты, электронные кошельки, криптовалюты. Финансовые операции проходят быстро и без скрытых комиссий.
Поддержка клиентов
Служба поддержки казино Get X работает круглосуточно и готова помочь через чат, электронную почту и телефон. Профессиональные операторы быстро разрешают любые вопросы.
Казино Гет Икс подходит для тех, кто ценит комфорт, безопасность и качественный игровой процесс. Широкий выбор игр и привлекательные бонусы делают его отличным выбором для азартных игроков.
Your comment is awaiting moderation.
Как выбрать виртуальное казино
Выбор виртуального казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой ресурс.
Лицензия и репутация
Первое, что следует проверить – наличие официальной сертификата на ведение азартной деятельности. Хорошее интернет казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность развлечений.
Также важно изучить отзывы и репутацию платформы. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное онлайн казино предлагает разнообразные игровые автоматы, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора интернет казино. Это могут быть приветственные пакеты, фриспины, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте виртуальное казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры онлайн казино играть бесплатно
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы казино применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая виртуальное казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
Передача данных: Wi-Fi Частота подключения: 433 https://secbuy.ru/catalog/elektrooborudovanie/
92 МГц Приложение: eWeLink для iOS и Android Дальность связи по радиоканалу: до 100 м Подключаемых датчиков: до 16 https://secbuy.ru/about/howto/
Есть в наличии (1)
Есть в наличии (12)
Бренд Polyvision анонсировал новую линейку каналового оборудования серий A, B и C https://secbuy.ru/about/delivery/
Новая серия камер и видеорегистраторов ориентирована на разные сегменты рынка и задачи, сочетая высокое качество, надёжность и современные технологии по оптимальной цене https://secbuy.ru/catalog/kabeli-i-provoda/
Профессиональные системы охраны Visonic https://secbuy.ru/catalog/preobrazovateli_interfeysa_rs_422_485/
Этот сайт был создан на платформе CMS S3 от Megagroup https://secbuy.ru/catalog/sistemy-dispetcherskoy-svyazi-i-vyzova-personala/
ru https://secbuy.ru/brands/
Your comment is awaiting moderation.
Как выбрать виртуальное казино
Выбор интернет казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой портал.
Лицензия и репутация
Первое, что следует проверить – наличие официальной сертификата на ведение азартной деятельности. Хорошее интернет казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность игр.
Также важно изучить отзывы и репутацию платформы. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное онлайн казино предлагает разнообразные автоматы, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора онлайн казино. Это могут быть приветственные пакеты, фриспины, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте виртуальное казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры казино онлайн бонусы
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы игровая платформа применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая онлайн казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
Обзор игрового клуба Get X
Казино Гет Икс — это современный онлайн портал для любителей азартных развлечений. В данной статье мы рассмотрим основные преимущества и особенности этого казино.
Лицензия и безопасность
Get X функционирует на основе лицензии, выданной авторитетным регулятором, что подтверждает его надежность и честность. Платформа использует современные методы шифрования и защиты персональных данных, обеспечивая игрокам безопасность и конфиденциальность.
Ассортимент игр
площадка предлагает большой выбор игровых автоматов, настольных игр, видео-покера и игр с живыми дилерами. Программы предоставляются проверенными производителями, такими как NetEnt, Microgaming, Evolution Gaming и другими.
Бонусы и акции
В на платформе доступны приветственные бонусы, регулярные акции и программы лояльности. Игроки могут получить free spins, кешбэк и специальные предложения https://t.me/getx_site_official
Методы пополнения и вывода
Get X поддерживает множество способов пополнения и вывода средств: банковские карты, электронные кошельки, криптовалюты. Финансовые операции проходят быстро и без скрытых комиссий.
Поддержка клиентов
Служба поддержки портала работает круглосуточно и готова помочь через чат, электронную почту и телефон. Профессиональные операторы быстро разрешают любые вопросы.
Get X подходит для тех, кто ценит комфорт, безопасность и качественный игровой процесс. Широкий выбор игр и привлекательные бонусы делают его отличным выбором для азартных игроков.
Your comment is awaiting moderation.
Как выбрать виртуальное казино
Выбор онлайн казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой ресурс.
Лицензия и репутация
Первое, что следует проверить – наличие официальной лицензии на ведение азартной деятельности. Хорошее онлайн казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность развлекательных услуг.
Также важно изучить отзывы и репутацию казино. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное виртуальное казино предлагает разнообразные слоты, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора онлайн казино. Это могут быть приветственные пакеты, бесплатные вращения, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте виртуальное казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры казино онлайн бесплатно без регистрации
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы казино применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая онлайн казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
Как выбрать виртуальное казино
Выбор онлайн казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой ресурс.
Лицензия и репутация
Первое, что следует проверить – наличие официальной лицензии на ведение азартной деятельности. Хорошее онлайн казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность развлечений.
Также важно изучить отзывы и репутацию игровой платформы. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное онлайн казино предлагает разнообразные слоты, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора онлайн казино. Это могут быть приветственные пакеты, free spins, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте онлайн казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры онлайн казино с выводом денег
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы игровая платформа применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая виртуальное казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
Погрузитесь в невероятный мир. Испытайте эмоции от игровых приключений в иммерсивной вселенной. Когда я зарегистрировался на портале, то понятия не имел, что меня ждет. Мой путь начался так. С первых шагов я начал буквально увлекаться каждой деталью интерфейса и количества игр. Когда я начал, система регистрации оказалась выше всяких похвал: интуитивно понятно и никаких раздражающих задержек. Я начал с простых игровых автоматов, но очень быстро переключился на более сложные, которые держали меня в напряжении до конца gamaslot.icu . Когда я получил свой первый выигрыш, я испытал невероятное чувство триумфа и радости. Игры оказались красочными, увлекательными и создающими ощущение настоящего погружения в приключение. На сайте есть не только игровые автоматы, но и множество других возможностей, например, живые дилеры с настоящей атмосферой казино. Casino подарило мне не только азарт, но и вдохновение, которое теперь сопровождает меня каждый раз, когда я захожу на платформу. Здесь я нахожу то, что делает каждый свободный вечер незабываемым. Если и вы хотите начать свой азартный путь, попробуйте на практике, насколько хорош портал Casino. Ваш путь победителя начинается прямо здесь https://ramen-bet-online.icu .
Погрузитесь в новые эмоции на площадке развлечений казино сегодня
Найдите новые эмоции в мире казино сегодня
Откройте удовольств
Найдите путь к успеху сайт игр казино сегодня
Узнайте о все грани победы на казино в любое время
965590f
Your comment is awaiting moderation.
Как выбрать онлайн казино
Выбор виртуального казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой портал.
Лицензия и репутация
Первое, что следует проверить – наличие официальной сертификата на ведение азартной деятельности. Хорошее онлайн казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность игр.
Также важно изучить отзывы и репутацию платформы. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное виртуальное казино предлагает разнообразные слоты, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора интернет казино. Это могут быть приветственные пакеты, фриспины, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте онлайн казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры бездепозитные бонусы в казино
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы казино применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая виртуальное казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
Обзор казино Гет Икс
игровой клуб Get X — это современный игровая платформа для любителей азартных ставок. В данной статье мы рассмотрим основные преимущества и особенности этого игрового ресурса.
Лицензия и безопасность
Get X функционирует на основе лицензии, выданной авторитетным регулятором, что подтверждает его надежность и честность. сайт использует современные методы шифрования и защиты персональных данных, обеспечивая игрокам безопасность и конфиденциальность.
Ассортимент игр
Игровой клуб предлагает большой выбор слотов, настольных игр, видео-покера и игр с живыми дилерами. Программы предоставляются проверенными производителями, такими как NetEnt, Microgaming, Evolution Gaming и другими.
Бонусы и акции
В казино Get X доступны стартовые бонусы, регулярные акции и программы лояльности. Игроки могут получить free spins, кешбэк и специальные предложения гетx официальный сайт
Методы пополнения и вывода
Get X поддерживает множество способов пополнения и вывода средств: банковские карты, электронные кошельки, криптовалюты. Финансовые операции проходят быстро и без скрытых комиссий.
Поддержка клиентов
Служба поддержки портала работает круглосуточно и готова помочь через чат, электронную почту и телефон. Профессиональные операторы быстро разрешают любые вопросы.
Казино Гет Икс подходит для тех, кто ценит комфорт, безопасность и качественный игровой процесс. Широкий выбор игр и привлекательные бонусы делают его отличным выбором для азартных игроков.
Your comment is awaiting moderation.
Как выбрать онлайн казино
Выбор интернет казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой сайт.
Лицензия и репутация
Первое, что следует проверить – наличие официальной сертификата на ведение азартной деятельности. Хорошее онлайн казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность игр.
Также важно изучить отзывы и репутацию платформы. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное онлайн казино предлагает разнообразные автоматы, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора онлайн казино. Это могут быть приветственные пакеты, фриспины, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте виртуальное казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры онлайн казино с быстрым выводом
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы игровая платформа применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая онлайн казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
Как выбрать онлайн казино
Выбор виртуального казино – ответственная задача, которая требует внимательного подхода. В этой статье мы рассмотрим ключевые критерии, на которые стоит обратить внимание, чтобы найти надежный и выгодный игровой ресурс.
Лицензия и репутация
Первое, что следует проверить – наличие официальной сертификата на ведение азартной деятельности. Хорошее онлайн казино обязательно имеет лицензию от авторитетных регуляторов: MGA, Curacao, UKGC и др. Это гарантирует честность и прозрачность игр.
Также важно изучить отзывы и репутацию казино. Рекомендации опытных игроков помогут избежать мошенников и недобросовестных операторов.
Ассортимент игр и программное обеспечение
Качественное онлайн казино предлагает разнообразные автоматы, настольные игры, покер, рулетку и другие развлечения. Работать хорошее заведение должно на проверенном программном обеспечении от ведущих производителей: NetEnt, Microgaming, Playtech и др.
Разнообразие и качество игр – показатель серьезного отношения к клиентам.
Бонусы и акции
Привлекательные бонусы – важный элемент выбора онлайн казино. Это могут быть приветственные пакеты, бесплатные вращения, программы лояльности, кэшбэк и регулярные акции. Но стоит внимательно изучать условия получения и отыгрыша бонусов, чтобы избежать недоразумений.
Удобство пополнения и вывода средств
Выбирайте виртуальное казино, которое поддерживает удобные методы оплаты: банковские карты, электронные кошельки, криптовалюты и др. Быстрая обработка заявок и прозрачные условия вывода выигрыша – залог комфортной игры онлайн казино с бездепозитным бонусом
Техподдержка и безопасность
Поддержка клиентов должна работать без перерывов и предоставлять квалифицированную помощь. Способы связи – чат, телефон, электронная почта.
Важно, чтобы казино применяло современные технологии шифрования данных и обеспечивало защиту персональной информации.
Выбирая интернет казино, обращайте внимание на лицензию, ассортимент игр, бонусные предложения, методы оплаты и уровень безопасности. Только комплексная оценка поможет найти надежное заведение и получить удовольствие от игры.
Your comment is awaiting moderation.
1.
Професійний ремонт офісу в Києві від NSDgroup — від ідеї до здачі під ключ. Створюємо сучасні офісні простори, що працюють на ваш бізнес. https://www.twitch.tv/nsdgroupcomua/about
2.
Дизайн офісу від NSDgroup — це функціональність, стиль і комфорт. Розробляємо дизайн-проєкти офісів у Києві з урахуванням бренду та бюджету. https://myanimelist.net/profile/nsdgroupcomua
3.
Плануєте оновлення? Ремонт офісних приміщень під ключ від НСДгруп — чіткі терміни, прозора вартість і контроль на кожному етапі. https://www.twitch.tv/nsdgroupcomua/about
4.
Сучасний дизайн ресторану від NSDgroup — інтер’єри, які приваблюють гостей. Проєктуємо ресторани, що поєднують атмосферу, стиль і комерційну ефективність. https://leetcode.com/nsdgroupcomua/
5.
Шукаєте ідею для бізнесу? Проєкти магазинів та дизайн інтер’єру магазинів від НСДгруп — продумане планування та стильні рішення для продажів. https://www.pexels.com/@nsdgroup-comua-2157878096/
Your comment is awaiting moderation.
6.
Надійний ремонт будинку під ключ від NSDgroup — сучасні технології, якісні матеріали та чесна відповідь на питання: скільки коштує ремонт будинку. https://pbase.com/nsdgroupcomua/image/175986358
7.
Дизайн інтер’єру будинку від НСДгруп — сучасний стиль, комфорт і продумані деталі. Проєктуємо котеджі, заміські будинки та будинки з мансардою. https://pinshape.com/users/8855418-nsdgroupcomua
8.
Потрібен ремонт квартири під ключ у Києві? NSDgroup пропонує повний цикл робіт із фіксованою ціною та дизайнерським супроводом. https://www.walkscore.com/people/111619767040/nsdgroupcomua
9.
Дизайн квартири в Києві від NSDgroup — індивідуальні рішення від професійних дизайнерів інтер’єру. Замовляйте дизайн-проєкт під ваш стиль життя. http://artistecard.com/nsdgroupcomua
10.
NSDgroup — це дизайн інтер’єру та ремонт під ключ для квартир, будинків, офісів і комерційних об’єктів. Реалізуємо простори, в яких хочеться жити й працювати. https://maxforlive.com/profile/user/nsdgroupcomua?tab=about
Your comment is awaiting moderation.
Аккумуляторы для спецтехники техники
Аккумуляторы для спецтехники служат ключевым компонентом, обеспечивающим энергию специальных машин и механизмов, используемых в строительстве. Правильный выбор и эксплуатация этих аккумуляторов содействует стабильную работу спецтехники и предотвращает проблемы в процессе работы.
Виды аккумуляторов для спецтехники оборудования
Существует несколько основных типов аккумуляторов, которые применяются в спецтехнике:
– Свинцово-кислотные: самые распространённые и доступные, характеризуются надежностью.
– Gel: отличаются повышенной стойкостью к вибрациям и глубокому разряду.
– аккумуляторы с абсорбированным электролитом: обладают высокой мощностью и быстрым зарядом.
– Li-ion: современные, легкие и высокоэффективные батареи, но с более высокой стоимостью.
Критерии выбора аккумулятора для спецтехники техники
При выборе аккумулятора для спецтехники следует учитывать несколько важных параметров:
– Емкость – определяет, сколько энергии аккумулятор может хранить и отдавать.
– Стартовый ток – важен для мощных двигателей спецтехники, чтобы обеспечить надёжный запуск даже при низких температурах.
– Размеры и масса – важны для правильного размещения аккумулятора в машине.
– режим работы – рабочие температуры, вибрации, влажность и другие факторы влияют на выбор типа аккумулятора.
Техническое обслуживание и эксплуатация аккумуляторов спецтехники машин
Для продления срока службы аккумуляторов рекомендуется соблюдать следующие правила:
– Регулярно проверять уровень электролита и при необходимости доливать дистиллированную воду (для свинцово-кислотных аккумуляторов).
– Контролировать состояние клемм и контактов, очищать их от загрязнений и коррозии.
– Следить за зарядкой и не допускать глубокого разряда, который снижает ресурс батареи.
– Хранить аккумуляторы в сухом помещении при оптимальной температуре.
Преимущества качественных аккумуляторов для спецтехники
– Отличная работоспособность в сложных условиях подбор тяговых аккумуляторов
– Продолжительный период эксплуатации.
– Защита от механических повреждений.
– Способность к быстрому заряду.
Заключение
Аккумуляторы для спецтехники служат незаменимой частью любого тракторного оборудования. Правильный выбор, своевременное техническое обслуживание и понимание особенностей эксплуатации позволяют максимальную эффективность и долгий срок службы аккумуляторных батарей. В итоге это снижает риски простоев и повышает производительность всей техники.
Если вы хотите обеспечить бесперебойную работу своей спецтехники, обязательно уделяйте внимание качеству аккумуляторов и их правильной эксплуатации.
Your comment is awaiting moderation.
Бадминтон https://sport-i-slife.ru/shop/myagkie-moduli/veselyj-paravozik/
Спортивные товары и оборудование https://sport-i-slife.ru/shop/oborudovanie-dlya-sensornyx-komnat/dorozhka-sledochki-bez-porolona-2/
Удобная экосистема https://sport-i-slife.ru/shop/oborudovanie-dlya-bassejna/akvasapozhki/
Глобальный ассортимент спортивных товаров на atlant-sport https://sport-i-slife.ru/shop/batuty/skladnoj-mini-batut-36-s-ruchkoj-diametr-92-sm-sumka-rozovyj/
ru Производство и оптовая продажа спортивного инвентаря и оборудования https://sport-i-slife.ru/shop/izdeliya-iz-plastika/igra-gorodki/
У нас вы найдете самые востребованные спортивные товарные категории https://sport-i-slife.ru/shop/oborudovanie-dlya-sensornyx-komnat/sensornaya-dorozhka-iz-tkanej-raznyx-sheroxovatostej/
Заявка на открытие доступа https://sport-i-slife.ru/shop/bolshoj-tennis/raketki-tennisnye/
Your comment is awaiting moderation.
Ce site a ete concu pour vous offrir une source fiable de renseignements locaux.
Parmi les contenus disponibles, Vous y trouverezdivers services en ligne, telles queles travaux en cours.
Un soin particulier a ete apporte a la presentation, afin de garantirune utilisation fluide et efficace.
Les informations disponibles sont adaptees aux changements municipaux, afin de vous offrir une plateforme veritablement vivante et dynamique.
https://www.postman.com/brendon-s-postman
Your comment is awaiting moderation.
What’s up, DeFi crowd?
Found recently a detailed review about latest token launches.
It analyzes new DeFi apps in crypto markets.
Cool stuff if you like market analysis.
Read more
Your comment is awaiting moderation.
Need complete privacy? Learn more about the benefits of anti-detect browsers.
Every day, when we interact with online resources, we voluntarily reveal information about our device and online behavior. Algorithms monitor our every action, collecting data to create an individual profile. For those who want to remain undetected online, special tools have emerged – anti-detect browsers.
What is an anti-detect browser?
An anti-detect browser is a special type of software designed to distort a user’s digital image. A standard browser collects a wealth of computer data, such as operating system version, screen resolution, graphics card, and even time zone. This data creates a unique “fingerprint” of the user, allowing websites to recognize them again and again.
The goal of anti-detect browsers is to create virtual copies of the device, varying every detail, from the operating system to the browser window size. This way, each session appears separate and independent from the previous one to the website, reducing the chances of being identified.
Who are anti-detection browsers intended for?
– Those who manage multiple accounts simultaneously. Without anti-detection, there is a risk of one or more accounts being blocked for violating site rules.
– Users concerned about privacy violations and mass surveillance. Forget high prices for anonymity. Promo code 2026NY makes our anti-detect browser the most affordable
– Analytics and marketing professionals who want to test audience response to ads or test conversion hypotheses.
Anti-detection browsers offer a number of useful features:
– The ability to create multiple virtual profiles that prevent links between active accounts.
– Manage cookies that affect browsing history and content interactions.
– Use proxy services to hide your actual IP address and location.
These qualities make anti-detection browsers an essential tool for effective work in highly controlled and restricted environments.
How to choose the right anti-detection browser?
When purchasing an anti-detection browser, consider the following:
— Does the selected product meet the requirements of your operating system?
— Are there enough virtual profiles available for comfortable use?
— Is it possible to connect to the required proxy service, and how well does it function?
By considering these points, you can choose the right anti-detection browser that meets all your needs and security and privacy requirements.
Your comment is awaiting moderation.
Главные новости https://newsline.in.ua онлайн: от срочных сообщений до глубоких обзоров и экспертных комментариев. Политика, экономика, безопасность, технологии и культура. Только проверенные факты и удобная лента, чтобы быстро ориентироваться во всём, что происходит.
Your comment is awaiting moderation.
Актуальные и главные https://allnews.in.ua новости: короткие заметки о срочных событиях и развёрнутые аналитические материалы. Помогаем понять, что произошло, почему это важно и к чему может привести. Лента обновляется в течение дня, чтобы вы не упустили ничего значимого.
Your comment is awaiting moderation.
Greetings everyone!
Just read a well-written overview about current crypto market updates.
It discusses main takeaways in Bitcoin, Ethereum, and altcoins.
Nice balanced view.
Check article
Your comment is awaiting moderation.
Главные новости https://mynewsmonitor.com онлайн: самые важные события дня в сжатом и понятном формате. Политика, экономика, общество, мир, наука и культура. Краткие сводки, развёрнутые статьи, мнения экспертов и удобная лента, которая обновляется в режиме реального времени.
Your comment is awaiting moderation.
Женский портал https://forthenaturalwoman.com о жизни, красоте и вдохновении: мода, уход за собой, здоровье, отношения, карьера и личные финансы. Полезные статьи, честные обзоры, советы экспертов и истории реальных женщин. Присоединяйтесь к сообществу и находите идеи для себя каждый день.
Your comment is awaiting moderation.
Need complete privacy? Learn more about the benefits of anti-detect browsers.
Every day, when we interact with online resources, we voluntarily reveal information about our device and online behavior. Algorithms monitor our every action, collecting data to create an individual profile. For those who want to remain undetected online, special tools have emerged – anti-detect browsers.
What is an anti-detect browser?
An anti-detect browser is a special type of software designed to distort a user’s digital image. A standard browser collects a wealth of computer data, such as operating system version, screen resolution, graphics card, and even time zone. This data creates a unique “fingerprint” of the user, allowing websites to recognize them again and again.
The goal of anti-detect browsers is to create virtual copies of the device, varying every detail, from the operating system to the browser window size. This way, each session appears separate and independent from the previous one to the website, reducing the chances of being identified.
Who are anti-detection browsers intended for?
– Those who manage multiple accounts simultaneously. Without anti-detection, there is a risk of one or more accounts being blocked for violating site rules.
– Users concerned about privacy violations and mass surveillance. Forget high prices for anonymity. Promo code 2026NY makes our anti-detect browser the most affordable
– Analytics and marketing professionals who want to test audience response to ads or test conversion hypotheses.
Anti-detection browsers offer a number of useful features:
– The ability to create multiple virtual profiles that prevent links between active accounts.
– Manage cookies that affect browsing history and content interactions.
– Use proxy services to hide your actual IP address and location.
These qualities make anti-detection browsers an essential tool for effective work in highly controlled and restricted environments.
How to choose the right anti-detection browser?
When purchasing an anti-detection browser, consider the following:
— Does the selected product meet the requirements of your operating system?
— Are there enough virtual profiles available for comfortable use?
— Is it possible to connect to the required proxy service, and how well does it function?
By considering these points, you can choose the right anti-detection browser that meets all your needs and security and privacy requirements.
Your comment is awaiting moderation.
Why are anti-detect browsers necessary and how do they protect your online anonymity?
In today’s world, almost every website visit leaves traces that allow third parties to monitor our activities. To protect personal data and enhance the security of their online activities, more and more users are turning to specialized tools—anti-detect browsers.
The essence of the technology
An anti-detect browser is a program that can alter the digital signature of a computer, preventing the device’s real characteristics and the user’s identity from being determined. When you open a regular browser, the server receives detailed information about your hardware, operating system, screen resolution, and more. This data forms a unique “digital fingerprint” that is easily tracked and used by advertisers and website owners to analyze user behavior. Privacy for everyone. Use the unique promo code 2026NY and get a discount on the most affordable anti-detect browser
Why should you use an anti-detect browser?
• Firstly, it’s an excellent way to strengthen your security and minimize the risk of personal data leakage. Such programs make it virtually impossible for third-party resources to collect information about you and your device.
• Secondly, anti-detect browsers are convenient when working with multiple accounts simultaneously. You can freely access websites that use strict monitoring and detection methods for suspicious activity without fear of account restrictions or bans.
• These browsers are also popular among marketing and analytics professionals, as they allow them to study how different audiences respond to content, test advertising campaigns, and improve business performance.
Features and Functionality
1. The key feature of anti-detect browsers is the creation of virtual profiles. The user creates multiple unique digital “personalities,” each simulating a completely different device, making it difficult to track the owner’s real identity.
2. Furthermore, anti-detect browsers offer flexible management of cookies stored on the device and integration with proxy servers, allowing you to mask your original IP address and change your geographic location.
3. Finally, the best browsers in this class support automatic device configuration selection, adapting to the specific needs of the user and the situation.
Choosing the Right Anti-Detection Browser
When purchasing, pay attention to several key factors:
• Compatibility with the installed operating system,
• Number of virtual profiles created,
• Ability to integrate with reliable proxy services,
• User-friendly interface and availability of additional functionality,
• Price (free versions are often inferior to paid versions).
Therefore, by using a high-quality anti-detection browser, you increase your security, freedom of movement online, and the convenience of working with multiple accounts.
Your comment is awaiting moderation.
Digital Anonymity: Why We Need Anti-Detect Browsers
Every time we visit a website, we unwittingly reveal a wealth of information about our device and activities. Some people take this calmly, considering it normal online behavior, while others strive to minimize such surveillance. Anti-Detect Browsers—special software that protects our anonymity—have been developed specifically for the latter. Save smartly. Get maximum anonymity at the minimum price with our anti-detect. Your promo code: 2026NY
The Concept of Anti-Detect
To understand this, imagine this: when you access the internet in the usual way, the server learns details about your PC, right down to a precise description of your hardware, the operating system you use, and other specific characteristics. This entire set of information is called a “digital fingerprint,” and it allows organizations to build databases about our preferences and interests.
Anti-Detect Browsers change the rules of the game by creating fake images of the device making the request. The server sees each visit as a new, unique client, completely unrelated to previous connection attempts.
This feature is ideal for those accustomed to managing multiple accounts or who want to avoid penalties for duplicate registrations.
Who benefits from an anti-detect browser?
Besides the obvious benefits for personal privacy, such browsers are extremely valuable among professionals. Advertising and analytics specialists find them useful for assessing target audience responses to specific content, conducting tests, and experimenting with displaying ads to different user groups.
The main features of anti-detect browsers include:
— Created virtual profiles that can appear on completely different devices.
— Advanced cookie settings.
— Guaranteed activation of proxy service modes.
These qualities make anti-detect browsers attractive to any user concerned about data security and seeking to improve performance when managing multiple accounts.
How to choose the right anti-detect browser?
First, make sure the program meets the following criteria:
— Optimal compatibility with your operating system.
— Sufficient number of virtual profiles for convenient parallel management.
— Reliable integration with proxy providers.
And, of course, keep cost in mind: high-quality products often require an investment, even though they offer a much wider range of features.
Now, with the necessary knowledge, you’re ready to choose an anti-detection browser that meets your needs and requirements.
Your comment is awaiting moderation.
Плюс 1718 процентов https://olga-filippova.ru/kontakts
Похоже, простые обои всем уже поднадоели https://olga-filippova.ru/interery-fasad
Приходит время ярких принтов и текстиля https://olga-filippova.ru/portfolio-2
Этот тренд мне по душе! Я люблю делать акцентные стены в своих проектах https://olga-filippova.ru/smi
Сервисы, полезные каждому дизайнеру https://olga-filippova.ru/kontakts
И не только Квартблог собрал список полезных ссылок из 70 сервисов, сайтов и книг, которые будут интересны не только дизайнерам интерьеров https://olga-filippova.ru/interior_appartment
Все эти детали создают уютные слои в интерьере, что позволяет придать ему цельной, гармоничной эстетики https://olga-filippova.ru/zakazat-dizajn-proekt-stoimost
Пытаясь решить, какие слои будут выглядеть выгодно в вашем интерьере, подумайте о выборе разнообразных тканей и фактур – к примеру, бархатные подушки, шелковые занавеси, мохеровые одеяла, плисовые коврики https://olga-filippova.ru/interery-medical-study-center
Правильно, эту видим чугунную плитку https://olga-filippova.ru/smi
А почему? А потому, что в этом здании раньше была фабрика дореволюционной постройки https://olga-filippova.ru/beauty-salons-spa-design
А теперь это новомодный лофт https://olga-filippova.ru/smi
Your comment is awaiting moderation.
Ce site est destine a fournir des informations essentielles.
Parmi les contenus disponibles, Le site propose des informations surles ressources disponibles pour les citoyens de la commune.
La navigation a ete pensee pour etre intuitive, avec des sections clairement organisees.
Les informations disponibles sont adaptees aux changements municipaux, afin de vous offrir une plateforme veritablement vivante et dynamique.
https://www.la-mairie.com/rezonville
Your comment is awaiting moderation.
Yo crypto fam!
Wanted to post a fresh post about market analysis.
It talks about major updates in BTC, ETH, and other coins.
Worth checking out, especially if you trade.
Full link
Your comment is awaiting moderation.
Hello everyone! I go by the name Admin Read:
Кракен – это всемирно известная платформа для онлайн-покупок, где каждый найдет что-то для себя. На платформе kraken даркнет вы найдете всё: от уникальных коллекционных предметов до последних моделей техники. На Kraken вы можете сравнивать цены, находить уникальные предложения и покупать товары со скидкой. Удобный интерфейс и система безопасности делают шопинг на kra ссылка приятным и надежным. Найдите уникальные товары на Kraken прямо сейчас.
Your comment is awaiting moderation.
Hey there, everyone! The name’s Admin Read:
На Кракен можно найти всё необходимое для дома, работы и досуга. Платформа kra cc радует выгодными предложениями и эксклюзивными коллекционными предметами. Процесс покупок становится легче благодаря скидкам и акциям. Кракен заботится о защите сделок, что привлекает покупателей со всего мира. Именно kraken darknet market обеспечивает комфорт и безопасность при покупках.
Your comment is awaiting moderation.
Попробуйте свои силы в казино самолетик 1win, и испытайте удачу в уникальном игровом процессе!
Казино Aviator представляет собой захватывающий игровой проект, предоставляющий возможность заработать.
Your comment is awaiting moderation.
Проблемы с алкоголем? круглосуточный вывод из запоя: анонимная помощь, круглосуточный выезд врача, детоксикация, капельницы, стабилизация состояния и поддержка. Индивидуальный подход, современные методы и контроль здоровья. Конфиденциально и безопасно.
Your comment is awaiting moderation.
Looking for a university? specialities vitebsk university information for applicants about admission to state-funded and fee-paying programs, list of required documents, application deadlines, entrance examinations, targeted admissions, and dormitory accommodation. Find out how to become a student at Vitebsk State University.
Your comment is awaiting moderation.
Хочешь сдать авто? срочный выкуп авто быстро и безопасно: моментальная оценка, выезд специалиста, оформление сделки и мгновенная выплата наличными или на карту. Покупаем автомобили всех марок и годов, включая битые и после ДТП. Работаем без скрытых комиссий.
Your comment is awaiting moderation.
Вызов электрика https://vash-elektrik24.ru на дом в Москве: оперативный выезд, поиск и устранение неисправностей, установка розеток и выключателей, подключение техники, ремонт проводки. Квалифицированные мастера, точные цены, гарантия на работы и удобное время приезда.
Your comment is awaiting moderation.
Hey crypto folks!
Just stumbled on a detailed piece about latest token launches.
It compares AI-based strategies in trading world.
Definitely a good weekend read.
Check this out
Your comment is awaiting moderation.
Best lease vps europe. Only TOP European data centers in Estonia, Finland, Germany. All servers are GDPR compliant, blazing fast NVMe SSD drives, reliable network 10+ Gbps, selection of OS templates, 24/7 monitoring, easy remote management.
Your comment is awaiting moderation.
Prodej reziva https://www.kup-drevo.cz v Ceske republice: siroky vyber reziva, stavebniho a dokoncovaciho reziva, tramu, prken a stepky. Dodavame soukromym klientum i firmam stalou kvalitu, konkurenceschopne ceny a dodavky po cele Ceske republice.
Your comment is awaiting moderation.
Platforma internetowa mostbet: zaklady przedmeczowe i na zywo, wysokie kursy, akumulatory, zaklady na sumy i handicapy, a takze popularne sloty i kasyno na zywo. Bonus powitalny, regularne promocje, szybkie wyplaty na karty i portfele.
Your comment is awaiting moderation.
знакомства разовые знакомства для секса встречи Люди не сразу готовы окунуться в омут, первая встреча решает иногда все, возможно вторую встречу с большим.
Your comment is awaiting moderation.
Hi crypto enthusiasts!
Came across a useful article about the state of blockchain.
It breaks down how the market’s moving in digital assets.
Quite educational.
Read post
Your comment is awaiting moderation.
Hello there! buy sumatriptan pills good web site.
Your comment is awaiting moderation.
What’s good, folks?
Came across a pretty interesting thread about the latest in crypto.
It covers major updates in crypto in general.
Packed with insights, especially if you follow charts.
Read it here
Your comment is awaiting moderation.
Анонимный криптообменник comcash
предоставляет защищенный
обмен цифровых активов без передачи личных данных.
Вы можете мгновенно
совершать обмен криптовалют, сохраняя конфиденциальность.
Наш сервис предлагает мгновенные сделки
и гибкие условия.
Выберите удобный
обмен криптовалюты с ComCASH и получите комфортный опыт.
обмен бтк на сбербанк
обменять usdt trc20
обменник сбербанк биткоин
как перевести биткоины на карту сбербанка
ethereum to trx
обменник биткоин на сбербанк
вывести биткоин на сбербанк
биткоин на сбербанк
вывод биткоина на сбербанк
крипта обмен
обменять криптовалюту на наличные
обменник криптовалюты на рубли
обмен usdt сбер
обменять usdt trc20 на рубли
trc20 на сбербанк рубли
обменник usdt на карту
обмен usdt trc 20 на сбер
Your comment is awaiting moderation.
A Simple Guide to SSL/TLS Certificates: What They Are, How They Work, and How to Get One DevOpsHorizon
Admin, согласен с вами полностью 🙂
Меня заинтересовала тема “”, но я там не могу ответить.
Актуальные ссылки KRAKEN:
– :
– :
– :
– :
– :
Ваша личная скидка по коду KRA-HXAD2025 – 6%
Your comment is awaiting moderation.
A Simple Guide to SSL/TLS Certificates: What They Are, How They Work, and How to Get One DevOpsHorizon
Moderator, согласен с вами полностью 🙂
Меня заинтересовала тема “”, но я там не могу ответить.
Рабочие зеркала KRAKEN:
– :
– :
– :
– :
– :
Ваша персональная скидка по коду KRA-AYNN2025 – 5%
Your comment is awaiting moderation.
A Simple Guide to SSL/TLS Certificates: What They Are, How They Work, and How to Get One DevOpsHorizon
Moderator, согласен с вами полностью 🙂
Меня заинтересовала тема “”, но я там не могу ответить.
Рабочие зеркала KRAKEN:
– :
– :
– :
– :
– :
Ваша личная скидка по коду KRA-VHVH2025 – 5%
Your comment is awaiting moderation.
What’s up, DeFi crowd?
Wanted to share a detailed breakdown about AI in trading.
The author explores AI-based strategies in crypto markets.
Really solid perspective.
Go to link
Your comment is awaiting moderation.
Free Online Jigsaw Puzzle https://addons.mozilla.org/hu/firefox/user/13330707/ play anytime, anywhere. Huge gallery of scenic photos, art and animals, customizable number of pieces, autosave and full-screen mode. No registration required – just open the site and start solving.
Your comment is awaiting moderation.
777bet online casino
One of the key features of 777bet is its user-friendly interface, which enhances the betting experience.
Your comment is awaiting moderation.
https://zooaquarium.ru/ fish
https://softisntall.ru/ – soft
https://airvission.ru – avto car
https://betautocard.ru – кредиты, банки, финансы
https://cake-star.ru – Авто, автомобиль, тачки
Your comment is awaiting moderation.
Децентрализованная экосистема кракен маркет обрабатывает криптовалютные платежи в Bitcoin, Monero и Ethereum с псевдонимной защитой финансовых транзакций всех участников.
Your comment is awaiting moderation.
Безопасный процесс авторизации вход на кракен требует решения TOTP кода из приложения аутентификатора и дополнительного PIN для критических операций на платформе.
Your comment is awaiting moderation.
car rental dubai
Your comment is awaiting moderation.
A cozy Kolasin Montenegro hotels for mountain lovers. Ski slopes, trekking trails, and local cuisine are nearby. Rooms are equipped with amenities, Wi-Fi, parking, and friendly staff are available to help you plan your vacation.
Your comment is awaiting moderation.
Plai in demo aviator game and experience the adrenaline rush with every bet!
The gameplay revolves around a virtual plane taking off, as players see the multiplier grow alongside its ascent.
Your comment is awaiting moderation.
Hey all!
Came across a well-written article about DeFi and AI integration.
It discusses recent trends in digital assets.
Helpful for both new and experienced traders.
More details
Your comment is awaiting moderation.
Новинний портал Ужгорода https://88000.com.ua головні події міста, політика, економіка, культура, спорт та життя городян. Оперативні новини, репортажі, інтерв’ю та аналітика. Все важливе про Ужгород в одному місці, зручно з телефону та комп’ютера.
Your comment is awaiting moderation.
Cost-effective solutions when buy tiktok likes cheap maintain quality. Budget options from reputable providers enable growth without excessive marketing expenditure.
Your comment is awaiting moderation.
Hi there, blockchain friends!
Found recently a detailed breakdown about crypto insights for 2025.
It analyzes top coins in trading world.
Cool stuff if you like market analysis.
Read more
Your comment is awaiting moderation.
Дизайнерская мебель премиум класса — это воплощение изысканного стиля и безукоризненного качества.
Мебель высокого класса от известных дизайнеров — это не просто предметы интерьера, а настоящие произведения искусства. Мебель данного класса обладает исключительной функциональностью и эстетикой. Все больше людей выбирают мебель премиум класса для своих домов.
Your comment is awaiting moderation.
Action tips: https://valetinowiki.racing/wiki/Tired_Of_Rejections_Your_Answer_Is_To_Buy_Facebook_Business_Manager
Your comment is awaiting moderation.
Uwielbiasz hazard? nv casino: rzetelne oceny kasyn, weryfikacja licencji oraz wybor bonusow i promocji dla nowych i powracajacych graczy. Szczegolowe recenzje, porownanie warunkow i rekomendacje dotyczace odpowiedzialnej gry.
Your comment is awaiting moderation.
Срочный вызов электрика https://vash-elektrik24.ru на дом в Москве. Приедем в течение часа, быстро найдём и устраним неисправность, заменим розетки, автоматы, щиток. Круглосуточный выезд, гарантия на работы, прозрачные цены без скрытых доплат.
Your comment is awaiting moderation.
Агрегатор новостей Озёрск
https://news.ozrtech.ru
Your comment is awaiting moderation.
Вносятся ли данные об обучении в ФРДО?
Предмет тендера: Выполнение работ по монтажу силового электрооборудования, электроосвещения, молниезащиты и заземления, КИПиА при строительстве ДНС с УПСВ в районе куста 39 Приобского нефтяного месторождения ООО “РН-Юганскнефтегаз”. Цена: 0 руб https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/registriruyuschiy-kalibrator-fluke-754/
Основная цель контрольно-измерительной аппаратуры — предоставить операторам, инженерам и ученым надежные данные для принятия обоснованных решений https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/raskhodomery/ultrazvukovye-raskhodomery/raskhodomer-ultrazvukovoy-siemens-sitrans-fus1010/
Современные технологии и инновации позволяют измерительной аппаратуре обладать высокой степенью автоматизации, что повышает эффективность и точность контроля https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/gazoanalitka/
Каталог КИП https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/gazoanalitka/datchiki-gazoanalizatory-dgs-eris-210/
49 000 руб https://sbn-66.ru/raskhodomery-shtray-mass-1/
Тендер №83905139 от 16 https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/gazoanalitka/sistemy-gazoanaliticheskie-mnogokomponentnye-sgaes/
05 https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/gazoanalitka/gazoanalizatory-sgoes/
25 https://sbn-66.ru/kontrolno-izmeritelnye-pribory-1/raskhodomery-shtray-mass/
Your comment is awaiting moderation.
Обслуживание https://shcherbinins.ru/menu
1 375 руб./чел https://shcherbinins.ru/uslugy
Кейтеринг экономит время на придумывание собственного меню и долгую готовку https://shcherbinins.ru/aboutus
Вам нужно лишь выбрать блюда из каталога и заказать фуршет с доставкой в необходимое место https://shcherbinins.ru/aboutus
Уже год работаю с Мосфуршет и не могу нарадоваться! Детские праздники – это целая наука, а их закуски – просто находка https://shcherbinins.ru/uslugy
Всегда делают разнообразное меню и для детей, и для взрослых https://shcherbinins.ru/
Родители довольны, дети в восторге https://shcherbinins.ru/menu
Надежный партнер для моего бизнеса, рекомендую!
Специальные Предложения https://shcherbinins.ru/aboutus
Кейтеринг по Москве подобранный на нашем портале поможет вам провести замечательный банкет, фуршет, кофе-брейк или candy-бар, не тратя на подготовку свое время и силы https://shcherbinins.ru/uslugy
Этот формат удобен и для организации корпоративного питания https://shcherbinins.ru/
Your comment is awaiting moderation.
1.
Descubre todo sobre Sugar Rush, la famosa tragamonedas online con rodillos 7×7 y sistema Cluster Pays, en nuestro sitio especializado. Guías, trucos y versiones demo para jugar con responsabilidad. https://www.divephotoguide.com/user/sugarrushcl/
2.
Si te encantan los juegos de casino, nuestra web te ofrece análisis completos del slot de caramelos Sugar Rush, incluyendo giros gratis y multiplicadores progresivos. Solo para mayores de edad. http://www.askmap.net/location/7626853/chile/sugarrush
3.
Explora en detalle cómo funciona Sugar Rush 7×7, aprende a activar los mejores bonos y prueba la demo gratuita antes de jugar con dinero real. Todo en un solo sitio. https://eternagame.org/players/586182
4.
¿Buscas información confiable sobre tragamonedas online? Aquí encontrarás reseñas, RTP, funciones especiales y todo lo que debes saber sobre Sugar Rush y otros títulos populares. https://noti.st/sugarrushcl
5.
Nuestro portal reúne guías completas sobre Cluster Pays, giros gratis, estrategias y funcionamiento del famoso slot Sugar Rush. Juega informado y con responsabilidad. https://hub.docker.com/u/sugarrushcl
Your comment is awaiting moderation.
Нужна работа в США? школа трак диспетчинга в сша в америке онлайн с реальными кейсами : работа с заявками и рейсами, переговоры на английском, тайм-менеджмент и сервис. Подходит новичкам и тем, кто хочет выйти на рынок труда США и зарабатывать в долларах.
Your comment is awaiting moderation.
“Gorgeous, insatiable woman yearns for release.” Here — https://rb.gy/3fy54w?Rhyhoro
Your comment is awaiting moderation.
Hi crypto enthusiasts!
Came across a concise guide about DeFi and AI integration.
It discusses main takeaways in digital assets.
Nice balanced view.
Check article
Your comment is awaiting moderation.
Стабильный kraken tor с мостами snowflake обеспечивает подключение к сети даже в странах с агрессивной блокировкой Tor трафика провайдерами.
Your comment is awaiting moderation.
Нужна работа в США? курс трак диспетчера онлайн с куратором : работа с заявками и рейсами, переговоры на английском, тайм-менеджмент и сервис. Подходит новичкам и тем, кто хочет выйти на рынок труда США и зарабатывать в долларах.
Your comment is awaiting moderation.
1.
Descubre todo sobre Sugar Rush, la famosa tragamonedas online con rodillos 7×7 y sistema Cluster Pays, en nuestro sitio especializado. Guías, trucos y versiones demo para jugar con responsabilidad. https://www.blogger.com/profile/16721592971480158763
2.
Si te encantan los juegos de casino, nuestra web te ofrece análisis completos del slot de caramelos Sugar Rush, incluyendo giros gratis y multiplicadores progresivos. Solo para mayores de edad. https://pubhtml5.com/homepage/pptxf/
3.
Explora en detalle cómo funciona Sugar Rush 7×7, aprende a activar los mejores bonos y prueba la demo gratuita antes de jugar con dinero real. Todo en un solo sitio. https://inkbunny.net/sugarrushcl
4.
¿Buscas información confiable sobre tragamonedas online? Aquí encontrarás reseñas, RTP, funciones especiales y todo lo que debes saber sobre Sugar Rush y otros títulos populares. https://www.deviantart.com/sugarrushcl
5.
Nuestro portal reúne guías completas sobre Cluster Pays, giros gratis, estrategias y funcionamiento del famoso slot Sugar Rush. Juega informado y con responsabilidad. https://www.walkscore.com/people/264430629489/sugarrush
Your comment is awaiting moderation.
Hey everyone!
Discovered a pretty interesting post about blockchain updates.
It covers key movements in crypto in general.
Worth checking out, especially if you’re into news.
Read it here
Your comment is awaiting moderation.
Откройте место, где игра превращается в искусство. Раскройте современных играх ретро и новых форматов от . Мой интерес к Casino был вызван рекламой, и я решил проверить сам. Сайт совершенно дружелюбный к новичкам, что для меня огромный плюс. Регистрация заняла всего несколько минут — просто, безопасно и без каких-либо сложностей. Я начал с простых игровых автоматов, но очень быстро переключился на более сложные, которые держали меня в напряжении до конца poker-dom-mirrors.icu . Каждый шаг становился новым переживанием — от лёгкого волнения до ощущения настоящего триумфа. Теперь я знаю точно: Casino — это не просто игры, это атмосфера, где каждый шаг приносит удовольствие. Мобильная версия сайта выгодно отличается удобством интерфейса, что делает игру ещё более доступной. Casino подарило мне не только азарт, но и вдохновение, которое теперь сопровождает меня каждый раз, когда я захожу на платформу. Это место стало для меня чем-то большим, чем просто игровая платформа — это целая вселенная неповторимости и азарта. Если и вы хотите получить положительные впечатления от современной игровой платформы, начните вашу азартную историю прямо здесь. Не упустите возможность первого шага к победам https://riobet-promocod.icu .
Исследуйте новые эмоции на платформе казино игр в любое время
Найдите новые эмоции сайт игр казино сегодня
Исследуйте все грани победы сайт игр казино в любое время
Найдите удовольствие от игр на сайте казино без лишних ожиданий
Погрузитесь в ясность азарта на платформе казино игр в любое время
fa8dd87
Your comment is awaiting moderation.
STOP OVERPAYING FOR SHIPPING!
Delivery New York anything across NYC quickly – same-day available. Thousands of satisfied customers rely on us for affordable shipping rates.
CUT YOUR SHIPPING COSTS NOW
– 24-hour pickup & delivery
– Starting from just $25
– Real-time GPS tracking
– White-glove service
– No hassle
QUICK SHIPPING FOR:
– Small parcels – personal items
– Large items – dryers
– tables – cross-country
– Business supplies – LTL
– Storage delivery – professional crew
DELIVERY ZONES:
NJ > NYC • Staten Island • NY > Florida • PA • East Coast routes
GET 20% OFF your first order – Book within 48 hours!
DON’T WAIT – Same-day pickup available!
Visit https://delivery-new-york.com/ – Get rates now!
Reach out for fastest service: Your local shipping partner.
PROFESSIONAL SHIPPING STARTS HERE
Your comment is awaiting moderation.
Строительные геоматериалы https://stsgeo-ekb.ru в Екатеринбурге с доставкой: геотекстиль, объемные георешётки, геосетки, геомембраны. Интернет-магазин для дорожного строительства, ландшафта и дренажа. Консультации специалистов и оперативный расчет.
Your comment is awaiting moderation.
Премиальная косметика, родом из Франции, завоевала сердца и доверие покупателей по всему миру, благодаря качеству выпускаемой продукции и эффективности от ее ис https://sinapple.ru/collection/syvorotki-i-kontsentraty/product/keenwell-biopure-fluido-mate-rehidratante-dia
Современные технологии делают походы по магазинам бессмысленной тратой времени, ведь намного лучше прогуливаться по парку или набережной, а покупки делать дома https://sinapple.ru/collection/gigi/product/gigi-new-age-g4-powerful-eye-sream Современные технологии позволяют открыть нужную страничку на сайте с известными или пока еще незнакомыми для вас брендами, которые просто заинтересовали https://sinapple.ru/collection/phytomer/product/phytomer-hydracontinue-12h-moisturizing-flash-gel Мы уверены, что вы не пройдете мимо продукции, представленной Spadream, ведь она действительно уникальна, благодаря эффективности, высокому качеству https://sinapple.ru/collection/phytomer/product/phytomer-sun-active-protective-sunscreen-dark-spots-signs
Прием заказов 24 часа в сутки https://sinapple.ru/collection/cantabria-labs-ispaniya/product/cantabria-labs-neoretin-discrom-control-lightening-peel
Your comment is awaiting moderation.
Сейчас куча сайтов с фильмами, но после длительного теста я определил для себя один – это Лордфильм без регистрации. Что меня в нем подкупило? Во-первых, порядочность . Нет обмана о «супер-качестве», а реально хороший контент . Во-вторых, скорость . Страницы грузятся мгновенно , а подгрузка видео незначительна . В-третьих, уважение к пользователю . Администрация внимательны к пожеланиям и постоянно улучшает функционал. В прошлом месяце, например, добавили возможность создания плейлистов для сериалов. Если вы в поиске стабильный, быстрый и удобный киносайт, то вы его уже нашли . Советую к использованию. – https://lordfilm-online.top/
Your comment is awaiting moderation.
Геосинтетические материалы https://stsgeo-spb.ru для строительства и благоустройства в Санкт-Петербурге и ЛО. Интернет-магазин геотекстиля, георешёток, геосеток и мембран. Работаем с частными и оптовыми заказами, быстро доставляем по региону.
Your comment is awaiting moderation.
Интернет-магазин https://stsgeo-krd.ru геосинтетических материалов в Краснодар: геотекстиль, георешётки, геоматериалы для дорог, фундаментов и благоустройства. Профессиональная консультация и оперативная доставка.
Your comment is awaiting moderation.
17 сентября 2021 https://skyprofi.ru/tipovye-resheniya/natyazhnye-potolki-11m2/
Площадь 77 м2 Теневои? профиль KRAAB SYSTEMS 45 м2 Обработка внешнего угла KRAAB 23 Обработка внутреннего угла KRAAB 15 Встроенныи? трек 4 https://skyprofi.ru/rew/page/2/
Вообще, вы сможете найти довольно много интересной информации у нас на сайте, например:
Тканевые потолки также имеют цветовое разнообразие https://skyprofi.ru/faq/govoryat-chto-probka-ot-shampanskogo-pri-vystrele-mozhet-probit-natyazhnoj-potolok-pravda-li-eto/
Они будут выглядеть не только красиво, но и сохранят благоприятный микроклимат в помещении благодаря своей структуре https://skyprofi.ru/stati/glyancevyj-ili-matovyj-natyazhnoj-potolok-chto-luchshe/
14 декабря 2021 https://skyprofi.ru/stati/oranzhevyj-natyazhnoj-potolok/
Парящий натяжной потолок на чёрном профиле, с чёрной гардиной для скрытого карниза и теневым профилем за гардиной https://skyprofi.ru/stati/vidy-natyazhnyx-potolkov/
Your comment is awaiting moderation.
Продажа систем видеонаблюдения, ОПС и GSM сигнализации, IP-видеонаблюдения https://secbuy.ru/catalog/shkafy-shchity-i-boksy/
Санкт-Петербург https://secbuy.ru/catalog/povtoriteli_interfeysa/
Каталог оборудования систем безопасности представлен наиболее востребованными категориями товаров, среди которых:
The product is already in the wishlist! В отложенных https://secbuy.ru/
178 667 руб https://secbuy.ru/catalog/oborudovanie-dlya-epidemiologicheskogo-kontrolya/
/шт https://secbuy.ru/catalog/preobrazovateli_interfeysa_rs_422_485/
Сенсор: 1/2,9″ Разрешение: 1920х1080 Стандарт видеосигнала: AHD Фокусное расстояние: 2 https://secbuy.ru/catalog/razvetviteli_interfeysa_rs_422_485/
8 мм Габариты: 42х41х42 мм https://secbuy.ru/reviews/
Your comment is awaiting moderation.
Songwriters use an ai music generator to find chord progressions that they might not have thought of manually.
Your comment is awaiting moderation.
Our most valuable: https://podcasts.apple.com/tw/podcast/puzzlefree/id1697682168?i=1000737823170
Your comment is awaiting moderation.
Immerse yourself in the world of exciting betting with avatar game india and try your luck!
This aspect of the game keeps players on the edge of their seats, adding to the overall enjoyment.
Your comment is awaiting moderation.
RxFree Meds RxFree Meds RxFree Meds maccosmeticswholesaleoutlet wholesale mac pencil c 3 maccosmeticswholesaleoutlet mac makeup 12pcs brushes maccosmeticswholesaleoutlet mac makeup 12pcs brushes maccosmeticswholesaleoutlet mac makeup 13pcs brushes maccosmeticswholesaleoutlet mac makeup 1… because of that pragmatic play made this slot very dynamic, sugar rush slots demo excellent suitable for supporters with a bankroll that will be enough for long sessions. maccosmeticswholesalers mac makeup 5pcs brushes c 10 maccosmeticswholesaleoutlet mac makeup 16pcs brushes maccosmeticswholesalers mac makeup 32pcs brushes c 1 maccosmeticswholesalers mac makeup 9pcs brushes c 10 maccosmeticswholesalers mac makeup 5pcs … Guide To Bioethanol Fireplace Freestanding: The Intermediate Guide To Bioethanol Fireplace Freestanding Ethanol fireplace freestanding (Lacy)
https://deathscovilro1986.iamarrows.com/playbison-kody-promocyjne
Najnowsza wersja BonBon Blast – Sugar Rush jest 1.1.0, wydany na 15.12.2023. Początkowo był to dodane do naszej bazy na 15.12.2023. W Lazybar zawsze możecie powrócić do gry w kilka sekund! Wystarczy nacisnąć F5 lub CTRL+R, aby na nowo załadować saldo w trybie demo i znów cieszyć się darmową grą. I powiedzmy sobie szczerze, z trybem Free Spins w Sugar Rush, łatwo przegrać całą demówkę! Na szczęście bez problemu odświeżycie stronę i zaczniecie cukierkowe wyzwanie od nowa, jakby nigdy nic. TEGO NIE ZOBACZYSZ NA BLOGU O MODZIE więcej o mnie Zadzwoń Wild w grze bonusowej rozszerza się i zajmuje całą linię, że gra za pośrednictwem smartfona ograniczy Twoje możliwości hazardowe. Fishin Frenzy ma niesamowitą maksymalną wygraną w wysokości 10 000 x Twój zakład, automat 6×5 20 linii wygrywających w bonus joker karta bankowa może potrwać od 3 do 6 dni.
Your comment is awaiting moderation.
Informacje na temat wszystkich symboli, także premiowych, znajdują się w opisie automatu, dostępnym po uruchomieniu maszyny. Zwykle jest to tzw. tabela wypłat, do której dołączony jest krótki poradnik dla gracza. Oczywiście każdego gracza interesuje pytanie, jak wygrać na slocie Gates of Olympus. Niemożliwe jest udzielenie jednoznacznej odpowiedzi na to pytanie, ponieważ sam automat działa w oparciu o generator liczb losowych. Dlatego nie ma sposobu, aby zagwarantować 100% wygranej, ale można zwiększyć swoje szanse na wygraną. Pierwszą rzeczą, którą należy zrobić, jest zapoznanie się z tabelą wypłat. W tej grze środki trafiają na konto gracza za pojawienie się następujących symboli: Firma powstała w 2023 roku, theymight nawet pstryknął selfie z zdezorientowaną bestią. System najlepiej jest używać podczas 37 obrotów, tuż przed tym. Kasyno w loutraki odbierz swoje darmowe spiny bonusy tutaj, więc gracz nie ponosi najmniejszego ryzyka finansowego.
https://rciims.mona.uwi.edu/user/quininrobe1985
Jeśli automaty to nie Twoja bajka, spokojnie – nasza oferta gier stołowych też robi wrażenie. Znajdziesz tu wszystkie klasyki: Decydując się na grę w Gates of Olympus, zanurzasz się w mitycznej narracji, w której każdy obrót odsłania nowy rozdział potencjalnej fortuny i niebiańskiej łaski. Gra, dzięki przyjaznemu interfejsowi i różnorodnej ofercie zakładów, gwarantuje przystępność zarówno doświadczonym graczom, jak i nowicjuszom. Co więcej, jego kompatybilność z wieloma urządzeniami gwarantuje, że do bram tego boskiego królestwa można uzyskać dostęp w dowolnym czasie i miejscu, oferując wszechstronne doświadczenie kasyna online Gates of Olympus. Najlepsze kasyna online rozliczają cashback bez obrotu i w złotówkach a raport strat publikują w panelu. Reload działa uczciwie, gdy obowiązuje limit stawki na spin i jasne wyłączenia gier stołowych. Warto śledzić kalendarz promocji, bo rotacja ofert bywa związana z premierami slotów.
Your comment is awaiting moderation.
Akcja Gates of Olympus 1000 rozgrywa się na siatce w formacie 6×5 i zawiera popularną mechanikę opadających wygranych. Stojąc obok bębnów, Zeus może uderzyć piorunem w dowolnym momencie gry podstawowej lub darmowych spinów, aby przyznać losowe mnożniki od 2x do 1000x. Czego oczekiwać: Nie pobieramy żadnych opłat od graczy. Potencjalne prowizje nie mają wpływu na obiektywizm naszych recenzji. Wydany pod koniec 2023 roku automat Gates of Olympus 1000 to odświeżona wersja hitu od Pragmatic Play. Gracze chętnie wybierają ten slot ze względu na swoje świetne funkcje. Są wśród nich darmowe spiny i możliwość kupowania funkcji bonusowych. Maksymalny potencjał wygranych 15000x daje znaczną przewagę nad standardowymi slotami mitologicznymi jak Age of the Gods (5000x) czy oryginalny Gates of Olympus (5000x). System mnożników do 1000x oraz funkcja darmowych spinów z kumulacją zapewniają większą złożoność niż tradycyjni konkurenci. Bezpośrednimi rywalami są inne ulepszone sloty mitologiczne od głównych dostawców, choć niewiele z nich dorównuje wszechstronnemu zestawowi funkcji i potencjałowi wygranych.
https://jobs.landscapeindustrycareers.org/profiles/7465443-shane-ruiz
Aktualizacja ceny Kingdom Two Crowns Norse Lands PS4: 28-10-2025 Rozszerzenie pozwala ci odkrywać zupełnie nową mapę wypełnioną ukrytymi skarbami i potężnymi artefaktami, podczas gdy ty podejmujesz ekscytujące wyzwania inspirowane starożytną Grecją. Odkrywaj i odblokowuj mitologiczne wierzchowce, takie jak Cerber i Pegaz, i stwórz niezłomną obronę przed bardziej wymagającym zagrożeniem ze strony Chciwości, które będzie atakować nocą. Prowadź natarcie frontalnie dzięki nowej mechanice oblężniczej, zbierz flotę z niszczycielskimi balistami montowanymi na statkach i odblokuj unikalne artefakty, które pomogą ci w walce. Szukaj mądrości u Wyroczni i władaj potężną technologią ognia, aby zwalczyć rosnące zagrożenie ze strony Chciwości.
Your comment is awaiting moderation.
Dive Deeper: https://fbawinterhills77.com/reshenija-dlja-mediabainga-i-arbitrazha/marketplejs-akkauntov-kupit-akkaunt-instagram-8/
Your comment is awaiting moderation.
Najważniejszym pojęciem jest warunek obrotu (wagering requirement). To mnożnik, który określa, ile razy musisz postawić kwotę bonusu, zanim będziesz mógł wypłacić wygrane. Szukając najlepszych promocji w kasyno online 2025, warto pamiętać, że kluczowym wskaźnikiem jest niski wymóg obrotu bonusem na start. Im jest on niższy, tym oferta staje się bardziej korzystna dla gracza. Yes – almost all children on the spectrum have dietary requirements that need attention. Due to the nature of ASD, autistic people can be fussy eaters with varying eating habits and particular food choices. Additionally, certain foods may also cause problems, or the lack thereof can cause deficiencies, thus, limiting the choices available to them even more. W ofercie InstaSpin znajduje się ponad 2000 gier, w tym popularne sloty takie jak Big Bass Splash, Temple Tumble, Big Bass Bonanza oraz Book of Dead.
http://www.redsea.gov.eg/taliano/Lists/Lista%20dei%20reclami/DispForm.aspx?ID=3189300
However, it is absolutely normal to lose at online pokies. You have to unlock your sign-up package in your account settings before you can claim it, youll need to register your account. Zostaw e-mail, a nie przegapisz ekskluzywnych bonusów i ważnych nowych informacji. Pozytywne aspekty automatu Gates of Olympus to: Pałeczki do jedzenia są wykonane z drewna, bambusa, metalu, kości, a obecnie także z plastiku. Srebrne pałeczki były rzekomo używane w Chinach do wykrywania zatrutego jedzenia. Jeśli obecna była trucizna, pałeczki czerniały w wyniku reakcji chemicznej. Ciekawostki: Korzystanie z bezpłatnego Gates of Olympus niesie ze sobą szereg korzyści. To mistrzostwo wolne od ryzyka, w którym możesz odkrywać i rozumieć mechanikę gry, funkcje specjalne i zwycięskie kombinacje we własnym tempie. Darmowa gra Gates of Olympus pozwala tworzyć strategie, odkrywać różne opcje zakładów i zanurzyć się w mitycznym świecie bez presji hazardu na prawdziwe pieniądze. Co więcej, jest to okazja, aby cieszyć się wciągającą grą wysokiej jakości, dzięki której możesz mieć pewność, że decydując się na hazard na prawdziwe pieniądze, zrobisz to z pewnością i wiedzą.
Your comment is awaiting moderation.
Tak, system bonusowy został zaprojektowany z myślą o każdym graczu. Nie ma znaczenia, czy uprawiasz hazard, czy wolisz automaty. Betano ma jeden z najlepszych programów lojalnościowych wśród kasyn online. Odwiedzający, którzy chcą wypróbować Gates of Olympus, mogą spodziewać się hojnego bonusu powitalnego i darmowych spinów podczas aktywnej gry. Łącznie w Gates Of Olympus automat online na pieniądze mamy do dyspozycji 11 oryginalnych symboli. Te grafiki to: korona, klepsydra, pierścionek, kielich, pięć klejnotów w różnych kolorach, grecki bóg i symbol mnożnika. Każda z nich ma odmienną wartość, którą gracz otrzymuje za wylosowanie danej kombinacji. W grze znajdziemy również wiele dodatków do rozgrywki. Jednym z nich jest scatter, który przedstawia Zeusa.
https://esetanem1973.iamarrows.com/nv-casino-bonus-code
Jeśli chodzi o najlepsze kasyno online, warto wymienić HotSlots. Jest ono liderem wśród kasyn, pod wieloma względami. Patrząc choćby na same kasyna mobilne, HotSlots prezentuje się bardzo dobrze i wyprzeda pozostałe, najlepsze kasyna online. Rywalizacja w tym aspekcie trwa jednak cały czas! Gates of Olympus to slot o wysokiej zmienności, więc nie zawsze wygrane wpadają szybko, ale kiedy już trafi się dobry spin, może być naprawdę ciekawie. Sprawdźmy, statystyki gry, wbudowane promocje i co jeszcze ma do zaoferowania Gates of Olympus! Gates of Olympus Olympus Trueways Jednym z najpopularniejszych automatów inspirowanych grecką mitologią jest Gates of Olympus. Jeśli słyszałeś o tej grze i chcesz ją wypróbować, w niniejszej recenzji znajdziesz swój kompletny przewodnik po automacie. Eksperci Slotsjudge analizują kluczowe elementy gry, takie jak rozgrywka, funkcje specjalne, zmienność, potencjał wygranej oraz solidne RTP wynoszące 96,5%.
Your comment is awaiting moderation.
Oferta powitalna 70 darmowych spinów o wartości 80 $! Dołącz teraz! Cały proces trwa zazwyczaj kilka minut, co pozwala graczom szybko skorzystać z dostępnych ofert promocyjnych. Rejestracja Czy kiedykolwiek marzyłeś o tym, aby dostać się na szczyt Olimpu i być w niebie na uczcie bogów? Możesz się tam znaleźć, jeśli będziesz miał szczęście i wygrasz ogromnego jackpota podczas gry w Gates of Olympus. Twórcy tytułu inspirowali się mitami i umieścili na bębnach kamienie szlachetne w różnych kolorach oraz boskie symbole bogactwa: puchary, korony i złote klepsydry. Po prawej stronie ekranu gry unosi się bóg Zeus, który od czasu do czasu zapewnia graczom mnożniki. Kasyna z Gates of Olympus, jak i sam automat wspierają również urządzenia mobilne. Slot został zaprojektowany w nowoczesnej technologii HTML5. Dzięki niej Gates of Olympus na telefon jest dostępny bez konieczności instalacji – grasz bezpośrednio w oknie przeglądarki.
https://www.avatarwebradio.com/sugar-rush-od-pragmatic-play-recenzja-wyjatkowej-gry-slotowej-dla-polskich-graczy/
Yes, it’s about right, there’s probably more now, ‘cause it was 12 years ago. I own about 5 or 6 guitars, a couple of violins… So I got about 10-15 string instruments. I’ve got more whistles than… There’s about 50 whistles in my whistle case. Flagolettes, penny whistles, you know? I collect them, I have one of every kind of whistle that’s being manufactured now — all the cheap ones. And I got a couple of nice, expensive ones, but I actually don’t tend to play them a lot. Also I’ve got a couple of victorian ones, some with lead mouthpieces, so, well, you know. Yes, and two flutes, a clarinet… Hundreds of instruments. You know, a suitcase with little instruments. Używamy plików cookie, aby pomóc użytkownikom w sprawnej nawigacji i wykonywaniu określonych funkcji. Szczegółowe informacje na temat wszystkich plików cookie odpowiadających poszczególnym kategoriom zgody znajdują się poniżej.
Your comment is awaiting moderation.
Elementy wizualne i dźwiękowe w Mjolnir wynoszą doświadczenie z gry na niezwykłe wyżyny. Gra oferuje oszałamiające grafiki w tematyce nordyckiej, które przenoszą graczy do innej epoki. Towarzyszy temu potężna ścieżka dźwiękowa z motywami mitologicznymi, zapewniając głęboko immersyjne doświadczenie. Przy adaptacji mitologii do form rozrywkowych pojawiają się pytania o etykę i odpowiedzialność twórców. Ważne jest, aby nie upraszczać czy stereotypizować źródła, a jednocześnie unikać banalizacji i komercjalizacji. Szacunek dla pierwotnych przekazów i ich głębi jest kluczem do tworzenia wartościowych dzieł, które będą inspirować, a nie naruszać dziedzictwa. Mitologia to zbiór opowieści, wierzeń i symboli, które wywodzą się z dawnych kultur i religii. Od starożytnej Grecji, przez Rzym, aż po nordyckie wierzenia, mitologie pełnią funkcję wyobrażeniowego szkicu wyjaśniającego świat oraz miejsce człowieka w nim. Wspólnie tworzą one nie tylko narracje o bogach i herosach, ale także stanowią podstawę kulturowej tożsamości, co ma kluczowe znaczenie dla rozwoju wyobraźni. Mitologia wpływa na kształtowanie wyobraźni zarówno w sztuce, literaturze, jak i w nowoczesnych mediach, w tym w branży gier komputerowych.
https://coachingpsychecialozmiloscia.pl/przeglad-i-recenzja-sugar-rush-slodka-podroz-w-kasynach-online/
Wizualnie oszałamiająca gra slotowa online Gates of Olympus czerpie inspirację z wspaniałości starożytnej mitologii greckiej. Pragmatic Play stworzyło tę grę slotową, która przenosi graczy do gromowładnego królestwa Zeusa, gdzie zasiada na tronie i obserwuje bębny. Ta gra slotowa wprowadza innowacyjną funkcję opadania, która eliminuje wygrywające symbole i pozwala nowym symbolom zająć ich miejsce, umożliwiając tym samym wielokrotne wygrane w jednym obrocie. Gates of Olympus Free Play Demo Co jeszcze jest ważne, kiedy odbieramy 20 free spinów? Oczywiście sama gra hot spot. Darmowe spiny standardowo są oferowane przez kasyna do wykorzystania na slotach. Warto więc, aby były to automaty hazardowe możliwie jak najbardziej atrakcyjne: z wysokim RTP (co najmniej 94%), ciekawymi opcjami specjalnymi i niską średnią zmiennością.
Your comment is awaiting moderation.
Moderne et épurée, l’interface principale s’articule autour d’une navigation fluide permettant d’accéder instantanément aux 4500+ jeux disponibles. Particulièrement adaptée aux écrans tactiles, cette plateforme offre une expérience identique sur ordinateurs, tablettes et smartphones via navigateur web. maltonfestivalofracing.co.uk – Amazing festival coverage, really captures the excitement of racing events beautifully. buy Zoloft online without prescription USA buy Zoloft online without prescription USA buy Zoloft online Avec son interface bien soignée, Bruno Casino invite les joueurs français à jouer à +6 000 jeux et à profiter d’événements sportifs majeurs. Ce nouvel établissement réglementé à Kahnawake depuis 2021 possède même une application mobile vous permettant de recevoir ses codes bonus sur et sans dépôt ainsi que vos gains encaissables sur PC et sur téléphone. Méthodes de dépôts et de retraits, sécurité, assitance et promotion, l’opérateur excelle sur tous ces plans, et nous allons le démontrer dans cet avis des offres du casino en 2025.
https://nvtechnoengineering.com/penalty-shoot-out-devoplay-decouvrez-un-jeu-de-casino-en-ligne-captivant-pour-les-joueurs-francais/
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data. Les symboles du jeu et proposer des expériences personnelles. En mettant l’accent sur le thème de la Grèce antique. Dès votre arrivée sur le thème de la Grèce antique. C’est un excellent moyen de développer l’économie de la Grèce antique. Selon les derniers jeux de hasard, surtout avec l’intégration de la mythologie et la Grèce antique. Pragmatic Play ne pouvait pas manquer l’opportunité de proposer Gates of Olympus 1000 sur mobile ! Comme l’ancienne version, l’interface s’adapte parfaitement aux petits écrans d’iPhone, Samsung ou même d’iPad. Vous n’avez qu’à lancer votre casino partenaire de Pragmatic depuis un navigateur web et à cliquer sur ” Gates of Olympus 1000 ” pour jouer sans téléchargement.
Your comment is awaiting moderation.
© Svenska Spel Sport & Casino AB Enligt mig är inte i bonusen du tar hem storkovan i Gates Of Olympus. Efter många timmar spelande har jag märkt att multiplikatorfunktionen betalar bäst. Man märker tydligt när Zeus ska smälla till med en mulitplikator då han reser sig upp. 18+ Gambling can be addictive. Play responsibly. gamblingtherapy.org & gamblersanonymous.org Det finns också en kaskadfunktion, vilket betyder att vinnande symboler försvinner och ersätts av nya – perfekt för att dra igång flera vinster på ett enda snurr. Du har också möjlighet att köpa dig direkt in i bonusspelet om du inte har tålamod att vänta, även om det kostar 100 gånger din insats. Det finns också en kaskadfunktion, vilket betyder att vinnande symboler försvinner och ersätts av nya – perfekt för att dra igång flera vinster på ett enda snurr. Du har också möjlighet att köpa dig direkt in i bonusspelet om du inte har tålamod att vänta, även om det kostar 100 gånger din insats.
https://allviolinshops.com/mega-fortune-dreams-en-casinorecension-for-svenska-spelare/
The Gods of Secrecy spelautomaten är utvecklad med HTML5 så den är kompatibel med alla mobila enheter. Det kan lätt nås på alla Android & iOS-enheter. Stakelogic har sett till att du får en bärbar upplevelse i toppklass när du spelar det här spelet på en mindre skärm. Det enda du behöver göra är att öppna spelet i din valda webbläsare. När vi hade upprepat vår fråga fick vi vänta på svar i 12 minuter. Svaret vi fick var utförligt och innehöll extra information som kan vara relevant. Gates of Olympus Super Scatters RTP ligger på 94,52 %, vilket är något under genomsnittet för moderna slots. Med Ante-insats sjunker RTP marginellt till 94,47 %, och vid köp av bonusfunktioner ligger det på 94,49 %. Även om det inte är lika hög RTP som jag hade önskat så kompenseras det av spelets extremt höga volatilitet och enorma maxvinst.
Your comment is awaiting moderation.
playboy888
Advanced security techniques are implemented to secure personal details and transaction data on the platform.
Your comment is awaiting moderation.
918kiss lama original offers a convenient way to download the gambling application.
Players often think about the safety of downloading APK files.
Your comment is awaiting moderation.
Discover a world of entertainment with 777 bet casino, where unforgettable gaming moments and big wins await you!
This diversity not only enhances the user experience but also keeps bettors engaged.
Your comment is awaiting moderation.
vpower apk download our website makes it easy and fast to access all the features of this great game.
Recently, the vpower apk has become a widely discussed application that attracts a lot of users.
Your comment is awaiting moderation.
В казино казино самолетик 1win игроки могут наслаждаться захватывающими взлетами и множеством возможностей для выигрыша.
Изучение условий игры и правил важно для успешной игры.
Your comment is awaiting moderation.
Free video chat emerald chat app download find people from all over the world in seconds. Anonymous, no registration or SMS required. A convenient alternative to Omegle: minimal settings, maximum live communication right in your browser, at home or on the go, without unnecessary ads.
Your comment is awaiting moderation.
Free video chat emerald chat webcam chat find people from all over the world in seconds. Anonymous, no registration or SMS required. A convenient alternative to Omegle: minimal settings, maximum live communication right in your browser, at home or on the go, without unnecessary ads.
Your comment is awaiting moderation.
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data. Situado em uma grade de 6×5 com o Deus grego adjacente às colunas, os jogadores devem combinar pelo menos oito símbolos – incluindo coroas, cálices e pedras preciosas – em qualquer giro para obter um ganho. Símbolos pagam em qualquer lugar na tela, e um recurso tumble remove as combinações ganhadoras da jogada, sendo substituídas por novos ícones que caem do topo do jogo. Mas, uma última observação, nem todos os jogos estarão disponíveis no modo demo. Por exemplo, os jogos de casino ao vivo normalmente não estarão disponíveis de forma gratuita, pois precisam de dealers reais e muitos equipamentos para difundir os jogos. Mas aqui no Temple of Slots fazemos o possível para oferecer uma boa seleção de todos os jogos grátis, para que você tenha muitas opções para escolher.
https://tokoacrylic.co.id/archives/17356
You can email the site owner to let them know you were blocked. Please include what you were doing when this page came up and the Cloudflare Ray ID found at the bottom of this page. A volatilidade alta, torna o Gates of Olympus 1000 perfeito para aplicar as nossas estratégias preferidas para as slot machines. As nossas estratégias para slots visam a maior volatilidade possível. A Betclic oferece mais de 1.600 slots online e conta com mais de 25 fornecedores reconhecidos no mercado, incluindo slots da Thunderkick (a nossa preferida, pessoalmente), iSoftBet e EGT. Estas ofertas são ativadas durante o registo. No formulário de inscrição, no campo “código de amizade”, insira o código promocional ESC Online ESTORILMAX para desbloquear estas ofertas. O Gates of Olympus, ou jogo do velho do raio, é um caça-níquel online desenvolvido pela Pragmatic Play, com temática mitológica grega, em que Zeus é o personagem principal. O objetivo do jogo é girar as bobinas e formar combinações vencedoras com pelo menos 8 símbolos iguais, utilizando o sistema de pagamento em qualquer lugar.
Your comment is awaiting moderation.
De online game-industrie is nu weergegeven in de heldere, vrolijke kleur die van het nieuwe scherm afspat. De nieuwe pluimveehoofdrolspelers zijn schattig bewegend, met expressieve reacties op bijna-missers en succesvolle kruisingen. De auto’s zijn gevarieerd en complex, van gestroomlijnde voetbalauto’s tot logge auto’s, elk met zijn eigen unieke structuur. Wij helpen u graag in onze showroom met het zoeken naar de vloer die bij uw wensen en ruimte past. MARKANT of een CITAAT De luchtopnamen werden gemaakt door Wiebe de Jager, met behulp van een Panono 360º camera onder een Yuneec Typhoon H hexacopter. Op de serie foto’s is onder andere het grootste kratermeer van de regio te zien, alsook de stad Gerolstein, het kratermeer van Windsborn, de Betradaburg en de Manderscheider Burgen. Veiligheid Panama CityWij vonden Panama City een fijne plek om onze reis door Panama te starten. Er hangt een ontspannen sfeer en er is genoeg te doen om je minimaal een dag of drie te vermaken. De stad voelt veilig aan en er zijn veel vriendelijke behulpzame agenten op straat. Natuurlijk moet je zelf goed nadenken welke wijken je bezoekt en kun je op veel plekken ´s avonds beter een taxi pakken maar dit geldt voor de meeste grote steden.
https://mescla.cc/?p=48120
Ken je dat gevoel dat je jezelf even onoverwinnelijk voelt nadat je flink hebt gesnoept? In de gokkast van Pragmatic Play genaamd Sugar Rush krijg je dit gevoel al bijna zodra je de gokkast opent. Dit is niet de eerste zoete gokkast van Pragmatic Play: eerder bracht de provider Sweet Bonanza al uit waarin alles om zoetigheid draaide. Ook Sweet Bonanza Candyland is een mierzoet spel, dit spel speel je in het live casino. Gids voor ouders De felle kleuren, opbeurende muziek en snelle gameplay is dit dan ook een perfecte gokkast om snel die suikerkick te halen. Sugar Rush is ook erg geschikt om te spelen op mobiele devices zoals een iPad, iPhone of Android Device. Met zijn 5 rollen beneden en 6 rollen boven is het met de IncaGold gokkast mogelijk om 20 winlijnen tegelijk te spelen, waar symbolen moeten uitlijnen om winnende combinaties te maken en in sommige spellen kunnen ze in verschillende posities. Engels, mobiele versie van het spel sugar rush en na de derde overwinning ga je terug naar 1 en herstart.
Your comment is awaiting moderation.
LuckyBlock heeft onder de sites die Cruks omzeilen de allerbeste welkomstbonus in huis. Deze bonus loopt op tot maximaal €25.000 + 150 free spins, en is ook beschikbaar voor jongvolwassenen. Ben je 18 jaar of ouder en heb je nog geen account bij LuckyBlock? Profiteer dan van deze bonusaanbieding. Sugar Rush 1000 is een weerzien met dezelfde (bonus) features als het origineel. Ze smaken alleen nét wat beter, aangezien de uitbetalingen flink zijn opgepimpt. We lopen alle speciale features in dit deel van de Sugar Rush 1000 slot review even kort met je door: Waar je bij andere slots vaak maar één of twee bonusfeatures vindt, word je bij Sugar Rush verrast met verschillende extra’s. Ten opzichte van andere populaire slots biedt Sugar Rush dan ook een unieke spelbeleving, zowel qua visuele stijl als qua gameplay.
https://unicohogarec.com/een-verleidelijke-zoete-wereld-sugar-rush-review/
Maar de bekendste variant is ongetwijfeld Mission Uncrossable. Het spel staat op naam van Roobet, een onbetrouwbaar online casino. Hier gaat het letterlijk om een kip die de straat wil oversteken en moet opletten voor het verkeer. Je wint er tot wel 3 miljoen keer de inzet met gelijke kansen op verlies als bij Chicken Road. Dans de nombreux casinos en ligne sous licence, les joueurs peuvent jouer à Chicken Cross gratuitement en utilisant la version démo. Pour la lancer, les utilisateurs doivent : Lightning Storm is een online game show uit het casino. Evolution blijft maar nieuwe en innovatieve live casino spellen ophoesten. Hier gebruiken ze het DigiWheel opnieuw net als in Funky Time, om… In Chicken Road zijn de spelers zij kunnen verkrijgen A winnen snel einde van de Eerst klik van de knop . De regels eenvoudig toestaan Van toename onmiddellijk De evenwicht en van poging De rilling van de spel . Chicken Road de weg is al beschikbaar in veel casino online En het maakt opgewonden beide beginners dat de spelers deskundigen .
Your comment is awaiting moderation.
Niet alleen bij Sugar Rush free play kun je gratis spins ontvangen, maar ook als je je eigen geld inzet! Om gratis spins te ontvangen bij dit slot, moet je scatters landen op de rollen tijdens het basisspel. Het aantal gratis spins dat je ontvangt, hangt af van het aantal scatters dat je draait: Vergeet traditionele winlijnen! Bij Sugar Rush 1000 win je door clusters te maken van minstens 5 dezelfde snoepjes die horizontaal of verticaal verbonden zijn. En met een speelveld van 7×7 zijn de mogelijkheden eindeloos. Probeer Plinko zelf! Ontdek onze demoversies, experimenteer met het laten vallen van de balletjes , leer de functies kennen en speel direct gratis Plinko. Deze Sugar Rush game laat je overwinning zoeter dan ooit smaken. Bij ons online casino Sugar Rush spelen geeft een nieuwe definitie aan de term ‘mierzoet’. De achtergrond van dit Sugar Rush slot bestaat voornamelijk uit roze en paarse tinten. De kleuren doen denken aan een suikerspin. Het perfecte spel voor de echte zoetekauw.
https://spaanslerenamsterdam.com/sugar-rush-slot-review-zoet-en-spannend-online-casino-spel-van-pragmatic-play/
Bestellingen voor 16:00 van maandag tot en met zaterdag worden dezelfde dag verzonden met DHL en worden in de meeste gevallen de volgende dag bezorgd Fountain Pen Day – gebruik kortingscode FPD25 voor 20% KORTING Totaal (0) producten€0,00 Een van mijn geweldige Sugar Rush speeltips: de free spins zijn opnieuw te triggeren. De 20bet-aanbieding combineert duizenden sportevenementen met live weddenschappen en casinospellen, maar zonder dat ze extra geld hoeven in te zetten. Zorg ervoor dat je het volledige bonusbedrag binnen 7 dagen gebruikt, dus ze troosten elkaar en zelfs kussen. Roulette op kleur spelen het beleid van de Raad van bestuur geeft vaak suggesties voor casino’s te volgen in plaats van biedt specifieke regels, met het systeem normaal gesproken debiteren van een groter bedrag in afwachting van forex tarieven. Het is belangrijk op te merken dat bancaire methoden kunnen veranderen afhankelijk van de regio een speler is gebaseerd, en vervolgens het verschil in krediet dagen later terug te keren.
Your comment is awaiting moderation.
The Scatter symbol in More Magic Apple takes the form of a majestic castle, reminiscent of the grand palaces found in fairy tales. Landing three or more of these enchanted castles anywhere on the reels is the key to unlocking the Free Spins feature. But the magic doesn’t stop there – the number of Scatters also plays a crucial role in determining the multiplier value for the Free Spins round. This dual function of the Scatter adds an extra layer of anticipation to every spin, as players eagerly watch for these symbols to align and reveal their full potential. The RTP (Return to Player) for More Magic Apple is 95.78%, slightly below the industry average of 96%. If you wager $100, you can expect to get back $95.78 on average. However, keep in mind that the volatility of this slot is high.
https://2bscargoegypt.com/more-magic-apple-slot-new-release-whats-new/
Yes, many online casinos offer demo versions of the lucky penny slot allowing players to practice without risking real money. The coast and hills around Trefor and extending into the wider Llyn Peninsula is a lovely unspoilt piece of the country for for walking, coastline, beaches, nature and ancient settlements. So what does it all add up to? In short, Lucky Penny is the real deal. Whether you’re a seasoned slot enthusiast or just looking to try your luck for the first time, this game offers an unparalleled combination of excitement, innovation, and potentially life-changing jackpots. Slot lucky penny by gameart demo free play it is also great to see the cascading wins feature in play too as this is hugely popular amongst online slot players and will be a big draw for many to spin the reels of The Legend of the Ice Dragon, you could attempt to relish in their defeat.
Your comment is awaiting moderation.
Spend a luxurious evening with good day 4!
Together, we can inspire a culture that values joy and creativity.
Your comment is awaiting moderation.
Find out further interesting facts about the casino in the following Slothino review, but unfortunately it does not have any specific terms and conditions on the websites. We always check out the sites parent company, aztec Fire Hold and Win odds calculator which will surely enhance your gaming experience no matter if taken on a mobile or desktop machine. “Do you have more bonuses for Phoenix Fire slot? Can I get 50 free spins no deposit bonus?” by | Jun 22, 2024 | Uncategorized Age 18 and above only to register or play at Surebet247. Play Responsibly. A thrilling expedition in Aztec Fire 2: Hold and Win can offer plenty of pleasant emotions and potentially substantial wins. The bright design, inspired by the culture of the ancient Aztecs, makes each spin a real adventure. Special Wild and Scatter symbols continuously add intrigue to the gameplay, while the bonus game with symbol locking, the possibility of unlocking additional rows, and the chance to catch impressive jackpots turns this slot into a real treasure trove for treasure hunters.
https://kuda999.org/lucky-penny-slot-by-3-oaks-an-exciting-spin-for-uk-players/
One of the biggest providers of slots & live casino titles in the US, Pragmatic Play has become the premiere software studio to watch out for in the market. Beginning operation in 2015, Pragmatic Play have been integral in producing some of the most memorable slots titles, with titles like Big Bass Bonanza spawning over 25+ sequels. Mystake Casino Login App Sign Up Aztec fire game there are a number of online casinos that cater specifically to Australian players and offer these benefits, along with a huge variety of casino games for players to enjoy. The dealer will often offer the player Insurance (or the opportunity to take an Even Money pay on a Natural) if the dealer is showing an Ace, substitute images. With no deposit bonuses and free spins, FortuneJack. The casino offers over 1,000 slot machines from top providers like NetEnt, and mBit Casino.
Your comment is awaiting moderation.
Are you ready to uncover the treasures of the Aztec civilization and experience the thrill of the Aztec Fire Hold and Win slot game? Head over to Casitsu today and embark on a captivating adventure filled with excitement and rewards! Online casinos provide a way to play a variety of games from your computer or mobile device. Here, at Mr Luck, you can explore a range of options, including roulette, blackjack, online slot machines, and live dealer games. Each game type has its own rules, features, and outcomes based on chance. This page will help you understand what’s available and how these games work. Not only does it offer a massive max win, but it also comes with a variety of features such as Cascading Wins, a Super Gems Bonus, a Free Spins Bonus with possible retriggers and an Unlimited Win Multiplier! That’s right, Unlimited – something that’s quite unique in the world of online slots.
https://geber888.org/big-bass-bonanza-floats-my-boat-a-players-perspective/
Amatic Industries has kept the Lucky Joker 10 Cash Spins slot machine simple, which we think is perfect for players who don’t like many bells and whistles. The game has 10 fixed paylines, low volatility, and 97.12% RTP. Increase your chances to win with wilds and land COIN symbols to trigger the Cash Spin Feature. Slot machines often display a series of spins where players appear to be only one symbol away from a win, leading them to believe that they almost won falsely. Slot games do not work cyclically, and slot machine jackpots don’t become due. Legacy of Dead is an online slot developed by Play’n GO. It’s yet another “Book” game. The slot has 5 reels, 3 rows, and 10 fixed pay lines. This penny slot offers higher win potential even with the smallest 1p bets. Spin the legendary big wheel for iconic prizes and classic excitement in this fan-favorite slot sensation!
Your comment is awaiting moderation.
How do you get these daily free spins? Simply sign up for an account at ReveryPlay Casino and check your account daily for any available free spins. Start spinning and winning today with 247 Slots! Never has the game been more realistic as you spin your way to the casino floor with bonuses and eye catching excitement you can play on your computer, phone or tablet! You’ll find Big Bass Splash pretty much everywhere – from traditional bank transfer casino sites to newer and more modern casino apps. This Pragmatic Play casino slot has spawned a whole lot of spinoffs, including a Megaways game and even a horse racing-themed slot. The gameplay peaks during the Free Spins bonus round, where a dynamic Total Multiplier is introduced. This multiplier begins at 1x and increases with every cascade, potentially reaching up to 1000x. All wins during this feature are multiplied by the current total value, creating a pathway to the game’s massive 20,000x maximum win potential. For players seeking immediate action, a Buy Bonus option provides instant access to this lucrative free spins feature.
https://tehnoauto.rs/2025/12/02/silver-numbers-feature-in-super-stake-roulette-a-uk-perspective/
Sign in to your account Hit the jackpot with old-school slot machines. If you have ever seen the Wolf Run, extra spel casino no deposit bonus codes for free spins 2025 so scrolling and tapping your way around the site couldnt be easier. As European Gaming reports, Yuriy Muratov, Chief Business Development Officer at 3 Oaks Gaming, said: “Aztec Fire 2 is a worthy sequel with the addition of the Unlockable Rows feature being the main differentiator from the original. This slot takes players on a breathtaking jungle journey where they can uncover modifiers and six in-game jackpots, rounding off our 2023 games roadmap in style.” The page you are trying to visit has restricted access. If you are using a proxy or VPN please turn these off and try again. At Lucky Slots, safety and security go hand-in-hand with entertainment. Our platform is fully compliant, ensuring a worry-free experience. Engage socially with friends, compete in leaderboards, and discover why Lucky Slots is rapidly becoming known as the best internet casino around.
Your comment is awaiting moderation.
Emissão de guia de pagamento de taxas de serviços administrativos. Os melhores sites de jogos de azar são os que oferecem segurança, e isso é a nossa prioridade máxima e, por isso, só apresentamos aqui cassinos online com licença da Secretaria de Prêmios e Apostas – SPA do Brasil. Consulta de editais de licitação, tomada de preço e pregões. Futsal começa com cerca de 600 alunos de escolas municipais na 3ª Olimpíada e Paralimpíada “Pequenos Esportistas” Embora não exista uma fórmula mágica para ganhar em casinos, a estratégia de Money Coming Expanded Bets pode ser uma ferramenta valiosa para apostadores que desejam aumentar suas chances de sucesso, transformando a experiência de jogo em uma atividade mais lucrativa e emocionante.
https://ambicagrp.in/master-joker-da-pragmatic-play-uma-revisao-completa-para-jogadores-brasileiros/
Os jogos 777 são uma plataforma online que oferece uma ampla gama de jogos de cassino para entretenimento e a chance de ganhar dinheiro real. O site possui uma interface conveniente e fácil de navegar, permitindo que os usuários encontrem e escolham jogos de acordo com seus gostos facilmente. Com uma interface amigável, uma variedade de jogos e um sistema de segurança confiável, o site oferece aos jogadores a oportunidade de desfrutar de jogar e testar sua sorte em uma atmosfera de cassino real diretamente de casa. Ao abrir o aplicativo, você encontrará Money Coming facilmente na seção de slots. A jogabilidade é fluida, com gráficos de alta qualidade e animações que se mantêm consistentes com a versão de desktop. Aqui estão algumas vantagens de jogar Money Coming no aplicativo:
Your comment is awaiting moderation.
Para aqueles que preferem jogar em um computador, o 1Win oferece uma versão completa da plataforma para desktop. Veja a seguir como começar a jogar o Money Coming em um PC: A slot Money Coming é uma aventura emocionante no mundo da riqueza e da sorte. Desenvolvido pela Tada, esse caça-níqueis chama a atenção não apenas por seu design colorido, mas também por sua jogabilidade empolgante. Testei tanto a Money Coming demo quanto a versão a dinheiro real para saber se o slot realmente vale a pena e como ele se diferencia de outros jogos populares de casino com propostas similares. Na minha experiência, depois de uma análise detalhada, o Money Coming tem mais pontos positivos do que pontos de melhoria. Os jogadores que usam dispositivos iOS também podem aproveitar o Money Coming graças à versão móvel do 1Win. Embora o aplicativo oficial para iOS não esteja disponível na App Store, você pode usar a versão otimizada para celular do site:
https://m6h.831.myftpupload.com/review-do-book-of-dead-da-playngo-emocao-e-aventura-no-cassino-online/
Central de Ajuda You can email the site owner to let them know you were blocked. Please include what you were doing when this page came up and the Cloudflare Ray ID found at the bottom of this page. You can email the site owner to let them know you were blocked. Please include what you were doing when this page came up and the Cloudflare Ray ID found at the bottom of this page. Central de Ajuda You can email the site owner to let them know you were blocked. Please include what you were doing when this page came up and the Cloudflare Ray ID found at the bottom of this page. You can email the site owner to let them know you were blocked. Please include what you were doing when this page came up and the Cloudflare Ray ID found at the bottom of this page. You can email the site owner to let them know you were blocked. Please include what you were doing when this page came up and the Cloudflare Ray ID found at the bottom of this page.
Your comment is awaiting moderation.
Sugar Rush 1000 speel je bij deze casino’s: In Malta you are not allowed to participate in games of chance if you are under 18 years of age and therefore, when you register on our website, we check that you are over 18 years of age. We recommend you take the following measures to help protect minors from accessing our website: Game of the week – Casino • Leestijd 2 min Een enorm voordeel op de Sugar Rush is de Tumble Feature. De functie biedt spelers de kans om meerdere winnende clusters te maken in één spin. Zodra de speler een prijs wint, verdwijnen alle winnende symbolen van het speelscherm. Daarvoor komen nieuwe symbolen in de plaats. Het kan voor een kettingreactie aan winsten zorgen op het Sugar Rush slot van Pragmatic Play. Zoals ik al vermelde, heeft Sugar Rush enkele voorgangers die in onze geselecteerde Zamsino casino’s nog steeds tot de top behoren. Sweet Bonanza heeft ondertussen zelfs een cultstatus gekregen. Het spel en het idee voor het spel werd ondertussen vele keren gekopieerd door de concurrentie. Pragmatic Play maakte er zelf ook een live spel van.
https://equipmentfunding.ca/?p=44165
Hoewel CRUKS omzeilen mogelijk is, brengt het risico’s met zich mee. Spelers die zelf hebben besloten om deze platforms te gebruiken, moeten weten dat ze hun eigen goklimieten moeten instellen en hun eigen gokgedrag in de gaten moeten houden. Ja, naast Sugar Rush kun je ook Sugar Rush Xmas en Sugar Rush 1000 bij JACKS.NL uitproberen. De online casino industrie heeft Pragmatic Play te danken voor het zegenen van de markt met onderhoudende en leuke casino slots. Vanaf 2015 is Pragmatic Play een van de beste spelaanbieders wereldwijd op dit moment voor hun vlaggenschip-kwaliteit spellen. En ze lopen deze keer voorop met hun nieuwste release, het Sugar Rush spel. Het online casino biedt slots, tafelspellen, jackpot games en een live casino met tafelspellen als roulette, blackjack en poker. Het biedt op dit moment geen live game shows aan, zoals je misschien gewend bent van andere Nederlandse goksites.
Your comment is awaiting moderation.
aviator game online offers an exciting experience and the opportunity to win real money directly from your device.
This game combines elements of chance and strategy, making it appealing to a wide audience.
Your comment is awaiting moderation.
Gates of Olympus är vårt officiella spel utvecklat av Pragmatic Play för spelare i Sverige. Du kan starta ditt mytologiska äventyr med en insats från endast 2 SEK. Registrera dig hos ett av de bästa casinona och få en bonus på 150 %. “Gates of Olympus har en maxvinst på hela 5 miljoner kronor – på ett enda spinn!” Gates of Olympus Xmas 1000 caters to all bankrolls with its flexible betting range and Ante Bet feature. By activating Ante Bet for an extra 25% per spin, you double your chances of triggering free spins – perfect for players chasing the game’s biggest rewards. This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data.
https://xgs888.net/book-of-dead-%e2%b8%ba-en-granskning-av-playn-gos-aventyrsspel-for-svenska-spelare/
The Super Scatter system and stacked Free Spins bonus inject real heat into the classic theme, while the gorgeous visuals and satisfying audio design keep each spin immersive. If you’re into mythological drama and massive win potential, this game is a must-spin. Att spela casino slots online är oftast väldigt enkelt. Det finns ett par saker man kan påverka innan man börjar spela. Antal rader kan du i de flesta casino slots själv bestämma. Trots detta är det vanligaste alternativet att aktivera alla spellinjer så att man inte går miste om en storvinst. Insatserna är också något du själv påverkar. Du kan satsa från 1 kr upp till över 2000 kr per spin. Detta påverkar självklart också hur mycket pengar du vinner. Om du spelat videoslots hos SpeedyCasino har du säkert stött på termen MegaWays. Detta banbrytande spelsystem har på kort tid blivit en favorit bland slotspelare världen över – och vi förstår varför. I den här artikeln reder vi ut vad MegaWays är, hur det fungerar och tipsar om några riktigt heta MegaWays-slots att testa.
Your comment is awaiting moderation.
Rispetto ad altre software house, Playson non dispone attualmente di un’offerta corposa di slot online, tuttavia i suoi prodotti non hanno nulla da invidiare a livello di qualità e giocabilità rispetto alla concorrenza. Per questo l’azienda maltese è destinata a crescere e catturare fette sempre più importanti di clienti. Giocare con soldi veri alle slot machine prodotte da iSoftBet è al momento possibile attraverso un numero elevato di casino online autorizzati AAMS. I Simboli Speciali, come il Wild, che sostituisce qualsiasi gemma, o il Coin, offrono moltiplicatori fino a 10.000x e aggiungono una dimensione strategica. I simboli Bonus attivano il Gioco Bonus, mentre simboli come Spacecorn e Black Hole modificano la griglia, creando percorsi attraversabili o assorbendo simboli per metterli in nuove posizioni.
https://saroncortinas.com.br/book-of-dead-la-recensione-del-celebre-gioco-playn-go-per-i-giocatori-italiani/
€9.50 Consiglio Pirots X? Sì. Nonostante l’elevata volatilità possa essere un fattore impegnativo, questa slot offre un livello di intrattenimento davvero alto. Le funzioni si attivano così frequentemente che sembrano quasi parte del gioco base. È davvero un’ottima aggiunta a una serie già ben riuscita. Dimensioni: H 14 cm x 2 Mt Circa Comienza a disfrutar de los beneficios exclusivos Gli imbarchi vengono effettuati direttamente dalle spiagge di Jesolo Lido (dai pontili) e dal litorale di Cavallino – Treporti (è necessario entrare in acqua e salire a bordo con una scaletta): scarica il pdf con orari, punti di partenza, prezzi ed altre informazioni oppure contattaci direttamente. Pirots è una slot machine a tema pirati sviluppata da ELK Studios e caratterizzata da una griglia 5×5, rulli ad espansione, simboli a cascata e 4 pappagalli pirateschi tanto colorati quanto avventurosi.
Your comment is awaiting moderation.
Howdy! online pharmacy tramadol very good web page.
Your comment is awaiting moderation.
Оформление медицинских анализов https://medim-pro.ru и справок без очередей и лишней бюрократии. Запись в лицензированные клиники, сопровождение на всех этапах, помощь с документами. Экономим ваше время и сохраняем конфиденциальность.
Your comment is awaiting moderation.
Hi there, blockchain friends!
Just stumbled on a smart piece about AI in trading.
It analyzes several big trends in trading world.
Worth reading for sure.
Read more
Your comment is awaiting moderation.
Работает по: черным и цветным металламРабочая температура: 0°С до +50°СМакс https://www.ndt-club.com/product-436-ips-mg4-04-izmeritel-prochnosti-betona-sklerometr.htm
измерение: 1250 микронШаг измерений: 1 микронПодсветка экрана: НетДоп https://www.ndt-club.com/product-263-planescan-a1050-skaner-topograf-dlya-listov-i-panelei-alluminii-ygleplastikplastik.htm
функции: поворотный экранПроизводство: КитайГарантия: 1 год
Для авто предназначен для автономного функцианирования, максимальное время работы его батарей составляет около 3-х лет https://www.ndt-club.com/product-971-akkymylyator-kuw103450.htm
Его преимущество: недосягаем для сканеров преступников, т https://www.ndt-club.com/product-154-tr110-izmeritel-sherohovatosti.htm
к https://www.ndt-club.com/product-697-a1040-mira-3d-nizkochastotnii-yltrazvykovoi-tomograf.htm
большую часть времени система находится в режиме https://www.ndt-club.com/news-69.htm
Включается маяк в заданные владельцем интервалы времени для передачи координат, по средством СМС или через специальный сайт https://www.ndt-club.com/product-324-a1220-anker-nizkochastotnii-yltrazvykovoi-defektoskop.htm
После установки для его настройки достаточно прислать специальную команду, указанную в руководстве пользователя, на установленную сим-карту https://www.ndt-club.com/product-672-klever-1-lum-luminescentnaya-indikatornaya-syspenziya.htm
Работает по: черным и цветным металламРабочая температура: -25°С до +50°СМакс https://www.ndt-club.com/product-740-kabeli-soedinitelnie-preobrazovatelei-serii-da-i-tolshinomerov-krautkramer.htm
измерение: 2000 микронШаг измерений: 0,1 микронПодсветка экрана: ЕстьДоп https://www.ndt-club.com/product-721-sendast-p111-plast-pryamie-sovmeshennie-preobrazovateli-dlya-kontrolya-plastikov.htm
функции: нетПроизводство: КитайГарантия: 1 год
Поверку осуществляют аккредитованные в установленном порядке в области обеспечения единства измерений государственные региональные центры метрологии, а так же другие аккредитованные юридические лица и индивидуальные предприниматели https://www.ndt-club.com/product-565-metolab-421-stacionarnii-tverdomer-po-vikkersy.htm
Цифровой толщиномер TT 210 ультракомпактный прибор с интегрированным датчиком для проведения замеров значений толщины защитных покрытий https://www.ndt-club.com/product-382-positest-at-rychnoi-adgezimetr-defelsko.htm
Используется на магнитных, и немагнитных основах, имеет запоминающее устройство на 500 значений https://www.ndt-club.com/produkcija-292-virybnie-pressi.htm
Your comment is awaiting moderation.
Читать больше на сайте: https://medim-pro.ru/kupit-spravku-mantu/
Your comment is awaiting moderation.
Иллюзию просторного помещения создаст эффект его цвет должен быть белым или же на тон светлее, чем стены https://olga-filippova.ru/beauty-salons-spa-design
Также расширит помещение использование плоских светильников и локального освещения https://olga-filippova.ru/smi
Зачастую мы узнаем об ошибках планировки слишком поздно, так почему бы сперва не создать виртуальный план комнаты и избежать необходимости передвигать мебель с места на место, ошибаясь снова и снова в попытках создать подходящую планировку?
Во-первых, стоит рассмотреть бесплатные рассылки и платные уроки от дизайн-студий https://olga-filippova.ru/interery-medical-study-center
Например, студия Надежды Зотовой предлагает дизайн-уроки и курсы совершенно по разным тематикам https://olga-filippova.ru/interior_appartment
Хочется красиво оформить маленькую квартирку, услуги дизайнера стоят прилично и не всегда повезет встретить профессионала https://olga-filippova.ru/shop
Свежие и яркие идеи на фото помогают определиться с направлением дизайна https://olga-filippova.ru/interery-fasad
Особенно ценны для меня советы по использованию разных цветов для визуального расширения пространства https://olga-filippova.ru/smi
Нравится спальня ниша https://olga-filippova.ru/beauty-salons-spa-design
Это очень удобно и выглядит эстетично https://olga-filippova.ru/zakazat-dizajn-proekt-stoimost
Беру на заметку https://olga-filippova.ru/uslugi_seny
Your comment is awaiting moderation.
Хочешь айфон? apple iphone выгодное предложение на новый iPhone в Санкт-Петербурге. Интернет-магазин i4you готов предложить вам решение, которое удовлетворит самые взыскательные требования. В нашем каталоге представлена обширная коллекция оригинальных устройств Apple. Каждый смартфон сопровождается официальной гарантией производителя сроком от года и более, что подтверждает его подлинность и надёжность.
Your comment is awaiting moderation.
Canadian players have no shortage of options when it comes to accessing Gates of Olympus—the game is widely available at most reputable online casinos that host Pragmatic Play titles. But availability alone isn’t enough. If you want to play with peace of mind, you need a site that’s licensed, secure, and tailored to Canadian users. Gates of Olympus Super Scatter se déroule sur une grille avec 6 rouleaux et 5 lignes. Il offre un RTP de 96,50% et combine une forte volatilité avec un système Scatter Pays, où les joueurs doivent obtenir au moins 8 symboles identiques n’importe où sur la grille pour gagner. Gates of Olympus est devenu très populaire grâce à son système de paiement partout, où les gains sont obtenus en faisant correspondre 8 symboles ou plus à n’importe quel endroit de la grille. Associé à des rouleaux en cascade et à des multiplicateurs, il offre un gameplay dynamique et gratifiant qui séduit un large public.
https://king169login.com/revue-complete-du-jeu-de-casino-1win-pour-les-joueurs-francais/
Après avoir choisi un casino en ligne, l’utilisateur doit suivre les étapes suivantes pour commencer à jouer à Gates of Olympus: La machine à sous Gates of Olympus™ est parfaitement accessible depuis un mobile ou une tablette. Il ne vous sera pas nécessaire de télécharger de logiciel spécifique en amont de vos sessions de jeux mobiles. En effet, le jeu étant doté de la technologie HTML5, vous n’aurez qu’à suivre ces quelques étapes : Gates of Olympus Dice affiche un taux de retour au joueur (RTP) de 96,5%, un chiffre supérieur à la moyenne du marché, tout comme la version slot originale. Cette donnée est rassurante pour les joueurs cherchant des sessions de jeu équilibrées sur le long terme. Download the Gates of Olympus 1000 app now and let the games begin!
Your comment is awaiting moderation.
Das beliebteste Slot-Game Deutschlands, und das zu Recht! Der RTP (Return to Player) liegt bei sehr guten 96,5 %. Dies ist ein Wert, der sich durchaus im oberen Drittel unter den RTPs der von uns getesteten Slots findet. Der Return to Player sagt aus, wie viel Prozent der Einsätze aller Spieler als Gewinne wieder ausgeschüttet werden. Beim Gates of Olympus Slot liegt dieser prozentuale Wert bei 96,5 %. Gates of Olympus ist der Slot durch Pragmatic Play, inside diesem parece um antike Götterwelten geht. Inside diesem Automatenspiel kannst du qua ein wenig Dusel achse Gewinne abjagen. Nachfolgende Auszahlungsquote sei hoch und wie Haupttreffer lockt das 5000-fache Einsatz. Die autoren fangen dir Gates of Olympus inside folgendem Bericht reichhaltig vorweg ferner darlegen dir alle Vertiefen & Schwächen.
https://www.docarnettefoundation.org/book-of-dead-ein-spannendes-abenteuer-fur-osterreichische-spieler/
Step into the mythological realm of Gates of Olympus, where Zeus himself can bless you with huge multipliers and free spins. This high-volatility slot features 6 reels and a unique Cluster Pays system. Furthermore, the game stands out for its tumbling reels and the chance to trigger multipliers up to 500x. With an RTP of 96.50%, it’s packed with potential for generous rewards, up to 5,000x your playing amount. Plus, by using a PlayFame promo code, you can get extra rewards to maximize your gameplay and enjoy this exciting PlayFame slots game with a head start. Attention, * Please note that the Return to Player (RTP) rate for this slot game may differ from one jurisdiction to another. Gates of Olympus offers an Ante Bet option, which doubles your chances of triggering the bonus feature. However, to activate this option, you’ll need to pay an additional 25% of your bet amount. Alternatively, for a direct route to triggering the free spins bonus game, players can opt for the Buy Bonus feature. Although it charges a substantial cost of 100 times the stake, the feature ensures 15 free games. The payout value is determined by the number of scatter symbols (4, 5, or 6) obtained in the triggering spin. It’s important to note that the Buy Bonus feature may not be accessible in certain jurisdictions.
Your comment is awaiting moderation.
Пошагово — этапы строительства загородного дома https://mospromstroy.ru/product-category/oborudovanie-dlya-detskih-ploshhadok/page/5/
После приемки дома, владелец может сразу же завозить мебель и утварь https://mospromstroy.ru/product/trenazher-ellipticheskij-aviator-611-08-2/
Жилье полностью готово к эксплуатации https://mospromstroy.ru/product/imitacziya-brusa-iz-listvenniczy-20h190h4000-sort-ekstra/
Инженерные работы https://mospromstroy.ru/product/urna-dlya-detskoj-ploshhadki-s-vkladyshemaviator-150-40/
Дома из керамоблоков https://mospromstroy.ru/product/gorka-czvetok-aviator-41-01-01-isp-1/
В 95% случаев предлагаем заказчику цену строительства дома под ключ ниже, чем другие строители, работающие в Москве и МО https://mospromstroy.ru/product/evrovagonka-iz-sosny-12-5h96h4000-sort-av/
«Загородный дом вашей мечты: строим с учётом ваших пожеланий»
Your comment is awaiting moderation.
Ihr möchtet anonym und ohne lästige Dokumentenprüfung spielen? Casinos ohne Verifizierung ermöglichen genau das – schnelle Gewinne, unkomplizierte Auszahlungen und maximale Privatsphäre für euer Spielerlebnis! Allzu groß unterscheiden sich die derzeit beliebten Casinos ohne Verifizierung allerdings nicht von den Pay‘n Play Casinos. Schließlich handelt es sich auch hier um Online Casinos ohne Handynummer, bei denen die Registrierung schnell und nur durch Angabe einer E-Mail-Adresse erledigt ist. In den meisten Online Casinos erfolgt auch die Auszahlung ohne Ausweis. Nicht nur beste Krypto Casinos haben ihre Stärken und Schwächen, auch im Casino ohne Verifizierung gibt es bestimmte Vor- und Nachteile. Nach unseren ausgiebigen Online Casino ohne Verifizierung Tests können wir Ihnen eine Liste mit den Vor- und Nachteilen präsentieren, die Ihnen bei Ihrer Entscheidung helfen können.
https://tkardinpisau.co.id/book-of-dead-review-ein-spannendes-abenteuer-fur-spieler-aus-osterreich/
Gates of olympus – the best choice for your entertainment. Be watchful for the code so you can claim the bonuses, many casinos offer bonuses for players who use wire transfers to fund their accounts. This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data. You can find many Asian inspired casino tables too, the online casino offers a wide range of some of the most popular payment solutions. Does the gates of olympus casino game have a free spins feature i would have to set these places as the new higher standard today, payment method. They are a trusted brand with significant experience and time in the industry, bonuses and promotions.
Your comment is awaiting moderation.
Контактная информация https://norsy.ru/pochemu-my
Пошив одежды оптом ПО ИНДИВИДУАЛЬНОМУ ДИЗАЙНУ https://norsy.ru/voprosy-otvety
брендирование и ПЕЧАТЬ принтов https://norsy.ru/ceny
Мы используем cookies для быстрой и удобной работы сайта https://norsy.ru/voprosy-otvety
Продолжая пользоваться сайтом, вы принимаете условия обработки персональных данных https://norsy.ru/poshiv-hudi
Пошив одежды оптом в Москве https://norsy.ru/voprosy-otvety
Для настрачивания лампас на любые изделия, для закрытия плечевого шва и горловины спинки одним приемом https://norsy.ru/kontakty
Your comment is awaiting moderation.
Photos of Pokfulam Fire Dragon Dance in 2018, showing the dragon and dancers (Source: Mr. Lau Wing Hong, with permission) Yan, M.M.Y. 2017. Sustaining a “village Community” in Urban Hong Kong: The Study of Fire Dragon Dance in Pokfulam Village. Mater’s thesis, Hong Kong University of Science and Technology. Besides the importance of dragon fruit as a source of bioactive compounds, the bioavailability is low. The development of delivery systems such as gold nanoparticles with these compounds can be an alternative to reach target tissues. Zhu, Y., and J. Liu. 2021. Cultural Reproduction: Ethnic Festivals as Intangible Cultural Heritage in China. Loisir Et Société 44 (3): 415–428. theguardian australia-news 2015 nov 23 hillsongs-brian-houston-failed-to-report-abuse-and-had-conflict-of-interest-royal-commission
https://www.istam.fr/book-of-dead-slot-review-playn-gos-thrilling-adventure-in-uk-casinos/
In this comprehensive guide, we’ll delve into the intricacies of Litecoin betting and the growing number of LTC betting sites. Whether you’re a seasoned bettor or new to cryptocurrency gambling, this article aims to equip you with the knowledge you need. We’ll cover everything from the basics of how Litecoin betting works to expert tips on selecting the most reliable platforms. BC Game offers phenomenal Litecoin online sports betting. The sportsbook provides pre-game and live wagering on 46 sports, from sumo wrestling and rugby to NFL football and top basketball games. Betting on esports and horse racing is available, and bettors can access hundreds of betting markets on a single event. Initially, only a few platforms supported LTC transactions. Over time, as cryptocurrency gained popularity, more betting sites started incorporating Litecoin. Today, many online casinos provide extensive support for LTC, offering bonuses and promotions to attract users. The evolution of blockchain technology has further solidified Litecoin’s position in the online gambling world. Some casinos now exclusively operate with cryptocurrencies, including LTC, to cater to tech-savvy gamblers.
Your comment is awaiting moderation.
Another remarkable aspect of 15 Dragon Pearls is the Dragon Pearl Bonus , activated when three or more dragon symbols appear on adjacent reels. This bonus round allows players to choose from a selection of dragon pearls, each hiding a unique multiplier and prize. Online Casino Without Registration: A New Era of Gaming, you will receive a generous welcome bonus that can be used to play blackjack and other games. A random number generator (RNG) is a mathematical algorithm that generates a string of numbers without any pattern or discernment, which is why they are ready to answer any inquiries with utmost care and attention. The promotion could have neat graphics and a well-presented idea that helps articulate the imagination behind it, with multiple paylines and bonus features that can help you win big.
https://bon77.org/unlocking-leaderboard-rewards-in-mines-casino-game-a-canadian-perspective/
With its single and group healing abilities and other buff abilities, it protects many warriors nearby and increases their chances of survival. Those who have debilitating abilities are indispensable in breaking the opponent’s defenses. Crown Wood International Film Festival The Wildlife Trafficking Alliance (WTA) is a coalition of more than 100 AZA-accredited zoos and aquariums, companies, and non-profit organizations working together to reduce, and eventually eliminate, the illegal trade of wildlife and wildlife products. With its single and group healing abilities and other buff abilities, it protects many warriors nearby and increases their chances of survival. Those who have debilitating abilities are indispensable in breaking the opponent’s defenses. This includes 15 Dragon Pearls among thousands of others. We found that the mobile browser version of the game functions beautifully due to its HTML5 technology, with the small-screen version including large enough buttons to optimise the spin mechanics and your bets. Gameplay is accessible, reliable, and stable through both iOS and Android platforms.
Your comment is awaiting moderation.
Strona internetowa mostbet – zaklady sportowe, zaklady e-sportowe i sloty na jednym koncie. Wygodna aplikacja mobilna, promocje i cashback dla aktywnych graczy oraz roznorodne metody wplat i wyplat.
Your comment is awaiting moderation.
Официальный Tor браузер обеспечивает кракен tor доступ через предустановленные настройки безопасности с отключенным JavaScript и строгой изоляцией каждой вкладки от других процессов.
Your comment is awaiting moderation.
Читать дальше: достопримечательности казахстана
Your comment is awaiting moderation.
Специальный протокол создает кракен onion адреса через криптографическое хеширование публичных ключей серверов что математически связывает адрес с инфраструктурой без возможности подделки.
Your comment is awaiting moderation.
беларусь события новости последние новости беларуси
Your comment is awaiting moderation.
Фуршет дома по случаю дня рожденья https://shcherbinins.ru/aboutus
Наш опытный персонал гарантирует высокое качество блюд и обслуживания https://shcherbinins.ru/
Мы следим за каждой деталью, чтобы ваше мероприятие прошло идеально https://shcherbinins.ru/menu
Наши услуги включают:
Мы предоставим все, что необходимо для организации вашего торжества — мебель, посуду, столовые приборы, бокалы, текстиль, дополнительное оборудование https://shcherbinins.ru/menu
Продумаем логистику, чтобы точно к началу мероприятия были сервированы столы со свежей, только что приготовленной едой https://shcherbinins.ru/contacts
Приведем площадку в порядок после мероприятия, демонтируем и вывезем конструкции, уберем мусор https://shcherbinins.ru/aboutus
CaterMe предлагает ряд преимуществ, делающих процесс выбора и заказа кейтеринга легким и удобным:
Спасибо, всё прошло хорошо – персонал работал чётко и слаженно https://shcherbinins.ru/contacts
По качеству еды претензий нет), всё огонь) отдельный респект за синие галстуки на чёрной форме – в соответствии с цветовой гаммой мероприятия https://shcherbinins.ru/
Выглядело – топ! ????
Корпоративные мероприятия Частные мероприятия https://shcherbinins.ru/uslugy
Your comment is awaiting moderation.
Профессиональная косметика Москва https://sinapple.ru/collection/germaine-de-capuccini/product/germaine-de-capuccini-hydracure-rich-cream-very-dry-skin
При помощи профессиональной косметики и средств можно делать укладки и стрижки любой сложности, выполнять все виды декоративного макияжа, ухаживать за ногтями, телом, кожей лица и рук https://sinapple.ru/collection/phytomer/product/phytomer-hydracontinue-12h-moisturizing-flash-gel
«В человеке всё должно быть прекрасно», – сказал классик https://sinapple.ru/collection/declare/product/declare-age-control-multi-lift-re-modeling-contour-cream Профессиональная косметика PREMIUM предназначена для того, чтобы сделать прекрасными ваше лицо и тело, дать коже всё, что ей необходимо https://sinapple.ru/collection/cantabria-labs-ispaniya/product/cantabria-labs-heliocare-360-md-a-r-emulsion-spa-50
Your comment is awaiting moderation.
Видеонаблюдение IP-видеонаблюдение Радиосигнализация GSM сигнализация Доводчики Охранная сигнализация Пожарная сигнализация Видеодомофоны Контроль доступа Системы оповещения Замки Оповещатели https://secbuy.ru/about/howto/
Есть в наличии (1)
The product is already in the wishlist! В отложенных https://secbuy.ru/catalog/domofony-i-peregovornye-ustroystva/
Есть в наличии (59)
Адресные системы 778 Беспроводные системы 1018 Домашняя автоматика 21 Интегрированные системы 256 Неадресные системы 866 https://secbuy.ru/
Коммутаторы POE (26)
Your comment is awaiting moderation.
Доставка грузов https://avalon-transit.ru из Китая «под ключ» для бизнеса и интернет-магазинов. Авто-, ж/д-, морские и авиа-перевозки, консолидация на складах, проверка товара, страхование, растаможка и доставка до двери. Работаем с любыми партиями — от небольших отправок до контейнеров. Прозрачная стоимость, фотоотчёты, помощь в документах и сопровождение на всех этапах логистики из Китая.
Your comment is awaiting moderation.
Геосинтетические материалы https://stsgeo.ru для строительства купить можно у нас с профессиональным подбором и поддержкой. Продукция для укрепления оснований, армирования дорожных одежд, защиты гидроизоляции и дренажа. Предлагаем геотекстиль разных плотностей, георешётки, геомембраны, композитные материалы.
Your comment is awaiting moderation.
Строительство домов https://никстрой.рф под ключ — от фундамента до чистовой отделки. Проектирование, согласования, подбор материалов, возведение коробки, кровля, инженерные коммуникации и внутренний ремонт. Работаем по договору, фиксируем смету, соблюдаем сроки и технологии. Поможем реализовать дом вашей мечты без стресса и переделок, с гарантией качества на все основные виды работ.
Your comment is awaiting moderation.
Доставка торфа https://bio-grunt.ru и грунта по Москве и Московской области для дач, участков и ландшафтных работ. Плодородный грунт, торф для улучшения структуры почвы, готовые земляные смеси для газона и клумб. Быстрая подача машин, аккуратная выгрузка, помощь в расчёте объёма. Работаем с частными лицами и организациями, предоставляем документы. Сделайте почву на участке плодородной и готовой к посадкам.
Your comment is awaiting moderation.
Доставка дизельного топлива https://ng-logistic.ru для строительных компаний, сельхозпредприятий, автопарков и промышленных объектов. Подберём удобный график поставок, рассчитаем объём и поможем оптимизировать затраты на топливо. Только проверенные поставщики, стабильное качество и точность дозировки. Заявка, согласование цены, подача машины — всё максимально просто и прозрачно.
Your comment is awaiting moderation.
Hey there, everyone! The name’s Admin Read:
Всё, что нужно для удобного и выгодного шопинга, есть на платформе kraken как зайти. Здесь вы найдёте товары на любой вкус, от техники до эксклюзивных предметов. Простой интерфейс и выгодные акции помогают существенно сэкономить. Kraken гарантирует защиту сделок, что укрепляет доверие покупателей. Именно ссылка kraken at остаётся любимым выбором для покупок.
Your comment is awaiting moderation.
Всё о камерах видеонаблюдения — полное руководство!
Приветствуем вас, уважаемые форумчане! Сегодня мы подробно поговорим обо всём, что касается видеокамер наблюдения. Мы поможем вам разобраться в огромном разнообразии предложений рынка и сделать правильный выбор оборудования для защиты вашего имущества и безопасности вашей семьи.
Почему важно установить систему видеонаблюдения?
Камеры видеонаблюдения становятся всё популярнее среди владельцев домов, офисов и коммерческих помещений. Они обеспечивают защиту имущества, предотвращают преступления и помогают контролировать происходящее даже дистанционно. Давайте рассмотрим самые важные аспекты выбора камеры и её установки.
Какие бывают виды камер видеонаблюдения?
Вы можете выбрать камеру исходя из ваших потребностей и условий эксплуатации:
– **Уличные** — предназначены для наружной установки, защищены от влаги и пыли.
– **Домашние** — компактные модели для внутренней установки.
– **IP-камеры** — позволяют подключаться к сети Интернет и просматривать записи онлайн.
– **Wi-Fi камеры** — удобны благодаря беспроводному соединению.
– **Камеры с SIM-картой** — работают независимо от интернета, передавая сигнал через мобильную сеть.
– **Миниатюрные камеры** — незаметны и подходят для скрытого наблюдения.
– **Поворотные камеры** — способны охватывать большие площади, поворачиваясь на 360 градусов.
– **Ночные камеры** — оснащены инфракрасной подсветкой для съёмки в темноте.
—
Как правильно выбрать камеру видеонаблюдения?
Перед покупкой обратите внимание на следующие характеристики:
– Разрешение камеры — HD/FullHD/UHD обеспечит чёткое изображение.
– Угол обзора — широкий угол позволяет видеть больше пространства.
– Наличие микрофона и динамика — возможность двусторонней связи.
– Датчик движения — экономия памяти устройства путём включения записи только при обнаружении активности.
– Питание — проверьте совместимость с вашим источником питания.
– Возможность удалённого доступа — управление камерой через смартфон или компьютер.
—
Установка и подключение камеры видеонаблюдения
Правильная установка и настройка камеры позволят вам эффективно пользоваться всеми возможностями системы видеонаблюдения. Рассмотрим ключевые моменты:
– Выберите оптимальное место для размещения камеры, обеспечивающее максимальный обзор охраняемой территории.
– Убедитесь, что камера защищена от погодных воздействий, если устанавливается снаружи здания.
– Настройте Wi-Fi соединение или кабельную линию подключения.
– Установите приложение для просмотра записей и управления камерой через мобильное устройство.
—
Где лучше всего приобрести камеру видеонаблюдения?
При покупке обращайте внимание на проверенные магазины и бренды. Рекомендуем выбирать оборудование известных производителей, предлагающих гарантии качества и поддержку клиентов. Обратите внимание на предложения крупных торговых площадок, таких как Ozon, Wildberries и специализированные магазины электроники.
—
Советы по установке камер видеонаблюдения:
– Изучите правила установки камер видеонаблюдения перед началом монтажа.
– Получите согласие жильцов многоквартирных домов на установку камер в подъездах и местах общего пользования.
– Позаботьтесь о защите личной жизни соседей, устанавливая камеры таким образом, чтобы избежать нарушения частной собственности.
—
Поделитесь своим опытом!
Расскажите нам о вашем опыте покупки и установки камер видеонаблюдения. Может быть, у вас есть советы или рекомендации для новичков? А может, вы столкнулись с проблемами при выборе или настройке оборудования? Оставляйте комментарии ниже, давайте делиться полезными советами вместе!
Автор:
Система видеонаблюдения
*Данная статья носит информационный характер и предназначена исключительно для ознакомительных целей.*
Your comment is awaiting moderation.
Hey, everyone! Allow me to introduce myself as Admin Read:
Kraken продолжает лидировать в онлайн-шопинге благодаря своему разнообразному ассортименту товаров и непревзойденному удобству. От повседневных товаров до предметов роскоши, обширный каталог что такое кракен сайт гарантирует, что вы найдете именно то, что ищете. Отзывы клиентов, защищённые платежи и молниеносная доставка делают шопинг с зайти на kraken лёгким и безопасным. Поднимите свои покупки на новый уровень, исследуя 2krn сегодня для эксклюзивных предложений и акций.
Your comment is awaiting moderation.
Инженерные изыскания https://sever-geo.ru в Москве и Московской области для строительства жилых домов, коттеджей, коммерческих и промышленных объектов. Геология, геодезия, экология, обследование грунтов и оснований. Работаем по СП и ГОСТ, есть СРО и вся необходимая документация. Подготовим технический отчёт для проектирования и согласований. Выезд на объект в короткие сроки, прозрачная смета, сопровождение до сдачи проекта.
Your comment is awaiting moderation.
Колодцы под ключ https://kopkol.ru в Московской области — бурение, монтаж и обустройство водоснабжения с гарантией. Изготавливаем шахтные и бетонные колодцы любой глубины, под ключ — от проекта до сдачи воды. Работаем с кольцами ЖБИ, устанавливаем крышки, оголовки и насосное оборудование. Чистая вода на вашем участке без переплат и задержек.
Your comment is awaiting moderation.
Howdy! propecia rx net excellent web site.
Your comment is awaiting moderation.
Скидка 100% на первый месяц!
Optimum https://proffseo.ru/kontakty
Еще истории успеха https://proffseo.ru/privacy
Геонезависимый запрос — запрос, выдача по которому никак не зависит от местоположения пользователя внутри страны https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Чаще всего, это информационные запросы, или запросы с упоминанием конкретного города https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
сотрудников https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Продвижение в ТОП-10 по России https://proffseo.ru/kontakty
Your comment is awaiting moderation.
Цена первого месяца раскрутки сайта 0 рублей! Оставьте заявку, и мы подготовим уникальное коммерческое предложение на основе аудита вашего проекта https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Цена: 24 700 ?
Это интересно!
Александр Дронов https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
– 60 видов работ – Гарантия выполненных работ – Гарантия результата – Гарантия возврата денег https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Продвижение в ТОП-10 регионального сайта (кроме МСК, СПб)
Your comment is awaiting moderation.
Погрузитесь в мир азартных игр и испытайте удачу в майн дроп слот, где каждый спин может стать выигрышным!
Таким образом, правильный подход к игре позволит увеличить шансы на удачу.
Your comment is awaiting moderation.
Yo crypto fam!
Found a fresh post about market analysis.
It goes over market shifts in BTC, ETH, and other coins.
I think you’ll like it, especially if you trade.
Take a look
Your comment is awaiting moderation.
Надёжные перевозчики грузов обеспечивают быстрые и безопасные грузовые перевозки по всему городу. Наша транспортная компания организует профессиональные грузоперевозки и аккуратную доставку по Киеву. Предлагаем также услуги грузчиков Киев — опытные грузчики Киев аккуратно выполнят любую работу. https://babelcube.com/user/transportal-pro
Ищете ответственных специалистов для доставки грузов? Наши грузоперевозчики выполняют услуги грузоперевозок быстро, недорого и с гарантией сохранности. Вся доставка по Киеву — с удобной логистикой и профессиональными грузчиками Киев. https://clearvoice.com/cv/transportalpro
Наша транспортная компания предлагает комплексные решения: от аккуратной погрузки до оперативной доставки грузов. Если вам нужны надёжные перевозчики грузов и проверенные грузчики Киев, мы обеспечим лучший сервис. Грузовые перевозки любого масштаба — быстро и выгодно. https://www.walkscore.com/people/295757639389/transportalpro
Профессиональные грузоперевозки в Киеве без задержек и рисков. Наши перевозчики грузов знают город и гарантируют быструю доставку по Киеву в любое время. К вашим услугам опытные грузчики Киев, готовые выполнить работу аккуратно и оперативно. https://www.speedrun.com/users/transportalpro
Нужна надёжная доставка грузов? Выбирайте нас — грузоперевозчики, которые работают честно и точно по графику. Транспортная компания предоставляет полный комплекс: грузовые перевозки, логистика и услуги грузчиков Киев. https://inkbunny.net/transportalpro
Your comment is awaiting moderation.
Оперативные и недорогие грузоперевозки в Киеве — это мы. Наши перевозчики грузов доставят всё, от бытовой техники до офисного оборудования. В наличии квалифицированные грузчики Киев и любые услуги грузоперевозок. https://www.renderosity.com/users/id:1799346
Если важно качество и скорость, выбирайте нашу транспортную компанию. Надёжные грузоперевозчики обеспечивают точную и безопасную доставку грузов. Профессиональные услуги грузчиков Киев помогут при переездах, ремонтах и коммерческих перевозках. https://gravatar.com/transportalpro
Мы выполняем грузовые перевозки по Киеву и области на выгодных условиях. Наши перевозчики грузов всегда готовы помочь, а грузчики Киев обеспечат аккуратную погрузку и выгрузку. Лучший выбор для тех, кому нужна быстрая доставка по Киеву. https://linqto.me/about/transportalpro
Ищете профессиональные услуги грузоперевозок? Мы — команда опытных специалистов, для которых доставка грузов — работа, выполняемая с полной ответственностью. Грузчики Киев и современные автомобили обеспечат удобный формат сотрудничества. https://bio.site/transportalpro
Наша транспортная компания — это надёжные грузоперевозчики, которые ценят ваше время. Выполняем любые грузовые перевозки с гарантией точной и быстрой доставки по Киеву. Предлагаем также услуги грузчиков Киев для любых задач. https://www.tumblr.com/transportalpro
Your comment is awaiting moderation.
6.
Boost your account quickly with our top-rated World of Tanks boosting services. Whether you need WoT boosting service, full World of Tanks powerleveling, or targeted WoT account boosting, we’ve got you covered. Our specialists also provide Maneuvers boost for fast team results, World of Tanks carry service, and efficient Personal Missions Boosting to help you unlock tanks, emblems, and achievements without stress. https://www.pozible.com/profile/boosthub-com
7.
If grinding isn’t for you, our website offers the best World of Tanks boosting solutions. Try our fast WoT boosting service, expert World of Tanks powerleveling, and flexible WoT account boosting options. Looking for mode-specific help? We provide Maneuvers boost, trusted World of Tanks carry service, and accurate Personal Missions Boosting for any difficulty or mission chain. https://www.callupcontact.com/b/businessprofile/boosthub/9871999
8.
Make your WoT experience easier with our complete set of boosting services. We specialize in World of Tanks boosting, giving players access to high-quality WoT boosting service and advanced World of Tanks powerleveling strategies. Need a boost to your rank or stats? Our WoT account boosting is fast and secure. We also offer Maneuvers boost, dedicated World of Tanks carry service, and full Personal Missions Boosting. https://yoomark.com/content/security-and-confidentiality-are-essential-when-using-any-form-world-tanks-boosting-which
9.
Progress faster in World of Tanks with our trusted services. Our site provides safe World of Tanks boosting, professional WoT boosting service, and efficient World of Tanks powerleveling for all account levels. For full account growth, choose WoT account boosting. We also offer Maneuvers boost, elite World of Tanks carry service, and guaranteed Personal Missions Boosting completed by top players. https://routinehub.co/user/boosthubcom
10.
Unlock new tiers and rewards quicker with our all-in-one WoT assistance platform. We provide World of Tanks boosting, customizable WoT boosting service, and fast World of Tanks powerleveling options. Want instant improvements? Our WoT account boosting ensures stable progress. You can also request Maneuvers boost, join a World of Tanks carry service, or complete hard tasks with our Personal Missions Boosting. https://www.codementor.io/@boosthubcom
Your comment is awaiting moderation.
Надёжные перевозчики грузов обеспечивают быстрые и безопасные грузовые перевозки по всему городу. Наша транспортная компания организует профессиональные грузоперевозки и аккуратную доставку по Киеву. Предлагаем также услуги грузчиков Киев — опытные грузчики Киев аккуратно выполнят любую работу. https://solo.to/transportalpro
Ищете ответственных специалистов для доставки грузов? Наши грузоперевозчики выполняют услуги грузоперевозок быстро, недорого и с гарантией сохранности. Вся доставка по Киеву — с удобной логистикой и профессиональными грузчиками Киев. https://maxforlive.com/profile/user/transportalpro?tab=about
Наша транспортная компания предлагает комплексные решения: от аккуратной погрузки до оперативной доставки грузов. Если вам нужны надёжные перевозчики грузов и проверенные грузчики Киев, мы обеспечим лучший сервис. Грузовые перевозки любого масштаба — быстро и выгодно. https://myanimelist.net/profile/transportalpro
Профессиональные грузоперевозки в Киеве без задержек и рисков. Наши перевозчики грузов знают город и гарантируют быструю доставку по Киеву в любое время. К вашим услугам опытные грузчики Киев, готовые выполнить работу аккуратно и оперативно. https://boosty.to/transportalpro
Нужна надёжная доставка грузов? Выбирайте нас — грузоперевозчики, которые работают честно и точно по графику. Транспортная компания предоставляет полный комплекс: грузовые перевозки, логистика и услуги грузчиков Киев. https://vc.ru/id5516406
Your comment is awaiting moderation.
Оперативные и недорогие грузоперевозки в Киеве — это мы. Наши перевозчики грузов доставят всё, от бытовой техники до офисного оборудования. В наличии квалифицированные грузчики Киев и любые услуги грузоперевозок. https://www.tumblr.com/transportalpro
Если важно качество и скорость, выбирайте нашу транспортную компанию. Надёжные грузоперевозчики обеспечивают точную и безопасную доставку грузов. Профессиональные услуги грузчиков Киев помогут при переездах, ремонтах и коммерческих перевозках. https://www.walkscore.com/people/295757639389/transportalpro
Мы выполняем грузовые перевозки по Киеву и области на выгодных условиях. Наши перевозчики грузов всегда готовы помочь, а грузчики Киев обеспечат аккуратную погрузку и выгрузку. Лучший выбор для тех, кому нужна быстрая доставка по Киеву. https://files.fm/transportalpro25/info
Ищете профессиональные услуги грузоперевозок? Мы — команда опытных специалистов, для которых доставка грузов — работа, выполняемая с полной ответственностью. Грузчики Киев и современные автомобили обеспечат удобный формат сотрудничества. https://disqus.com/by/transportalpro/about/
Наша транспортная компания — это надёжные грузоперевозчики, которые ценят ваше время. Выполняем любые грузовые перевозки с гарантией точной и быстрой доставки по Киеву. Предлагаем также услуги грузчиков Киев для любых задач. https://solo.to/transportalpro
Your comment is awaiting moderation.
6.
Boost your account quickly with our top-rated World of Tanks boosting services. Whether you need WoT boosting service, full World of Tanks powerleveling, or targeted WoT account boosting, we’ve got you covered. Our specialists also provide Maneuvers boost for fast team results, World of Tanks carry service, and efficient Personal Missions Boosting to help you unlock tanks, emblems, and achievements without stress. https://kemono.im/boosthubcom/world-of-tanks-is-a-complex-game-where-performance-is-heavily-influenced-by
7.
If grinding isn’t for you, our website offers the best World of Tanks boosting solutions. Try our fast WoT boosting service, expert World of Tanks powerleveling, and flexible WoT account boosting options. Looking for mode-specific help? We provide Maneuvers boost, trusted World of Tanks carry service, and accurate Personal Missions Boosting for any difficulty or mission chain. https://gitee.com/boosthubcom
8.
Make your WoT experience easier with our complete set of boosting services. We specialize in World of Tanks boosting, giving players access to high-quality WoT boosting service and advanced World of Tanks powerleveling strategies. Need a boost to your rank or stats? Our WoT account boosting is fast and secure. We also offer Maneuvers boost, dedicated World of Tanks carry service, and full Personal Missions Boosting. https://www.apsense.com/user/boosthubcom
9.
Progress faster in World of Tanks with our trusted services. Our site provides safe World of Tanks boosting, professional WoT boosting service, and efficient World of Tanks powerleveling for all account levels. For full account growth, choose WoT account boosting. We also offer Maneuvers boost, elite World of Tanks carry service, and guaranteed Personal Missions Boosting completed by top players. https://belgaumonline.com/profile/boosthubcom/
10.
Unlock new tiers and rewards quicker with our all-in-one WoT assistance platform. We provide World of Tanks boosting, customizable WoT boosting service, and fast World of Tanks powerleveling options. Want instant improvements? Our WoT account boosting ensures stable progress. You can also request Maneuvers boost, join a World of Tanks carry service, or complete hard tasks with our Personal Missions Boosting. https://www.zazzle.com/mbr/238291662600851413
Your comment is awaiting moderation.
777bet apk.
One of the main attractions of 777bet is its extensive selection of games.
Your comment is awaiting moderation.
Погрузитесь в захватывающий мир игра авиатор 1вин и испытайте удачу на каждой ставке!
В Aviator казино проводятся различные акции, которые привлекают игроков и повышают интерес.
Your comment is awaiting moderation.
Откройте для себя невероятные возможности в aviator 1win и погрузитесь в захватывающий мир азартных игр!
Опытные пользователи часто применяют различные стратегии, чтобы не допустить больших финансовых потерь.
Your comment is awaiting moderation.
Попробуйте свою удачу в aviator 1win игра и насладитесь уникальными возможностями!
Каждый пользователь может рассчитывать на захватывающие моменты и шанс выиграть крупные денежные призы.
Your comment is awaiting moderation.
777bet online casino.
With a wide array of games and betting options, it caters to diverse preferences.
Your comment is awaiting moderation.
like it jaxx
Your comment is awaiting moderation.
https://zooaquarium.ru/ fish
https://softisntall.ru/ – soft
https://airvission.ru – avto car
Your comment is awaiting moderation.
Приветствую, искатели рождественского чуда! В преддверии самых сказочных дней в году, когда сердце замирает в ожидании волшебства, я хочу поделиться с вами секретом идеальной новогодней ели. И имя ей – величественная пихта Нордмана!
Забудьте о мимолетной красоте и осыпающихся иголках! Нордманская пихта – это долговечность и элегантность в одном флаконе. Представьте себе: стройная красавица с густой, насыщенной зеленью, которая гордо возвышается в вашей гостиной, озаряя все вокруг своим благородством. Ее мягкие, неколючие иголки так приятно трогать, а ветви идеально расположены для украшения любыми игрушками. Подскажите где датская елка пихта нордмана
Your comment is awaiting moderation.
Погрузитесь в мир увлекательных ставок с 1win самолетик, где каждый спин может стать вашим шагом к успеху!
нестандартному подходу к азартным играм.
Your comment is awaiting moderation.
oficjalne pobieranie mostbet mostbet global
Your comment is awaiting moderation.
oficjalny mostbet mostbet
Your comment is awaiting moderation.
ігри казіно ігри в казино
Your comment is awaiting moderation.
ігрові слоти ігри слоти
Your comment is awaiting moderation.
ігри в казино ігри казіно
Your comment is awaiting moderation.
слоти безкоштовно слоти ігрові автомати
Your comment is awaiting moderation.
Погружайтесь в захватывающий мир авиатор казино и испытайте удачу в игре на деньги!
Также регулярные турниры и акции делают атмосферу игры более насыщенной и увлекательной.
Your comment is awaiting moderation.
Seduction queen wants to strip and post her nudes. Here — rb.gy/8rrwju?stype
Your comment is awaiting moderation.
казино з бонусами казіно з бонусами
Your comment is awaiting moderation.
бонуси казіно бонуси казино
Your comment is awaiting moderation.
креатин 1win 1win официальный скачать
Your comment is awaiting moderation.
Хочешь развлечься? купить альфа пвп федерация – это проводник в мир покупки запрещенных товаров, можно купить гашиш, купить мефедрон, купить кокаин, купить меф, купить экстази, купить альфа пвп, купить гаш в различных городах. Москва, Санкт-Петербург, Краснодар, Владивосток, Красноярск, Норильск, Екатеринбург, Мск, СПБ, Хабаровск, Новосибирск, Казань и еще 100+ городов.
Your comment is awaiting moderation.
1win протеин 1win скачать на андроид бесплатно
Your comment is awaiting moderation.
Хочешь развлечься? купить альфа пвп федерация – это проводник в мир покупки запрещенных товаров, можно купить гашиш, купить мефедрон, купить кокаин, купить меф, купить экстази, купить альфа пвп, купить гаш в различных городах. Москва, Санкт-Петербург, Краснодар, Владивосток, Красноярск, Норильск, Екатеринбург, Мск, СПБ, Хабаровск, Новосибирск, Казань и еще 100+ городов.
Your comment is awaiting moderation.
Погрузитесь в захватывающий мир авиатор игра и испытайте удачу уже сегодня!
В этом казино представлены разнообразные игры на любой вкус.
Your comment is awaiting moderation.
https://t.me/s/officials_pokerdom/780
Your comment is awaiting moderation.
Откройте для себя захватывающий мир авиатор игры, где каждый раунд может стать шансом на крупный выигрыш!
Важно учитывать, что, как и в других азартных играх, в aviator присутствует элемент удачи.
Your comment is awaiting moderation.
– 50 видов работ – Гарантия выполненных работ https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Подведем итоги https://proffseo.ru/prodvizhenie-zarubezhnykh-sajtov
Поисковые запросы — фразы, по которым пользователи ищут нужную им информацию, можно разделить на две большие группы: геозависимые и геонезависимые https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
К последним относятся запросы, содержащие общую информацию без привязки к конкретному региону, например, фильмы, книги, образовательные ресурсы https://proffseo.ru/
В данном случае пользователя не интересует местонахождение компании, главное — сама информация https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Сильные узкопрофильные специалисты вместо «мастеров на все руки»
Специально под ваши условия и техническое задание мы разработаем индивидуальный план продвижения, состоящий из 12 шагов по 22 дня https://proffseo.ru/
выросла видимость проекта в Санкт-Петербурге https://proffseo.ru/prodvizhenie-sajtov-po-rf
Your comment is awaiting moderation.
Discover how we’re making it easier for you to work more sustainably and minimise your environmental impact. Some of our products are investments, which means there’s a risk you could get back less money than you put in. Always do your own research. There’s a Plum plan for everyone, and all paid plans are free to try for 30 days. We’re updating our subscription offerings. If you subscribed to any Plum plans before 07 07 2025, please visit this link to explore your full offering. explore colours Discover how we’re making it easier for you to work more sustainably and minimise your environmental impact. FXCess is a trade name of Notesco Int Limited; a company incorporated in Anguilla with registration number A000001800 and registered address The Valley, AI2640, Cosely Drive, 1338, AI. Whether you’re new to prediction games or just want a casual app to pass the time, Colour Trading is worth a try. But as always, play responsibly and stick with versions that are free of shady practices or financial risk.
https://participez.perigueux.fr/profiles/tagselfterja1988/activity
You can complete and sign an Endowment withdrawal instruction and email the form to instructions@allangray.co.za. For other withdrawals, you can complete and sign a Pension or Provident Preservation Fund withdrawal instruction and email the form to instructions@allangray.co.za. Insurance products (excluding Travel Insurance) are issued by RACQ Insurance Limited ABN 50 009 704 152 (RACQ). Conditions, limits and exclusions apply. This is general advice only and may not be right for you. This information does not take your personal objectives, circumstances or needs into account. Read the Product Disclosure Statement (PDS) and any applicable Supplementary PDS before making a purchase decision on this product. You can also access our Target Market Determinations on this website.
Your comment is awaiting moderation.
On the dashboard, go to ‘Quick Access’ and select ‘Mobile Registration Renewal’ The digital registration process through UAE Pass only takes a couple of minutes, following which the renewal request will generally be approved within 2 hours. If you believe that any of your vehicle’s details such as engine, VIN, colour, or weight details were recorded incorrectly at an AIS, DVS centre, regional DoT office or agent, you can call the Customer Contact Centre on 13 11 56 to have the matter investigated. Website T&Cs The MantriMall platform, also called Mantri Mall or Mantrimall, is an Android-based gaming application where users predict which colour will appear next in a given round. The colours are typically: But what exactly is it, how does it work, and is it worth your time? In this article, we provide a full review and explain how to play Colour Trading.
https://md.yeswiki.net/s/o0yK8N953
Choose one of the available languages. Text you enter is read aloud and text you speak is transcribed in this language to other players if they’re also using chat transcription. By default, your console language is used as your spoken language. If your console language isn’t supported, the spoken language defaults to English. After you set up chat transcription, the voices of other players are converted to text and appear on the right side of the voice chat card. © 2024 Sunflower floral foam Fortis Hospital Kangra (A unit of Himachal Healthcare Private Limited) is a 100 bedded, tertiary healthcare hospital situated at Kangra (Dharamshala Road). We commenced operations in July 2012 and since then have achieved immediate recognition with world class clinical and medical excellence. Looking for the best colour prediction Telegram channel or group to win in online colour games? These Telegram groups provide tips, signals, and predictions to help you bet on the right colour, usually red, green, or violet and make money.
Your comment is awaiting moderation.
「ベラジョンカジノで還元率が高いスロットは?」「ベラジョンカジノのスロットはどれが勝ちやすい?」 落ちもの系スロットにはフリースピンがない機種もあります。通常時でもきっかけがあれば、高額配当になりやすいためです。 ハイローラープレイヤーにとって魅力的なのは、出金条件が1倍以下で、現金に近い使い勝手の初回入金ボーナスです。大きな資金を入金しながらも、余計な縛りなく即座に利益へつなげられるのが最大の強み。 日本のカジノで特に人気のあるPlay’n GOのタイトルには、「Book of Dead」「Reactoonz」「Legacy of Dead」「Beasts of Fire Maximum」「Fire Joker」などがあります。 オンラインスロットはいつでもどこでも遊べるのが魅力で、日本でもたくさんの人がプレイしています。
https://docs.monadical.com/s/fQz9PtVlS
『Reactoonz』は同じシンボルが縦横に5個以上並ぶと配当となるドロップ方式のスロットゲームです。 『Reactoonz 2』は当チームがおすすめできる一押しスロットです。 Hawaiian Dreamのペイアウト率(RTP)は「97.00%」です。 Spinight Casino No Deposit Bonus 100 Free Spins 『リアクトゥーンズ 2(Reactoonz 2)』とは、数多くの人気スロットを輩出しているPlay’n GO社が2020年にリリースしたオンラインスロットです。 シャッフル入金不要ボーナス$20賭け条件・受取方法・使い方 初代よりパワーアップした「リアクトゥーンズ2(Reactoonz2)」が2020年10月1日にリリースされました。 Je me toi-même préconisons de créer en cette amitié ce spéculation via Cashpot Salle de jeu de amuser à la outil a dessous Lucky Lady’s Charm de mode de financment profond. Avec votre casino, les joueurs ont à disposition de nombreuses produits parfois de faire une estafette de trois-cents% pour altitude en compagnie de €. Et cela est plutôt un avantage pertinente avec abandonner l’aventure tel un Prince ou cet Souveraine pour la appareil pour thunes Lucky Lady’s Charm.
Your comment is awaiting moderation.
https://t.me/s/site_official_1win/539
Your comment is awaiting moderation.
Повышаем трафик за счет проработки структуры сайта https://proffseo.ru/prodvizhenie-sajtov-po-moskve
При этом, в качестве регионов может быть указана страна, субъект государства и город https://proffseo.ru/
млрд ? оборот https://proffseo.ru/
Это интересно!
Региональное продвижение помогает улучшить позиции сайта в поисковой выдаче в одном или нескольких регионах, привлечь целевую аудиторию и увеличить конверсию при сравнительно невысоких затратах https://proffseo.ru/
Поисковые системы лояльнее относятся к местным компаниям, и конкуренция в одном регионе ниже, чем по всей России, поэтому, продвигаясь по геозависимым запросам, достигнуть первой страницы поиска намного проще https://proffseo.ru/prodvizhenie-sajtov-po-rf
В статье мы расскажем, какие способы регионального продвижения сайта наиболее эффективны, и как вести SEO-продвижение сайта в топ-10 Яндекса и Google в одном и нескольких регионах https://proffseo.ru/prodvizhenie-sajtov-po-rf
В нашей команде:
Your comment is awaiting moderation.
Стоимость регионального SEO-продвижения в ТОП-10 Яндекса в необходимые города и области России https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Старший менеджер отдела поискового продвижения https://proffseo.ru/kontakty
– 70 видов работ – Гарантия выполненных работ – Гарантия результата https://proffseo.ru/kontakty
рост целевого трафика https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
В нашей команде:
Даже если открыть TOR-browser (или VPN, анонимайзер), где конфиденциальность на высшем уровне и история не сохраняется, Яндекс присвоит выдаче регион прокси-сервера https://proffseo.ru/prodvizhenie-sajtov-po-rf
В нашем случае, это Москва:
Your comment is awaiting moderation.
увеличили количество заказов https://proffseo.ru/privacy
заявок и заказов из поисковых систем https://proffseo.ru/prodvizhenie-sajtov-po-moskve
Полный список идентификаторов часто используемых стран и российских регионов, с сортировкой по алфавиту доступен по ссылке https://proffseo.ru/prodvizhenie-sajtov-po-moskve
– 70 видов работ – Гарантия выполненных работ – Гарантия результата https://proffseo.ru/prodvizhenie-sajtov-po-rf
Аудит сайта https://proffseo.ru/privacy
Переходы, звонки и интернет-заказы с брендового трафика – бесплатно https://proffseo.ru/prodvizhenie-angloyazychnykh-sajtov
Your comment is awaiting moderation.
301 Moved Permanently
301 Moved Permanently!..
https://whitealley.ru/
https://statrk.ru/
Your comment is awaiting moderation.
Гидравлические моторы, или гидромоторы, – это устройства, преобразующие энергию гидравлической жидкости в механическую энергию вращения. Они являются ключевым элементом гидравлических систем, обеспечивая мощное и управляемое движение в широком спектре промышленных и мобильных приложений.
Принцип работы гидромотора основан на использовании давления жидкости для перемещения поршней, шестерен или пластин, что приводит к вращению выходного вала. Конструкция гидромоторов варьируется в зависимости от типа, но обычно включает корпус, ротор (или его аналог), распределительный механизм и уплотнения. Подскажите где лучший гидравлика
Your comment is awaiting moderation.
узнать больше https://weekpay.ru
Your comment is awaiting moderation.
In recent times, the education industry has experienced a dramatic transformation, greatly driven by the rapid advancement of innovation. One of one of the most substantial developments in this world is the emergence of academic innovation, or EdTech, platforms. These digital systems have not just redefined conventional learning approaches however Na webu jsou k dispozici automaty od těchto poskytovatelů: Pragmatic Play, Spinomental, Amatic, EGT, 3 Oaks, Playson, Wazdan, Igrosoft, Endorphina, Amusnet, Smartsoft Gaming a další. Gates of Olympus využívá netradiční formát herního pole 6 válců × 5 řad, což je větší než u klasických slotů 5×3. Hra má 20 stále aktivních výherních linií, ale ve skutečnosti používá systém Scatter Pays, při kterém symboly vyplácejí kdekoli na obrazovce bez nutnosti seřazení na konkrétních liniích.
https://gorilla138.net/gates-of-olympus-recenze-online-kasinove-hry-od-pragmatic-play/
nebo přes CASINOGURU Se všemi způsoby platí, automaty gates of olympus zdarma než se přesunuli na Dragons Fire Megaways. Česká kasina, spustíte 10 roztočit zdarma kolo. Mobilní Kasino Uvítací bonus je nutností pro hráče, že svět se alespoň připravuje na návrat k normálu. FanDuel sázková kancelář byla zahájena se spoustou fanfár v Sams Town Hotel And Casino v lednu 2023, protože ve většině zemí po celém světě se zmírňují blokovací opatření. Teoretická návratnost automatu (RTP) Gates of Olympus je na úrovni 95,5 %. Hodnocení online slotu Gates of Olympus: 9,5 10
Your comment is awaiting moderation.
Yksi kasinoalan parhaista kolikkopeleistä saa entistä suuremmat kertoimet Pragmatic Playn uusimmassa julkaisussa Gates Of Olympus 1000 on äärimmäisen korkean volatiliteetin slotti eli voitot eivät tule helposti, mutta voittopotentiaali on suuri. Gates of Olympus -kolikkopelissä ei ole ainoastaan kiillotettu Zeuksen haarniskaa, sillä sen verran ylimaallisia voittoja tässä on mahdollisuus kerätä. Peli on uusinta uutta, sillä Pragmatic Play on julkaissut sen vuonna 2021. Gates of Olympus 1000 Dice on mielenkiintoinen lisäys Pragmatic Playn valikoimaan, mutta se ei eroa merkittävästi alkuperäisestä pelistä, lukuun ottamatta noppa-aiheisia symboleita. Pelin ydinmekaniikat ovat edelleen samat, ja korkea volatiliteetti sekä voittokertoimien kertyminen tekevät siitä potentiaalisesti erittäin tuottoisan.
https://rpanusantara.com/koe-uusi-gates-of-olympus-2025-slot-arvostelu-ja-kokemuksia/
Ei ole. Kuten jo aiemmin totesimme, Age of the Gods: King of Olympus ei ole huijaus. Kyseessä on erittäin luotettavan pelitalon tuotos, jonka toiminta on testattu huolella. On tärkeää kuitenkin varmistaa, että pelaaminen tapahtuu luotettavalla kasinolla, jolta löytyy vaadittavat lisenssit. Pelin turvallisuus ei yksinään riitä takaamaan turvallista elämystä, vaan pelipaikan valinnalla on merkitystä. Tämän Age of the Gods: King of Olympus -arvostelun operaattorit ovat luotettavia ja lisensoituja. Lopuksi Gates of Olympus kolikkopelin arvioinnista, on syytä huomata, että tämä peli on erinomainen valinta sekä online-rahapelien maailmaan uusille tulokkaille että kokeneille pelaajille. Tuplaus on Maltan lisenssillä toimiva pikakasino Briten verkkopankkimaksuilla, joka hoitaa voitot verovapaina jopa minuuteissa tilillesi. Pelivalikoimassa on mm. slotit ja livekasinon pelit ja kampanjoissa hauskoja turnauksia ja kisoja, uskollisuusohjelma Tuplanopeutta unohtamatta. Uuden pelaajan etuna on melkoinen paketti: 200 % bonus 100 € asti, 200 ilmaiskierrosta sekä 5 Tuplaus-peliä!
Your comment is awaiting moderation.
бонуси казино бонусы казино
Your comment is awaiting moderation.
best cam chat sites 321chat
Your comment is awaiting moderation.
Aviator هي لعبة مسلية وغير معقدة لكل من يجربها. توفر النسخة التجريبية نفس المتعة الرائعة سواء تم لعبها مقابل حصص أموال حقيقية أم لا في لعبة المقامرة. العب لعبة تحطم الطيار ✈ بالاضافة الى المهام المشوقة سواء المهام الرئيسية أو المهام الجانبية التي تزيد من اثارة تحميل gta sa للاندرويد 11 من ميديا فاير، كما ان اللعبة تسمح لك بقيادة جميع انواع المركبات سيارات والطائرات، والدراجات النارية بالإضافة إلى القوارب، كما تحتوي المهام على بعض المهمات القتال اليدوي والمسلح. بالإضافة إلى السماح للاعبين التمتع بتخصيص الشخصية من ملابس وتسريحة شعر بالاضافه الى حريه اختيار مسارات وانماط اللعبه.
https://swe-techs.net/%d9%85%d8%b1%d8%a7%d8%ac%d8%b9%d8%a9-%d8%b4%d8%a7%d9%85%d9%84%d8%a9-%d9%84%d9%84%d8%b9%d8%a8%d8%a9-aviator-%d9%85%d9%86-spribe-%d9%81%d9%8a-%d9%83%d8%a7%d8%b2%d9%8a%d9%86%d9%88%d9%87%d8%a7%d8%aa/
عفوًا، هذا المنتج غير متوفر. يرجى اختيار مجموعة أخرى. حاول استخدام الزر أدناه للعودة إلى الصفحة السابقة. يمكنك لعبها على مواقع الكازينو الرسمية مثل Blaze و 1Win و 1xBet و Pin Up و CBet ؛ على سبيل المثال لا الحصر. تستخدم جميع منصات الألعاب هذه طرق دفع آمنة حتى يتمكن اللاعبون من اللعب دون قلق. جملتنا اكبر سوق لبيع المنتجات بسعر الجمله في مصر و الشرق الاوسط استبدال وارجاع مجاني ووفق إحصائيات رسمية صدرت عن منظمات حقوقية، فإن أكثر من 40 ألف حالة طلاق حول العالم حتى الآن سُجلت نتيجة خلافات بسبب الألعاب الإلكترونية وإدمانها.
Your comment is awaiting moderation.
Además, los aparatos de ajuste tienen una amplia aplicación en el sector de la prevención y el supervisión de estándar. Facilitan detectar posibles errores, reduciendo intervenciones elevadas y averías a los equipos. Además, los datos obtenidos de estos aparatos pueden usarse para maximizar métodos y aumentar la exposición en sistemas de investigación. PRO88 adalah situs game online deposit pulsa terbaik tahun 2020 di Indonesia. Kami menyediakan berbagai macam game online terbaik dan terlengkap yang bisa Anda mainkan di situs game online kami. Hanya dengan mendaftar satu ID, Anda bisa memainkan seluruh permainan yang tersedia di PRO88. The brand’s sportswear evolution began in 1972. Fila was the first to bring color to the tennis court with the White Line collection, aesthetically surprising for its functional design and unconventional use of color. It sparked a sensation among athletes and fans alike, followed by innovation from Fila in mountaineering, skiing, water sports, basketball, golf, and motorsports. The brand always married a bold sense of style with the mandatory ease of movement, which is what made Fila appealing for playing sports and living life in total freedom.
https://interlinecontact.alphatoolsblog.com/index.php/2025/11/03/review-del-juego-balloon-de-smartsoft-para-jugadores-peruanos/
Y así es como se nos presenta temáticamente este Satori, el primer juego de caja grande de Perro Loko Games y que se convierte en el plato fuerte de la editorial española para esta su primera expedición en SPIEL. En él los jugadores compiten por progresar en el camino espiritual, por el que guiarán a sus seguidores hacia varios lugares sagrados donde meditar y orar, llevar a los monjes a las montañas en busca de sabiduría y claridad, y colaborar en la edificación de una imponente pagoda. Envío gratuito a partir de 45€ A bGaming Creó un juego 3D increíblemente realista. La jugabilidad también es un poco diferente. En cada ronda, eliges una celda de una fila de 5. Si golpeas la mina, el juego termina. Si tienes suerte, el juego continúa y se abre la siguiente línea. Puedes retirar en cualquier momento. La personalización de campos también está disponible. Sin embargo, no es posible elegir el número de minas: cada vez solo hay una seguida. Después de experimentar con él, entendemos que un diseño cautivador es la característica principal. En otras palabras, es bastante sencillo y puede resultar aburrido para los jugadores experimentados.
Your comment is awaiting moderation.
Sí, es seguro jugar a Sugar Rush en línea en México siempre y cuando elijas un casino en línea confiable y con licencia. Es importante verificar que el sitio web esté regulado por una autoridad competente y que ofrezca métodos de pago reconocidos. ¿Cuál es el atractivo de programas de telerrealidad como Sugar Rush: Delicias navideñas? ¿Inspiran o enseñan algo a los espectadores? ¿Publicitan algo a su audiencia? ¿Hasta qué punto podemos confiar en la “realidad” de la telerrealidad? Todos los productos de nuestra tienda de cannabis medicinal California Dreaming son 100% naturales y cuentan con registro INVIMA vigente. Si el casino acepta MasterCard como método de pago, Book of Dead. Si el jugador conoce la cantidad o el riesgo involucrado, Danger High Voltage. Esta compañía de software ofrece variaciones impecables de los modos de juego con crupier en vivo para todos los juegos de mesa que son populares, Wolf Hunters. En algunos casos, White Rabbit.
https://melhoresbarbeadores.com.br/resena-del-juego-de-casino-balloon-de-smartsoft-para-jugadores-de-mexico/
Los concursantes están en esta competencia para ganarla, y trabajan duro para lograr su objetivo. Aun así, no se trata de un torneo despiadado; los reposteros elogian a sus oponentes y son receptivos a los comentarios de los jueces, que mezclan sus críticas con palabras de aliento. Una guía para todos y cada uno de los casinos en línea; Reseñas imparciales de casinos con licencia, reseñas de tragamonedas de video, probabilidades y datos de RTP para todos los juegos populares, guías de estrategia, los mejores bonos de casino y noticias del mundo de los juegos en línea. Además, promovemos prácticas de juego responsable, recordando que nuestros servicios están destinados exclusivamente a mayores de 18 años. Publicado el 20 de julio de 2023 Introduce un máximo de 375 caracteres para añadir una descripción a tu widget:
Your comment is awaiting moderation.
Dentre esses slots, os de maior destaque são o Gates of Olympus, o Sugar Rush e o The Dog House, jogos com RTP acima de 97% no cassino Estrela Bet. As slots da Pragmatic Play transportam-nos para universos distintos e com detalhes que contam uma história. A Gates of Olympus, por exemplo, é inspirada na história do rei do Olimpo, o deus Zeus. A trilha sonora de mistério e tambores estrondeantes trazem certo tipo de imersão para o usuário que quer aprender a como jogar Gates of Olympus. Antes tudo, é importante entender que, por se tratar de um jogo de cassino, o operador nunca estará na vantagem. As chances para o usuário são menores do que pra casa, e o jogador precisará contar com a sorte para vencer. Contudo, existe a possibilidade de analisar as rodadas e estudar a melhora hora de realizar uma entrada e exercitar como jogar Gates of Olympus.
http://thcsnghiaan.pgdnamtruc.edu.vn/3869/review-do-coin-volcano-da-3-oaks-uma-explosao-de-moedas-no-cassino-online-4.html
Se você quer saber como jogar Ninja Crash, saiba que o jogo possui regras simples, mas é essencial entender como ele funciona antes de apostar dinheiro real. Isso ajuda a evitar decisões impulsivas e aumenta suas chances de uma experiência positiva. O Ninja Crash é um jogo de multiplicadores único em que o jogador precisa cortar doces com a espada de um ninja. Cada doce cortado revela múltiplos que podem ir de 0x a centenas de vezes o valor apostado. O jogador pode decidir sair com o lucro quando quiser, desde que ainda não tenha tido o azar de tirar o zero nos cortes. Com um depósito mínimo de R$ 10, você já consegue começar a jogar Ninja Crash com dinheiro real. Abaixo, mostramos como é fácil o processo após clicar no botão de depósito. O exemplo mostra R$ 50 porque é um valor que permite ativar bônus quando disponíveis e também é suficiente para participar do sorteio da plataforma em questão!
Your comment is awaiting moderation.
Mas não há como saber qual será o resultado. Você pode acabar com um multiplicador abaixo de 1.0x e tomar um prejuízo, ou conseguir um multiplicador alto e levar um prêmio consigo. Limite de atividade O slot tem a seguinte estrutura: Se você está interessado em testar sua sorte em slots com jackpots, aqui estão alguns dos mais famosos do mercado: Privacidade Em Fruit Million Este slot de 243 vias da Microgaming é baseado na popular série de TV Game of Thrones. Neste slot você pode escolher sua casa favorita e viajar pelos Sete Reinos de Westeros para conquistar o Trono de Ferro junto com grandes vitórias. Este jogo de caça-niqueis tem símbolos especiais e rodadas grátis para aumentar suas chances de ganhar. Se ainda tiveres dúvidas sobre a emocionante slot Gates of Olympus, não te preocupes! Aqui estão as nossas respostas para as perguntas mais comuns dos leitores. Estas informações são essenciais para iniciares a tua jornada, pois trazem detalhes sobre o RTP, recursos disponíveis e a editora do jogo. Além disso, não faltam aqui sequer as nossas recomendações dos melhores sites para jogar Gates of Olympus em Portugal.
https://www.nourlondonglobalservices.com/modos-de-jogo-em-jetx-variedade-para-todos-os-perfis/
Embora os cassinos não possam mais oferecer bônus de boas-vindas com giros grátis no cadastro, a maioria ainda oferece promoções recorrentes com rodadas grátis sem depósito — como é o caso da Roda da Sorte da Betano, a Super Spin da Superbet e outras roletas promocionais. A BetMGM é uma plataforma com bônus que possui ofertas personalizadas desde o registro. Ofertas como bolão, torneios e apostas combinadas estão disponíveis. A BetMGM é uma plataforma com bônus que possui ofertas personalizadas desde o registro. Ofertas como bolão, torneios e apostas combinadas estão disponíveis. A BetMGM é uma plataforma com bônus que possui ofertas personalizadas desde o registro. Ofertas como bolão, torneios e apostas combinadas estão disponíveis.
Your comment is awaiting moderation.
Привет всем!
Решил поделиться своими впечатлениями о бренде Dahua . Я давно интересуюсь системами видеонаблюдения и вот недавно решил установить себе камеру. Рассматривал разные варианты, но остановился именно на Dahua.
Что меня привлекло:
Цена-качество: Оборудование вполне доступное, при этом работает стабильно и надежно.
Широкий выбор: Камеры разных форматов, видеорегистраторы, аксессуары — каждый найдет подходящее решение.
Простота настройки: Даже новичкам разобраться несложно, все интуитивно понятно.
Новинки и технологии: Постоянно появляются новые модели с улучшенными характеристиками, например, встроенный интеллект для анализа изображений.
Короче говоря, если ищете качественное оборудование для дома или бизнеса, рекомендую обратить внимание на Dahua . Уверен, вас порадует результат!
Делитесь вашим мнением, интересно услышать ваши истории и советы.
Your comment is awaiting moderation.
Цена ремонта будет зависеть от того, что предстоит сделать https://dialdrive.ru/
К примеру, замена двигателя начинается от 14 000 руб., а рихтовка царапин – от 1000 руб https://dialdrive.ru/dvs
ЗАМЕНА РЫЧАГА ПЕРЕДНЕГО https://dialdrive.ru/dvs
Сеть шинных и сервисных центров КОЛЕСО https://dialdrive.ru/katalizator
ру с 1998 года обеспечивает своих клиентов правильно подобранными шинами и колесными дисками, профессиональным шиномонтажом, услугами ремонта и сервисного обслуживания автомобилей https://dialdrive.ru/
Телефон и соцсеть подтверждены https://dialdrive.ru/dvs
Документы подтверждены https://dialdrive.ru/katalizator
Диагностика https://dialdrive.ru/dvs
Your comment is awaiting moderation.
ГАРАНТИИ https://dez-spasatel.ru/articles/authors/oksana-petrovna-zhitnikova/
Лаборатория СЭС https://dez-spasatel.ru/articles/tarakany/pomogaet-li-bornaya-kislota-ot-tarakanov/
ПОДОРОБНЕЕ О СЭС САО https://dez-spasatel.ru/unichtozhenie-borshchevika/
СЭС Москвы работает для юридических и частных лиц в режиме 24/7/365 https://dez-spasatel.ru/deratizatsiya-unichtozhenie-gryzunov/krysy/
В зависимости от типа заражения и используемых средств, дезинфекторы санэпидстанции применяют различные методы: санобработку паром, химическое обеззараживание, ультрафиолетовое облучение и т https://dez-spasatel.ru/dezinfekciya/obrabotka-kholodnym-tumanom/
д https://dez-spasatel.ru/dezinsekciya/komary/
Мы оказываем эти типы услуг https://dez-spasatel.ru/articles/dezinfektsiya/
Your comment is awaiting moderation.
Заказчик https://drogal.ru/portfolio-items/takelazh-s-mpu/
Расстояние https://drogal.ru/glossary/edo/
Посмотрите что говорят наши клиенты https://drogal.ru/glossary/benchmarking/
Такелаж сопряжен с погрузочно-разгрузочными операциями и транспортировкой крупногабаритных или очень тяжелых грузов, а также монтажными работами https://drogal.ru/takelazhniki-kto-eto-i-chem-oni-otlichayutsya-ot-gruzchika/
Ввиду большого веса и громоздкости грузов приходится использовать грузоподъемные механизмы и грузозахватные устройства https://drogal.ru/glossary/takelazh/
Дополнительные услуги https://drogal.ru/glossary/vigodopriobretatel/
ГАЗон – 5 т, 6 м, 45 м?
Your comment is awaiting moderation.
Арт. 790783.
Грузоподъемность от 2000 до 4000 кг Высота подъема от 1600 до 1700 мм.
Грузоподъемность: 150 кг.
В сложенном состоянии высота от 80 до 100 мм. Позволяют использовать паллетную тележку.
Гидравлические столы совершают оперативный подъем различных грузов на небольшую высоту. Они используются в складских помещениях, на промышленных предприятиях, погрузочно-разгрузочных пунктах, в лабораториях.
Арт. 791988.
Your comment is awaiting moderation.
Всем привет! Хочу посоветовать киноресурс, который стал для меня находкой . Это Лордфильм на русском языке. Я дорожу своим временем , поэтому для меня важна скорость и простота. Здесь меня все нравится : сайт шустро грузится , поиск работает без нареканий , а в плеере есть все необходимые функции , включая субтитры . Отдельно хочу отметить мобильную версию сайта – она выполнена на высшем уровне . Воспроизведение с планшета или телефона такое же комфортное десктопной версии, все элементы подогнаны идеально . Если вы, как и я, часто любите посмотреть кино в дороге или в кровати перед сном, то этот сайт станет для вас отличным помощником . – https://lordfilm-online.top/
Your comment is awaiting moderation.
Sup traders!
Wanted to post a fresh thread about blockchain updates.
It covers market shifts in crypto in general.
Really a good read, especially if you trade.
Take a look
Your comment is awaiting moderation.
авиатор игра онлайн
Именно благодаря этому, игра находит своих поклонников среди разных возрастных групп.
Your comment is awaiting moderation.
Привет всем!
Решил поделиться своими впечатлениями о бренде Dahua . Я давно интересуюсь системами видеонаблюдения и вот недавно решил установить себе камеру. Рассматривал разные варианты, но остановился именно на Dahua.
Что меня привлекло:
Цена-качество: Оборудование вполне доступное, при этом работает стабильно и надежно.
Широкий выбор: Камеры разных форматов, видеорегистраторы, аксессуары — каждый найдет подходящее решение.
Простота настройки: Даже новичкам разобраться несложно, все интуитивно понятно.
Новинки и технологии: Постоянно появляются новые модели с улучшенными характеристиками, например, встроенный интеллект для анализа изображений.
Короче говоря, если ищете качественное оборудование для дома или бизнеса, рекомендую обратить внимание на Dahua . Уверен, вас порадует результат!
Делитесь вашим мнением, интересно услышать ваши истории и советы.
Your comment is awaiting moderation.
What’s good, folks?
Wanted to post a super informative post about the latest in crypto.
It goes over major updates in BTC, ETH, and other coins.
Really a good read, especially if you trade.
Take a look
Your comment is awaiting moderation.
Sup traders!
Just dropping by to share a pretty interesting article about Bitcoin & altcoin trends.
It goes over major updates in crypto in general.
Worth checking out, especially if you trade.
Full link
Your comment is awaiting moderation.
посетить сайт kra43 cc
Your comment is awaiting moderation.
Hi all! My name is Admin Read:
Для самых выгодных покупок обращайтесь в Kraken — ваш универсальный магазин. От бытовой техники и электроники до модной одежды — kraken зеркало сайта удовлетворяет любые потребности. Ежедневные скидки, эксклюзивные акции и интуитивная платформа кракен дарк нет превращают шопинг в удовольствие. Быстрая доставка и первоклассное обслуживание клиентов кракен сайт тор ссылка помогут вам извлечь максимум из каждой покупки.
Your comment is awaiting moderation.
Перевозка грузов включает в себя ряд действий, необходимых для обеспечения оптимального качества перевозки https://yaschiki.ru/uslugi/upakovka-v-termousadochnuyu-plenku/
Очень важным элементом является подготовка поддонов с грузами, от которых зависит устойчивость конструкции, а значит и безопасность перевозимых товаров https://yaschiki.ru/product-category/derevyannie-yashchiki/
Для этого иногда необходимо использовать правильно подобранную деревянную тару https://yaschiki.ru/product/derevyannii-yashchik-1400-1000-800/
Все мы знаем, что надлежащая защита товаров во время транспортировки особенно важна, в частности, из-за ответственности экспедитора за любой уще РФ, который возникает при получении товара от отправителя и прекращается при передаче товара получателю https://yaschiki.ru/product/derevyannii-yashchik-1400-1000-800/
Поэтому перевозчики тщательно проверяют соответствие грузов, предназначенных для перевозки, правилам безопасности https://yaschiki.ru/product/derevyannii-yashchik-1400-1200-1500/
Тип ящика: Деревянные ящики https://yaschiki.ru/product/derevyannaya-obreshetka-1200-800-1000/
Деревянные ящики имеют конструкцию https://yaschiki.ru/upakovka-press-form-dlya-otpravki-v-kitai/
Промышленная упаковка отличается от обычной своей высокой прочностью и долговечностью https://yaschiki.ru/
Основные функции упаковки:
Для изготовления используются различные сорта древесины и пиломатериалов: тарная доска, фанера, ДВП, бруски и т https://yaschiki.ru/morskaya-upakovka-sbornogo-gruza/
д https://yaschiki.ru/product/derevyannii-yashchik-1400-1000-1700/
При выборе материалов, как и конструкции деревянной тары, исходят из условий, в которых будет производиться транспортировка груза, его вес, объем и необходимый уровень защиты https://yaschiki.ru/product/derevyannii-yashchik-1300-1300-500/
Деревянные ящики являются универсальной упаковочной тарой именно благодаря возможности совершенно различного исполнения каркаса, сортов древесины, вида пиломатериала и вида крепления https://yaschiki.ru/product/derevyannii-yashchik-1450-1000-2200/
Таким образом, деревянная тара один из наиболее надежных видов упаковки обеспечивающих сохранность товаров во время транспортировки https://yaschiki.ru/product-category/yashchiki-iz-faneri/
Кроме того они недорого в производстве ящики удобно перевозить, складировать, работать во время разгрузочных и погрузочных работ, как людям так и специализированной технике https://yaschiki.ru/upakovka-press-form-dlya-otpravki-v-kitai/
В основном в деревянную тару , стоимость на которую можно найти на сайте , осуществляется при перевозке тяжелых грузов, на кораблях https://yaschiki.ru/product/derevyannii-yashchik-1200-1200-750/
Это связано с тем, что она отличается прочностью https://yaschiki.ru/product/derevyannii-yashchik-1200-1200-750/
Единственный недостаток — слабая устойчивость к атмосферным осадкам https://yaschiki.ru/upakovka-stankov-dlya-transportirovki/
Your comment is awaiting moderation.
Hi all! My name is Admin Read:
Kraken сохраняет первенство в интернет-торговле, предлагая широчайший ассортимент и максимальное удобство. В каталоге kraken darknet ссылка есть всё, что вам нужно — от базовых вещей до предметов премиум-класса. Благодаря проверенным отзывам, удобным оплатам и быстрой доставке, kraken at ссылка обеспечивает вам комфортный и уверенный опыт покупок. Начните покупать в кракен маркет тор прямо сейчас, чтобы получить доступ к эксклюзивным предложениям и привлекательным распродажам.
Your comment is awaiting moderation.
“Gorgeous nymphomaniac yearns for release.” Here — rb.gy/8rrwju?stype
Your comment is awaiting moderation.
Once in a while content builders roll out massive hits that gain worldwide recognition. Pragmatic has quite a few of them, including Gates of Olympus. It features a fantastic scatter pays engine that contributes a lot to the success of the pokie machine, because who doesn’t love the idea of being paid without similar symbols forming certain patterns or landing on adjacent reels. Players will find themselves at the entrance to the realm of the Gods, Olympus. An ominous Zeus hovers at the gate, daring those who approach to be worthy. We’d recommend this game if you enjoy the original Gates of Olympus slot game, or you’re just a fan of mythical slots in general. The Super Scatters really make this game stand out. Plus, who wouldn’t want to win up to 50,000x their stake? The Gates of Olympus 1000 demo version includes all the features of the real game – same grid layout, multipliers, and free spins, so you can test out your strategies before playing for real. Whether you’re new to the series or just want to experience the power of Zeus without pressure, demo mode is a great place to start.
https://www.assistwise.co.uk/gates-of-olympus-max-win-how-to-hit-the-biggest-payouts/
They’ll also reactivate the bonus – you just need to find four Wild symbols during the bonus to do this. Only players above the age of 18 are permitted to play our games. Underage gambling is an offence. Of course! You can play the Bigger Bass Bonanza slot for free right here at VegasSlotsOnline. You’ll find thousands of other demo games by top providers to try out too. You can email the site owner to let them know you were blocked. Please include what you were doing when this page came up and the Cloudflare Ray ID found at the bottom of this page. The low-paying symbols of Bigger Bass Bonanza are those of the ace-ten cards, which makes sense given how often fishermen can play cards to pass the time. The higher-paying catches are, in order, a tackle box, a lure, a rod, and finally the boat on which you set sail. A fish symbol can also appear; this offers a randomised amount of money each round.
Your comment is awaiting moderation.
Care instructions SIGN UP FOR CASINO AND SPORTS BETTING UPDATES Connect with us SIGN UP FOR CASINO AND SPORTS BETTING UPDATES The cascade feature takes place after every spin as winning combinations pay out and then the winning symbols vanish. The symbols that are left drop to the bottom of the screen and then the empty positions are filled with fresh symbols. Players may receive unlimited cascades. Our main plates (excluding Fish & Chips) are served with vegetables and your choice of roasted potatoes or rice. When you land matching symbols on an active pay line you will receive a payout, players can enjoy the game and increase their chances of winning. This means that the odds can vary depending on the specific wheel and ball used, as well as any bonuses or promotions that may be available.
https://subur188.net/casino-gates-of-olympus-top-irish-sites-reviewed/
Gates of Olympus 1000 is a great sequel to the original game, featuring larger multipliers and better animations. The main gameplay is still the same, but the top prize has gone up, along with the number and worth of multiplier symbols. The table below highlights the key features of the game, such as max win, RTP, variance, and betting limits. Can’t wait for the Free Spins to land naturally? The Bonus Buy option in Gates of Olympus 1000 slot lets you skip the wait and dive straight into the heart of the action. The global multiplier is another awesome feature that is part of the Gates of Olympus experience. It is an ingenious way to make sure that the player gets a guaranteed win at the end of the game. Regardless of your spin value, the multiplier will remain active throughout the entire game, and without any limits whatsoever. The RTP is up to the standard, and the 5000x winning potential means that you should expect far more frequent wins. And considering that the multiplier orbs are both 500x and can drop anywhere, anytime and without a limit, Gates of Olympus truly sounds like the right choice.
Your comment is awaiting moderation.
Hi there, blockchain friends!
Wanted to share a smart review about latest token launches.
It analyzes several big trends in trading world.
Definitely a good weekend read.
Go to link
Your comment is awaiting moderation.
Nos avantages sur Mystake casino : Pour ceux impatients d’expérimenter directement les frissons des Free Spins, Sugar Rush 1000 propose une option Buy Free Spins. Pour accéder directement à la fonctionnalité Free Spins, optez pour les options d’achat de fonctionnalité : De Quoi Avez-Vous Besoin Pour Obtenir Des Jeux, règles des jeux de casin Sugar Rush Bitcoin est la solution parfaite pour les transactions en ligne. Cependant, au Black Jack. L’embauche va être un véritable problème pour les aspirants livres en dehors du Nevada, examen complet des machines à sous Sugar Rush de push gaming à l’Hold’em Poker et à la Bataille. Lors de votre inscription, et en exclusivité. Release The Kraken Symbole Scatter
https://altiustennisacademy.com/best-withdrawal-aviator-sites-for-canadians/
Les joueurs commencent la partie en plaçant les mises souhaitées, car c’est seulement censé améliorer l’expérience. Lorsqu’un casino en ligne est sur la liste noire, ainsi que pour les joueurs bibliques parmi vous qui sont religieux et qui aiment aussi jouer aux machines à sous en ligne pour de l’argent réel. En stock – Expédition sous 24h 48h Les tours gratuits offrent de nombreux avantages dans Sugar Rush 1000. Ils permettent aux joueurs d’augmenter leurs gains sans risque supplémentaire. Cette fonctionnalité est particulièrement bénéfique dans un jeu qui offre déjà un RTP élevé. Les joueurs peuvent observer comment leurs gains s’accumulent au fil des tours, créant une sensation de suspense et d’excitation.
Your comment is awaiting moderation.
1. La ligne de l’indicateur de vortex positif (+VI) est calculée en divisant la somme du mouvement directionnel positif (+DM) sur une certaine période de temps par la somme de la plage réelle (TR) sur la même période de temps. Le +DM est la différence entre le plus haut actuel et le plus haut précédent, tandis que le TR est le plus élevé des éléments suivants : la différence entre le plus haut actuel et le plus bas actuel, la valeur absolue de la différence entre le plus haut actuel et la clôture précédente. , et la valeur absolue de la différence entre le plus bas actuel et la clôture précédente. La communauté WordPress se réunit régulièrement dans des événements tels que des WordCamps, des rencontres locales, des conférences en ligne et des forums de discussion pour échanger des idées, partager des connaissances et travailler ensemble sur des projets liés à WordPress.
https://valofficer.com/?p=15889
Subvention accordée : 15 000 activités près de chez vous Dé pour jouer ou à collectionner. Super qualité pour vos jeux. Vortex Expérience Nantes9 rue des Piliers de la Chauvinière 44800 Saint-Herblain02 52 59 66 30 Vortex Nantes Pendant votre team building, Vortex Expérience est à vous ! Jouez à nos différentes expériences pendant 3 heures. Vortex Expérience s’adresse à tous les âges. « Jeunes ou personnes plus âgées, notre objectif c’est qu’au bout de 20 secondes, on puisse déjà s’amuser », se réjouit Pierre Chicorp. Il est cependant recommander de jouer à partir de 13 ans, en raison du poids de l’équipement. Certifiée sans spam, riche en idées cadeaux uniques, offres exclusives et actualités de la biodiversité !
Your comment is awaiting moderation.
Погрузитесь в захватывающий мир 1вин игра авиатор и испытайте удачу!
Безопасность и прозрачность – важные аспекты, которые гарантирует ‘1win’.
Your comment is awaiting moderation.
Наслаждайтесь увлекательными играми и щедрыми бонусами в Лаки Пари регистрация 2025!
Уникальной платформой можно назвать LuckyPari, которая предоставляет пользователям широкий спектр услуг. На сайте представлено множество спортивных событий, на которые можно делать ставки. Одним из значительных преимуществ LuckyPari является удобный интерфейс. которые могут столкнуться с различными вопросами. Связаться с поддержкой можно как через онлайн-чат, так и по электронной почте,
Your comment is awaiting moderation.
Download VidMate 2024 APK – Fast & Free Video Downloader for Android Application Name VidMate Current Version 5.0257 Size 18.97 MB Android Version Required Android 4.4 and up Last Updated August 02, 2024 Download VidMate 2024 APK – Fast & Free Video Downloader for Android VidMate 2024 is a powerful Android application that allows users… Any questions for InShot (FREE video editor with music & video maker, photo slideshow maker)? Please contact us at inshot.android@inshot A free short video platform. Once the download is complete, open your File Manager or Downloads folder.You’ll find a file named InShot_Pro_Mod.apk — this is the setup package for the InShot Pro Mod version. Video Editor & Maker – InShot Mod Video Editor & Maker – InShot Mod Inshot MOD APK is a powerful tool for anyone looking to create high-quality videos with premium features for free. With no watermarks, unlocked effects, and an ad-free interface, it offers an excellent video editing experience, making it a must-have for video enthusiasts.
https://espanol.safecreditsolutions.com/bonus-round-expectations-in-balloon-game-indian-player-review/
Released on the 25th of February 2021, the Gates of Olympus slot sees you head to Mount Olympus. With a Greek mythology theme, you are transported to the gates of Zeus’ realm (Olympus). In case you’ve lived under a rock all your life, Zeus is the sky and thunder god in ancient Greek mythology who’s known as the king of the Greek gods. With an impressive RTP of 96.5% and the potential for a royal max win of 5,000x your bet, how does Gates of Olympus compare to other Greek mythology slots? Find out in our comprehensive Gates of Olympus slot review below, where we delve into the features, strategies, and winning potential of this Pragmatic Play masterpiece. That means you could property step 3 for the reel step 1, cuatro to the reel 3 and you may 1 for the re3l 5 whilst still being create a winning mix of symbols. Open up the brand new Gates out of Olympus position games and you’lso are served with an excellent 6 reel, 5 line game presenting all the way down-investing jewels, and better-spending goblets, crowns, hours servings, and bands. The first Doors out of Olympus is actually a knock to own Pragmatic Play, which means this video game is a pleasant sequel.
Your comment is awaiting moderation.
“Gorgeous nymphomaniac yearns for release.” Here — rb.gy/8rrwju?stype
Your comment is awaiting moderation.
was reading earlier and thought i’d share just generic content, maybe someone finds it useful. came across: more fyi.
Your comment is awaiting moderation.
scrolling through random stuff leaving something i saw just generic content, neutral mention. found this: background just context.
Your comment is awaiting moderation.
Yo crypto fam!
Just dropping by to share a surprisingly solid thread about the latest in crypto.
It covers key movements in crypto in general.
Really a good read, especially if you follow charts.
Read it here
Your comment is awaiting moderation.
don’t even know how i got here might as well drop this here not detailed at all, neutral mention. found this: source just context.
Your comment is awaiting moderation.
Hey all!
Checked out a concise article about current crypto market updates.
It explains how the market’s moving in Bitcoin, Ethereum, and altcoins.
Nice balanced view.
More details
Your comment is awaiting moderation.
o0h8vk
Your comment is awaiting moderation.
Подробнее kra45 at
Your comment is awaiting moderation.
Posting up my sincere impression centered on that gaming site. I cover bonuses, payment speed, and gameplay vibe. Exploring welcome deals and transaction speed. Outlining how the service loads and handles withdrawals. Talking about benefits and drawbacks I tested. Describing what I liked and what I didn’t like. The full article contains additional information Crowngreen
Your comment is awaiting moderation.
What’s up, DeFi crowd?
Just stumbled on a smart breakdown about crypto insights for 2025.
It compares top coins in crypto markets.
Definitely a good weekend read.
Go to link
Your comment is awaiting moderation.
Thanks you”)
https://www.youtube.com/@SupremeAudiobooks
Your comment is awaiting moderation.
Leaving my sincere feedback concerning this site. I discuss rewards, payouts, and general feedback. Discussing mostly special rewards and processing time. Explaining how the site runs and verifies payments. Noting what works and what doesn’t I saw. Explaining what I found useful and what could be better. The full article contains additional information https://newsvibesindia.com/explore-crown-green-casino-and-enjoy-guaranteed/
Your comment is awaiting moderation.
ended up checking different pages and thought i’d share not detailed at all, still maybe worth a look. random link: background just context.
Your comment is awaiting moderation.
Знакомства для взрослых в Алматы месте
В современном живом городе Алматы обнаружение новых связей для взрослых становится важной задачей. люди зрелого возраста желают найти собеседника для совместного времяпрепровождения.
Основные способы создания знакомств
В Алматы широко распространены различные варианты знакомства. Это интернет-ресурсы для взрослых, специализированные клубы и личные знакомства. Каждый вариант имеет свои плюсы, которые позволят найти подходящего собеседника проститутки алматы vk
Онлайн-знакомства в Алматы
технологичные сайты и приложения предоставляют разнообразие вариантов для общения зрелой аудитории. Здесь можно завести аккаунт, просмотреть анкеты и написать сообщение с теми, кто разделяет интересы.
Your comment is awaiting moderation.
Dropping my true take centered on Crowngreen Online. I highlight offers, banking, and overall experience. Going through casino perks and payouts. Mentioning how the experience performs and pays out. Exploring positives and negatives I found. Reviewing what felt good and what wasn’t great. Further details are available in the full article https://coachrimabhattacharya.com/2025/10/29/appreciate-crown-green-casino-and-have-endless-fun/
Your comment is awaiting moderation.
футбол Томск
Your comment is awaiting moderation.
6.
Aprende cómo realizar tu login en Rojabet de forma rápida y segura. Tutoriales, soluciones a problemas comunes y recomendaciones de seguridad. https://triberr.com/rojabetclcom
7.
Guía paso a paso para el registro en Rojabet: cómo crear tu cuenta, validar tu identidad y comenzar a disfrutar de apuestas y casino online. https://promosimple.com/ps/3e99e/rojabet-cl
8.
Encuentra las mejores opciones de casino online en Chile, comparaciones, análisis y listas actualizadas de plataformas destacadas. https://triberr.com/rojabetclcom
9.
Toda la información sobre el casino en línea de Rojabet, incluyendo juegos, métodos de pago, promociones y ventajas. ¡Tu referencia confiable! https://www.blogger.com/profile/07108643177435324012
10.
Descubre los mejores juegos de casino en Chile, desde tragamonedas y ruletas hasta blackjack online. Información clara, actualizada y pensada para jugadores chilenos. https://onespotsocial.com/rojabetcl
Your comment is awaiting moderation.
1.
Descubre todo sobre Rojabet Chile en un solo lugar: apuestas deportivas, casino online, bonos exclusivos y mucho más. ¡Ingresa y aprovecha cada oportunidad! https://myanimelist.net/profile/rojabetclcom
2.
¿Buscas información confiable sobre apuestas deportivas en Rojabet? Encuentra guías, tips y las mejores promociones actualizadas. ¡Todo en un mismo sitio! https://www.walkscore.com/people/314581415087/rojabet-cl
3.
Explora el mundo del casino online Rojabet: reseñas, juegos destacados, consejos y novedades. ¡Tu guía completa para jugar con confianza! https://hub.docker.com/u/rojabetclcom
4.
Conoce cómo funciona el casino en vivo de Rojabet y descubre las mejores mesas de ruleta, blackjack y otros juegos con crupieres reales. ¡Toda la info aquí! https://www.elephantjournal.com/profile/rojabetclcom/
5.
¿Quieres aprovechar el bono de bienvenida de Rojabet? Te explicamos requisitos, beneficios y cómo sacarle el máximo provecho. ¡Infórmate antes de jugar! https://sketchfab.com/rojabetclcom
Your comment is awaiting moderation.
6.
Aprende cómo realizar tu login en Rojabet de forma rápida y segura. Tutoriales, soluciones a problemas comunes y recomendaciones de seguridad. https://able2know.org/user/rojabetcl/
7.
Guía paso a paso para el registro en Rojabet: cómo crear tu cuenta, validar tu identidad y comenzar a disfrutar de apuestas y casino online. https://www.anobii.com/en/0134b9b1fa2b1f7c36/profile/activity
8.
Encuentra las mejores opciones de casino online en Chile, comparaciones, análisis y listas actualizadas de plataformas destacadas. https://gravatar.com/rojabetclcom
9.
Toda la información sobre el casino en línea de Rojabet, incluyendo juegos, métodos de pago, promociones y ventajas. ¡Tu referencia confiable! https://hub.docker.com/u/rojabetclcom
10.
Descubre los mejores juegos de casino en Chile, desde tragamonedas y ruletas hasta blackjack online. Información clara, actualizada y pensada para jugadores chilenos. https://files.fm/rojabetclcom/info
Your comment is awaiting moderation.
1.
Descubre todo sobre Rojabet Chile en un solo lugar: apuestas deportivas, casino online, bonos exclusivos y mucho más. ¡Ingresa y aprovecha cada oportunidad! https://www.goodreads.com/user/show/194712795-bwin–casino
2.
¿Buscas información confiable sobre apuestas deportivas en Rojabet? Encuentra guías, tips y las mejores promociones actualizadas. ¡Todo en un mismo sitio! https://issuu.com/rojabetclcom
3.
Explora el mundo del casino online Rojabet: reseñas, juegos destacados, consejos y novedades. ¡Tu guía completa para jugar con confianza! https://tawk.to/rojabetcl.com
4.
Conoce cómo funciona el casino en vivo de Rojabet y descubre las mejores mesas de ruleta, blackjack y otros juegos con crupieres reales. ¡Toda la info aquí! https://www.hogwartsishere.com/1776675/
5.
¿Quieres aprovechar el bono de bienvenida de Rojabet? Te explicamos requisitos, beneficios y cómo sacarle el máximo provecho. ¡Infórmate antes de jugar! http://www.askmap.net/location/7574601/%D1%81hile/rojabet-cl
Your comment is awaiting moderation.
What’s good, folks?
Just dropping by to share a super informative thread about Bitcoin & altcoin trends.
It goes over market shifts in Web3 & DeFi projects.
Really a good read, especially if you’re into news.
Read it here
Your comment is awaiting moderation.
Posting up my real review related to Crowngreen Casino. I discuss welcome packages, payment speed, and gameplay vibe. Emphasizing welcome deals and processing time. Describing how the platform acts and manages payouts. Reviewing the good and the bad I discovered. Going over what I appreciated and what I didn’t like. The full article contains additional information https://bhavnainteriors.co.in/be-part-of-the-winners-at-crown-green-casino-and-3/
Your comment is awaiting moderation.
Publishing my individual take centered on Crowngreen. I share details about rewards, fund transfers, and overall feel. Highlighting special rewards and fund releases. Outlining how the page acts and handles withdrawals. Pointing out pros and cons I came across. Talking about what felt good and what could be better. Further details are available in the full article Crowngreen
Your comment is awaiting moderation.
Posting up my individual feedback about that gaming site. I share details about bonuses, cashouts, and overall feel. Highlighting welcome deals and payment system. Showing how the casino responds and verifies payments. Summing up what works and what doesn’t I found. Talking about what was nice and what could be better. Further details are available in the full article https://kopislot.blog/try-new-adventures-at-crown-green-casino-and-join/
Your comment is awaiting moderation.
Эй, друзья. Trance Reality оставил у меня смешанные эмоции. Музыка была потрясающей: Paul van Dyk и Markus Schulz выдали свои лучшие сеты. Но логистика фестиваля подвела. Добраться до территории было сложно: указателей было мало, а на входе была огромная очередь. К тому же, фудкорты не справлялись с потоком людей, и к концу вечера еда просто закончилась. Конечно, такие моменты не отменяют качества музыки, но хотелось бы большего внимания к деталям. А вас когда-нибудь разочаровывала организация на фестивалях?
Your comment is awaiting moderation.
Hey, everyone! Allow me to introduce myself as Admin Read:
Площадка Kraken предлагает миллионы новых предложений ежедневно, делая ваш шопинг удобным и экономным. Если вы в поиске эксклюзивных товаров, винтажных предметов или антиквариата, Кракен — идеальное место для вас. С кракен даркнет ссылка тор вы можете быть уверены в безопасности сделок и в быстрой доставке ваших заказов. Откройте для себя kraken market тор, чтобы насладиться лучшими возможностями онлайн-шопинга.
Your comment is awaiting moderation.
Publishing my true feedback centered on this online casino. I outline special incentives, deposit & withdrawal process, and site quality. Going through reward system and payment system. Explaining how the site acts and releases funds. Highlighting main takeaways I tested. Writing about what I liked and what needs improvement. Read the full article for more insights https://olimpiapartners.com.br/spin-the-reels-at-crown-green-casino-and-feel-the/
Your comment is awaiting moderation.
“Gorgeous nymphomaniac yearns for release.” Here — https://rb.gy/8rrwju?Rhyhoro
Your comment is awaiting moderation.
Перейти на сайт vodka casino
Your comment is awaiting moderation.
This high-volatility title raises the intensity with upgraded features, tumbling reels, and surprise multipliers that can appear at any moment. The visuals are bold, the soundtrack is electrifying, and the overall experience feels epic, whether you’re familiar with the first game or diving into the Gates of Olympus universe for the first time. It’s a mythic adventure designed for players who crave powerful themes and fast-paced mechanics. “Newbie wajib coba! Belajar main high risk tanpa modal. RTP terjaga, menang beruntun!” Even though it looks the same and many of the features are the same, it’s a warranted upgrade. Read my Gates of Olympus 1000 review to learn why. If you are a fan of the original game, you might not immediately notice the differences in Gates of Olympus 1000 Pragmatic Play. The thing is, this ‘1000’ version has different math, including a higher max win potential and higher volatility. And the key contributor to this change is up to x1,000 multiplier that is double the multiplier of the original game.
https://g2gplayslot.com/ludo-king-earning-app-tadagamings-royalty-compared/
These types of symbols hold beliefs anywhere between 2x to 500x and they are obtained throughout the for every tumble sequence. If tumbles prevent, the full value of all of the multiplier signs to the grid is deposit 5£ get 20£ casino 2025 added together and you will placed on your own total earn for the bullet. Regarding the 100 percent free revolves added bonus, multipliers collect, undertaking even greater winnings prospective. Be looking for those icons, because they can dramatically increase earnings. Gates of Olympus is one of the cornerstones of Pragmatic Play’s slot portfolio. Its bold design, scatter-pay mechanic, and powerful multipliers create a thrilling, high-risk gaming experience that has captivated slot enthusiasts worldwide, including in Norway. The Gates of Olympus slot is a 6×5 reel, scatter pays slot game from Pragmatic Play that introduces up to 5,000x bet wins thanks to Tumbling Reels, Free Spins & Random Multipliers rewarding up to 500x your bet.
Your comment is awaiting moderation.
Gambola Casino Bonus Codes 2025 Get ready for a feature-packed adventure in 15 Dragon Pearls, where every spin can unlock a new layer of excitement. This slot is designed to keep players engaged with a blend of classic and innovative features, including wild substitutions, free spins, and the thrilling Hold and Win bonus round. With a focus on high-value symbols and multiple jackpot opportunities, the game appeals to both casual players and high rollers seeking big wins. The bonus mechanics are not only rewarding but also interactive, ensuring that each session offers something new to discover. Whether you’re chasing free spins or aiming for the grand jackpot, 15 Dragon Pearls delivers a dynamic and captivating gameplay experience. Content is well-sized so it doesnt dominate the screen but remains easily readable, the chances of landing this max win are 1 in 00 spins. I would like to invite Maximal Wins Casino into this conversation, there is the games Cascading Reels mode which is common in Cluster Pays slots.
https://i-network2u.com/astronaut-slot-review-a-stellar-journey-with-100hp-gaming-for-players-in-pakistan/
Crate-Crates are an additional reward through which the players can win crowns (Adda52 currency), which can offer up to 10,000 coins and can double wins after substitution. No Limit Holdem is still king, Caribbean Stud Poker. The noteworthy maximum win, which offers up to 5,000 times the player’s stake, is the primary zenith. Feature, which is loaded with Bonus symbols and allows you to open the slot’s treasure trove by gathering as many pearls as you can, is how you can achieve this ultimate win. It perfectly captures the 15 Dragon Pearls slot’s abundant payout potential. Two gold spaces trigger the bonus, you will be sharing some personally-identifiable information with us. As you will discover within the table games category, you can see lightning fall. Winning combinations can be obtained by spinning three or more of the same symbol going from left to right across the reels – with a total of 20 possible combinations, the city of Asgard. The artists did a good job creating a bright slot with predominant light colors, you might get different results – maybe Bovada or Ignition comes up instead.
Your comment is awaiting moderation.
No account? Join now Transactions with Gates of Olympus Casino no wonder there is not bad actor clauses in the bill supported by Morongo, with 10 active paylines. There is a separate the page dedicated to rules specifically, gates of Olympus Recent Earnings which is about as standardised as the online slot world gets. What are the different types of payouts at Gates of Olympus keep in mind that options will vary depending on your location and your currency, contact the Michigan Association on Problem Gambling (MAPG) or call the toll-free Michigan Problem Gambling Helpline. Get Your R25 Sign Up Bonus With so many slot games to choose from, it can feel a bit overwhelming if you're just getting started. Trying out different online slots is the best way to find the ones you enjoy most. Choosing easy-to-play games with fun features can help you feel more confident and have a great time. We have a huge variety of slot games, so there’s something for everyone. Let’s take a look at some of the popular ones you might want to try.
https://oktala.net/2025/11/03/aviator-simulator-online-realistic-gaming-experience/
Security is the foundation of a trustworthy crypto casino. We examine whether a platform offers SSL encryption to protect your personal and financial information, and valid licensing and regulation, ensuring the site adheres to industry standards. Platforms meeting these criteria provide peace of mind, letting players focus on gameplay without worrying about the safety of their funds. There are 350+ questions in our collection covering a wide range of topics, including food and drink, geography, fashion, and more. We’ve also included easy and hard questions, kid-friendly questions, and general knowledge questions. But why stop at trivia? You can also use some of these questions in a fun personality quiz, where the answers don’t just test knowledge but reveal something unexpected about the participant.
Your comment is awaiting moderation.
Copyright © 2025 Slots Capital Now we still have good equity on this board but just one more diamond or straight card could put us on the back foot in this pot, many players are seeking a reliable platform to enjoy their favorite games while having the convenience of using their Mastercard for deposits and withdrawals. Its also the scatter and behind bonus payouts whenever two hit the screen, with no limit on the size of the bonus. Johnny Kash Casino – This casino offers a huge selection of games, you’ll have the best possible experience and the chance to win big. This means you can choose from a variety of different games, who is streamed live from a studio or casino. Pragmatic Play boasts a catalogue exceeding 1,000 free games to play on their website, including fan favorites like Gates of Olympus and Sweet Bonanza. The provider is especially popular for its Drops & Wins slot mechanic, while its live casino titles cover roulette, blackjack, game shows, and speed games.
https://a3autohub.com/how-to-play-aviator-with-cash-deposit-in-ghana/
Connect with us Regarding the number of fundamental symbols, The Gates of Olympus is similar to most other games. A list of nine important symbols is provided. Remember that winning doesn’t require matching symbols to appear on a payline or adjacent reels. These symbols function like scatters and pay anywhere they are visible. You’ll get paid if you acquire three sets of matching symbols (8, 9, 10, 11, or 12 to 30). Blue gem combinations will pay 0.25, 0.75, and twice the base bet for the low, medium, and high crosses. Standard bonuses with a UK casino offer will include free spins and deposit matches. Always ensure you read the terms- particularly those that outline your wagering contradictions, plus see if the terms allow the bonus to be stacked with other bonuses so you can enjoy Gates of Olympus at no cost for as long as you can. Bonus buy (100× stake) is available in some markets- but use that option with care! That option has a higher cost and a much higher risk to your bankroll.
Your comment is awaiting moderation.
La volatilità medio-alta di Pirots è sinonimo di un mix di vincite di dimensioni moderate e altre occasionali di dimensioni più grandi. La tabella che segue raccoglie i migliori casinò italiani che propongono queste promozioni dedicate: un’opportunità utile per confrontare in un colpo d’occhio le offerte più vantaggiose su cui utilizzare la slot Pirots 4. Ricorda che i bonus sono un ottimo modo per testare la slot e familiarizzare con le sue dinamiche, ma è sempre fondamentale giocare responsabilmente. Machineslotonline.it è il punto di riferimento per gli appassionati di giochi online, con un focus speciale sulle slot machine. Offriamo recensioni approfondite di oltre 5.000 giochi, tutti disponibili gratuitamente in modalità “fun mode”, senza limiti di tempo né necessità di download. La nostra piattaforma non raccoglie scommesse né dati sensibili, ponendo la trasparenza e la sicurezza degli utenti al primo posto. Gestita da esperti del settore, Machineslotonline.it opera nel pieno rispetto delle normative ADM per il mercato italiano, promuovendo solo siti con regolare licenza ADM.
https://blessthechildrenhome.org/?p=53242
Con Big Bass Reel Repeat slot, la serie del pescatore sbarca in un mondo… Oltre 200.000 con una puntata da 20€. Un’altra vincita memorabile di un giocatore di Netwin, ottenuta su Pirots 3 di ELK Studios, uno dei giochi più apprezzati tra le proposte di casinò online dal vivo. Il fortunato utente ha chiuso la propria sessione con un profitto complessivo pari a 213.091€. Prima i pirati, poi le culture primordiali e ora il selvaggio West. I pappagalli di Elk Studios sono pronti per una nuova avventura nella slot digitale Pirots 3. Una mandria di simboli modificatori, funzioni variegate in perfetta sintonia western: Coin Game, duelli all’ultimo colpo di pistola, Bonus Free Drops e perfino un’entusiasmante Rapina al treno con un bottino in palio fino a un massimo di 10.000 volte la puntata.
Your comment is awaiting moderation.
“Barely legal nymph wants to sin.” Here — https://rb.gy/8rrwju?Rhyhoro
Your comment is awaiting moderation.
Эй, народ! Trance Reality — это не просто фестиваль, это место, где сбываются мечты. Музыка от Aly & Fila и Solarstone была настолько мощной, что я чувствовал, как вибрации наполняют всё вокруг. А потом я отправился исследовать зоны отдыха и наткнулся на ребят, которые рисовали огромные световые картины. Мы познакомились, и они рассказали о своих путешествиях по другим фестивалям. Это был момент, когда я понял, что музыка объединяет людей со всего мира. А что для вас самое главное на фестивалях? Делитесь своими мыслями!
Your comment is awaiting moderation.
Якщо шукаєте корисні поради для повсякденного життя, ось тут є все, що потрібно.
Your comment is awaiting moderation.
15% Доля рынка в регионах присутствия https://metall-sity.ru/sortovoj-prokat/
ООО “МеталлСити” имеет собственный автопарк грузовых автомобилей (в том числе с манипулятором).
Квадратные профильные трубы и прямоугольные профильные трубы обеспечивают значительную экономию средств за счет своего собственного небольшого веса и следовательно, более простой транспортировки и быстрой сборки https://metall-sity.ru/postavshchiki/
Профильные трубы имеют меньшую площадь поверхности по сравнению с открытыми профилями, что приводит к экономии материалов: полимерного, для оцинкованной трубы и других покрытий https://metall-sity.ru/catalog/
АрселорМиттал Темиртау https://metall-sity.ru/catalog/
Общего назначения для холодной и горячей воды, газа с рабочим давлением не более 25 МПа https://metall-sity.ru/
Трубы из квадратного и прямоугольного профиля изготавливаются из существующих бесшовных или сварных круглых стальных труб https://metall-sity.ru/sortovoj-prokat/
Чтобы преобразовать эти трубы в квадратную форму, они обрабатываются в нескольких четырехвалковых клетях, расположенных друг за другом https://metall-sity.ru/
Этот процесс может осуществляться как в виде холодной штамповки, так и при температуре около 950°С под воздействием тепла, при этом технологические свойства конечного продукта различны в зависимости от методов изготовления https://metall-sity.ru/postavshchiki/
Your comment is awaiting moderation.
Чтобы мебель не только радовала глаз, но и прослужила достаточно долго, необходимо использовать только качественную мебельную фурнитуру из твердого металла с продуманным механизмом и возможностью регулировки https://kupefurnitur.ru/price
Вам нужна качественная фурнитура для мебели оптом? Не хотите переплачивать посредникам? Приобрести весь необходимый комплект мебельной фурнитуры вы можете в нашей компании крупным или мелким оптом https://kupefurnitur.ru/
Мы работаем только с проверенными поставщиками, выпускающими действительно надежную продукцию и зарекомендовавшие себя на российском и европейском рынке https://kupefurnitur.ru/onas
Большой популярностью среди производителей мебели также пользуется мебельная фурнитура оптом из Китая по доступной цене https://kupefurnitur.ru/
руководителями представителями контрагентов, юридическими лицами и их работниками, индивидуальными предпринимателями и их работниками (при наличии), физическими лицами, имеющими или имевшими договорные отношения с Обществом, в том числе находящимися на преддоговорном этапе установления таких отношений https://kupefurnitur.ru/price
рамочные и безрамочные механизмы; системы для радиусных шкафов; роликовые системы https://kupefurnitur.ru/price
Первый магазин КДМ был открыт в 2000 году https://kupefurnitur.ru/price
Сегодня 30 магазинов КДМ — это более 25 000 наименований фурнитуры и комплектующих для производства мебели, представляющих продукцию собственных торговых марок «КДМ» и «EVA», а также фурнитуру известных европейских производителей https://kupefurnitur.ru/onas
Команда профессионалов КДМ подобрала ассортимент, который максимально удовлетворяет потребности наших клиентов https://kupefurnitur.ru/
У нас Вы можете купить алюминиевый профиль для шкафов-купе «Найди», ручки российских, турецких, китайских производителей и др https://kupefurnitur.ru/price
В ассортименте нашей компании представлены все виды наименований фурнитуры и комплектующих для производства мебели и многое, многое другое https://kupefurnitur.ru/catalog
Наш магазин фурнитуры для мебели нацелен на долгосрочные партнерские отношения и индивидуальный подход https://kupefurnitur.ru/contact
Компания ориентирована на потребности клиента и предлагает для заводов-производителей, дизайнеров и частных мастеров:
Your comment is awaiting moderation.
Начните знакомство с возможности погружения в виртуальный азартный мир. Оцените с первого взгляда ярком игровом портале. Мне впервые рассказали о Casino друзья, упомянув их положительный опыт. Для новичка важно удобство — на Casino всё оказалось на высоте. Один из самых интуитивных и приятных сайтов для начала игры. Игровые автоматы Casino оказались яркими, инновационными и способными увлечь меня с головой kushkazino.sbs . Каждый шаг становился новым переживанием — от лёгкого волнения до ощущения настоящего триумфа. Игры оказались красочными, увлекательными и создающими ощущение настоящего погружения в приключение. Платформа позволяет открыть доступ к продвинутым формам игры, включая мобильные версии, которые комфортно использовать на ходу. Casino подарило мне не только азарт, но и вдохновение, которое теперь сопровождает меня каждый раз, когда я захожу на платформу. Теперь Casino для меня — это больше чем развлечение, это мир эмоций, которые нельзя забыть. Если и вы хотите испытать подобные эмоции, не теряйте времени. Не упустите возможность первого шага к победам https://casinocactus.top .
Погрузитесь в путь
Найдите удовольстви
Погрузитесь в новые эмоции на платформе казино игр сегодня
Погрузитесь в удово
Найдите все грани победы сайт игр казино без лишних ожиданий
33d53_3
Your comment is awaiting moderation.
Привет, тусовка! SFF IN UA подарил невероятные эмоции! Я кайфовал на сете Ferry Corsten, а потом заглянул в арт-зону. Как у вас?
Your comment is awaiting moderation.
“Gorgeous nymphomaniac yearns for release.” Here — https://rb.gy/t0g3zk?Rhyhoro
Your comment is awaiting moderation.
На сайті рішення побачив портфоліо, яке вразило своїм рівнем виконання. Це точно компанія, якій я готовий довірити свій проєкт.
Your comment is awaiting moderation.
Учредитель и редакция – АО «Москва Медиа» https://pdd-svet.ru/
Главный редактор сетевого издания И https://pdd-svet.ru/o-kompanii/
И https://pdd-svet.ru/avtogorodki-s-pitaniem-ot-solnechnoj-elktrostanczii/
Лобанова https://pdd-svet.ru/mobilnye-avtogorodki-dlya-shkol/
Адрес редакции: 125124, РФ, г https://pdd-svet.ru/staczionarnye-avtogorodki/
Москва, ул https://pdd-svet.ru/staczionarnye-avtogorodki/
Правды, д https://pdd-svet.ru/igrovye-makety-i-bizibordy/
24, стр https://pdd-svet.ru/dopolnitelno/
2 https://pdd-svet.ru/o-kompanii/
Почта: mosmed@m24 https://pdd-svet.ru/igrovye-makety-i-bizibordy/
ru https://pdd-svet.ru/mobilnye-avtogorodki-dlya-dou/
Тел.: +7 (495) 009-12-89 https://pdd-svet.ru/staczionarnye-avtogorodki/
Читайте также: Как учить английский вместе с детьми: семейные привычки https://pdd-svet.ru/staczionarnye-avtogorodki/
Информация о погоде предоставлена Центром «ФОБОС» https://pdd-svet.ru/staczionarnye-avtogorodki/
Информация о курсах валют предоставлена Центральным банком Российской Федерации https://pdd-svet.ru/kontakty/
Информация о пробках предоставлена ООО «Яндекс https://pdd-svet.ru/mobilnye-avtogorodki-dlya-dou/
Пробки» https://pdd-svet.ru/mobilnye-avtogorodki-dlya-dou/
Читайте также: Книга для взрослеющих и взрослых: «НЕТ — всегда НЕТ»
Your comment is awaiting moderation.
Плануєте подорож із родиною? Дізнайтеся більше про туристичні лайфхаки, які зроблять вашу поїздку комфортнішою.
Your comment is awaiting moderation.
Писала реферат про культуру, і знайшла сайт із найкращими прикладами української літератури. Це джерело натхнення для будь-якого дослідника.
Your comment is awaiting moderation.
При изготовлении стеклянных панелей применяется закаленное стекло, имеющее большую прочность https://www.perof.ru/news/zvukoizolyatsionnye-peregorodki-diema-lux-v-ofise-kompanii-ulma-bts-olimp/
При повреждении стеклянной перегородки не образуются острые осколки, что гарантирует безопасность ее использования https://www.perof.ru/news/covid-19/
Материал изготовления открывает широкие возможности по оформлению поверхности ограждения: тонировка, гравировка, оклейка разноцветными пленками и другие https://www.perof.ru/politika/
от 10 дней https://www.perof.ru/glossariy/kamen-keramicheskiy/
Матовое (сатиновое)
Для установки безрамных цельностеклянных зонирующих систем применяется зажимной профиль https://www.perof.ru/news/prozrachnye-dveri-dlya-glukhikh-peregorodok-originalnoe-interernoe-reshenie-pozvolyayushchee-uvelich/
Стандарт ЛДСП 25мм, фурнитура Alboy, оцинкованные опоры https://www.perof.ru/catalog/ofisnye-peregorodki/diema-ofisnye-peregorodki/
Срок изготовления:
Your comment is awaiting moderation.
Читаючи інтерв’ю з Сергієм Середою, я сміялася до сліз. Його здатність знаходити гумор у найбанальніших речах – це щось неймовірне. Але найбільше мене вразило, як він використовує жарт як спосіб піднімати дух людям навколо. Це інтерв’ю стало для мене справжньою дозою оптимізму. Рекомендую прочитати тут.
Your comment is awaiting moderation.
Якщо вас цікавить Наші друзі, вам варто відвідати цей сайт!
Your comment is awaiting moderation.
Crowngreen Casino is a trusted online casino that delivers thrilling games for gamers. Crowngreen shines in the online gaming world and has gained trust among enthusiasts.
Every visitor at https://donvinilo.es/uncategorized/taste-real-entertainment-at-crown-green-casino-now
is able to play the latest slots and benefit from rewarding offers. Crowngreen Casino provides reliable gameplay, smooth transactions, and 24/7 customer support for every player.
With , gamers unlock a huge selection of casino games, including jackpot options. The site prioritizes fun and maintains a safe gaming environment.
Whether you are experienced or an expert, Crowngreen Casino guarantees something special for everyone. Join at Crowngreen Casino today and discover exciting games, exclusive bonuses, and a reliable gaming environment.
Your comment is awaiting moderation.
What is mirror life? Scientists are sounding the alarm
https://top20.ua/dp/biznes-poslugi/yuridichni-poslugi/advokat-dnepr.html
адвокат
адвокат Запорожье цены
Scientist Kate Adamala doesn’t remember exactly when she realized her lab at the University of Minnesota was working on something potentially dangerous — so dangerous in fact that some researchers think it could pose an existential risk to all life forms on Earth.
She was one of four researchers awarded a $4 million US National Science Foundation grant in 2019 to investigate whether it’s possible to produce a mirror cell, in which the structure of all of its component biomolecules is the reverse of what’s found in normal cells.
The work was important, they thought, because such reversed cells, which have never existed in nature, could shed light on the origins of life and make it easier to create molecules with therapeutic value, potentially tackling significant medical challenges such as infectious disease and superbugs. But doubt crept in.
“It was never one light bulb moment. It was kind of a slow boiling over a few months,” Adamala, a synthetic biologist, said. People started asking questions, she added, “and we thought we can answer them, and then we realized we cannot.”
The questions hinged on what would happen if scientists succeeded in making a “mirror organism” such as a bacterium from molecules that are the mirror images of their natural forms. Could it inadvertently spread unchecked in the body or an environment, posing grave risks to human health and dire consequences for the planet? Or would it merely fizzle out and harmlessly disappear without a trace?
Your comment is awaiting moderation.
What is mirror life? Scientists are sounding the alarm
https://www.advokat-zp.best/ru/%D0%B2%D1%96%D0%B9%D1%81%D1%8C%D0%BA%D0%BE%D0%B2%D0%B8%D0%B9-%D0%B0%D0%B4%D0%B2%D0%BE%D0%BA%D0%B0%D1%82-%D1%83-%D0%B7%D0%B0%D0%BF%D0%BE%D1%80%D1%96%D0%B6%D0%B6%D1%96/
Военный адвокат Запорожье
Военный адвокат Запорожье
Scientist Kate Adamala doesn’t remember exactly when she realized her lab at the University of Minnesota was working on something potentially dangerous — so dangerous in fact that some researchers think it could pose an existential risk to all life forms on Earth.
She was one of four researchers awarded a $4 million US National Science Foundation grant in 2019 to investigate whether it’s possible to produce a mirror cell, in which the structure of all of its component biomolecules is the reverse of what’s found in normal cells.
The work was important, they thought, because such reversed cells, which have never existed in nature, could shed light on the origins of life and make it easier to create molecules with therapeutic value, potentially tackling significant medical challenges such as infectious disease and superbugs. But doubt crept in.
“It was never one light bulb moment. It was kind of a slow boiling over a few months,” Adamala, a synthetic biologist, said. People started asking questions, she added, “and we thought we can answer them, and then we realized we cannot.”
The questions hinged on what would happen if scientists succeeded in making a “mirror organism” such as a bacterium from molecules that are the mirror images of their natural forms. Could it inadvertently spread unchecked in the body or an environment, posing grave risks to human health and dire consequences for the planet? Or would it merely fizzle out and harmlessly disappear without a trace?
Your comment is awaiting moderation.
Светлана Меньшикова, 39 https://berezov-lsk.ru/
«Арт Стори»
от 300 000 ?
КП Яхрома парк, 20 соток https://berezov-lsk.ru/
Альпийская горка https://berezov-lsk.ru/
Создадим уникальный проект вашего сада с детальной 3D визуализацией и полным комплектом чертежей https://berezov-lsk.ru/
Your comment is awaiting moderation.
Hello! I sent a request but haven’t received a response yet. Please contact me via WhatsApp or by phone.
wa.me+380508607093
Your comment is awaiting moderation.
Свежий доступ к KRAKEN — вот здесь:
kraken зекрало
Работает на сегодня.
Если старый адрес не работает — заходи через запасной линк: https://kristi.su/threads/37
Обновлено сегодня.
Your comment is awaiting moderation.
Актуальный вход KRAKEN доступен тут:
кракен зайти
Если вход не работает, пользуйтесь зеркалом: https://anicore.ru/threads/1/.
Не требует VPN.
Проверено лично.
Your comment is awaiting moderation.
Кто жаловался, что не заходит KRAKEN?
Вот рабочая ссылка, только что проверил:
кракен онион
Если снова будет блокировка — вот резерв: https://anicore.ru/threads/1/.
Без VPN и редиректов.
Your comment is awaiting moderation.
Хай, комьюнити!
Кто ищет рабочий KRAKEN — держите рабочий линк ??
кракен магазин
Открывается моментально.
На случай блокировок — вот запасной вариант: https://kristi.su/threads/37
Добавьте в закладки.
Your comment is awaiting moderation.
Конструкции классифицируются по трем направлениям:
Для установки безрамных цельностеклянных зонирующих систем применяется зажимной профиль https://www.perof.ru/kak-my-rabotaem/tdts-kaluzhskiy-stan-g-troitsk/
Перегородки на алюминиевом каркасе с вертикальными стойками https://www.perof.ru/news/mobilnye-peregorodki-funktsionalnyy-i-ekonomichnyy-variant-dlya-bystrogo-obustroystva-privatnykh-rab/
В качетсве материала заполнения используется 1-ое или 2-ое стекло, нередко в конструкциях испозуется комбинированный тип заполнения, например: ЛДСП + стекло https://www.perof.ru/news/my-mozhem-polnostyu-obustroit-bank-s-pomoshchyu-peregorodok-perof-mobilnye-resheniya-dlya-klientskoy/
“Первый Бит” это группа компаний в которую входят 1С и Bitrix24 https://www.perof.ru/glossariy/generalnyy-proektirovshchik/
Больше 20 лет занимается автоматизацией бизнеса и разработкой собственных IT-решений https://www.perof.ru/news/ofisnye-peregorodki-chasto-ispolzuyut-dlya-zonirovaniya-uchebnykh-zavedeniy-mozhno-bystro-i-krasivo-/
В 2018 году https://www.perof.ru/kak-my-rabotaem/tts-rts-na-volochaevskoy/
Вы отправляете заявку https://www.perof.ru/catalog/ofisnye-peregorodki/mobilnye-ofisnye-peregorodki/
от 1580 р https://www.perof.ru/news/kombinirovannye-peregorodki-dlya-kompanii-r-svyaz-v-bts-vereyskaya-plaza-glukhoy-nizhniy-impost-do-2/
/м2 https://www.perof.ru/news/my-sozdali-obemnoe-peregovornoe-prostranstvo-iz-neskolkikh-komnat-dlya-gigantskogo-ofisa-open-space-/
Your comment is awaiting moderation.
Кому нужен актуальный доступ к KRAKEN — вот зеркало
кракен зекрало
Загружается стабильно.
Резервный адрес на случай блокировок: https://kristi.su/threads/37
Использую ежедневно.
Your comment is awaiting moderation.
Всем привет!
Для тех, кто ищет доступ к KRAKEN — держите свежий линк ??
kraken даркнет
С любого устройства.
На случай блокировок — вот запасной вариант: https://kristi.su/threads/37
Проверено лично — всё ок.
Your comment is awaiting moderation.
Хай, комьюнити!
Когда заблокировали KRAKEN — держите проверенный линк ??
kraken зайти
Открывается моментально.
Если вдруг старый сайт не грузится — вот запасной вариант: https://kristi.su/threads/37
Сохраняйте.
Your comment is awaiting moderation.
BMW 335d (E90): A popular sedan known for its powerful inline-6 diesel engine. It was a favorite among enthusiasts.
deadbeautygameplay.com
http://technosoul.ru/grfdfsdv/AbkCzLPkpI.html
http://technosoul.ru/grfdfsdv/BEHpvaTSxS.html
http://technosoul.ru/grfdfsdv/braQdqEuRu.html
http://technosoul.ru/grfdfsdv/cAYMvteCgO.html
http://technosoul.ru/grfdfsdv/cZkVoqggbr.html
http://technosoul.ru/grfdfsdv/CZurTUHkat.html
http://technosoul.ru/grfdfsdv/FVhMacgdeb.html
http://technosoul.ru/grfdfsdv/fvlktJcmZl.html
http://technosoul.ru/grfdfsdv/hdOHIplNWK.html
http://technosoul.ru/grfdfsdv/IwzvDeylYf.html
http://technosoul.ru/grfdfsdv/LHcCfsemuF.html
http://technosoul.ru/grfdfsdv/nSRSJBwcUz.html
http://technosoul.ru/grfdfsdv/OBmcFhyAvh.html
http://technosoul.ru/grfdfsdv/OWWPdYmpTT.html
http://technosoul.ru/grfdfsdv/oZWxmdjpay.html
http://technosoul.ru/grfdfsdv/pRukzlmQch.html
http://technosoul.ru/grfdfsdv/pwhLFuxyer.html
http://technosoul.ru/grfdfsdv/QPdQIqorzE.html
http://technosoul.ru/grfdfsdv/QpeSAtQneH.html
http://technosoul.ru/grfdfsdv/RTBEYrdtZC.html
http://technosoul.ru/grfdfsdv/sbBlQHShKg.html
http://technosoul.ru/grfdfsdv/ShgiGzczJG.html
http://technosoul.ru/grfdfsdv/suRNFCamKN.html
http://technosoul.ru/grfdfsdv/UlqMPJgSdX.html
http://technosoul.ru/grfdfsdv/uPubAUhhCM.html
http://technosoul.ru/grfdfsdv/VeeIVnTJDC.html
http://technosoul.ru/grfdfsdv/VTyBQkbvjx.html
http://technosoul.ru/grfdfsdv/wSwBWVgPLZ.html
http://technosoul.ru/grfdfsdv/WxYOkDdKig.html
http://technosoul.ru/grfdfsdv/YIYKdaBPAE.html
http://kbgtk.ru/grfdfsdv/AbkCzLPkpI.html
http://kbgtk.ru/grfdfsdv/BEHpvaTSxS.html
http://kbgtk.ru/grfdfsdv/braQdqEuRu.html
http://kbgtk.ru/grfdfsdv/cAYMvteCgO.html
http://kbgtk.ru/grfdfsdv/cZkVoqggbr.html
http://kbgtk.ru/grfdfsdv/CZurTUHkat.html
http://kbgtk.ru/grfdfsdv/FVhMacgdeb.html
http://kbgtk.ru/grfdfsdv/fvlktJcmZl.html
http://kbgtk.ru/grfdfsdv/hdOHIplNWK.html
http://kbgtk.ru/grfdfsdv/IwzvDeylYf.html
http://kbgtk.ru/grfdfsdv/LHcCfsemuF.html
http://kbgtk.ru/grfdfsdv/nSRSJBwcUz.html
http://kbgtk.ru/grfdfsdv/OBmcFhyAvh.html
http://kbgtk.ru/grfdfsdv/OWWPdYmpTT.html
http://kbgtk.ru/grfdfsdv/oZWxmdjpay.html
http://kbgtk.ru/grfdfsdv/pRukzlmQch.html
http://kbgtk.ru/grfdfsdv/pwhLFuxyer.html
http://kbgtk.ru/grfdfsdv/QPdQIqorzE.html
http://kbgtk.ru/grfdfsdv/QpeSAtQneH.html
http://kbgtk.ru/grfdfsdv/RTBEYrdtZC.html
http://kbgtk.ru/grfdfsdv/sbBlQHShKg.html
http://kbgtk.ru/grfdfsdv/ShgiGzczJG.html
http://kbgtk.ru/grfdfsdv/suRNFCamKN.html
http://kbgtk.ru/grfdfsdv/UlqMPJgSdX.html
http://kbgtk.ru/grfdfsdv/uPubAUhhCM.html
http://kbgtk.ru/grfdfsdv/VeeIVnTJDC.html
http://kbgtk.ru/grfdfsdv/VTyBQkbvjx.html
http://kbgtk.ru/grfdfsdv/wSwBWVgPLZ.html
http://kbgtk.ru/grfdfsdv/WxYOkDdKig.html
http://kbgtk.ru/grfdfsdv/YIYKdaBPAE.html
http://redmeh.ru/grfdfsdv/AbkCzLPkpI.html
http://redmeh.ru/grfdfsdv/BEHpvaTSxS.html
http://redmeh.ru/grfdfsdv/braQdqEuRu.html
http://redmeh.ru/grfdfsdv/cAYMvteCgO.html
http://redmeh.ru/grfdfsdv/cZkVoqggbr.html
http://redmeh.ru/grfdfsdv/CZurTUHkat.html
http://redmeh.ru/grfdfsdv/FVhMacgdeb.html
http://redmeh.ru/grfdfsdv/fvlktJcmZl.html
http://redmeh.ru/grfdfsdv/hdOHIplNWK.html
http://redmeh.ru/grfdfsdv/IwzvDeylYf.html
http://redmeh.ru/grfdfsdv/LHcCfsemuF.html
http://redmeh.ru/grfdfsdv/nSRSJBwcUz.html
http://redmeh.ru/grfdfsdv/OBmcFhyAvh.html
http://redmeh.ru/grfdfsdv/OWWPdYmpTT.html
http://redmeh.ru/grfdfsdv/oZWxmdjpay.html
http://redmeh.ru/grfdfsdv/pRukzlmQch.html
http://redmeh.ru/grfdfsdv/pwhLFuxyer.html
http://redmeh.ru/grfdfsdv/QPdQIqorzE.html
http://redmeh.ru/grfdfsdv/QpeSAtQneH.html
http://redmeh.ru/grfdfsdv/RTBEYrdtZC.html
http://redmeh.ru/grfdfsdv/sbBlQHShKg.html
http://redmeh.ru/grfdfsdv/ShgiGzczJG.html
http://redmeh.ru/grfdfsdv/suRNFCamKN.html
http://redmeh.ru/grfdfsdv/UlqMPJgSdX.html
http://redmeh.ru/grfdfsdv/uPubAUhhCM.html
http://redmeh.ru/grfdfsdv/VeeIVnTJDC.html
http://redmeh.ru/grfdfsdv/VTyBQkbvjx.html
http://redmeh.ru/grfdfsdv/wSwBWVgPLZ.html
http://redmeh.ru/grfdfsdv/WxYOkDdKig.html
http://redmeh.ru/grfdfsdv/YIYKdaBPAE.html
http://zelenyi-mir.ru/grfdfsdv/AbkCzLPkpI.html
http://zelenyi-mir.ru/grfdfsdv/BEHpvaTSxS.html
http://zelenyi-mir.ru/grfdfsdv/braQdqEuRu.html
http://zelenyi-mir.ru/grfdfsdv/cAYMvteCgO.html
http://zelenyi-mir.ru/grfdfsdv/cZkVoqggbr.html
http://zelenyi-mir.ru/grfdfsdv/CZurTUHkat.html
http://zelenyi-mir.ru/grfdfsdv/FVhMacgdeb.html
http://zelenyi-mir.ru/grfdfsdv/fvlktJcmZl.html
http://zelenyi-mir.ru/grfdfsdv/hdOHIplNWK.html
http://zelenyi-mir.ru/grfdfsdv/IwzvDeylYf.html
http://zelenyi-mir.ru/grfdfsdv/LHcCfsemuF.html
http://zelenyi-mir.ru/grfdfsdv/nSRSJBwcUz.html
http://zelenyi-mir.ru/grfdfsdv/OBmcFhyAvh.html
http://zelenyi-mir.ru/grfdfsdv/OWWPdYmpTT.html
http://zelenyi-mir.ru/grfdfsdv/oZWxmdjpay.html
http://zelenyi-mir.ru/grfdfsdv/pRukzlmQch.html
http://zelenyi-mir.ru/grfdfsdv/pwhLFuxyer.html
http://zelenyi-mir.ru/grfdfsdv/QPdQIqorzE.html
http://zelenyi-mir.ru/grfdfsdv/QpeSAtQneH.html
http://zelenyi-mir.ru/grfdfsdv/RTBEYrdtZC.html
http://zelenyi-mir.ru/grfdfsdv/sbBlQHShKg.html
http://zelenyi-mir.ru/grfdfsdv/ShgiGzczJG.html
http://zelenyi-mir.ru/grfdfsdv/suRNFCamKN.html
http://zelenyi-mir.ru/grfdfsdv/UlqMPJgSdX.html
http://zelenyi-mir.ru/grfdfsdv/uPubAUhhCM.html
http://zelenyi-mir.ru/grfdfsdv/VeeIVnTJDC.html
http://zelenyi-mir.ru/grfdfsdv/VTyBQkbvjx.html
http://zelenyi-mir.ru/grfdfsdv/wSwBWVgPLZ.html
http://zelenyi-mir.ru/grfdfsdv/WxYOkDdKig.html
http://zelenyi-mir.ru/grfdfsdv/YIYKdaBPAE.html
https://solend.ru/grfdfsdv/AbkCzLPkpI.html
https://solend.ru/grfdfsdv/BEHpvaTSxS.html
https://solend.ru/grfdfsdv/braQdqEuRu.html
https://solend.ru/grfdfsdv/cAYMvteCgO.html
https://solend.ru/grfdfsdv/cZkVoqggbr.html
https://solend.ru/grfdfsdv/CZurTUHkat.html
https://solend.ru/grfdfsdv/FVhMacgdeb.html
https://solend.ru/grfdfsdv/fvlktJcmZl.html
https://solend.ru/grfdfsdv/hdOHIplNWK.html
https://solend.ru/grfdfsdv/IwzvDeylYf.html
https://solend.ru/grfdfsdv/LHcCfsemuF.html
https://solend.ru/grfdfsdv/nSRSJBwcUz.html
https://solend.ru/grfdfsdv/OBmcFhyAvh.html
https://solend.ru/grfdfsdv/OWWPdYmpTT.html
https://solend.ru/grfdfsdv/oZWxmdjpay.html
https://solend.ru/grfdfsdv/pRukzlmQch.html
https://solend.ru/grfdfsdv/pwhLFuxyer.html
https://solend.ru/grfdfsdv/QPdQIqorzE.html
https://solend.ru/grfdfsdv/QpeSAtQneH.html
https://solend.ru/grfdfsdv/RTBEYrdtZC.html
https://solend.ru/grfdfsdv/sbBlQHShKg.html
https://solend.ru/grfdfsdv/ShgiGzczJG.html
https://solend.ru/grfdfsdv/suRNFCamKN.html
https://solend.ru/grfdfsdv/UlqMPJgSdX.html
https://solend.ru/grfdfsdv/uPubAUhhCM.html
https://solend.ru/grfdfsdv/VeeIVnTJDC.html
https://solend.ru/grfdfsdv/VTyBQkbvjx.html
https://solend.ru/grfdfsdv/wSwBWVgPLZ.html
https://solend.ru/grfdfsdv/WxYOkDdKig.html
https://solend.ru/grfdfsdv/YIYKdaBPAE.html
https://tak-stroy.ru/grfdfsdv/AbkCzLPkpI.html
https://tak-stroy.ru/grfdfsdv/BEHpvaTSxS.html
https://tak-stroy.ru/grfdfsdv/braQdqEuRu.html
https://tak-stroy.ru/grfdfsdv/cAYMvteCgO.html
https://tak-stroy.ru/grfdfsdv/cZkVoqggbr.html
https://tak-stroy.ru/grfdfsdv/CZurTUHkat.html
https://tak-stroy.ru/grfdfsdv/FVhMacgdeb.html
https://tak-stroy.ru/grfdfsdv/fvlktJcmZl.html
https://tak-stroy.ru/grfdfsdv/hdOHIplNWK.html
https://tak-stroy.ru/grfdfsdv/IwzvDeylYf.html
https://tak-stroy.ru/grfdfsdv/LHcCfsemuF.html
https://tak-stroy.ru/grfdfsdv/nSRSJBwcUz.html
https://tak-stroy.ru/grfdfsdv/OBmcFhyAvh.html
https://tak-stroy.ru/grfdfsdv/OWWPdYmpTT.html
https://tak-stroy.ru/grfdfsdv/oZWxmdjpay.html
https://tak-stroy.ru/grfdfsdv/pRukzlmQch.html
https://tak-stroy.ru/grfdfsdv/pwhLFuxyer.html
https://tak-stroy.ru/grfdfsdv/QPdQIqorzE.html
https://tak-stroy.ru/grfdfsdv/QpeSAtQneH.html
https://tak-stroy.ru/grfdfsdv/RTBEYrdtZC.html
https://tak-stroy.ru/grfdfsdv/sbBlQHShKg.html
https://tak-stroy.ru/grfdfsdv/ShgiGzczJG.html
https://tak-stroy.ru/grfdfsdv/suRNFCamKN.html
https://tak-stroy.ru/grfdfsdv/UlqMPJgSdX.html
https://tak-stroy.ru/grfdfsdv/uPubAUhhCM.html
https://tak-stroy.ru/grfdfsdv/VeeIVnTJDC.html
https://tak-stroy.ru/grfdfsdv/VTyBQkbvjx.html
https://tak-stroy.ru/grfdfsdv/wSwBWVgPLZ.html
https://tak-stroy.ru/grfdfsdv/WxYOkDdKig.html
https://tak-stroy.ru/grfdfsdv/YIYKdaBPAE.html
Your comment is awaiting moderation.
seo agents http://www.reiting-seo-kompaniy.ru .
Your comment is awaiting moderation.
Проверенное зеркало KRAKEN — вот здесь:
кракен тор
Без сбоев.
Если основное зеркало не открылось — заходи через запасной линк: https://kristi.su/threads/37
Обновлено сегодня.
Your comment is awaiting moderation.
Свежий доступ к KRAKEN — вот здесь:
кракен даркнет
Без сбоев.
Если основное зеркало не открылось — заходи через запасной линк: https://kristi.su/threads/37
Обновлено сегодня.
Your comment is awaiting moderation.
Проверенное зеркало KRAKEN — вот здесь:
kraken даркнет
Без блокировок.
Если старый адрес не работает — заходи через запасной линк: https://kristi.su/threads/37
Удобно, быстро, безопасно.
Your comment is awaiting moderation.
Для тех, кто спрашивал актуальный доступ к KRAKEN — вот ссылка
kraken официальный
Открывается без ограничений.
Резервный адрес на случай блокировок: https://kristi.su/threads/37
Переходите без опасений.
Your comment is awaiting moderation.
Всем привет!
Для тех, кто ищет доступ к KRAKEN — держите проверенный линк ??
кракен маркет
С любого устройства.
Если основное зеркало недоступно — вот запасной вариант: https://kristi.su/threads/37
Проверено лично — всё ок.
Your comment is awaiting moderation.
“Tempting tease longs for ecstasy.” Click Here \u003e rb.gy/34p7i3?stype
Your comment is awaiting moderation.
1.
¡Descubre Retabet Perú!
Tu portal de apuestas deportivas y casino online con las mejores cuotas, juegos y bonos de bienvenida. ¡Regístrate y gana hoy! https://www.wikidot.com/user:info/retabets
2.
Apuesta con Retabet Perú
Las mejores apuestas deportivas en línea y juegos de casino online te esperan. Vive la emoción en cada jugada. https://www.weddingbee.com/members/retabets/
3.
Casino online Perú con Retabet
Disfruta de los mejores juegos de casino, tragamonedas y casino en vivo desde casa. Bonos exclusivos para nuevos usuarios. https://gravatar.com/retabets
4.
Retabet Apuestas Perú
Haz tus apuestas deportivas con total seguridad y las mejores cuotas del mercado. ¡Apuesta y gana en tus deportes favoritos! https://www.pexels.com/@retabets-pe-2156671339/
5.
Bonos de bienvenida en Retabet Perú
Aprovecha promociones únicas en apuestas deportivas y casino online. Empieza con ventaja y multiplica tus ganancias. https://freeicons.io/profile/840608
Your comment is awaiting moderation.
The Dog House Megaways slot review wouldn’t be complete without touching on the bonuses. There are ten different features in the slot, most of which are activated randomly. Amaya Gaming, best roxor gaming online casinos free spins with 3x coefficient and other numerous bonuses. Wonky wabbit is a game which offers players the chances of winning big only if they are patient enough, which means you can play between 1 – 10 pay lines. What is the maximum payout in The Dog House Megaways? The potential max win for The Dog House Megaways Slot comes in at 12,305x your total stake (or “max bet”) per spin or free spin. The maximum win (or “max win”) is the highest possible win you could walk away with when playing this online slot. With a 20p bet, you have the chance to win a grand prize of £2,461.
http://vrenta.mx/in-depth-review-colour-trading-by-tadagaming-for-pakistani-players/
Then again, The Dog House Royal Hunt’s cap isn’t much greater than The Dog House’s max win of 6,750x, which might be slightly disappointing for players who have their eyes on royal free spins, where wild symbols can have much greater multipliers on them. Especially considering royal free spins cost a not insignificant 500x the bet to buy and cannot be triggered organically. Add it up, and you’ve got an entertaining sticky wild multiplier Dog House slot, but maybe one with more entertainment value for deep-pocketed bonus buyers – others might have wanted more from a new DH slot than bigger multiplier values that you have to pay for. pragmatic playonline slot gameegyptian fortunesthe dog house Yes, it is. We reviewed The Dog House: Dog or Alive slot in detail before deeming it safe to play. Be sure to sign up to a secure online casino to get started the right way.
Your comment is awaiting moderation.
Crowngreen Casino is a leading entertainment site that delivers thrilling slots for users. Crowngreen Casino stands out in the online gaming world and has achieved reputation among gamers.
Every user at Crowngreen
has the chance to enjoy top-rated slots and receive rewarding bonuses. Crowngreen Casino ensures reliable gameplay, smooth transactions, and constant customer support for all users.
With , gamers unlock a diverse range of table games, including classic options. The site prioritizes user satisfaction and maintains a safe gaming environment.
Whether you are experienced or a pro, Crowngreen provides something special for everyone. Start playing at Crowngreen today and discover rewarding games, fantastic bonuses, and a safe gaming environment.
Your comment is awaiting moderation.
Актуальное KRAKEN зеркало позволяет пользоваться кракен ссылка.
Your comment is awaiting moderation.
KRAKEN кракен тор официальный сайт всегда публикует актуальные ссылки кракен даркнет. Рабочее зеркало помогает войти.
Your comment is awaiting moderation.
KRAKEN снова доступен!
Переходите по ссылке: кракен автобус
Если старый домен заблокирован — пользуйтесь зеркалом: https://kristi.su/threads/37
Поддерживает вход без VPN.
Не потеряй актуальный адрес.
Your comment is awaiting moderation.
Актуальный вход в KRAKEN — вот здесь:
кракен маркетплейс
С любого устройства.
Если старый адрес не работает — заходи через запасной линк: https://kristi.su/threads/37
Обновлено сегодня.
Your comment is awaiting moderation.
KRAKEN сайт предлагает проверенные способы обхода блокировок. Вход возможен всегда через кракен зеркало.
Your comment is awaiting moderation.
Рабочее кракен маркетплейсделает вход простым. Ссылки проверены и помогают авторизоваться без рисков.
Your comment is awaiting moderation.
Привет всем!
Для тех, кто ищет доступ к KRAKEN — держите свежий линк ??
кракен зекрало
Работает стабильно.
Если вдруг старый сайт не грузится — вот запасной вариант: https://kristi.su/threads/37
Использую сам, всё работает.
Your comment is awaiting moderation.
darknet markets tor https://github.com/topics/dark-web-monitoring-services
darkweb market https://github.com/topics/darknet-market-phishing-scams
darknet markets original https://github.com/topics/onion-markets-list
darknet market exit scam history https://github.com/topics/payments-cryptocurrency-guide-darknet
darknet online shops https://github.com/topics/market-protection-with-escrow-darknet
Your comment is awaiting moderation.
Актуальное зеркало KRAKEN!
Переходите по ссылке: kraken магазин
Если не грузится сайт — пользуйтесь зеркалом: https://kristi.su/threads/37
Сайт работает.
Сохрани ссылку.
Your comment is awaiting moderation.
Чтобы открыть маркетплейс, воспользуйтесь KRAKEN зеркало. Актуальная кракен онионбезопасна и подходит для любых устройств.
Your comment is awaiting moderation.
Официальное кракен тор зеркало подходит для любых устройств.
Your comment is awaiting moderation.
Рабочий сайт KRAKEN найден!
Переходите по ссылке: kraken зайти
Если не грузится сайт — пользуйтесь зеркалом: https://kristi.su/threads/37
Поддерживает вход без VPN.
Добавь в закладки.
Your comment is awaiting moderation.
Чтобы открыть маркетплейс, воспользуйтесь KRAKEN зеркало. Актуальная
безопасна и подходит для любых устройств.
Your comment is awaiting moderation.
KRAKEN кракен магазин— это безопасный способ войти через TOR. Рабочая ссылка позволяет подключиться анонимно и пользоваться маркетплейсом.
Your comment is awaiting moderation.
Рабочее зеркало
позволяет пользоваться маркетом без ограничений.
Your comment is awaiting moderation.
Чтобы открыть кракен сайт, используйте KRAKEN ссылка. Рабочее зеркало помогает избежать блокировок.
Your comment is awaiting moderation.
Beispielsweise besagt eine Casino Auszahlungsquote von 96 % in Top 15 Online Casinos, dass von 100 Euro, die an einem Online Spielautomaten eingesetzt wurden, mindestens 96 Euro wieder als Gewinn an Casino Spieler in einem Online Casino in Deutschland ausgeschüttet werden. Kreativität, Kunstfertigkeit, Mathematik und Wissenschaft kommen zusammen, wenn es darum geht, Slots zu entwerfen. Jedes Jahr im Herbst versammeln sich die Hersteller auf der Global Gaming Expo in Las Vegas, um ihre neuesten Ideen vorzustellen. Spiele werden so gestaltet, dass sie den Spielern „Spiel mich!“ zurufen, während sie den Casino-Betreibern „Kauf mich!“ signalisieren. Spiele Top Slots mit beeindruckenden RTPs, profitiere von starken Freispiel-Boni und messe dich mit anderen Spielern in Duellen um Freispiel-Preise.
https://fuelpumpexpress.com/boomerang-casino-deutschland-schnelle-auszahlungen-und-top-spielerlebnis/
X-iter – Pirots X bietet den Spielern mehrere Kaufoptionen, um das Gameplay zu verbessern: Alle Netent Spielautomaten ➡️ Die Symbole im Pirots 4 Slot bestehen aus verschiedenen bunten Vögeln, Juwelen und Spezial-Icons. Hochwertige Symbole sind die roten und blauen Pirots, während die grünen und gelben Vögel mittlere Werte haben. Niedrigwertige Symbole sind die Edelsteine, die zwar häufiger erscheinen, aber geringere Gewinne bringen. Ein spezielles Wild-Symbol ersetzt andere Symbole in einem Cluster und erhöht so die Gewinnchancen. Scatter-Symbole sind der Schlüssel zum Freischalten von Freispielen, die wiederum zusätzliche Features aktivieren können. Eine vollständige Auszahlungstabelle ist im Spielmenü einsehbar und gibt einen detaillierten Überblick über die Multiplikatoren.
Your comment is awaiting moderation.
KRAKEN сайт — это надёжный источник для входа на кракен онион.
Your comment is awaiting moderation.
KRAKEN сайт — это платформа, где всегда доступны зеркала и
. Вход возможен даже через TOR и онион.
Your comment is awaiting moderation.
KRAKEN ссылка позволяет обходить блокировки и заходить на сайт даже с телефона. Рабочее зеркало — гарантия стабильного входа.
Your comment is awaiting moderation.
Чтобы не терять доступ, сохраняйте актуальную KRAKEN ссылка. Рабочее зеркало кракен онион открывает маркет и личный кабинет.
Your comment is awaiting moderation.
Crowngreen is a trusted gaming platform that offers engaging slots for users. Crowngreen excels in the online gaming world and has achieved trust among enthusiasts.
Every player at Crowngreen
can play the latest slots and receive exciting offers. Crowngreen ensures secure gameplay, seamless transactions, and constant customer support for every gamer.
With , players discover a wide range of table games, including live dealer options. The casino delivers user satisfaction and ensures a safe gaming environment.
Whether you are experienced or an expert, Crowngreen provides unique experiences for everyone. Join at Crowngreen Casino today and experience rewarding games, generous bonuses, and a fun gaming environment.
Your comment is awaiting moderation.
KRAKEN сайт помогает сохранять доступность ресурса. Достаточно перейти по актуальной ссылке или кракен маркетплейс.
Your comment is awaiting moderation.
С помощью кракен тор легко продолжить покупки.
Your comment is awaiting moderation.
KRAKEN официальный сайт всегда снабжён инструкциями для пользователей. Рабочая кракен сайтгарантирует доступ в личный кабинет без проблем.
Your comment is awaiting moderation.
Here’s a closer look at what players can experience with the Gates of Olympus online slot. Stake definitely deserves a spot on your list of Bitcoin gambling sites. This legit Bitcoin gambling site appeals to both sports bettors and casino players, offering something for everyone. Instead of a standard welcome bonus, players can take part in daily and weekly raffles as well as frequent giveaways. As one of the most trusted Bitcoin casinos, Stake also features a strong collection of exclusive games — 44 in total. If you prefer to stick with well-known software providers, the platform makes it easy to filter titles. Pragmatic Play, iSoftBet, Belatra, Endorphina, and Play’n GO are among the leading names, alongside many others worth exploring. Ever wondered what happens when Zeus gets festive? The Gates of Olympus X-mas 1000 slot game brings the same explosive features from the 1000 edition, but wraps them in a holiday-themed wonderland.
https://elifetech.vn/astronaut-crash-game-by-100hp-gaming-a-review-for-indian-players/
Flourpower Pragmatic Play has a lot of expertise in bingo and casino table games, but it also offers an excellent range of modern slot games to its customers. With great aesthetics throughout and an impressive selection of bonus features, Pragmatic slots score highly among players. Check this top 5 slot games that have taken the Filipino streaming community on Facebook enjoy slot game. With the rise of online casino and the vibrant presence of Filipino streamers, these games have become fan favorites, offering thrilling gameplay, stunning graphics, and the chance to hit that big win. Whether you’re a seasoned player or a newcomer looking for some fun, these slot games are sure to keep you entertained. Let’s Check and see the top 5 slot games that are captivating audiences and why they’ve become the top picks among Filipino streamers.
Your comment is awaiting moderation.
©2025 Hearst UK is the trading name of the National Magazine Company Ltd, 30 Panton Street, Leicester Square, London, SW1Y 4AJ. Registered in England 112955. All Rights Reserved. Check your inbox or spam folder to confirm your subscription. Jam Gacor: 05.55 – 08.25 WIB 17.50 – 20.40 WIB O mistress … of the gods … inscrutable (light) … first-born (in) mist (or heaven) … Erôs willed, when (Night) … and was nurtured then … family of gods …[88] The coin isn’t the only part of the underworld Kaos got right. Caeneus’s three-headed dog, Fotis, is a Cerebus. In Greek myth, there was only one Cerebus, a gnarly beast referred to as the Hound of Hades or the Hell-Hound. Cerebus had “a serpent for a tail and along his back the heads of all kinds of snakes.” Hesiod described his duties in his Theogony:
https://storyangels.es/how-to-play-vortex-game-beginners-guide/
Gameworld este deținut și operat integral de Megabet International SRL cu sediul în România, București, Bd. Tudor Vladimirescu, Nr. 29A, AFI Tech Park 1, Etaj 5, și capital social de 11.000.000 LEI. Les bonus sans dépôt : ces offres vous permettent de jouer et de remporter de l’argent réel sur les casinos. Elles vous sont attribuées sans que vous ayez crédité au préalable votre compte. Cependant, pour être éligible à ce type d’offre, vous devez vous inscrire. Par ailleurs, les bonus sans dépôt se présentent sous plusieurs formes (argent gratuit, tours gratuits et remises en argent). Gates of Olympus Xmas 1000 has a big play space with six reels of five rows each. Unusually, all the main symbols function as scatters. Wins are generated simply by landing eight or more symbols (or four or more in the case of the Bonus symbol).
Your comment is awaiting moderation.
Note: If you like Gates of Olympus, you can play other similar slots in demo mode on Temple of Games. Try other casino games from Pragmatic Play, other free online slots, or other Mythology-themed casino games. SugarVille 1000 DOWNLOAD H&M APP Put your ego aside and go forward toward your missing of making an impact regardless of what other people say. There is a huge selection of gaming sites offering Pragmatic slots, enough to satisfy even the most demanding gamblers. But apart from choosing a legitimate, safe, and fair casino, you have another job on your hands, which is checking slot RTPs. Note that the average return to play generally varies from one site to another. Gates of Olympus oyna seçeneğiyle, oyuncular Zeus’un gücünü keşfederken yüksek kazançlar elde edebilirler. Oyun, üstün grafik kalitesi ve dinamik oynanış özellikleri ile dikkat çeker.
https://fotopani.rs/660/vortex-by-turbo-games-an-in-depth-review-for-players-from-pakistan/
The Tumble Feature ensures a dynamic experience—winning symbols disappear, allowing new ones to drop in their place for potential chain reactions. Meanwhile, multiplier symbols with values between 2x and 1,000x can appear at any time, boosting your win totals during tumbling sequences. Uncommon analytics are of those which might be additional particular range that we think getting normal. Flagged stats are usually the consequence of a limited amount of spins having been played for the a-game, however, this is not usually the way it is. Both, also games having a huge number of tracked spins provides flagged stats. In summary, the mechanics are matched across both games—scatter pays on a 6×5 grid, tumbling sequences, random multiplier symbols that sum and apply, and a free spins feature with a persistent multiplier. The two points of differentiation are quantifiable: return-to-player percentage and the top visible multiplier value. Players moving from Gates of Olympus to Gates of Olympus 1000 will not learn new rules; instead, they’ll notice that the updated version nudges the underlying math toward slightly higher theoretical return and rarer yet higher ceiling moments tied to multiplier drops.
Your comment is awaiting moderation.
KRAKEN официальный сайт поддерживает зеркала для обхода блокировок. Вход через кракен тор выполняется моментально.
Your comment is awaiting moderation.
KRAKEN сайт всегда содержит актуальные способы входа на кракен официальный сайт
.
Your comment is awaiting moderation.
\u201CAt its very heart it\u2019s about understanding the world around me. Once you make things and work with the land you start to learn about it and your relationship with it. Nature for me isn\u2019t just outside the city, it\u2019s everywhere. It\u2019s such a powerful thing nature. And to have an art that actually opens your eyes and mind to what\u2019s there, shows me what\u2019s there, is quite amazing. Instead of art being this means of expressing yourself, it\u2019s been a way of understanding.\u201D – Goldsworthy. “I upgraded my SVGator plan to PRO! The support and thoroughness (diving into one of my own personal WordPress sites to help solve a problem for me) really impressed and convinced me to switch to a yearly plan and stick with it. Keep up the amazing support! I have fallen in love with SVGator.”
https://coralbluehomes.com/plinko-by-bgaming-a-uk-players-review-of-the-exciting-casino-game/
Keep an eye on in-cabinet multipliers and how they stack during free spins — that’s the engine that turns routine runs into headline wins. If your platform is running a short-term promotion or boosted spins package for this title, act fast; those limited-time boosts can amplify your return on a lucky session. Maybe you have viewed Disney’s Hercules and you may ask yourself what it might possibly be desire to level the fresh levels away from Attach Olympus and stay face-to-face that have the new mighty Zeus? Doorways of Olympus try a top volatility position game on the are already aware of creators Pragmatic Enjoy! From the spread out-pays system for the grand multipliers, the game and its own following iterations has had the web gambling establishment world from the storm while the their discharge. Although not, if you wish to try the fortune i also provide particular of the very trusted casinos currently available!
Your comment is awaiting moderation.
Online and offline gambling is strictly prohibited for individuals who have not yet reached the age of majority, typically 18 years old. Additionally, gambling can be highly addictive, and if you find that you have an uncontrollable urge to gamble, you must seek help from one of the many gambling addiction centers available. The catalog is lean (just over 150 games, including crash gambling) and built around proven anchors like 777, Achilles Deluxe, and 5 Wishes. If you’re chasing multiplier ladders, Gates of Olympus demo is usually available: try the Gates of Olympus demo to learn its tumble cycles and pacing, then move to the Gates of Olympus online slot. The Gates of Olympus slot fits short sessions or longer grinds without feeling clunky. After several such updates, orange and yellow colour. Just like all games by Urgent Play Puppy is made with the use of HTML5 technology, these sites get a big old thumbs down from us. Gates of olympus casino jackpot win for players who would rather use an e-wallet, a Washington-based team.
https://arabpack.org/casino-slots/sugar-rush-1000-an-exciting-pragmatic-play-slot-experience/
To embed a YouTube video in Google Slides, go to Insert -> Video -> YouTube and paste the video URL. Alternatively, you can also select a video from Google Drive to embed into your slide. Once the video is embedded, use drag-and-drop to resize and reposition the player as needed. The Format Options sidebar can help you further customize the embedded video by allowing you to set playback options, such as triggering the video to play (e.g., on mouse click), setting the start and end times, and muting the audio. You can also use this sidebar to set the size and position, rotate the video, and add a drop shadow. 100+ Extempore Topics for Students with Tips to Speak Confidently Here’s an example slides animation from history (click here to open the Google Slides file): the start of the Battle of Little Big Horn. This one is pretty rudimentary, but by doing that, it can be created pretty quickly. This one was done in a matter of minutes!
Your comment is awaiting moderation.
Crowngreen is a leading entertainment site that offers exciting slots for players. Crowngreen shines in the online gaming world and has achieved popularity among enthusiasts.
Every visitor at https://likememore.net/spin-the-reels-at-crowngreen-casino-and-win-big-2/
can play the latest slots and benefit from generous offers. Crowngreen Casino ensures secure gameplay, smooth transactions, and constant customer support for every player.
With , gamers unlock a huge variety of casino games, including live dealer options. The platform delivers fun and ensures a secure gaming environment.
Whether you are experienced or experienced, Crowngreen Casino offers something special for everyone. Sign up at Crowngreen today and experience thrilling games, generous bonuses, and a reliable gaming environment.
Your comment is awaiting moderation.
What’s good, folks?
Just dropping by to share a super informative article about market analysis.
It covers major updates in Web3 & DeFi projects.
Worth checking out, especially if you follow charts.
Take a look
Your comment is awaiting moderation.
Crowngreen is a leading online casino that provides exciting slots for users. Crowngreen Casino stands out in the online gaming world and has earned trust among visitors.
Every player at https://2bscargoegypt.com/discover-crowngreen-casino-and-enjoy-exclusive/
has the chance to experience exclusive tournaments and receive exciting promotions. Crowngreen guarantees secure gameplay, fast transactions, and 24/7 customer support for every gamer.
With , players discover a huge variety of table games, including jackpot options. The casino focuses on fun and guarantees an enjoyable gaming environment.
Whether you are new or a pro, Crowngreen guarantees something special for everyone. Join at Crowngreen today and discover thrilling games, generous bonuses, and a reliable gaming environment.
Your comment is awaiting moderation.
1win Mexico: La Mejor Plataforma de Apuestas
Descubre todo lo que necesitas saber sobre 1win Mexico, la plataforma de apuestas en linea mas confiable y popular del pais. Ofrece una amplia gama de opciones para jugadores mexicanos. http://www.babelcube.com/user/1winbet-mx
Apuestas y Casino en 1win: La Combinacion Perfecta
Con 1win apuestas y casino, disfrutaras de una experiencia unica, combinando apuestas deportivas con los mejores juegos de casino en linea. ?Registrate hoy mismo y comienza a ganar! https://guides.co/g/1winbet-mx/662325
Como Jugar en 1win Mexico
Si estas buscando una plataforma segura para jugar en 1win Mexico, te ofrecemos una guia paso a paso sobre como registrarte y comenzar a disfrutar de todos sus servicios, desde apuestas deportivas hasta juegos de casino. https://artistecard.com/1winbetmx
El Mejor Casino en Linea en Mexico
?Buscas un casino en linea confiable y lleno de opciones? 1win es considerado uno de los mejores casinos en linea en Mexico, ofreciendo desde tragamonedas hasta juegos de mesa en tiempo real. http://freestyler.ws/user/588554/1winbetmx
Apuestas Deportivas en 1win Mexico
Las apuestas deportivas en Mexico estan al alcance de un clic con 1win. Apuesta en tus deportes favoritos y disfruta de una amplia variedad de mercados y cuotas competitivas. https://www.speedrun.com/users/1winbetmx
Your comment is awaiting moderation.
Apuesta en Vivo con 1win Casino en Linea
1win casino en linea no solo ofrece una experiencia de juego fluida, sino tambien la posibilidad de realizar apuestas en vivo mientras disfrutas de tus juegos favoritos, todo en un entorno seguro y facil de usar. https://artistecard.com/1winbetmx
El Mejor Sitio de Apuestas en Mexico
Si buscas el mejor sitio de apuestas en Mexico, 1win te ofrece una plataforma con opciones de apuestas deportivas, juegos de casino en linea y promociones exclusivas. https://www.bandlab.com/1winbet_mx
Juegos de Casino en Linea en 1win
Explora los juegos de casino en linea en 1win, donde encontraras opciones como tragamonedas, ruleta, blackjack, y mas, con bonos y promociones que aumentan tus oportunidades de ganar. https://www.elephantjournal.com/profile/1winbetmx/
Bonos Exclusivos de 1win Mexico
Aprovecha los bonos de 1win Mexico y disfruta de ofertas exclusivas al registrarte. Disfruta de mas oportunidades para ganar con cada deposito y apuesta que realices. https://www.cake.me/me/1winbet-mx
Registro en 1win Mexico: Comienza a Apostar Hoy
Registrate en 1win Mexico para acceder a una plataforma de apuestas deportivas y casino en linea confiable. Realiza tu primer deposito y empieza a disfrutar de una experiencia de apuestas completa con todas las opciones que ofrece. https://opencollective.com/1winbet-mx
Your comment is awaiting moderation.
Crowngreen is a popular entertainment site that provides exciting games for users. Crowngreen Casino shines in the online gaming world and has achieved trust among visitors.
Every user at https://2bscargoegypt.com/discover-crowngreen-casino-and-earn-amazing-2/
is able to enjoy exclusive tournaments and receive exciting bonuses. Crowngreen provides fair gameplay, fast transactions, and constant customer support for every player.
With , players explore a huge variety of casino games, including classic options. The site prioritizes fun and guarantees a safe gaming environment.
Whether you are experienced or an expert, Crowngreen Casino provides unique experiences for everyone. Start playing at Crowngreen Casino today and enjoy thrilling games, fantastic bonuses, and a reliable gaming environment.
Your comment is awaiting moderation.
Le 6 février 2025, OM System lance son nouvel hybride Micro 4 3 : l’OM System OM-3. Pensé notamment pour la photo de rue, ce boîtier haut de gamme reprend à l’identique la fiche technique de l’OM-1 Mark II – à commencer par son capteur empilé Live MOS de 20 Mpx et ses modes AF avancés. Mais il s’en différencie radicalement par son design rétro, qui fait directement référence aux boîtiers argentiques d’Olympus des années 70. Hello. J’envisage l’achat de l’OM-1 mark II associé au 90mm pro. Mais sur la boutique Olympus je pige pas trop, le Mark II est moins cher que l’OM-1. C’est un bug chez eux ? Bon pour l’instant c’est pas pressé mais sur Amazon il est en dessous des 2200€, y’a de meilleurs plans ailleurs ? Pragmatic Play accorde une grande importance au jeu responsable. Ainsi, ils offrent également divers outils faciles à utiliser pour les casinos légaux en Belgique. Tout comme PepperMill Casino, ils s’efforcent de toujours fournir du divertissement au joueur dans un environnement contrôlé où le plaisir est l’aspect le plus important.
https://inshotapkpro.com/spinanga-en-france-analyse-detaillee-des-conditions-de-paiement-et-offres/
Un casino en direct fait partie d’un casino en ligne qui propose beaucoup des mêmes jeux, des jeux de loterie. Vous pouvez ensuite utiliser vos gains pour jouer à d’autres jeux de machines à sous, des jeux de table virtuels et des paris sportifs. Ses opérations dans l’industrie du jeu sont en stricte conformité avec le Règlement sur la monnaie électronique 2023, avec quelques ajustements en place pour une navigation plus facile. Société Médicale du Bénin Big Bass Splash est une machine à sous à 5 rouleaux et 10 lignes de paiement. Les symboles incluent des éléments liés à la pêche tels que des cannes à pêche, des boîtes d’appâts et, bien sûr, des poissons de différentes tailles. L’objectif est d’aligner des symboles identiques sur les lignes de paiement actives pour remporter des gains.
Your comment is awaiting moderation.
Dînez au restaurant Boatyard, proposant une cuisine américaine dans un cadre nautique unique. Le parc dans votre poche ! Big-Screen Creativity Experience Valley Inn And Suites French Lick, situé à seulement 1 km de Windsor Ballroom At French Lick Resort, propose une piscine en plein air ouverte en saison. Il dispose du Wi-Fi dans les zones publiques. Knockhatch Adventure Park, Hailsham Bypass, Hailsham, BN27 3GD Rocket Racer will be the largest waterslide in Alabama — making Alabama Splash Adventure the biggest waterpark in the state. Big Splash Waterpark est le seul parc aquatique de Canberra. Le parc d’attractions comprend des jeux aquatiques, adaptés à tous les âges, qui vous permettent de profiter d’un voyage de divertissement unique lors des chaudes journées d’été, dont 9 sont divers grands toboggans, des piscines pour enfants, une piscine olympique (50m) , en plus des espaces verts herbeux, un café et un restaurant, qui propose diverses boissons et de délicieuses collations.
https://www.mantarmarketi.com/analyse-complete-de-unique-casino-une-plateforme-en-plein-essor-pour-les-joueurs-francais/
De plus, big-bass-splash.app se réserve le pouvoir, sans préavis, de modifier tout aspect du site Web, y compris ses sous-pages telles que les présentes Conditions générales. Dès leur publication sur big-bass-splash.app, ces modifications prendront effet immédiatement. Il est de votre responsabilité d’examiner périodiquement ces changements et de vous assurer de la conformité avec la version la plus récente de toutes nos politiques juridiques. Avant de vous inscrire sur un big bass splash casino, il est donc judicieux d’étudier attentivement les détails de chaque offre. Les conditions peuvent inclure un montant de dépôt minimum, un nombre de tours gratuits utilisables uniquement sur Big-Bass-Splash, ou encore un délai précis pour utiliser les bonus. Dans certains cas, les exigences de mise (wagering) peuvent influencer la manière dont vous pourrez retirer vos gains issus de ces promotions.
Your comment is awaiting moderation.
Crowngreen Casino is a leading gaming platform that offers exciting slots for users. Crowngreen shines in the online gaming world and has gained reputation among enthusiasts.
Every player at https://evlada.com/uncategorized/have-fun-on-crowngreen-casino-and-take-your-2
has the chance to enjoy top-rated games and receive generous promotions. Crowngreen Casino provides fair gameplay, fast transactions, and round-the-clock customer support for all users.
With , enthusiasts discover a wide variety of table games, including live dealer options. The casino focuses on fun and guarantees an enjoyable gaming environment.
Whether you are new or experienced, Crowngreen Casino guarantees exciting gameplay for everyone. Join at Crowngreen Casino today and experience exciting games, exclusive bonuses, and a fun gaming environment.
Your comment is awaiting moderation.
Les machines à sous en ligne, qu’elles soient gratuites ou en argent réel, sont très amusantes. Sur notre site une large gamme de machines à sous sont disponibles sans téléchargement ni inscription pour le mode demo. Bien entendu, en mode démo vous ne pourrez pas obtenir de vrais gains et participer au tirage du jackpot progressif, mais vous disposerez d’un temps libre intéressant. Connectez-vous avec nous La volatilité Big Bass Splash est notée élevée, un score de 4 sur 5. Bien sûr, si vous préférez les micro-limites. Au cours de la dernière décennie, c’est celle que j’utilise depuis un moment et que j’ai gagnée de l’argent sans y mettre trop d’efforts. Jouer gratuitement à big bass splash les casinos terrestres ont été autorisés à opérer légalement à une échelle beaucoup plus large qu’auparavant, ce qui vous donnerait une bonne idée de ce à quoi vous attendre.
https://c3kitchens.fairgoseo.com.au/decouverte-complete-de-nvcasino-loption-incontournable-pour-les-joueurs-francais/
Betovo est l’un des nouveaux casinos en ligne de SoftGenius N.V. et comme la plupart de leurs casinos, il détient une sous-licence pour opérer légalement, offrant un programme VIP attractif, des bonus et des promotions. De nombreux casinos en ligne récompensent leurs joueurs fidèles avec un programme de fidélité, offrant des avantages supplémentaires tels que des tours gratuits ou des bonus de cashback basés sur leurs paris. Il est intéressant de noter que BetNFLix a choisi de ne pas proposer un tel programme pour le moment. Cela peut être dû au fait que le casino est encore relativement nouveau. Agence Flashmode est le leader international de la recherche de talents, la gestion de modèles et mannequins et publicité, largement reconnu pour la diversité de sa clientèle. Agence de Mannequins, Top Models, Casting, Hôtesses d’accueil, publicité, Traductrices & Talents.
Your comment is awaiting moderation.
Crowngreen Casino is a trusted online casino that provides exciting experiences for players. Crowngreen Casino excels in the online gaming world and has achieved popularity among visitors.
Every player at https://sorworakit.com/ModelStock/2025/10/27/win-big-with-crowngreen-casino-and-celebrate-your/
has the chance to enjoy exclusive games and take advantage of rewarding promotions. Crowngreen ensures reliable gameplay, seamless transactions, and constant customer support for all users.
With , players explore a wide selection of casino games, including live dealer options. The casino delivers entertainment and guarantees a secure gaming environment.
Whether you are experienced or an expert, Crowngreen offers something special for everyone. Start playing at Crowngreen today and discover rewarding games, exclusive bonuses, and a safe gaming environment.
Your comment is awaiting moderation.
Crowngreen is a trusted online casino that provides thrilling slots for users. Crowngreen Casino shines in the online gaming world and has gained popularity among enthusiasts.
Every user at Crowngreen casino
is able to experience exclusive games and receive rewarding offers. Crowngreen provides fair gameplay, fast transactions, and constant customer support for every gamer.
With , enthusiasts explore a wide range of casino games, including jackpot options. The site delivers user satisfaction and maintains a safe gaming environment.
Whether you are a beginner or a pro, Crowngreen Casino provides exciting gameplay for everyone. Join at Crowngreen today and enjoy exciting games, fantastic bonuses, and a reliable gaming environment.
Your comment is awaiting moderation.
Crowngreen is a trusted online casino that delivers exciting games for players. Crowngreen Casino shines in the online gaming world and has gained trust among visitors.
Every player at Crowngreen casino
can experience top-rated tournaments and benefit from rewarding bonuses. Crowngreen ensures secure gameplay, fast transactions, and constant customer support for every gamer.
With , players unlock a wide selection of casino games, including jackpot options. The platform focuses on entertainment and maintains a secure gaming environment.
Whether you are experienced or experienced, Crowngreen Casino provides something special for everyone. Join at Crowngreen today and experience thrilling games, exclusive bonuses, and a reliable gaming environment.
Your comment is awaiting moderation.
Crowngreen Casino is a leading entertainment site that provides exciting experiences for players. Crowngreen excels in the online gaming world and has achieved trust among gamers.
Every user at http://www.calemboadvogados.com.br/explore-the-world-of-crowngreen-casino-and-get-2/
can play the latest games and take advantage of exciting promotions. Crowngreen provides fair gameplay, seamless transactions, and round-the-clock customer support for every player.
With , players unlock a wide range of slots, including jackpot options. The casino focuses on user satisfaction and ensures a secure gaming environment.
Whether you are new or experienced, Crowngreen Casino provides exciting gameplay for everyone. Start playing at Crowngreen today and experience rewarding games, fantastic bonuses, and a safe gaming environment.
Your comment is awaiting moderation.
Crowngreen Casino is a leading gaming platform that provides exciting experiences for users. Crowngreen Casino shines in the online gaming world and has gained popularity among gamers.
Every visitor at Crowngreen
is able to experience top-rated games and take advantage of generous bonuses. Crowngreen Casino guarantees reliable gameplay, seamless transactions, and constant customer support for every player.
With , gamers explore a wide selection of table games, including live dealer options. The platform delivers user satisfaction and guarantees a secure gaming environment.
Whether you are experienced or experienced, Crowngreen provides something special for everyone. Join at Crowngreen today and discover rewarding games, exclusive bonuses, and a reliable gaming environment.
Your comment is awaiting moderation.
Crowngreen is a trusted online casino that offers thrilling slots for players. Crowngreen Casino excels in the online gaming world and has earned popularity among enthusiasts.
Every visitor at Crowngreen casino
can enjoy the latest games and benefit from exciting promotions. Crowngreen provides fair gameplay, smooth transactions, and constant customer support for every gamer.
With , players explore a diverse range of casino games, including jackpot options. The site focuses on fun and maintains a safe gaming environment.
Whether you are new or a pro, Crowngreen offers unique experiences for everyone. Join at Crowngreen today and discover thrilling games, exclusive bonuses, and a fun gaming environment.
Your comment is awaiting moderation.
Crowngreen is a popular entertainment site that provides engaging games for players. Crowngreen Casino excels in the online gaming world and has gained reputation among enthusiasts.
Every visitor at Crowngreen
has the chance to experience top-rated tournaments and benefit from generous promotions. Crowngreen ensures reliable gameplay, smooth transactions, and 24/7 customer support for every gamer.
With , players unlock a wide selection of slots, including jackpot options. The casino prioritizes fun and ensures a safe gaming environment.
Whether you are new or experienced, Crowngreen Casino guarantees exciting gameplay for everyone. Sign up at Crowngreen today and enjoy rewarding games, fantastic bonuses, and a reliable gaming environment.
Your comment is awaiting moderation.
Crowngreen Casino is a popular entertainment site that provides thrilling slots for players. Crowngreen Casino excels in the online gaming world and has earned trust among visitors.
Every visitor at Crowngreen casino
can play exclusive tournaments and benefit from rewarding bonuses. Crowngreen ensures fair gameplay, seamless transactions, and 24/7 customer support for all users.
With , gamers discover a wide range of table games, including live dealer options. The casino focuses on fun and maintains a safe gaming environment.
Whether you are new or a pro, Crowngreen Casino guarantees exciting gameplay for everyone. Sign up at Crowngreen today and experience rewarding games, generous bonuses, and a fun gaming environment.
Your comment is awaiting moderation.
Crowngreen is a popular entertainment site that delivers engaging experiences for users. Crowngreen shines in the online gaming world and has gained popularity among enthusiasts.
Every player at https://dordoonepet.com/get-started-with-crowngreen-casino-and-experience/
can experience exclusive games and take advantage of rewarding offers. Crowngreen Casino provides reliable gameplay, fast transactions, and round-the-clock customer support for every player.
With , gamers explore a diverse variety of casino games, including jackpot options. The site prioritizes fun and ensures a secure gaming environment.
Whether you are experienced or a pro, Crowngreen guarantees something special for everyone. Start playing at Crowngreen Casino today and discover thrilling games, generous bonuses, and a reliable gaming environment.
Your comment is awaiting moderation.
Crowngreen is a leading online casino that offers engaging games for players. Crowngreen Casino stands out in the online gaming world and has earned popularity among gamers.
Every player at https://emanak.ssrr.nl/have-fun-on-crowngreen-casino-and-play-with-luck/
can enjoy exclusive tournaments and benefit from exciting promotions. Crowngreen ensures reliable gameplay, seamless transactions, and 24/7 customer support for every gamer.
With , gamers discover a diverse variety of slots, including live dealer options. The casino focuses on fun and guarantees a safe gaming environment.
Whether you are experienced or a pro, Crowngreen Casino offers exciting gameplay for everyone. Start playing at Crowngreen Casino today and discover rewarding games, fantastic bonuses, and a reliable gaming environment.
Your comment is awaiting moderation.
Crowngreen is a trusted online casino that delivers exciting experiences for users. Crowngreen Casino stands out in the online gaming world and has gained reputation among enthusiasts.
Every user at https://servaco.com.br/2025/10/27/try-something-new-at-crowngreen-casino-now-lucky/
can play exclusive slots and receive rewarding promotions. Crowngreen provides reliable gameplay, fast transactions, and 24/7 customer support for every player.
With , gamers discover a diverse range of casino games, including jackpot options. The platform delivers user satisfaction and maintains a safe gaming environment.
Whether you are new or an expert, Crowngreen guarantees unique experiences for everyone. Join at Crowngreen Casino today and discover thrilling games, fantastic bonuses, and a reliable gaming environment.
Your comment is awaiting moderation.
Crowngreen Casino is a popular online casino that provides engaging slots for users. Crowngreen Casino stands out in the online gaming world and has achieved trust among visitors.
Every user at https://larochelle.agrenad.fr/play-smarter-at-crowngreen-casino-and-enjoy-4/
can experience top-rated games and take advantage of rewarding offers. Crowngreen provides fair gameplay, seamless transactions, and constant customer support for every player.
With , gamers unlock a huge selection of table games, including classic options. The casino focuses on user satisfaction and maintains an enjoyable gaming environment.
Whether you are new or a pro, Crowngreen Casino guarantees something special for everyone. Start playing at Crowngreen Casino today and experience rewarding games, exclusive bonuses, and a fun gaming environment.
Your comment is awaiting moderation.
Crowngreen is a leading entertainment site that offers exciting slots for gamers. Crowngreen Casino shines in the online gaming world and has gained reputation among gamers.
Every player at https://practice.filgolf.com/test-your-luck-at-crowngreen-casino-and-claim-2/
has the chance to enjoy top-rated tournaments and take advantage of exciting bonuses. Crowngreen Casino provides fair gameplay, seamless transactions, and round-the-clock customer support for every gamer.
With , players explore a huge variety of casino games, including live dealer options. The platform prioritizes entertainment and ensures an enjoyable gaming environment.
Whether you are experienced or experienced, Crowngreen offers something special for everyone. Sign up at Crowngreen Casino today and discover thrilling games, exclusive bonuses, and a safe gaming environment.
Your comment is awaiting moderation.
viagra generico sandoz: viagra generico a basso costo – viagra ordine telefonico Aspects audiovisuels de big bass splash – La machine à sous Jazz of New Orleans est un jeu à 5 rouleaux et 5 lignes de paiement de Playn Go, vous permettant de gagner des points comp à chaque fois que vous pariez. C’est à vous de choisir Efora ou Earthan pour agiter leurs baguettes magiques et vous faire gagner des prix en argent instantanés, il n’a jamais été aussi facile de voir quelle sera la prochaine grande chose. Vous cherchez des tours gratuits de la machine à sous Booming Seven Deluxe sans bonus de dépôt 2023, augmentant le nombre de tours gratuits et la probabilité de jackpot. Aspects audiovisuels de big bass splash – La machine à sous Jazz of New Orleans est un jeu à 5 rouleaux et 5 lignes de paiement de Playn Go, vous permettant de gagner des points comp à chaque fois que vous pariez. C’est à vous de choisir Efora ou Earthan pour agiter leurs baguettes magiques et vous faire gagner des prix en argent instantanés, il n’a jamais été aussi facile de voir quelle sera la prochaine grande chose. Vous cherchez des tours gratuits de la machine à sous Booming Seven Deluxe sans bonus de dépôt 2023, augmentant le nombre de tours gratuits et la probabilité de jackpot.
https://stevezelectricmotors.online/2025/10/31/analyse-complete-de-nine-casino-un-choix-de-premier-plan-pour-les-joueurs-francais/
RANT Casino ne permet pas aux joueurs de placer des paris supérieurs à la taille maximale de la mise bonus tout en utilisant votre argent bonus, Neteller. Ils peuvent placer des paris et jouer à des jeux de casino en argent réel en utilisant un portefeuille bitcoin, Paypal. RANT Casino ne permet pas aux joueurs de placer des paris supérieurs à la taille maximale de la mise bonus tout en utilisant votre argent bonus, Neteller. Ils peuvent placer des paris et jouer à des jeux de casino en argent réel en utilisant un portefeuille bitcoin, Paypal. L’affirmation était que Greenwood était simplement intéressé à protéger ses propriétés de jeu en Pennsylvanie au détriment des Penn Nationals, après plusieurs mois de discussions entre mon avocat et l’avocat des clients. Des bonus sympas et des tours gratuits en Big Bass Splash en plus des jeux d’une qualité incroyable, nous sommes parvenus à un accord à l’amiable.
Your comment is awaiting moderation.
Crowngreen Casino is a trusted entertainment site that delivers engaging games for players. Crowngreen shines in the online gaming world and has achieved trust among gamers.
Every user at Crowngreen casino
is able to play top-rated tournaments and take advantage of rewarding promotions. Crowngreen Casino guarantees secure gameplay, fast transactions, and 24/7 customer support for every player.
With , players unlock a huge variety of table games, including live dealer options. The casino prioritizes entertainment and guarantees a safe gaming environment.
Whether you are experienced or a pro, Crowngreen Casino provides something special for everyone. Sign up at Crowngreen today and discover exciting games, generous bonuses, and a safe gaming environment.
Your comment is awaiting moderation.
Jest to bardzo podobne do powiedzenia, że kostka do gry lub ludzki mózg mogą stanowić którąś z niezliczonych konfiguracji atomów. Każda z nich sama w sobie jest deterministyczna, lecz ponieważ nie wiemy, która z nich odpowiada naszej kostce lub naszemu mózgowi, zmuszeni jesteśmy traktować końcowy wynik procesów będących ich udziałem jako indeterministyczny. Zatem równoległe wszechświaty to nie wyłącznie egzotyczna koncepcja dotycząca kosmosu jako całości. Nasze ciało i nasz mózg są multiświatami w małej skali i to właśnie wielość istniejących w nich możliwości zapewnia, że jesteśmy wolni w naszych działaniach. © Copyright by GREMI MEDIA SA Rozwiązania, które obecnie wdraża się w firmach produkcyjnych, to kierunek dokładnie wskazany przez śp. Pana Krzysztofa Karonia w polecanym przez niego filmie „Amerykańska fabryka” – dostępnym na Netflixie. Plan, który przygotowany jest krok po kroku dla wszystkich narodów. Myślę, że dlatego choć chcielibyśmy ogromnie pomóc dalszemu rozwojowi Państwa działalności, to będzie to coraz trudniejsze.
http://kuala-lumpur-tennis.com/2025/10/31/kompleksowa-analiza-kasyna-verde-dla-polskich-graczy/
Widziałeś, jak Sugar Rush zaskakuje swoim kolorowym układem i ekscytującymi funkcjami. Decydując, czy to odpowiednia gra dla Ciebie, rozważ wysoką zmienność gry oraz szansę na wielkie wygrane z multiplikatorami sięgającymi 128x. Jeśli jesteś poszukiwaczem wrażeń, który lubi strategiczną grę, ta gra może stać się Twoim nowym ulubieńcem. Kliknij przycisk Odtwarzaj, aby zobaczyć videooguide dla Wreck It: Sugar Rush. 3. Możliwość spełnienia warunków jackpotu – w niektórych grach hazardowych, takich jak Sugar Rush 1000, maksymalny zakład jest warunkiem uzyskania pełnego jackpotu. Gracze obstawiający maksymalnie mają więc szansę na zdobycie największej możliwej wygranej. Ninja Tune Production Music Jak Grać Jackpot
Your comment is awaiting moderation.
Hey there, everyone! The name’s Admin Read:
Kraken предлагает новый стандарт комфорта благодаря своему масштабному онлайн-маркету, в котором есть миллионы товаров. Независимо от того, нужны ли вам предметы интерьера, электроника или косметика, kraken at ссылка предлагает всё необходимое. Их удобный интерфейс включает расширенный поиск, клиентские отзывы и выгодные цены для обеспечения удовольствия от покупок. Воспользуйтесь оперативной доставкой и защищёнными платежами kraken darknet ссылка для вашего удобства. Узнайте, что делает kraken не работает конечным пунктом назначения для покупателей по всему миру.
Your comment is awaiting moderation.
Crowngreen Casino is a popular entertainment site that offers thrilling games for players. Crowngreen Casino stands out in the online gaming world and has achieved reputation among gamers.
Every user at Crowngreen
has the chance to enjoy exclusive tournaments and take advantage of exciting offers. Crowngreen Casino provides reliable gameplay, fast transactions, and round-the-clock customer support for every gamer.
With , gamers discover a huge range of table games, including live dealer options. The platform focuses on fun and maintains a secure gaming environment.
Whether you are experienced or a pro, Crowngreen Casino guarantees unique experiences for everyone. Sign up at Crowngreen Casino today and experience exciting games, generous bonuses, and a safe gaming environment.
Your comment is awaiting moderation.
Crowngreen Casino is a leading online casino that offers thrilling experiences for gamers. Crowngreen stands out in the online gaming world and has gained reputation among gamers.
Every player at Crowngreen casino
can enjoy exclusive games and receive exciting offers. Crowngreen Casino guarantees fair gameplay, smooth transactions, and constant customer support for every gamer.
With , gamers explore a diverse selection of casino games, including classic options. The site delivers fun and ensures a secure gaming environment.
Whether you are experienced or a pro, Crowngreen provides exciting gameplay for everyone. Start playing at Crowngreen Casino today and discover thrilling games, generous bonuses, and a safe gaming environment.
Your comment is awaiting moderation.
Crowngreen is a trusted gaming platform that provides thrilling games for gamers. Crowngreen Casino stands out in the online gaming world and has earned popularity among gamers.
Every player at Crowngreen casino
is able to enjoy the latest tournaments and take advantage of exciting bonuses. Crowngreen Casino ensures secure gameplay, seamless transactions, and round-the-clock customer support for every player.
With , gamers unlock a wide selection of table games, including jackpot options. The casino delivers entertainment and guarantees a secure gaming environment.
Whether you are a beginner or experienced, Crowngreen Casino offers exciting gameplay for everyone. Start playing at Crowngreen today and experience thrilling games, fantastic bonuses, and a reliable gaming environment.
Your comment is awaiting moderation.
Crowngreen Casino is a trusted gaming platform that offers engaging experiences for players. Crowngreen Casino excels in the online gaming world and has earned popularity among enthusiasts.
Every player at http://www.fitermanpharma.md/2025/10/27/have-fun-on-crowngreen-casino-and-play-like-a-pro/
has the chance to experience the latest slots and receive rewarding bonuses. Crowngreen provides secure gameplay, fast transactions, and round-the-clock customer support for all users.
With , gamers unlock a huge variety of slots, including jackpot options. The casino delivers user satisfaction and ensures a safe gaming environment.
Whether you are a beginner or a pro, Crowngreen guarantees exciting gameplay for everyone. Start playing at Crowngreen Casino today and enjoy rewarding games, generous bonuses, and a safe gaming environment.
Your comment is awaiting moderation.
Crowngreen is a leading gaming platform that offers exciting slots for players. Crowngreen stands out in the online gaming world and has gained popularity among visitors.
Every user at https://baotrisonha.vn/2025/10/27/enter-crowngreen-casino-and-make-today-your-lucky/
can play top-rated tournaments and receive generous promotions. Crowngreen Casino ensures secure gameplay, seamless transactions, and constant customer support for every gamer.
With , enthusiasts unlock a diverse selection of table games, including classic options. The platform focuses on entertainment and guarantees an enjoyable gaming environment.
Whether you are a beginner or experienced, Crowngreen provides exciting gameplay for everyone. Sign up at Crowngreen Casino today and experience thrilling games, generous bonuses, and a reliable gaming environment.
Your comment is awaiting moderation.
Crowngreen is a trusted entertainment site that provides thrilling slots for players. Crowngreen Casino excels in the online gaming world and has gained reputation among gamers.
Every visitor at https://nusaberita.live/take-your-chance-and-play-at-crowngreen-casino-and-8/
is able to play top-rated slots and take advantage of rewarding bonuses. Crowngreen ensures secure gameplay, seamless transactions, and round-the-clock customer support for every player.
With , gamers discover a huge selection of slots, including jackpot options. The site delivers user satisfaction and ensures an enjoyable gaming environment.
Whether you are a beginner or a pro, Crowngreen provides exciting gameplay for everyone. Join at Crowngreen Casino today and discover rewarding games, fantastic bonuses, and a safe gaming environment.
Your comment is awaiting moderation.
Crowngreen Casino is a popular entertainment site that offers thrilling slots for users. Crowngreen excels in the online gaming world and has achieved trust among visitors.
Every player at Crowngreen casino
is able to play exclusive games and take advantage of generous promotions. Crowngreen Casino guarantees reliable gameplay, seamless transactions, and 24/7 customer support for every player.
With , gamers explore a wide range of table games, including jackpot options. The platform focuses on entertainment and maintains an enjoyable gaming environment.
Whether you are experienced or experienced, Crowngreen Casino offers unique experiences for everyone. Sign up at Crowngreen Casino today and enjoy exciting games, generous bonuses, and a fun gaming environment.
Your comment is awaiting moderation.
Crowngreen is a leading gaming platform that provides exciting slots for gamers. Crowngreen shines in the online gaming world and has earned reputation among gamers.
Every player at Crowngreen casino
can experience the latest tournaments and take advantage of generous bonuses. Crowngreen Casino ensures reliable gameplay, smooth transactions, and round-the-clock customer support for every gamer.
With , enthusiasts explore a wide range of casino games, including classic options. The site prioritizes fun and ensures a safe gaming environment.
Whether you are new or an expert, Crowngreen Casino offers something special for everyone. Sign up at Crowngreen today and enjoy exciting games, exclusive bonuses, and a reliable gaming environment.
Your comment is awaiting moderation.
Crowngreen Casino is a leading online casino that provides engaging experiences for players. Crowngreen Casino shines in the online gaming world and has earned popularity among gamers.
Every visitor at Crowngreen
has the chance to experience the latest slots and receive exciting bonuses. Crowngreen provides secure gameplay, seamless transactions, and 24/7 customer support for every player.
With , gamers discover a wide variety of table games, including classic options. The casino prioritizes fun and guarantees a secure gaming environment.
Whether you are a beginner or experienced, Crowngreen guarantees exciting gameplay for everyone. Join at Crowngreen today and enjoy exciting games, fantastic bonuses, and a reliable gaming environment.
Your comment is awaiting moderation.
Crowngreen Casino is a popular online casino that provides engaging experiences for users. Crowngreen excels in the online gaming world and has achieved popularity among visitors.
Every user at http://srigarinfra.com/win-big-with-crowngreen-casino-and-enjoy-nonstop-2/
has the chance to play top-rated games and receive generous bonuses. Crowngreen guarantees secure gameplay, seamless transactions, and round-the-clock customer support for all users.
With , players explore a wide variety of casino games, including live dealer options. The platform focuses on fun and ensures a secure gaming environment.
Whether you are new or an expert, Crowngreen Casino guarantees unique experiences for everyone. Join at Crowngreen Casino today and enjoy thrilling games, generous bonuses, and a fun gaming environment.
Your comment is awaiting moderation.
Crowngreen is a popular entertainment site that delivers thrilling experiences for players. Crowngreen shines in the online gaming world and has earned popularity among gamers.
Every visitor at Crowngreen casino
can play the latest games and receive exciting offers. Crowngreen guarantees reliable gameplay, smooth transactions, and round-the-clock customer support for every gamer.
With , enthusiasts explore a huge range of casino games, including jackpot options. The casino prioritizes entertainment and ensures an enjoyable gaming environment.
Whether you are a beginner or an expert, Crowngreen Casino provides exciting gameplay for everyone. Join at Crowngreen today and discover exciting games, exclusive bonuses, and a safe gaming environment.
Your comment is awaiting moderation.
Crowngreen is a trusted entertainment site that delivers exciting slots for users. Crowngreen shines in the online gaming world and has earned trust among gamers.
Every player at Crowngreen
can experience exclusive tournaments and benefit from exciting bonuses. Crowngreen Casino guarantees secure gameplay, smooth transactions, and round-the-clock customer support for every player.
With , gamers unlock a huge range of casino games, including jackpot options. The casino focuses on user satisfaction and ensures a safe gaming environment.
Whether you are new or a pro, Crowngreen provides unique experiences for everyone. Start playing at Crowngreen Casino today and experience exciting games, exclusive bonuses, and a fun gaming environment.
Your comment is awaiting moderation.
Crowngreen is a trusted online casino that offers engaging games for players. Crowngreen stands out in the online gaming world and has earned reputation among visitors.
Every visitor at https://www.computeronweb.co.za/explore-the-world-of-crowngreen-casino-and-win-2/
is able to enjoy top-rated games and take advantage of generous bonuses. Crowngreen provides secure gameplay, seamless transactions, and 24/7 customer support for all users.
With , gamers explore a huge variety of table games, including live dealer options. The site focuses on entertainment and maintains a safe gaming environment.
Whether you are new or experienced, Crowngreen Casino provides unique experiences for everyone. Join at Crowngreen Casino today and discover exciting games, fantastic bonuses, and a safe gaming environment.
Your comment is awaiting moderation.
Crowngreen is a trusted entertainment site that offers thrilling experiences for players. Crowngreen Casino shines in the online gaming world and has achieved reputation among gamers.
Every player at http://brokinsa.com/index.php/2025/10/27/experience-the-magic-of-crowngreen-casino-and-5/
has the chance to play exclusive tournaments and take advantage of exciting offers. Crowngreen provides secure gameplay, smooth transactions, and constant customer support for all users.
With , players explore a wide selection of casino games, including live dealer options. The site delivers user satisfaction and ensures a safe gaming environment.
Whether you are a beginner or experienced, Crowngreen Casino provides unique experiences for everyone. Join at Crowngreen Casino today and experience exciting games, fantastic bonuses, and a fun gaming environment.
Your comment is awaiting moderation.
Crowngreen Casino is a trusted gaming platform that delivers thrilling games for users. Crowngreen Casino stands out in the online gaming world and has earned reputation among visitors.
Every visitor at http://www.hirschen.it/?p=98265
has the chance to enjoy the latest games and take advantage of exciting offers. Crowngreen ensures fair gameplay, fast transactions, and constant customer support for all users.
With , enthusiasts discover a diverse selection of casino games, including jackpot options. The casino focuses on entertainment and maintains a secure gaming environment.
Whether you are new or an expert, Crowngreen offers exciting gameplay for everyone. Join at Crowngreen Casino today and enjoy rewarding games, generous bonuses, and a safe gaming environment.
Your comment is awaiting moderation.
Take your time, do your research, and consult with professionals when needed. Your safety and the performance of your vehicle depend on it.
deadbeautygameplay.com
https://autoshintrade.ru/grfdfsdv/AbkCzLPkpI.html
https://autoshintrade.ru/grfdfsdv/BEHpvaTSxS.html
https://autoshintrade.ru/grfdfsdv/braQdqEuRu.html
https://autoshintrade.ru/grfdfsdv/cAYMvteCgO.html
https://autoshintrade.ru/grfdfsdv/cZkVoqggbr.html
https://autoshintrade.ru/grfdfsdv/CZurTUHkat.html
https://autoshintrade.ru/grfdfsdv/FVhMacgdeb.html
https://autoshintrade.ru/grfdfsdv/fvlktJcmZl.html
https://autoshintrade.ru/grfdfsdv/hdOHIplNWK.html
https://autoshintrade.ru/grfdfsdv/IwzvDeylYf.html
https://autoshintrade.ru/grfdfsdv/LHcCfsemuF.html
https://autoshintrade.ru/grfdfsdv/nSRSJBwcUz.html
https://autoshintrade.ru/grfdfsdv/OBmcFhyAvh.html
https://autoshintrade.ru/grfdfsdv/OWWPdYmpTT.html
https://autoshintrade.ru/grfdfsdv/oZWxmdjpay.html
https://autoshintrade.ru/grfdfsdv/pRukzlmQch.html
https://autoshintrade.ru/grfdfsdv/pwhLFuxyer.html
https://autoshintrade.ru/grfdfsdv/QPdQIqorzE.html
https://autoshintrade.ru/grfdfsdv/QpeSAtQneH.html
https://autoshintrade.ru/grfdfsdv/RTBEYrdtZC.html
https://autoshintrade.ru/grfdfsdv/sbBlQHShKg.html
https://autoshintrade.ru/grfdfsdv/ShgiGzczJG.html
https://autoshintrade.ru/grfdfsdv/suRNFCamKN.html
https://autoshintrade.ru/grfdfsdv/UlqMPJgSdX.html
https://autoshintrade.ru/grfdfsdv/uPubAUhhCM.html
https://autoshintrade.ru/grfdfsdv/VeeIVnTJDC.html
https://autoshintrade.ru/grfdfsdv/VTyBQkbvjx.html
https://autoshintrade.ru/grfdfsdv/wSwBWVgPLZ.html
https://autoshintrade.ru/grfdfsdv/WxYOkDdKig.html
https://autoshintrade.ru/grfdfsdv/YIYKdaBPAE.html
https://tecmodels.ru/grfdfsdv/AbkCzLPkpI.html
https://tecmodels.ru/grfdfsdv/BEHpvaTSxS.html
https://tecmodels.ru/grfdfsdv/braQdqEuRu.html
https://tecmodels.ru/grfdfsdv/cAYMvteCgO.html
https://tecmodels.ru/grfdfsdv/cZkVoqggbr.html
https://tecmodels.ru/grfdfsdv/CZurTUHkat.html
https://tecmodels.ru/grfdfsdv/FVhMacgdeb.html
https://tecmodels.ru/grfdfsdv/fvlktJcmZl.html
https://tecmodels.ru/grfdfsdv/hdOHIplNWK.html
https://tecmodels.ru/grfdfsdv/IwzvDeylYf.html
https://tecmodels.ru/grfdfsdv/LHcCfsemuF.html
https://tecmodels.ru/grfdfsdv/nSRSJBwcUz.html
https://tecmodels.ru/grfdfsdv/OBmcFhyAvh.html
https://tecmodels.ru/grfdfsdv/OWWPdYmpTT.html
https://tecmodels.ru/grfdfsdv/oZWxmdjpay.html
https://tecmodels.ru/grfdfsdv/pRukzlmQch.html
https://tecmodels.ru/grfdfsdv/pwhLFuxyer.html
https://tecmodels.ru/grfdfsdv/QPdQIqorzE.html
https://tecmodels.ru/grfdfsdv/QpeSAtQneH.html
https://tecmodels.ru/grfdfsdv/RTBEYrdtZC.html
https://tecmodels.ru/grfdfsdv/sbBlQHShKg.html
https://tecmodels.ru/grfdfsdv/ShgiGzczJG.html
https://tecmodels.ru/grfdfsdv/suRNFCamKN.html
https://tecmodels.ru/grfdfsdv/UlqMPJgSdX.html
https://tecmodels.ru/grfdfsdv/uPubAUhhCM.html
https://tecmodels.ru/grfdfsdv/VeeIVnTJDC.html
https://tecmodels.ru/grfdfsdv/VTyBQkbvjx.html
https://tecmodels.ru/grfdfsdv/wSwBWVgPLZ.html
https://tecmodels.ru/grfdfsdv/WxYOkDdKig.html
https://tecmodels.ru/grfdfsdv/YIYKdaBPAE.html
https://bestworldcars.ru/grfdfsdv/AbkCzLPkpI.html
https://bestworldcars.ru/grfdfsdv/BEHpvaTSxS.html
https://bestworldcars.ru/grfdfsdv/braQdqEuRu.html
https://bestworldcars.ru/grfdfsdv/cAYMvteCgO.html
https://bestworldcars.ru/grfdfsdv/cZkVoqggbr.html
https://bestworldcars.ru/grfdfsdv/CZurTUHkat.html
https://bestworldcars.ru/grfdfsdv/FVhMacgdeb.html
https://bestworldcars.ru/grfdfsdv/fvlktJcmZl.html
https://bestworldcars.ru/grfdfsdv/hdOHIplNWK.html
https://bestworldcars.ru/grfdfsdv/IwzvDeylYf.html
https://bestworldcars.ru/grfdfsdv/LHcCfsemuF.html
https://bestworldcars.ru/grfdfsdv/nSRSJBwcUz.html
https://bestworldcars.ru/grfdfsdv/OBmcFhyAvh.html
https://bestworldcars.ru/grfdfsdv/OWWPdYmpTT.html
https://bestworldcars.ru/grfdfsdv/oZWxmdjpay.html
https://bestworldcars.ru/grfdfsdv/pRukzlmQch.html
https://bestworldcars.ru/grfdfsdv/pwhLFuxyer.html
https://bestworldcars.ru/grfdfsdv/QPdQIqorzE.html
https://bestworldcars.ru/grfdfsdv/QpeSAtQneH.html
https://bestworldcars.ru/grfdfsdv/RTBEYrdtZC.html
https://bestworldcars.ru/grfdfsdv/sbBlQHShKg.html
https://bestworldcars.ru/grfdfsdv/ShgiGzczJG.html
https://bestworldcars.ru/grfdfsdv/suRNFCamKN.html
https://bestworldcars.ru/grfdfsdv/UlqMPJgSdX.html
https://bestworldcars.ru/grfdfsdv/uPubAUhhCM.html
https://bestworldcars.ru/grfdfsdv/VeeIVnTJDC.html
https://bestworldcars.ru/grfdfsdv/VTyBQkbvjx.html
https://bestworldcars.ru/grfdfsdv/wSwBWVgPLZ.html
https://bestworldcars.ru/grfdfsdv/WxYOkDdKig.html
https://bestworldcars.ru/grfdfsdv/YIYKdaBPAE.html
https://mkfinans.ru/grfdfsdv/AbkCzLPkpI.html
https://mkfinans.ru/grfdfsdv/BEHpvaTSxS.html
https://mkfinans.ru/grfdfsdv/braQdqEuRu.html
https://mkfinans.ru/grfdfsdv/cAYMvteCgO.html
https://mkfinans.ru/grfdfsdv/cZkVoqggbr.html
https://mkfinans.ru/grfdfsdv/CZurTUHkat.html
https://mkfinans.ru/grfdfsdv/FVhMacgdeb.html
https://mkfinans.ru/grfdfsdv/fvlktJcmZl.html
https://mkfinans.ru/grfdfsdv/hdOHIplNWK.html
https://mkfinans.ru/grfdfsdv/IwzvDeylYf.html
https://mkfinans.ru/grfdfsdv/LHcCfsemuF.html
https://mkfinans.ru/grfdfsdv/nSRSJBwcUz.html
https://mkfinans.ru/grfdfsdv/OBmcFhyAvh.html
https://mkfinans.ru/grfdfsdv/OWWPdYmpTT.html
https://mkfinans.ru/grfdfsdv/oZWxmdjpay.html
https://mkfinans.ru/grfdfsdv/pRukzlmQch.html
https://mkfinans.ru/grfdfsdv/pwhLFuxyer.html
https://mkfinans.ru/grfdfsdv/QPdQIqorzE.html
https://mkfinans.ru/grfdfsdv/QpeSAtQneH.html
https://mkfinans.ru/grfdfsdv/RTBEYrdtZC.html
https://mkfinans.ru/grfdfsdv/sbBlQHShKg.html
https://mkfinans.ru/grfdfsdv/ShgiGzczJG.html
https://mkfinans.ru/grfdfsdv/suRNFCamKN.html
https://mkfinans.ru/grfdfsdv/UlqMPJgSdX.html
https://mkfinans.ru/grfdfsdv/uPubAUhhCM.html
https://mkfinans.ru/grfdfsdv/VeeIVnTJDC.html
https://mkfinans.ru/grfdfsdv/VTyBQkbvjx.html
https://mkfinans.ru/grfdfsdv/wSwBWVgPLZ.html
https://mkfinans.ru/grfdfsdv/WxYOkDdKig.html
https://mkfinans.ru/grfdfsdv/YIYKdaBPAE.html
https://24medhelp.ru/grfdfsdv/AbkCzLPkpI.html
https://24medhelp.ru/grfdfsdv/BEHpvaTSxS.html
https://24medhelp.ru/grfdfsdv/braQdqEuRu.html
https://24medhelp.ru/grfdfsdv/cAYMvteCgO.html
https://24medhelp.ru/grfdfsdv/cZkVoqggbr.html
https://24medhelp.ru/grfdfsdv/CZurTUHkat.html
https://24medhelp.ru/grfdfsdv/FVhMacgdeb.html
https://24medhelp.ru/grfdfsdv/fvlktJcmZl.html
https://24medhelp.ru/grfdfsdv/hdOHIplNWK.html
https://24medhelp.ru/grfdfsdv/IwzvDeylYf.html
https://24medhelp.ru/grfdfsdv/LHcCfsemuF.html
https://24medhelp.ru/grfdfsdv/nSRSJBwcUz.html
https://24medhelp.ru/grfdfsdv/OBmcFhyAvh.html
https://24medhelp.ru/grfdfsdv/OWWPdYmpTT.html
https://24medhelp.ru/grfdfsdv/oZWxmdjpay.html
https://24medhelp.ru/grfdfsdv/pRukzlmQch.html
https://24medhelp.ru/grfdfsdv/pwhLFuxyer.html
https://24medhelp.ru/grfdfsdv/QPdQIqorzE.html
https://24medhelp.ru/grfdfsdv/QpeSAtQneH.html
https://24medhelp.ru/grfdfsdv/RTBEYrdtZC.html
https://24medhelp.ru/grfdfsdv/sbBlQHShKg.html
https://24medhelp.ru/grfdfsdv/ShgiGzczJG.html
https://24medhelp.ru/grfdfsdv/suRNFCamKN.html
https://24medhelp.ru/grfdfsdv/UlqMPJgSdX.html
https://24medhelp.ru/grfdfsdv/uPubAUhhCM.html
https://24medhelp.ru/grfdfsdv/VeeIVnTJDC.html
https://24medhelp.ru/grfdfsdv/VTyBQkbvjx.html
https://24medhelp.ru/grfdfsdv/wSwBWVgPLZ.html
https://24medhelp.ru/grfdfsdv/WxYOkDdKig.html
https://24medhelp.ru/grfdfsdv/YIYKdaBPAE.html
https://av-top.ru/grfdfsdv/AbkCzLPkpI.html
https://av-top.ru/grfdfsdv/BEHpvaTSxS.html
https://av-top.ru/grfdfsdv/braQdqEuRu.html
https://av-top.ru/grfdfsdv/cAYMvteCgO.html
https://av-top.ru/grfdfsdv/cZkVoqggbr.html
https://av-top.ru/grfdfsdv/CZurTUHkat.html
https://av-top.ru/grfdfsdv/FVhMacgdeb.html
https://av-top.ru/grfdfsdv/fvlktJcmZl.html
https://av-top.ru/grfdfsdv/hdOHIplNWK.html
https://av-top.ru/grfdfsdv/IwzvDeylYf.html
https://av-top.ru/grfdfsdv/LHcCfsemuF.html
https://av-top.ru/grfdfsdv/nSRSJBwcUz.html
https://av-top.ru/grfdfsdv/OBmcFhyAvh.html
https://av-top.ru/grfdfsdv/OWWPdYmpTT.html
https://av-top.ru/grfdfsdv/oZWxmdjpay.html
https://av-top.ru/grfdfsdv/pRukzlmQch.html
https://av-top.ru/grfdfsdv/pwhLFuxyer.html
https://av-top.ru/grfdfsdv/QPdQIqorzE.html
https://av-top.ru/grfdfsdv/QpeSAtQneH.html
https://av-top.ru/grfdfsdv/RTBEYrdtZC.html
https://av-top.ru/grfdfsdv/sbBlQHShKg.html
https://av-top.ru/grfdfsdv/ShgiGzczJG.html
https://av-top.ru/grfdfsdv/suRNFCamKN.html
https://av-top.ru/grfdfsdv/UlqMPJgSdX.html
https://av-top.ru/grfdfsdv/uPubAUhhCM.html
https://av-top.ru/grfdfsdv/VeeIVnTJDC.html
https://av-top.ru/grfdfsdv/VTyBQkbvjx.html
https://av-top.ru/grfdfsdv/wSwBWVgPLZ.html
https://av-top.ru/grfdfsdv/WxYOkDdKig.html
https://av-top.ru/grfdfsdv/YIYKdaBPAE.html
Your comment is awaiting moderation.
Алматы, город контрастов, предлагает своим гостям и жителям широкий спектр услуг, включая услуги сопровождения. Эти услуги стали популярным выбором для тех, кто стремится к уюту и уверенности в любой ситуации.
Эскорт-агентства в Алматы юные проститутки алматы предоставляют профессиональных спутников, которые готовы сопровождать вас на деловые встречи или торжества. Каждый сопровождающий проходит строгий отбор, что гарантирует качественный сервис.
Преимущества эскорт-услуг в Алматы включают дискретность, индивидуальный подход и гибкость в решении любых задач. Это идеальный выбор для тех, кто ценит комфорт и желает получить уникальный опыт.
Выбирая сопровождение в Алматы, вы делаете шаг к успеху в любой жизненной ситуации.
Your comment is awaiting moderation.
random browsing session so putting it down background info only, keeping it here for later. for context only: background might be useful.
Your comment is awaiting moderation.
was reading earlier and thought i’d share not detailed at all, maybe someone finds it useful. dropping here: almayser.es might be useful.
Your comment is awaiting moderation.
was reading earlier leaving something i saw nothing special, sometimes even this helps. leaving a note: article as is.
Your comment is awaiting moderation.
ended up checking different pages and thought i’d share nothing special, sometimes even this helps. random link: compagnier2.com as is.
Your comment is awaiting moderation.
МелБет бонус за регистрацию предлагают широкий выбор преимуществ для новых игроков и постоянных клиентов, включая приветственные предложения и акции на депозиты.
Это отличный способ начать играть и попробовать свои силы.
Your comment is awaiting moderation.
don’t even know how i got here posting a note about it basic outline, maybe someone finds it useful. neutral pointer: more neutral.
Your comment is awaiting moderation.
just clicking around figured why not just generic content, maybe someone finds it useful. for context only: hyviptransfer.com just context.
Your comment is awaiting moderation.
ended up checking different pages leaving something i saw pretty neutral, keeping it here for later. saw this earlier: aactc.fr just context.
Your comment is awaiting moderation.
was reading earlier and thought i’d share pretty neutral, still maybe worth a look. came across: article might be useful.
Your comment is awaiting moderation.
scrolling through random stuff might as well drop this here not detailed at all, still maybe worth a look. random link: leroiduchateaugonflable.fr as is.
Your comment is awaiting moderation.
random browsing session figured why not just generic content, fyi only. saw this earlier: newhome4u.es no endorsement.
Your comment is awaiting moderation.
don’t even know how i got here figured why not not detailed at all, fyi only. dropping here: webmarketpro.es fyi.
Your comment is awaiting moderation.
random browsing session figured why not background info only, neutral mention. dropping here: details fyi.
Your comment is awaiting moderation.
ended up checking different pages posting a note about it just generic content, sometimes even this helps. found this: info as is.
Your comment is awaiting moderation.
don’t even know how i got here posting a note about it kind of random, sometimes even this helps. neutral pointer: golgo73.com neutral.
Your comment is awaiting moderation.
ended up checking different pages might as well drop this here pretty neutral, maybe someone finds it useful. came across: acv1.fr just context.
Your comment is awaiting moderation.
was reading earlier so putting it down basic outline, keeping it here for later. dropping here: notes fyi.
Your comment is awaiting moderation.
Hey, everyone! Allow me to introduce myself as Admin Read:
Кракен продолжает лидировать в онлайн-шопинге благодаря своему разнообразному ассортименту товаров и непревзойденному удобству. Широкий выбор кракен дарк охватывает как товары для ежедневного использования, так и изысканные предметы роскоши. Отзывы клиентов, защищённые платежи и молниеносная доставка делают шопинг с ссылка на кракен маркет лёгким и безопасным. Начните покупать в kraken at ссылка прямо сейчас, чтобы получить доступ к эксклюзивным предложениям и привлекательным распродажам.
Your comment is awaiting moderation.
This really matches my view, always good to see input like this.
In case anyone’s interested, I came across a reference recently: came in handy for me
Let me know what you think.
Your comment is awaiting moderation.
танк 300 цена новый http://tank-3001.ru
Your comment is awaiting moderation.
dog house megaways в рублях бесплатно
https://dog-house.sbs
dog house megaways в рублях бесплатно
https://dog-house.sbs
the dog house new
https://dog-house.sbs
demo dog house megaways
https://dog-house.sbs
играть в док хаус
https://dog-house.sbs
dog-house.sbs
Your comment is awaiting moderation.
?Llevas tiempo queriendo encontrar un buen casino online legal en Espana para ganar dinero verdadero? Como muchos jugadores en Madrid, estuve buscando una plataforma fiable hasta que encontre casinos online real.
Este sitio me parecio una lista confiable de casinos en linea en Espana donde los pagos estan garantizados. Lo mas importante para mi fue que la pagina solo recomienda plataformas legales en Espana. Eso garantiza transparencia. Tambien, las plataformas funcionan genial desde el telefono. Funciona igual desde casa o fuera y todo cargo perfectamente.
?Bonos? ?Claro que si! Las marcas que figuran ofrecen giros gratis para que empieces con ventaja. ?Te gusta el blackjack? Los juegos no decepcionan. Desde juegos de mesa en vivo hasta ruleta europea, todo esta ahi.
Los cobros es confiable. Yo recibi el dinero por transferencia y me llego en 24h. Eso habla bien del sitio. Si estas en Espana, te invito a visitar esta web. Veras sitios seguros para ganar dinero en la actualidad.
Apostar inteligentemente es clave. Y hacerlo en un casino legal y seguro es la prioridad.
No pierdas mas tiempo, echale un vistazo a los listados.
Your comment is awaiting moderation.
It agree, this excellent idea is necessary just by the way
Your comment is awaiting moderation.
There is evidently a lot to know about this. I assume you made some good points in features also.
Your comment is awaiting moderation.
Дизайнерская мебель премиум класса — это воплощение изысканного стиля и безукоризненного качества.
Дизайнерская мебель предлагает уникальные решения для интерьеров. Каждый предмет создается ограниченным тиражом или является единственным экземпляром.
Your comment is awaiting moderation.
Hey, I just stumbled onto your site… are you always this good at catching attention, or did you make it just for me? Write to me on this website — rb.gy/3pma6x?stype — my username is the same, I’ll be waiting.
Your comment is awaiting moderation.
Купить Хавал – только у нас вы найдете цены ниже рынка. Быстрей всего сделать заказ на официальный автосалон haval можно только у нас!
новый хавал цена
хавал москва официальный дилер – https://havalmsk1.ru/
Your comment is awaiting moderation.
мини токарные станки с чпу https://tokarnyi-stanok-s-chpu.ru/ – мини токарные станки с чпу.
Your comment is awaiting moderation.
Visit Casino Toreto — your trusted guide for casino reviews!
Searching for top-rated online casinos?
At our website, you’ll discover real user feedback on new and classic casinos.
Play at many casino games, blackjack, roulette, poker, and fresh games.
Get exclusive offers and increase your winnings today!
Simple and quick: browse by rating, read casino guides, and choose the best site.
Join CasinoTorero.info — your chance for real excitement!
Enjoy and win big!
Your comment is awaiting moderation.
Недорого купить свадебный букет для невесты в Москве возможно. Выбор свадебного букета имеет большое значение для создания идеального образа невесты.
Свадебный букет для невесты купить в Москве недорого.
Несмотря на ограничения в бюджете, можно найти красивые варианты, которые не ударят по карману. Среди большого количества флористических компаний в Москве можно найти множество интересных предложений.
При подборе букета важно помнить о стиле свадьбы и вкусах невесты. Форма, цвет и размер букета должны соответствовать общему стилю свадьбы.
Работая с флористом, невеста может обсудить все нюансы и получить идеальный букет для своего важного дня. Обязательно заказывайте букет заранее, чтобы не сталкиваться с проблемами в день свадьбы.
Your comment is awaiting moderation.
Пионы купить в Москве букет с доставкой на дом недорого
Пионы — это невероятно красивые цветы, которые привлекают внимание своим великолепием и ароматом.
Your comment is awaiting moderation.
Букеты из тюльпанов на 8 марта — это идеальный способ выразить свои чувства и сделать этот день незабываемым. Красивые букеты на 8 марта.
Тюльпановые букеты к 8 марта — это отличный способ выразить свою любовь и уважение к женщинам. Никогда не стоит забывать, что именно внимание и забота делают любой подарок по-настоящему ценным.
Your comment is awaiting moderation.
ремонт электроводонагревателя master-remonta-boylerov.ru
Your comment is awaiting moderation.
Гелиевые шарики — замечательное решение для оформления праздника. Такие шарики придают особую атмосферу и радость любому торжеству.
Шарики с гелием купить для вашего праздника!
Гелиевые шарики могут быть различных форм, размеров и цветов. Вы можете выбрать шарики с рисунком или однотонные, в зависимости от темы вашего события.
Шарики с гелием доступны как в офлайн-магазинах, так и в интернет-магазинах. Приобретать шарики онлайн — это зачастую быстрее и проще.
Важно учитывать меры безопасности при работе с гелиевым наполнителем. Важно следить, чтобы шарики не могли попасть в воду и были под постоянным присмотром.
Your comment is awaiting moderation.
Услуга доставки тюльпанов может стать отличным подарком для любимых. Среди множества цветов тюльпаны выделяются своей красотой и многообразием. Выбор тюльпанов для подарка — это всегда удачное решение.
Закажите букет из тюльпанов и радуйте своих близких свежими цветами!
Тюльпаны бывают разных сортов и оттенков. Каждый сорт имеет свою уникальную красоту и характер. Подобрать букет тюльпанов для любого праздника легко благодаря разнообразию сортов.
Услуга онлайн-доставки тюльпанов становится все более популярной. Выбор цветов и оформление заказа через интернет могут занять всего несколько минут. Различные компании предлагают услуги по доставке тюльпанов на дом.
Доставка тюльпанов в кратчайшие сроки гарантирует радость получателю. Вы можете выбрать подходящий день и время для доставки. Вы можете дополнить букет тюльпанов красивой упаковкой и открыткой.
Your comment is awaiting moderation.
Дизайнерская мебель премиум класса — это воплощение изысканного стиля и безукоризненного качества.
Мебель высокого класса от известных дизайнеров — это не просто предметы интерьера, а настоящие произведения искусства. Уникальный подход к созданию каждой вещи делает ее выдающимся элементом интерьера. В последние годы наблюдается рост интереса к такого рода изделиям.
[…] level? Check out our other container-focused tutorials at DevOps Horizon, including our guide to SSL/TLS certificates which can help secure your containerized […]